DHCP Snooping & Dynamic ARP Inspection
DHCP Snooping is a security feature that prevents rogue DHCP servers from distributing malicious IP configurations. It works by allowing DHCP responses only from trusted ports and maintaining a binding table of valid IP-MAC pairs.
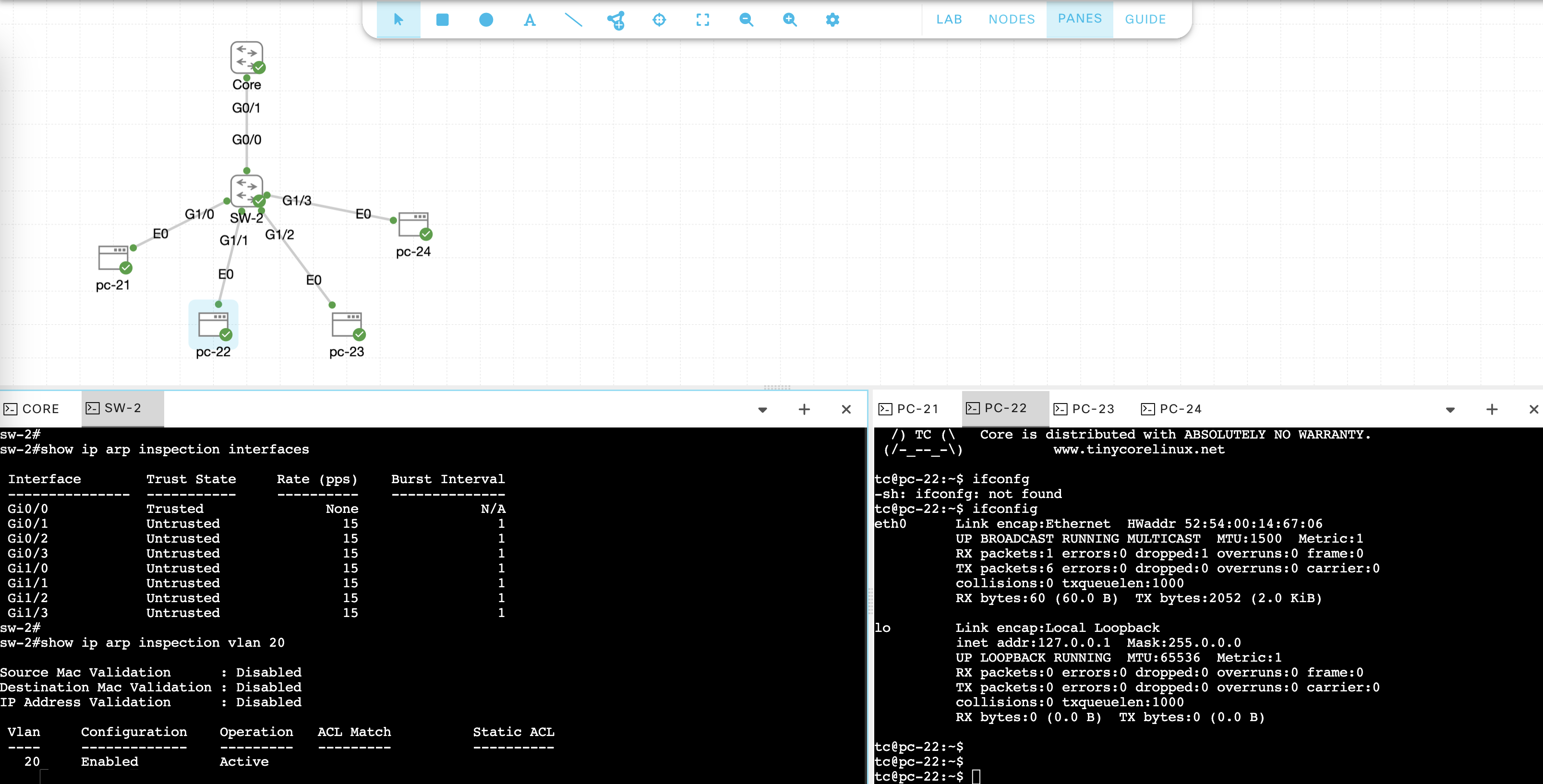
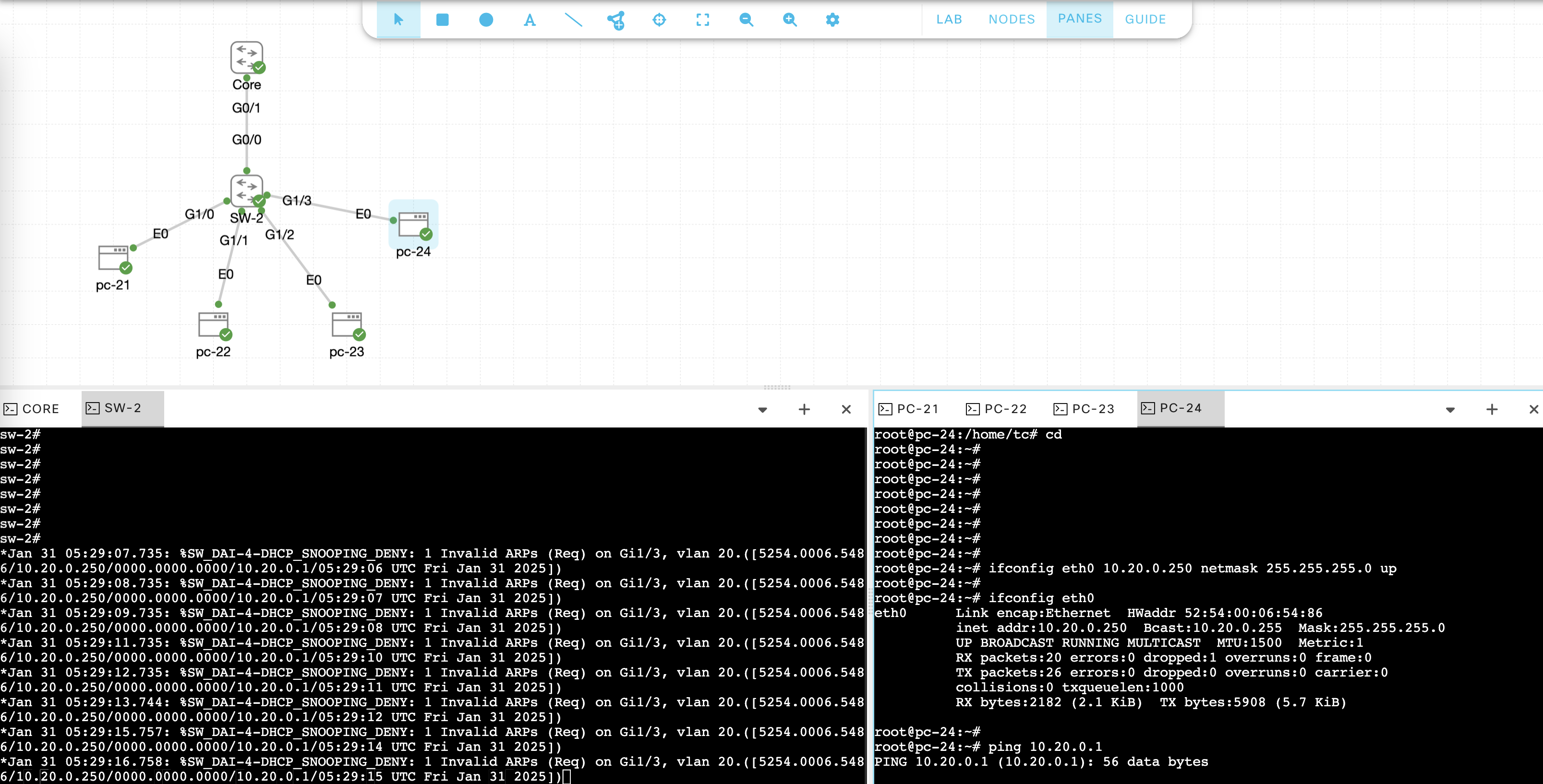
Dynamic ARP Inspection (DAI) prevents ARP spoofing attacks by verifying ARP packets against the DHCP Snooping binding table. It ensures that only legitimate ARP requests and replies are forwarded, blocking malicious attempts to intercept network traffic.
