Cisco Duo with Check Point VPN
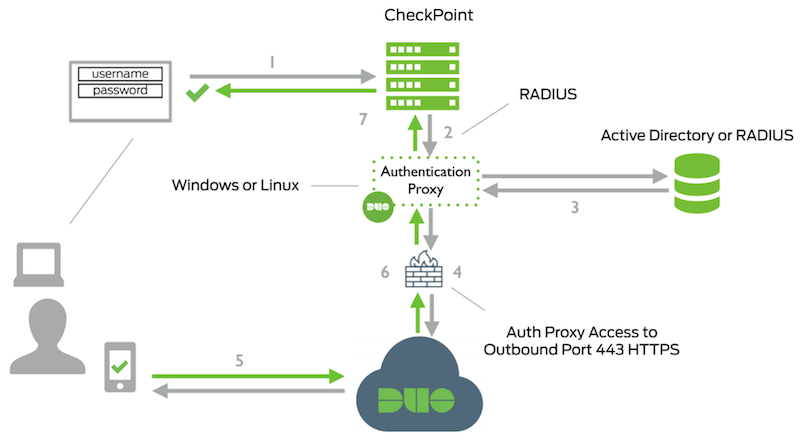
Cisco Duo adds multi-factor authentication (MFA) to secure Check Point Remote Access VPN logins. When a user connects to the Check Point VPN, Duo verifies their identity with a second factor before granting access, ensuring stronger