FortiAnalyzer
FortiAnalyzer is a centralized logging, analytics, and reporting solution for Fortinet devices. It collects logs from products like FortiGate, FortiWeb, and other Forti Devices as well as other products, enabling real-time visibility, threat analysis, and compliance reporting across the network.
Installing FortiAnalyzer
Deploy the VM like any other forti devices, and upon opening the web ui, we can enter forti account to enable free trial
When deploying on lab with trial fortigates VM, we have to enable low encrytion mode so it can communicate to fortigate devices
1
2
3
4
5
config system global
set enc-algorithm low
set oftp-ssl-protocol sslv3
set ssl-low-encryption enable
end
Adding Fortinet Devices
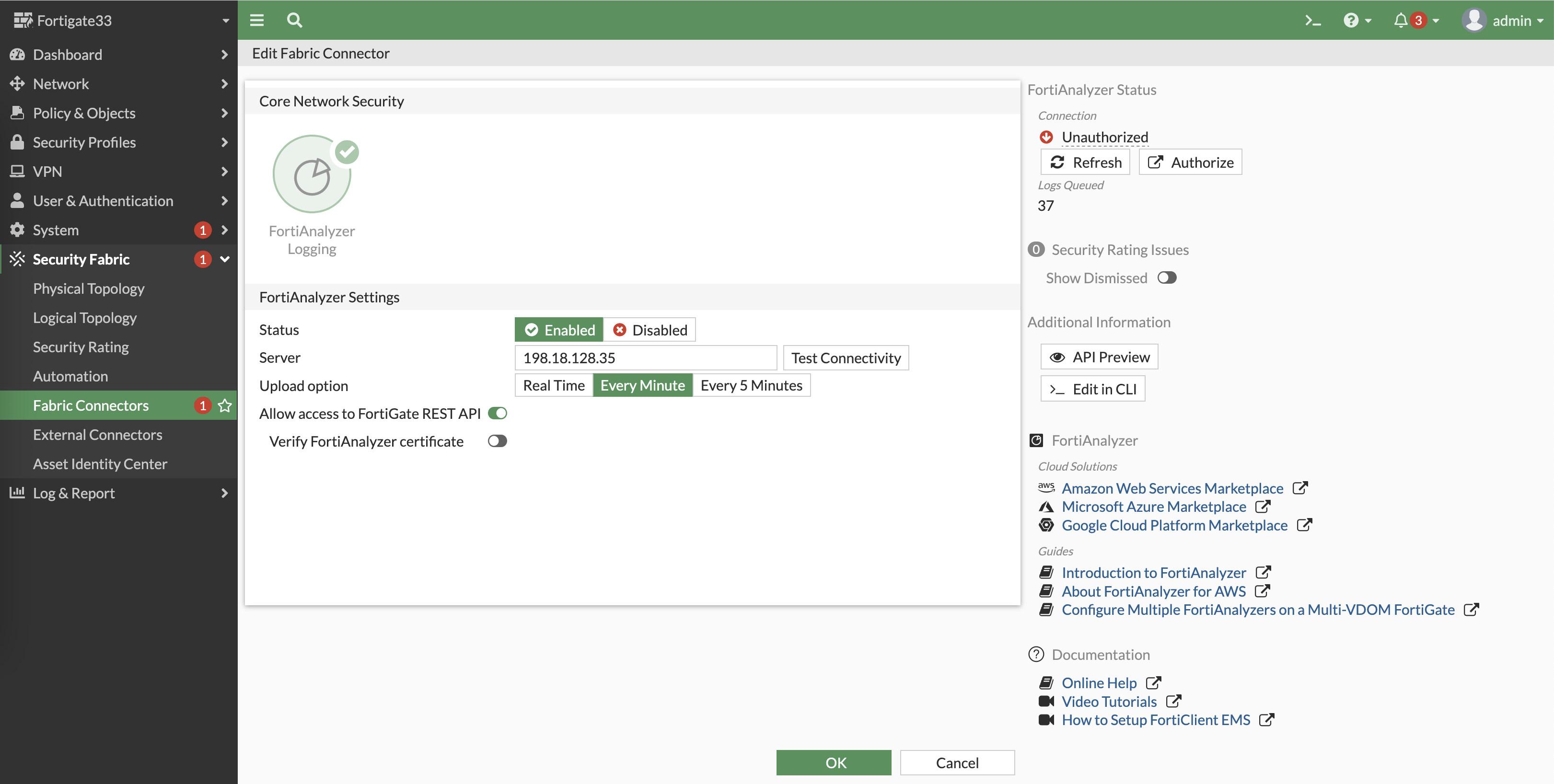
On Fortigate, enable the FortiAnalyzer on Fabric Connectors and point it to our FAZ
Then authorize the device
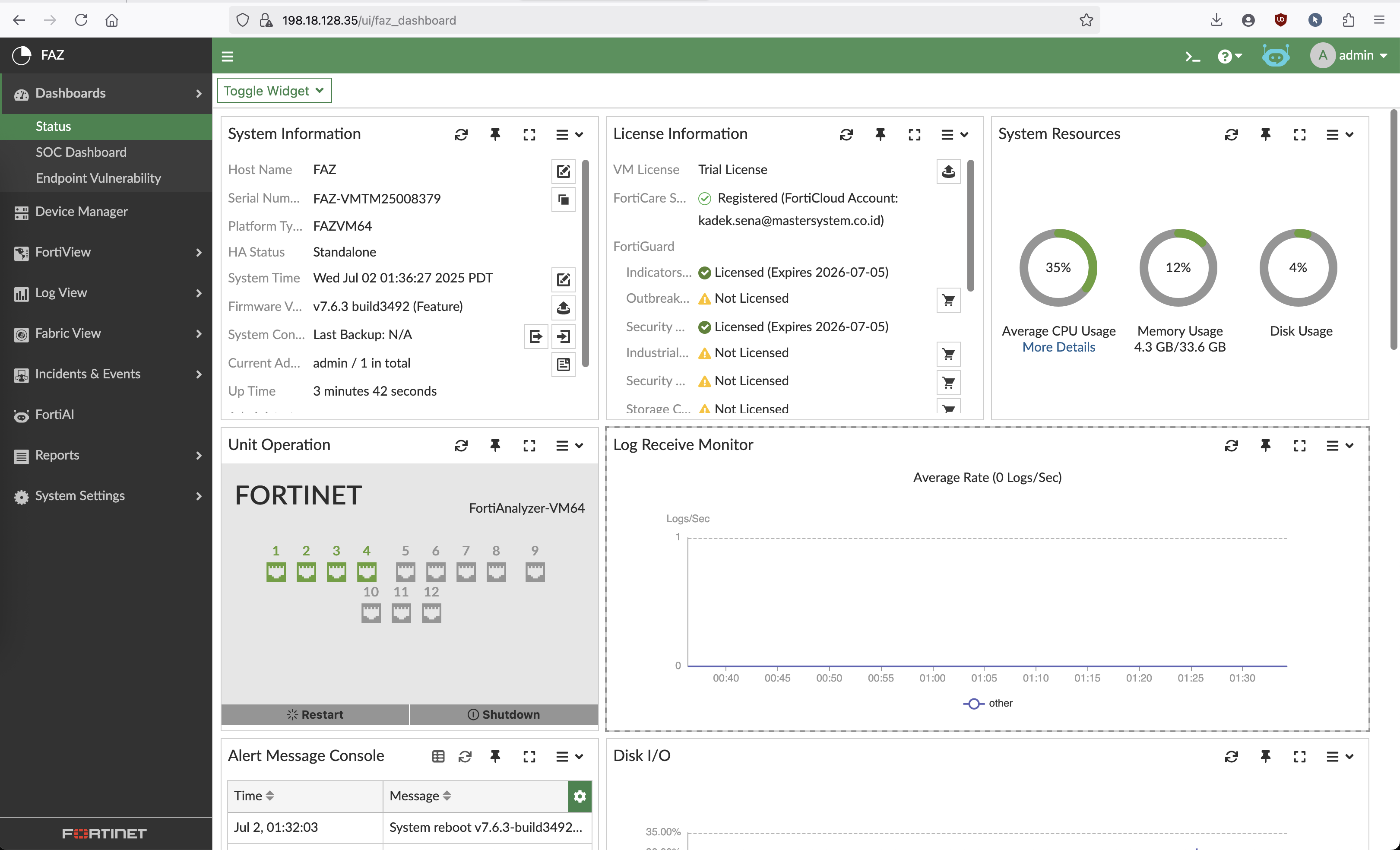
After that the devices will show up as on Device Managed on FAZ
