FortiAuthenticator
FortiAuthenticator is Fortinet’s centralized authentication management solution that provides secure identity and access services for enterprise networks. It supports user authentication through various methods like RADIUS, LDAP, SAML, and certificate-based login, and integrates with Fortinet devices (like FortiGate) to enforce user-based policies, enable SSO, and improve visibility and control over network access.
Once installed like any other Fortinet device, access the Web GUI
LDAP Integration
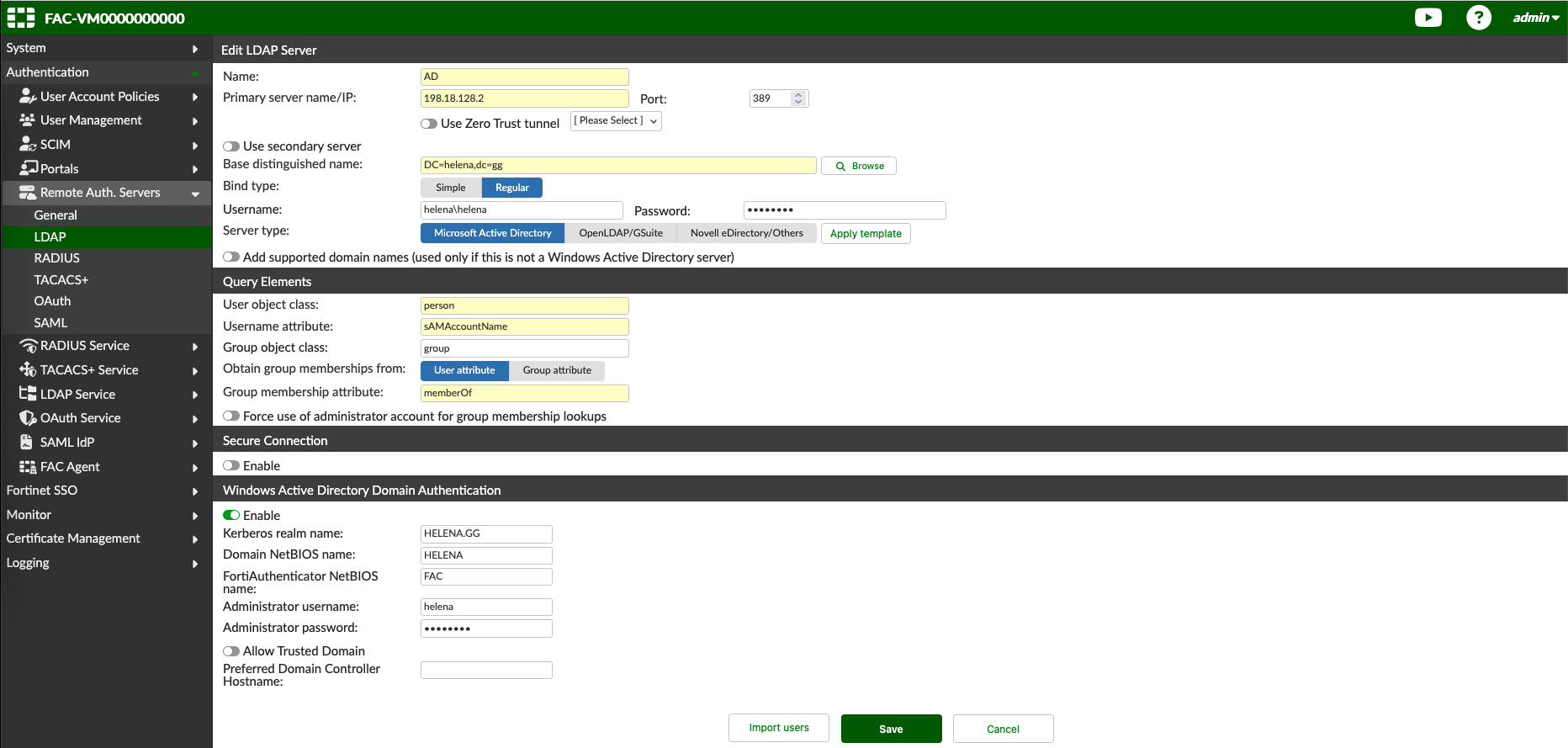
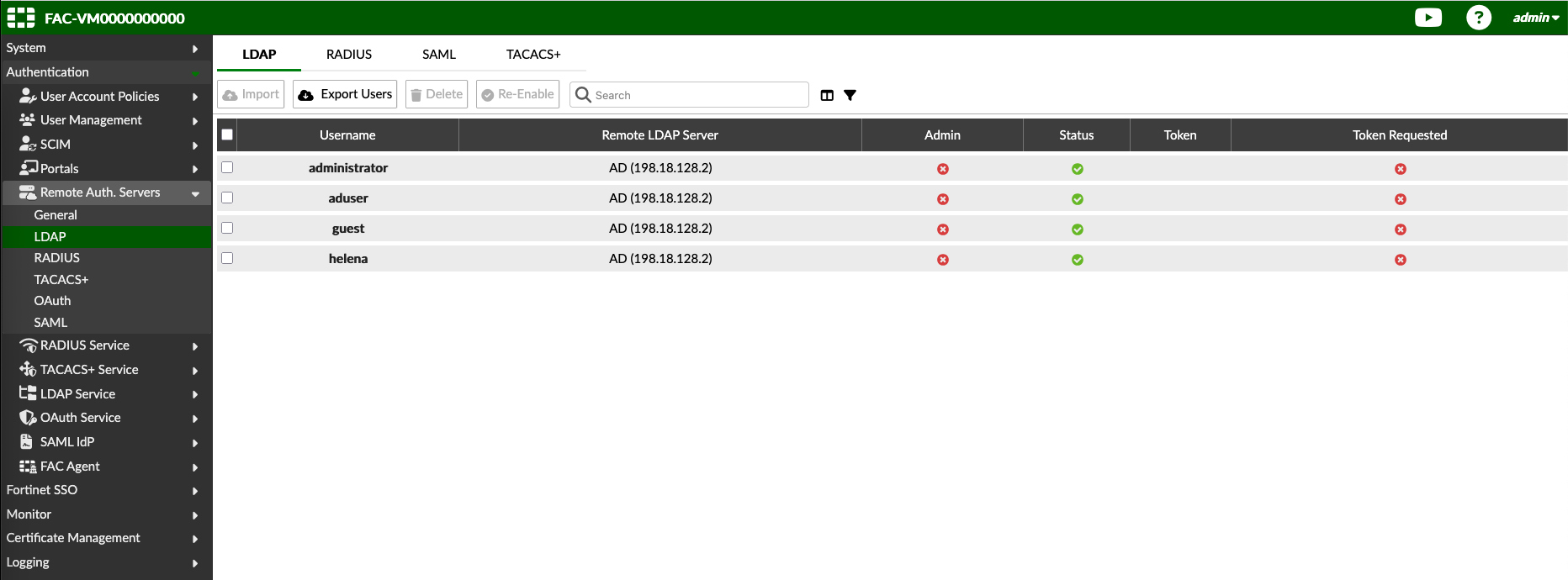
On Authentication » Remote Auth Servers » LDAP, create a new LDAP integration to Domain Controller
