Active Directory Certificate Services (ADCS)
What is Active Directory Certificate Services?
Active Directory Certificate Services (AD CS) is a Microsoft Windows Server role that manages digital certificates for secure network communications, encryption, user/device authentication, and trust establishment. It includes a Certificate Authority (CA) for issuing and managing certificates and builds the Public Key Infrastructure (PKI) framework.
Adding ADCS Roles
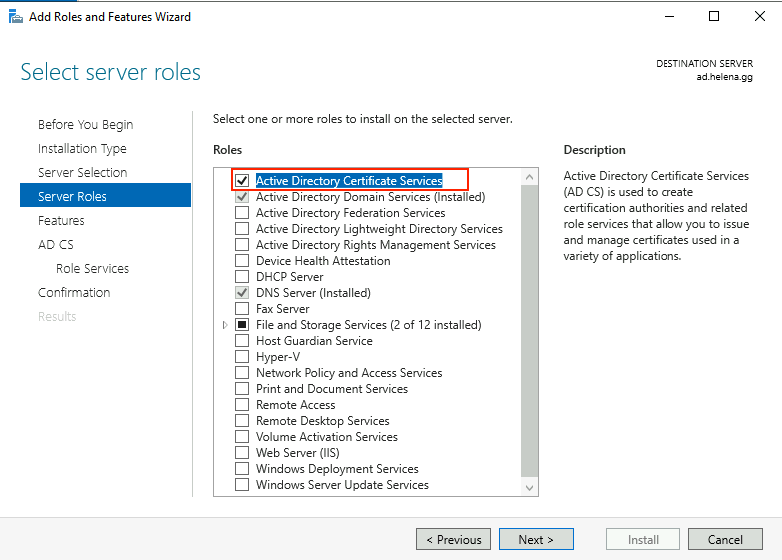
Add the role Active Directory Certificate Services
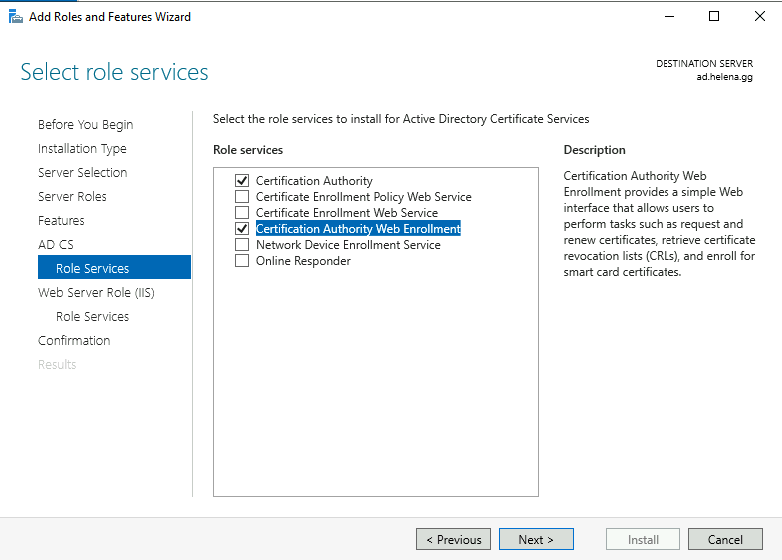
On role, select Certiticate Authority and Certiticate Authority Web Enrollment
CA Web Enrollment is a web-based interface that allows users to request and manage digital certificates from a Certificate Authority (CA)
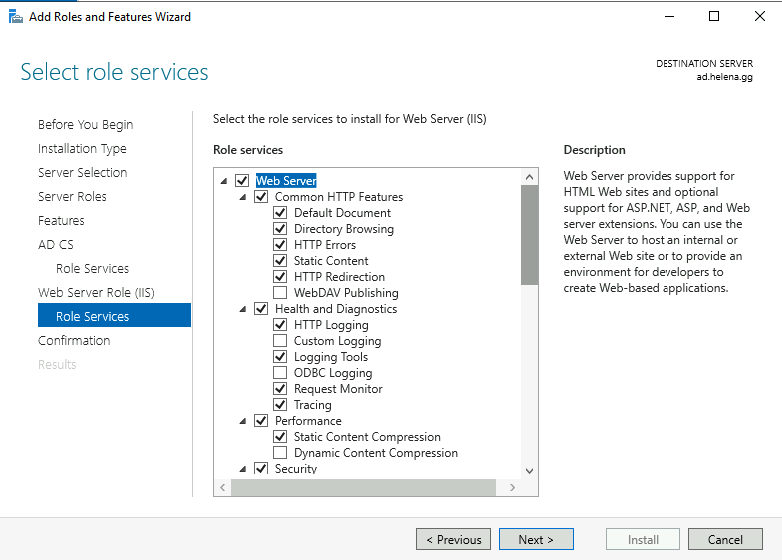