protection against compromised credentials.
VPN with Domain Users
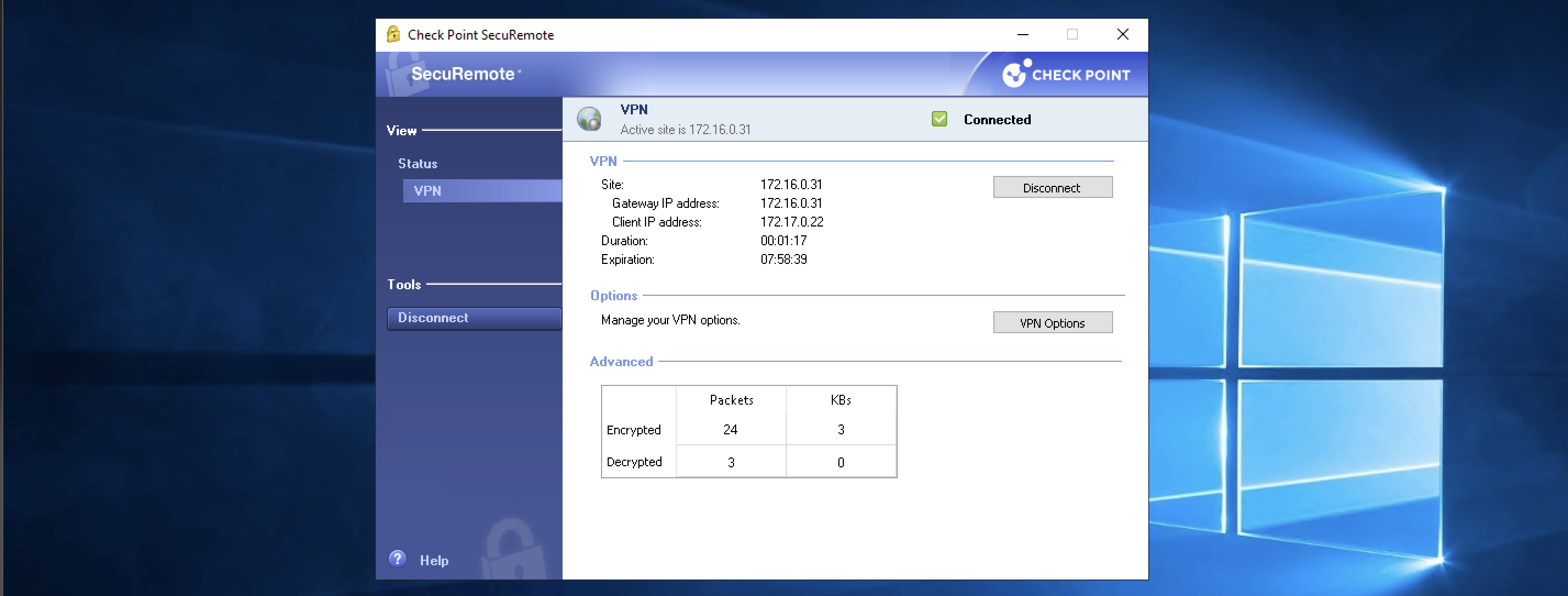
Here we have a working Check Point Remote Access VPN that uses local users to log in
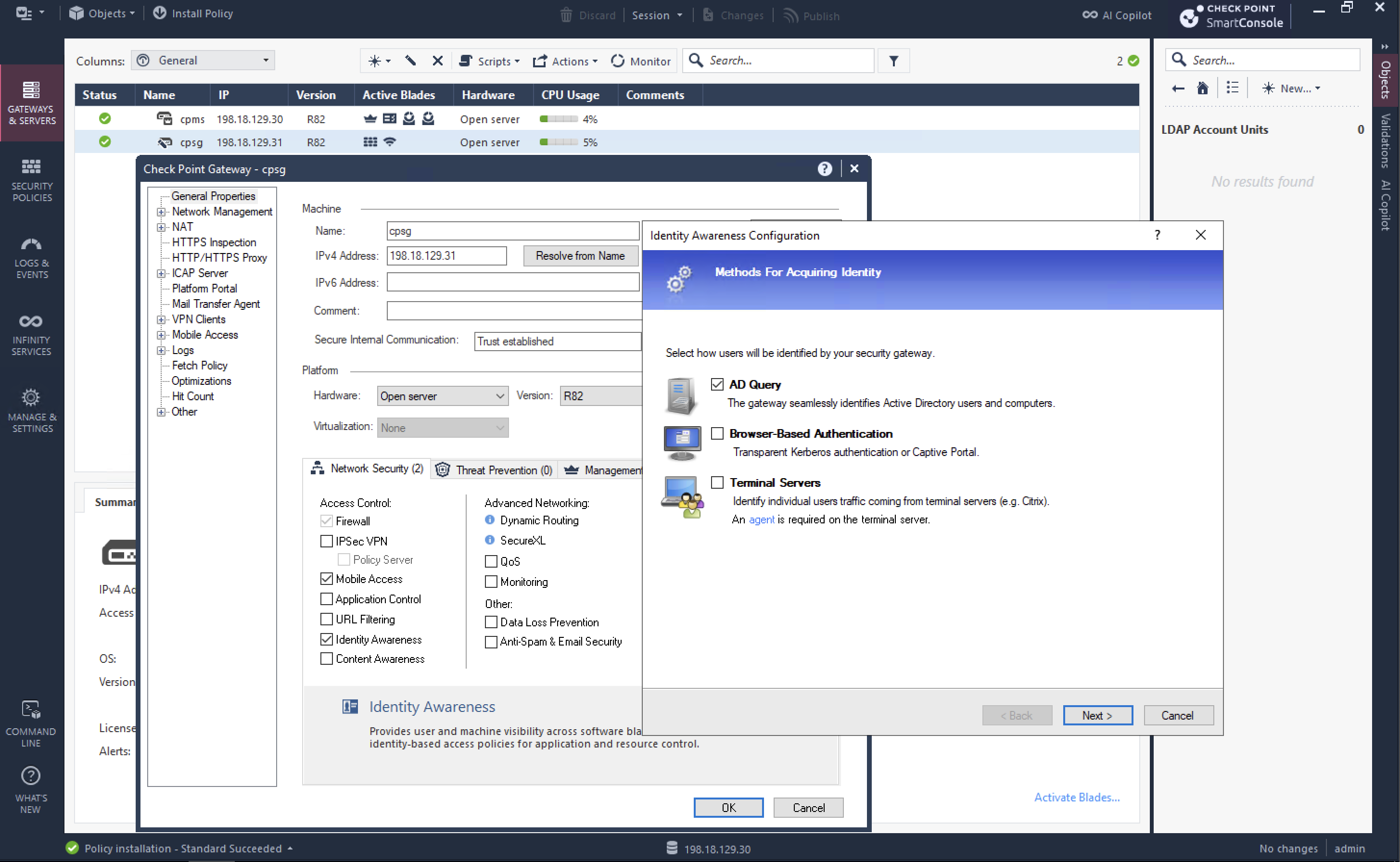
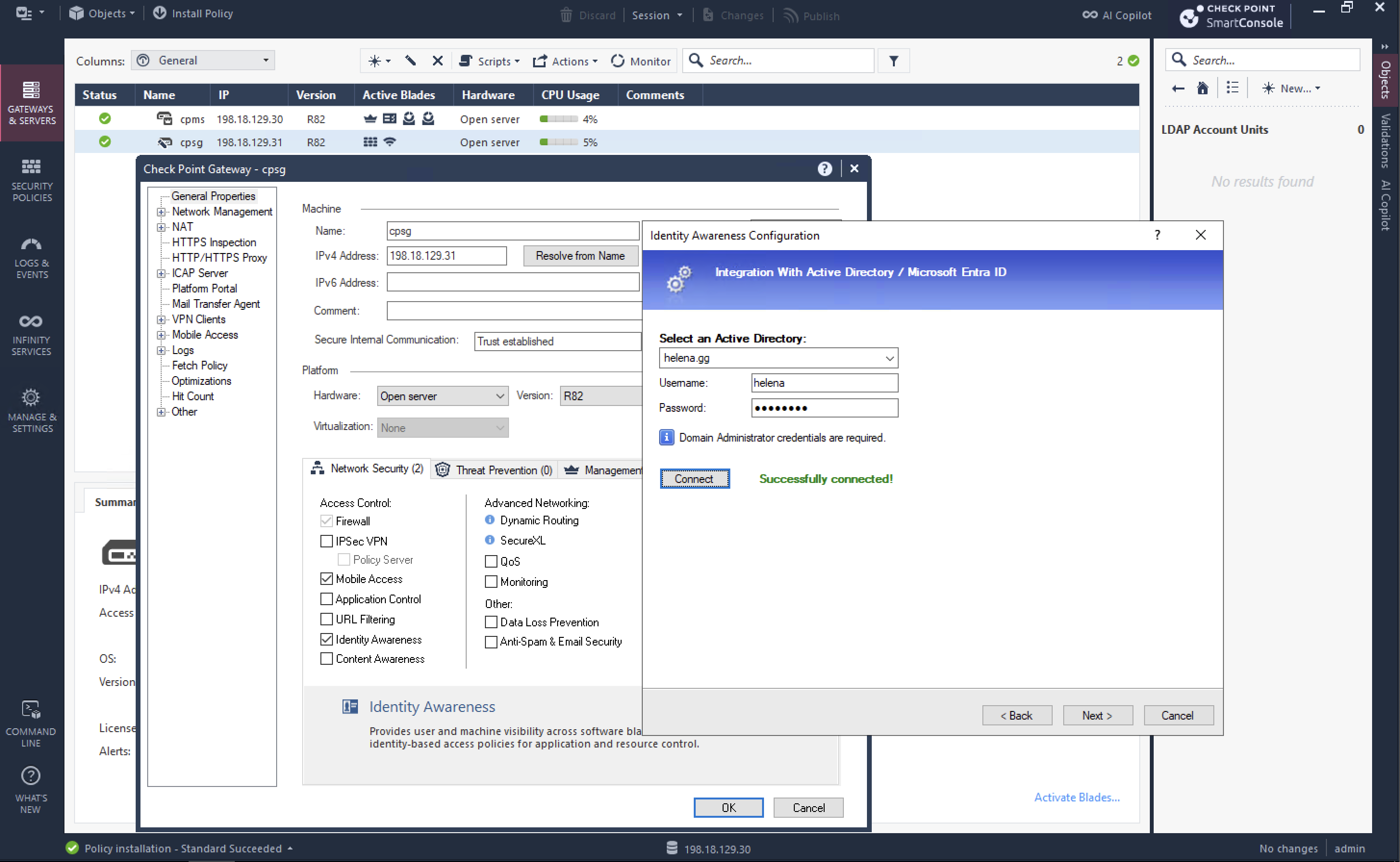
