Palo Alto Captive Portal
Palo Alto Captive Portal is a web-based authentication method that forces unauthenticated users to log in before gaining network access. When a user initiates traffic, the firewall intercepts it and redirects the user to a login page, where credentials are validated against an authentication source (like LDAP or local DB).
Configuring Captive Portal
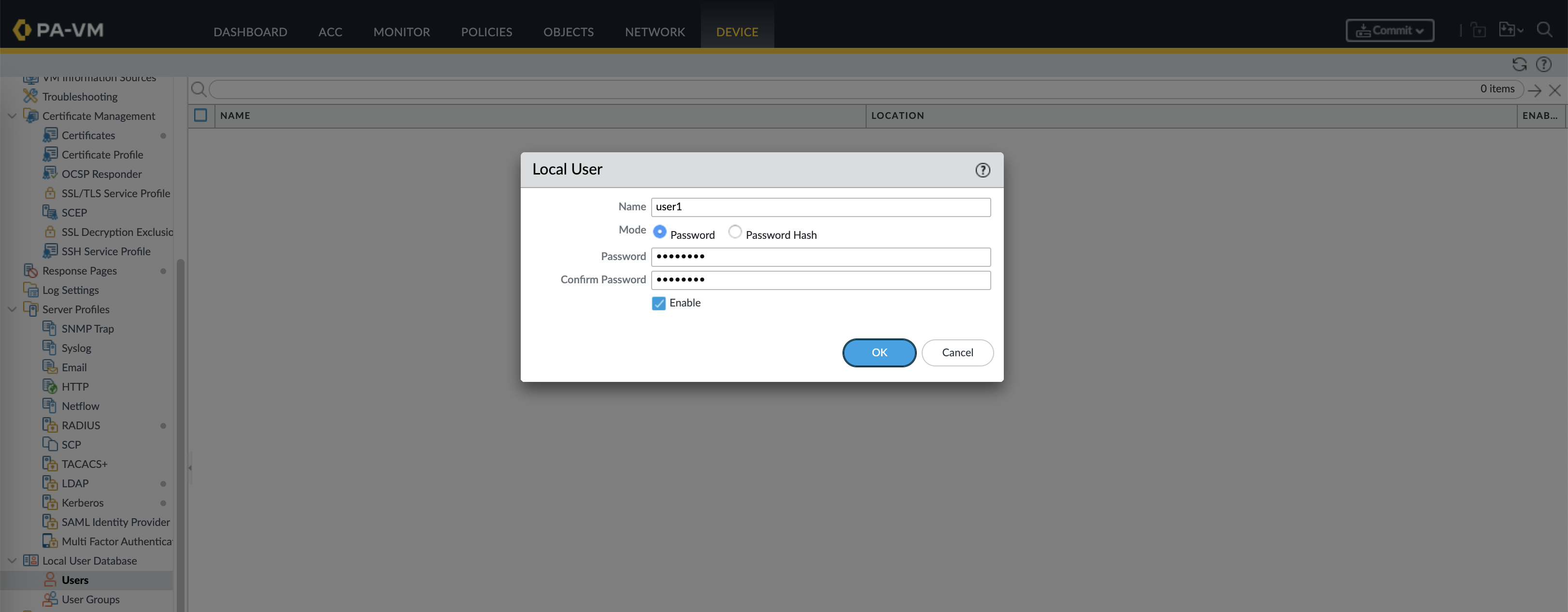
First we’ll setup a portal that authenticate using local users, here we create a new user for that
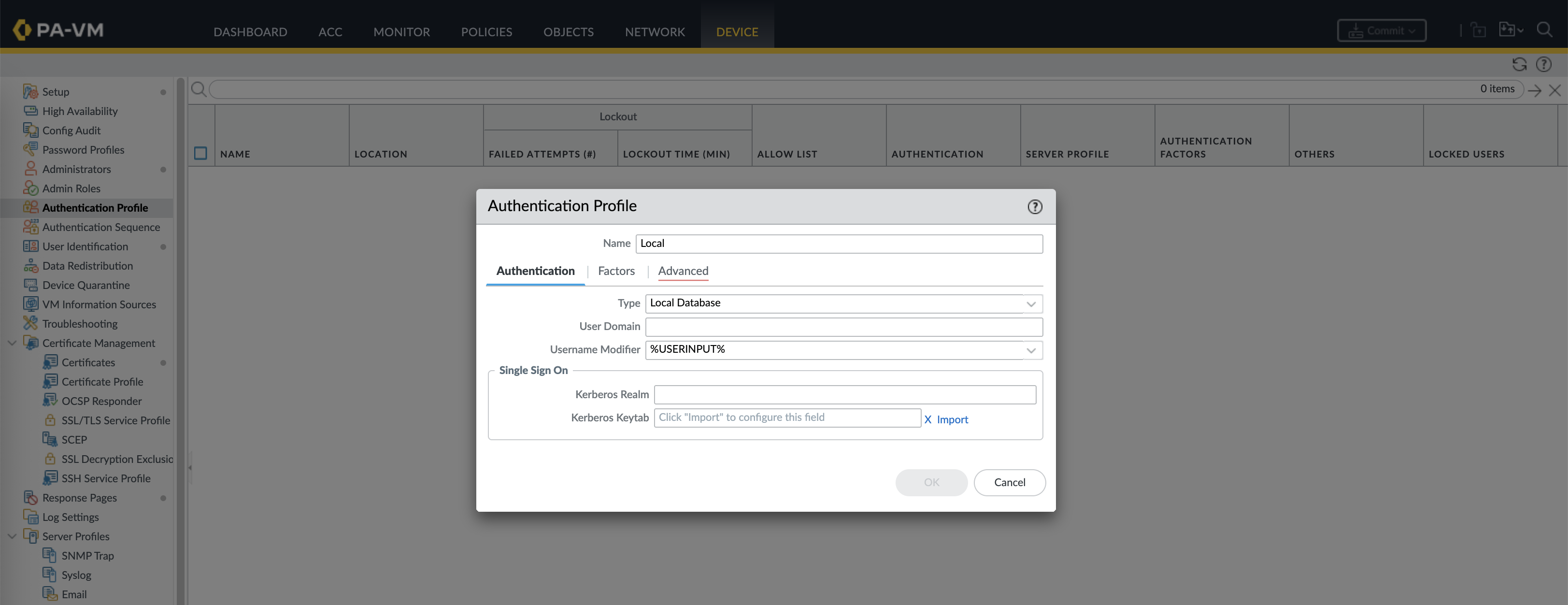
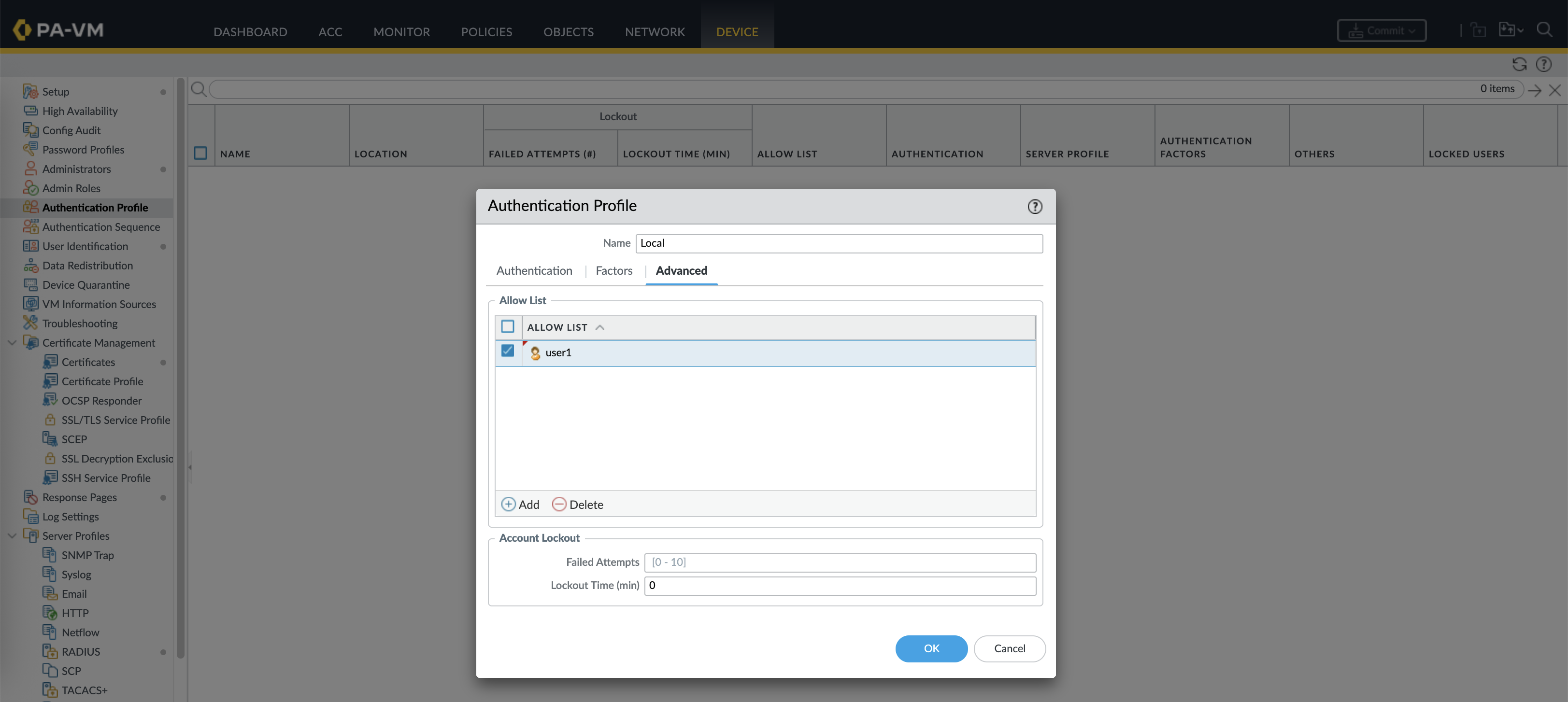
Next create a new Authentication Profile for Local Database that allows User1 to authenticate