For role services, leave it as it is and proceed with install
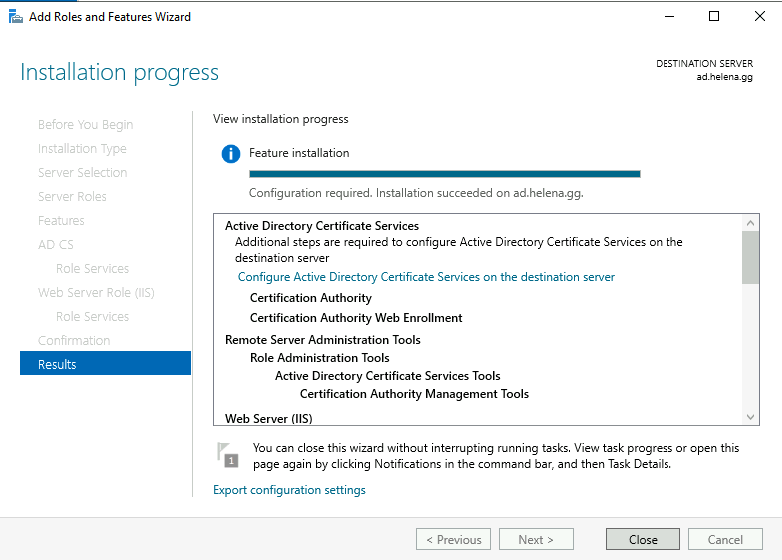
After it finishes, select Configure Active Directory Certificate Services on Desination Server
Configuring ADCS
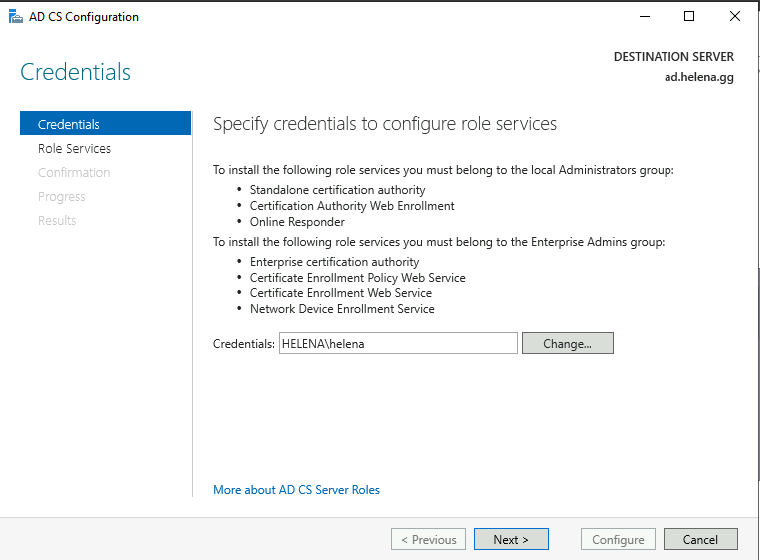
First, select the admin account to manage the CA
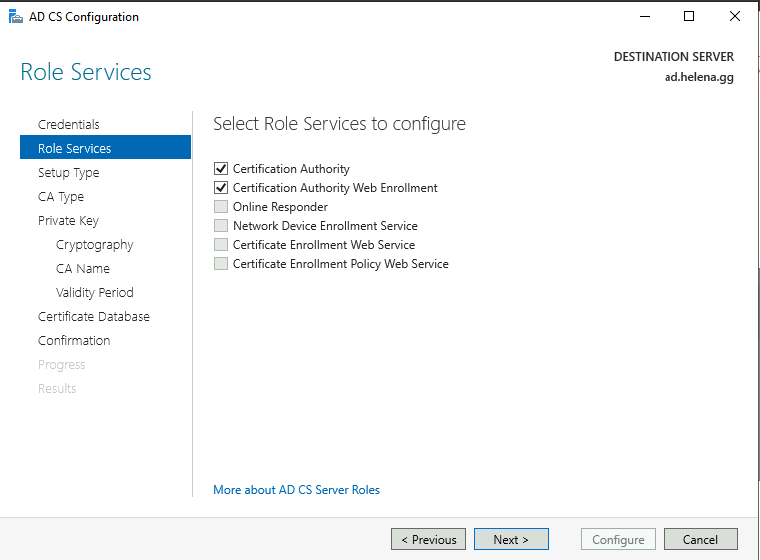
Select both roles
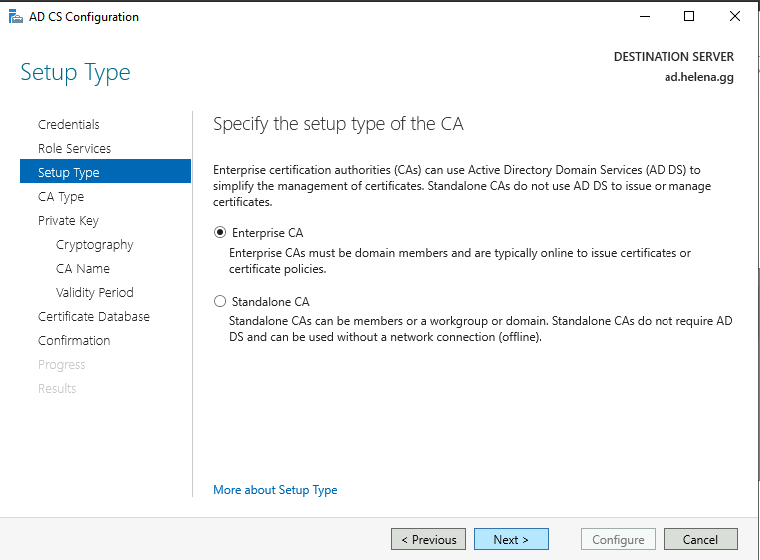
Select Enterprise CA
- Enterprise CA is centralized system integrated with Active Directory, offering advanced features like hierarchical structures and certificate templates.
- Standalone CA is isolated, simpler instance without Active Directory integration.
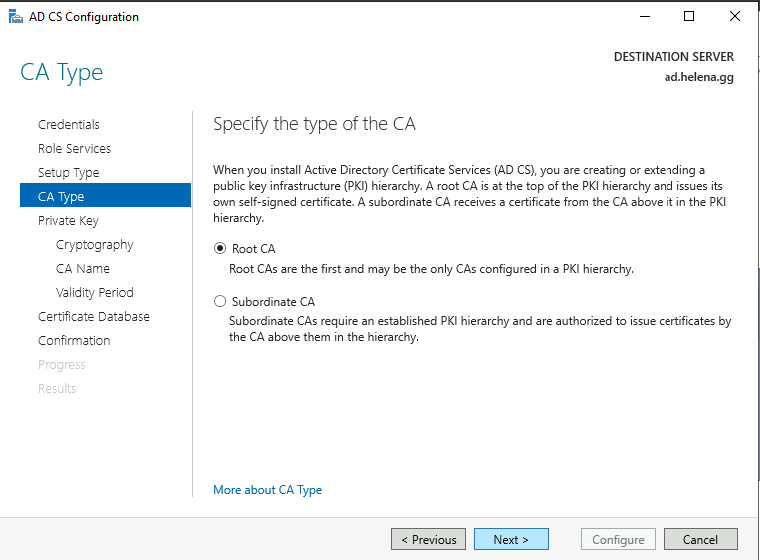
Select Root CA
- Root CA is the top-level authorities in a PKI hierarchy.
- Subordinate CA is intermediary entitiy that inherits from existing Root CA.
