Cisco Access Control System (ACS)
Cisco Secure Access Control System (ACS) is a comprehensive network access policy solution that provides authentication, authorization, and accounting (AAA) services. It enables organizations to centrally manage network access policies, ensuring secure and efficient access to network resources by validating user credentials and enforcing security policies.
Installing ACS
Deploy the ACS VM as usual
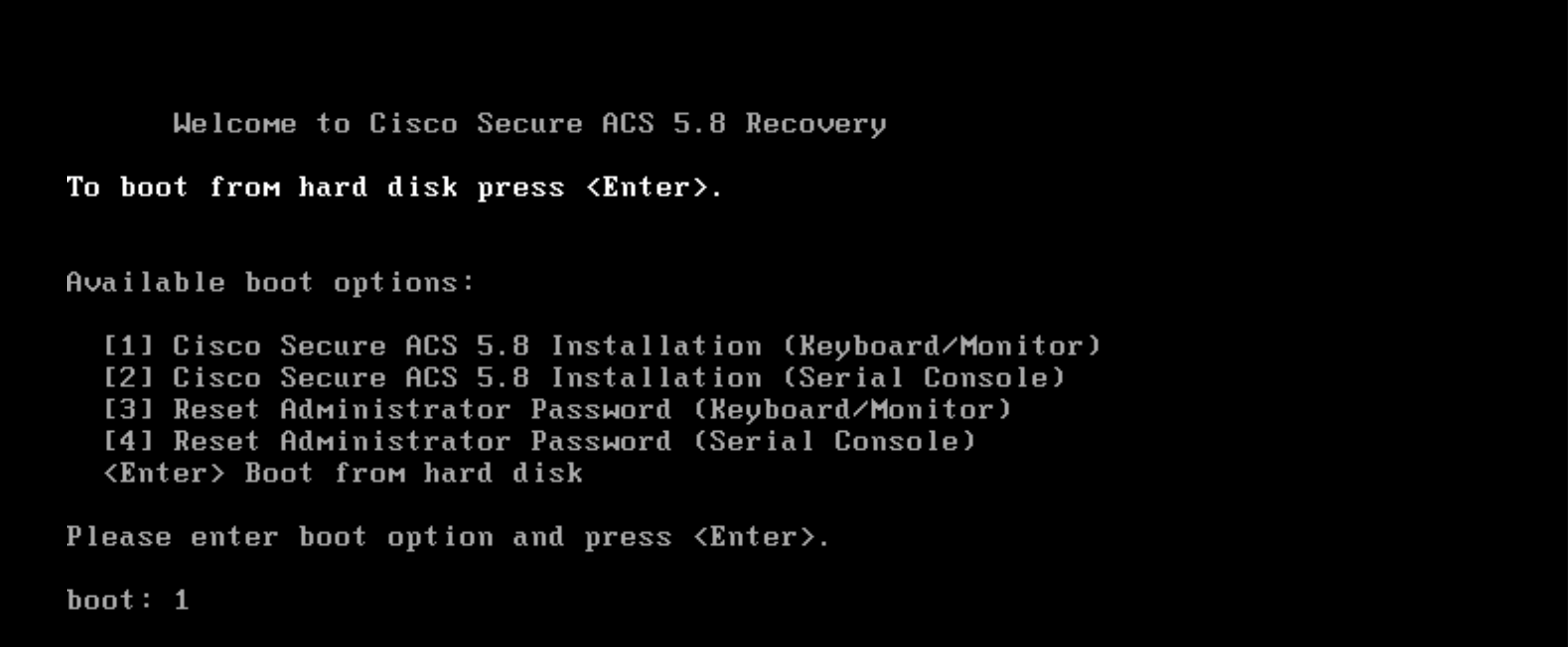
Connect the console and select the boot option
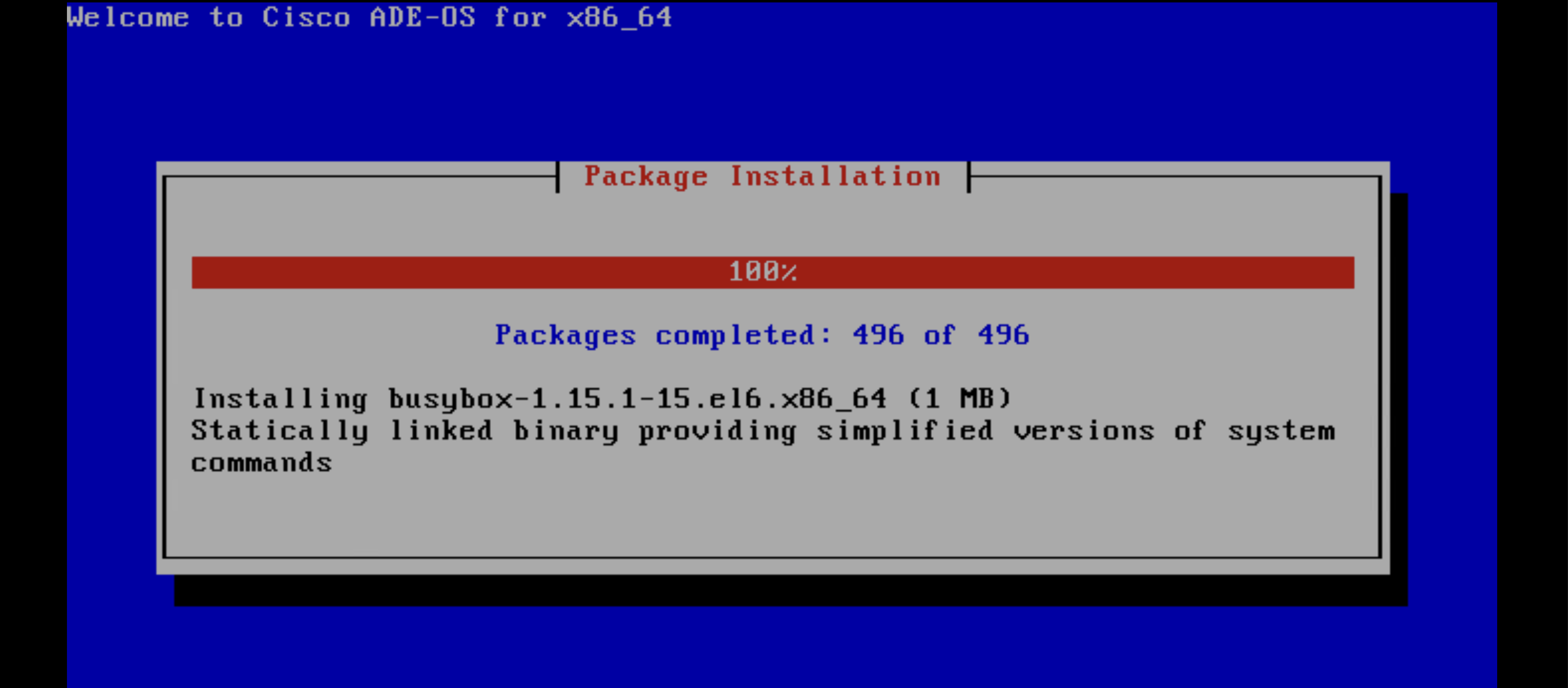
The package installation will start
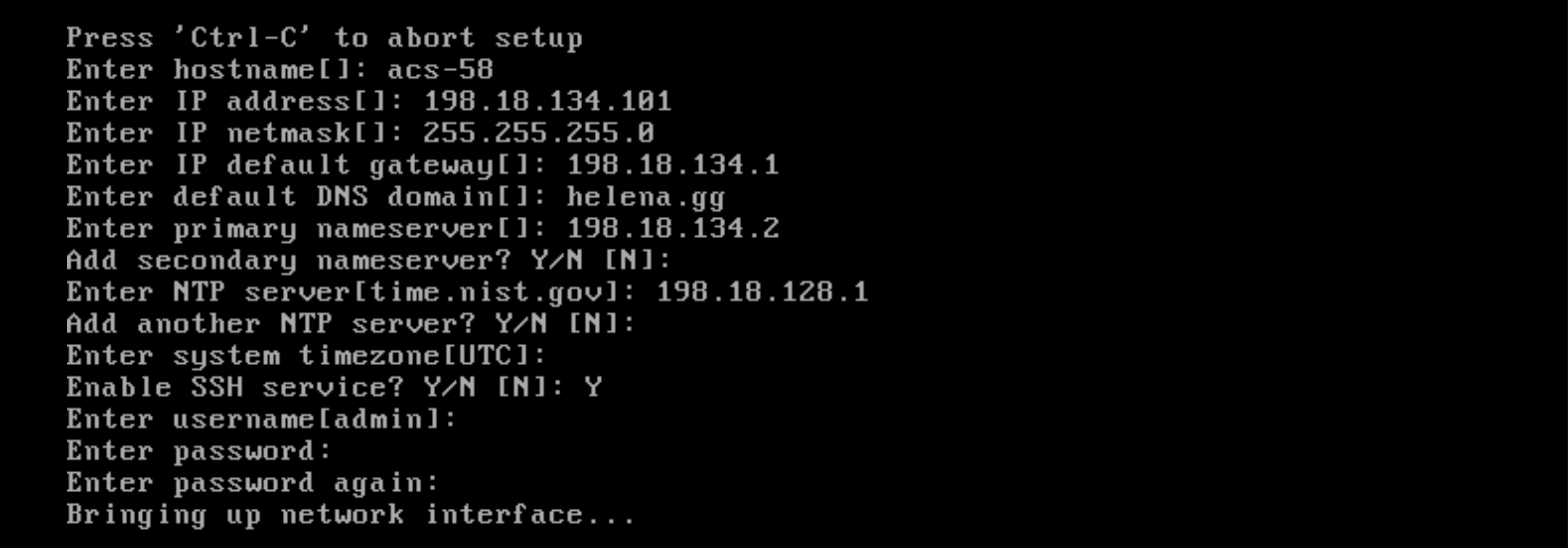