Before enabling MFA, first we have to enable VPN login using AD users, lets enable Identity Awareness Blade
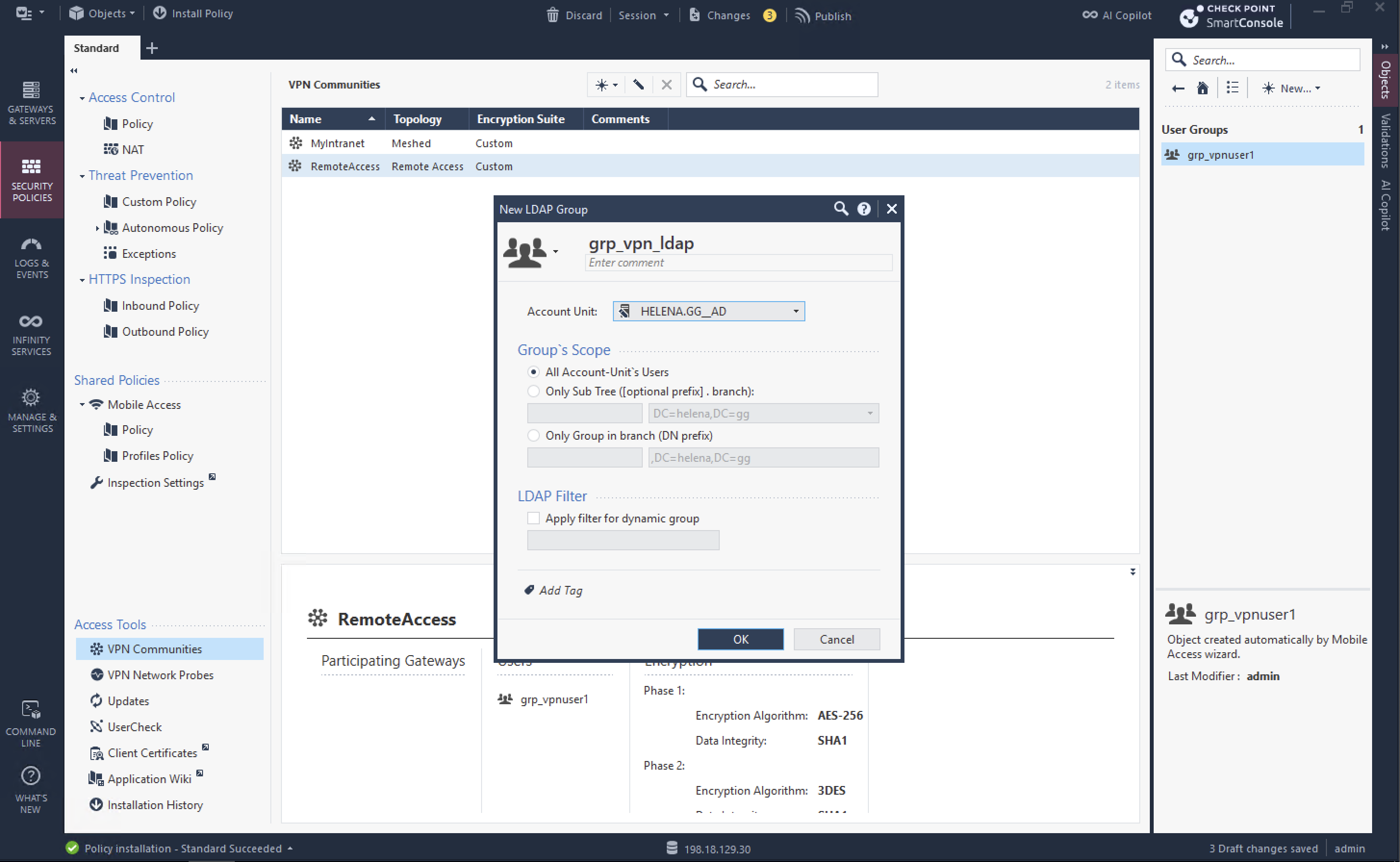
Next create a new LDAP Group that points to the newly created AD LDAP Unit
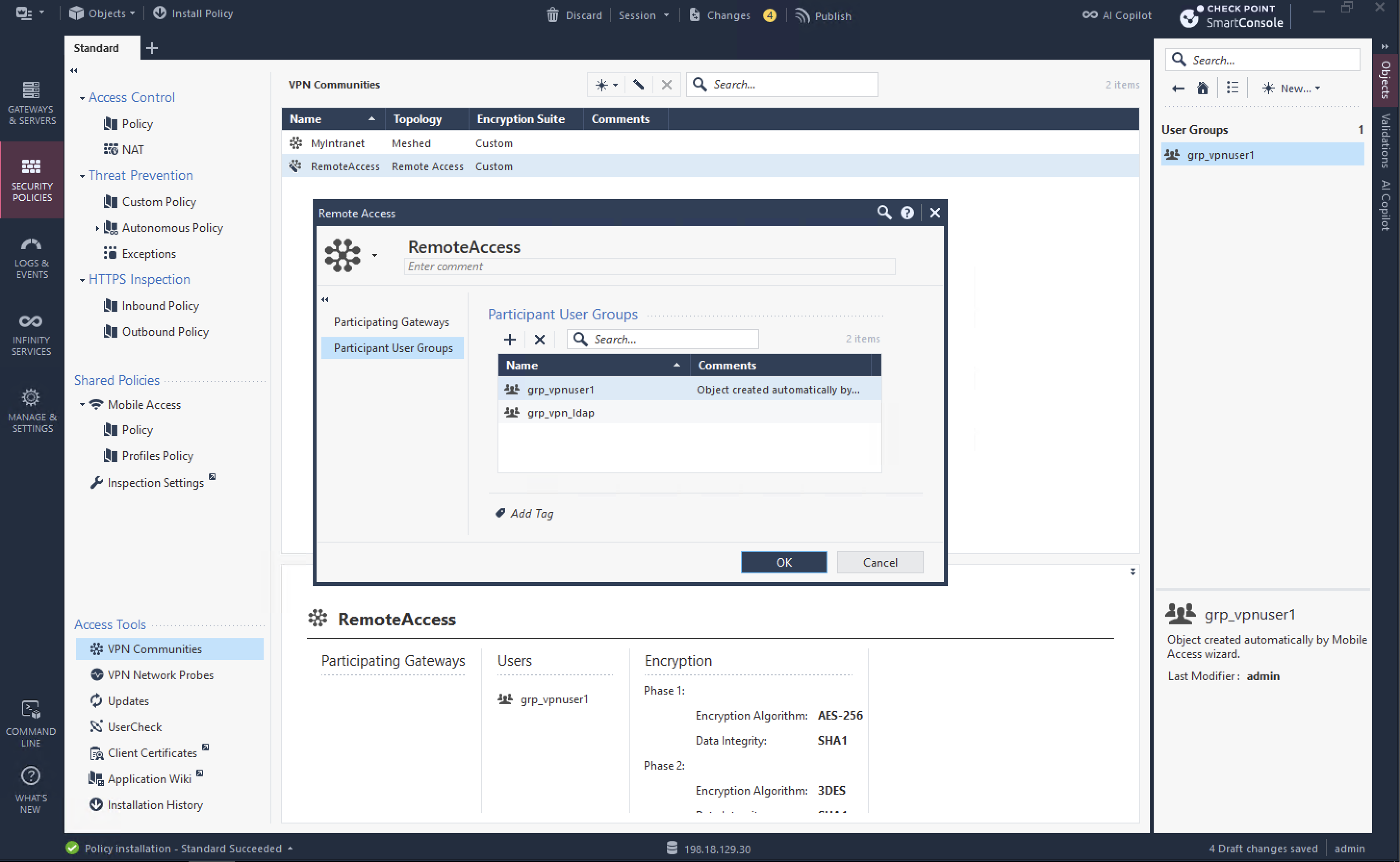
Then add the LDAP Group as a participant in the Remote Access VPN