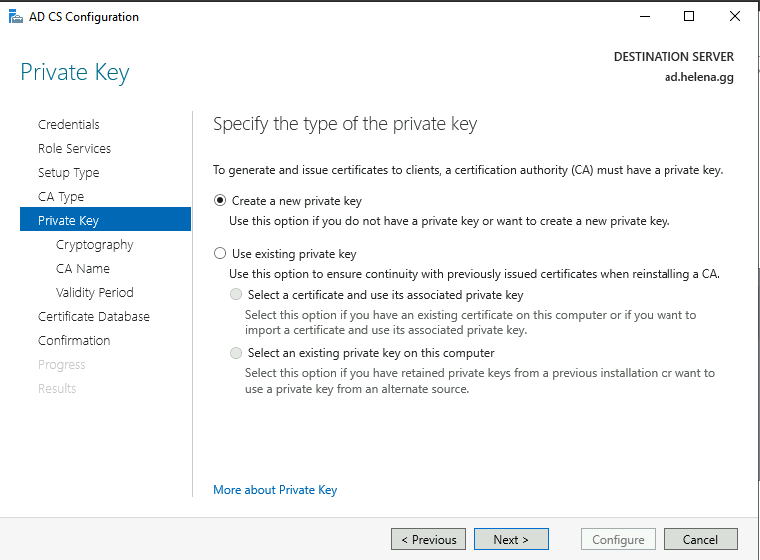
Select create New Private Key
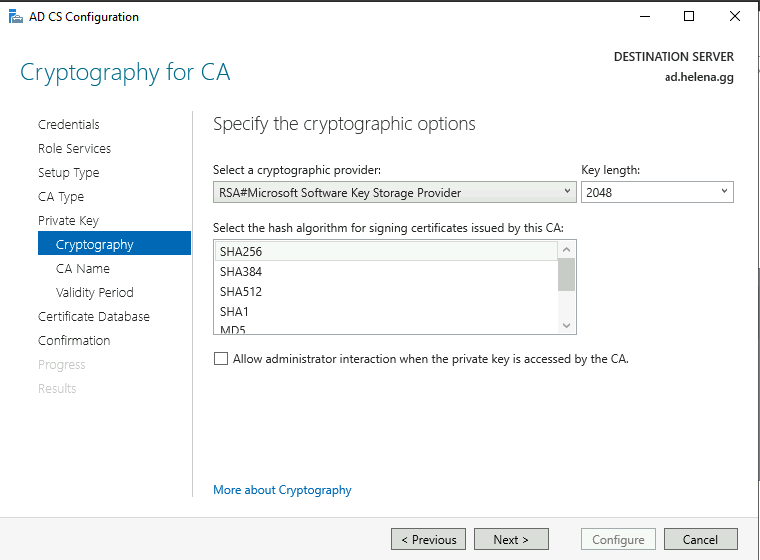
For cryptographic option, leave it as default and next
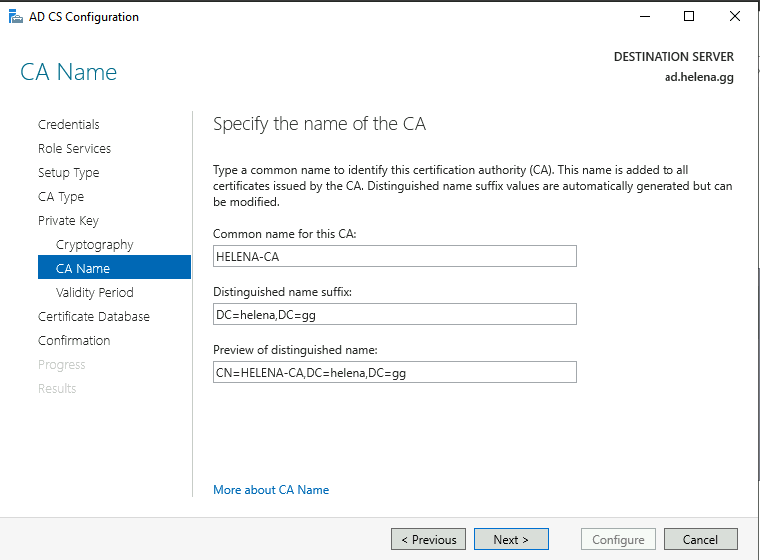
Specify the CA’s name
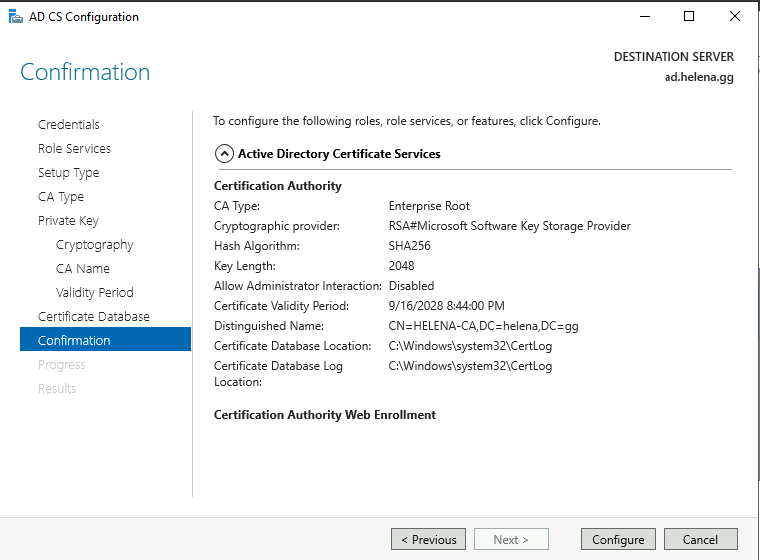
Confirm and configure
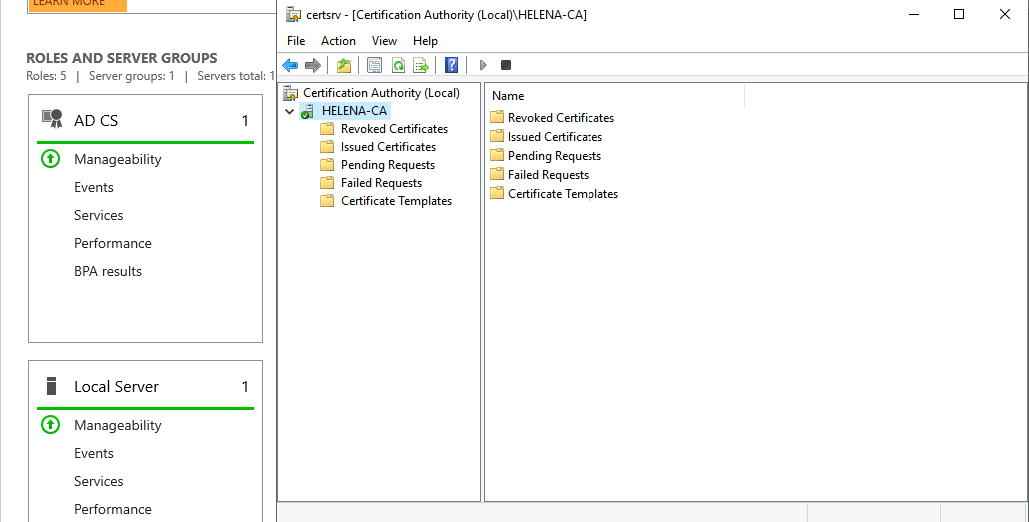
Now the CA is up and running
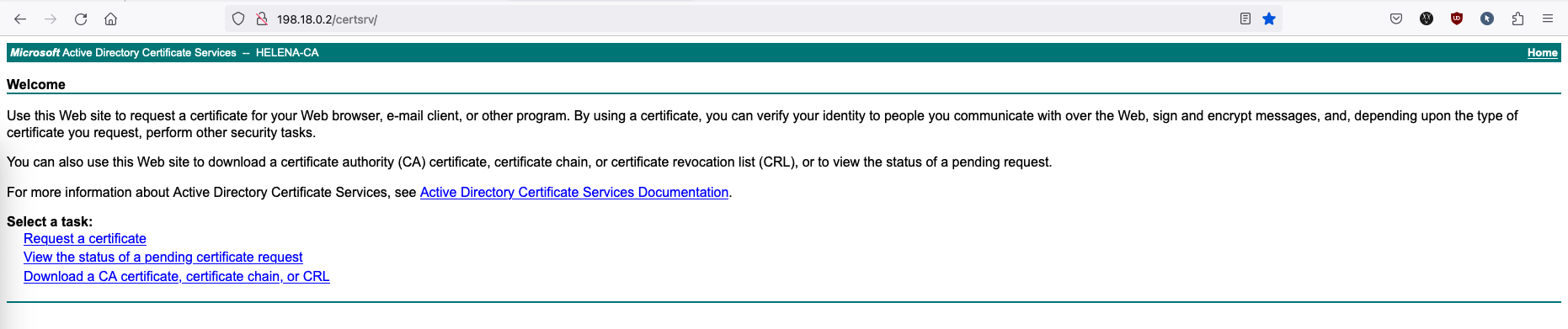
