Check Point Sandblast
Check Point Threat Emulation SandBlast is a security solution that proactively defends against advanced threats by simulating and analyzing potentially malicious files in a secure, isolated environment (sandbox). This technology detects and prevents zero-day attacks, ransomware, and other sophisticated malware by executing suspicious files in a virtual environment to observe their behavior before they can impact the network.
Enabling Threat Emulation
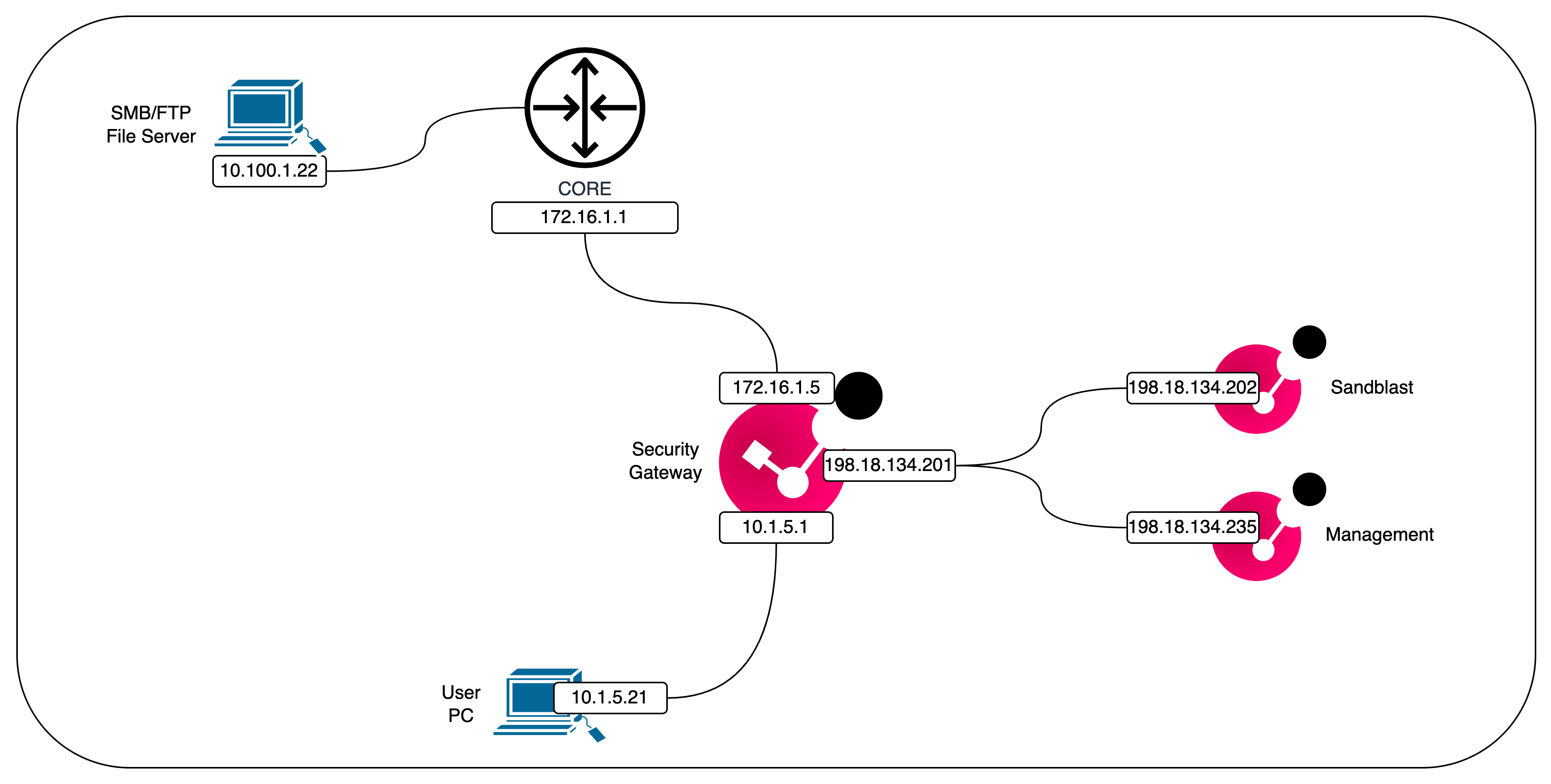
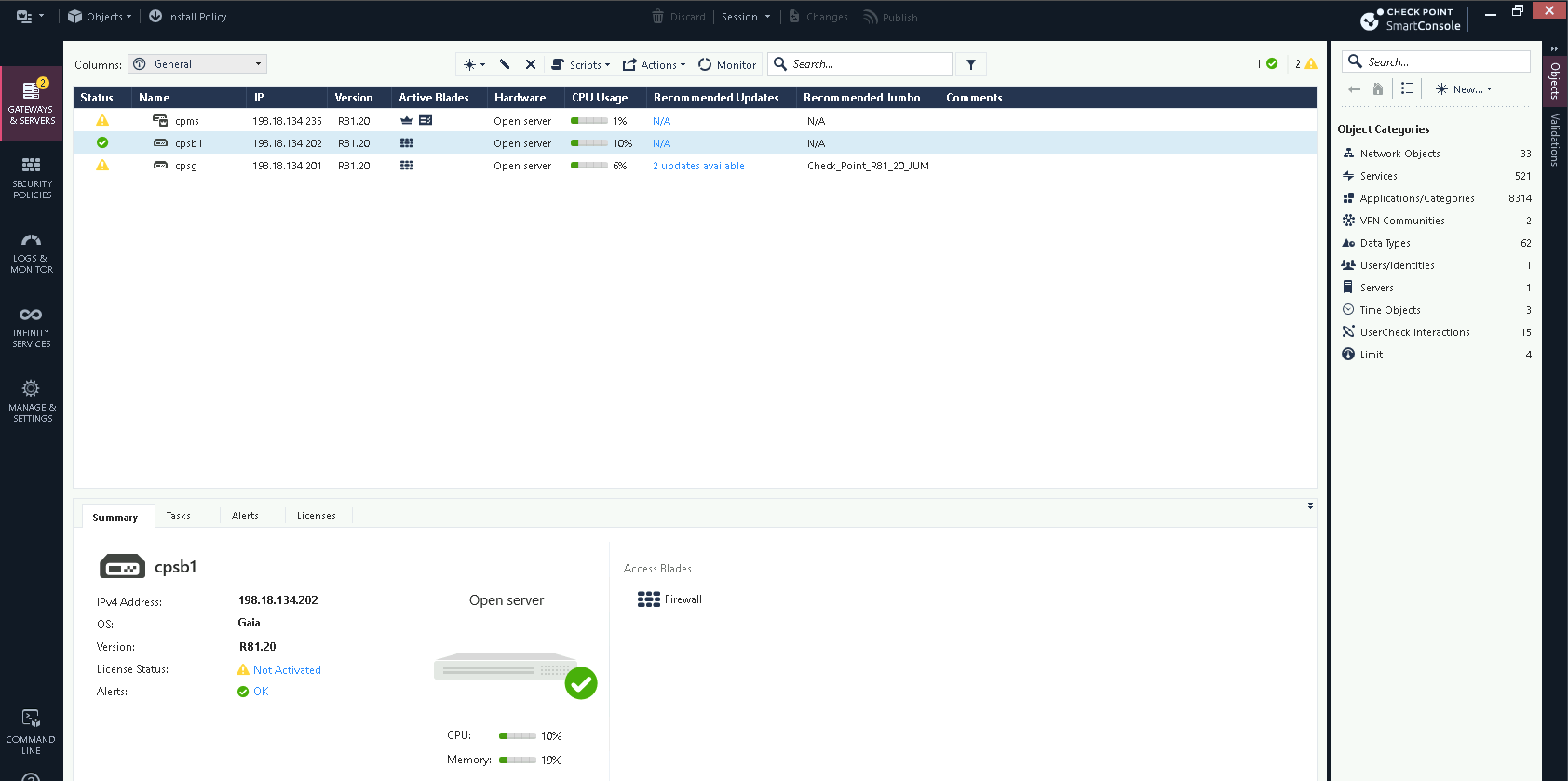
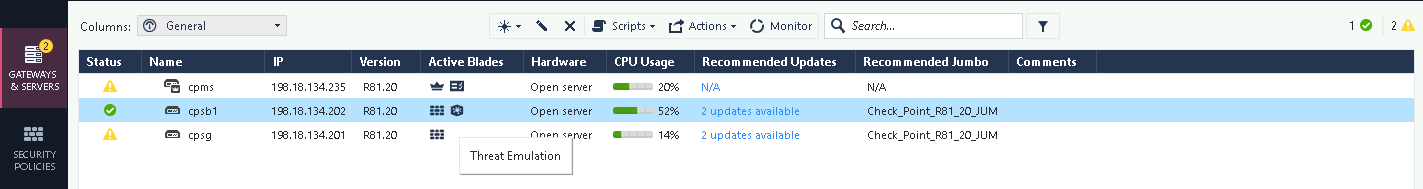
In this deployment, we added a freshly installed Security Gateway that we’ll use as the Sandblast Box (cpsb)
Before enabling Sandblast, make sure this box can access internet
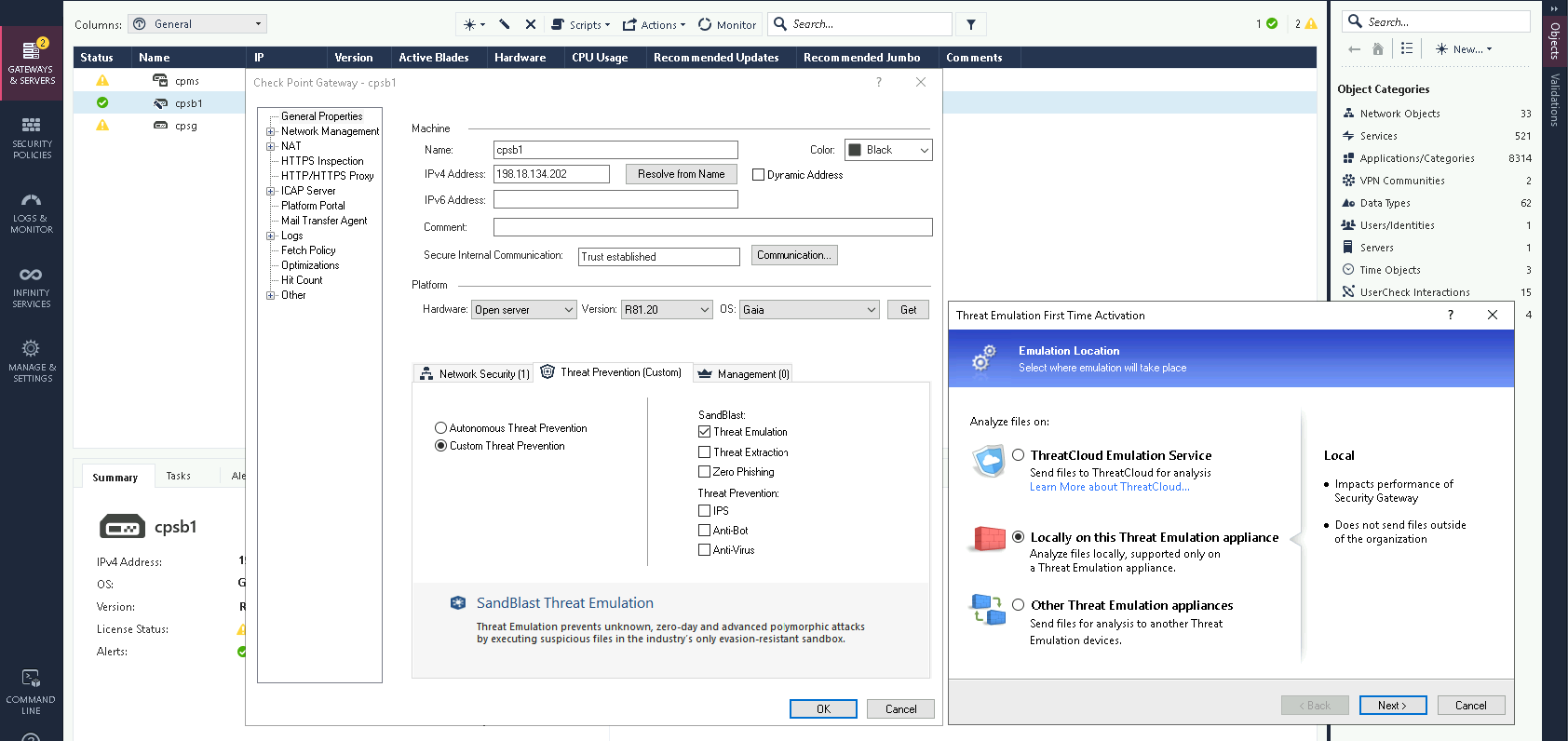
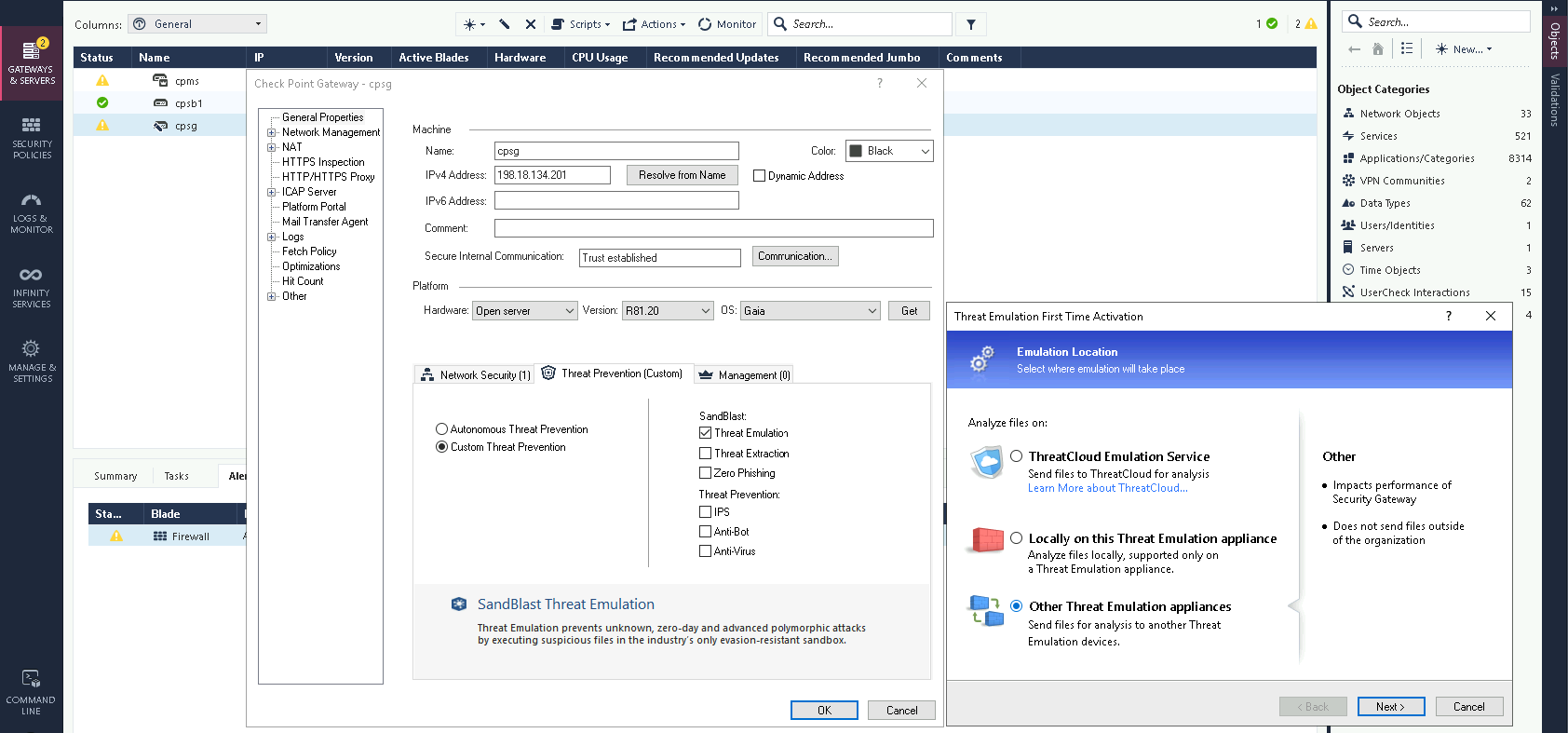