Verifying everything is working
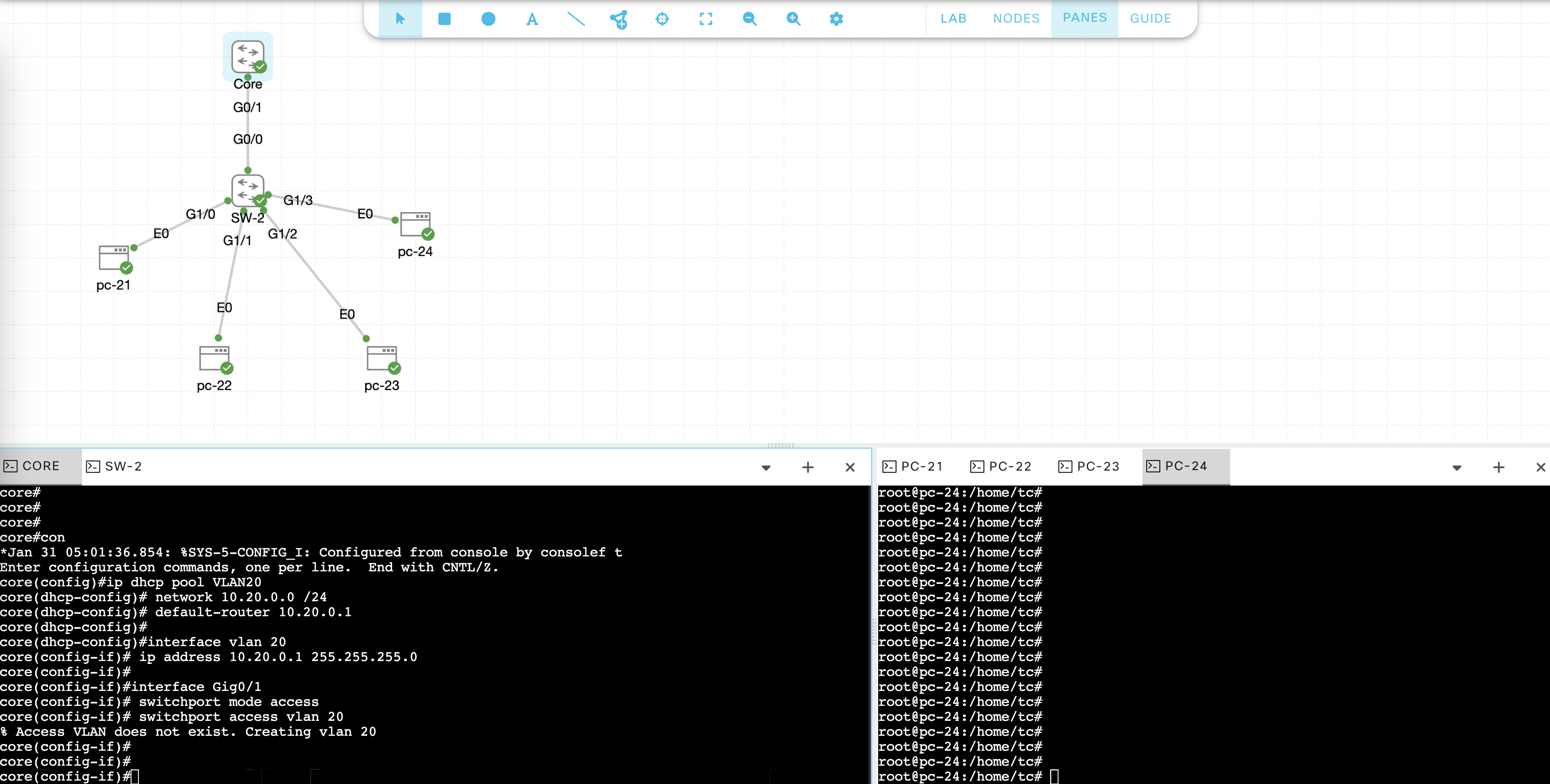
First we’ll create the DHCP Pool on Core Switch
1
2
3
4
5
6
7
8
9
10
11
12
ip dhcp pool VLAN20
network 10.20.0.0 /24
default-router 10.20.0.1
interface vlan 20
ip address 10.20.0.1 255.255.255.0
interface Gig0/1
switchport mode access
switchport access vlan 20