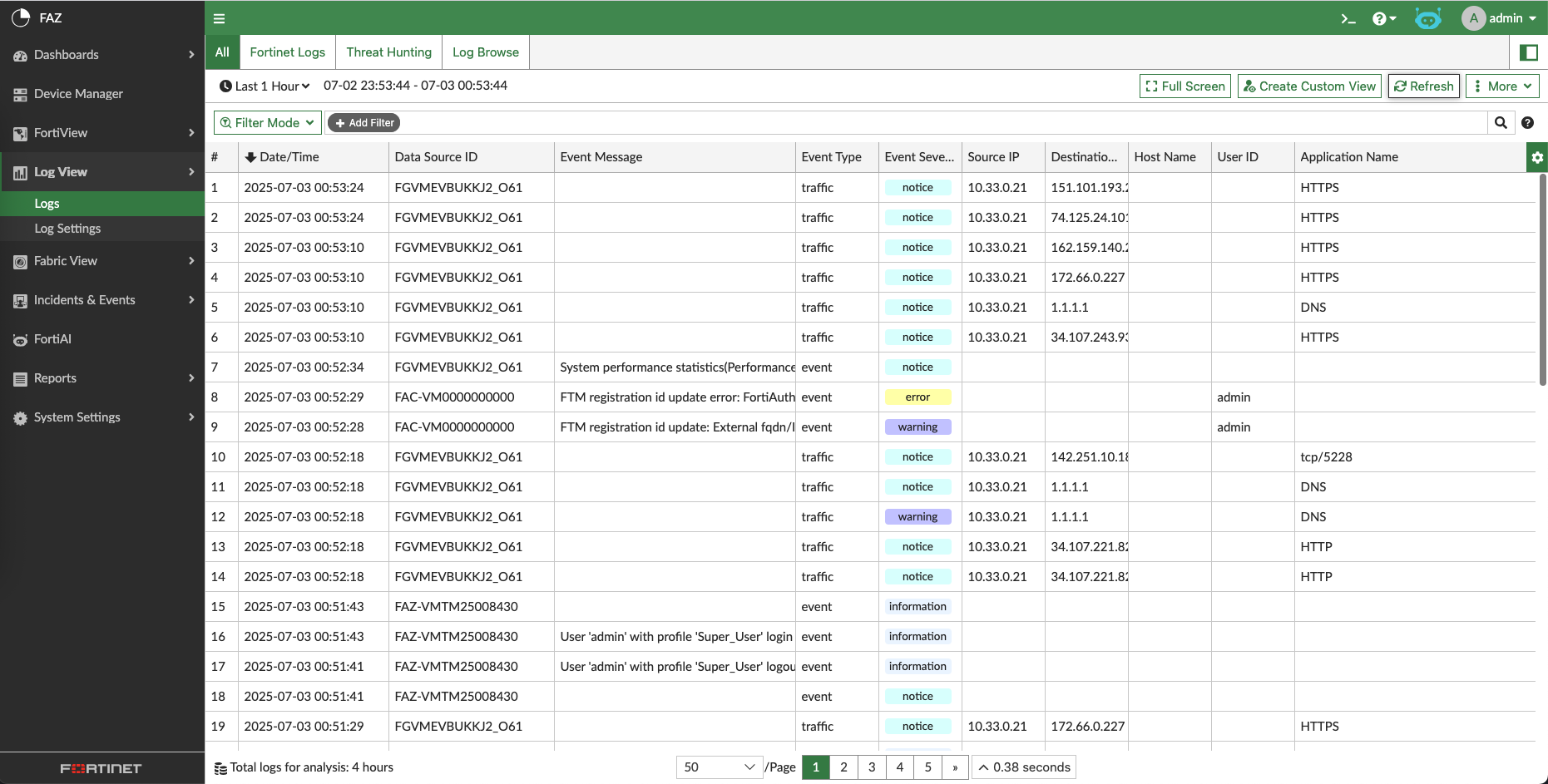
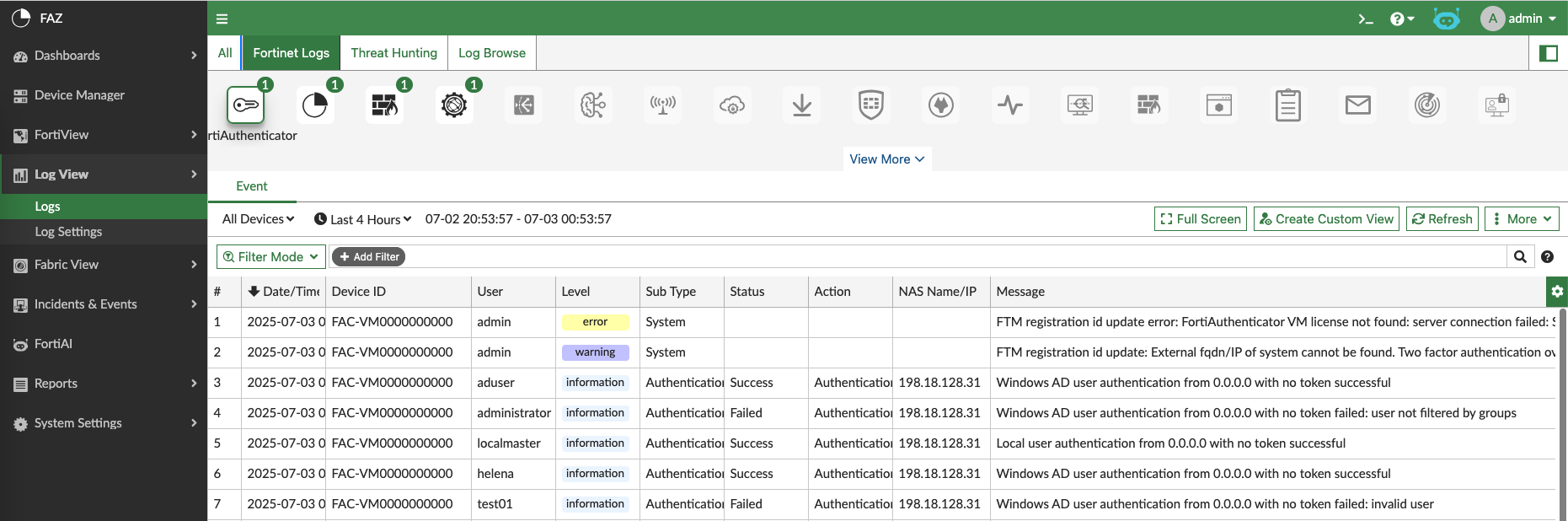
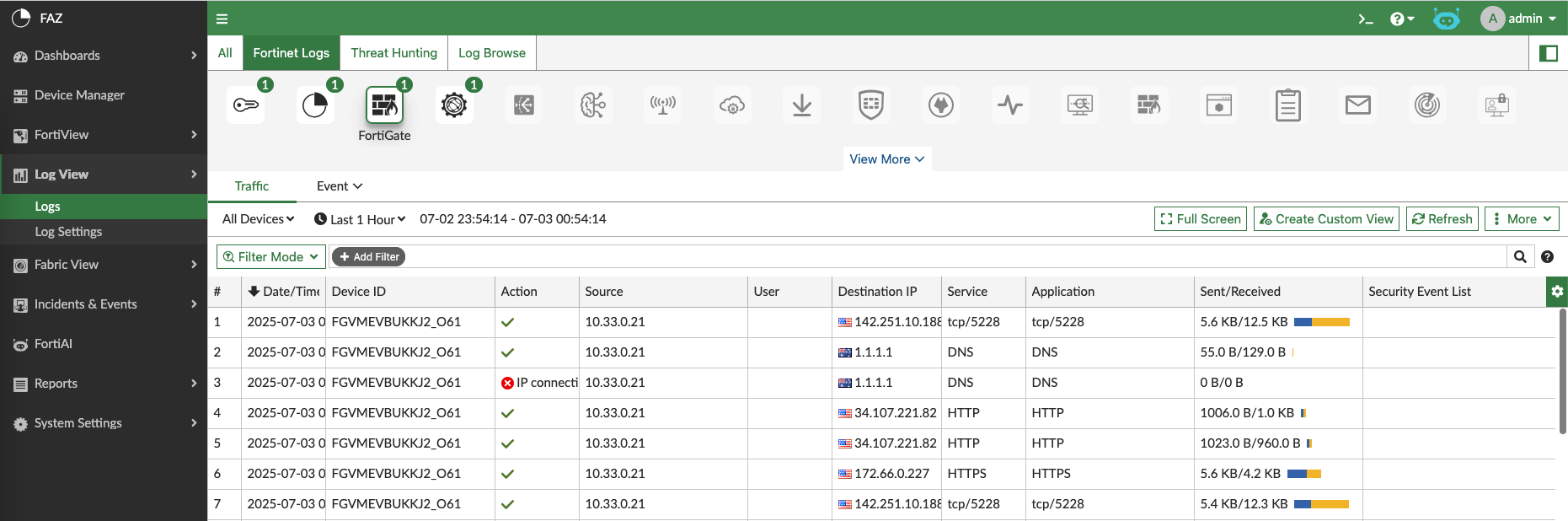
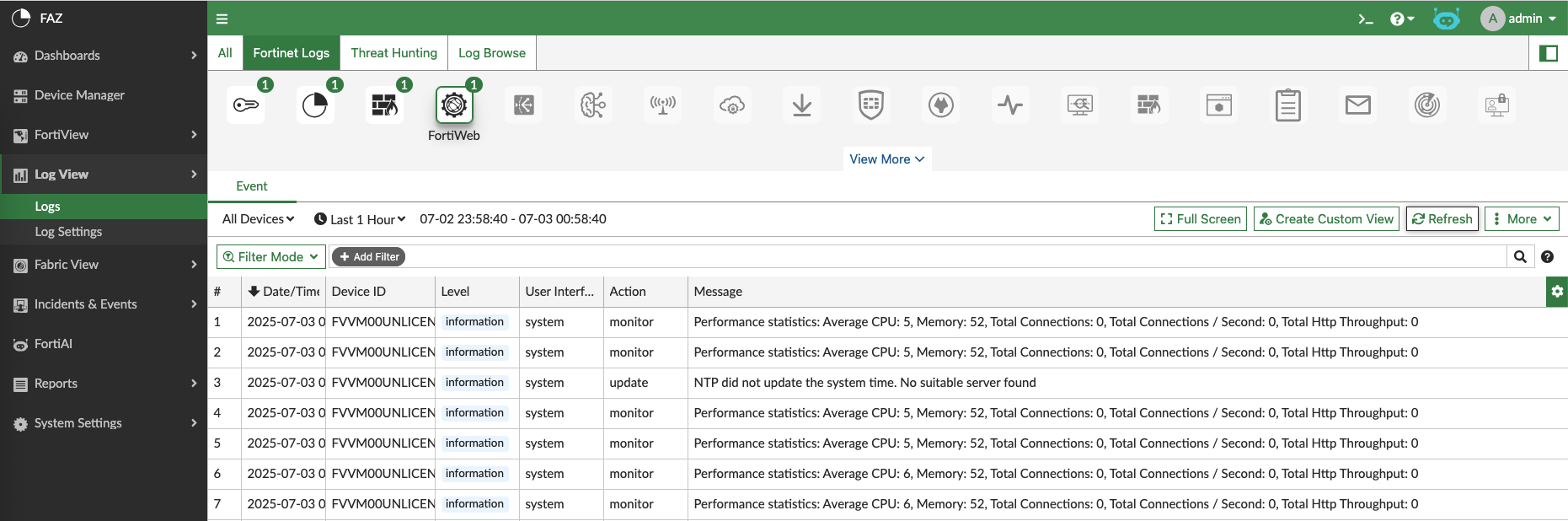
FAZ will now start ingesting logs from managed devices, we can see all the logs in Log View
Or we can see the logs based on the device type