Community, this will allow AD Users to login to VPN
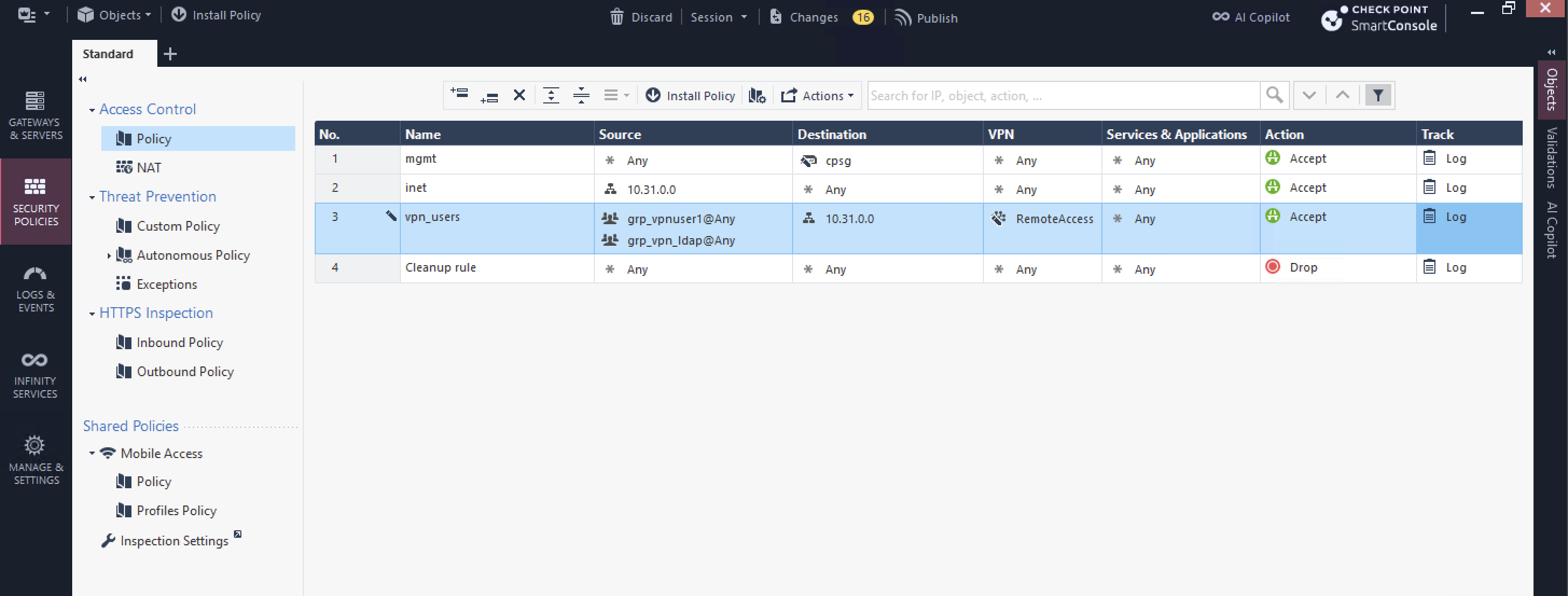
And lastly we also need to add policy for the AD users to access internal network
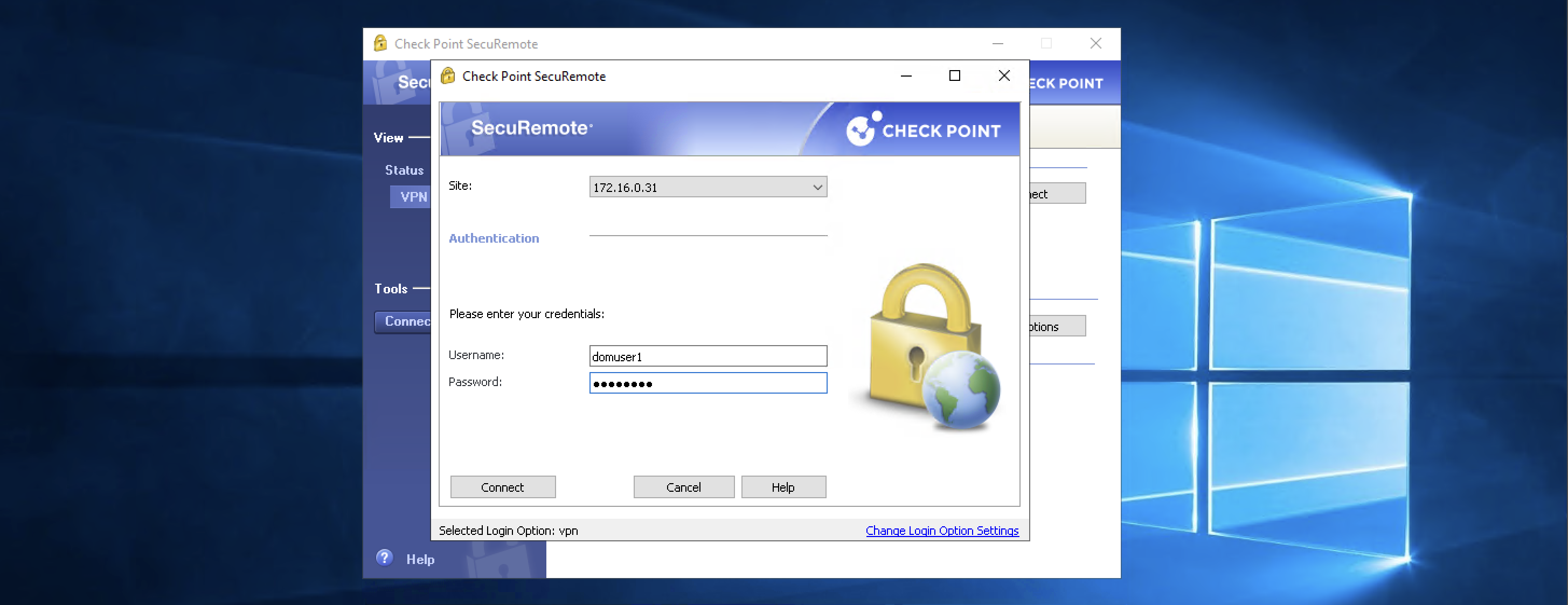
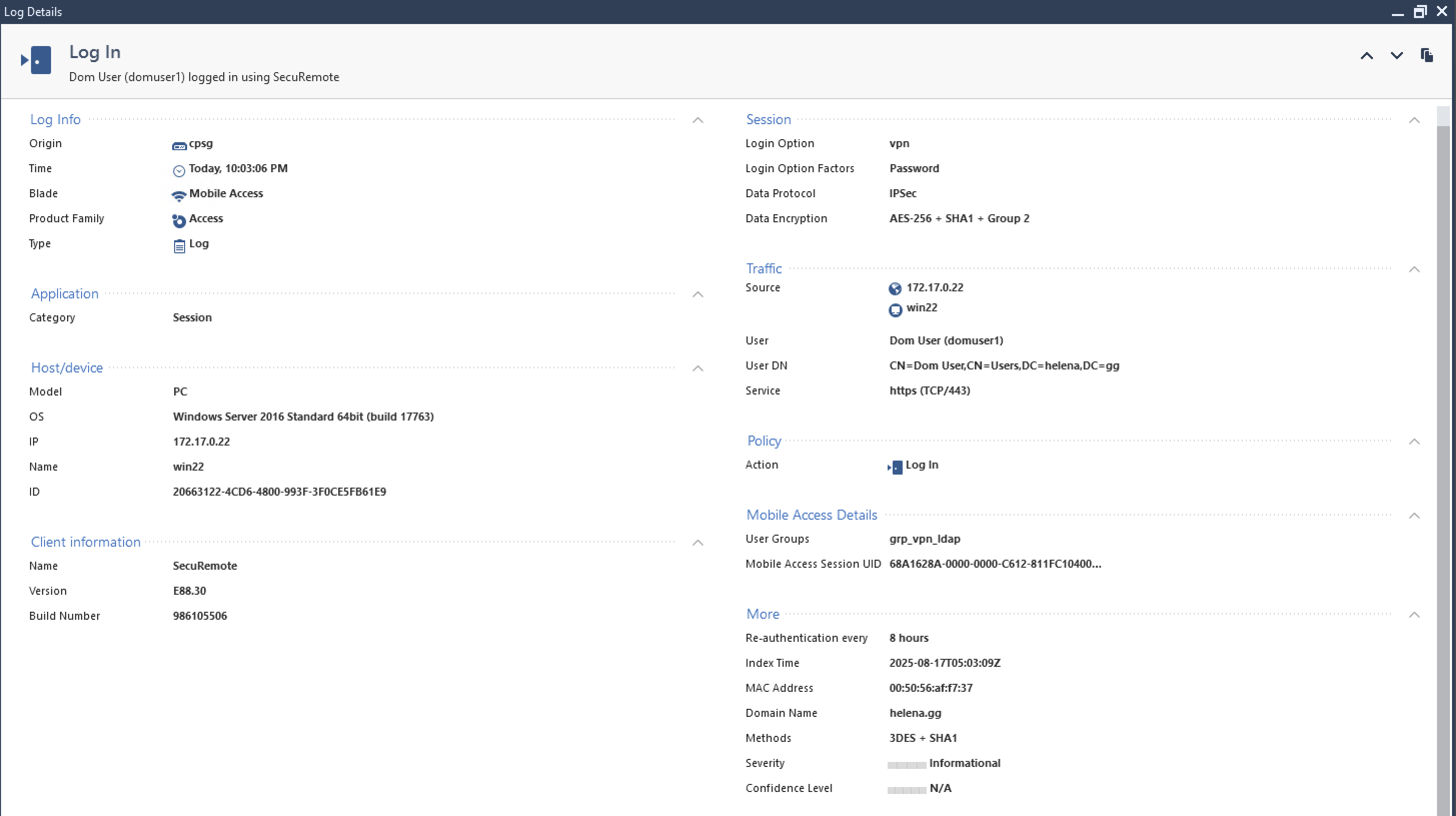
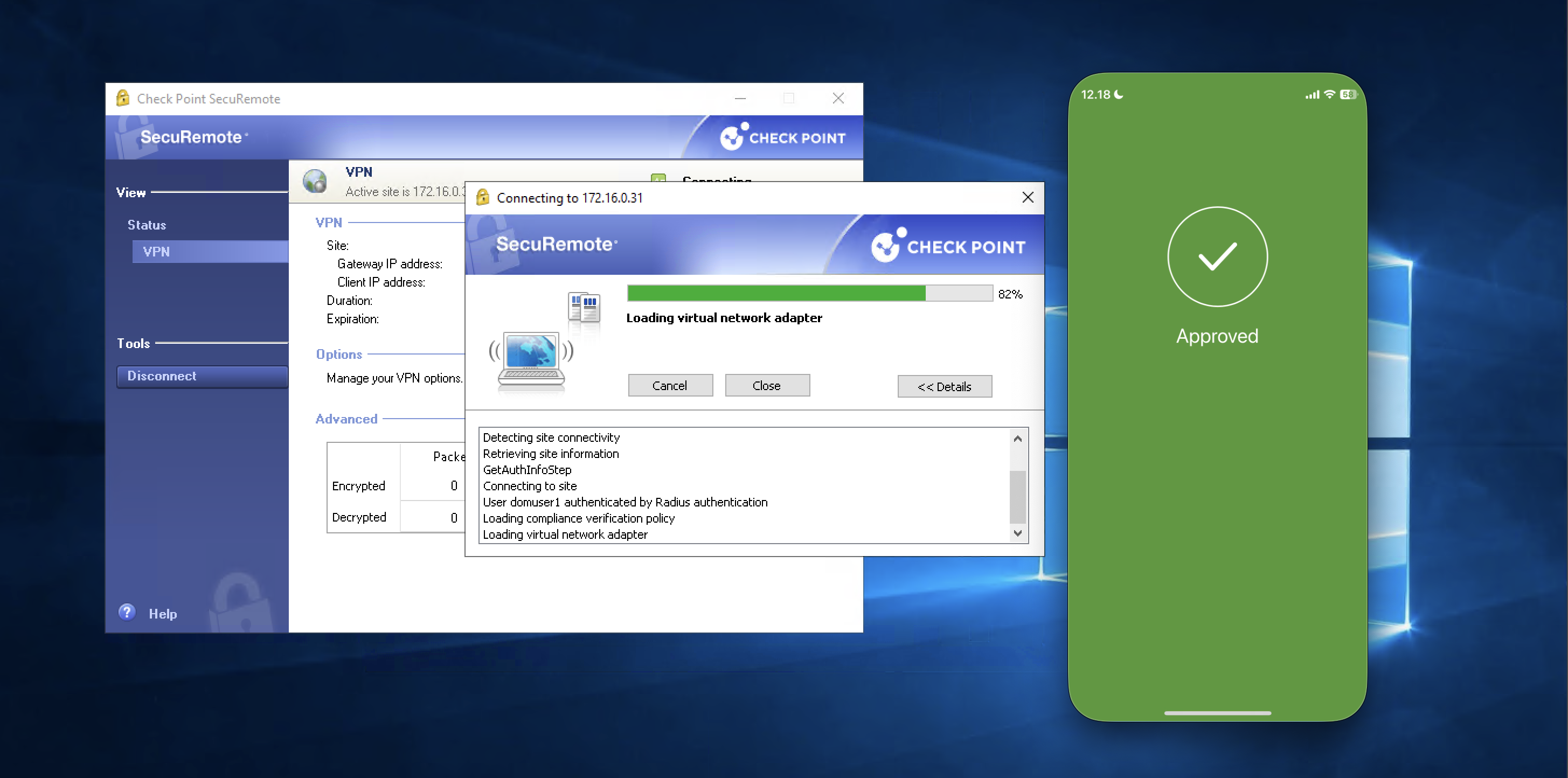
