Check Point IPSec Remote Access VPN
Check Point IPsec Remote Access VPN allows users to securely connect to their organization’s internal network over the internet using an encrypted IPsec tunnel. It provides authenticated access to resources as if the user were on-site, ensuring data confidentiality and integrity.
IPSec VPN
On Check Point SmartConsole, here we enable the IPSec VPN blade
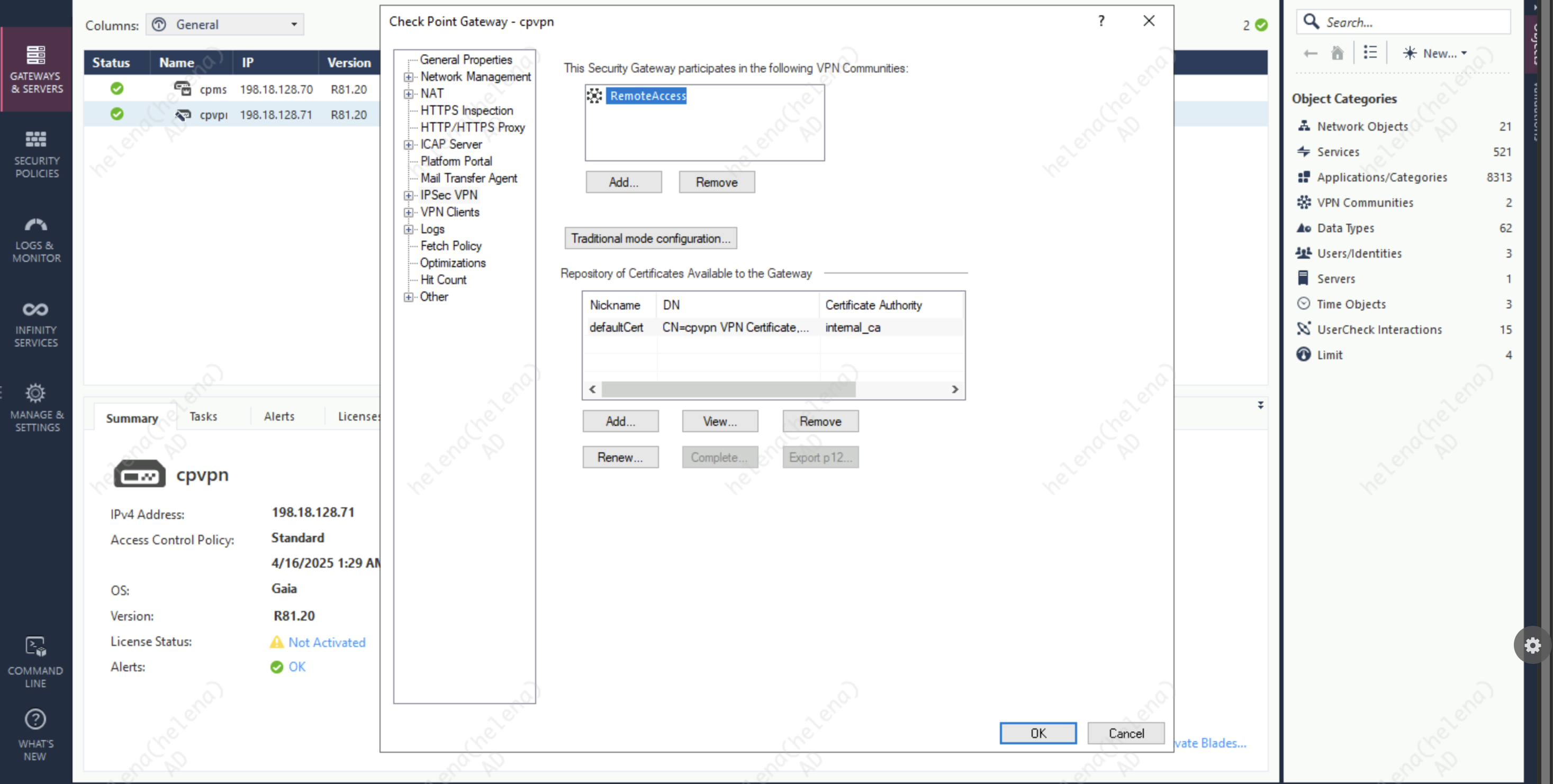
