Cisco ASA - Access List Policy & NAT
Configuring Access List Policy
Create access list to enable traffic from inside to outside and vice versa
1
2
access-list inside_access_out extended permit ip any any
access-list outside_access_in extended permit ip any any
Apply the access list to the respective interface
1
2
access-group inside_access_out in interface inside
access-group outside_access_in in interface outside
Here’s how the config shown in ASDM
Configuring Static NAT
Next configure the static NAT
1
2
3
object network INSIDE_HOST
host 63.0.0.141
nat (inside,outside) static 198.100.0.3
Here’s the static route configuration on ASDM
Testing Static Route
Inside to Outside
Connecting from inside host to the internet shows a success
Outside to Inside
The web server on inisde host can be accessed using the NAT IP Address
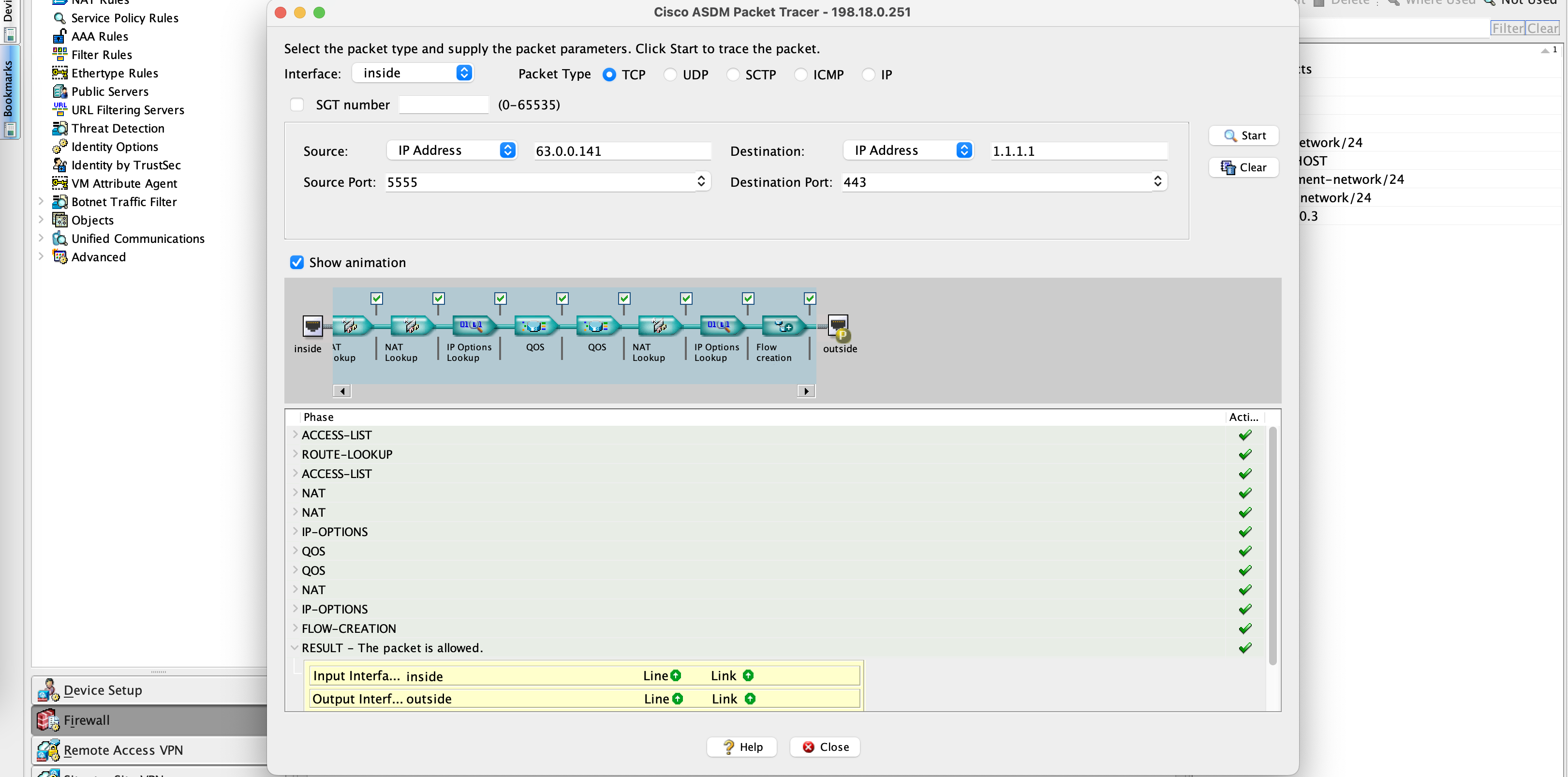
ASDM also has a neat packet tracer feature to test traffic
Inside to Outside
Outside to Inside
Configuring Dynamic NAT Overload
Because we already have the policy configured, we can proceed with configuring the PAT configuration
1
2
3
object network INSIDE_NETWORK
subnet 63.0.0.0 255.255.255.0
nat (inside,outside) dynamic interface
This is the configuration shown on ASDM
Now trying to connect to internet from any IP on the inside segment should be successful
This post is licensed under CC BY 4.0 by the author.