Now on cpsb, enable Threat Emulation and select the location to be local
Hit next until it finishes, after that we have Threat Emulation Blade enabled on this box
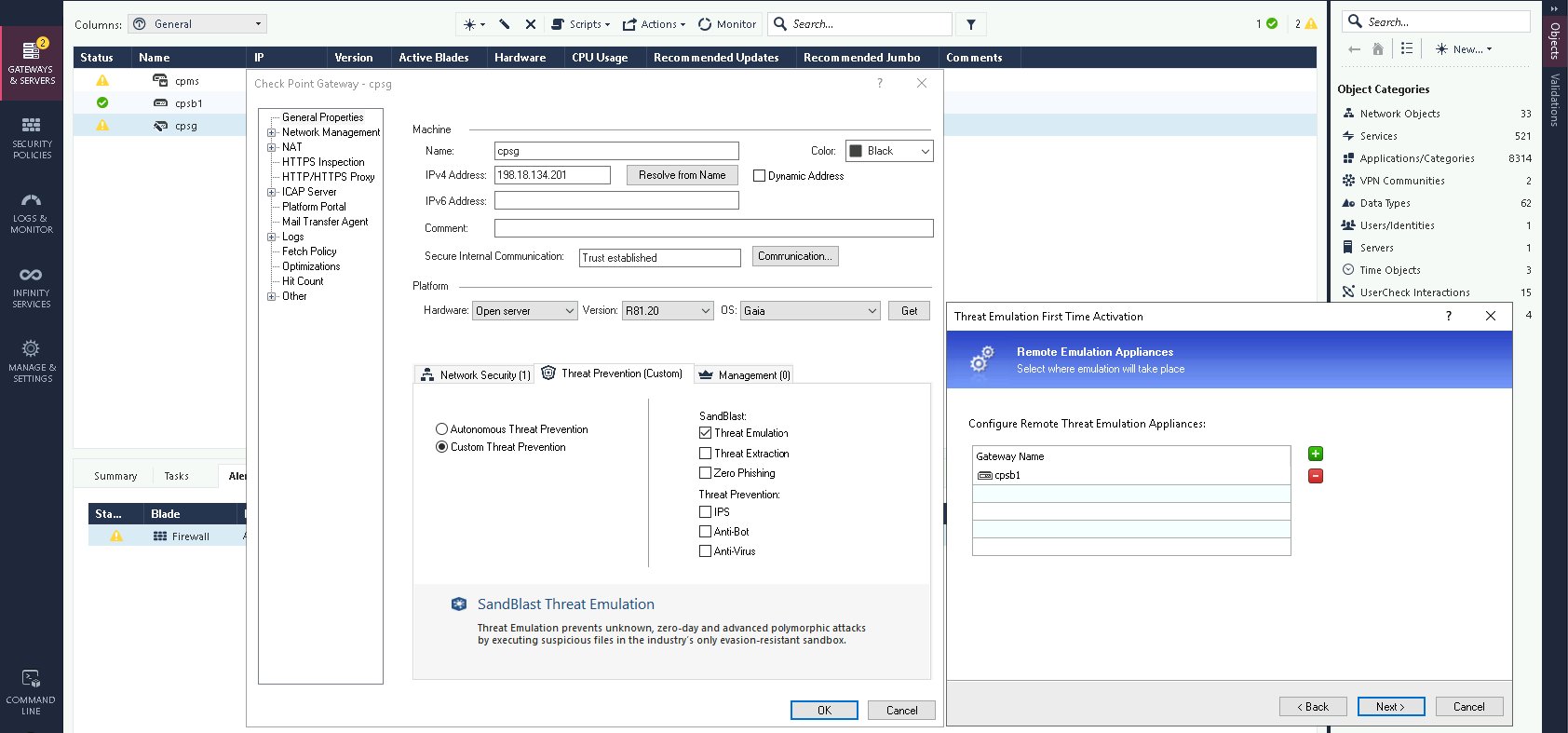
Next on the Security Gateway (cpsg), enable the Threat Emulation as well and point it to other box
And select the cpsb box
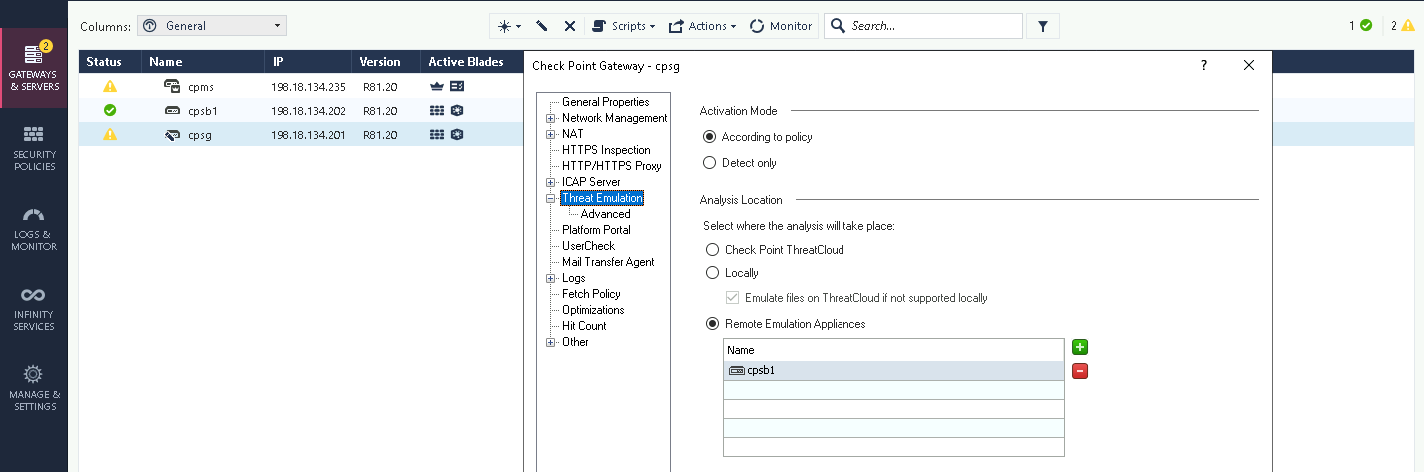
Now the Security Gateway also has Threat Emulation enabled, but pointing to a remote box