And if we access the CA’s IP on web browser, we should see the CA Web Enrollment page
Now we can use the CA to sign cerfificates
Creating Custom Templates
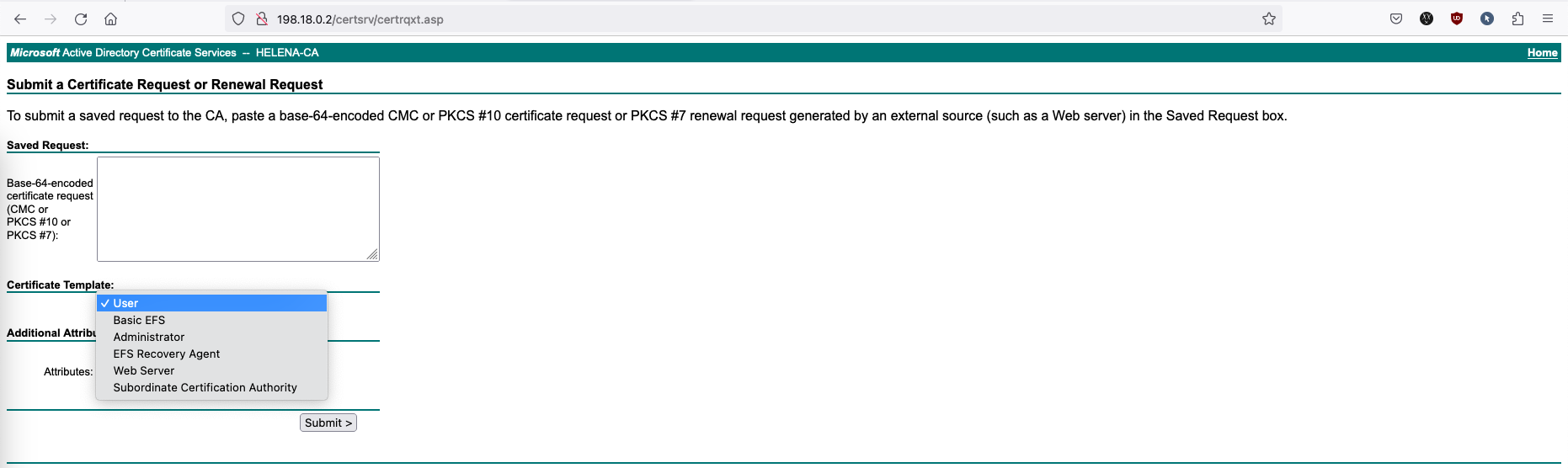
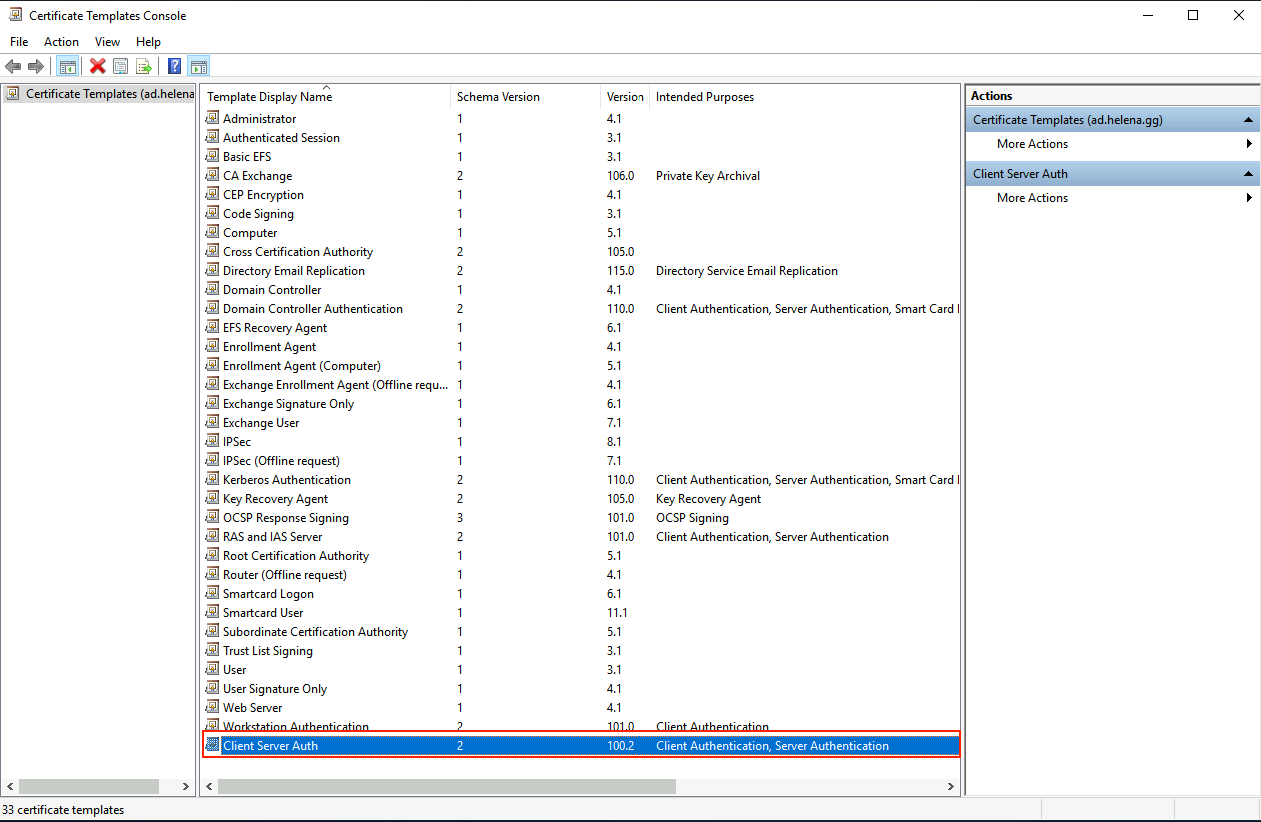
By default, the CA only offers 5 certificate templates, which is enough if all we need is this CA to only sign normal web servers.