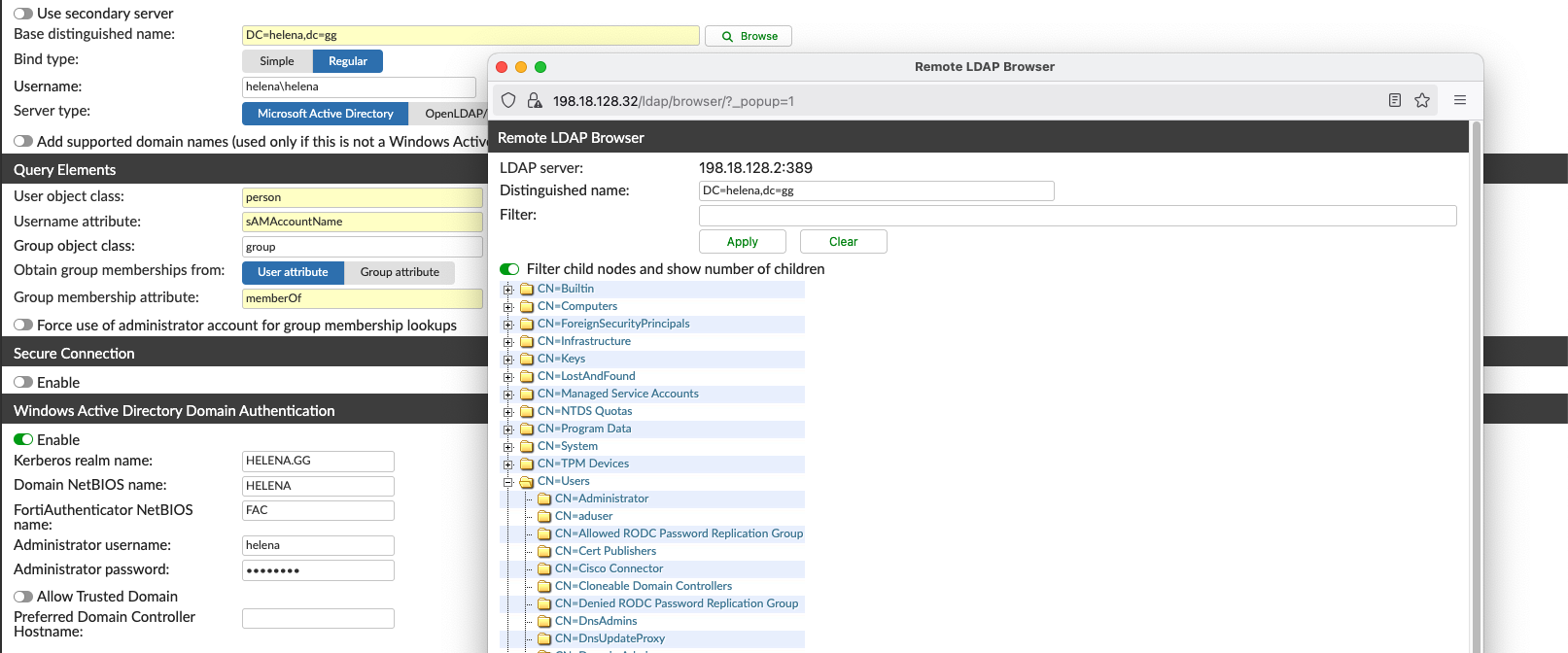
Once configured correctly, we can now browse the domain grops and users
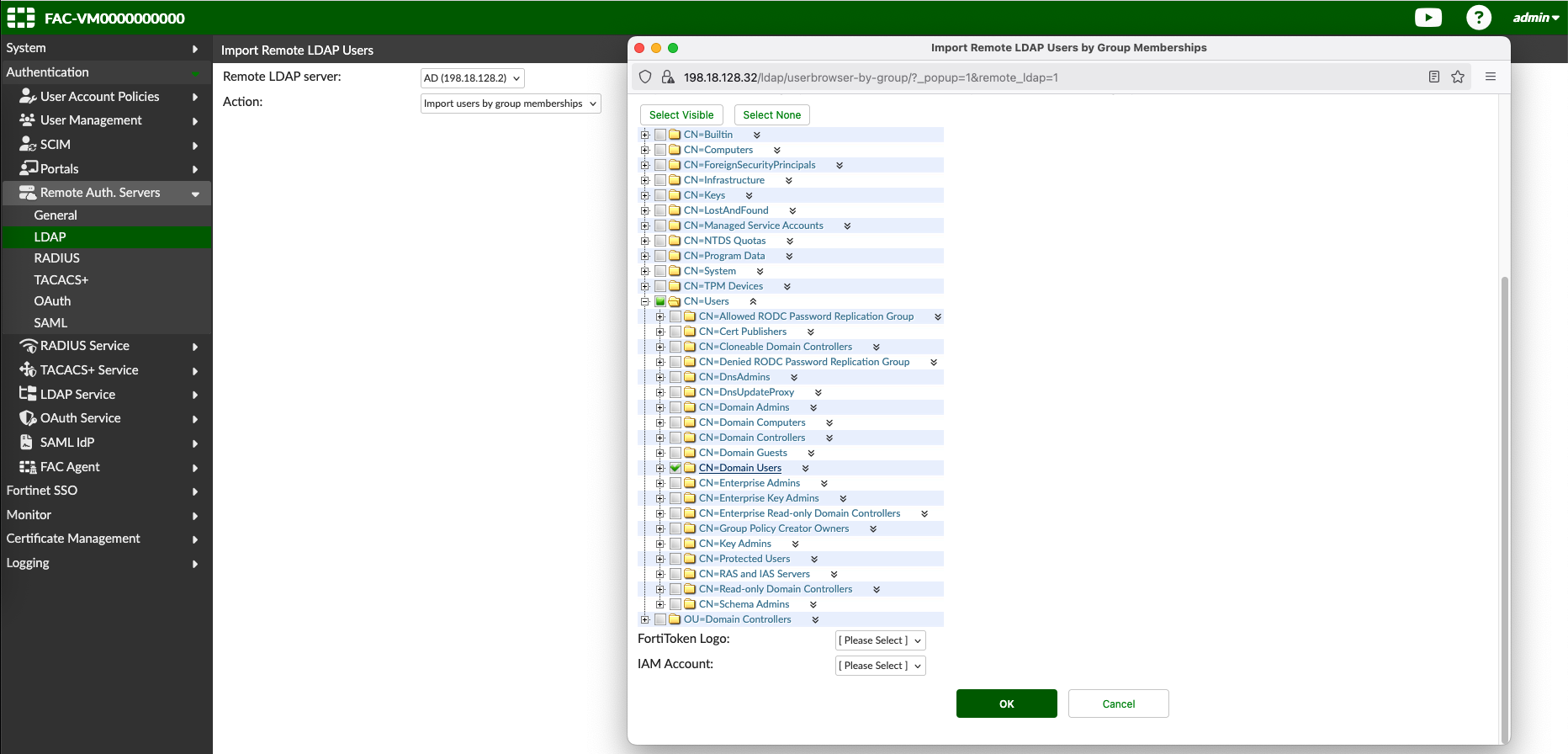
Next hit Import Users, and import the LDAP Users based on the desired groups
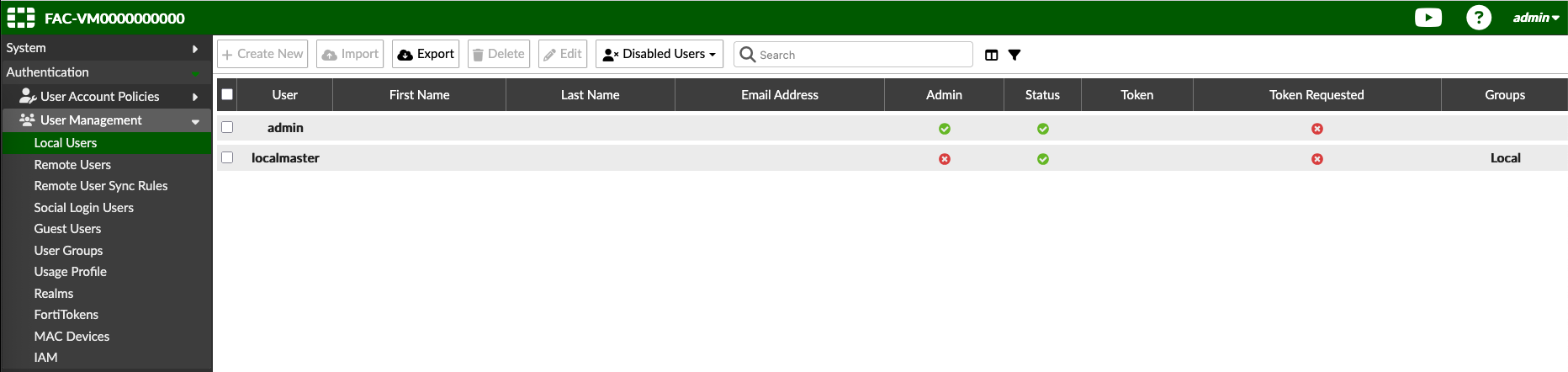
After that, the LDAP users are now available on User Manaement » Remote Users