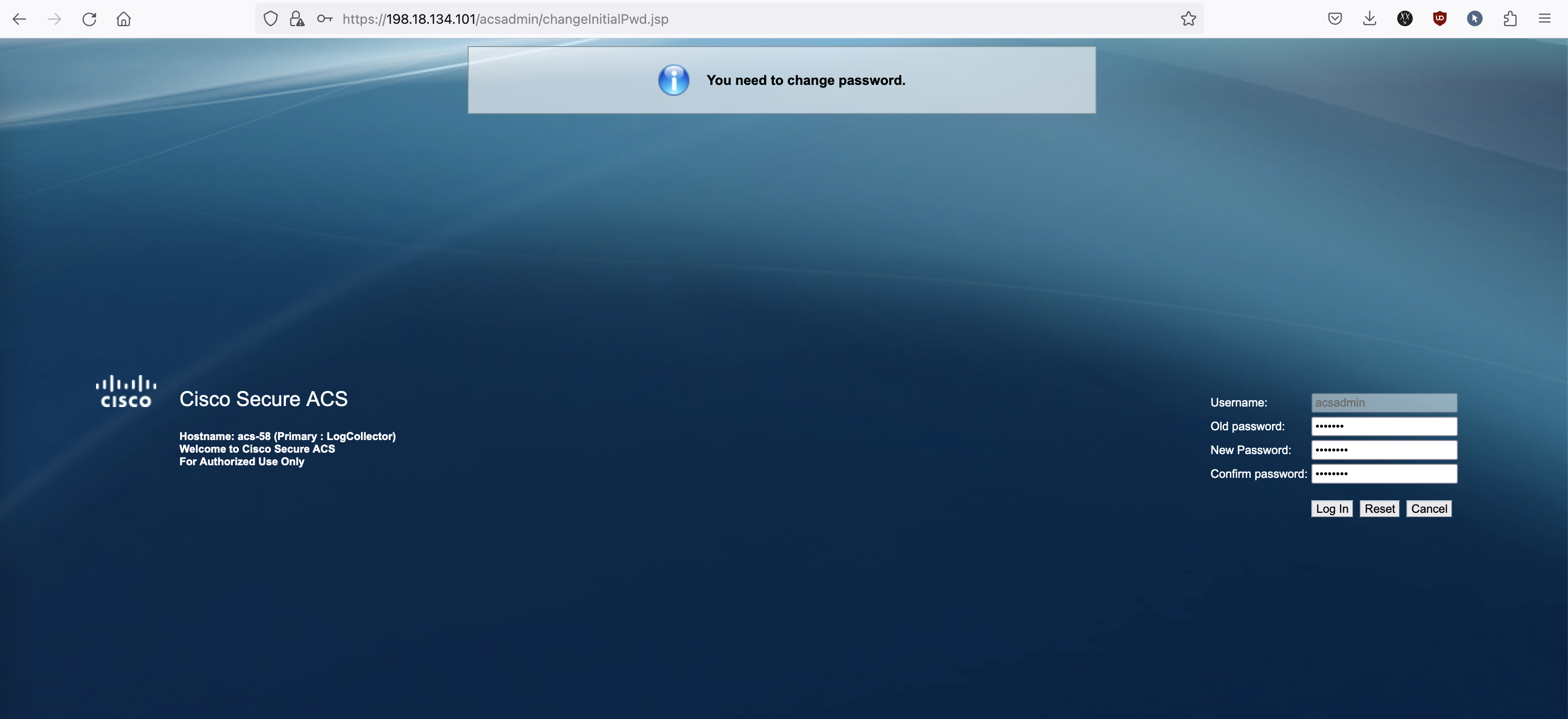
After installation finishes, type “setup” and configure the networking stuff
Next the Web UI should be accessible
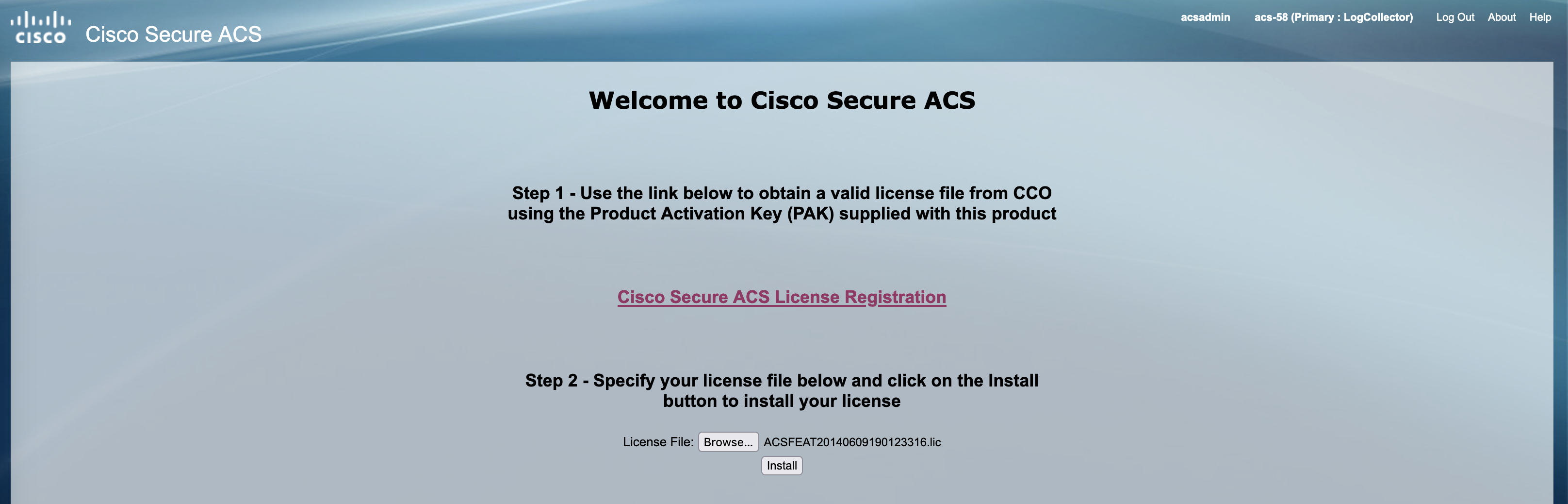
Finally select the license
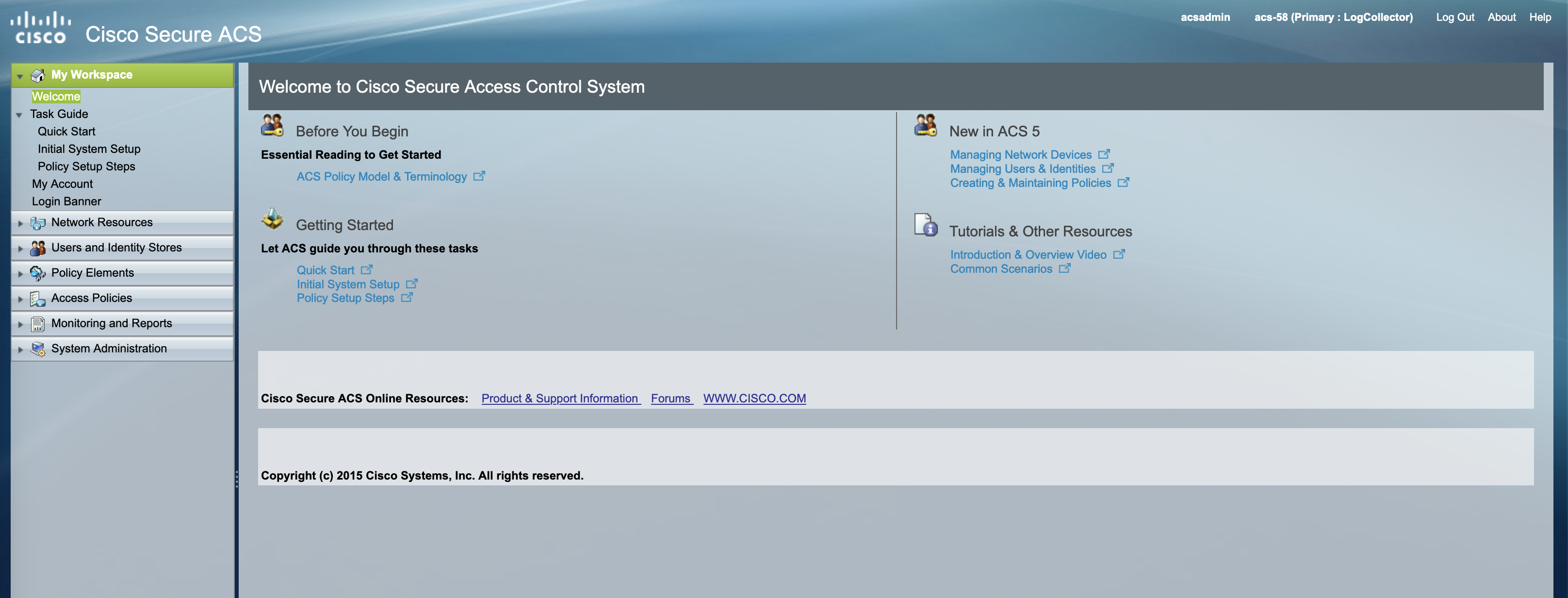
Now the ACS is up and running
