Cisco Expressway Mobile Remote Access (MRA)
Mobile and Remote Access (MRA) allows remote and mobile workers to securely access the corporate collaboration services without the need for a VPN. It facilitates secure connections for voice, video, instant messaging, and presence directly through the Expressway edge and core servers, enabling seamless communication as if users were within the corporate network.
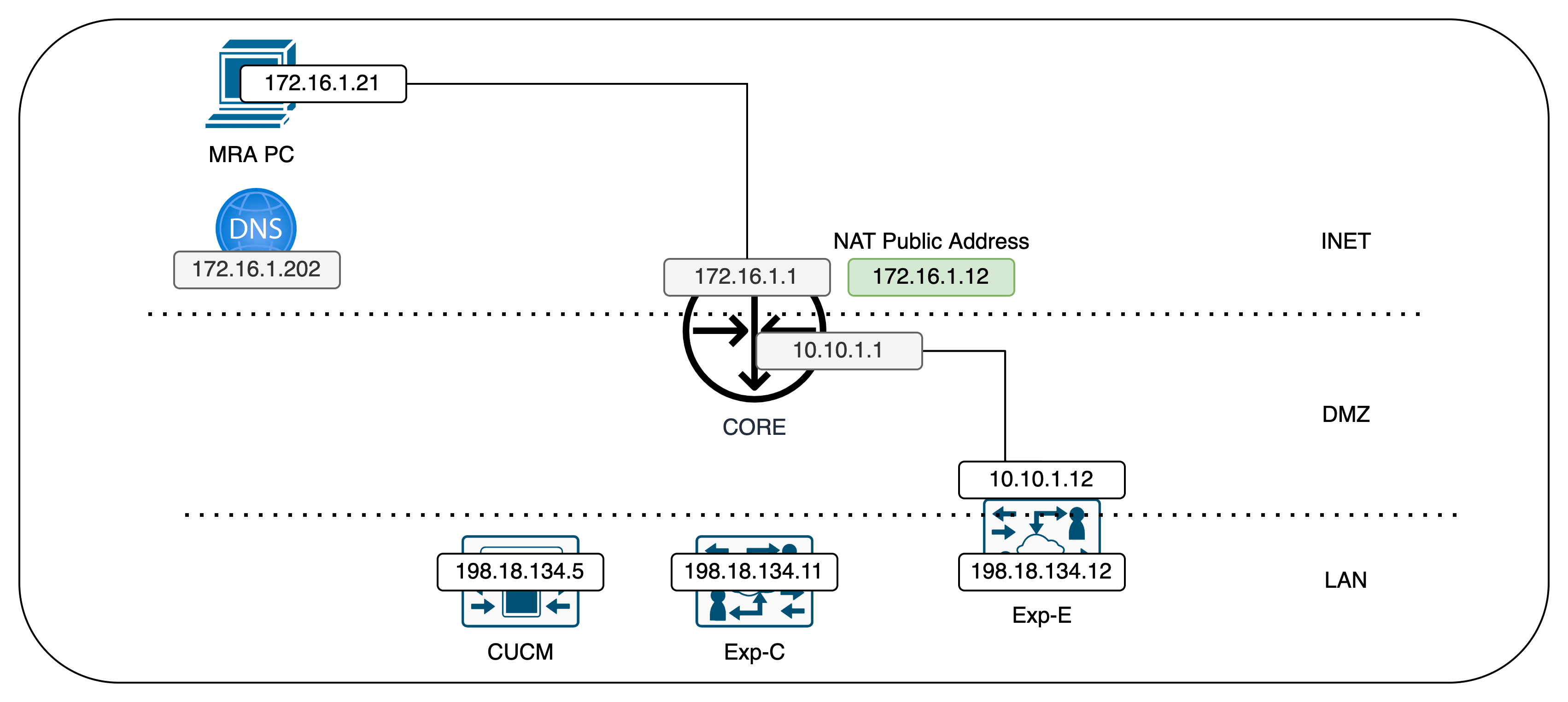