On IPSec VPN, include this gateway into the RemoteAccess VPN Community
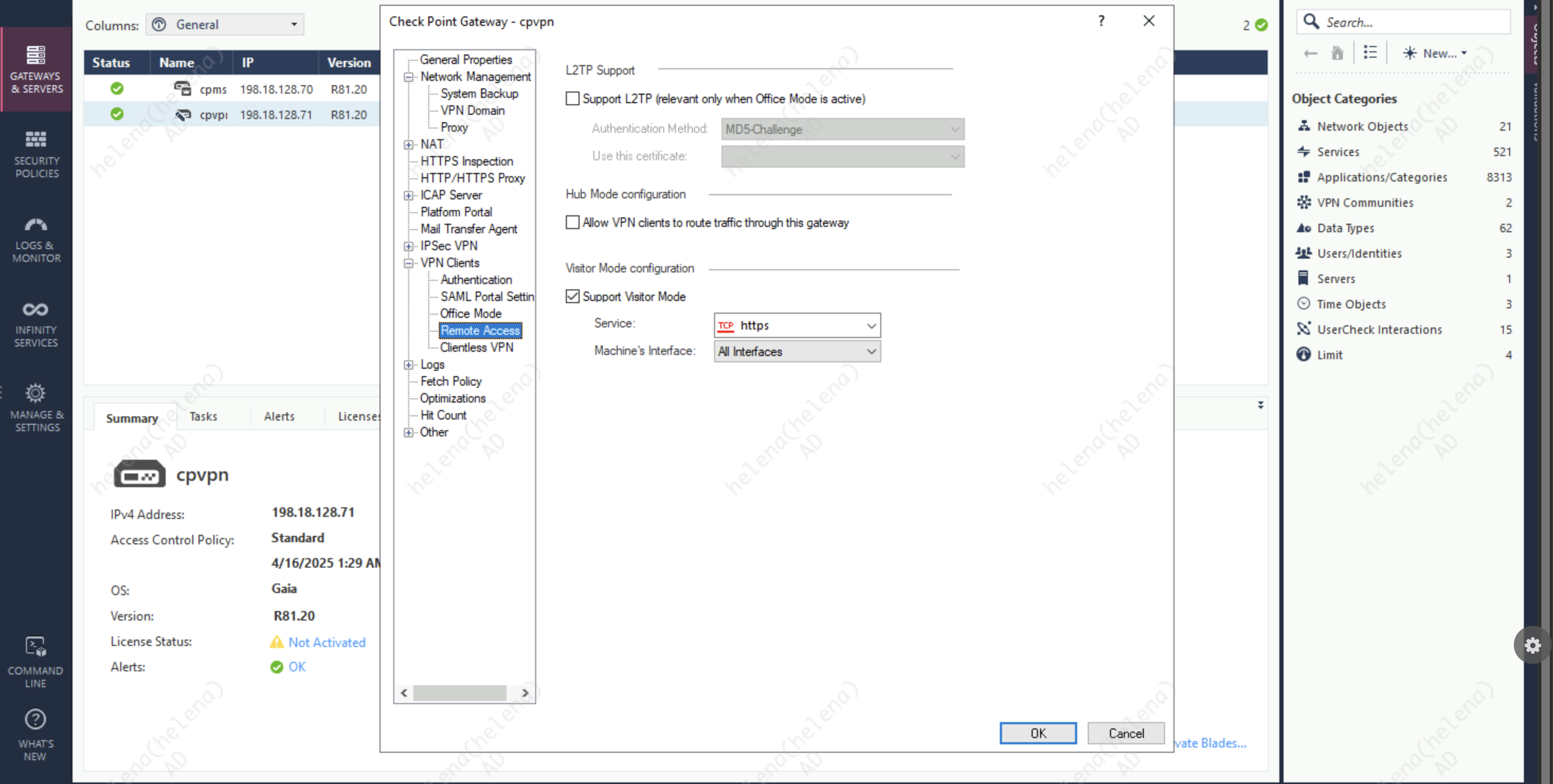
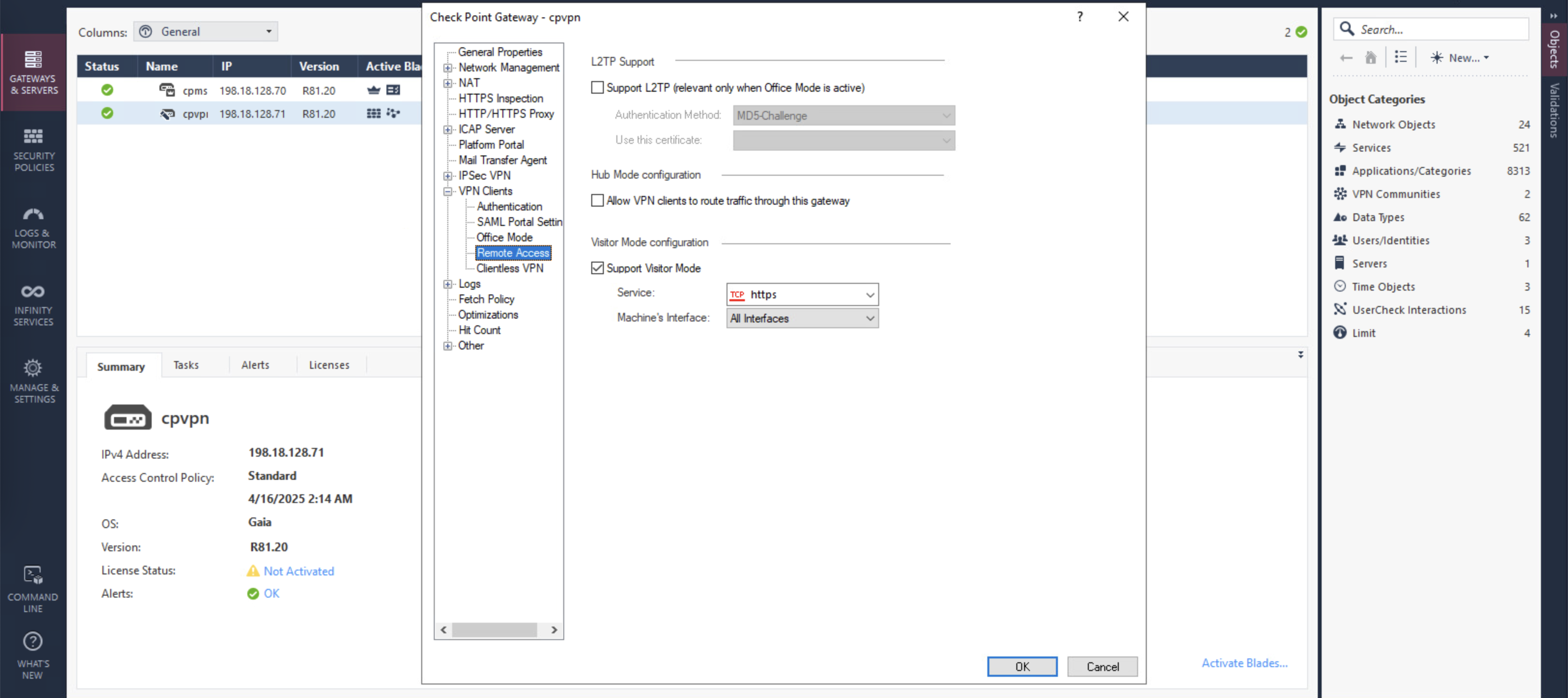
Then on VPN Clients » Remote Access, enable Visitor Mode
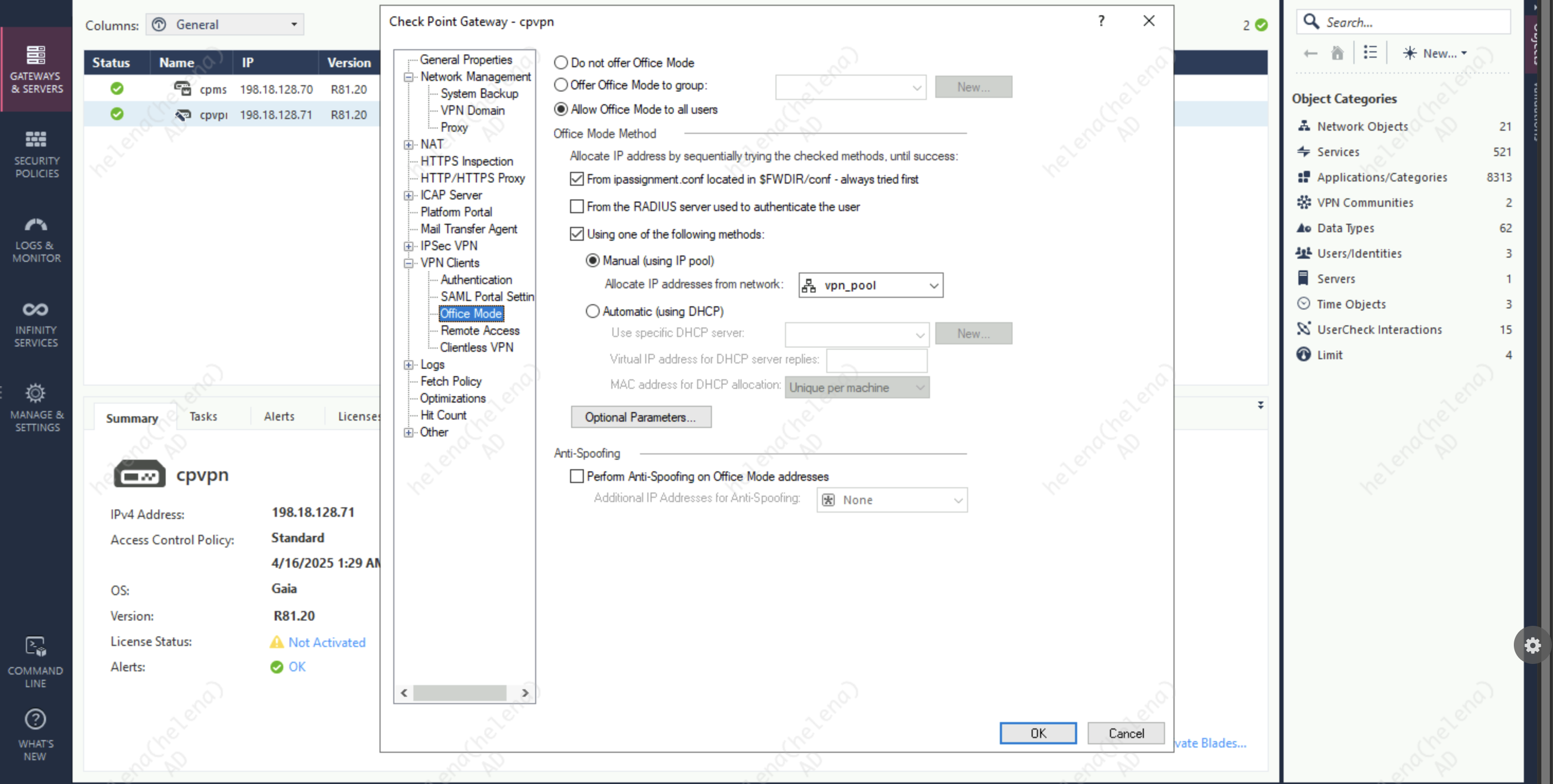