Here we also add a local user ‘localmaster’ for testing purposes
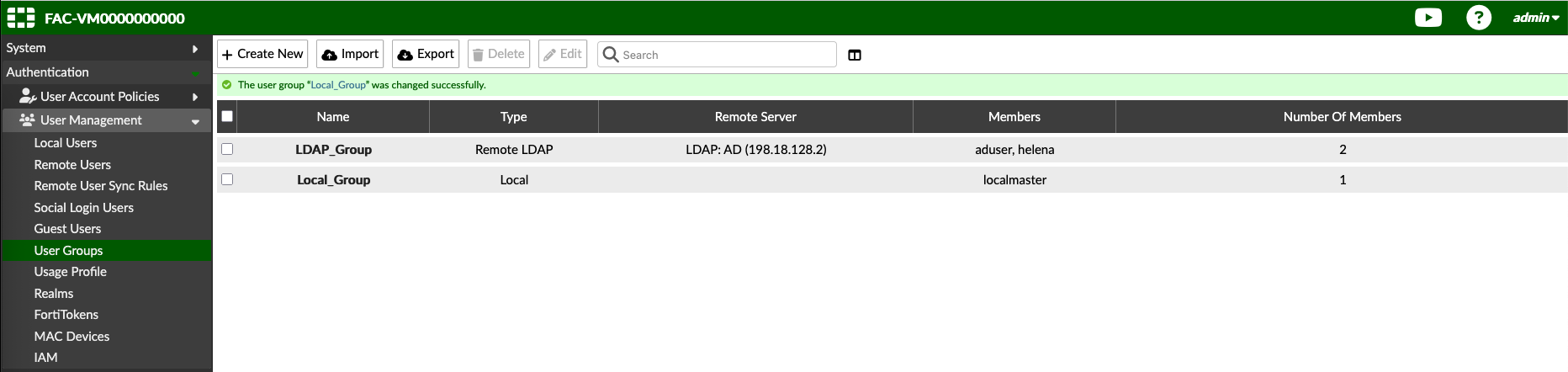
Next we create 2 new goups, one for Locaol Users and the other for LDAP Users, here we add the users that we’d like to include
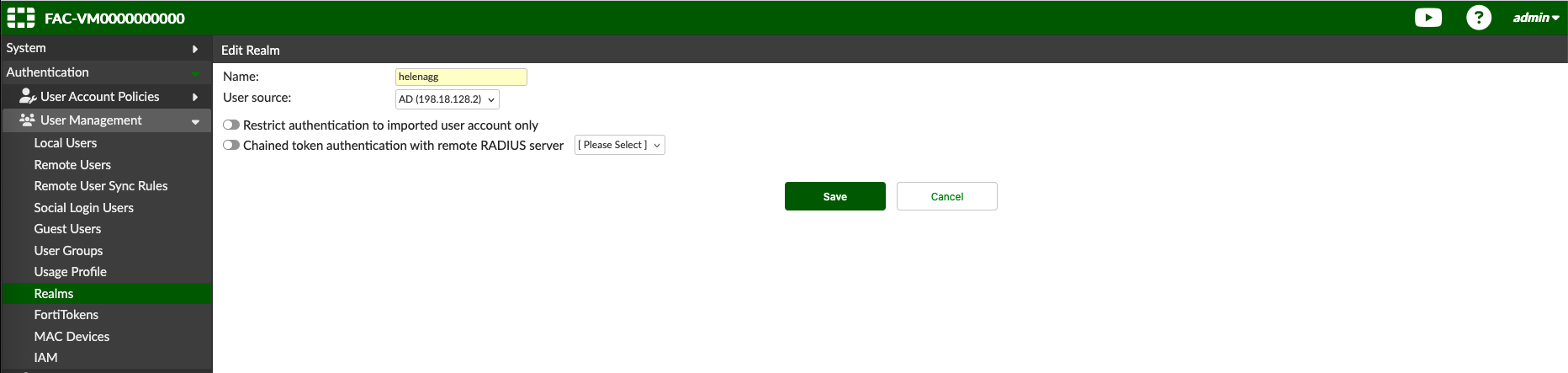
After that we create a new Realm to point to the integrated LDAP