Here’s the topology for this MRA deployment
Installing Expressways
First deploy 2 Expressways VMs, one for Expressway Core and the other for Expressway Edge
Run the CLI configuration and the web UI should be accessible right after
Expressway Core
On the Expressway Core VM, select Expressway-C and for the service select MRA
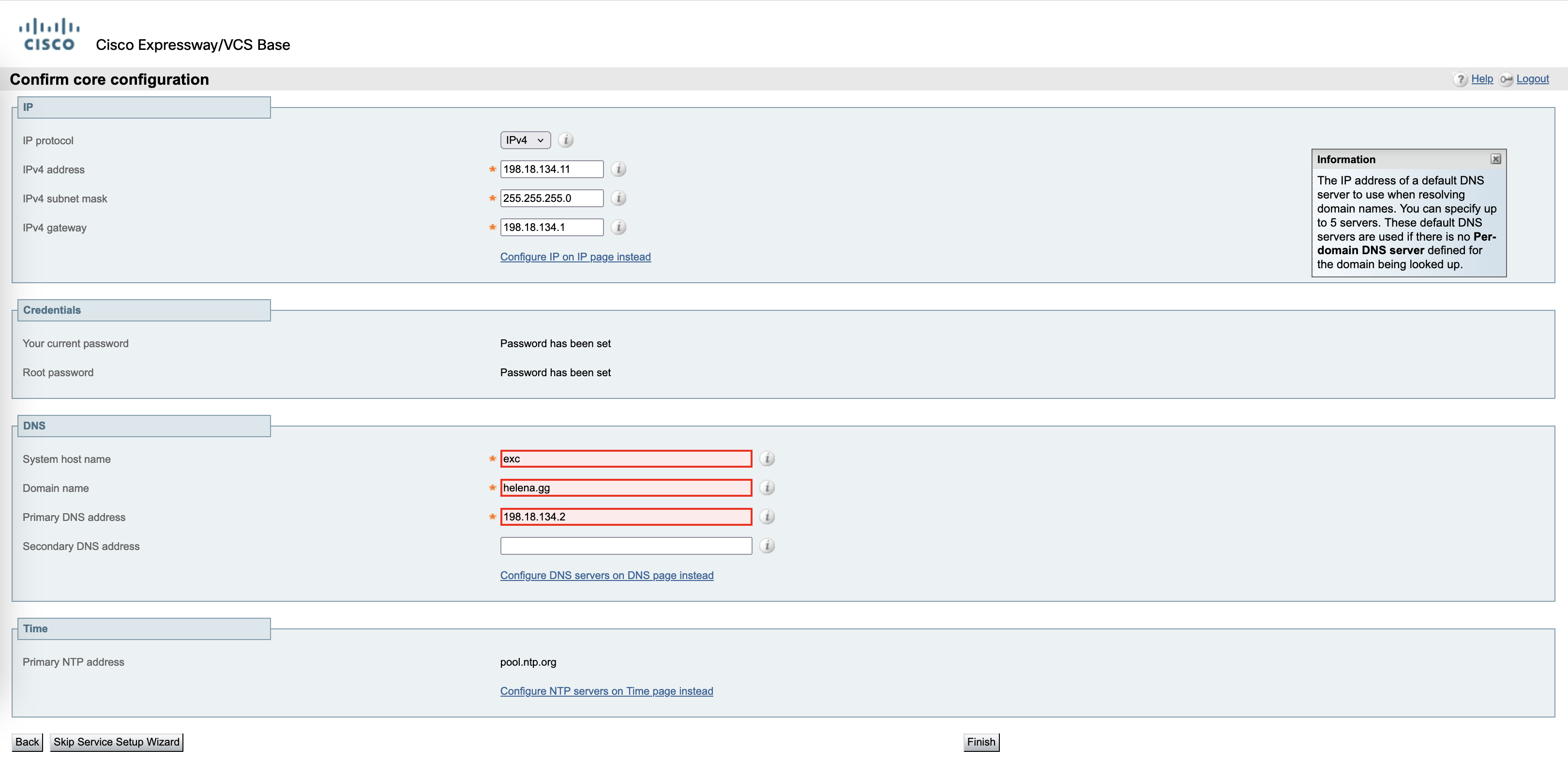
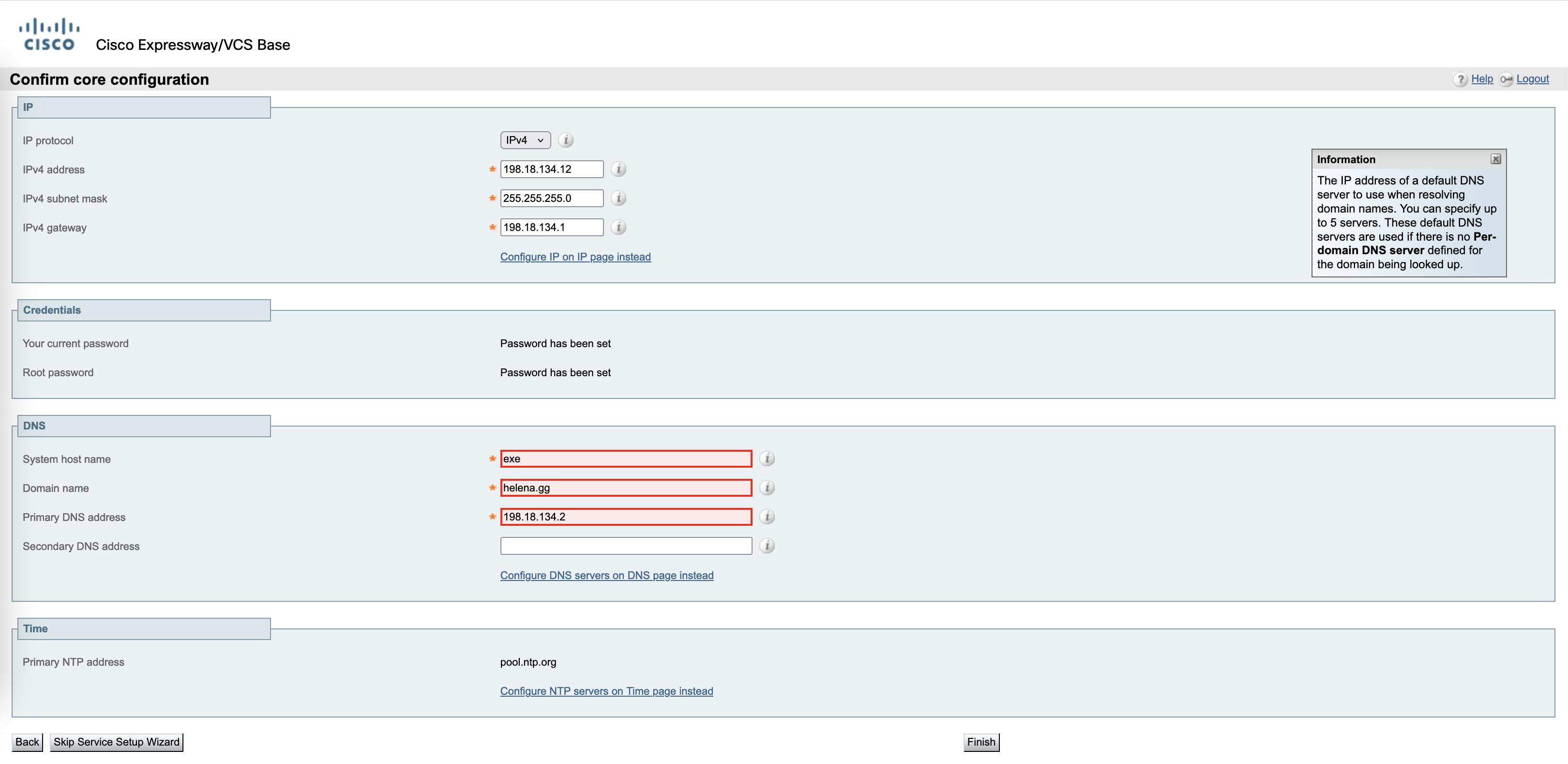
Configure the IP address, credentials, DNS and NTP