Configuring TACACS Device Admin
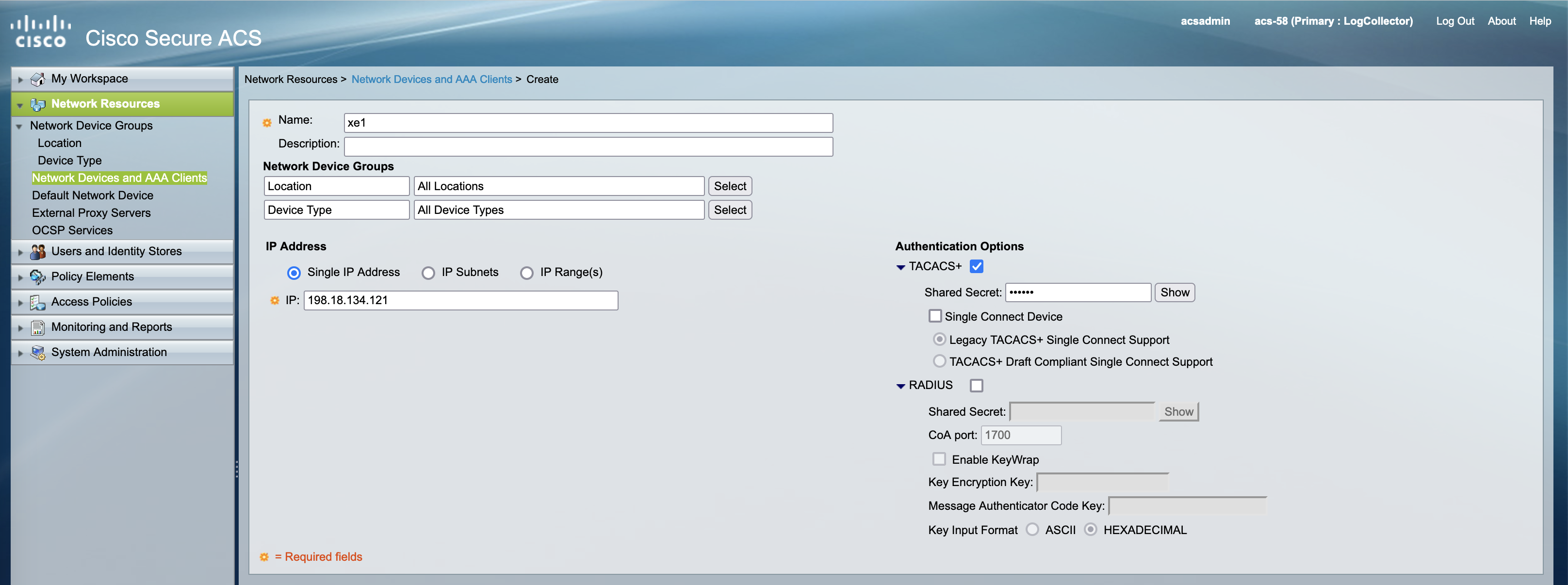
Adding Network Acccess Device
On Network Resources, add the Network Device
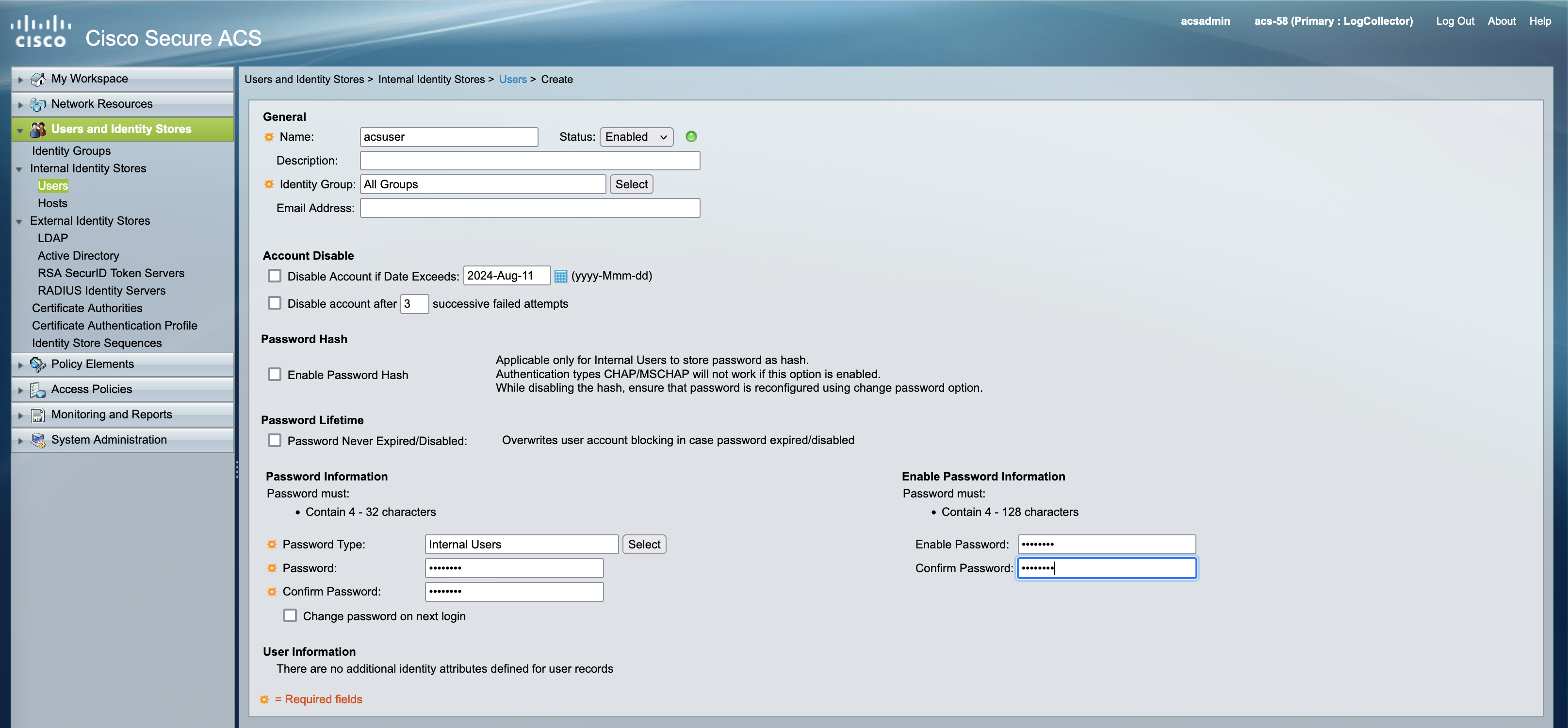
Creating User
Next create an internal user used for authentication
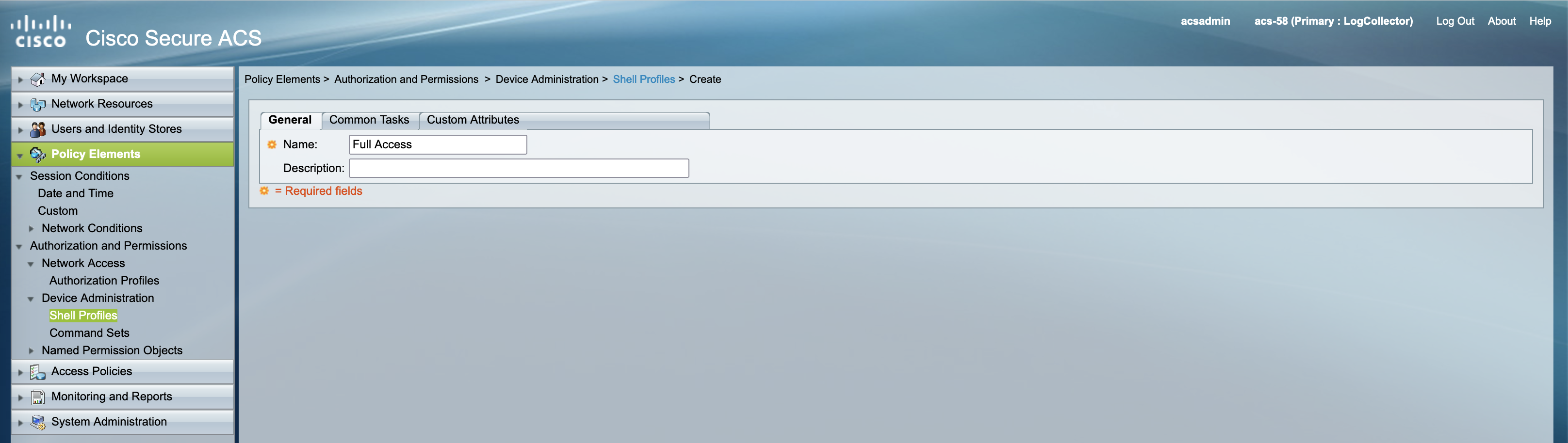