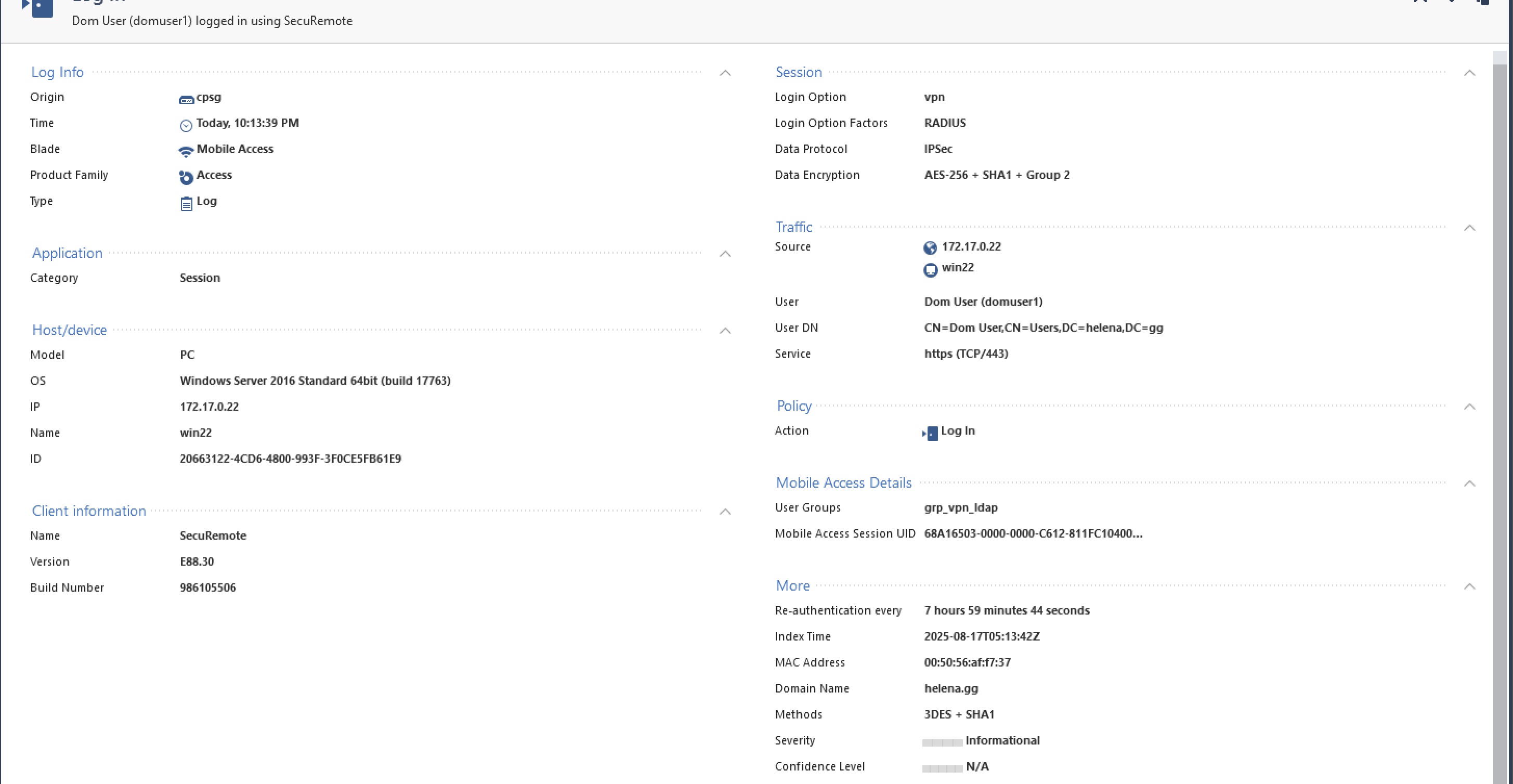
Now we can login to VPN using AD users (domuser1@helena.gg)
VPN with Duo MFA
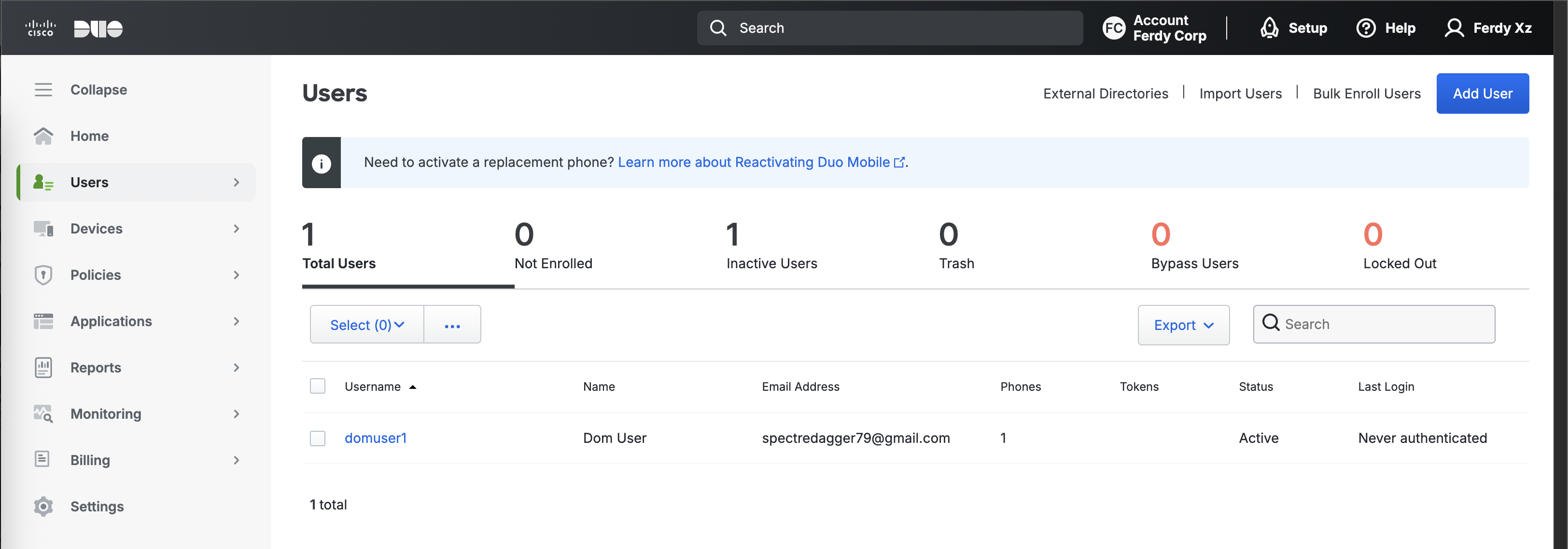
Lets enable Duo to be used as MFA, we’ll pretty much follow a similar implementation as this one, first we make sure the user is present on Duo with same username as the one on AD