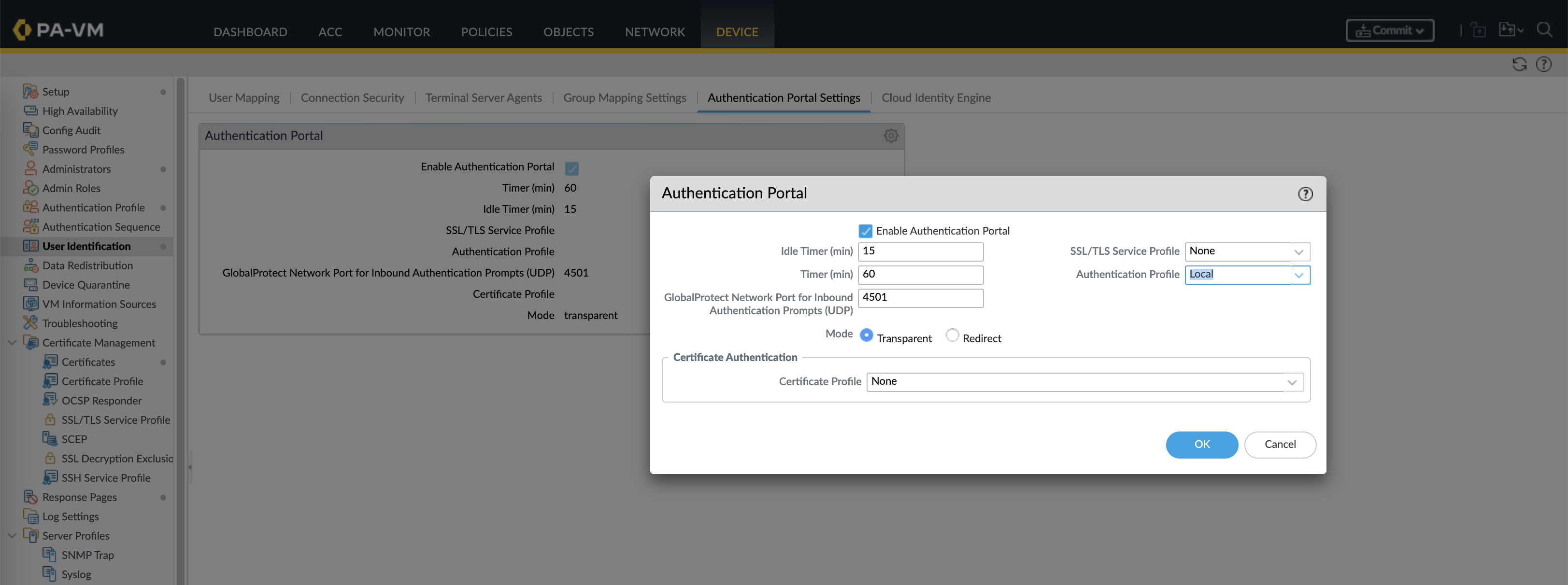
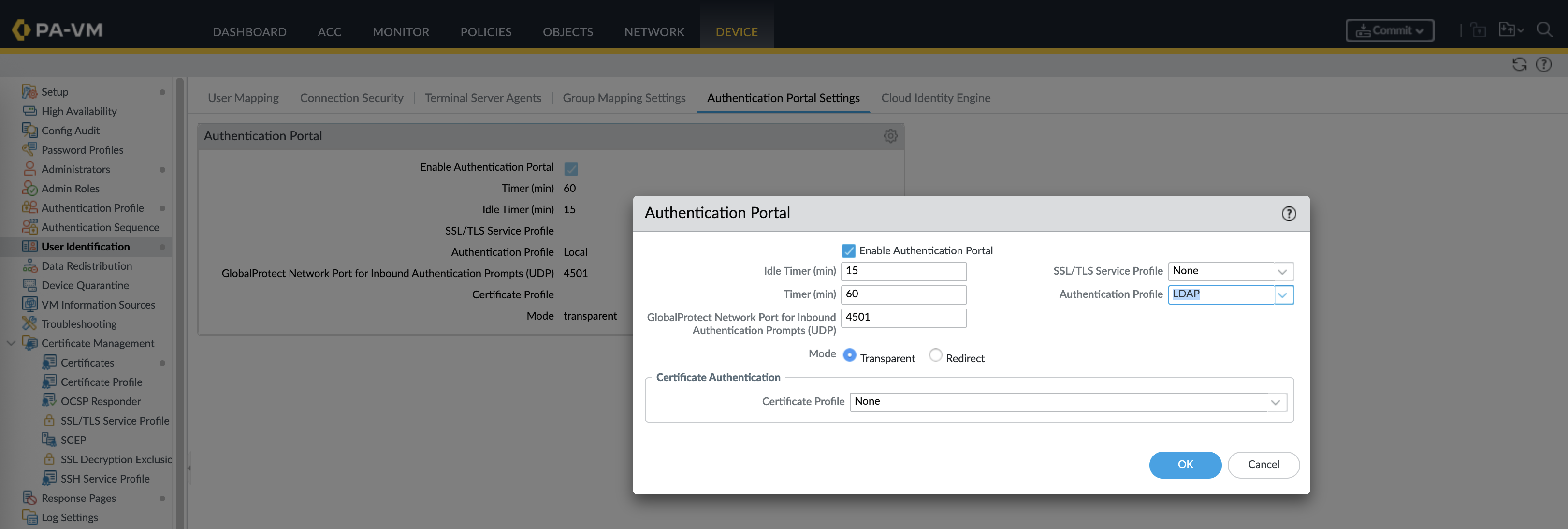
Then configure the Authentication Portal to use the Local Auth Profile
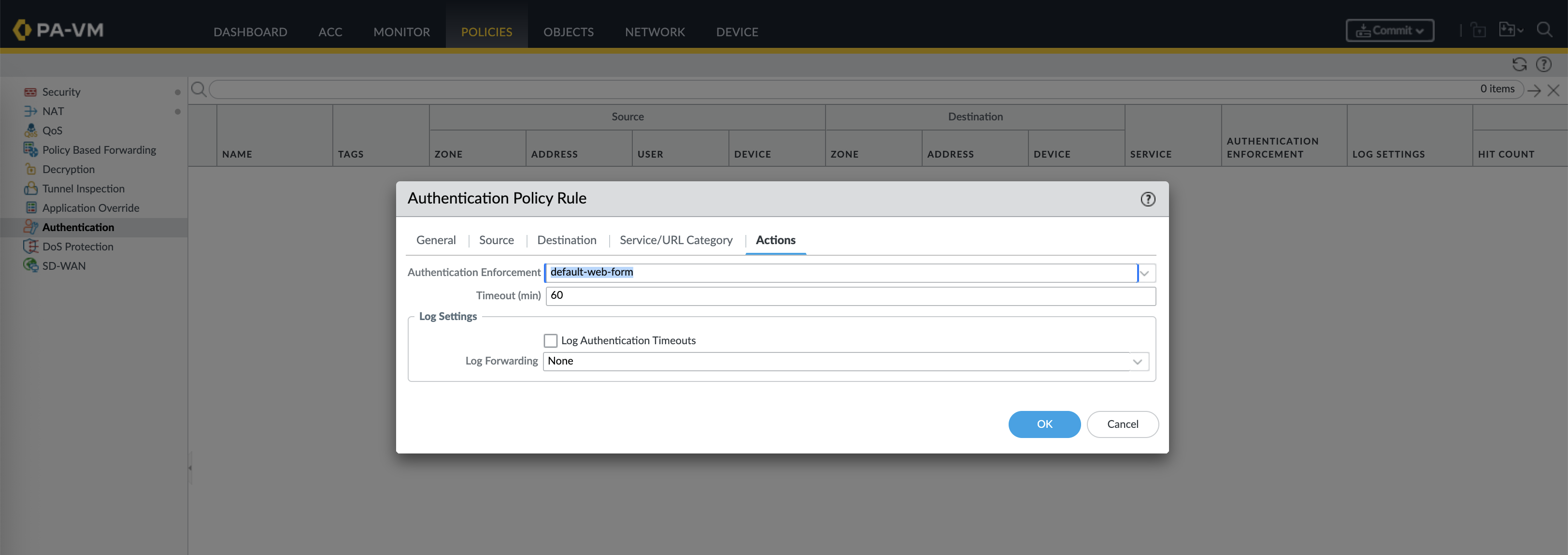
After that, create a new Authentication Policy Rule to enforce authentication though default web form
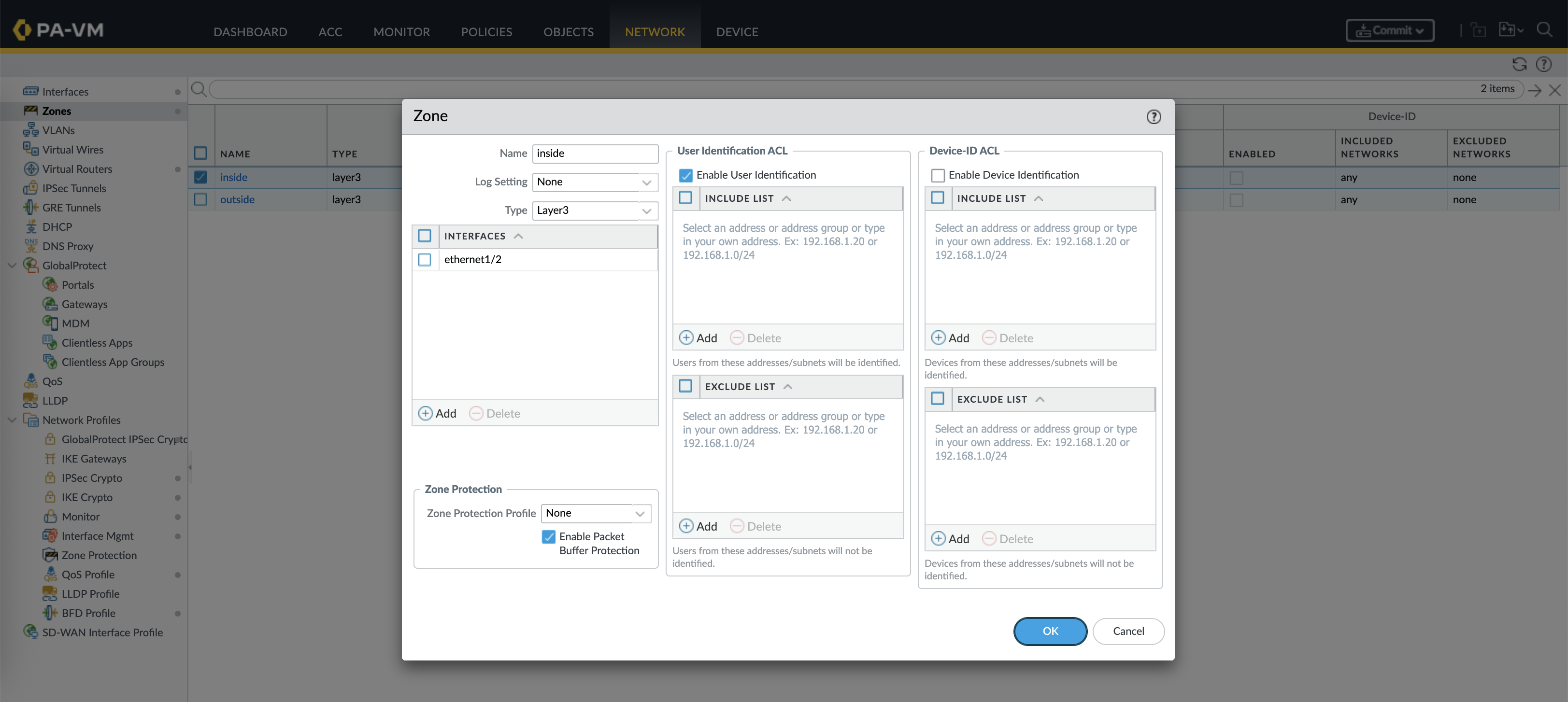
And lastly, on the Inside Zone enable User Identification