Configuring Policy
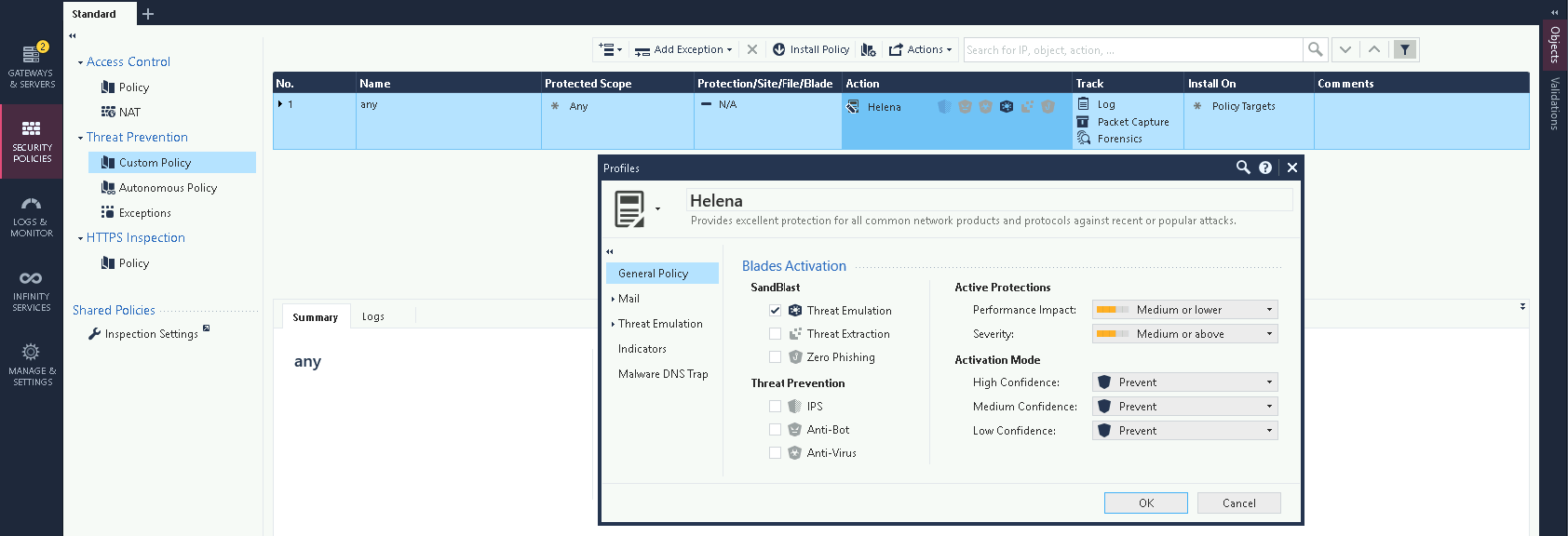
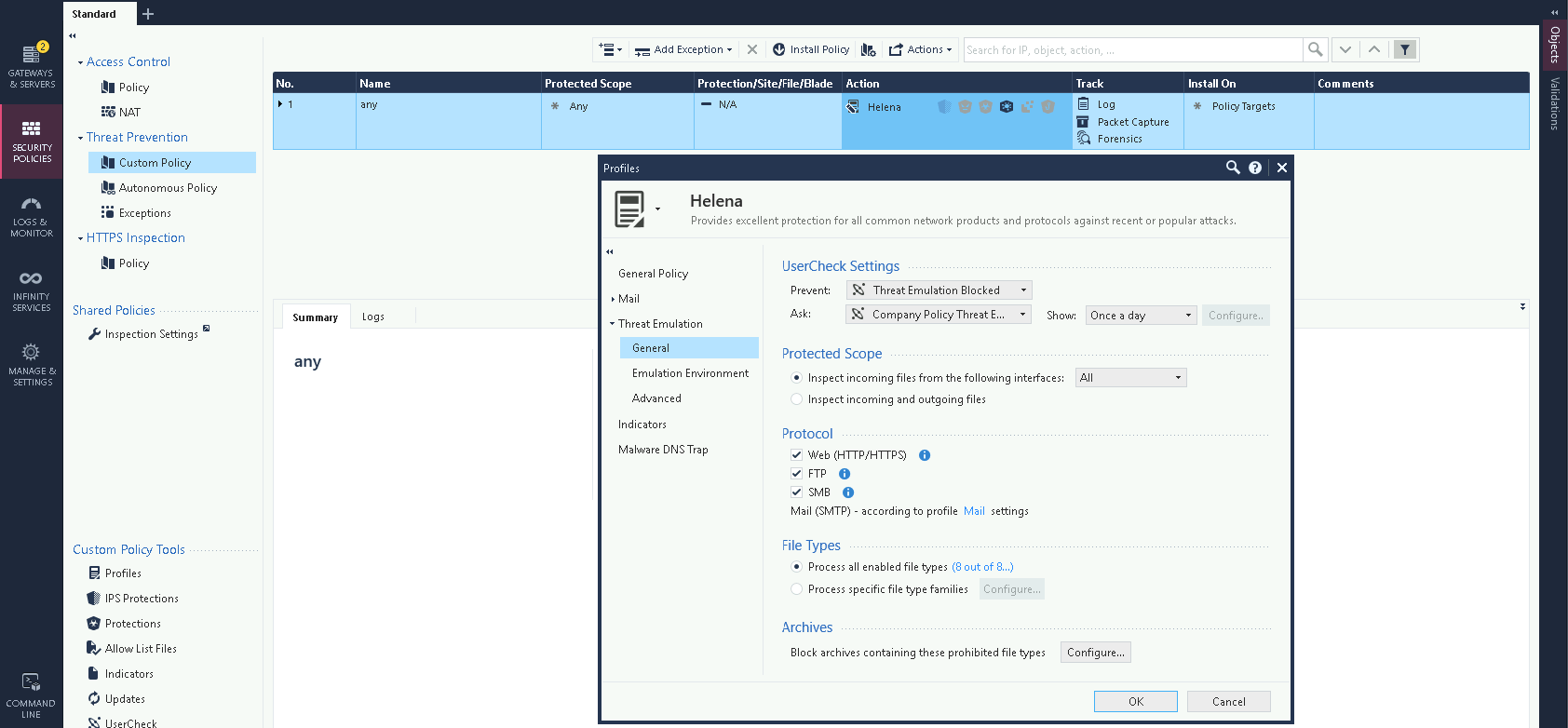
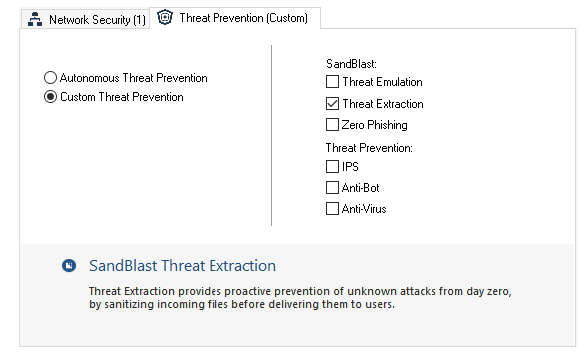
On Threat Prevention » Custom Policy, create a new Profile and enable Threat Emulation Blade
Enable the protocols which we’d like to send to sandbox, in this case we’ll focus on SMB
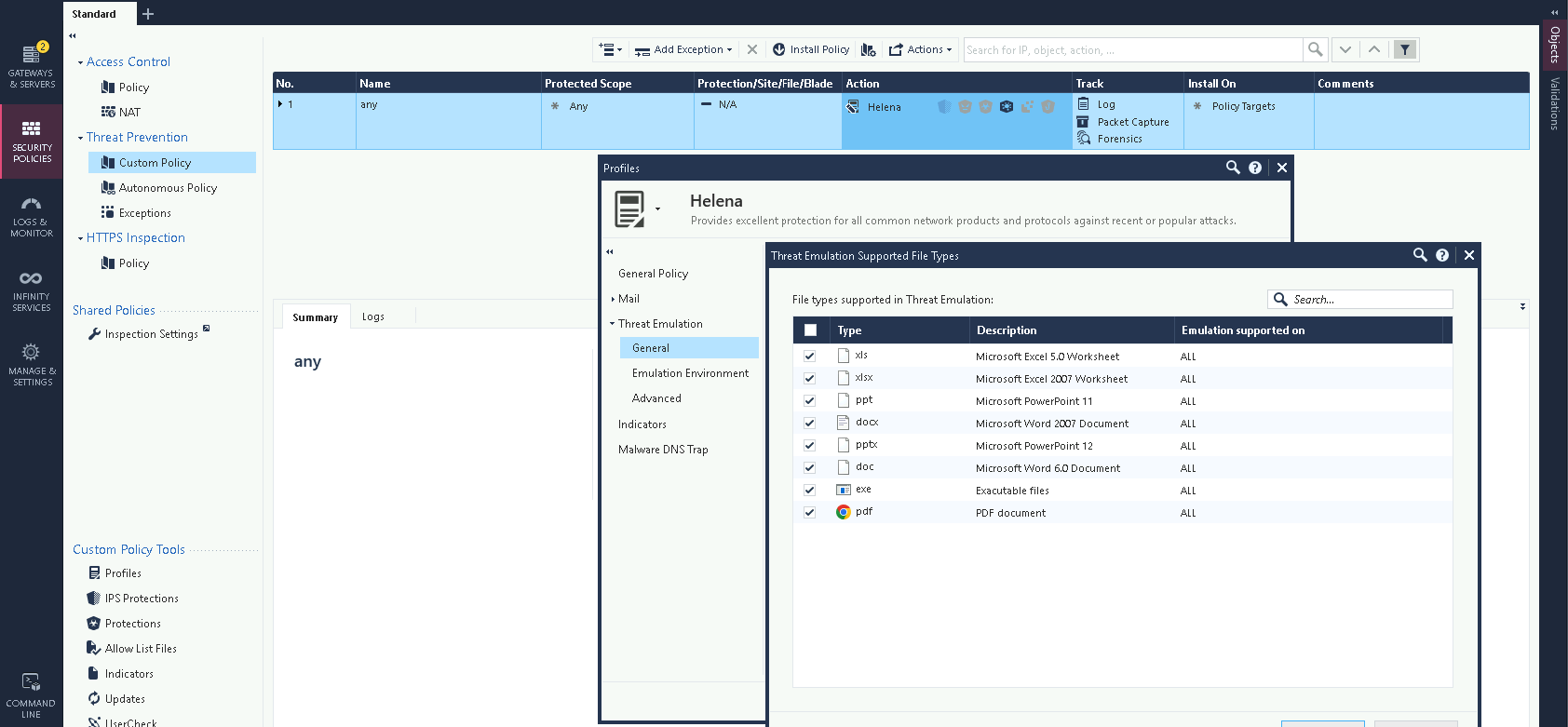