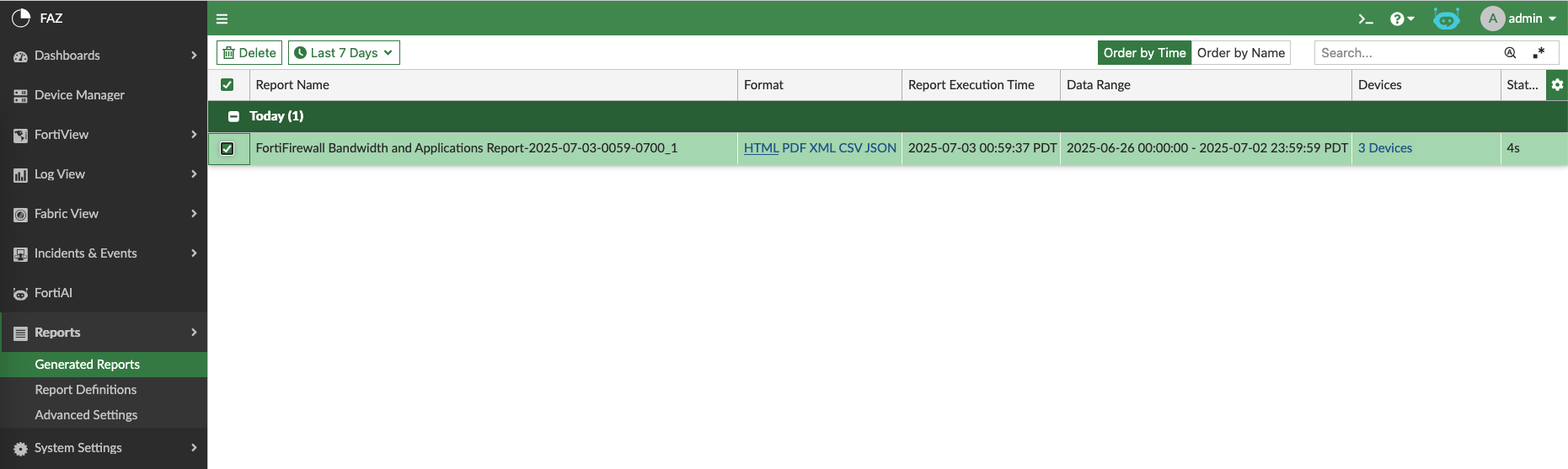
We can also generate reports using predefined report definitions
Adding Other Devices
FortiAnalyzer can function as a syslog server, allowing it to ingest and store syslog data from non-Fortinet devices such as firewalls, routers, or servers. This enables centralized log collection and basic