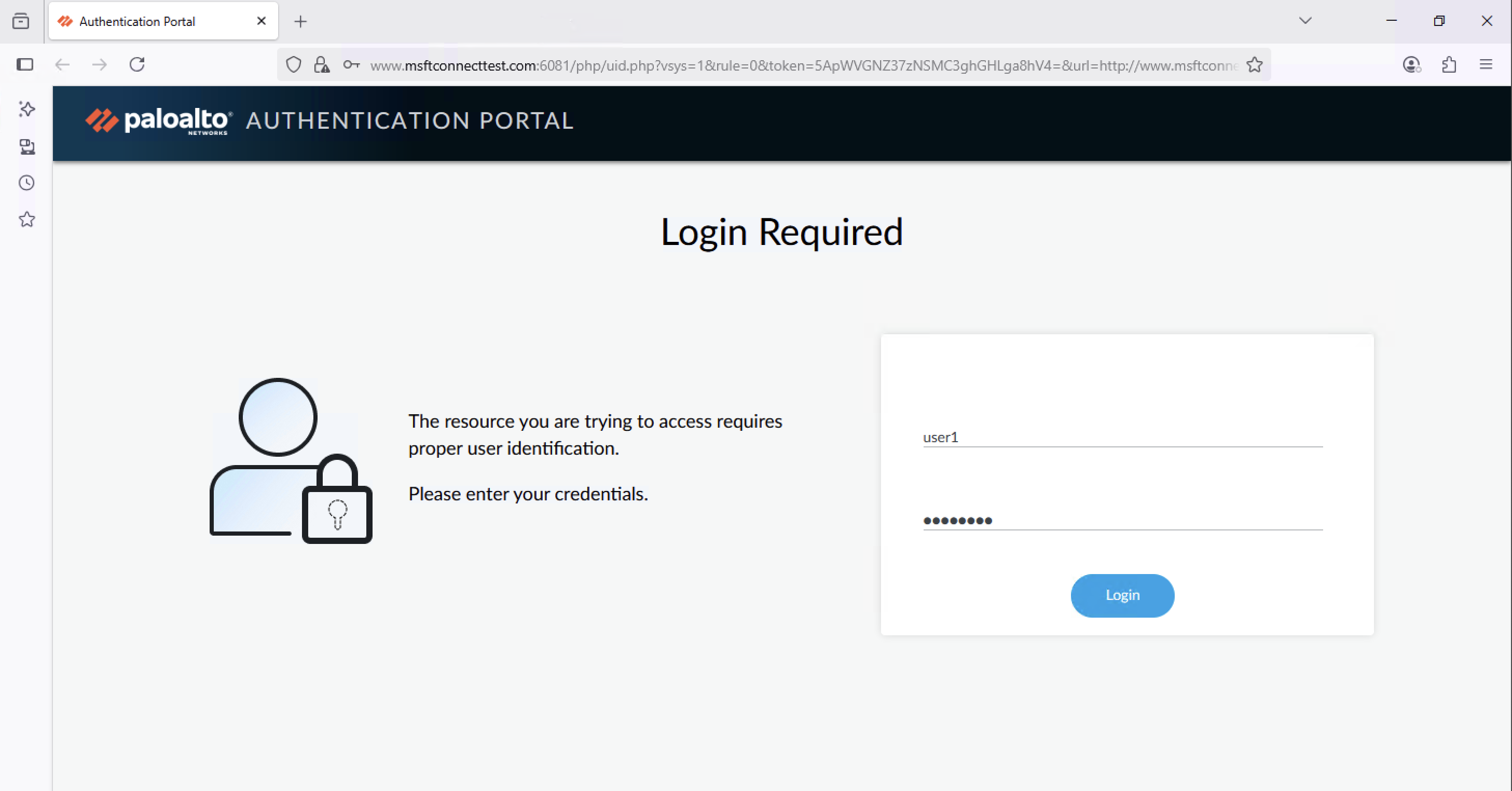
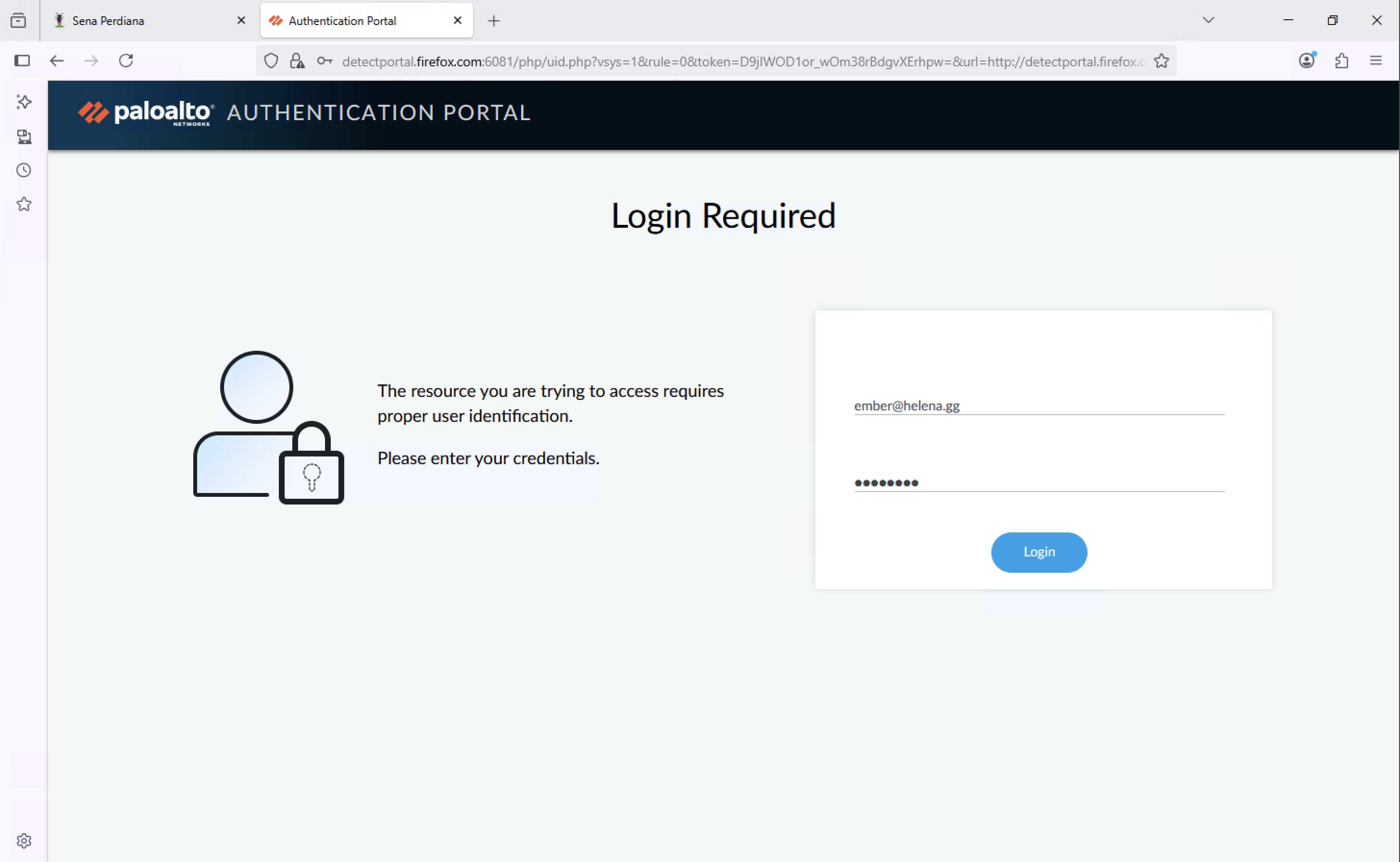
Now on the client side, on the first time connecting to the internet they’ll be redirected to login on the portal using local users
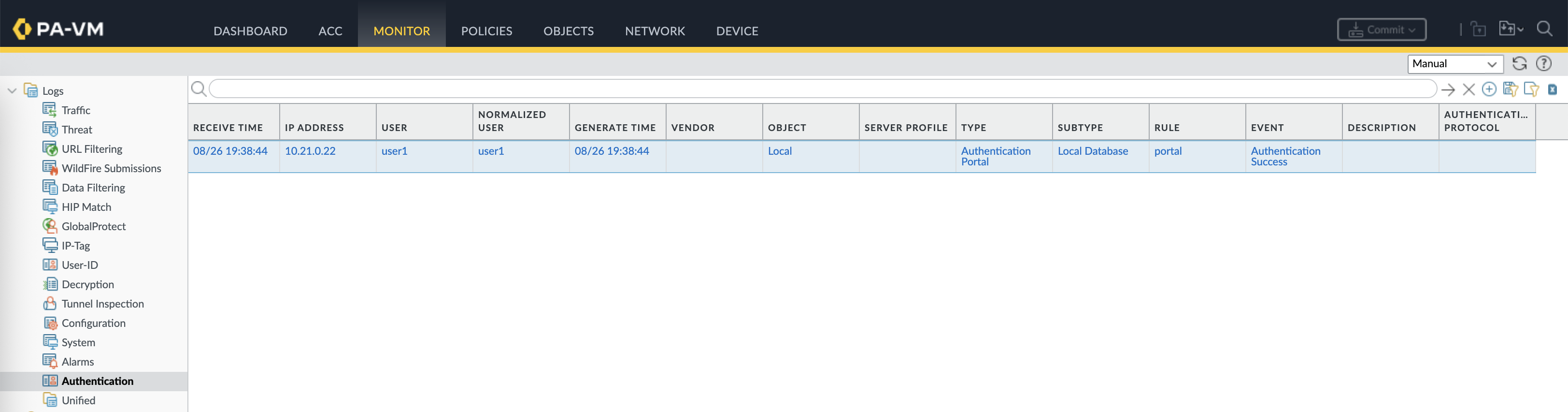
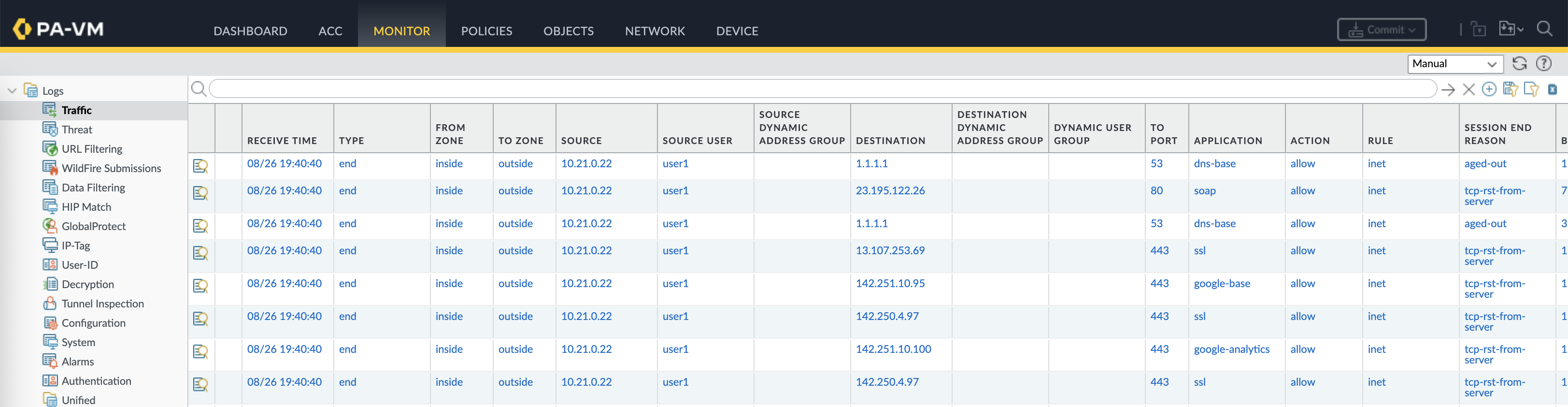
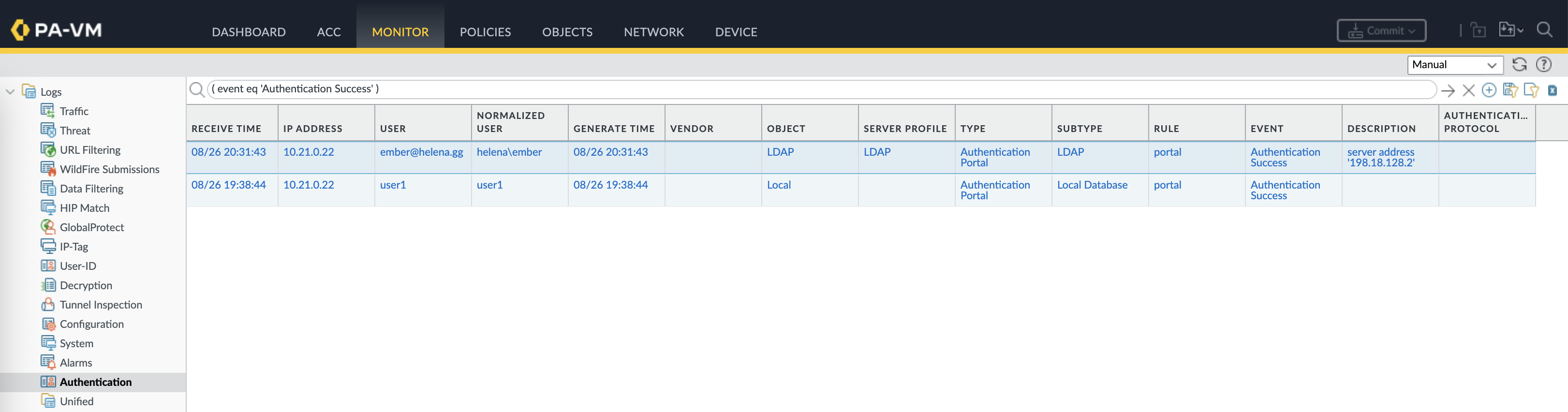