And that should do it for the Exp-C configuration
Expressway Edge
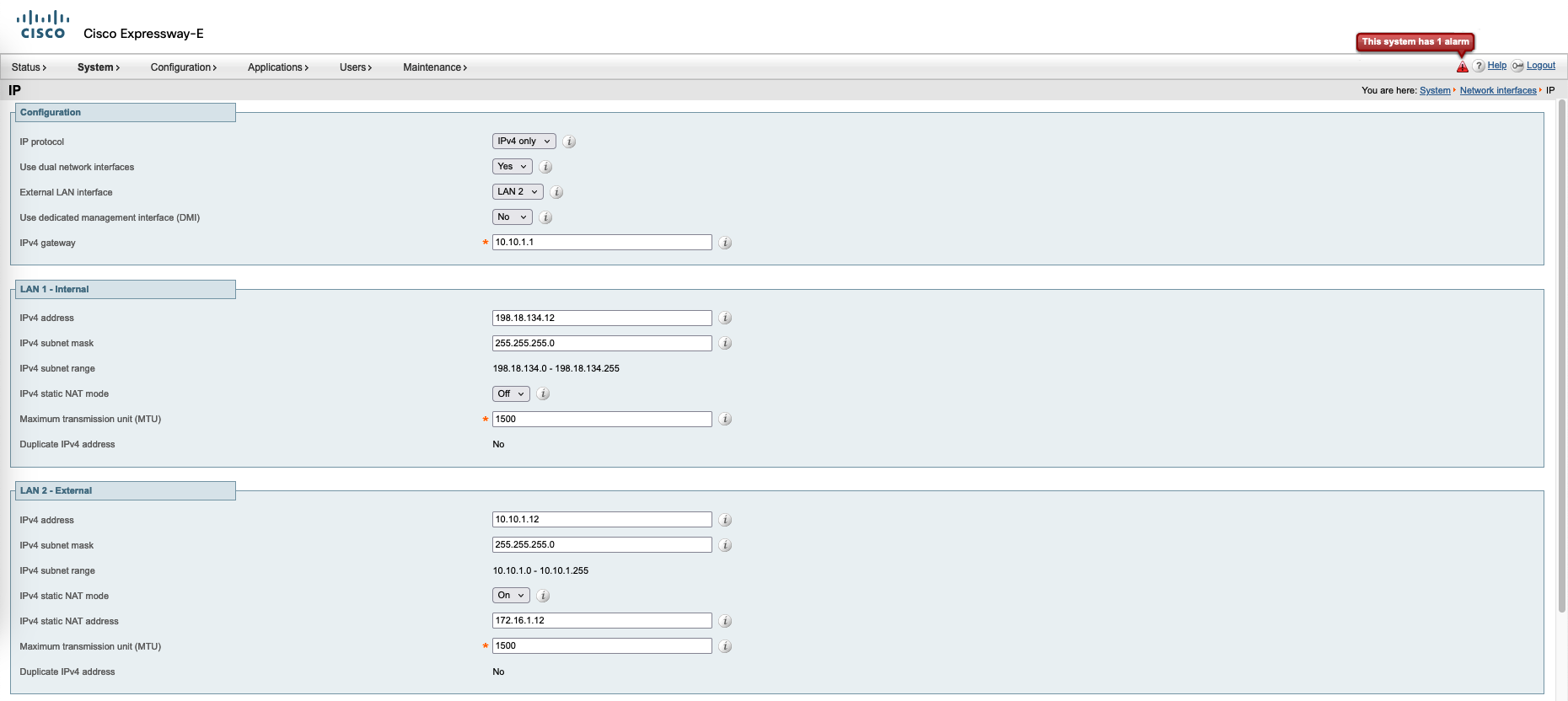
For the Edge, select Expressway-E at the beginning and the rest should be roughly the same
Because Exp-E uses two interfaces, go to System » Network interfaces and configure the Internal and External interfaces
Configuring CUCM Integration
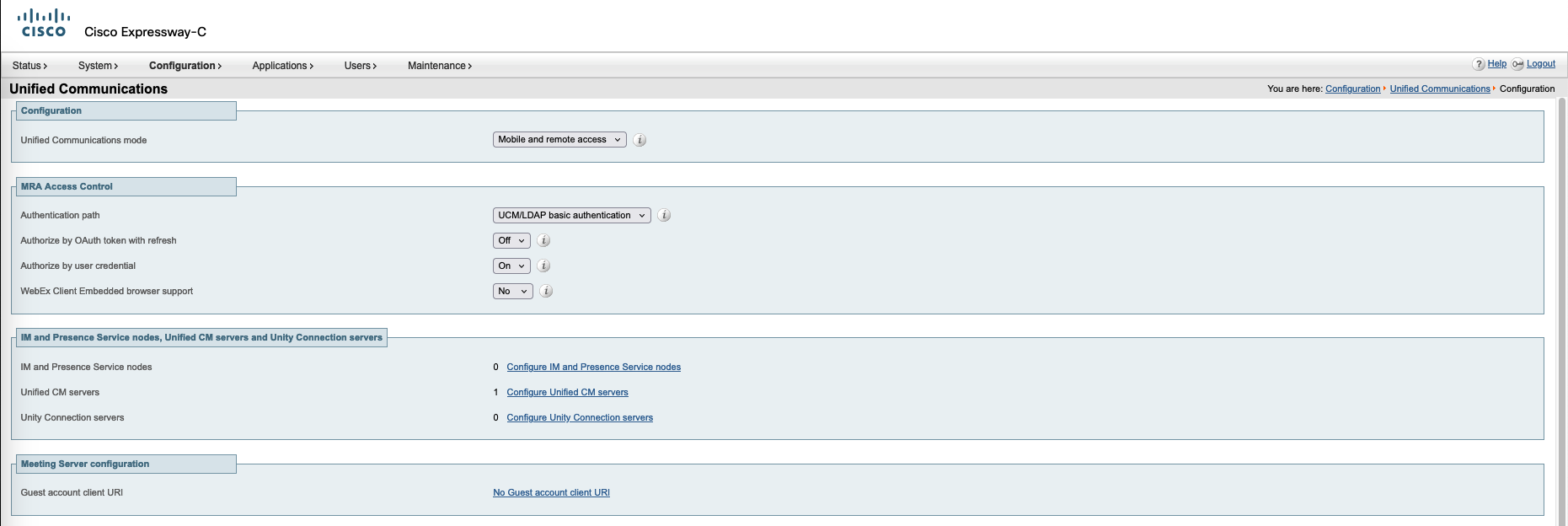
Expressway C
On Core, go to Configuration » Unified Communications, select the mode to be MRA and configure the authentication method