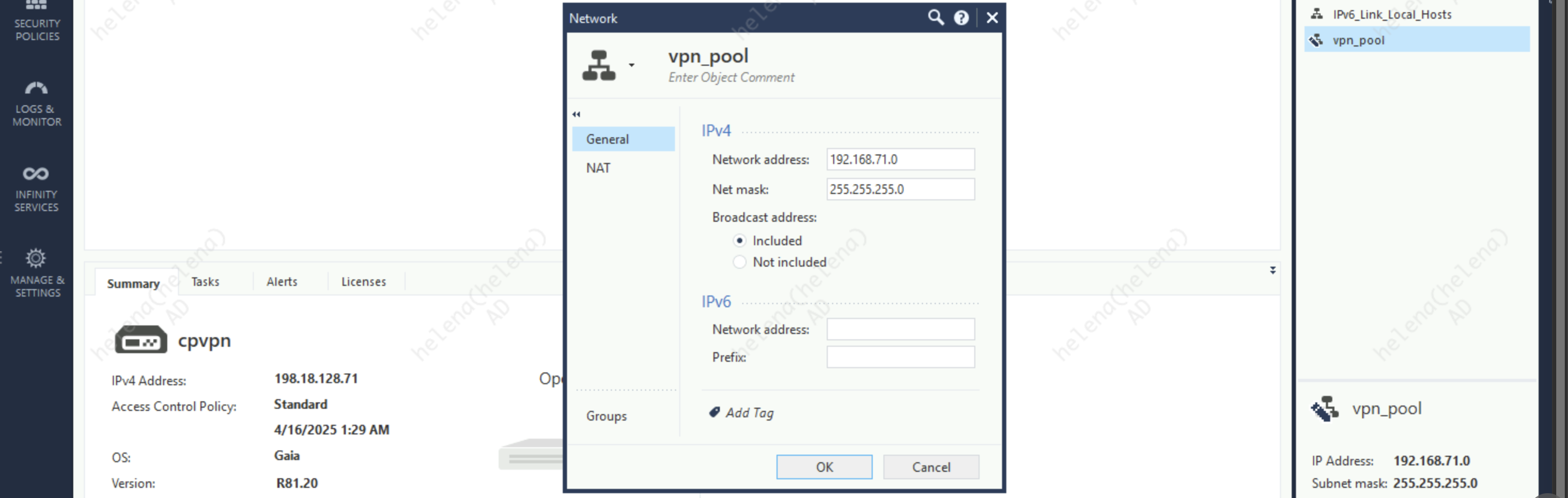
Next on Office Mode, select Allow Office Mode and assign the VPN IP Pool
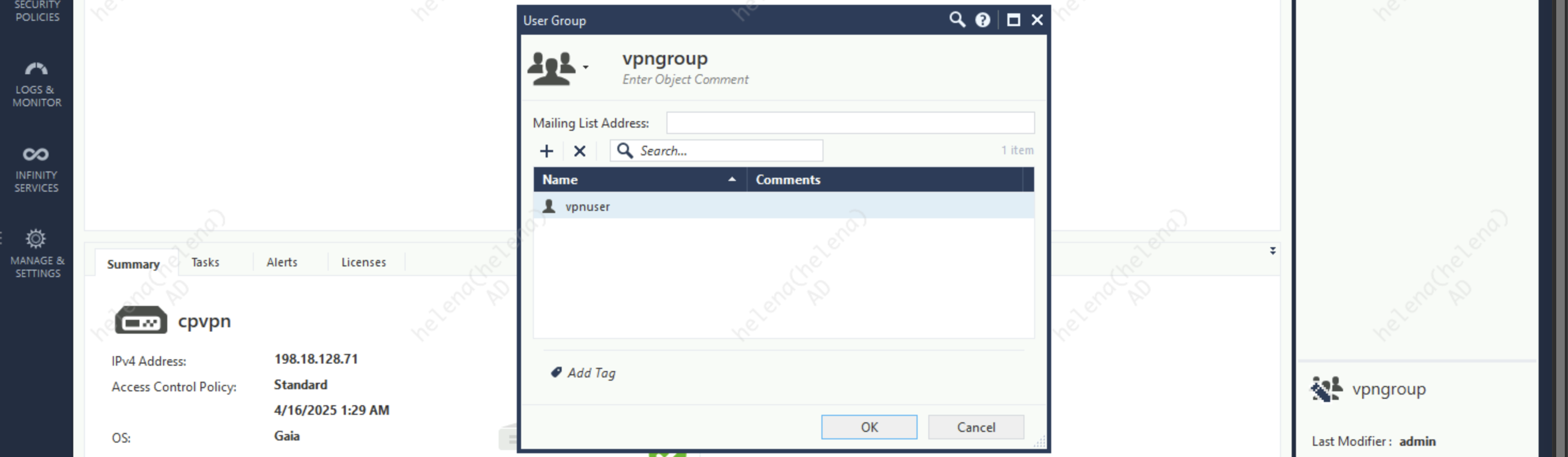
VPN User Group
Next configure the VPN User Group, which