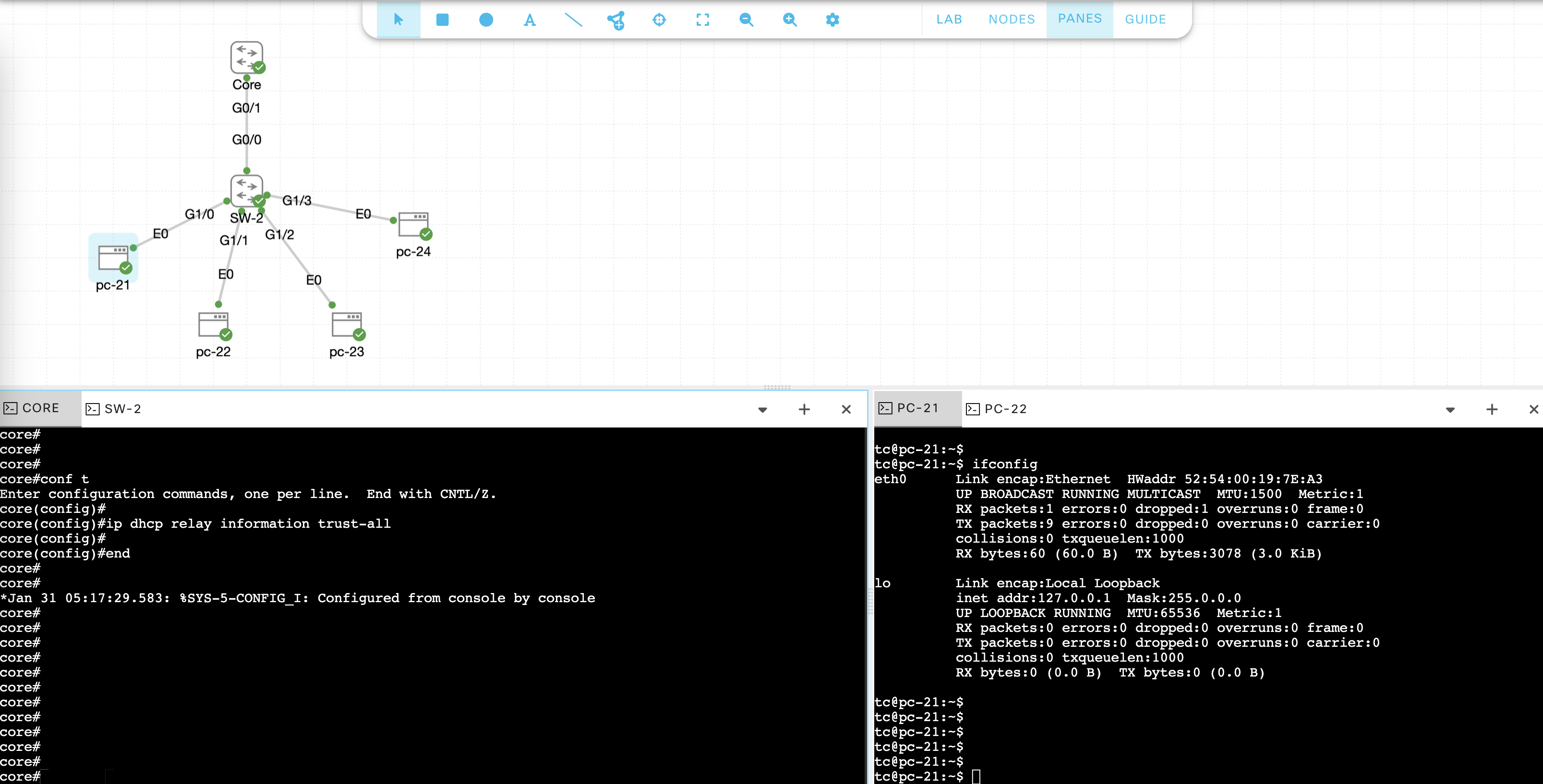
ip dhcp relay information trust-all
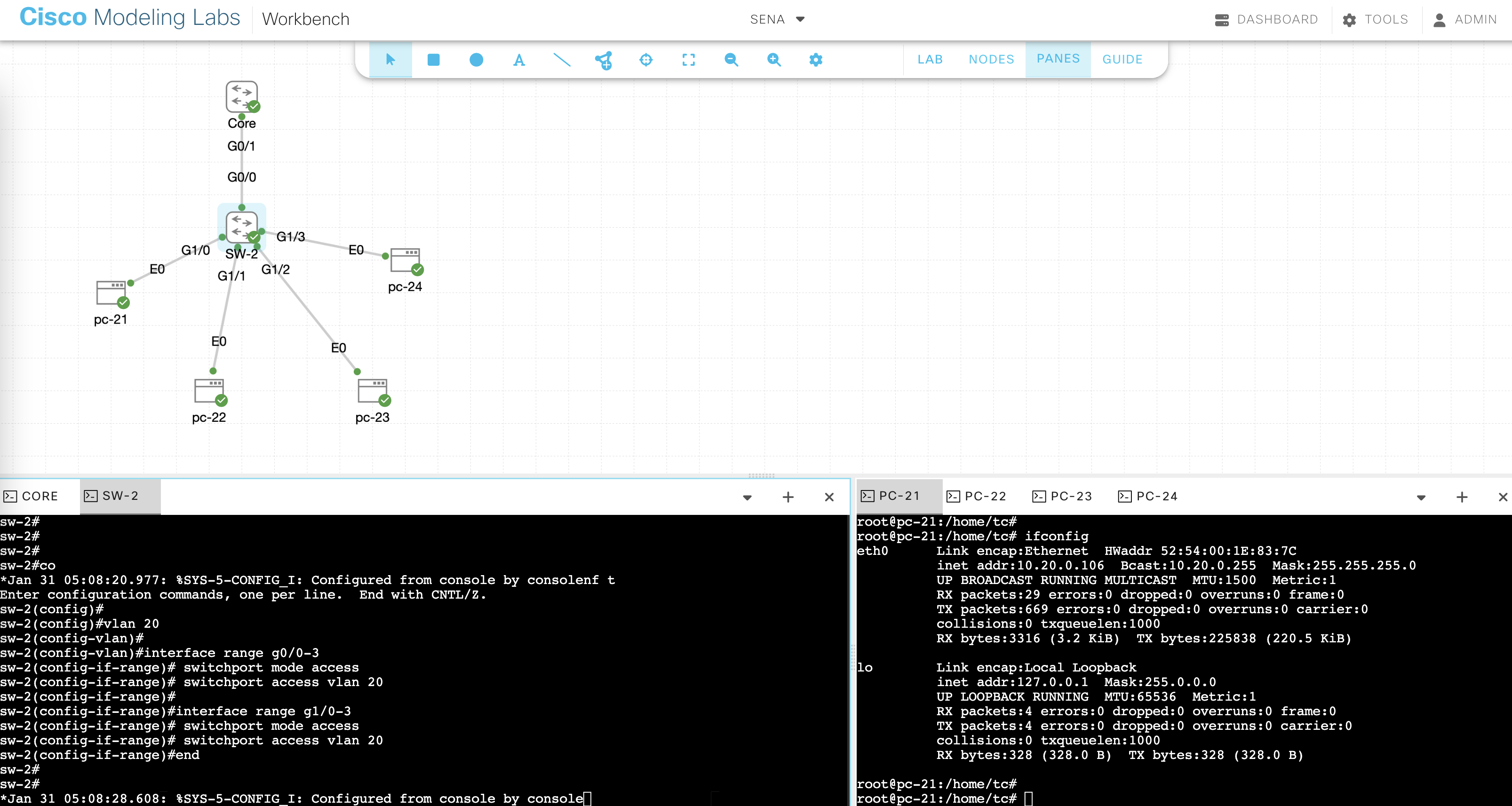
Then on SW-2, we’ll put all the ports on VLAN 20 so it can communicate with the Core Switch, and verify the Clients are getting IP Addresses
1
2
3
4
5
6
7
interface range g0/0-3
switchport mode access
switchport access vlan 20
interface range g1/0-3