Fortigate Integration
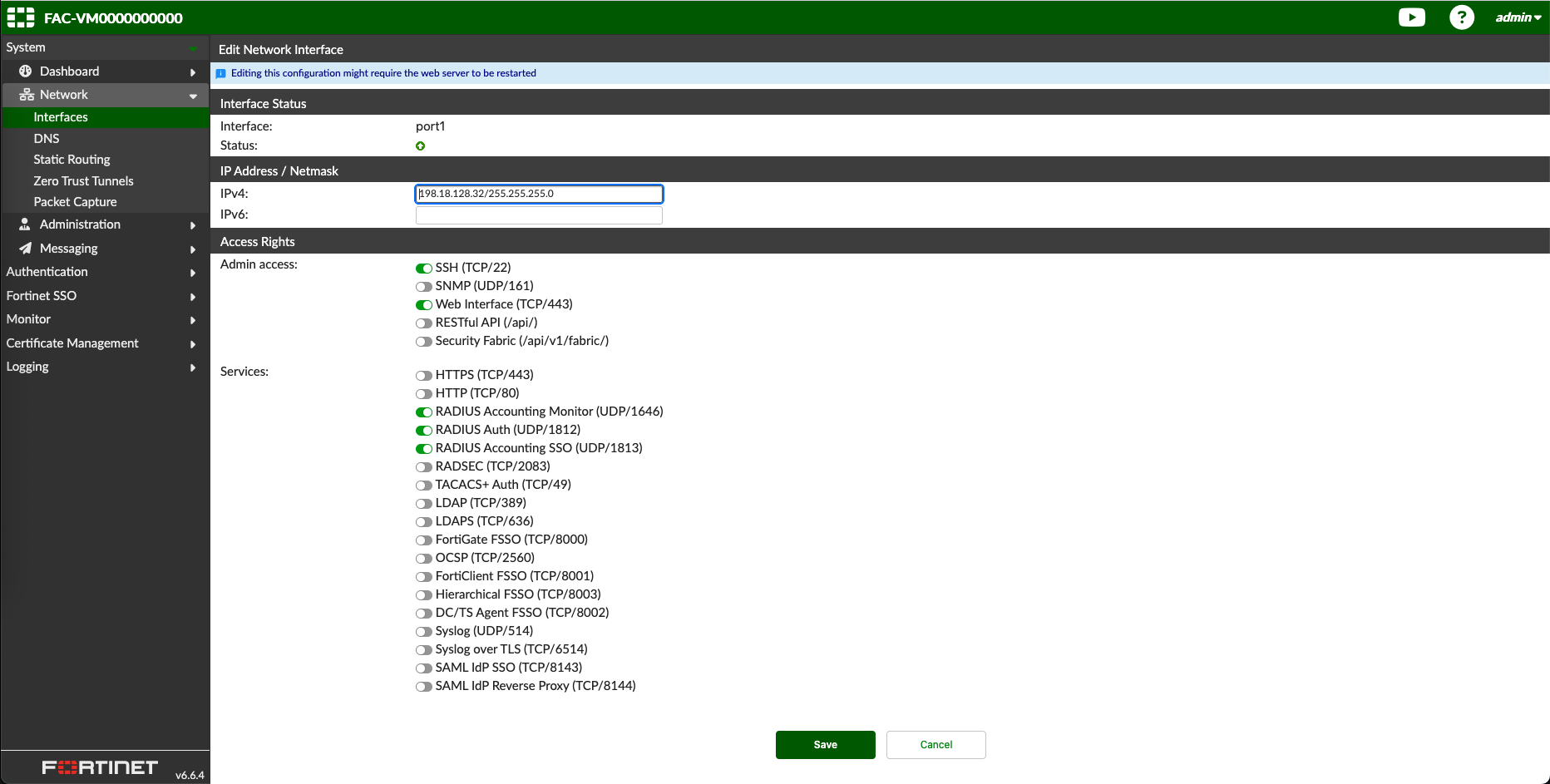
On FortiAuthenticator’s intefrace, make sure its able to receive Radius connections from fortigate
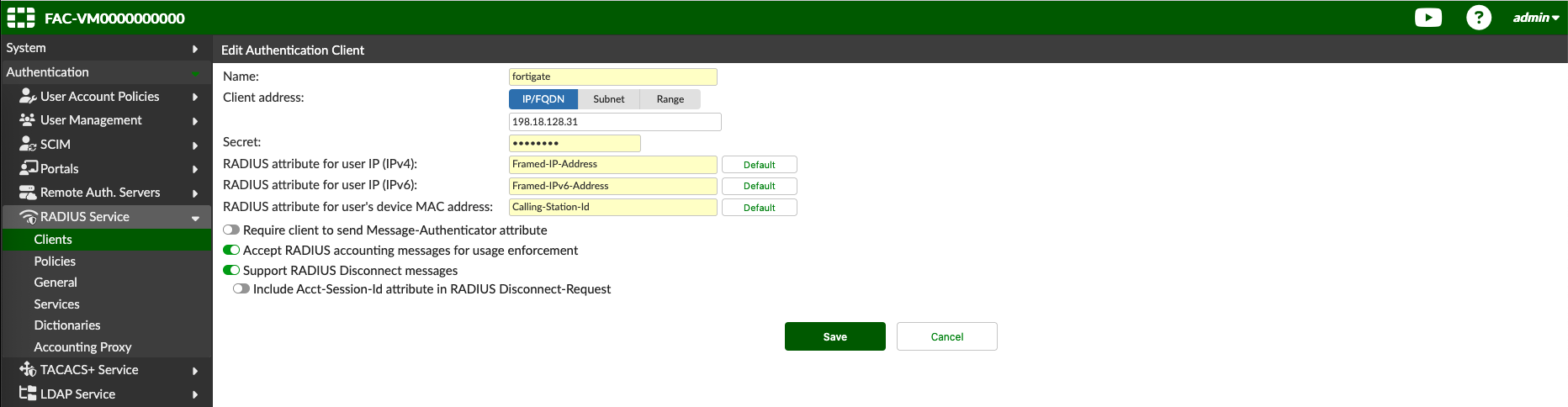
Then on RADIUS Service » Clients, add Fortigate as the client
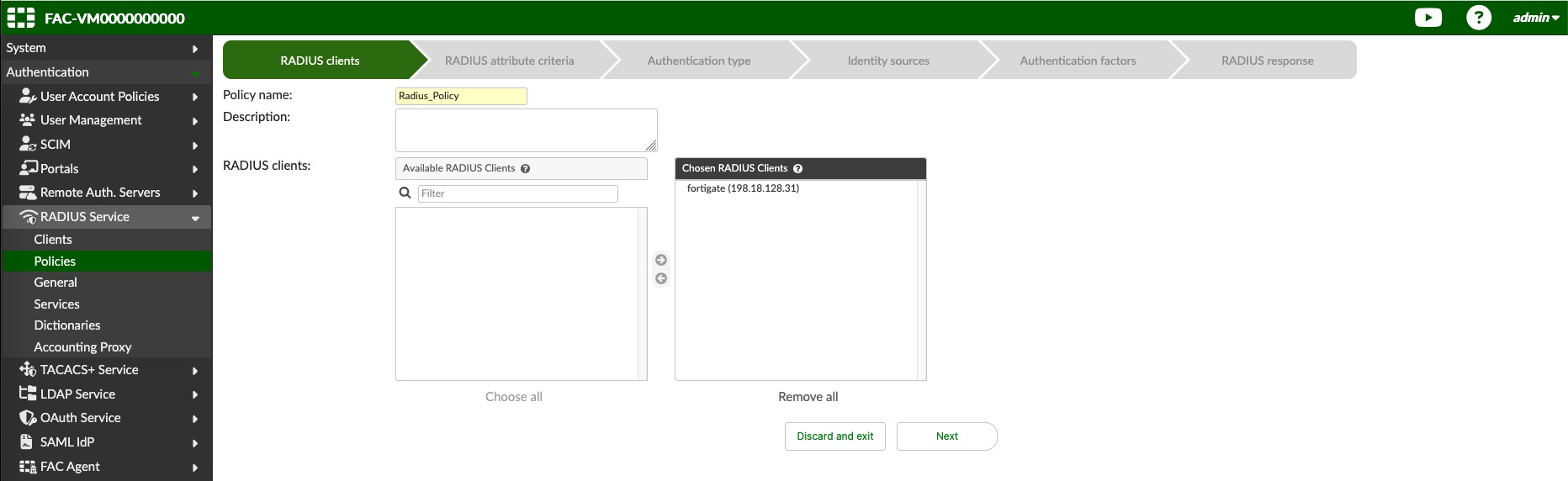