Then on the File Types, we can see all the supprted types for sandboxing
Emulating Threat
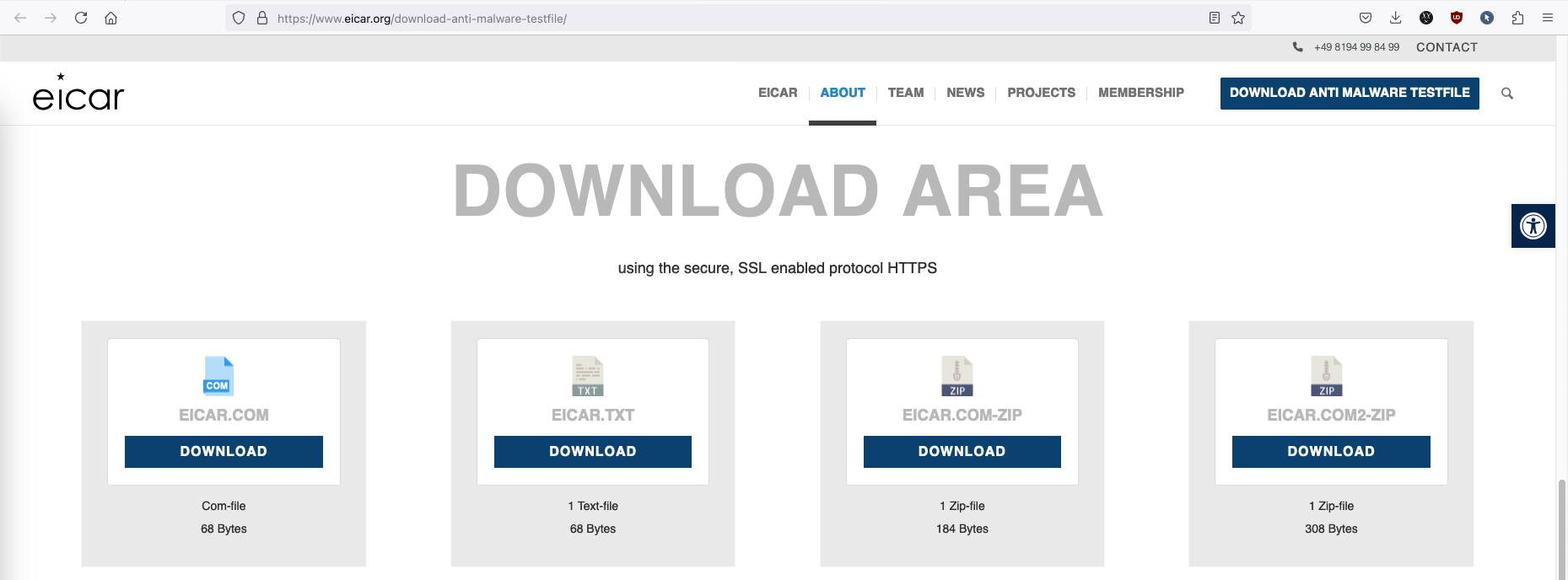
To emulate threat, we’ll download infected files from Eicar and save it on our file server
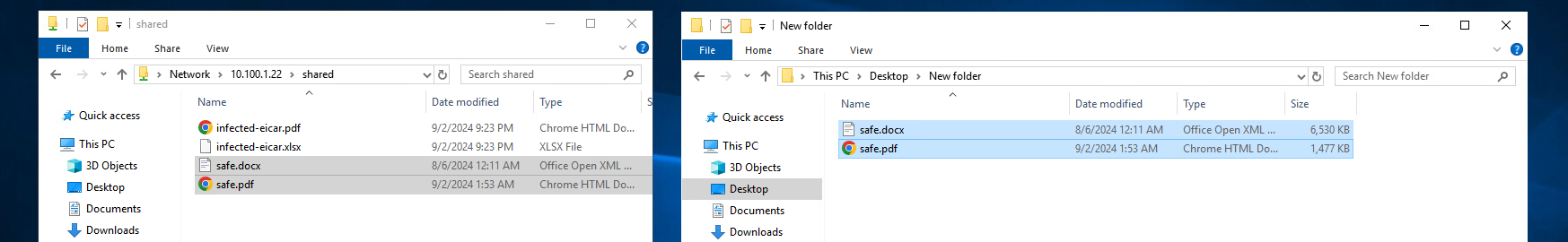
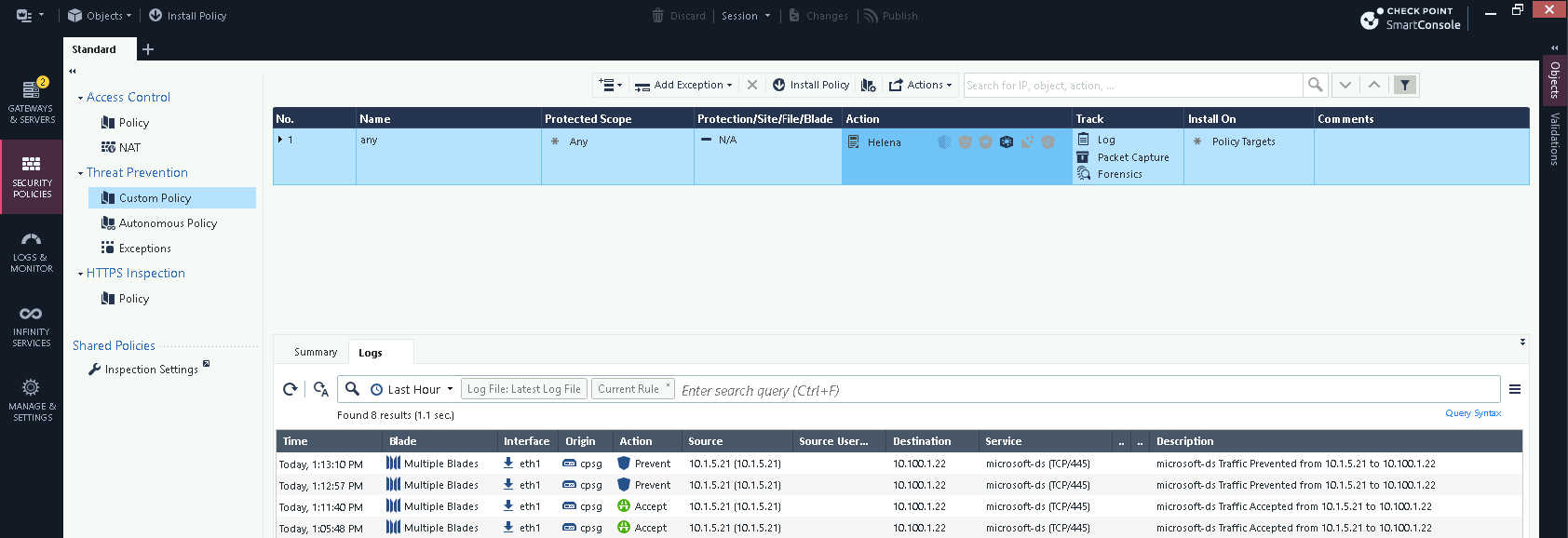
Here on the user PC, first we try copying normal files over SMB
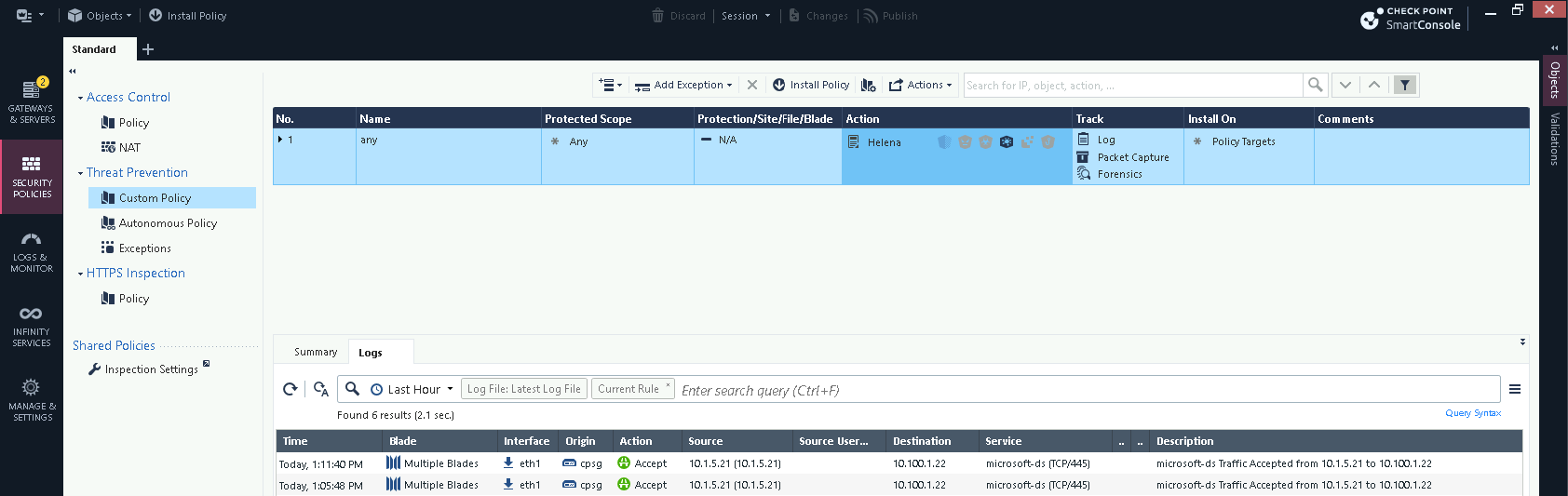
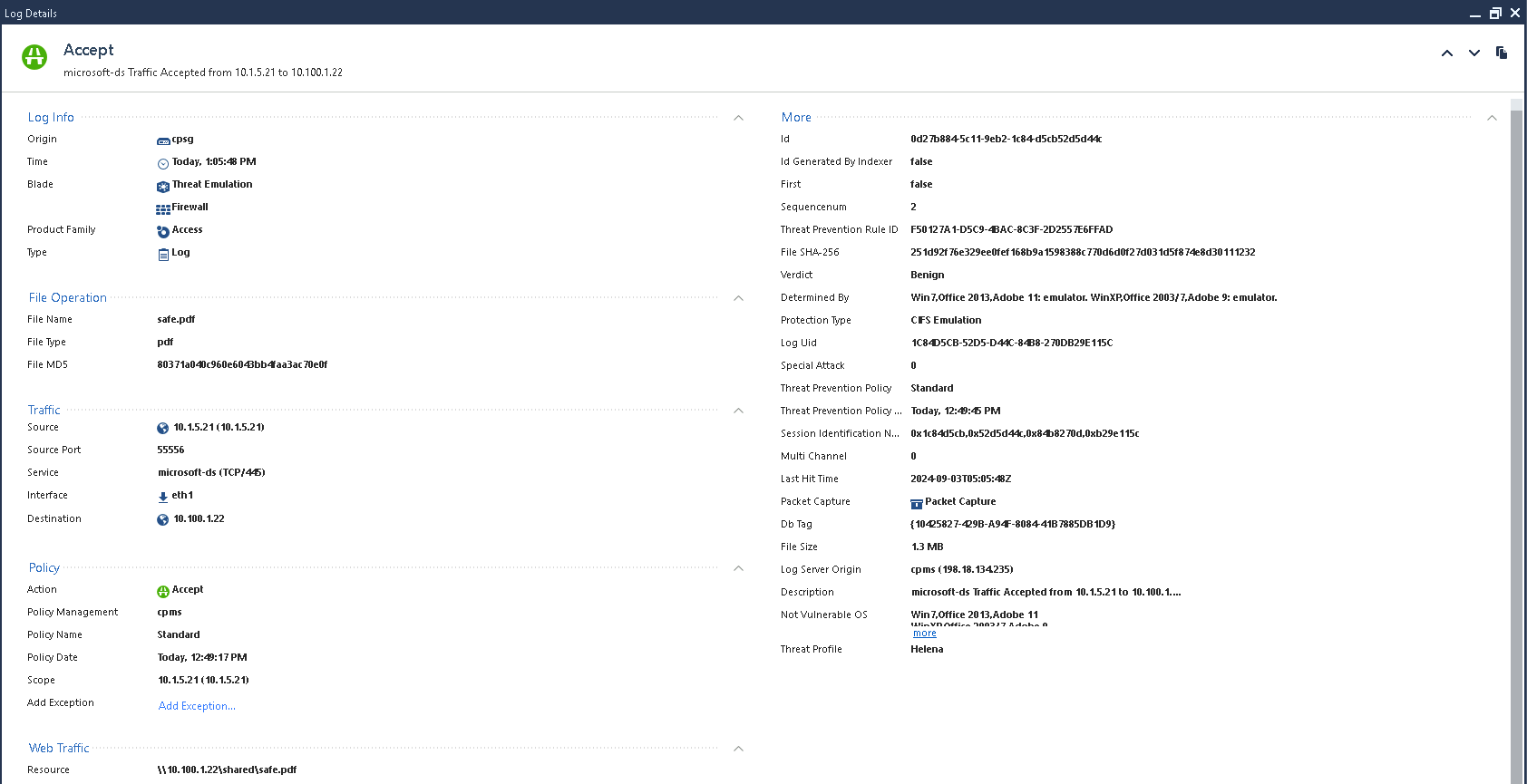