analysis, though advanced parsing and reporting features are limited for third-party logs compared to Fortinet-native data.
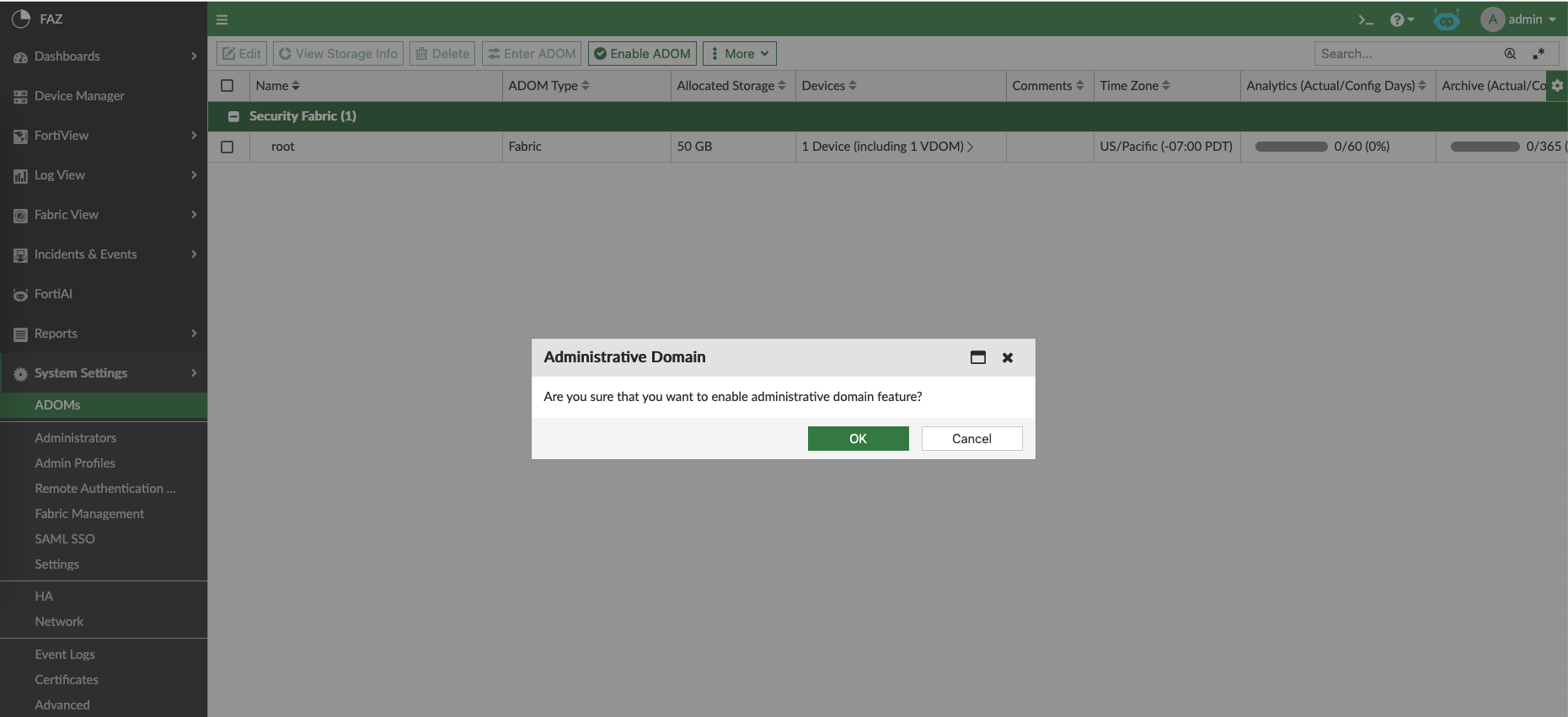
To enable FAZ as Syslog Server, we need to enable ADOM
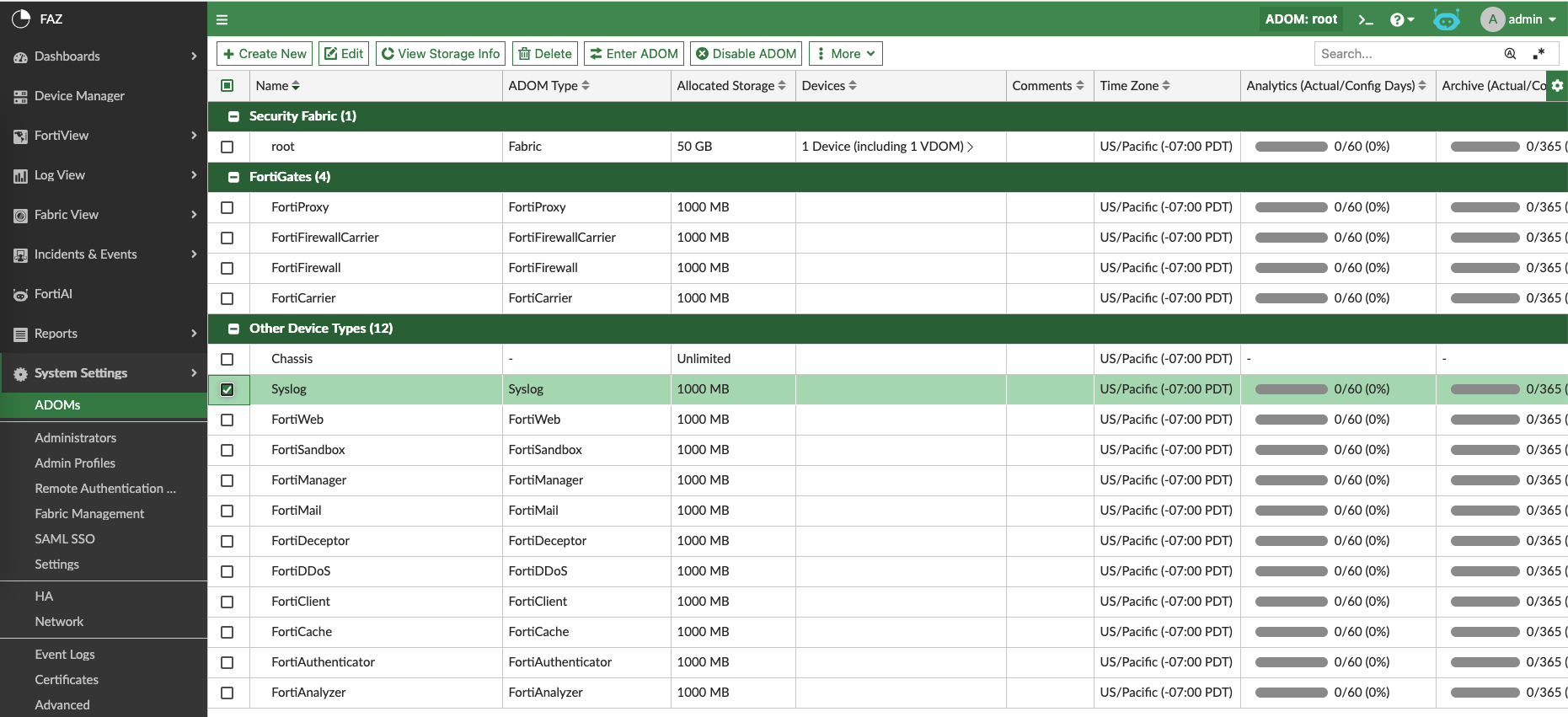
This will result multiple ADOMs created, the one we are interested in is Syslog