Next create a Radius Policy, select the created Radius Client
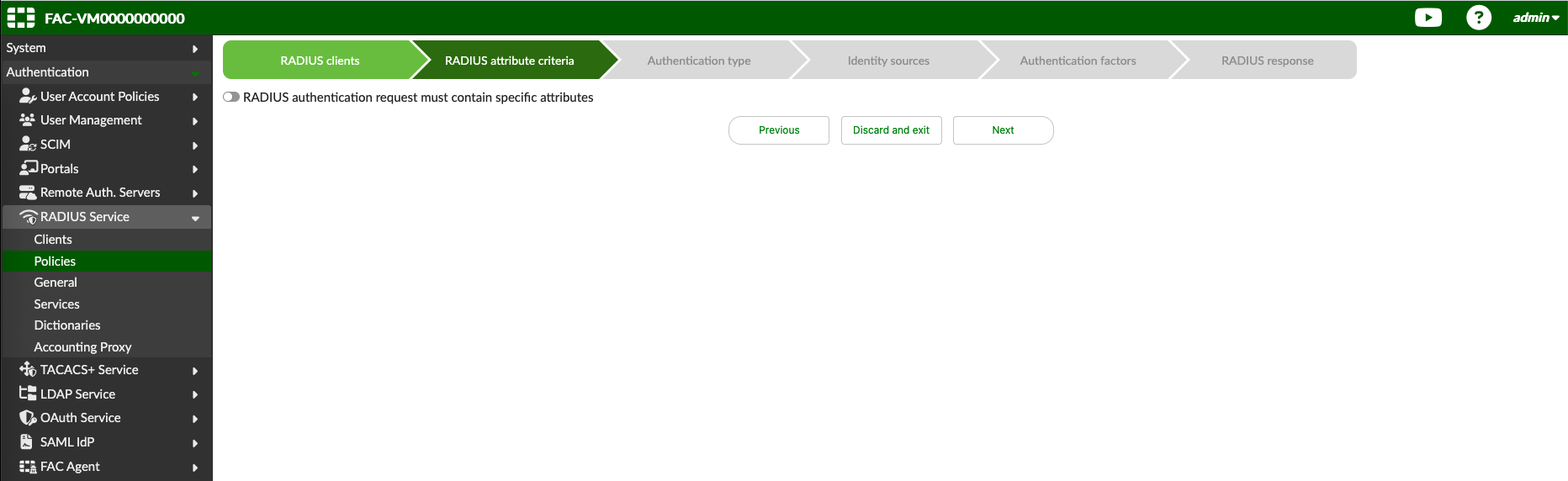
Here we just skip ahead because we dont configure any specific attributes
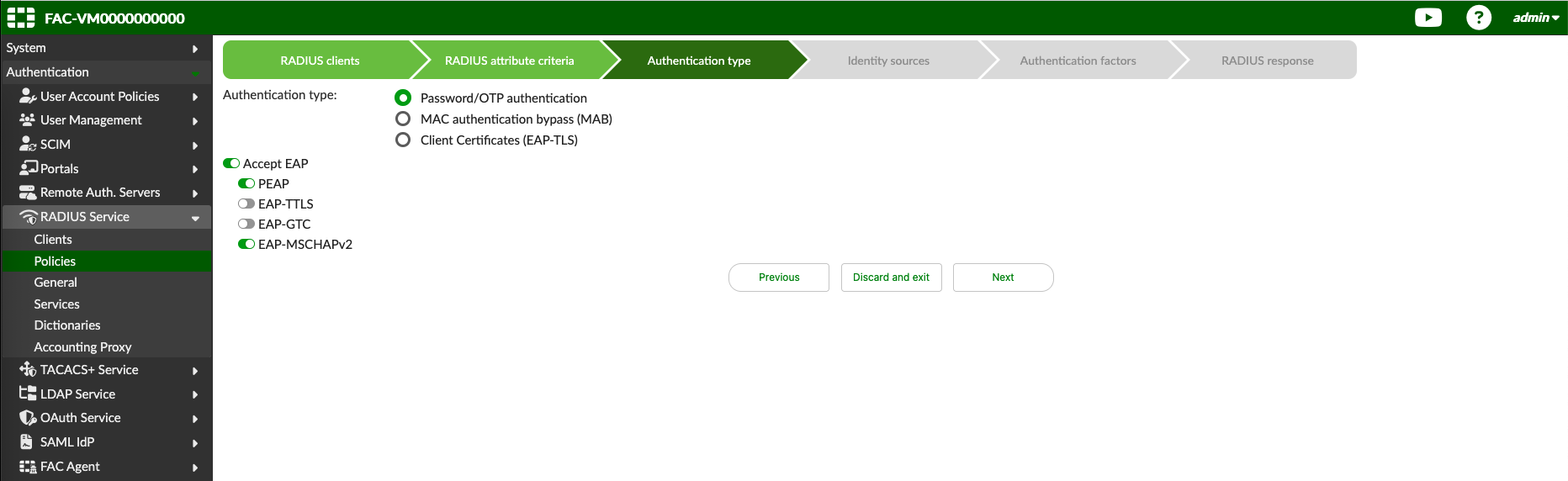
For authentication type, we stick with default Password/OTP and we enable some EAP protocols incase needed in the future