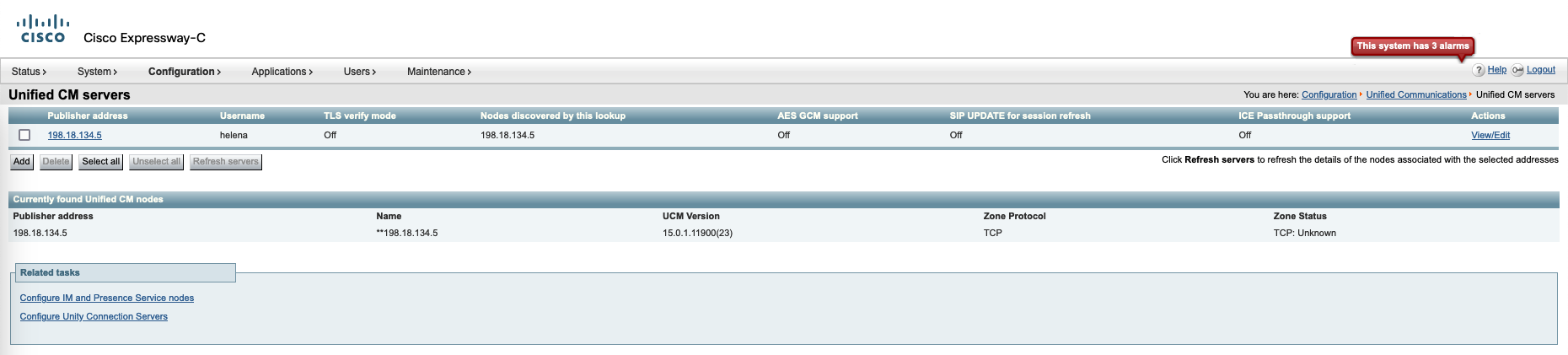
Next add the CUCM servers
Expressway E
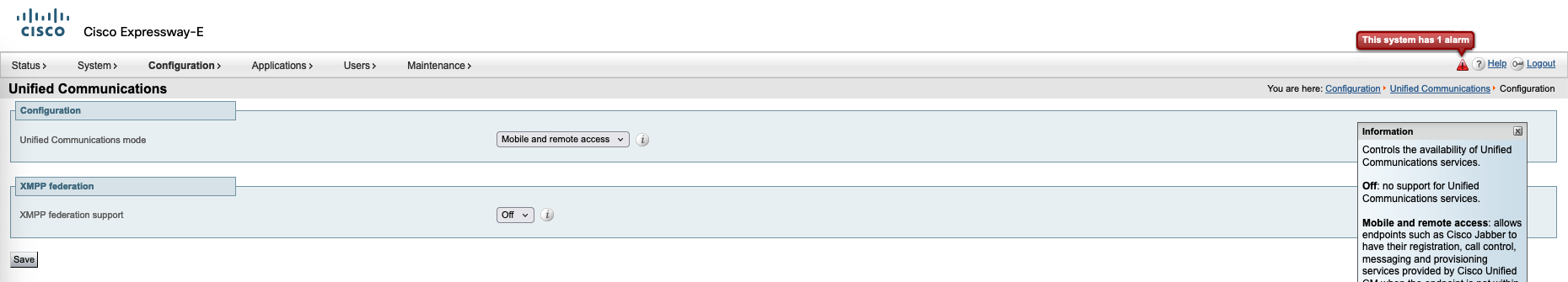
On Edge, go to Configuration » Unified Communications and select the MRA
Configuring Domains
Expressway C
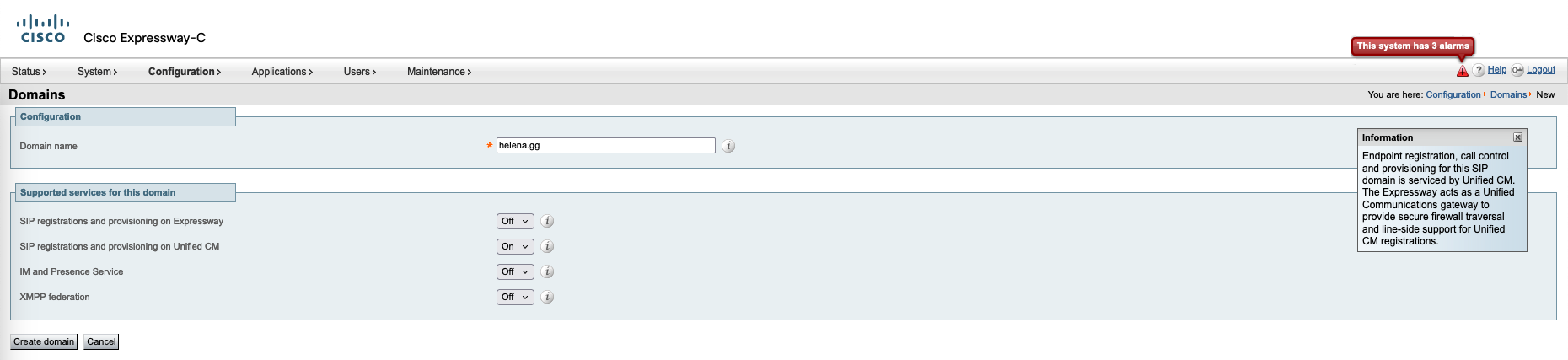
On Core, go to Configuration » Domains, input the domain name the supported services
Dealing with Certificates
Expressway C