in this case includes one user named “vpnuser”
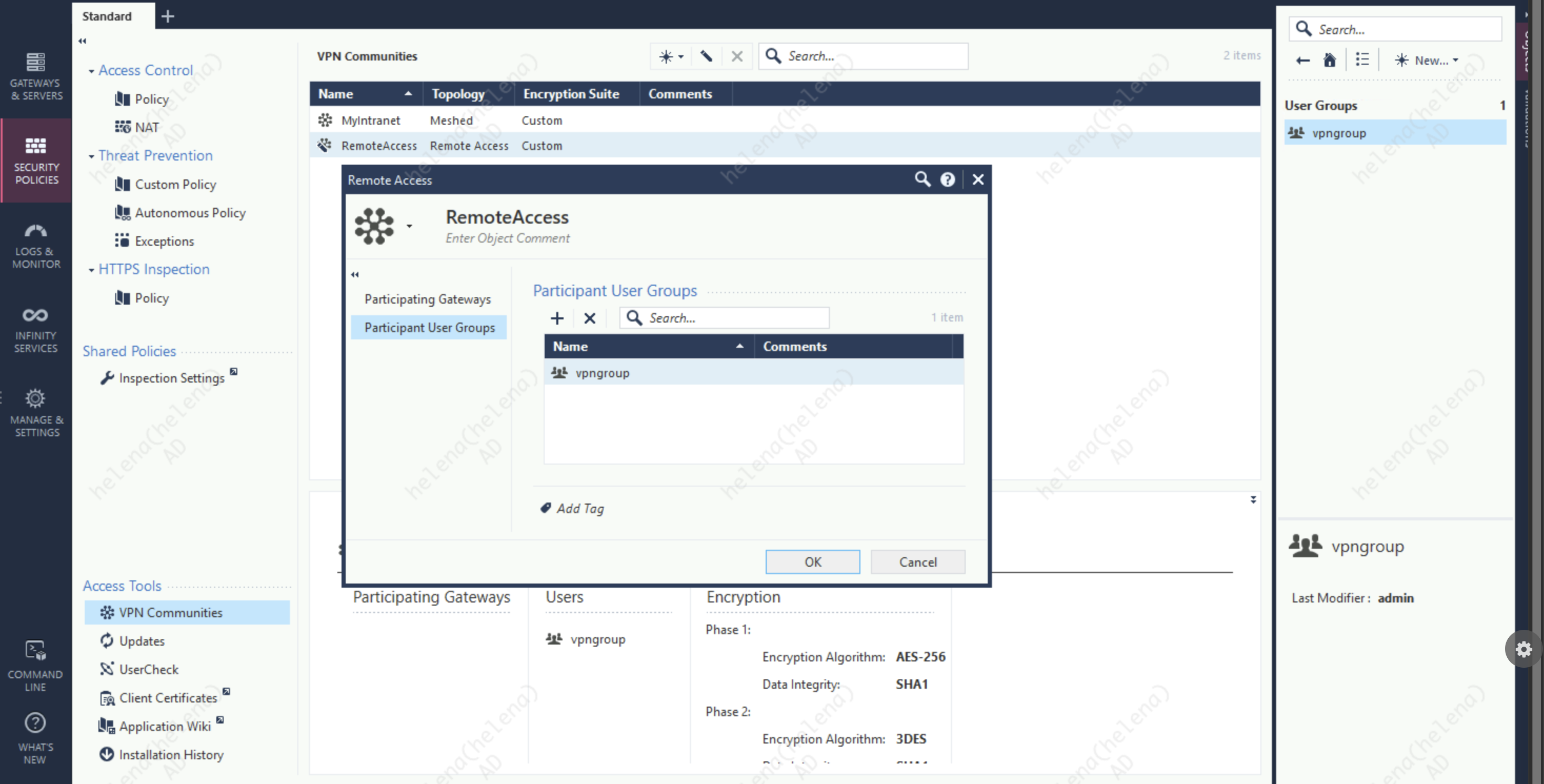
Set that User Group as the VPN Community’s Participant so we can use it to login to VPN
Finally, we just need to make a policy to