But some app requires different kind of template, for example Cisco Expressway and Cisco Meeting Server (CMS) require certificate that allow both Server Authentication and Client Authentication, so lets create the template for that case.
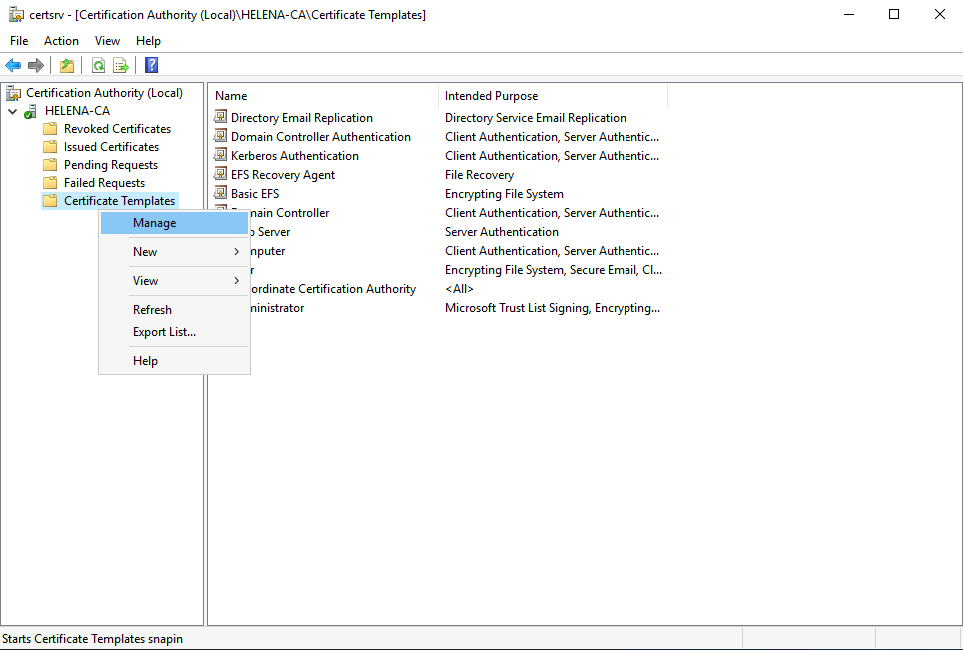
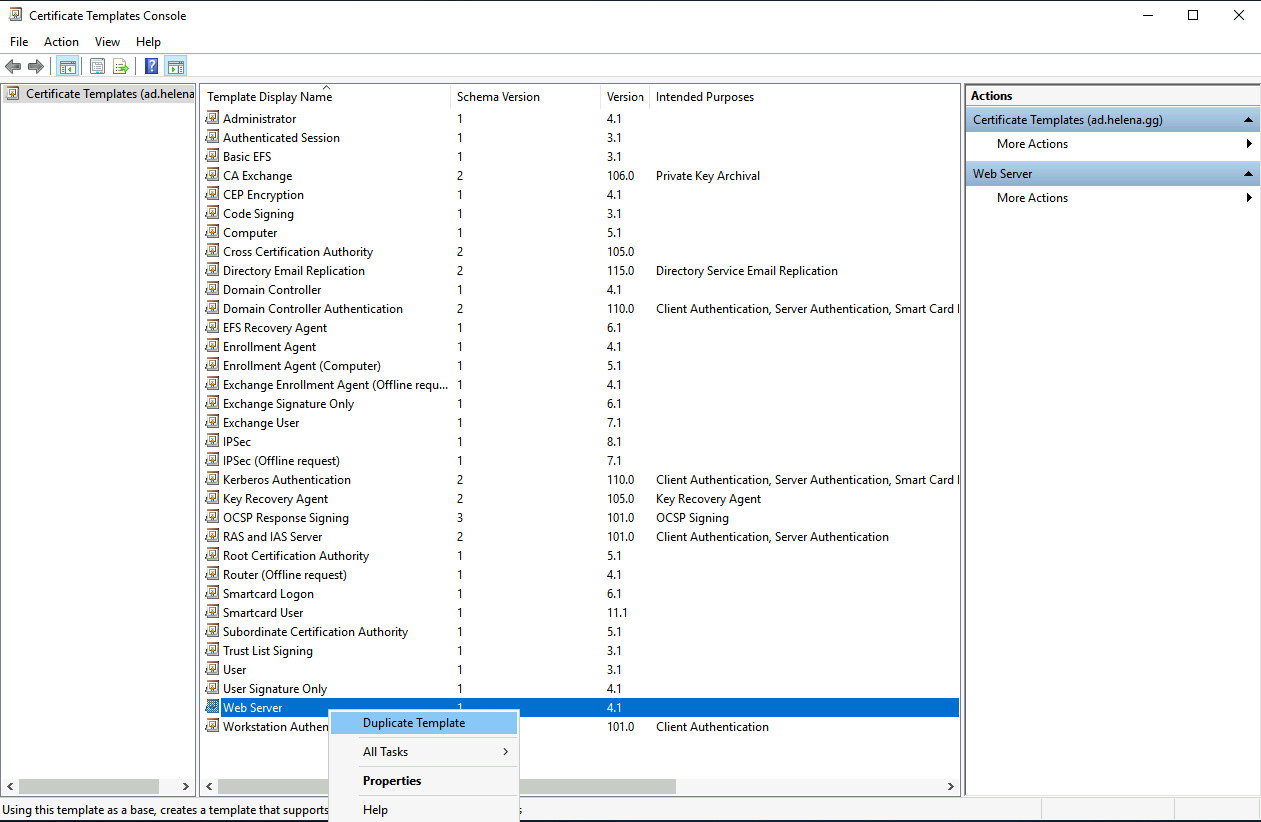