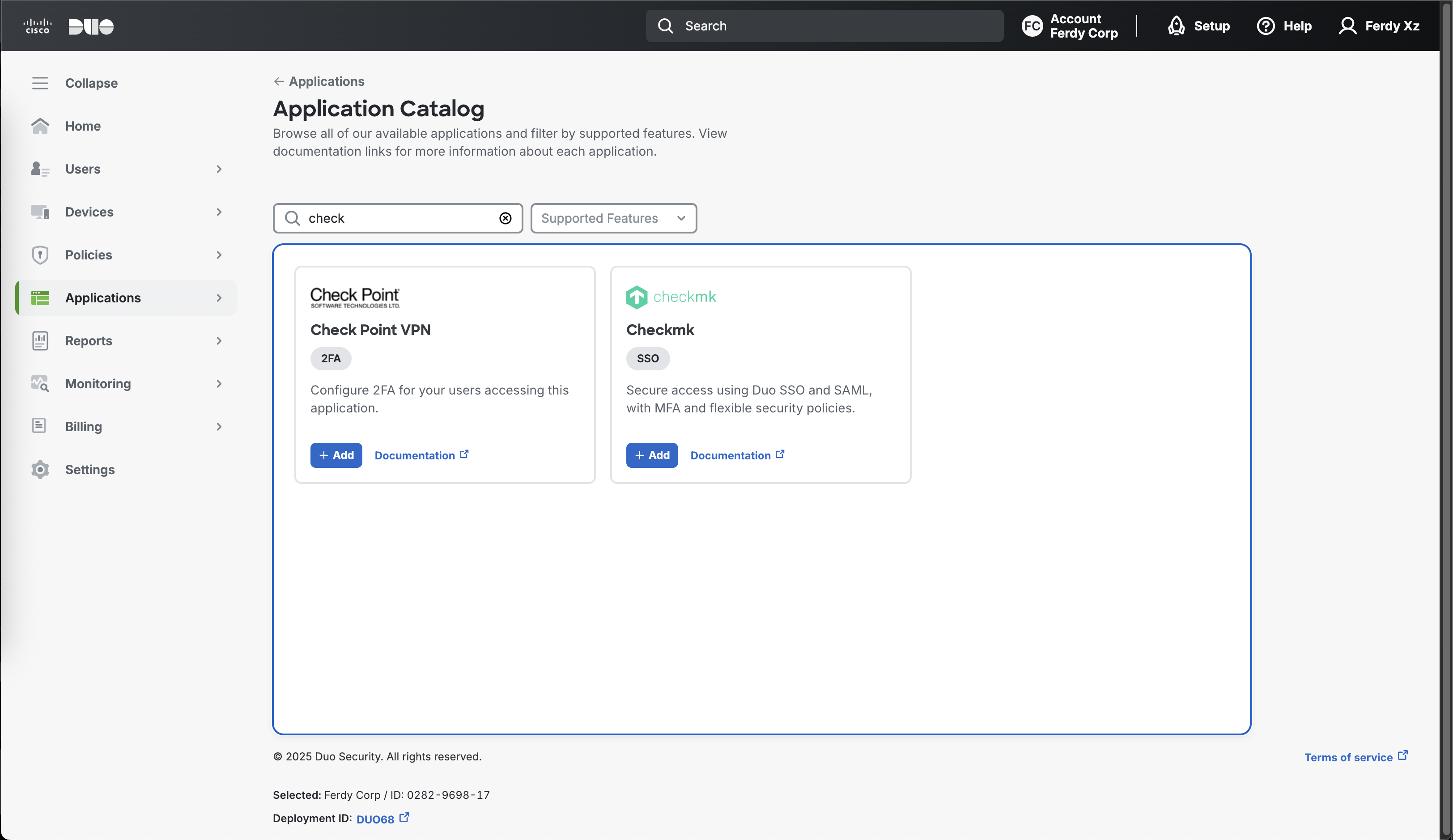
Then we add a Protected Application, Duo already provides a template for Check Point VPN so lets use that
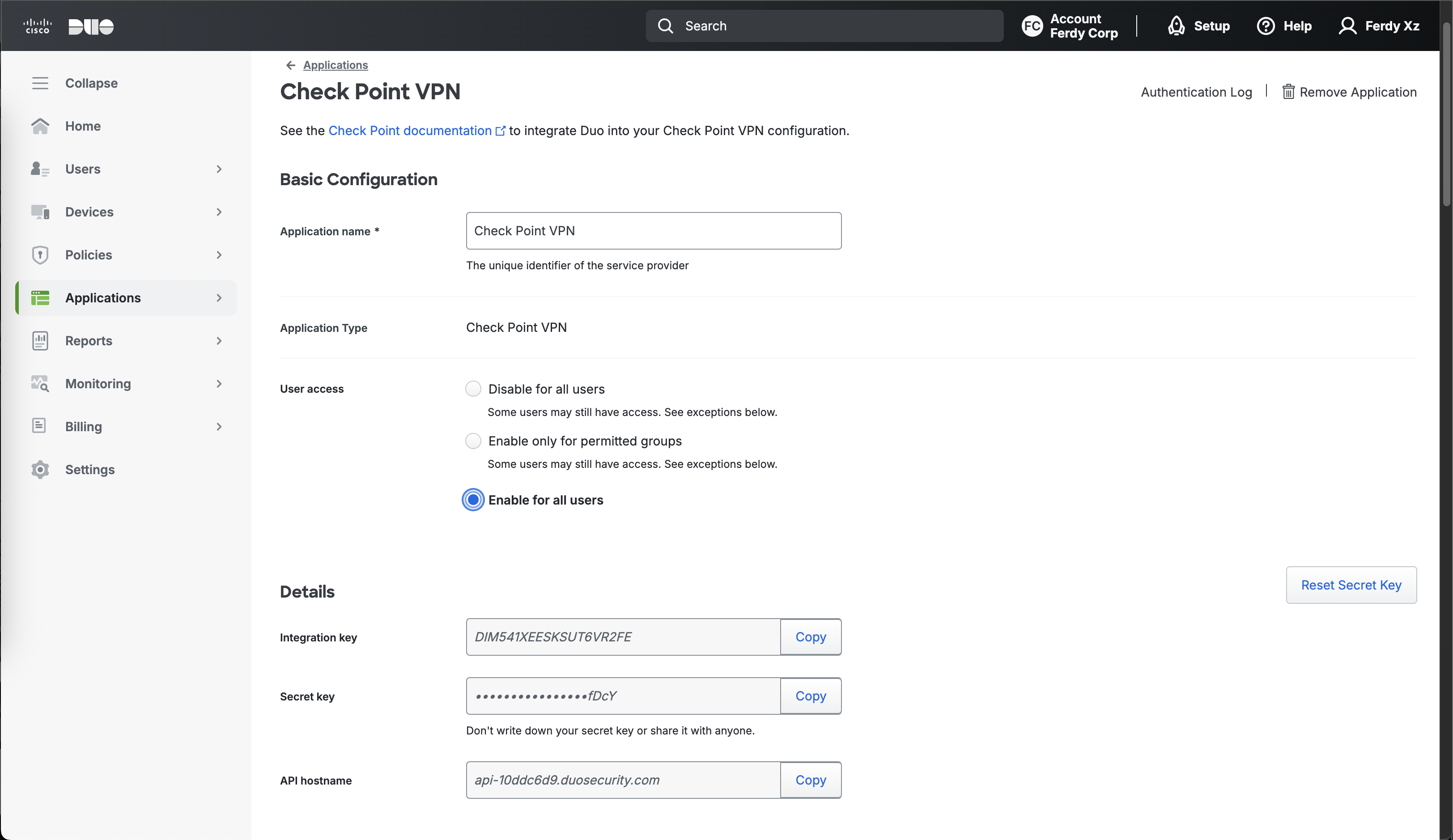
Copy all the necessary credentials
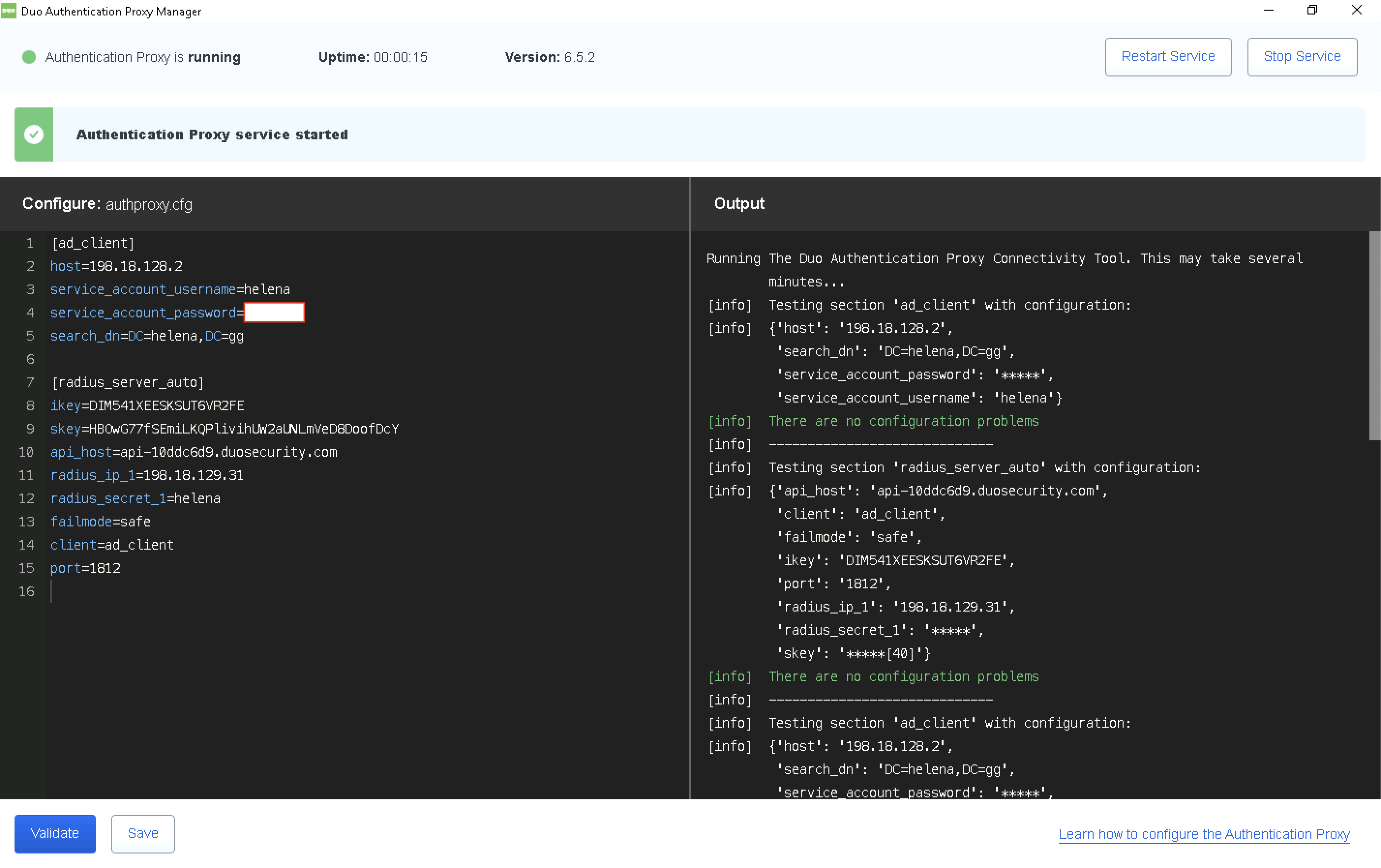