switchport mode access
switchport access vlan 20
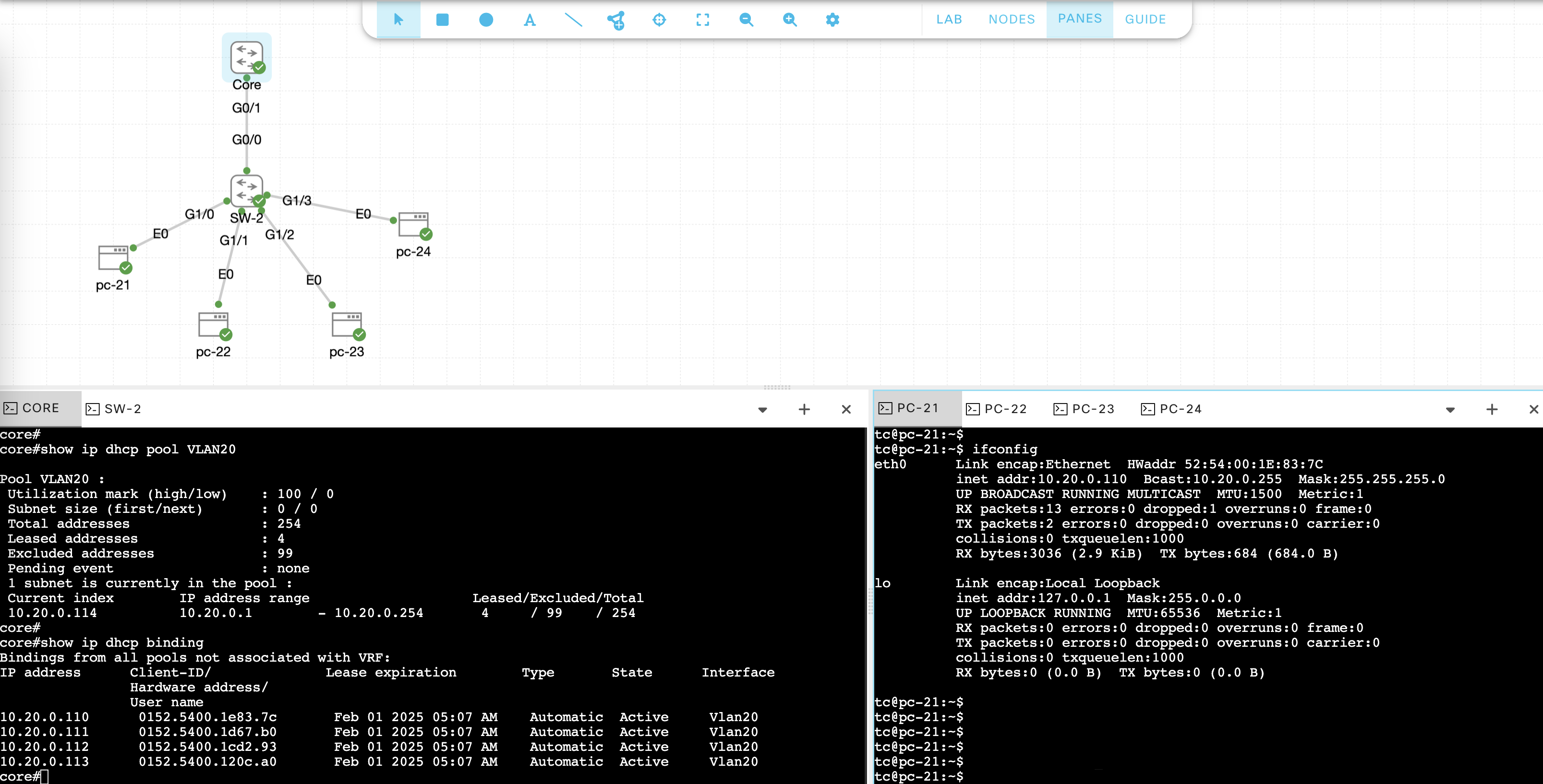
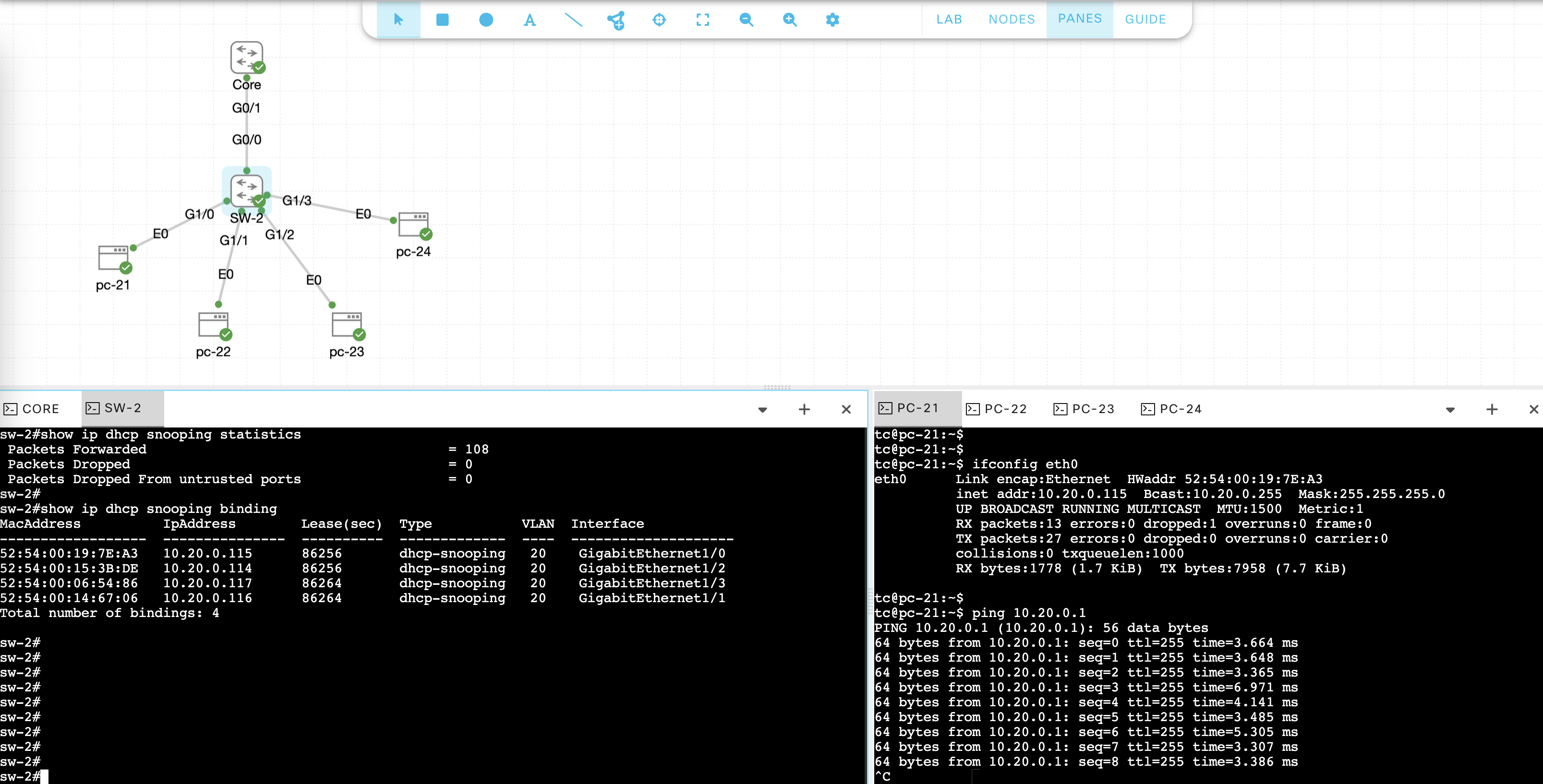
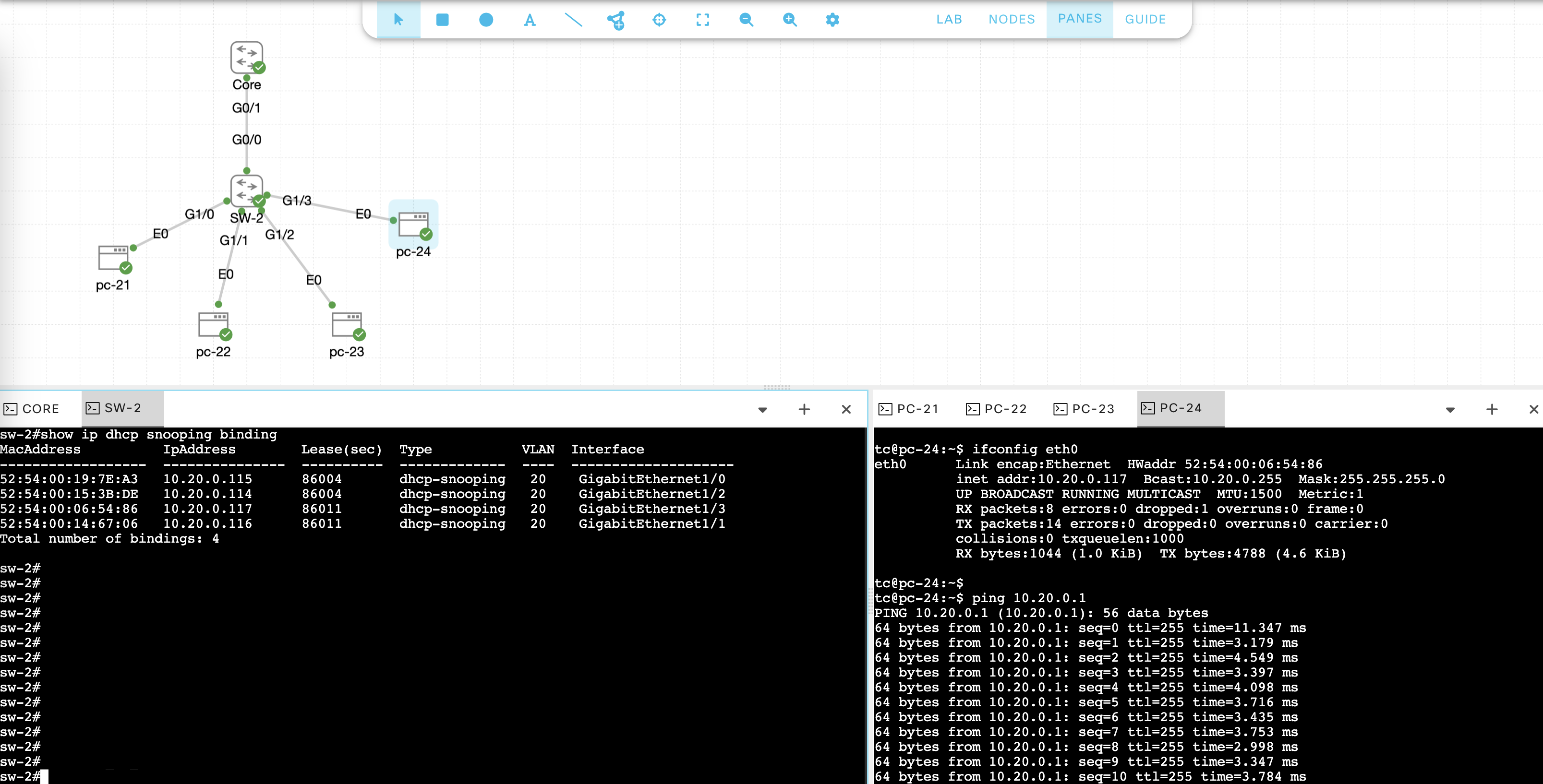
Verify Core is giving out IP Addresses with “show ip dhcp binding”
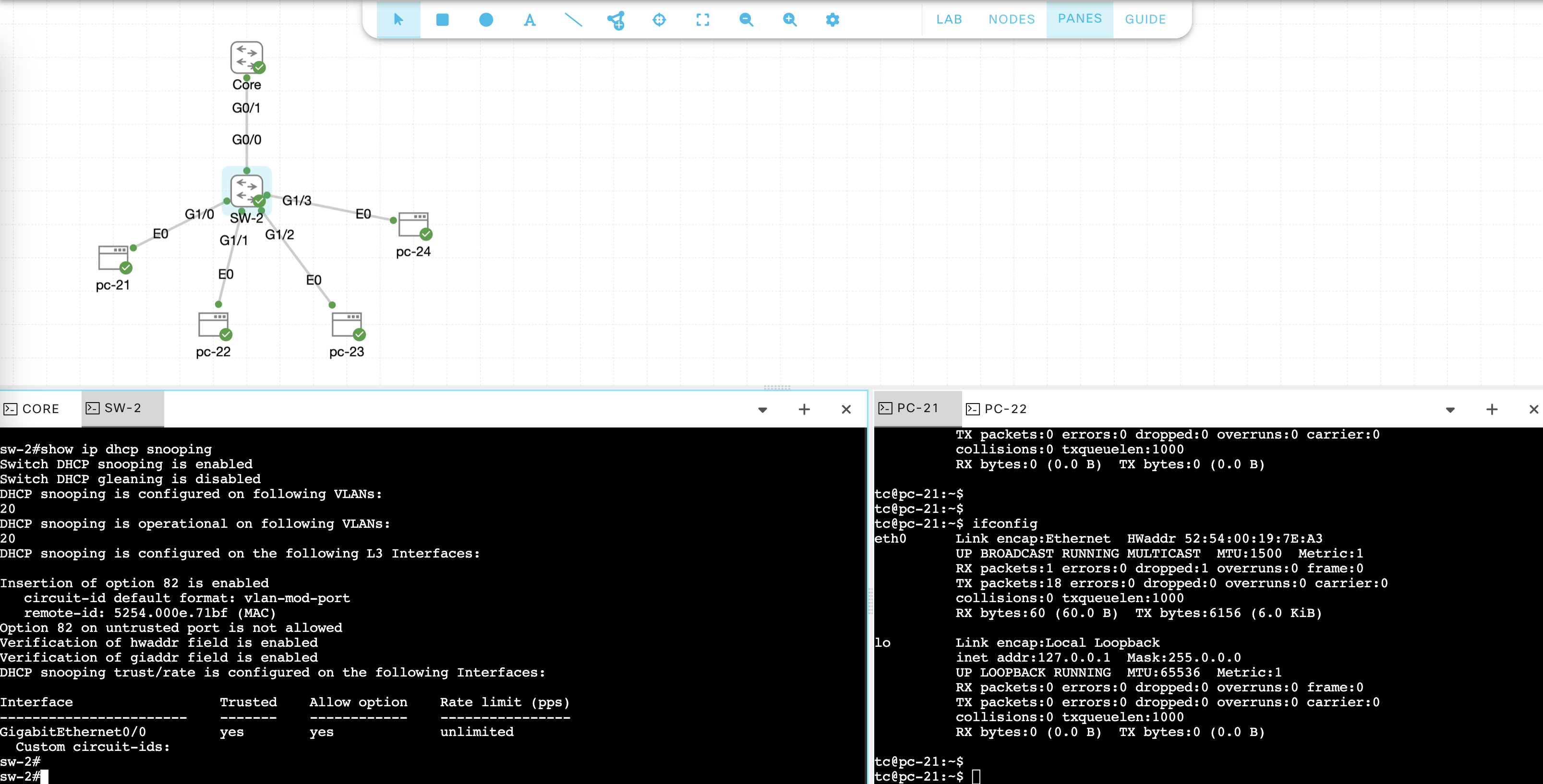
Enabling DHCP Snooping
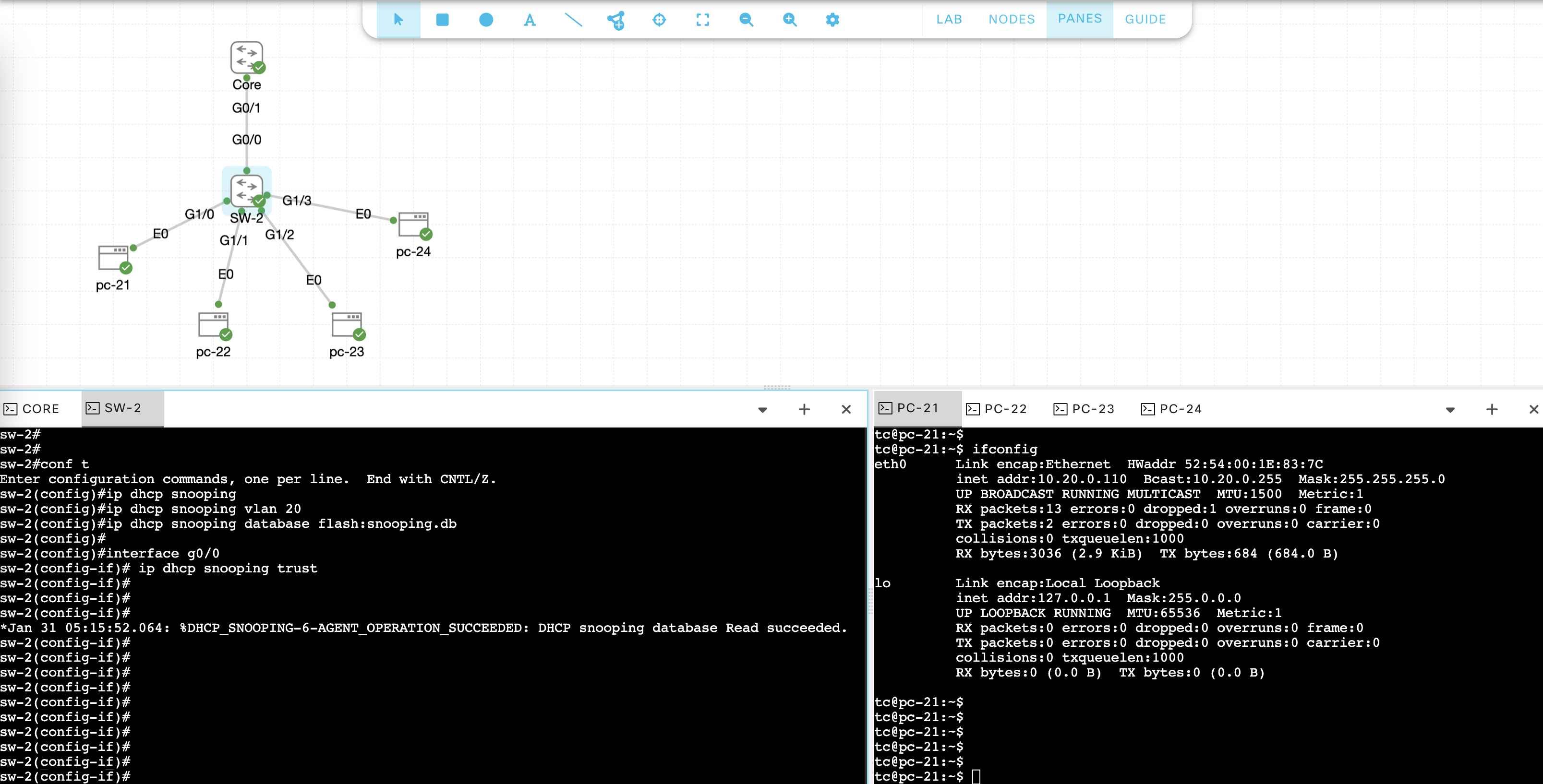