allow VPN users to access internal networks
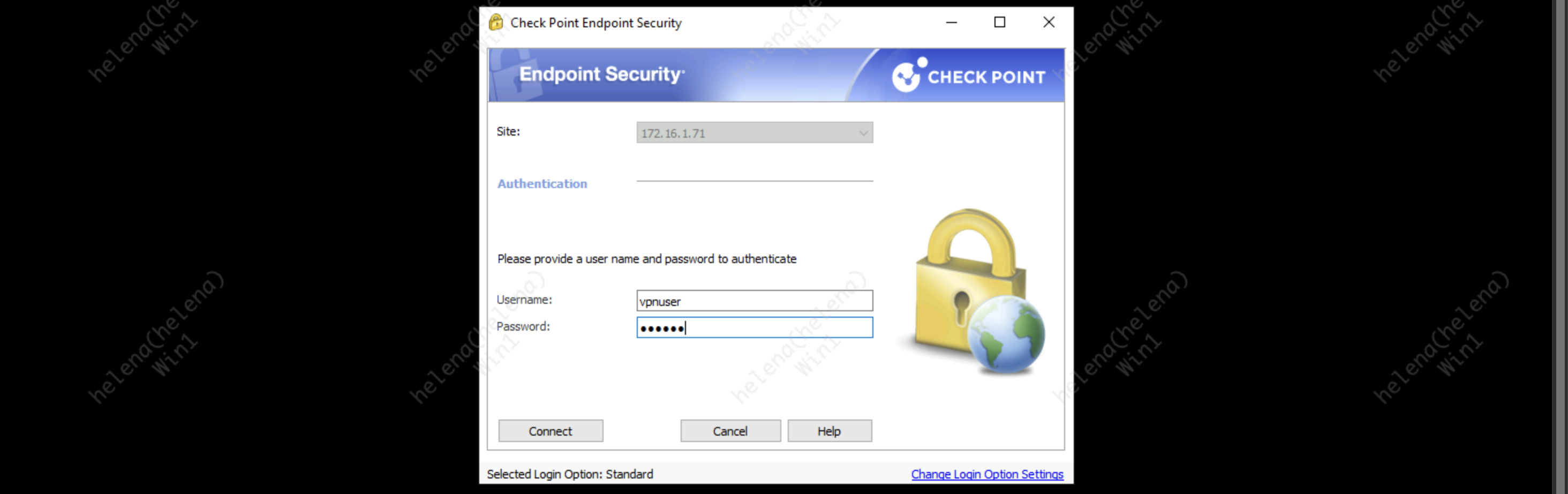
Connecting to VPN
Now we can try connecting to the VPN gateway
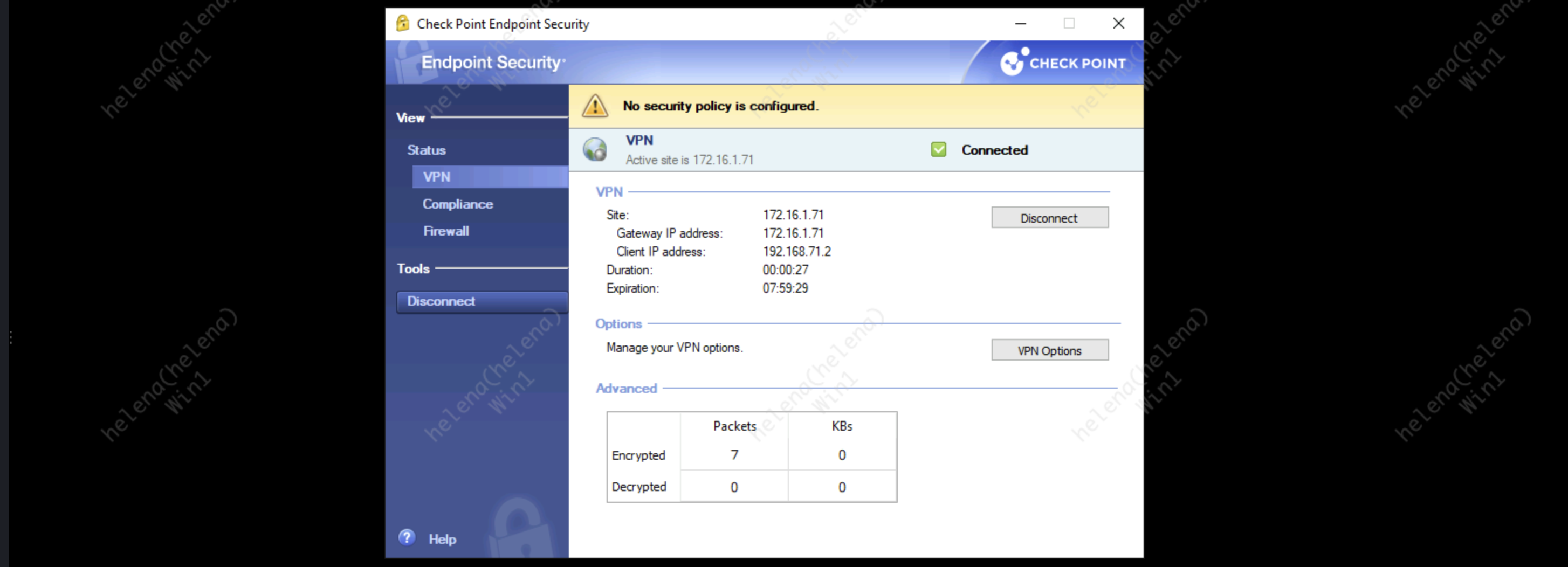
Here we are getting the correct