And configure it on the Duo Proxy Server
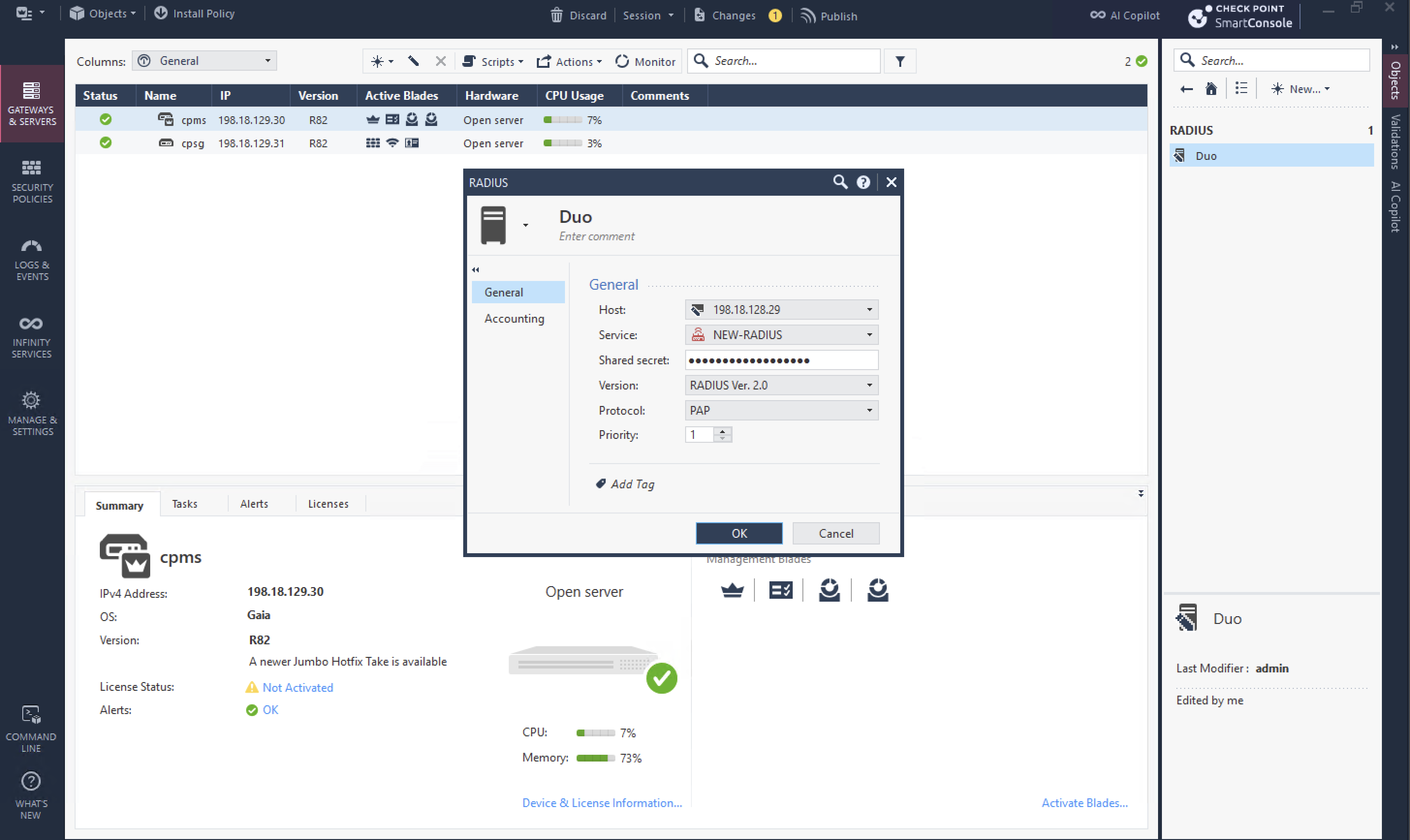
Now we go back to Check Point, lets create a new RADIUS Server Object pointing to Duo Proxy Server
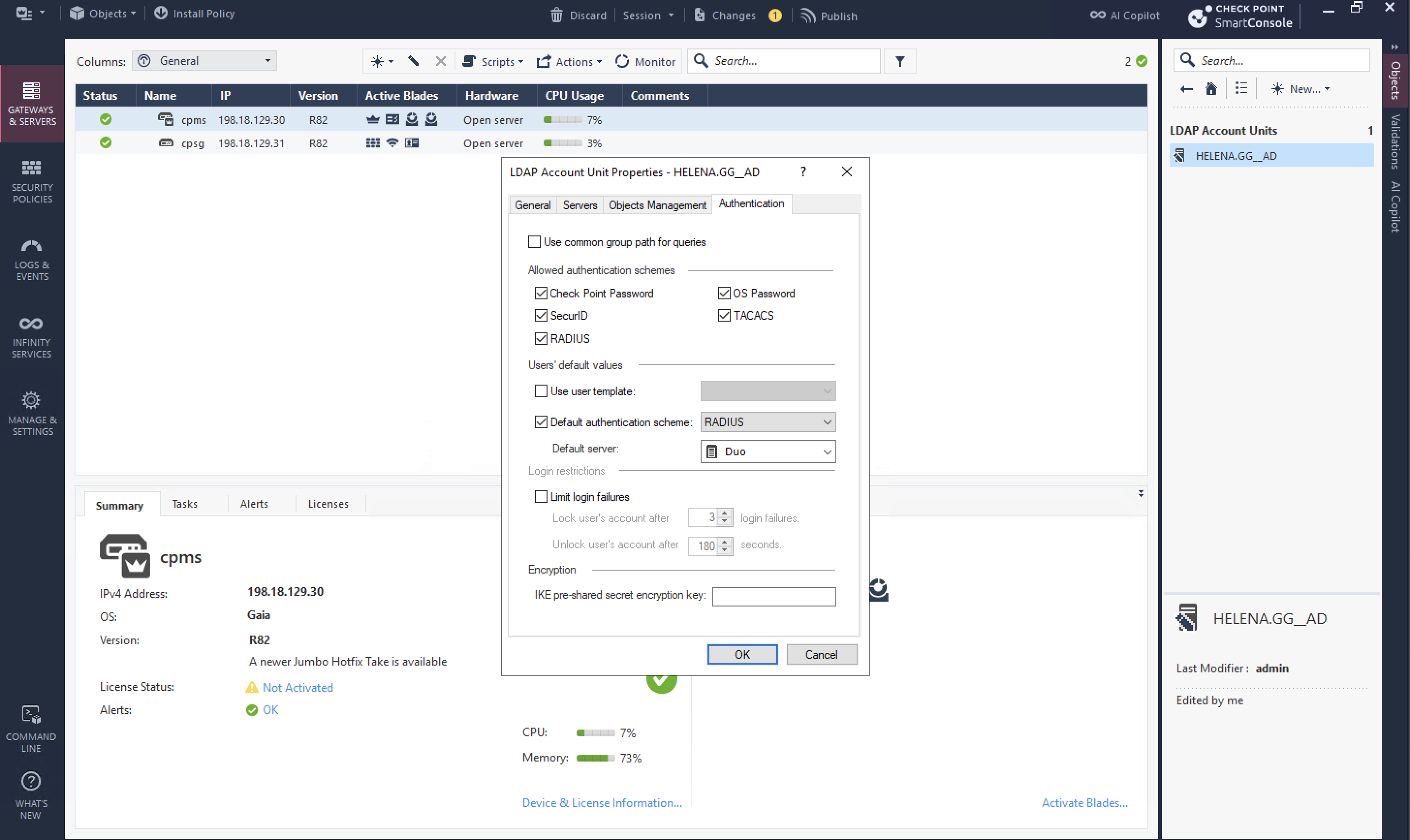
Then on the LDAP Account Unit, enable Radius Authentication Scheme and point it to the previously created RADIUS Object