Logs on the firewall side verify that the authentication is working
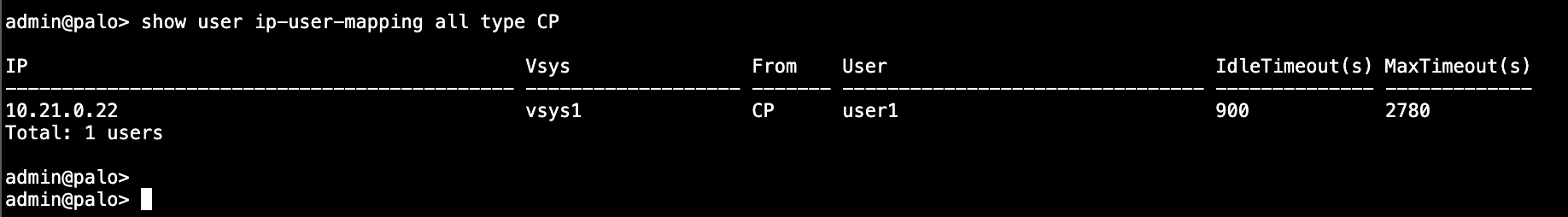
We can run ‘show user ip-user-mapping all’ to see the mapped users
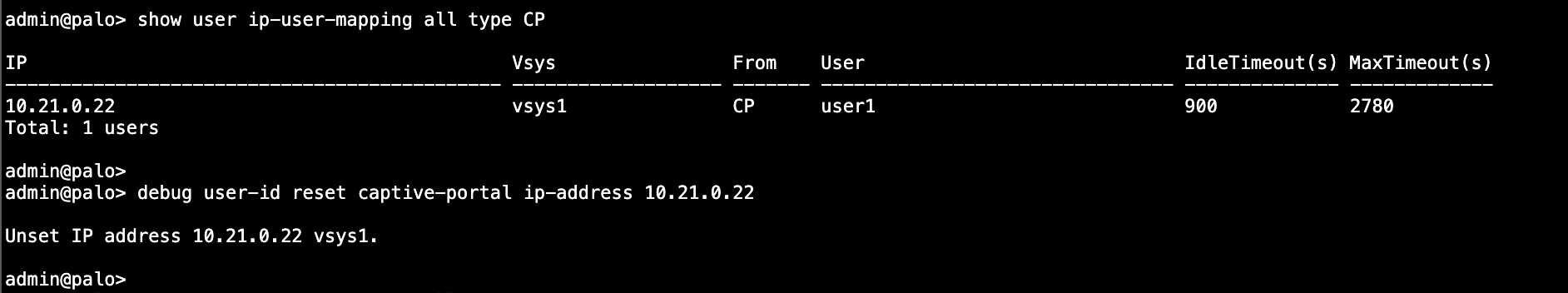
And running ‘debug user-id reset captive-portal ip-address’ allows us to deautheticate specific user
Configuring LDAP