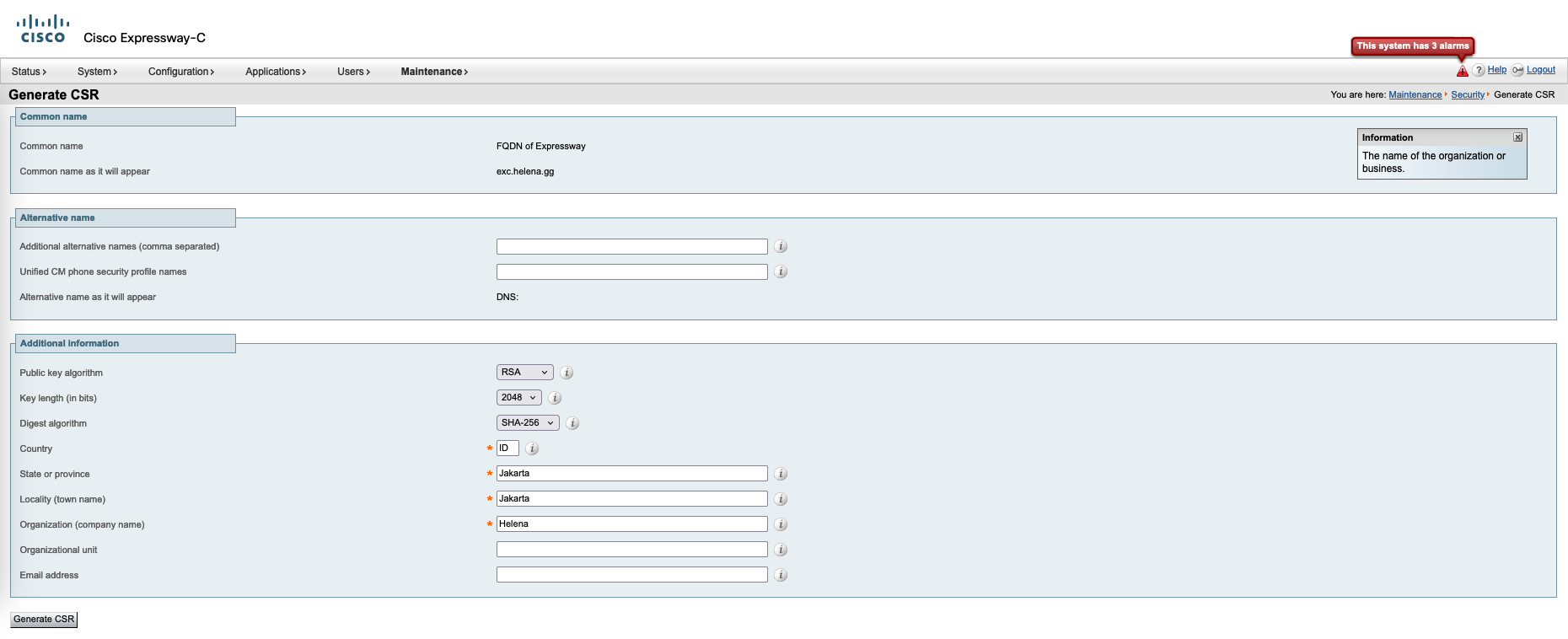
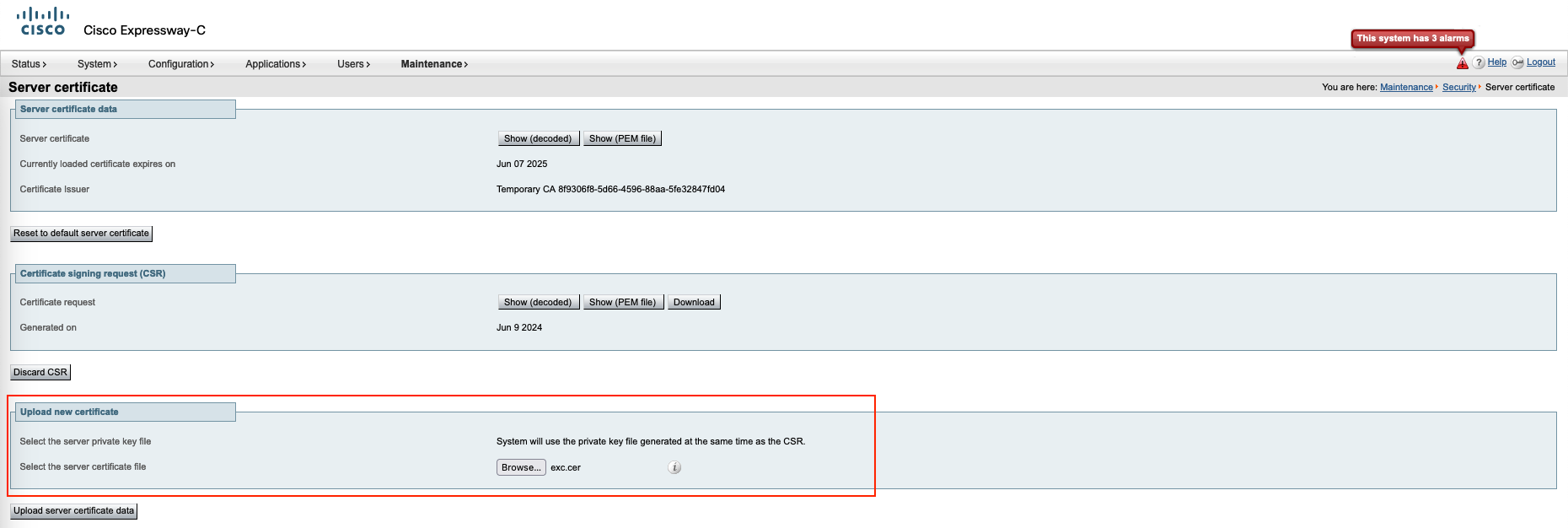
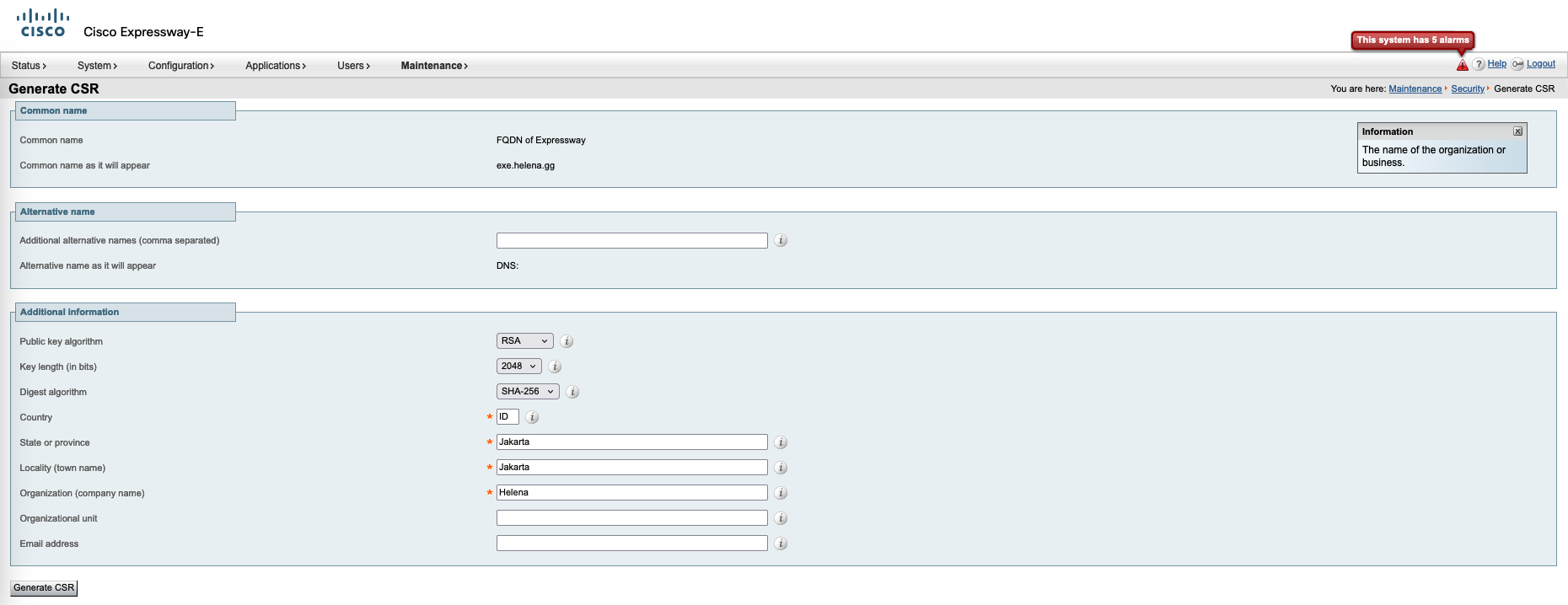
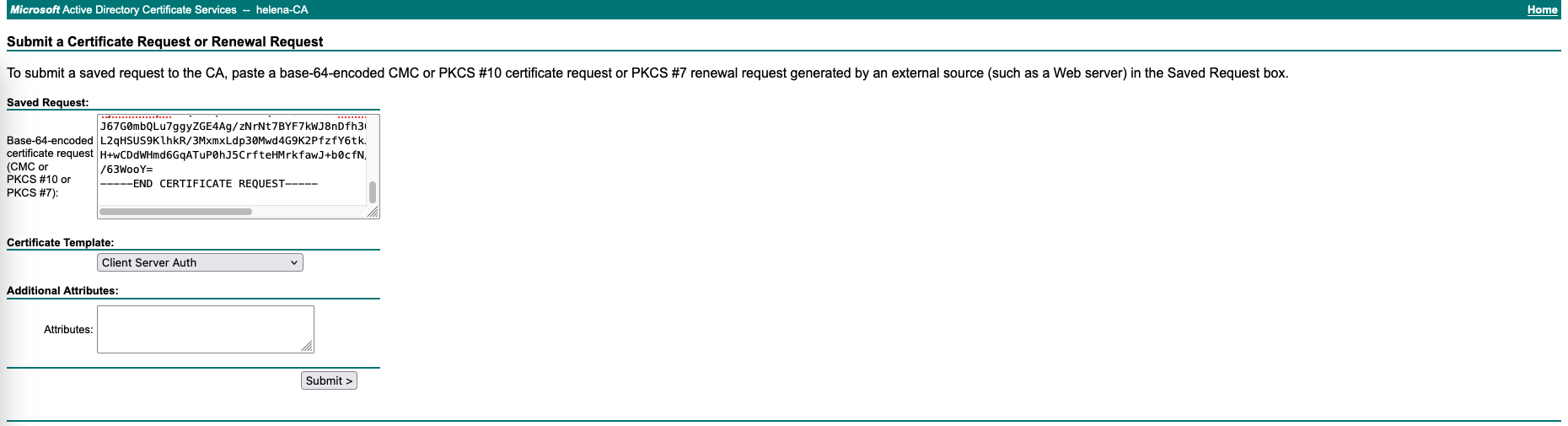
On Core, go to Maintenance » Security » Server certificate, select generate CSR
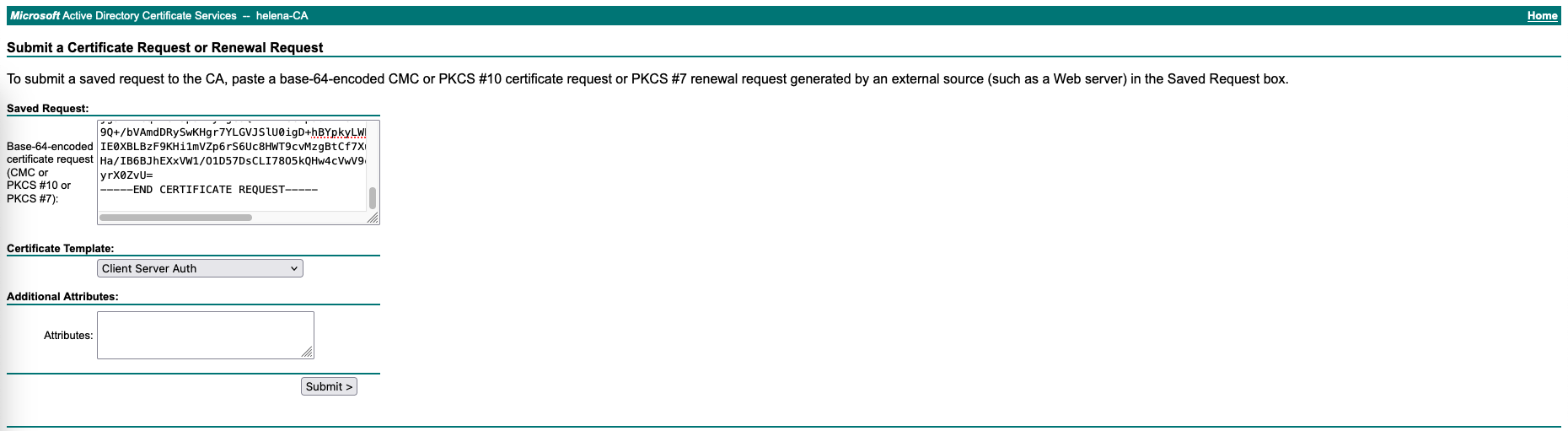
Then sign the CSR on the Certificate Authority using Client Server Auth Template
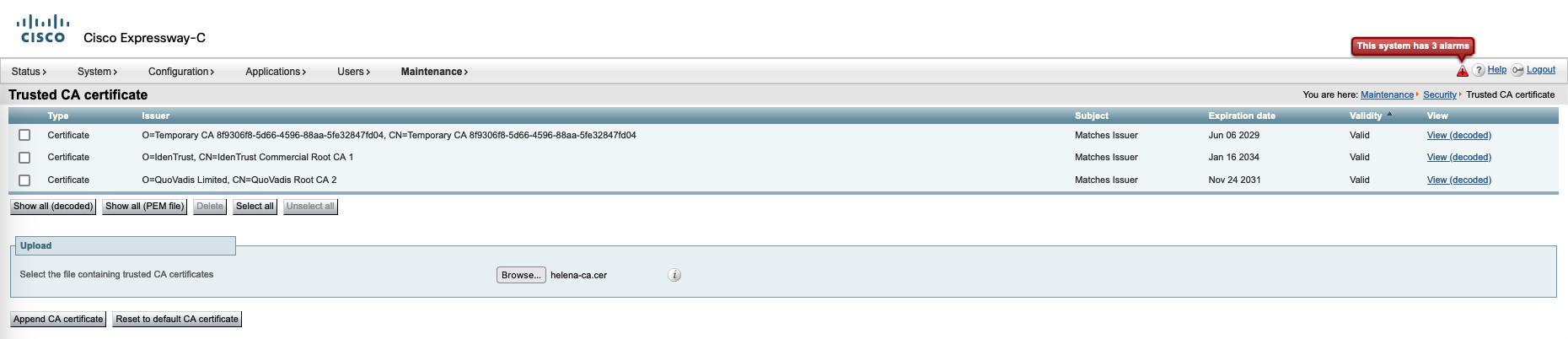
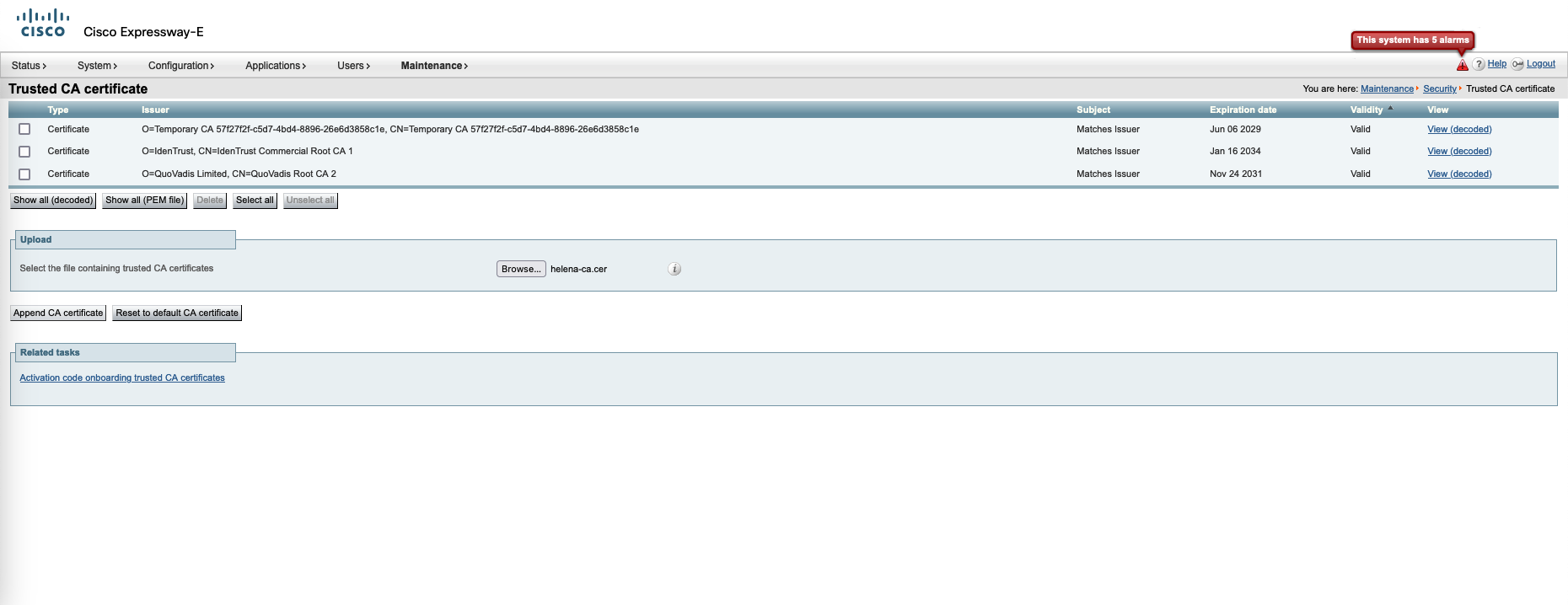