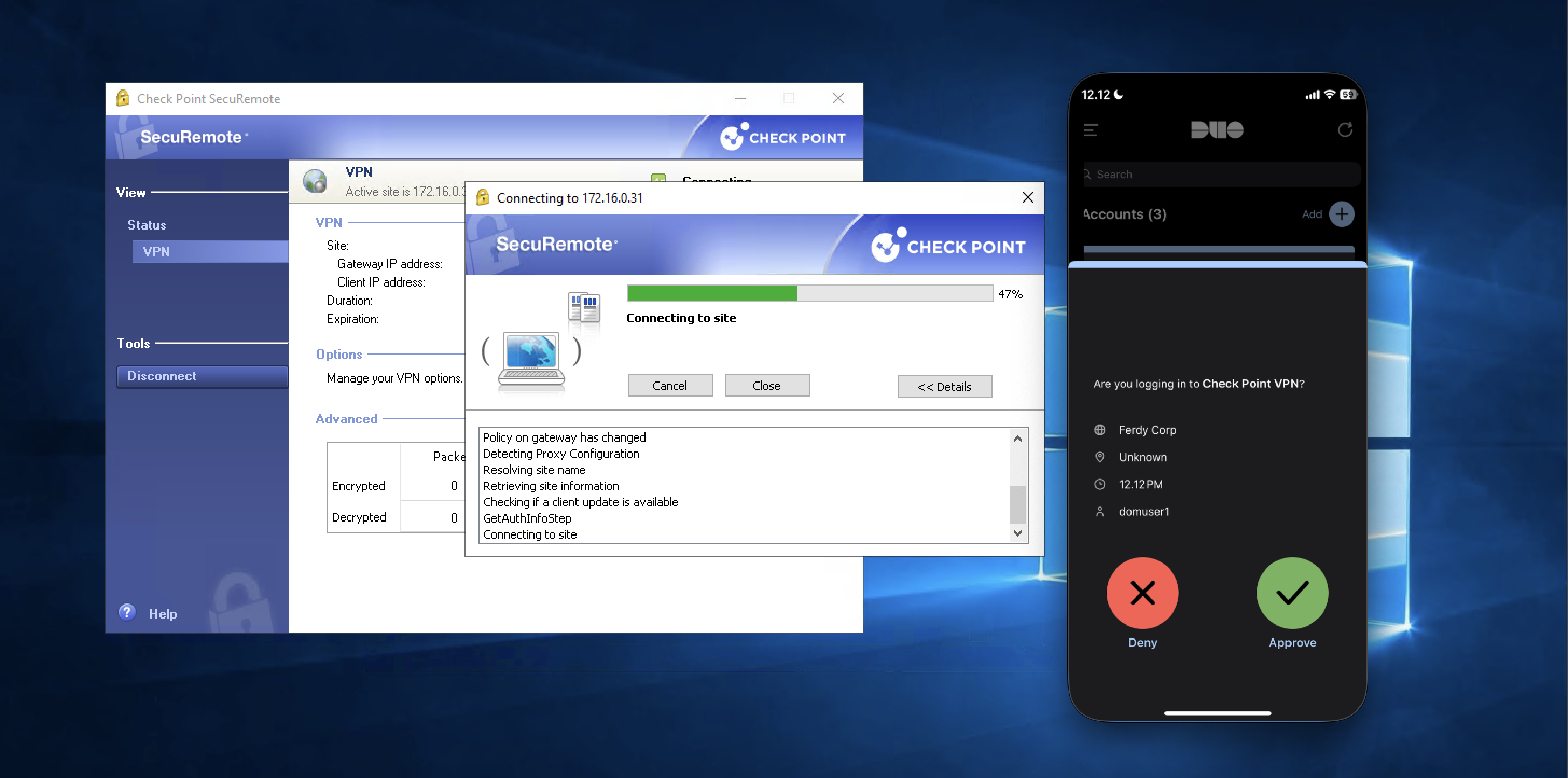
And thats pretty much it, if we try connecting to VPN using AD users, we will now be prompted a Duo MFA
But if we login using local users, which we still allow on the Community Configuration, we will connect directly without MFA