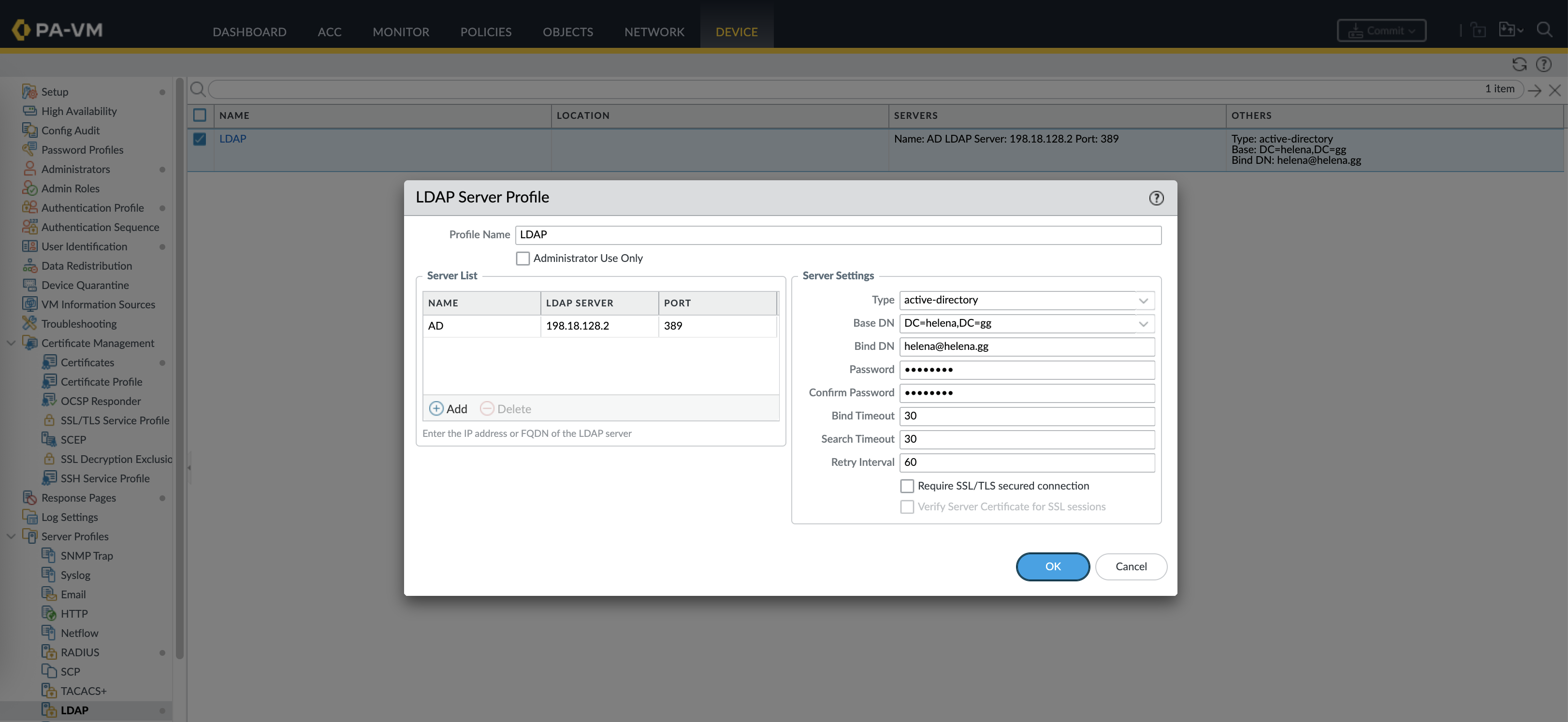
To allow clients to use LDAP Users on the portal, first we create or use existing LDAP Server Profile
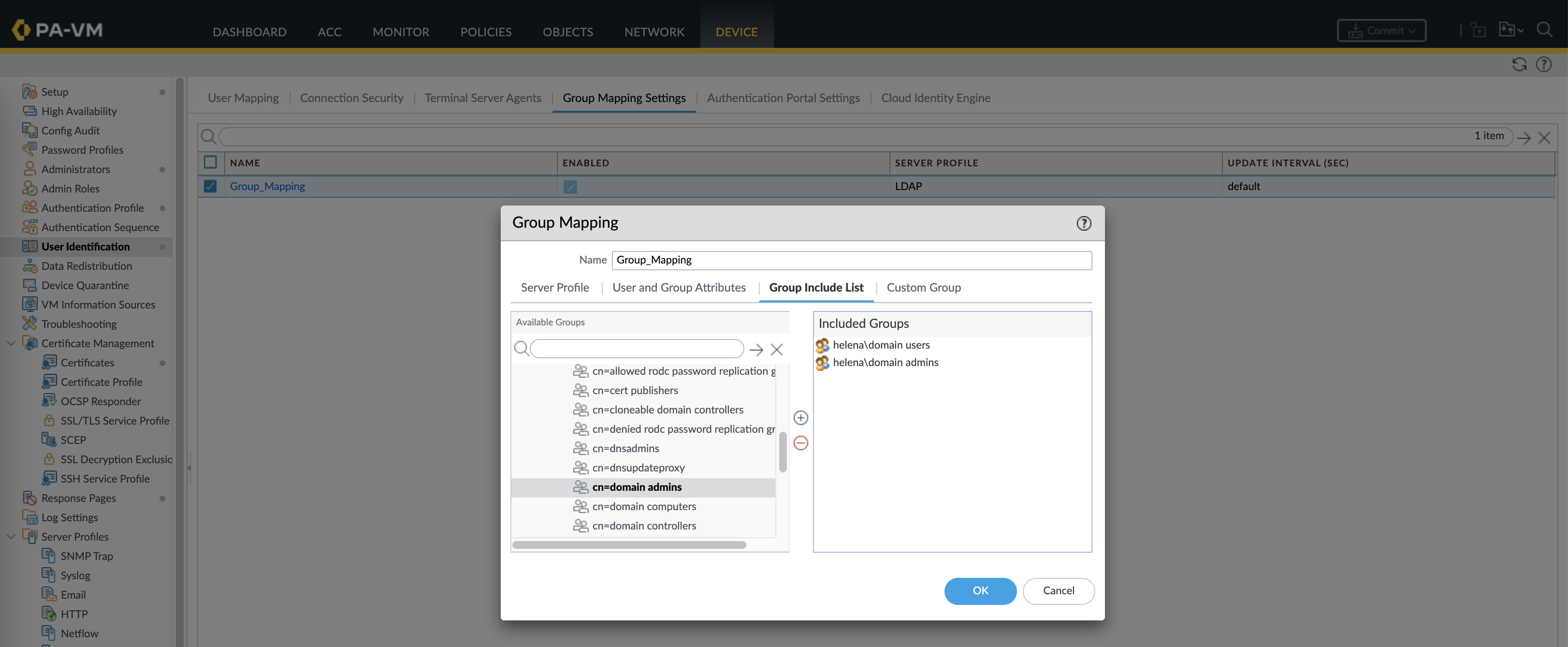
And then use the Group Mapping to import groups that we’d like to allow to authenticate on the portal
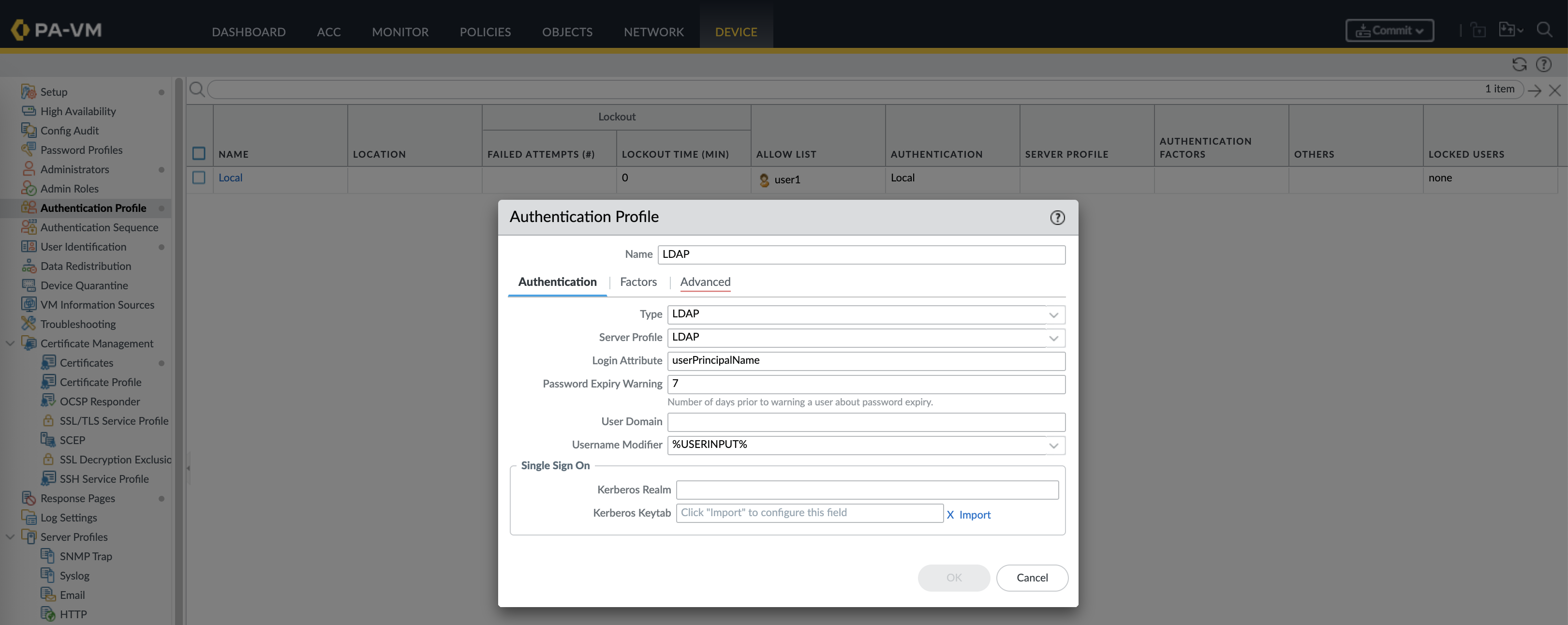
Then create a new Authentication Profile for LDAP Users