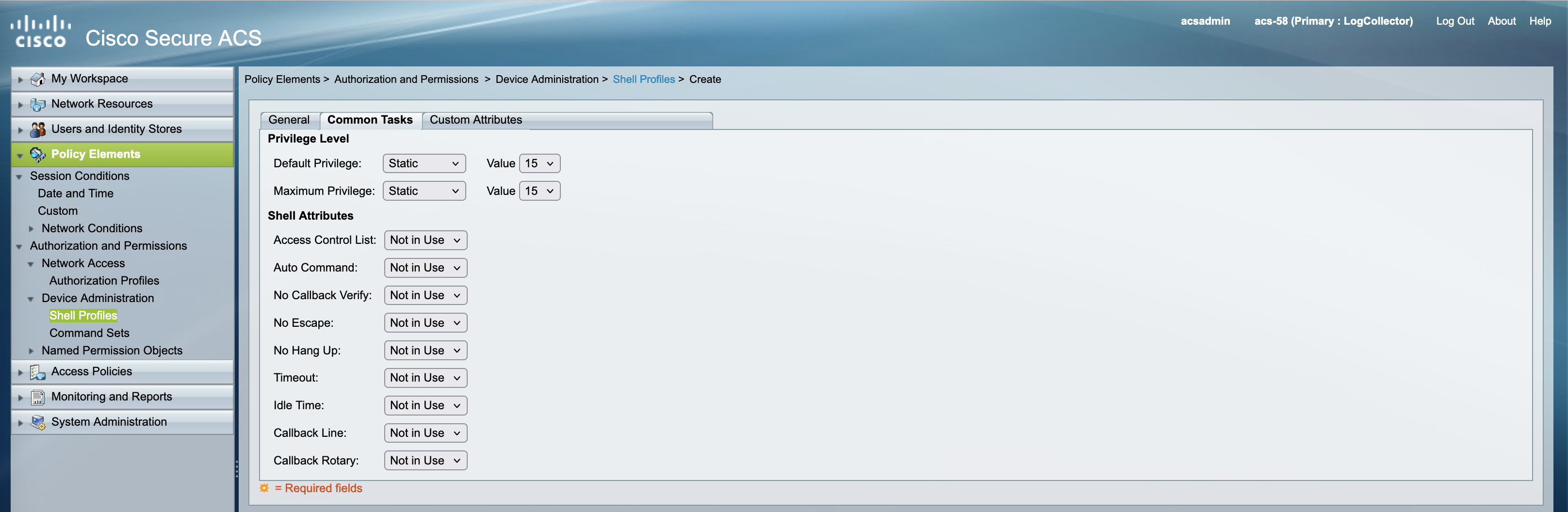
Configuring Shell Profiles
Next create a shell profile providingg full access to the NAD
Here we configure the privilege level to be 15 which is the highest for cisco devices
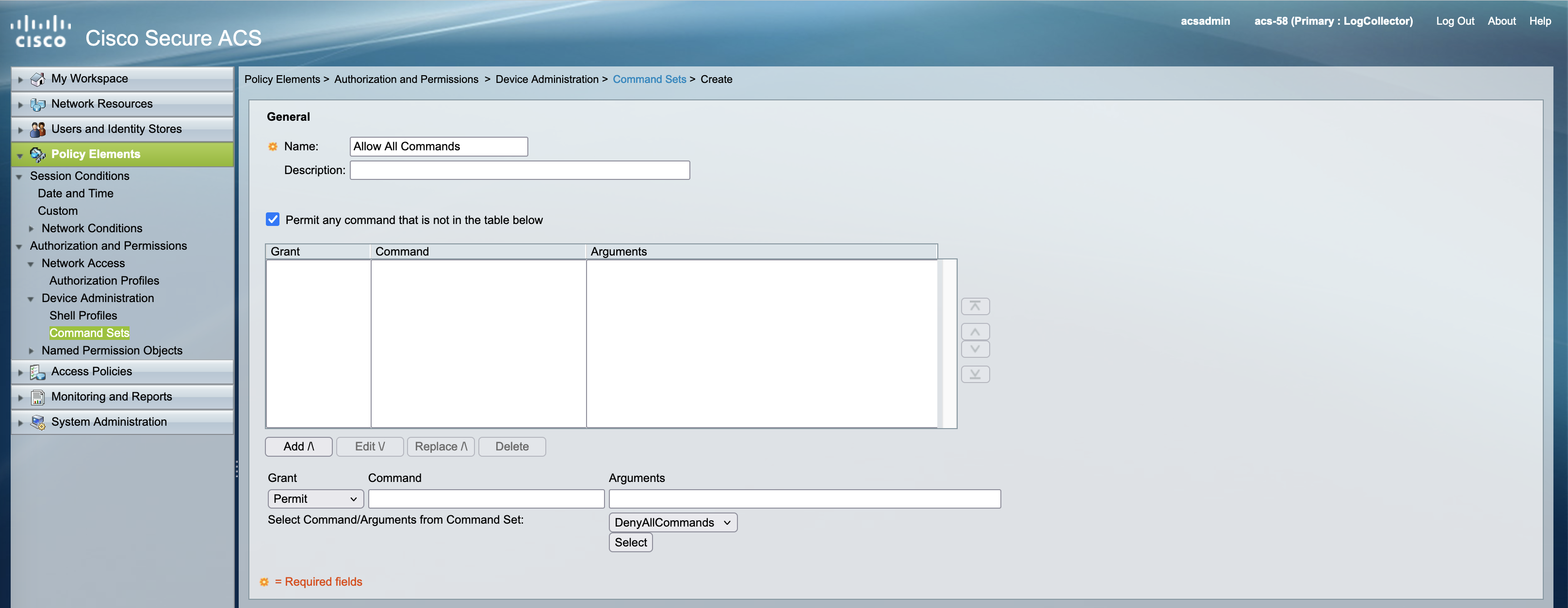
Configuring Command Sets