To enable DHCP Snooping on SW-2, run these commands, and then set G0/0 to be trusted interface
1
2
3
4
5
6
ip dhcp snooping
ip dhcp snooping vlan 20
ip dhcp snooping database flash:snooping.db
interface g0/0
ip dhcp snooping trust
And lastly, we need to run this command if the dhcp server is a cisco network device
1
ip dhcp relay information trust-all
Run “show ip dhcp snooping” to verify configuration
And run “show ip dhcp snooping binding” to see the binding records
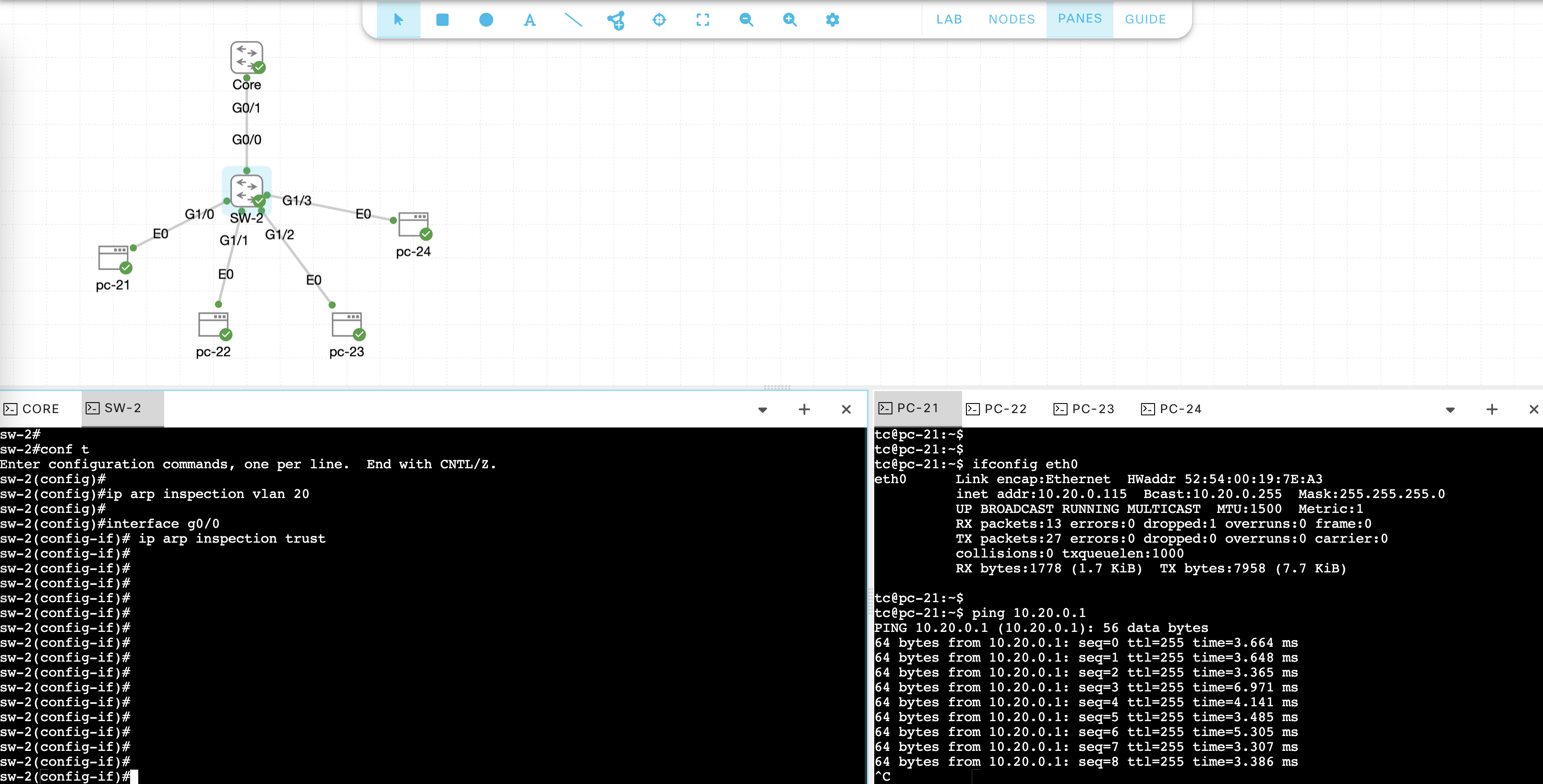
Enabling Dynamic ARP Inspection
To enable DAI, run these commands on SW-2
1
2
3
4
ip arp inspection vlan 20
interface g0/0
ip arp inspection trust
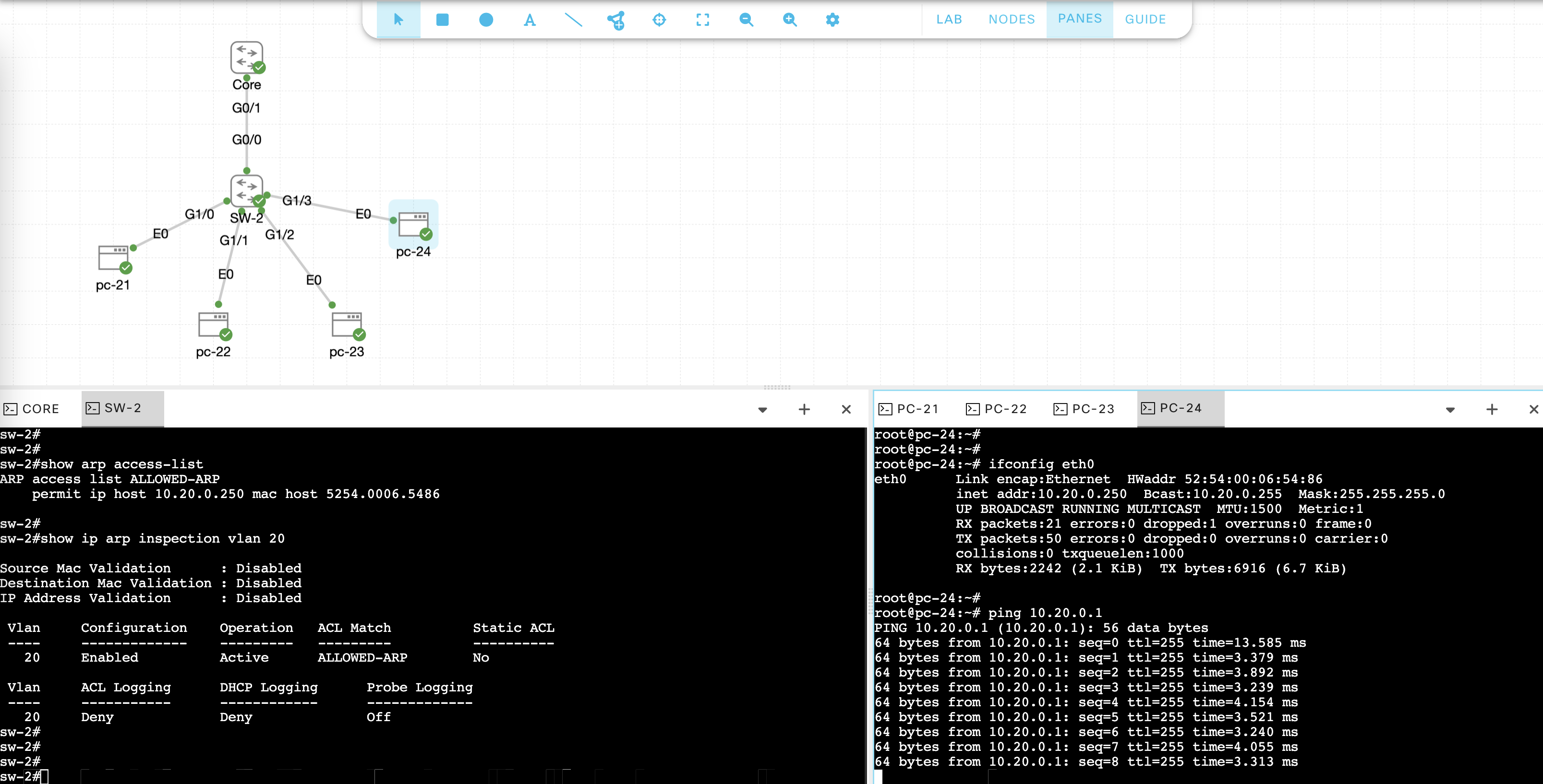