Next add the Root CA Certificate on to the Trusted CA Certificates
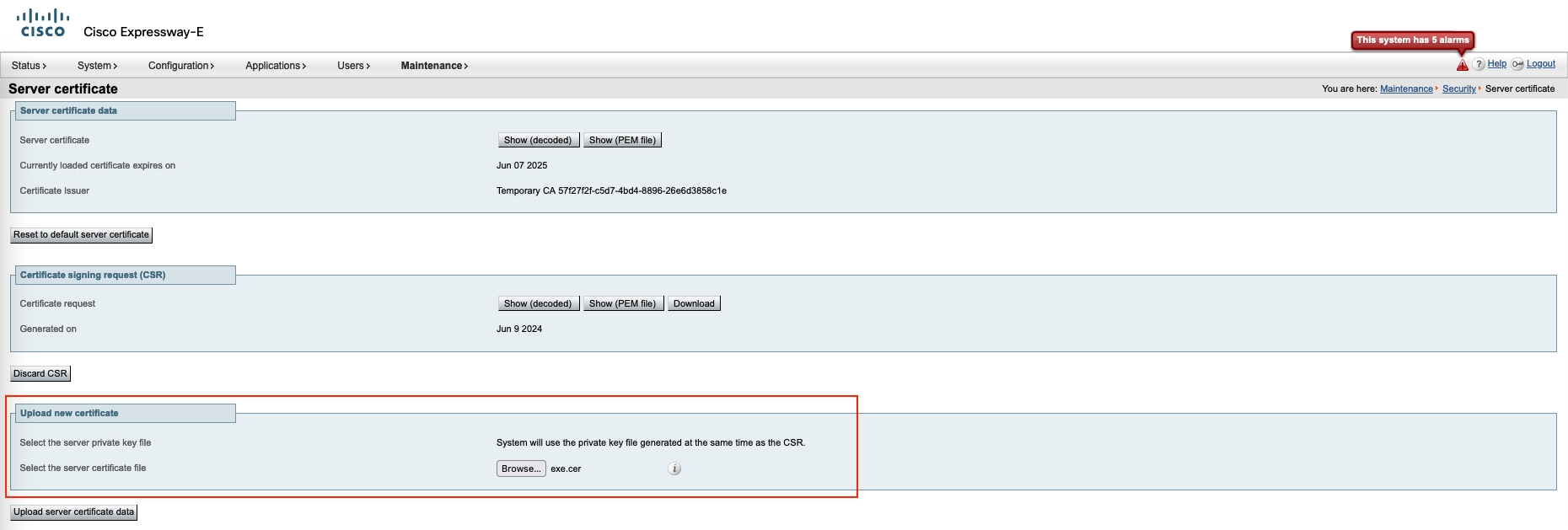
Back to Server certificate, finish the CSR by uploading the signed certificate
Expressway E
Repeat the process for the Edge
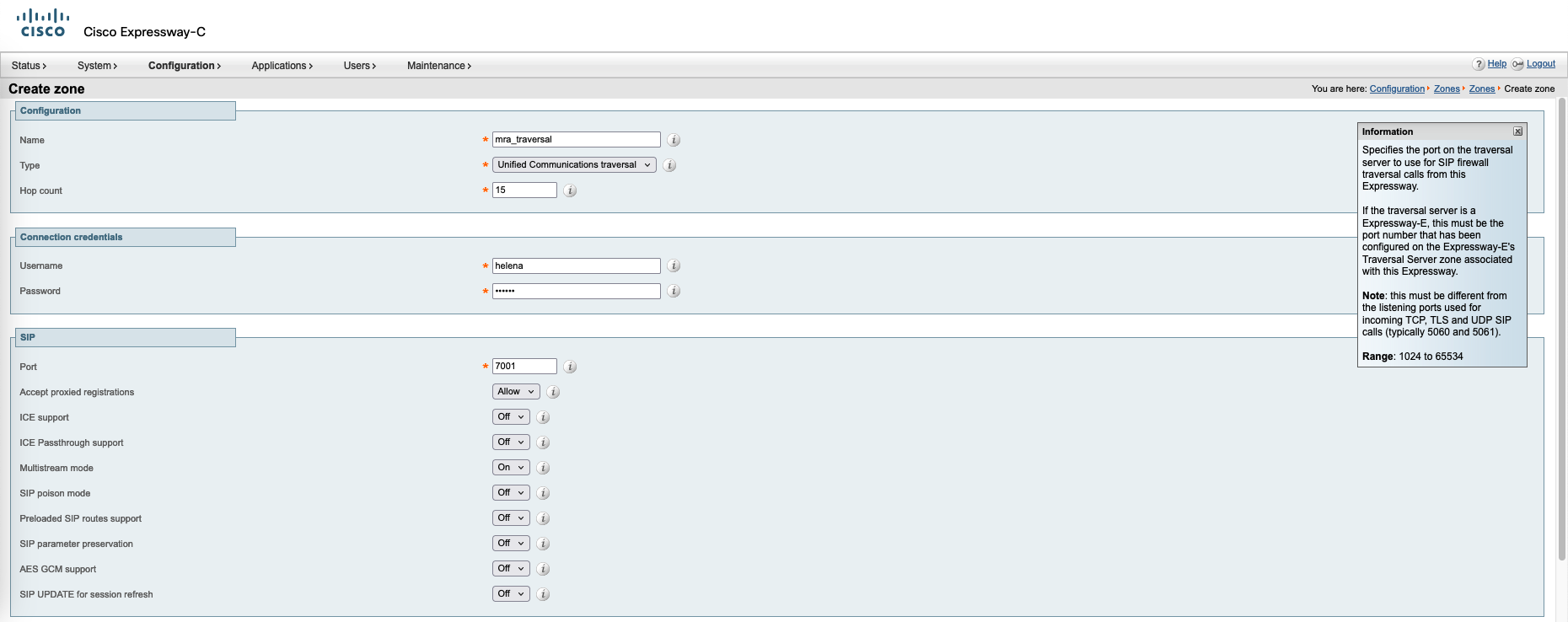
Creating Zone
Expressway E
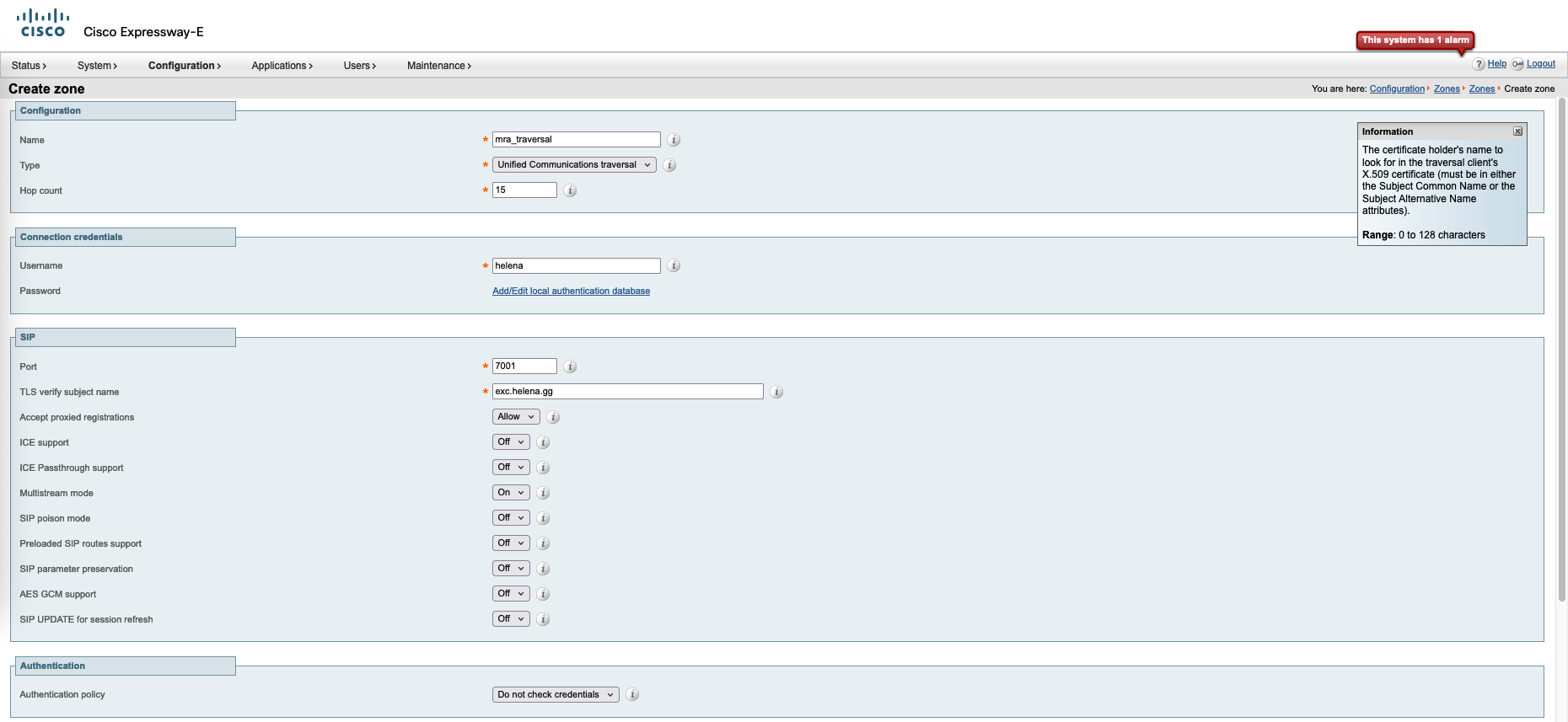
On the Edge, go to Configuration » Zones, create the traversal zone pointing to the Core
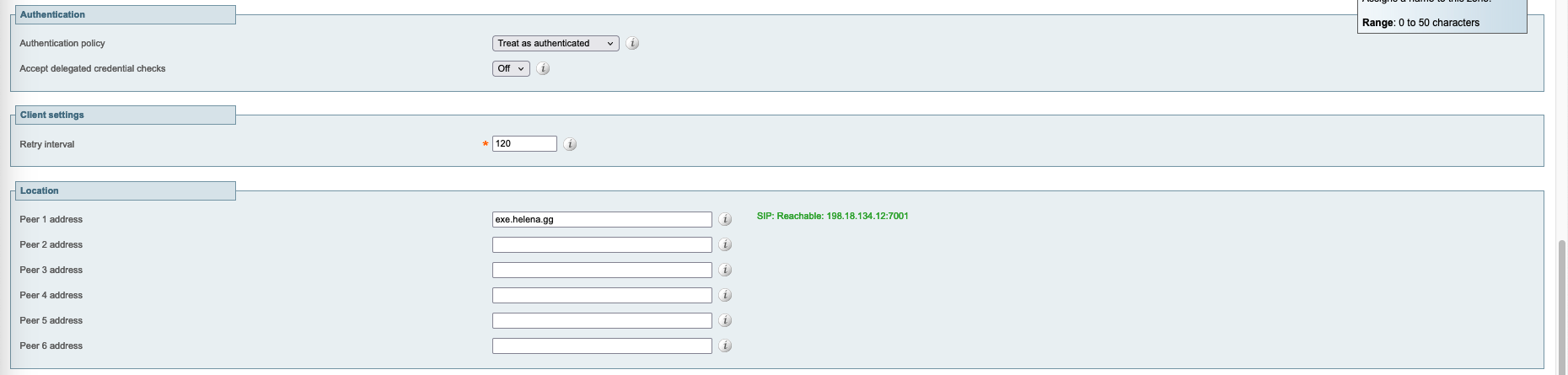
Expressway C