After that create a command sets allowing full access to all available commands
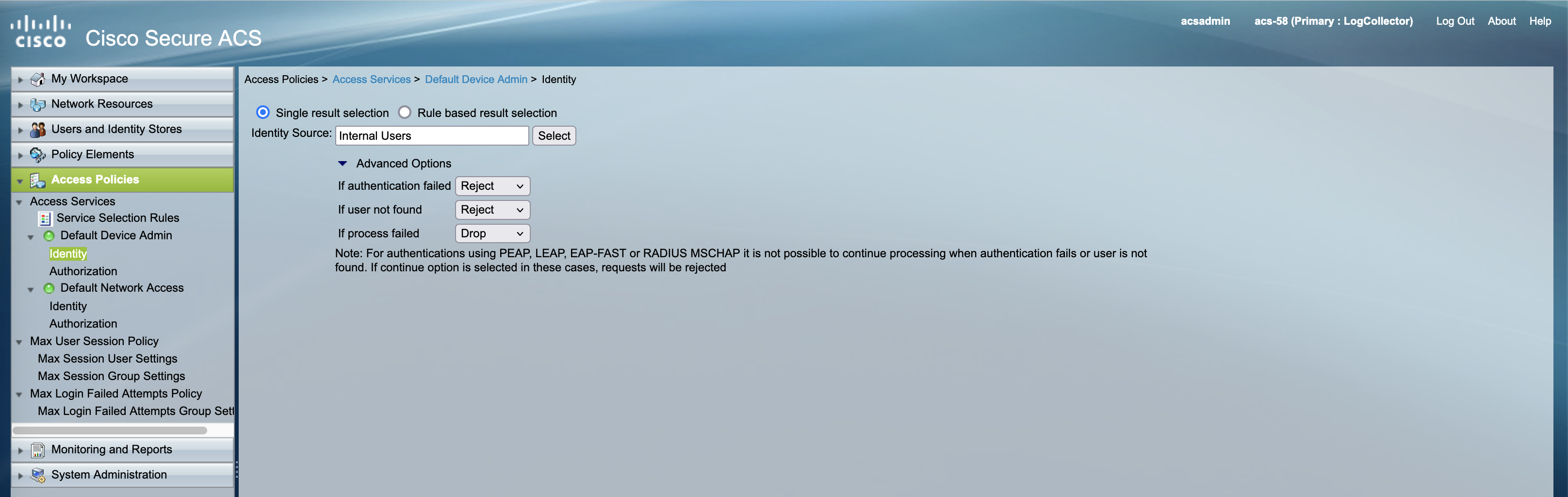
Configuring Identity
Here we configure the identity source for user authentication
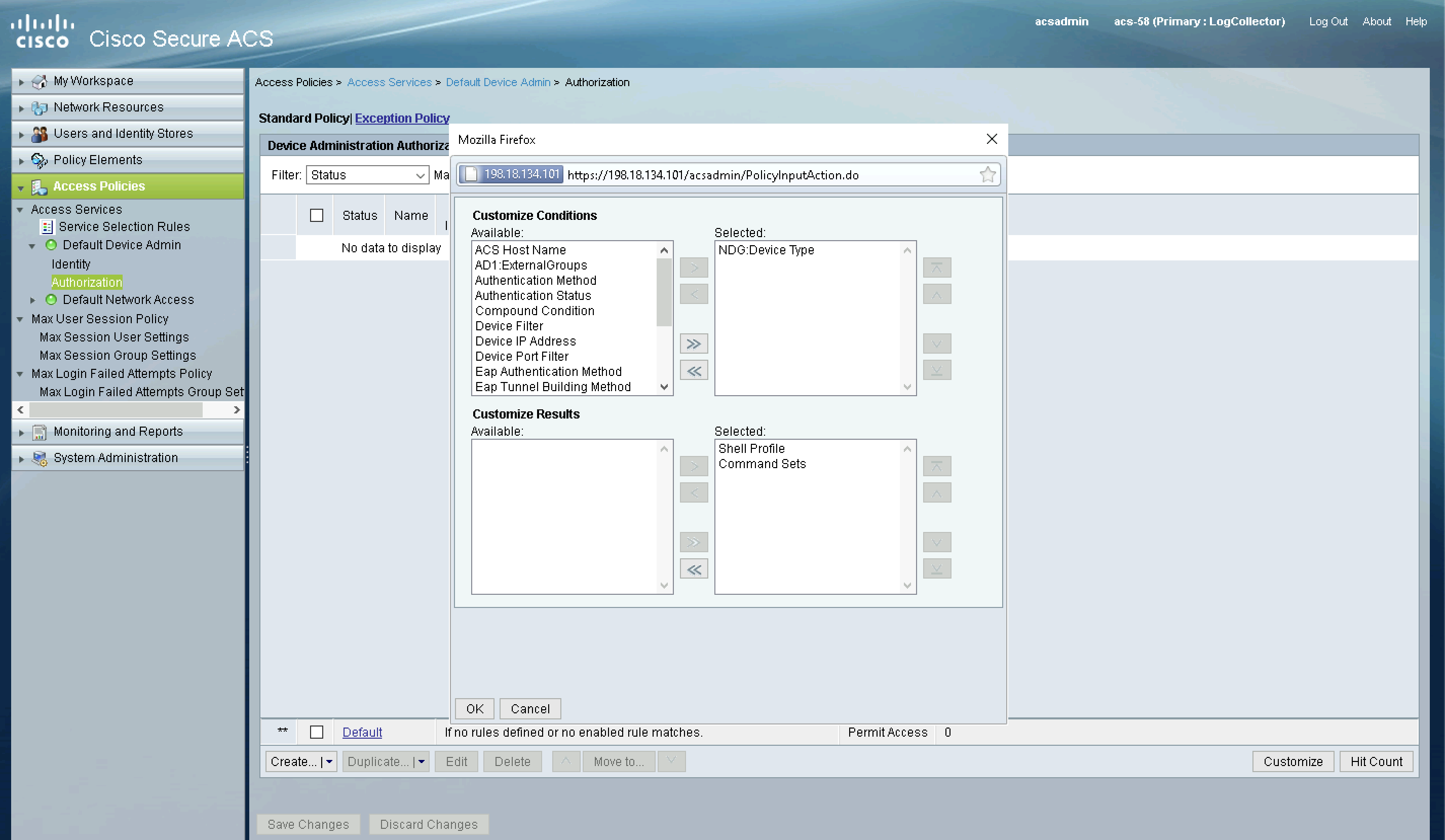
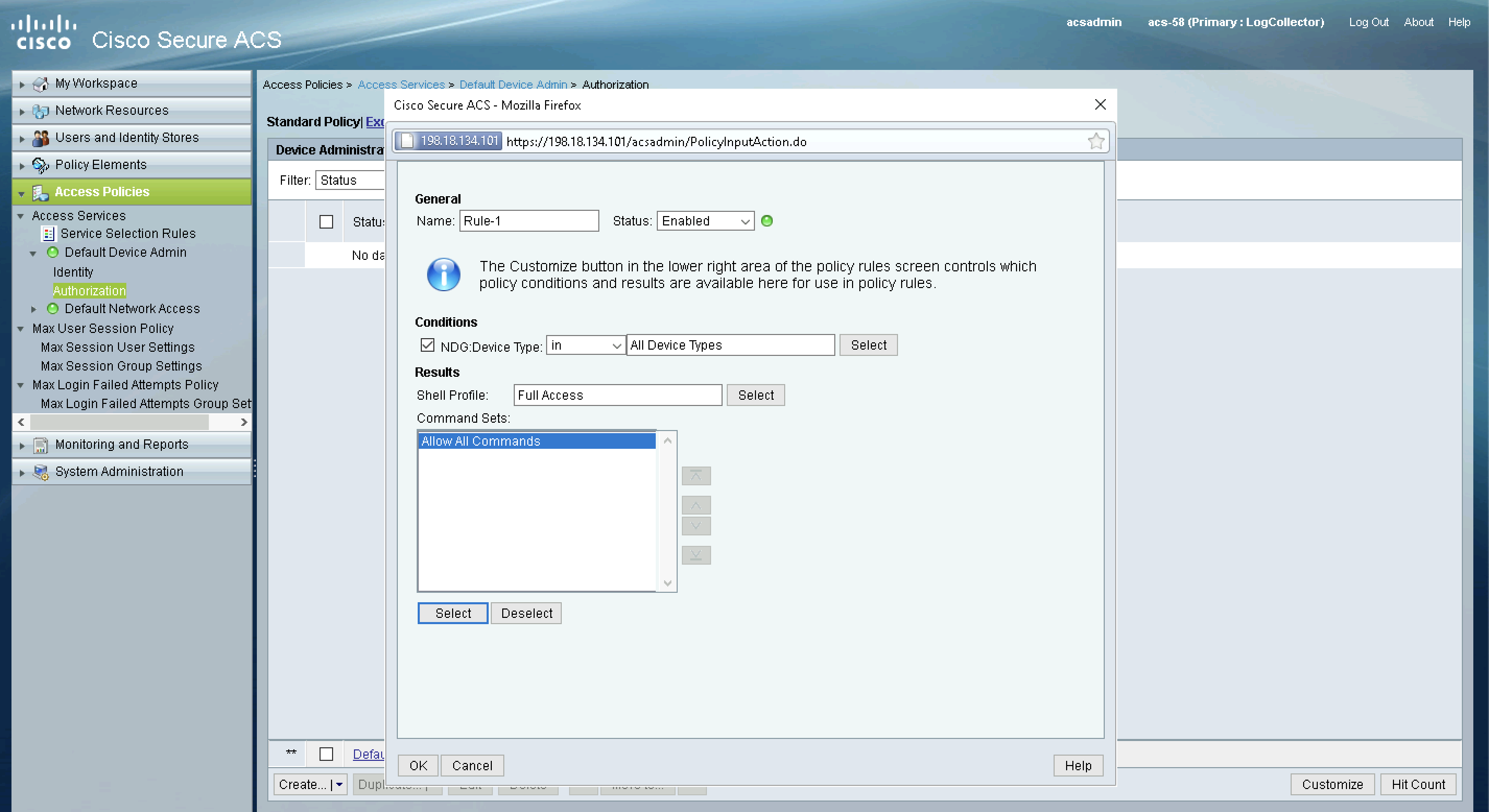
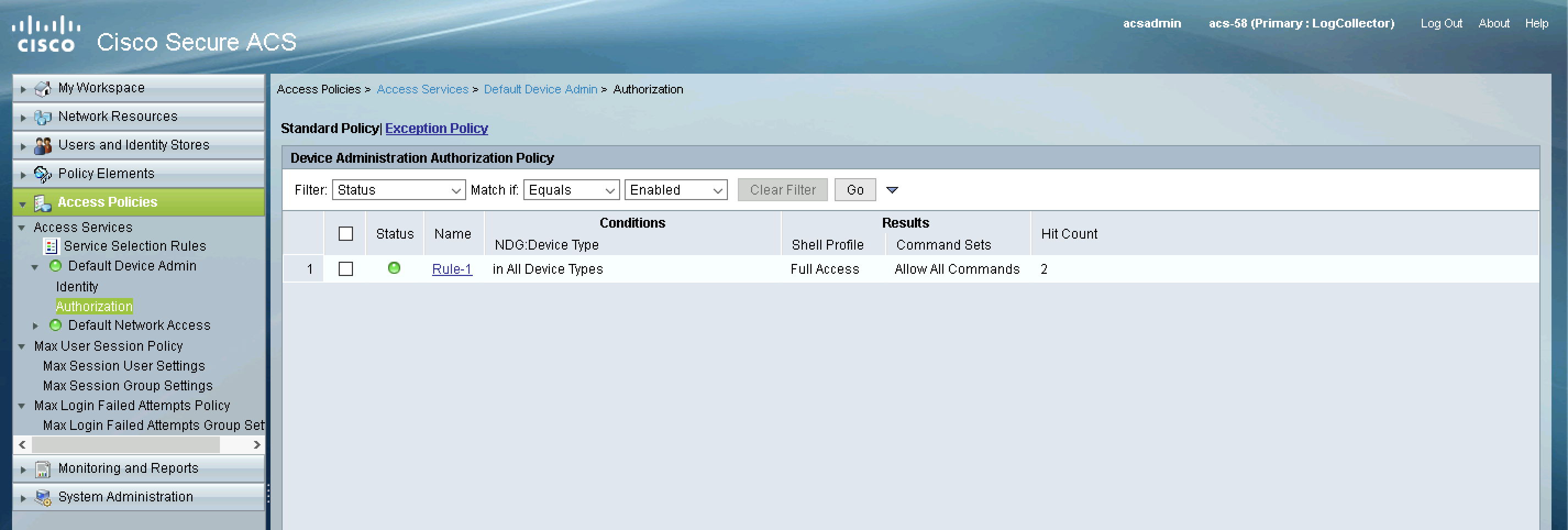
Configuring Authorizaton Policy