Run these commands to verify DAI configurations
And now only Clients with existing binding records will be allowed to access the network
If we try accessing network with statically configured IP Address, we will be denied access
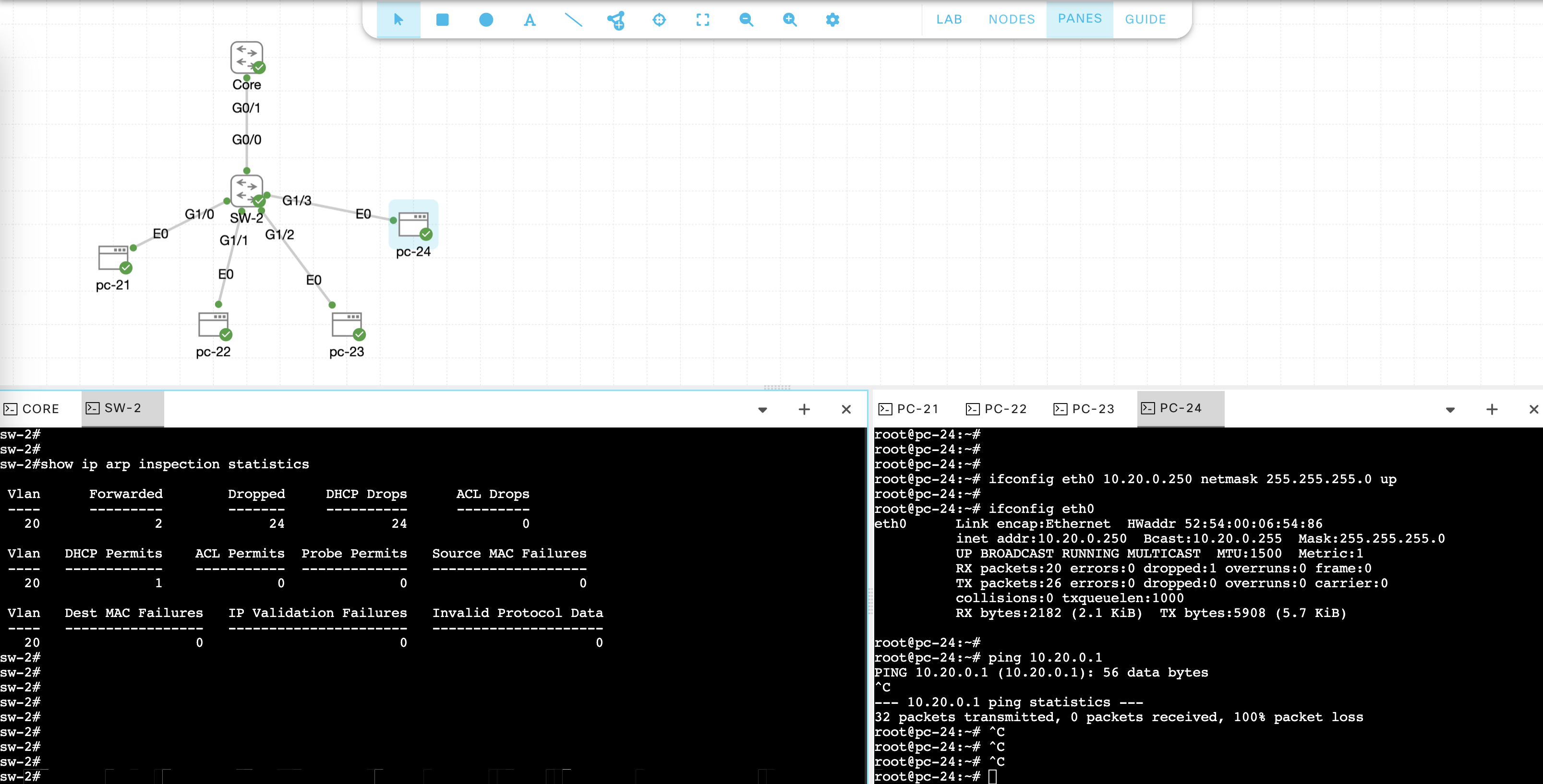
And running “show ip arp inspection statistics” will show the drops counter going up
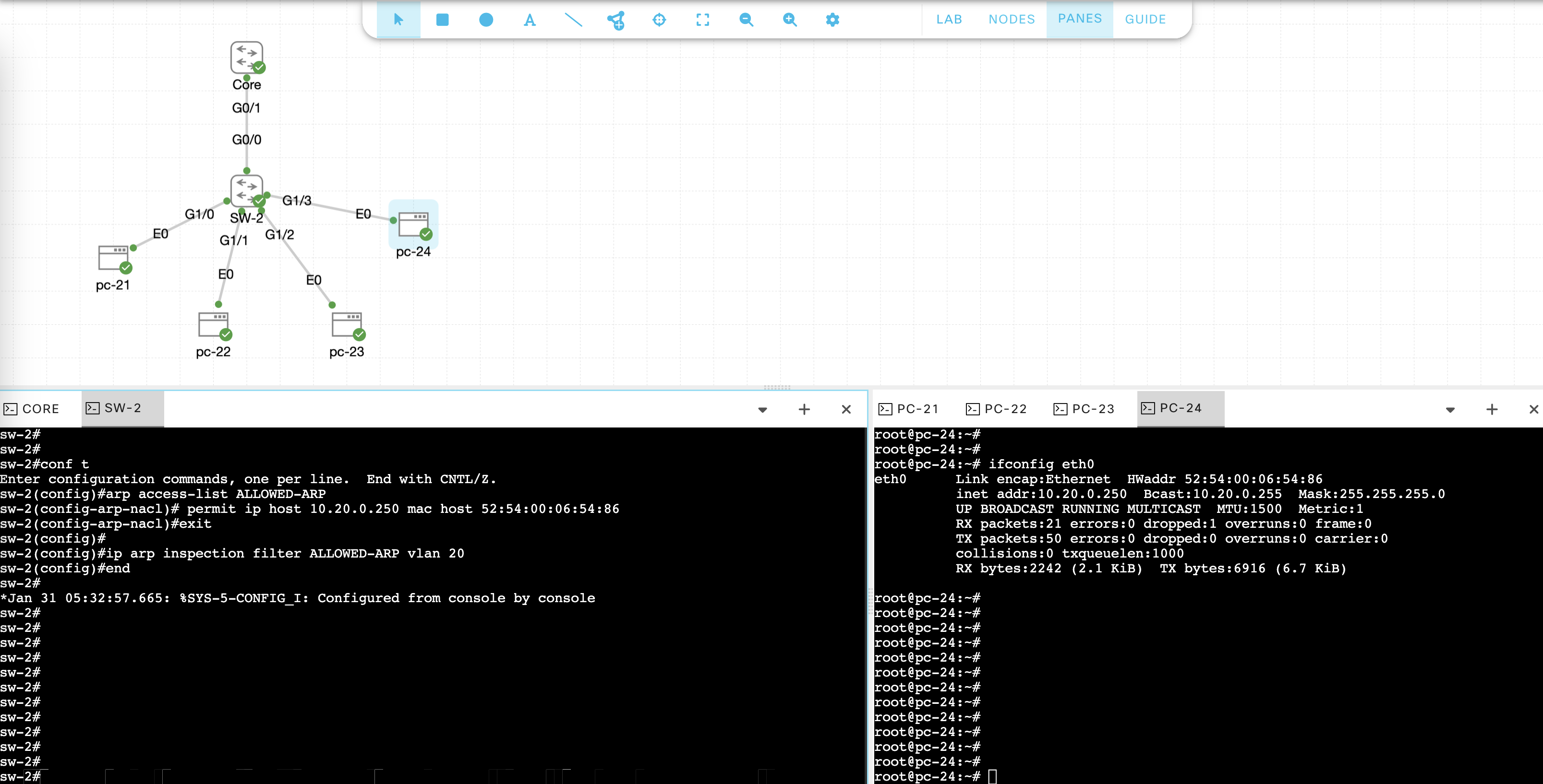
To add a statically configured IP Address, we can whitelist them with ARP ACL
1
2
3
4
arp access-list ALLOWED-ARP
permit ip host 10.20.0.250 mac host 52:54:00:06:54:86
ip arp inspection filter ALLOWED-ARP vlan 20
And now on top of the DHCP Snooping table, access are also given to the statically configured MAC Addresses on the ARP ACL