On the Core, enter the same credential and port as configured on the Edge
And add the Edge’s address as the peer
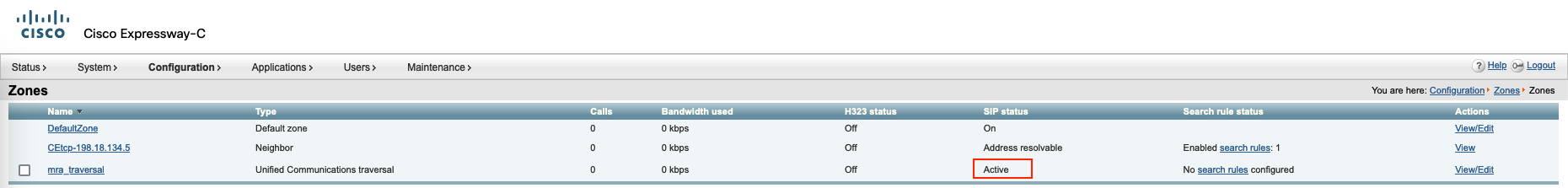
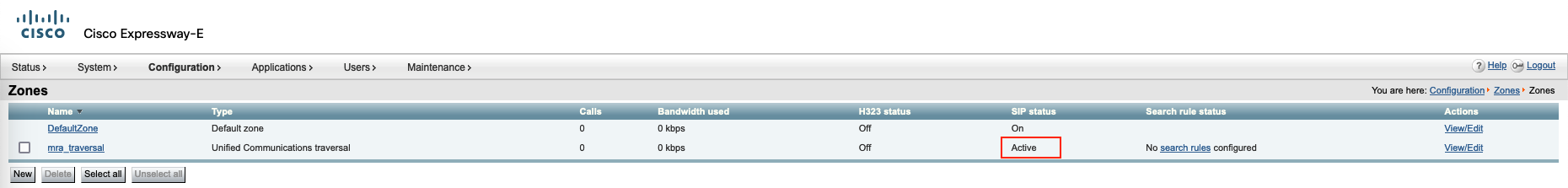
Now we can see the traversal zone is active
Expressway C
Expressway E
Configuring DNS Srv
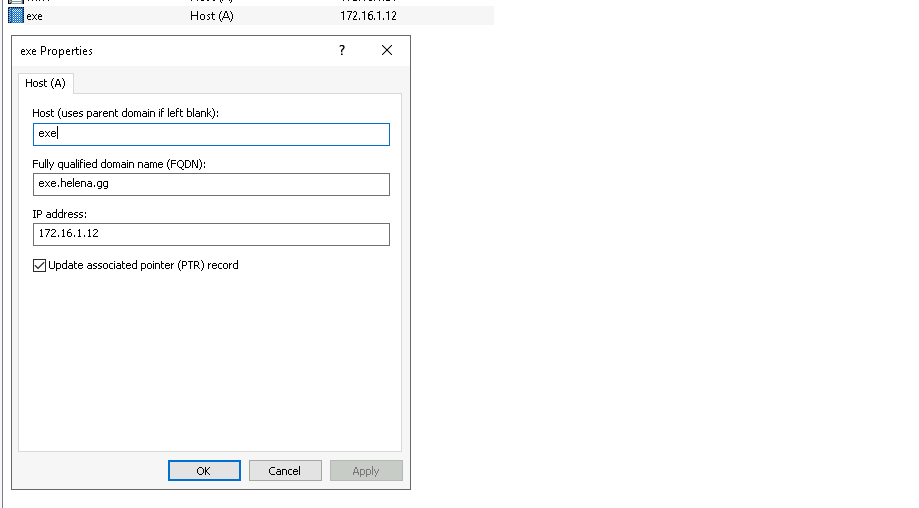
On the internet, configure the hostname to point to the Edge External NAT IP Address
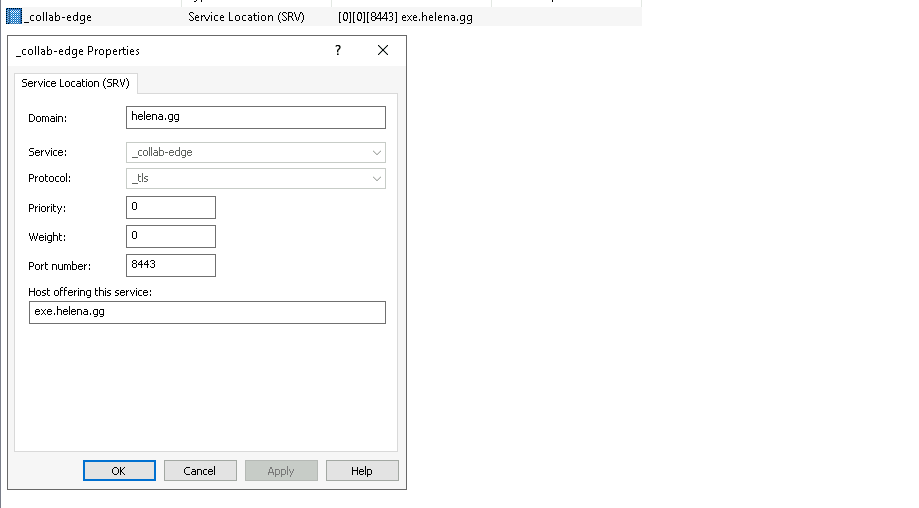