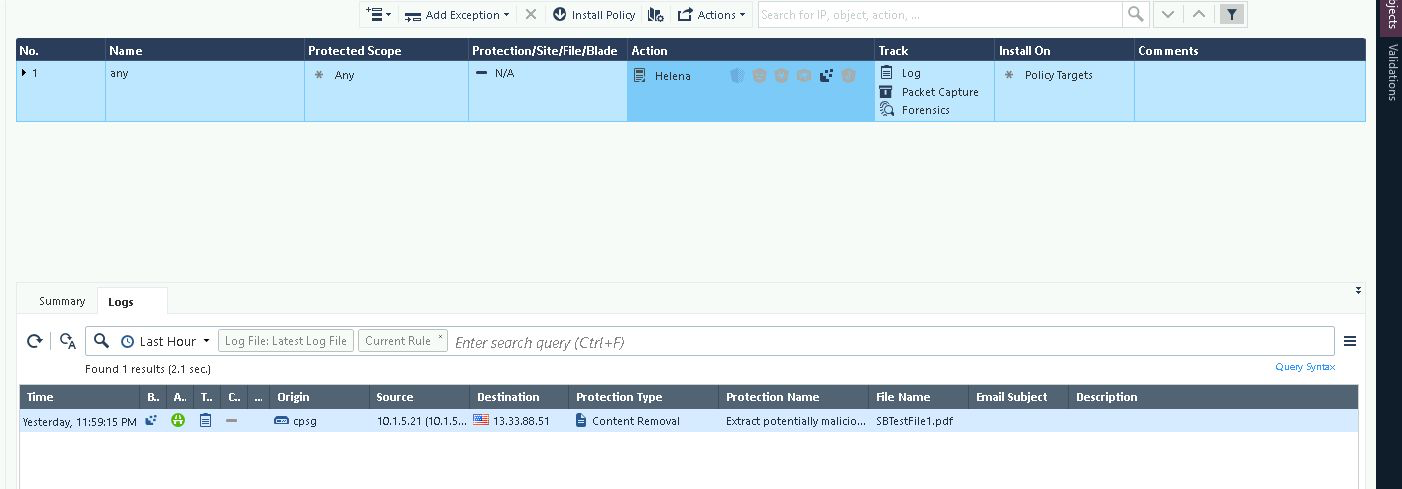
On the Sandblast log we can see the files are determined to be clean and allowed
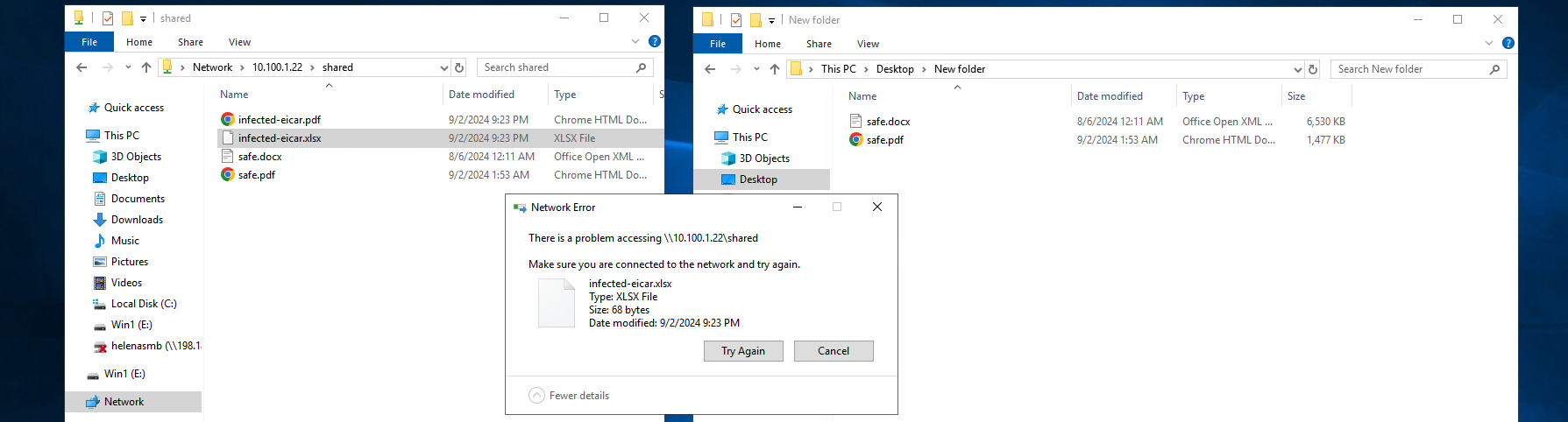
But when we try copying infected files, we get a network error
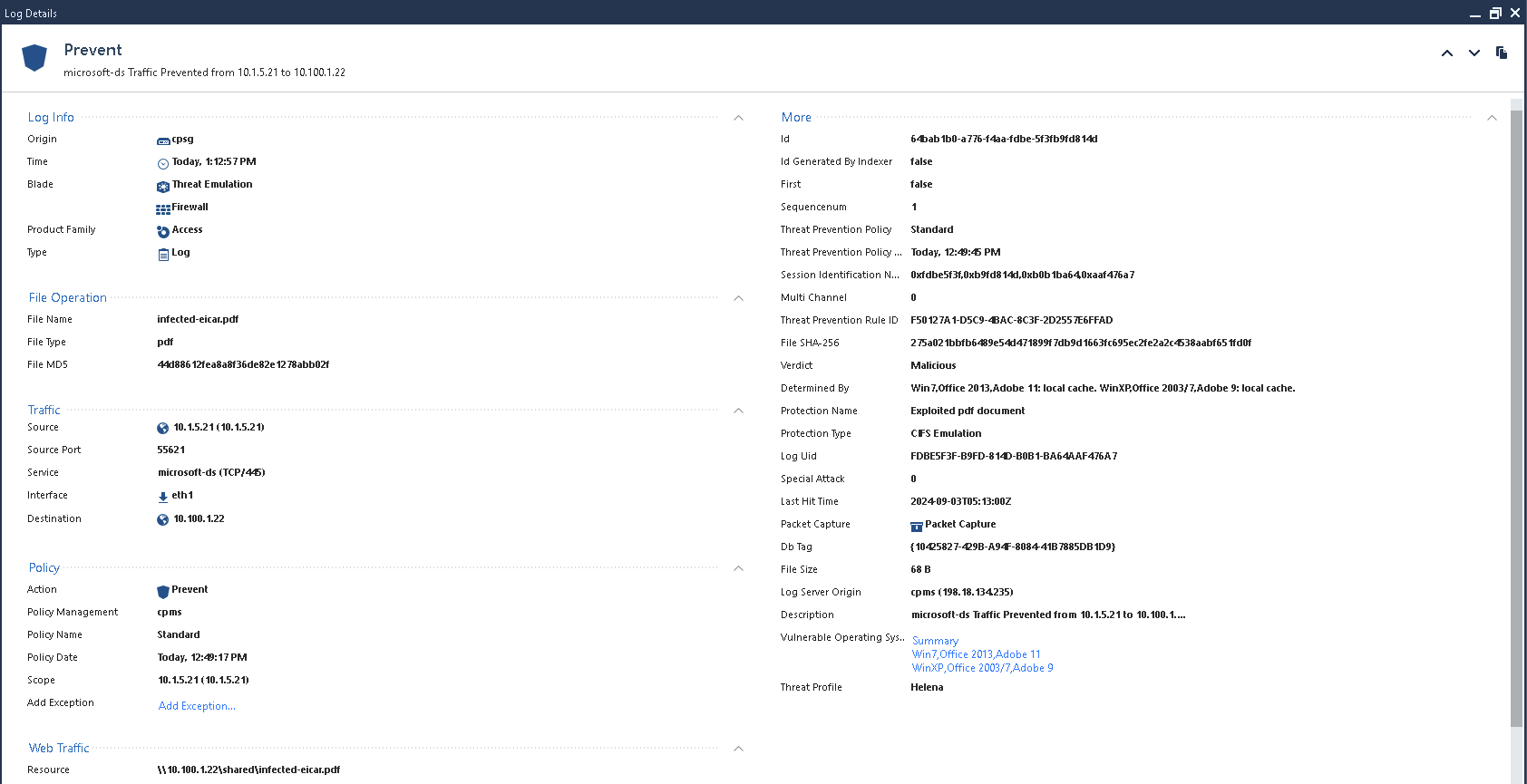
That’s because Check Point determines that the files are not safe and take the prevent action
Threat Extraction
Check Point Threat Extraction is a cybersecurity solution designed to protect against document-based threats by removing potentially malicious content from files. It proactively cleans files by extracting and reconstructing them, stripping away exploitable content, such as embedded macros or active code, while preserving the original format. This ensures that only safe, sanitized files are delivered to users, reducing the risk of zero-day attacks and malware infections.