Open Certificate Authority » Certificate Templates » Manage
On Web Server, right click and choose duplicate
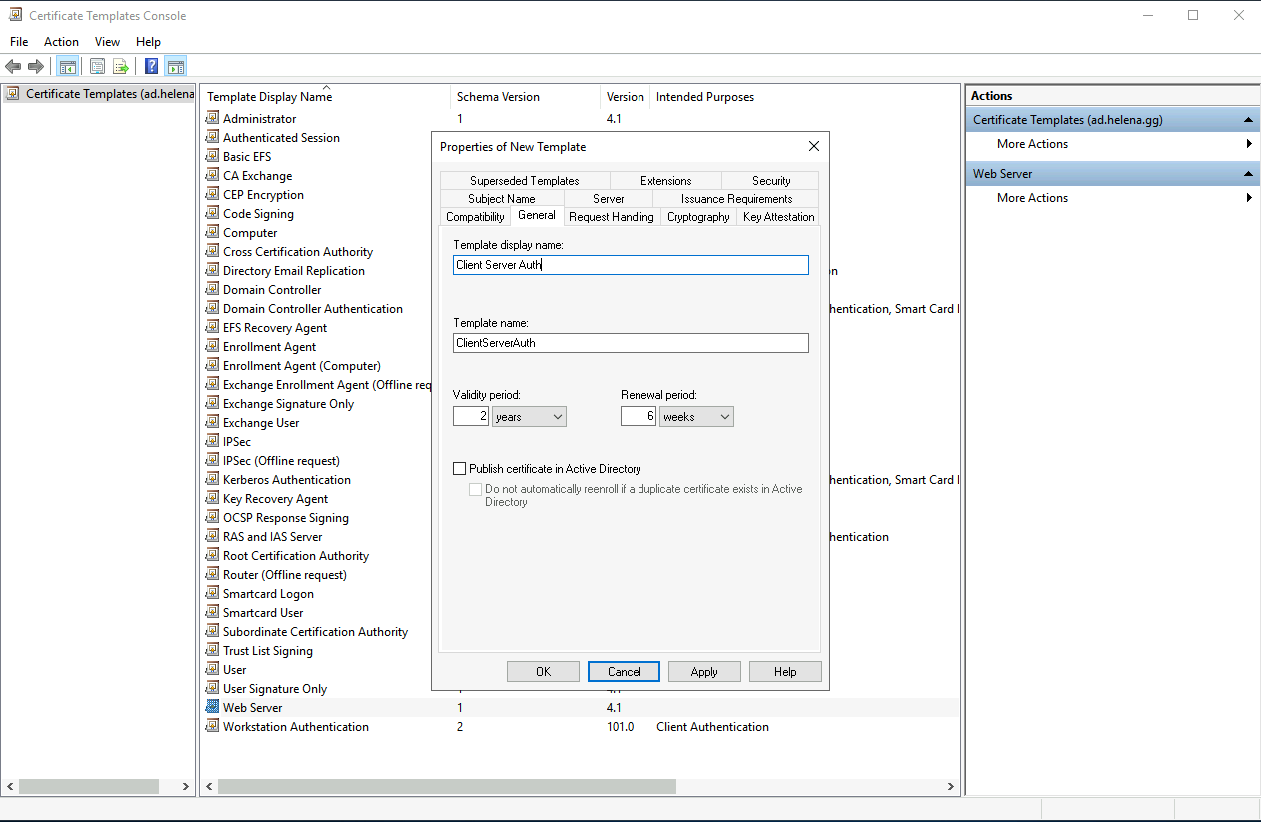
On General, give it a name
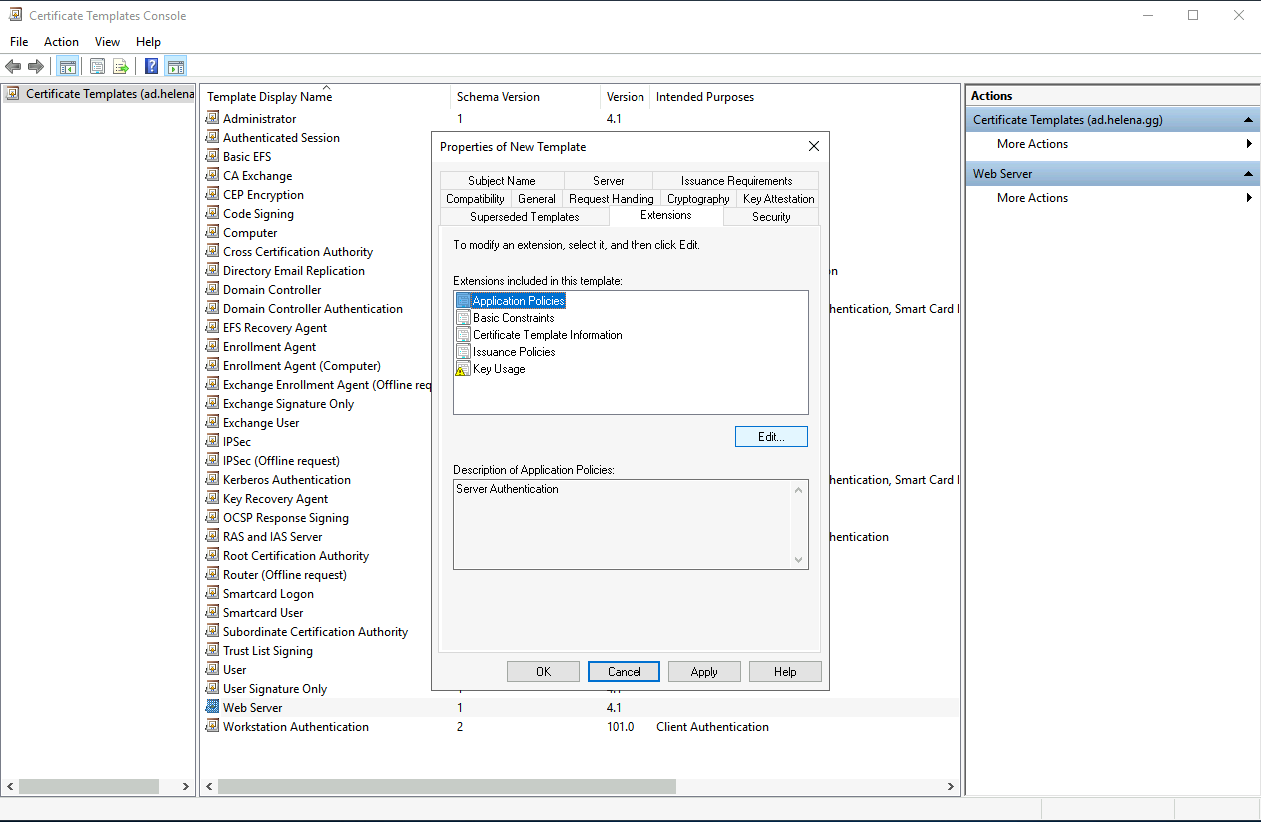
On Extensions, select Application Policies, edit
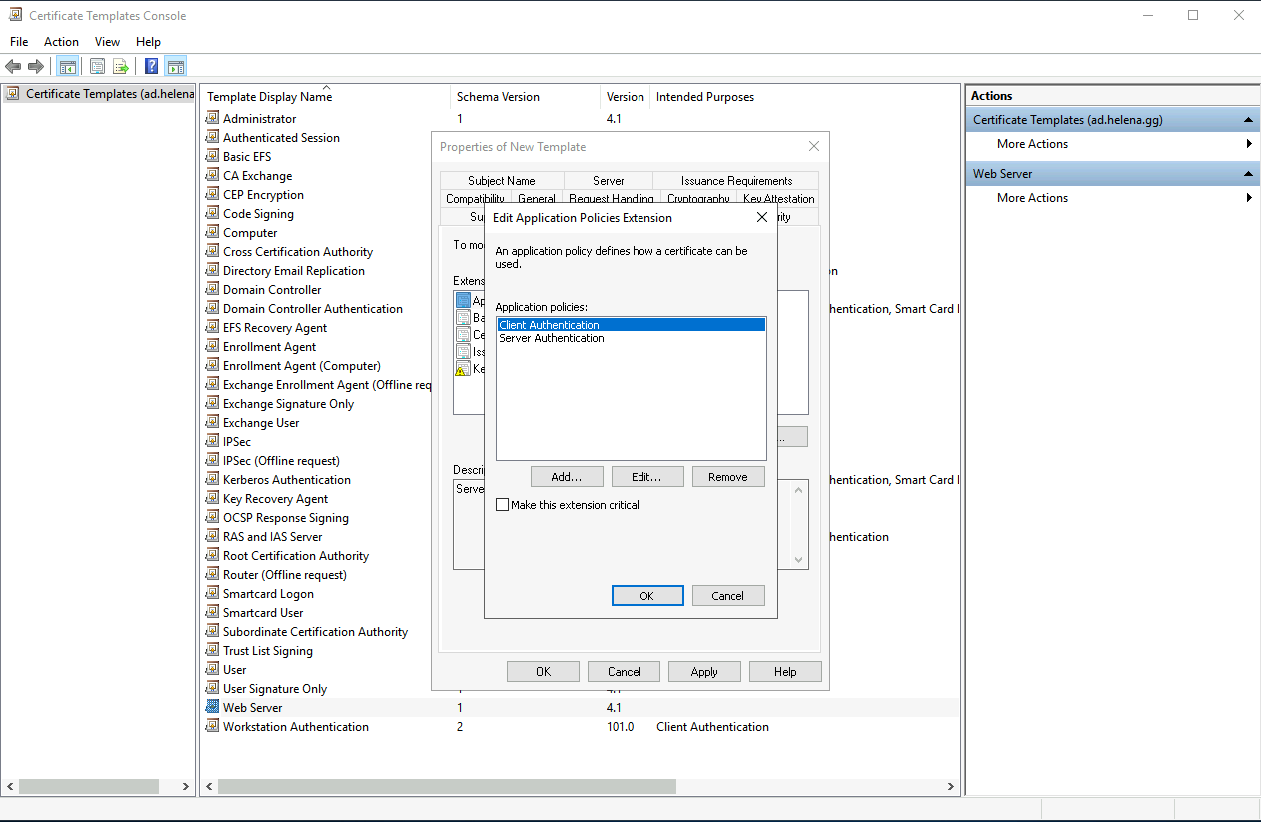
Add Client Authentication on top of the existing Server Authentication