Now on the device that we’d like to send syslog on, configure it to send syslog to FAZ. Here we have a linux server that also acts as a syslog server for Cisco FTD devices, we will forward the logs from this linux to FAZ
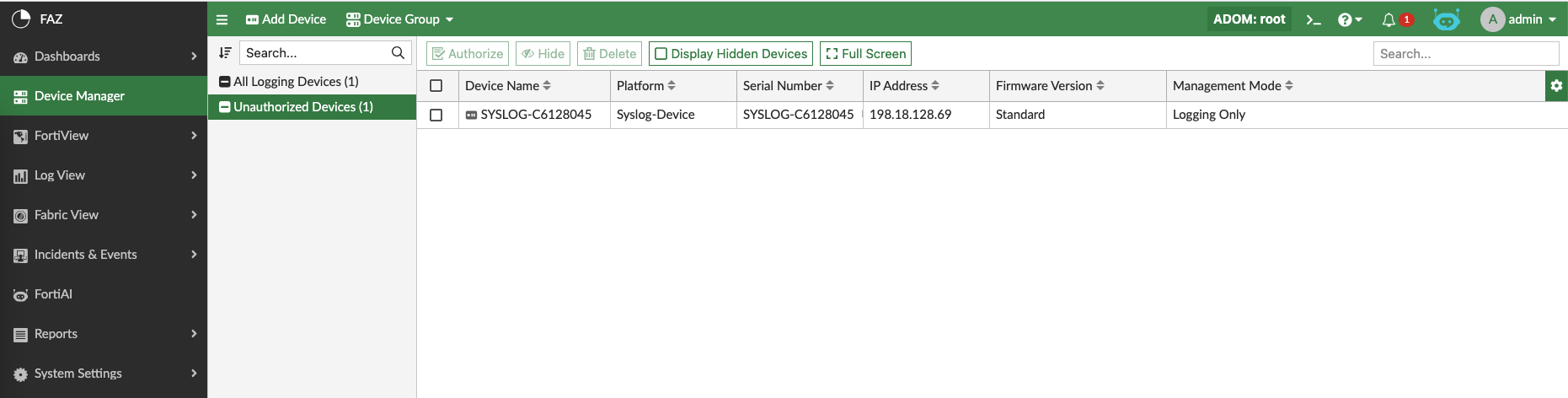
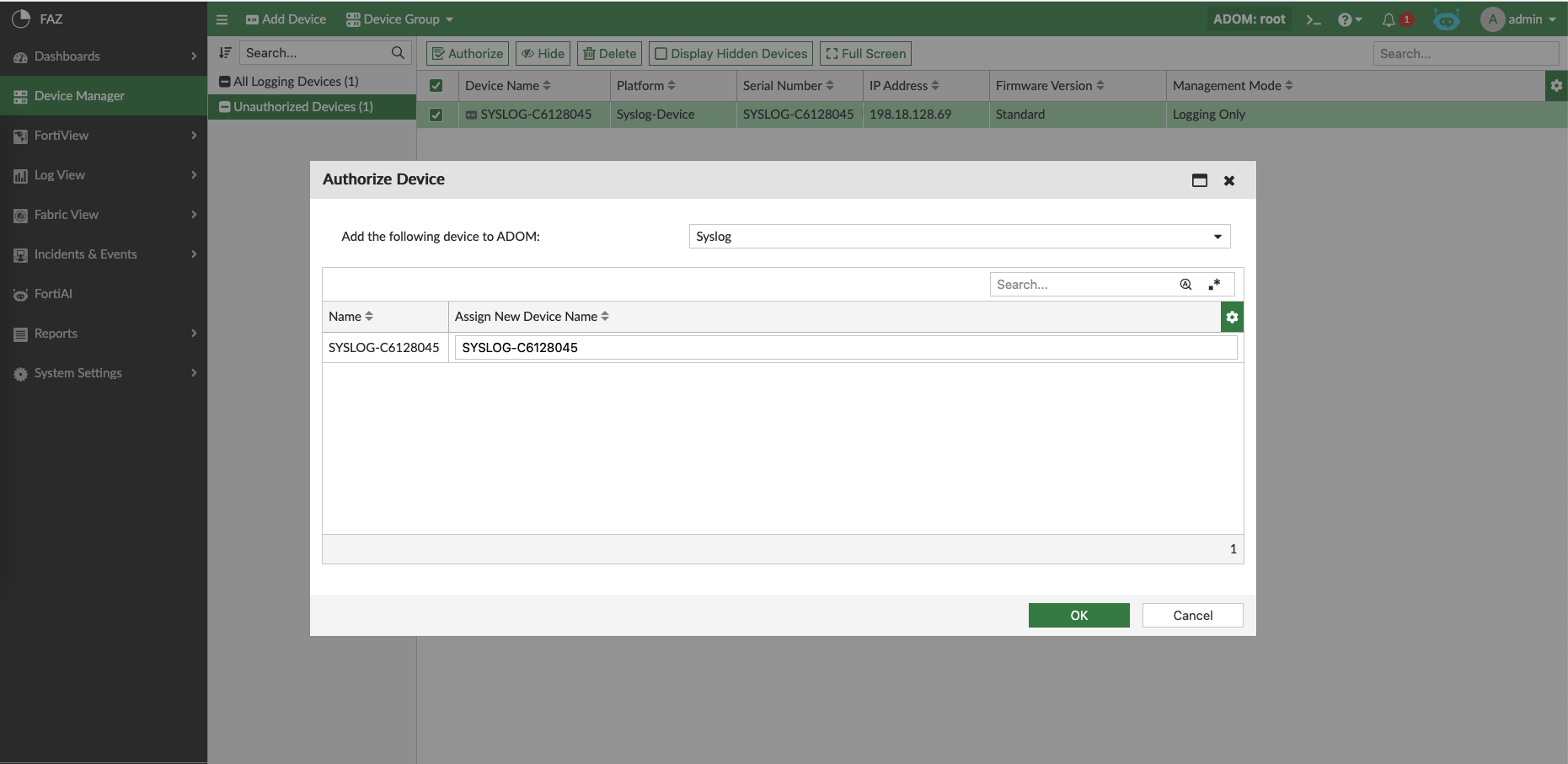