Login Attribute field defines which LDAP attribute the firewall will use to match a username entered during login, userPrincipalName (UPN) is the Active Directory logon name in the format user@domain.com
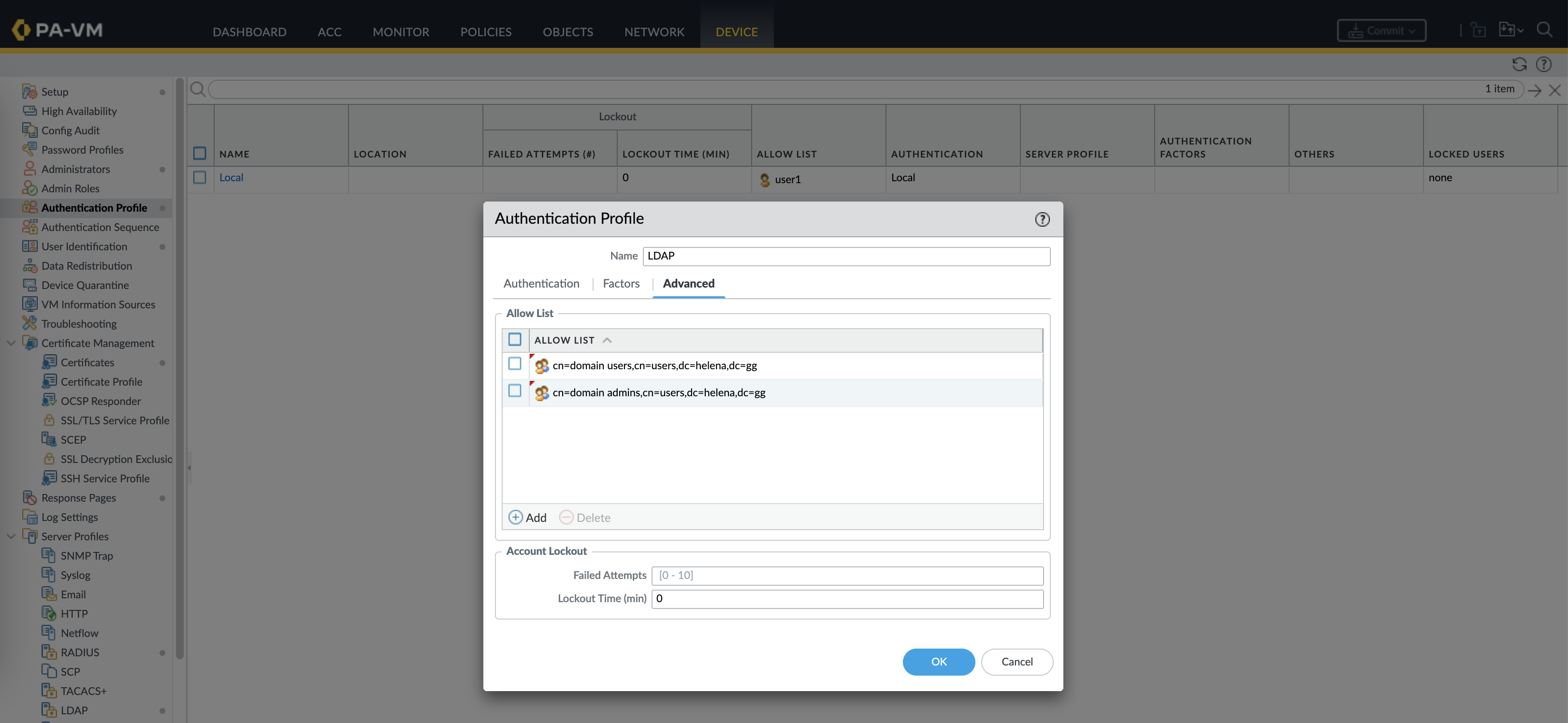
Then we define which AD Groups are allowed to login based on the ones we imported earlier