Finally configure the Authorization Policy to use the Device Type as the condition and Shell Results & Command Sets created earlier as the results
Then create a new rule for the TACACS authentication
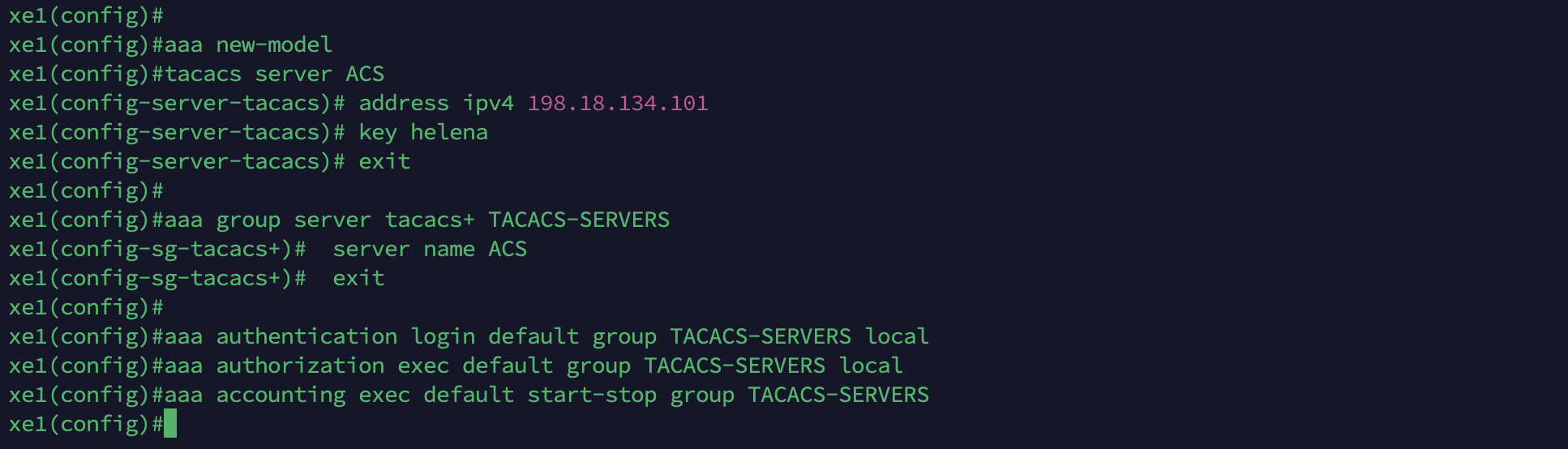
Configuring TACACS on Cisco Router