- Server Authentication confirms the identity of the server or service that the client is connecting to.
- Client Authentication confirms the identity of the client (user or device) trying to access a service or server.
Now we have the new template, exit from this window
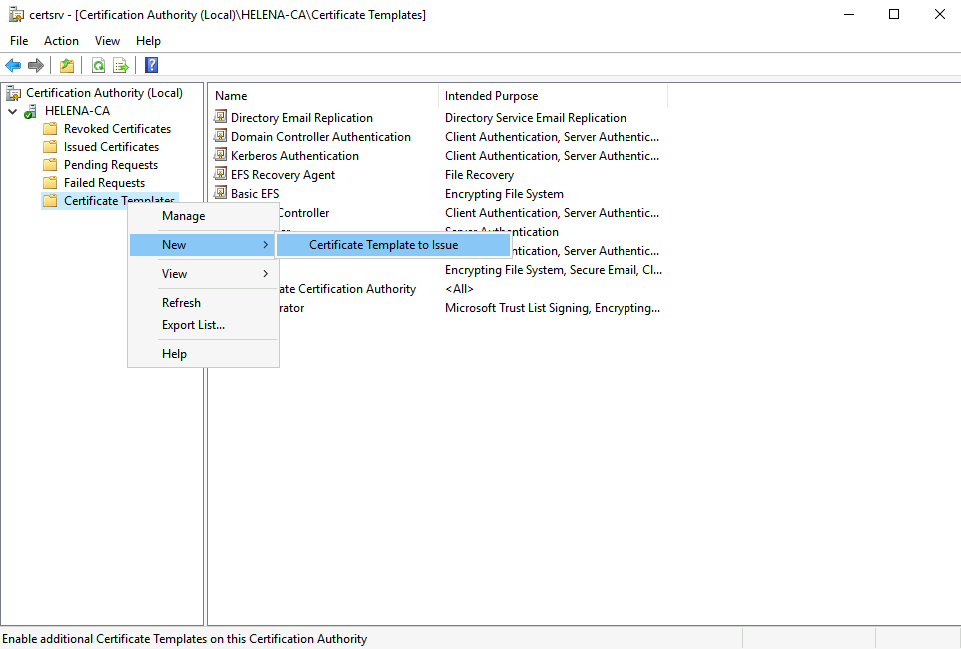