Then create a DNS Srv _collab-edge that points to the Edge’s FQDN
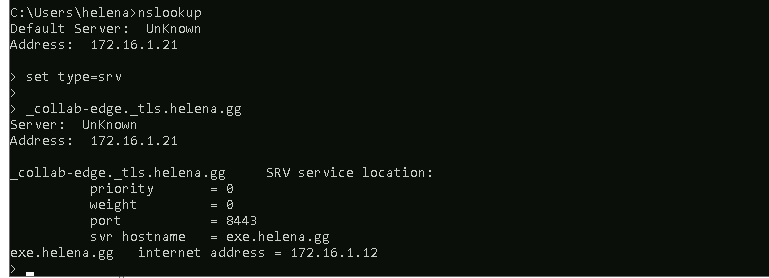
Run a nslookup to validate the configuration
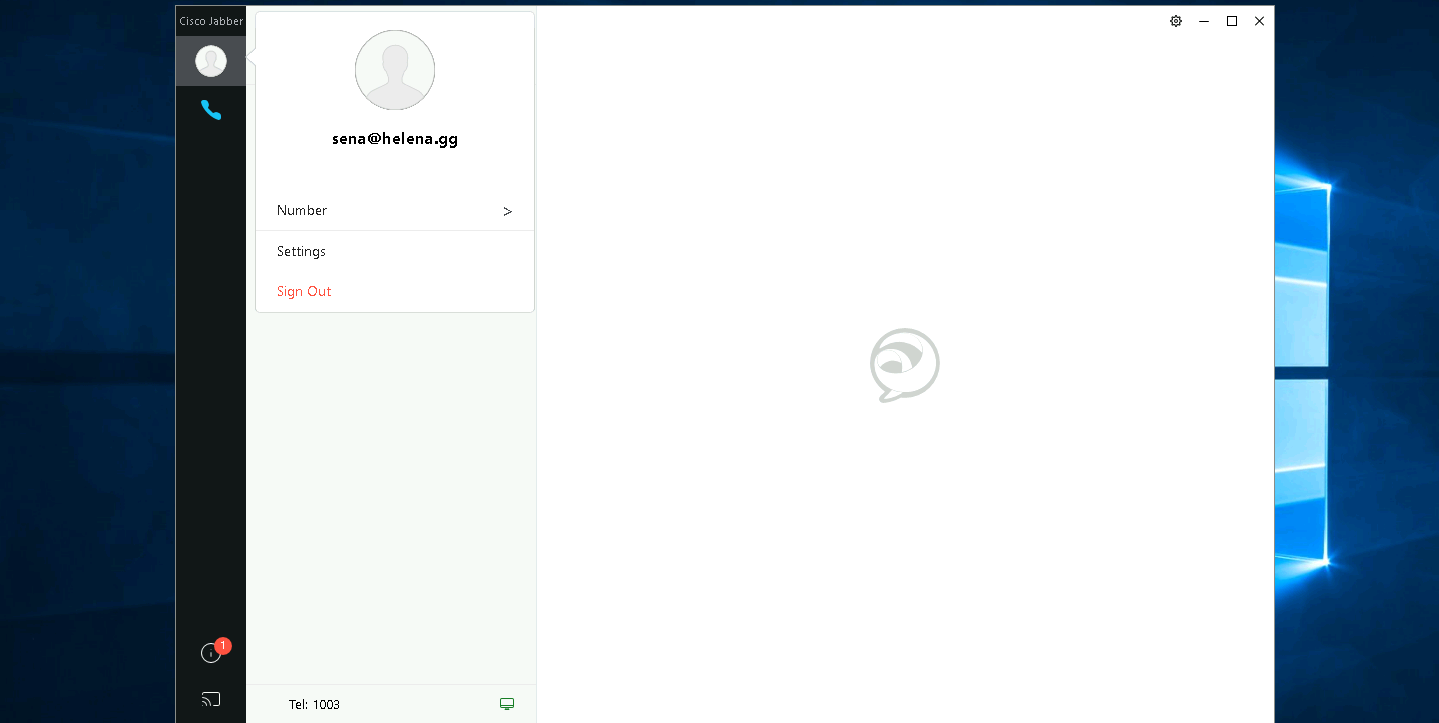
Logging in using MRA
Now on the internet, when we try to hit the helena.gg domain, the endpoint will use the _collab-edge DNS Srv Record to locate the CUCM Service
On Maintenance » Logging, we can see the the logs of the users authenticating to CUCM through Expressway