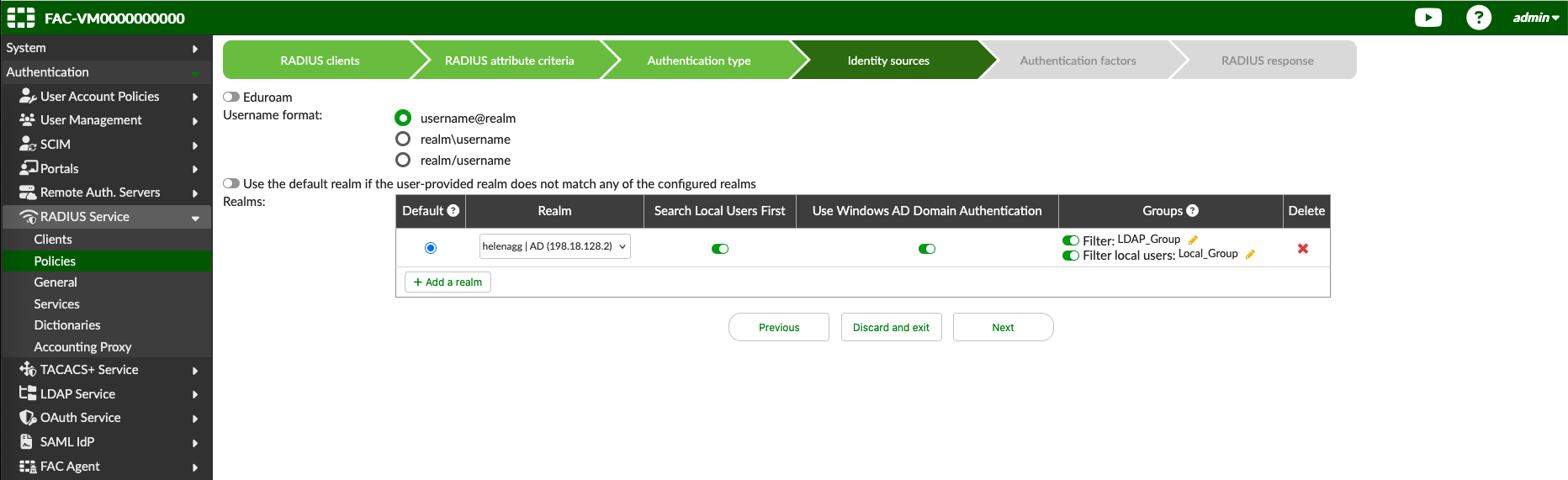
And here we add the created Realm, we configure so it looks up users on the 2 User Groups created earlier
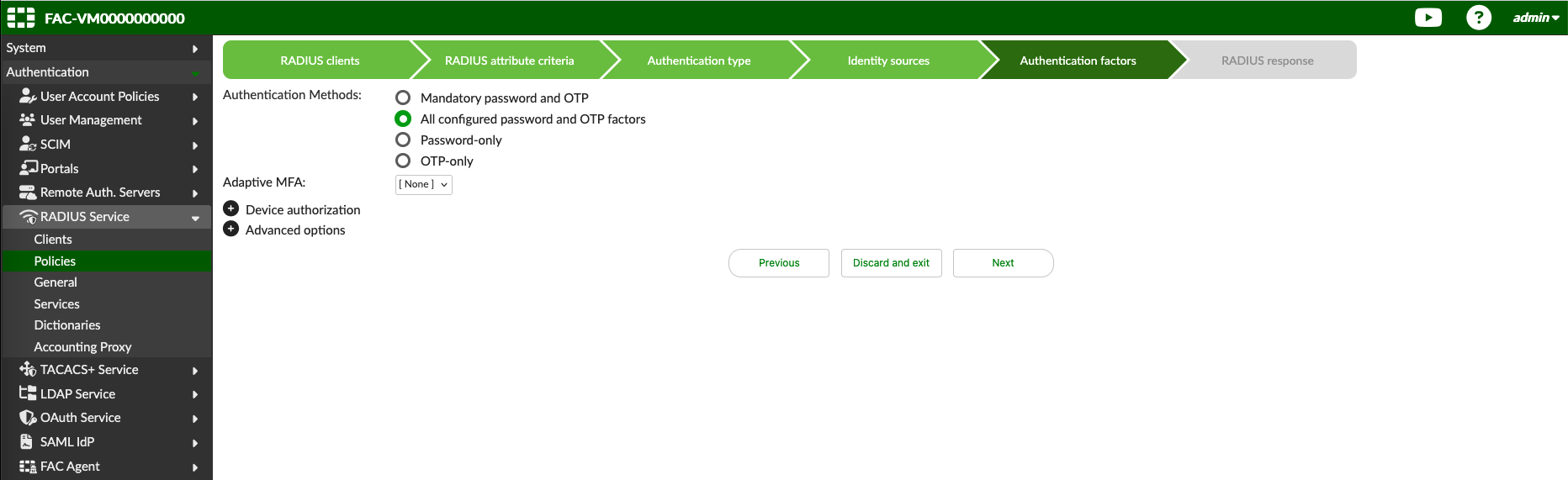
For the factor, we keep the default
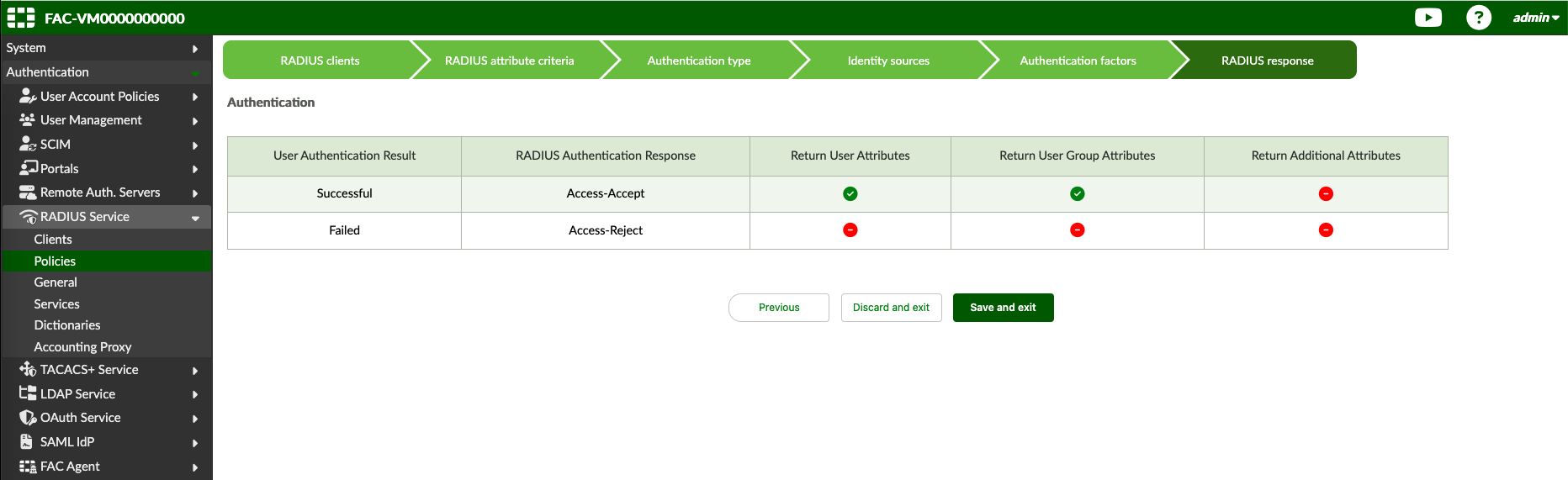
And lastly we can hit Save and Finish
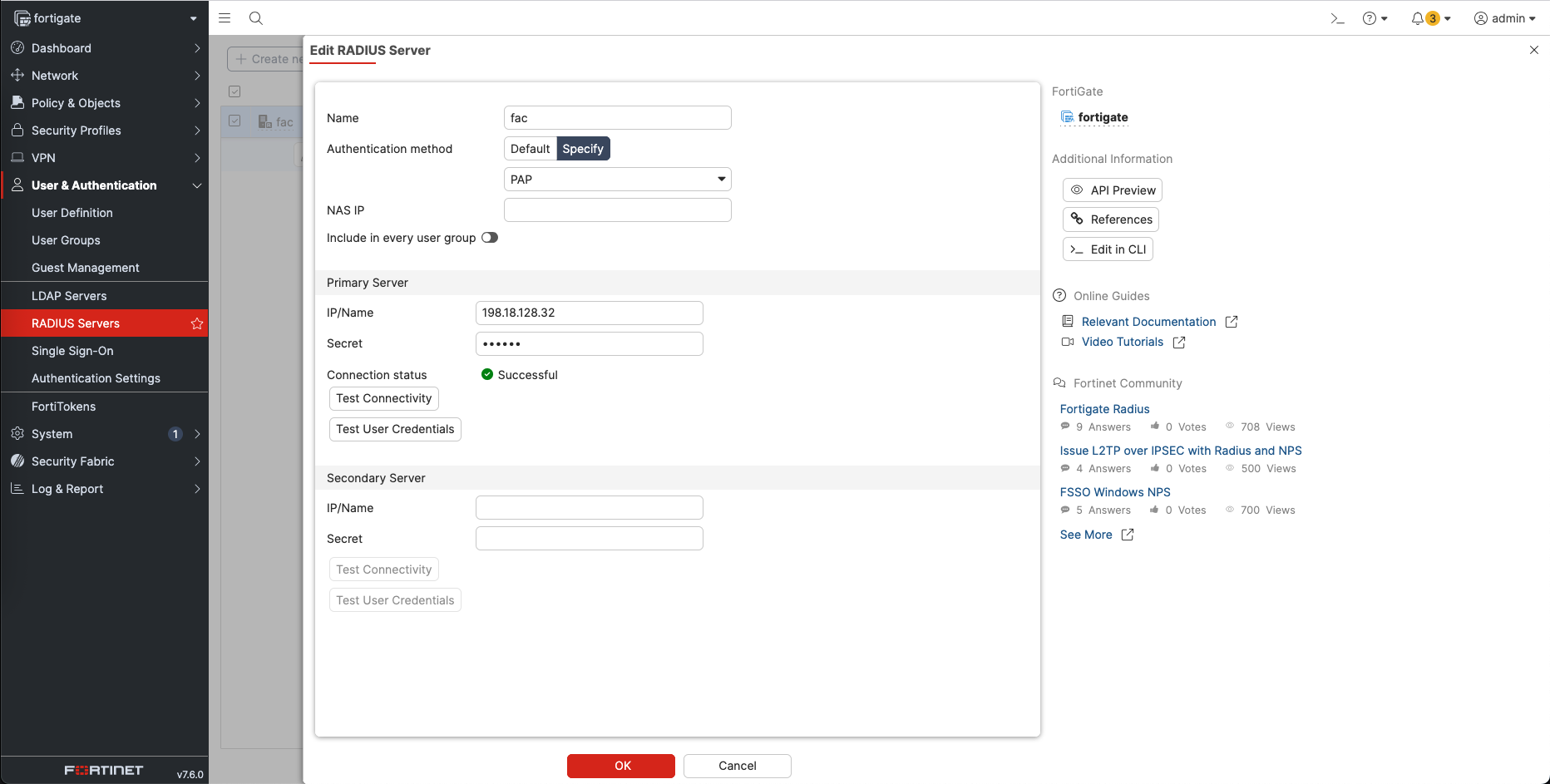