Next configure the NAD to use the ACS for TACACS authentication
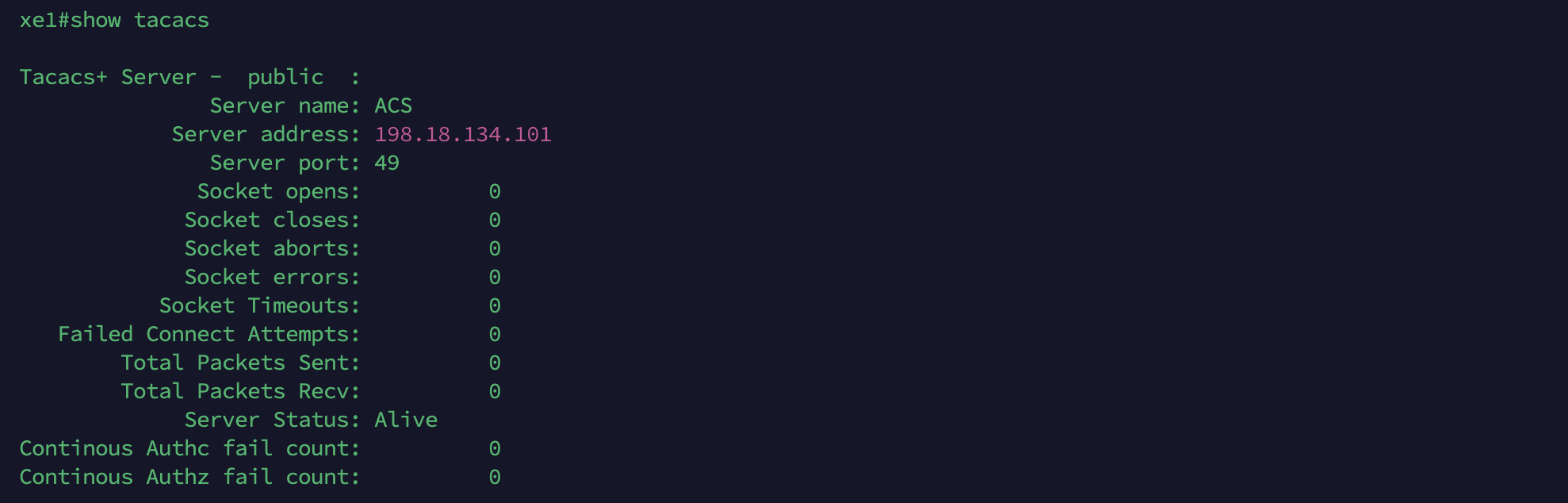
Run show tacacs to show the configured server
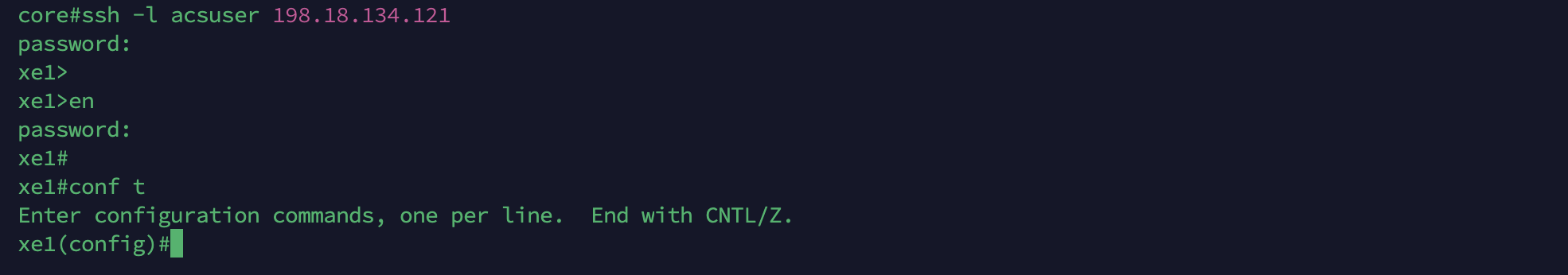
Loggin in to NAD
Now when we try logging in using ACS user, we should be able to access the device
Back on the ACS, we can see the rule being hit