assigned IP Address from VPN IP Pool, we also get the routes to internal network
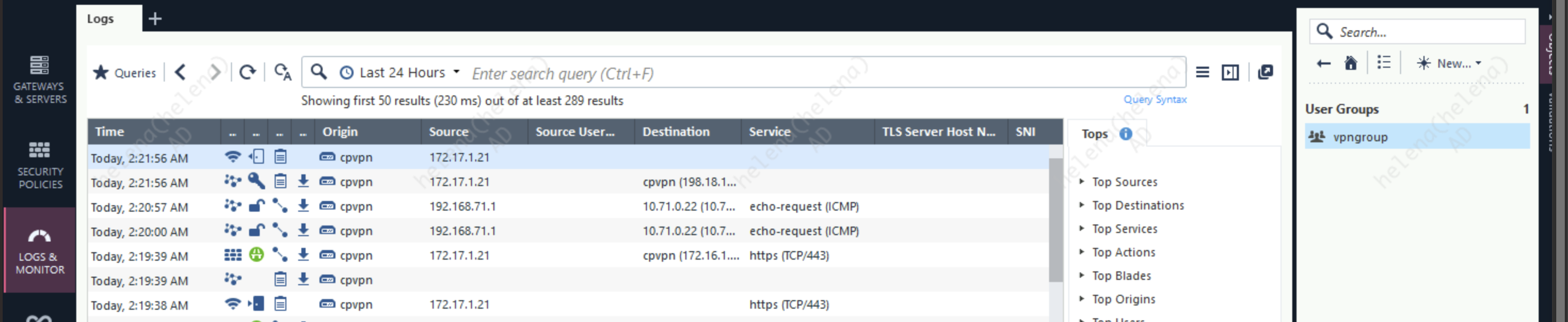
The logs show the successfull vpn connections
Split Tunnel
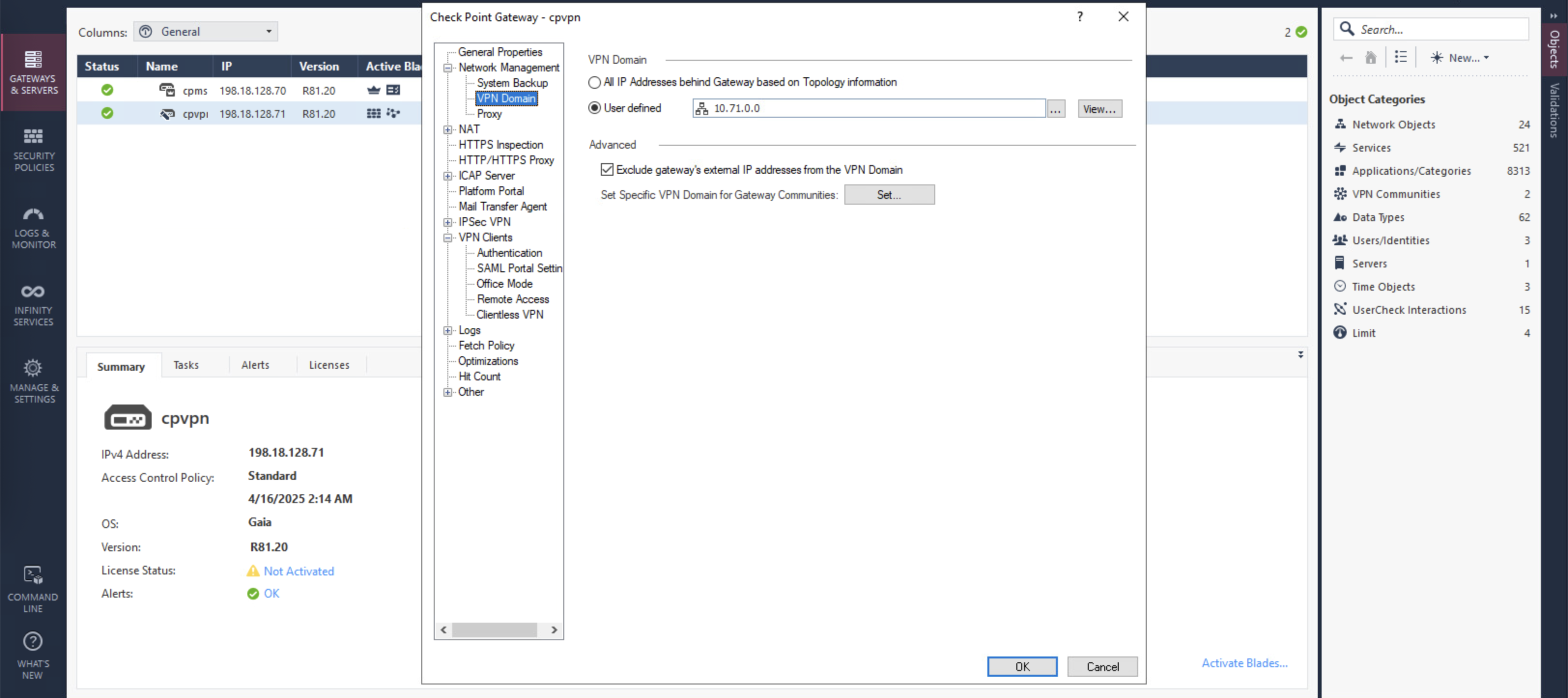
By default Split Tunneling is on, but we can modify what segments to advertise to VPN clients, first we disable the “Allow Clients to route traffic to this gateway”
Then on VPN Domain, we can specify the segments to advertise