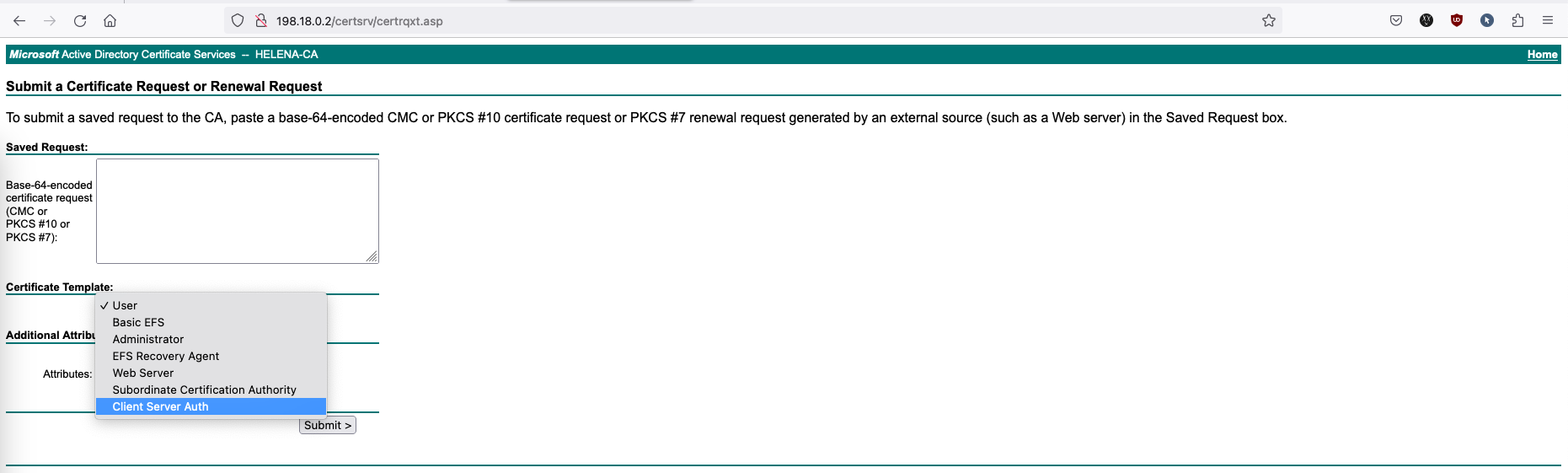
On the main CA page, select New » Certificate Template to issue
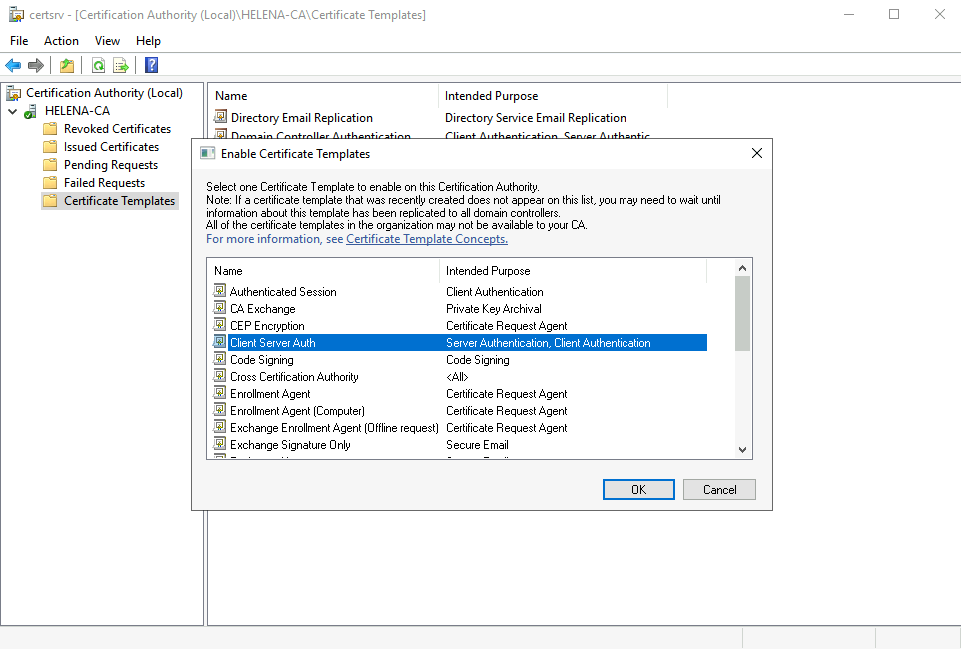
Select the new template
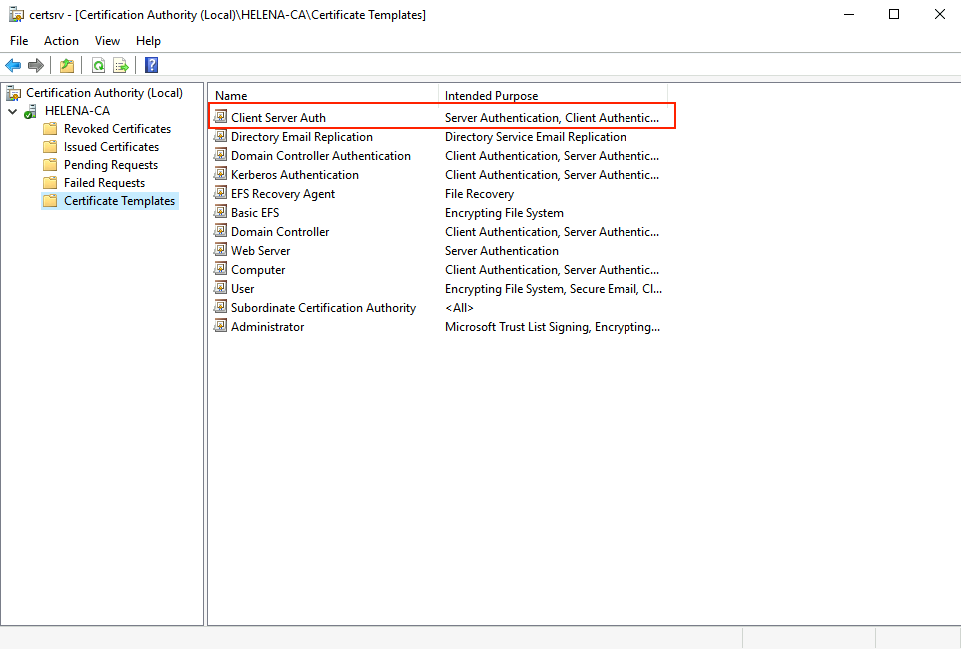
Now we can see the new template listed here as well
And now it is also available to be used to sign CSRs on Web Enrollment page