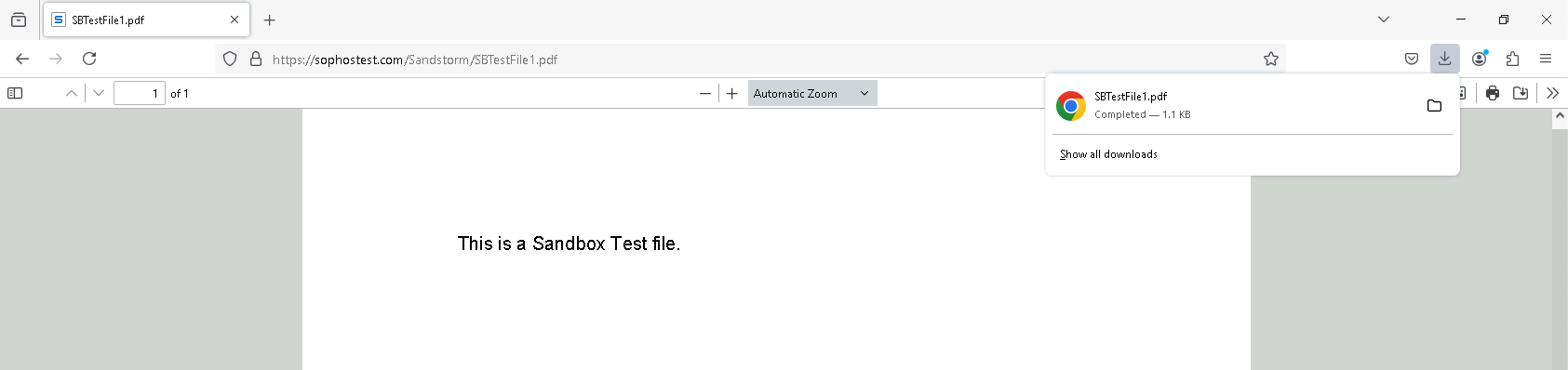
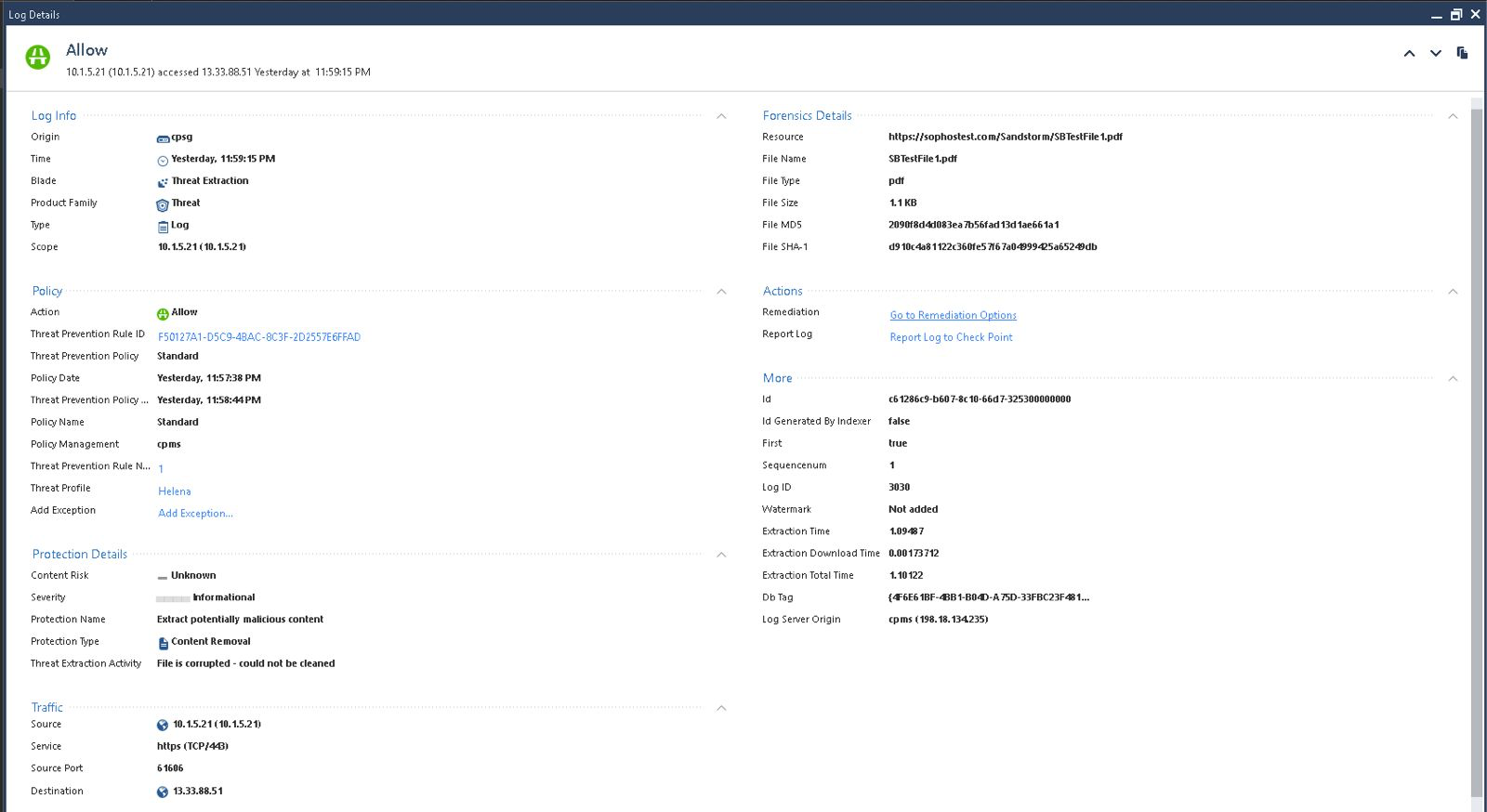
On the Client PC, if we try accessing malicious files like this Test File, we will still be able to download it like normal
But behind the hood, Check Point runs an extraction to remove any potensially malicious threat inside the file, and delivering the cleaned up version of it