Back on FAZ on Root ADOM, the linux server has shown up as Unauthorized
Authorize the device and add it to Syslog ADOM
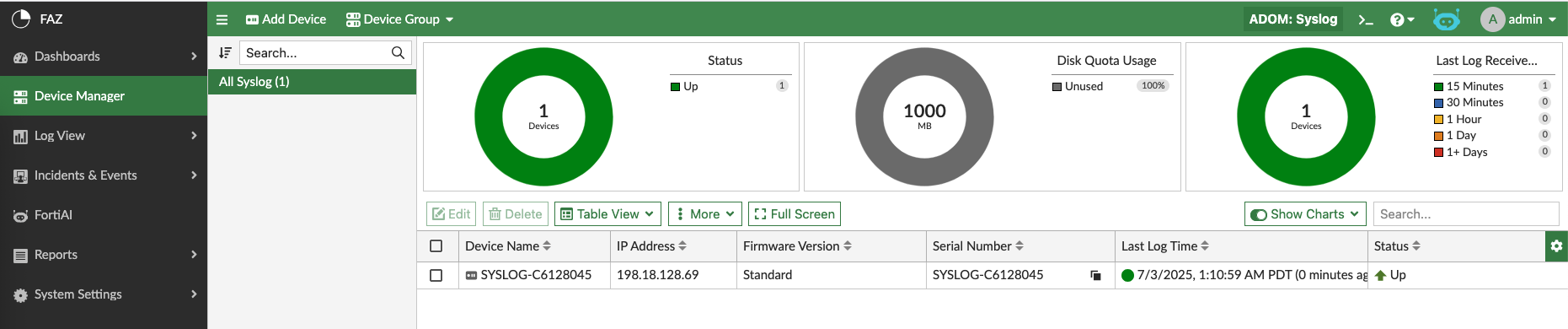
Switch to Syslog ADOM, we will see the device in Device Manager
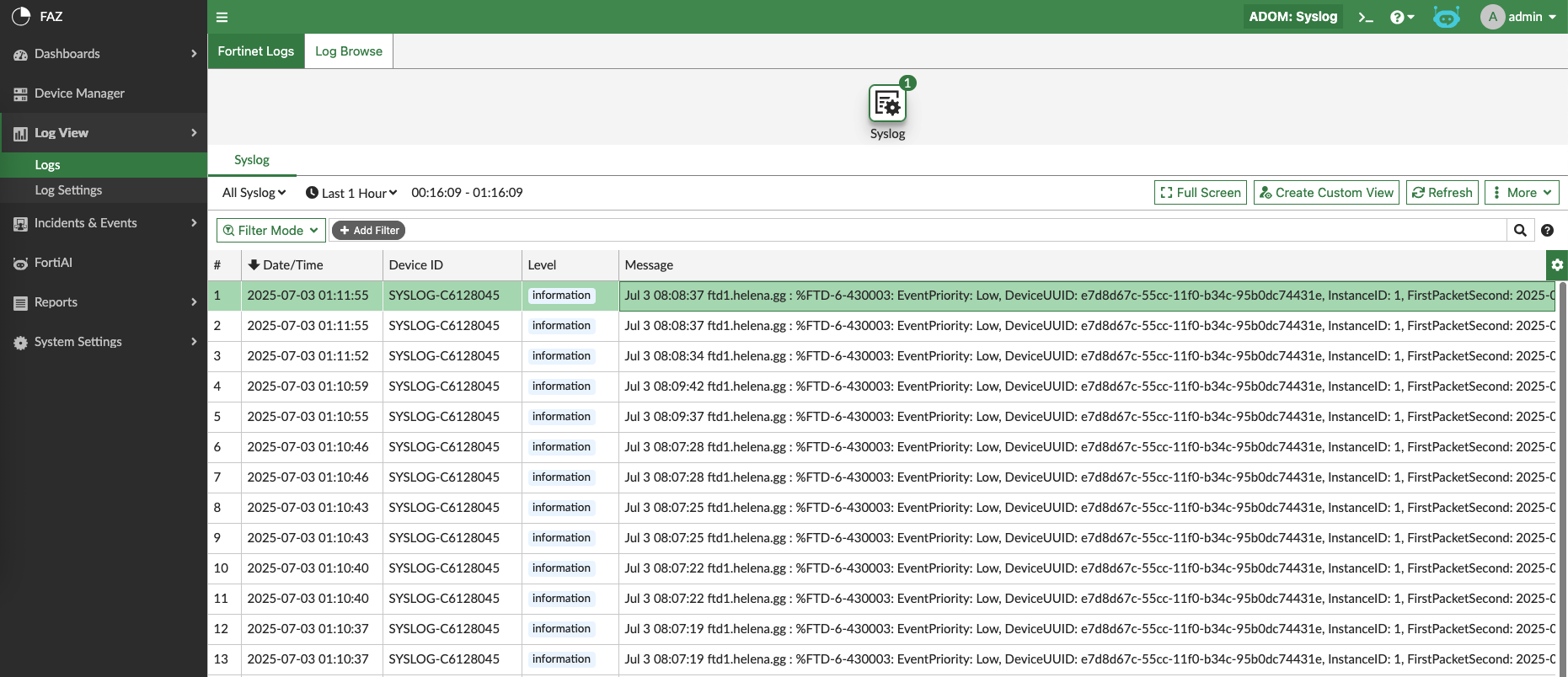
And now the syslog from the device can be seen on ‘Log View’