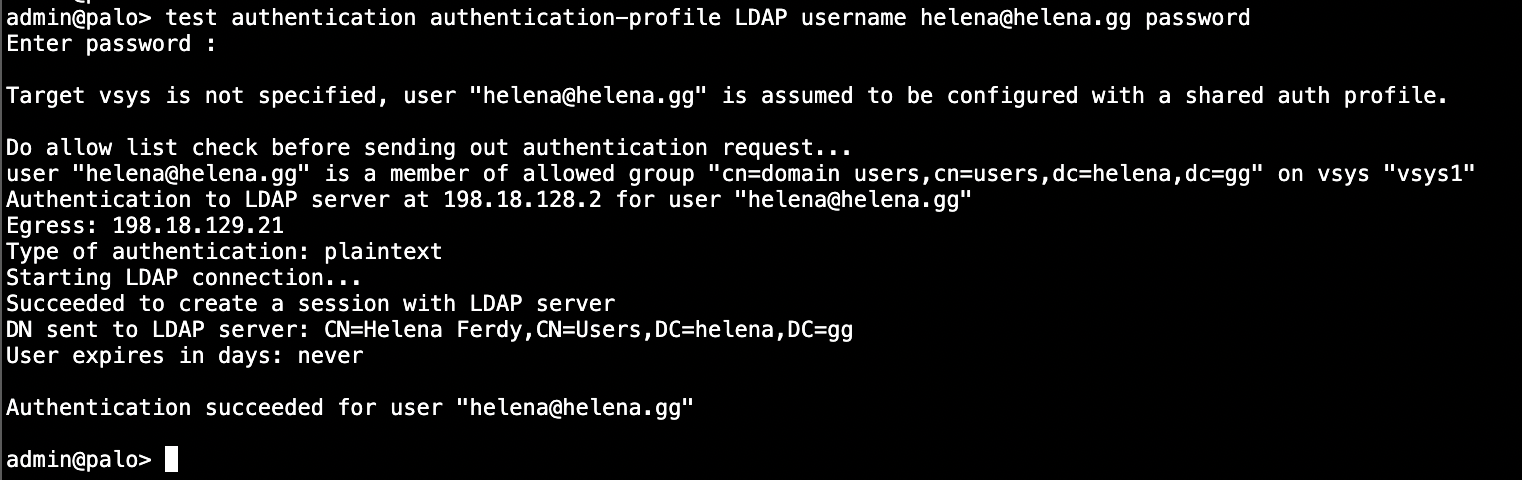
At this point we can run a CLI test to make sure the LDAP Authentication Configuration is working
1
test authentication authentication-profile LDAP username helena password
Lastly we need to change the Authentication Profile on the Authentication Portal configuration
And now the portal will accept LDAP Users