On the Fortigate side, we add a new Radius Server pointing to the FortiAuthenticator
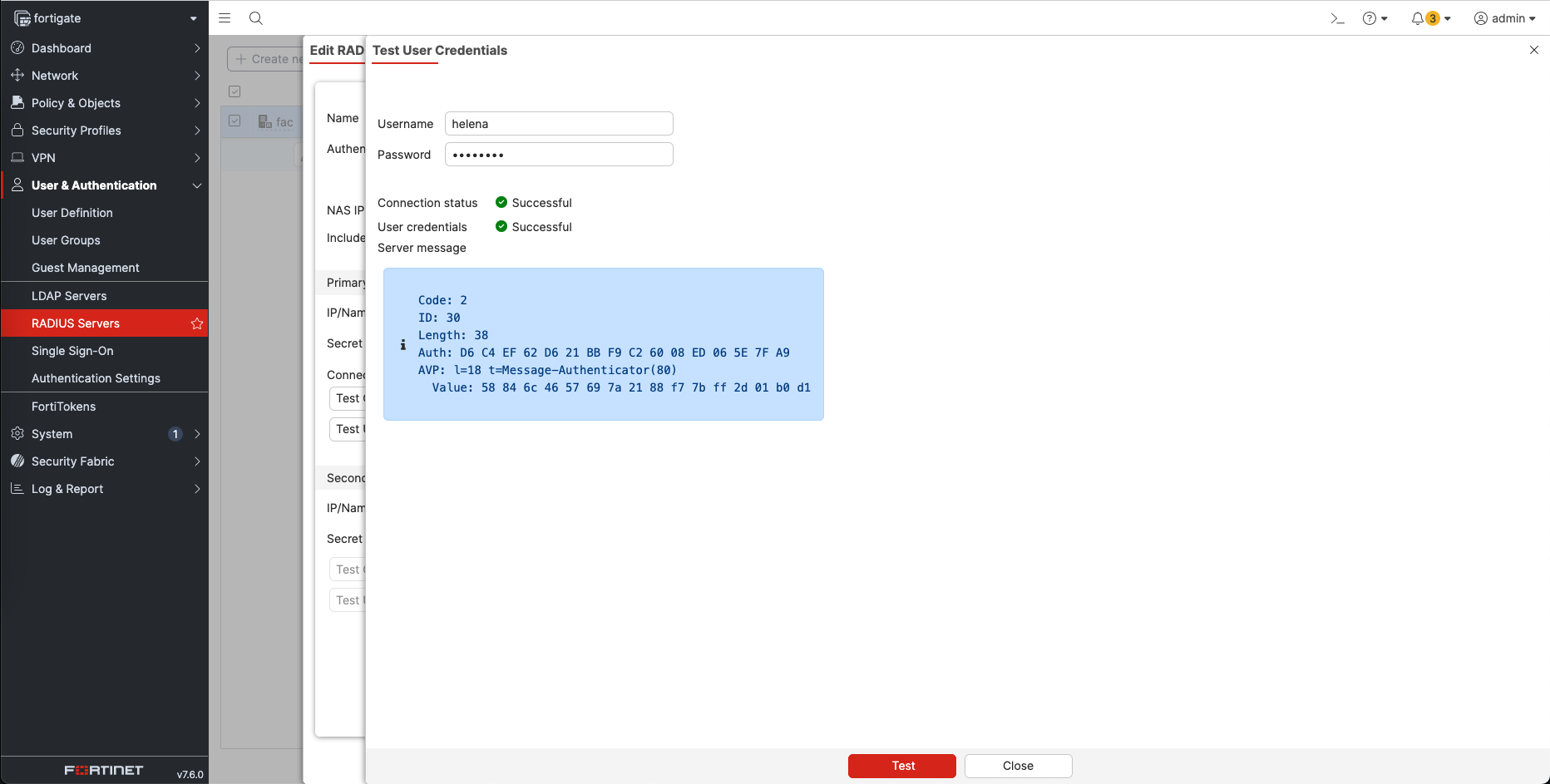
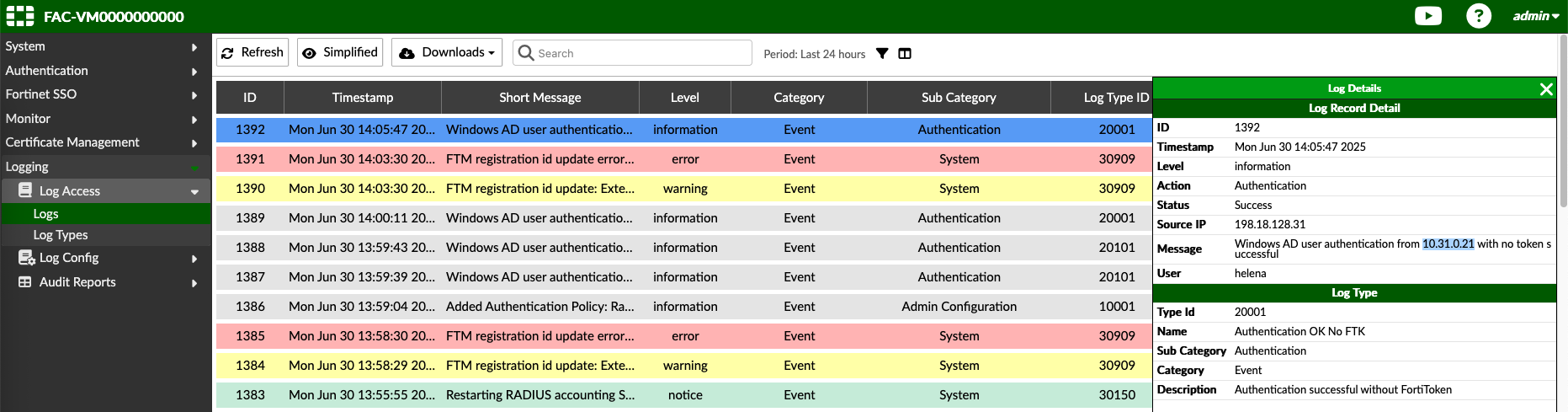
We can test the user credentials to make sure the integration is running
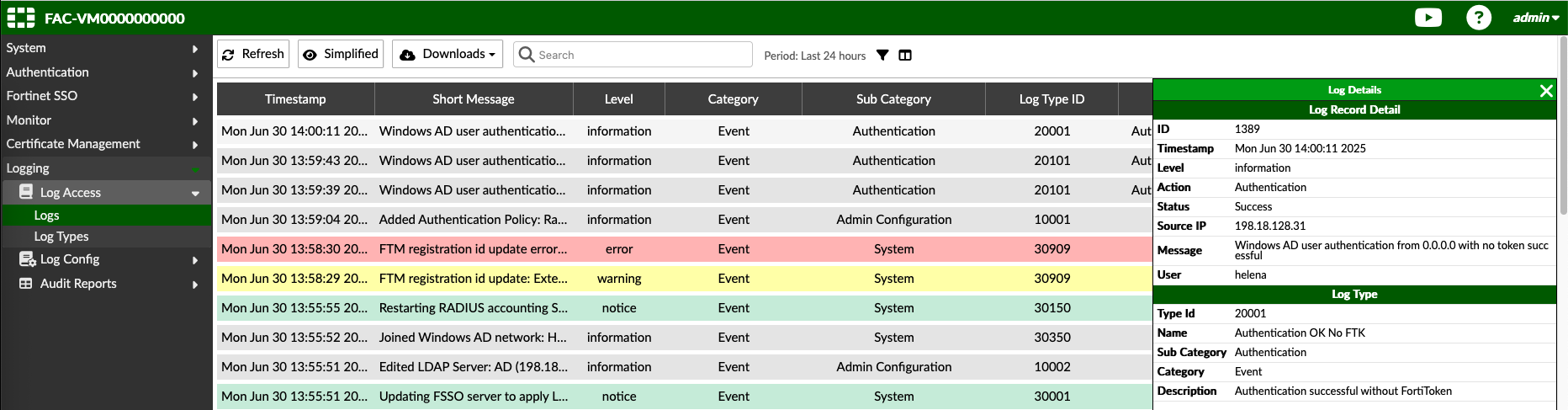
On the FAC, we can see the success log for the tested user
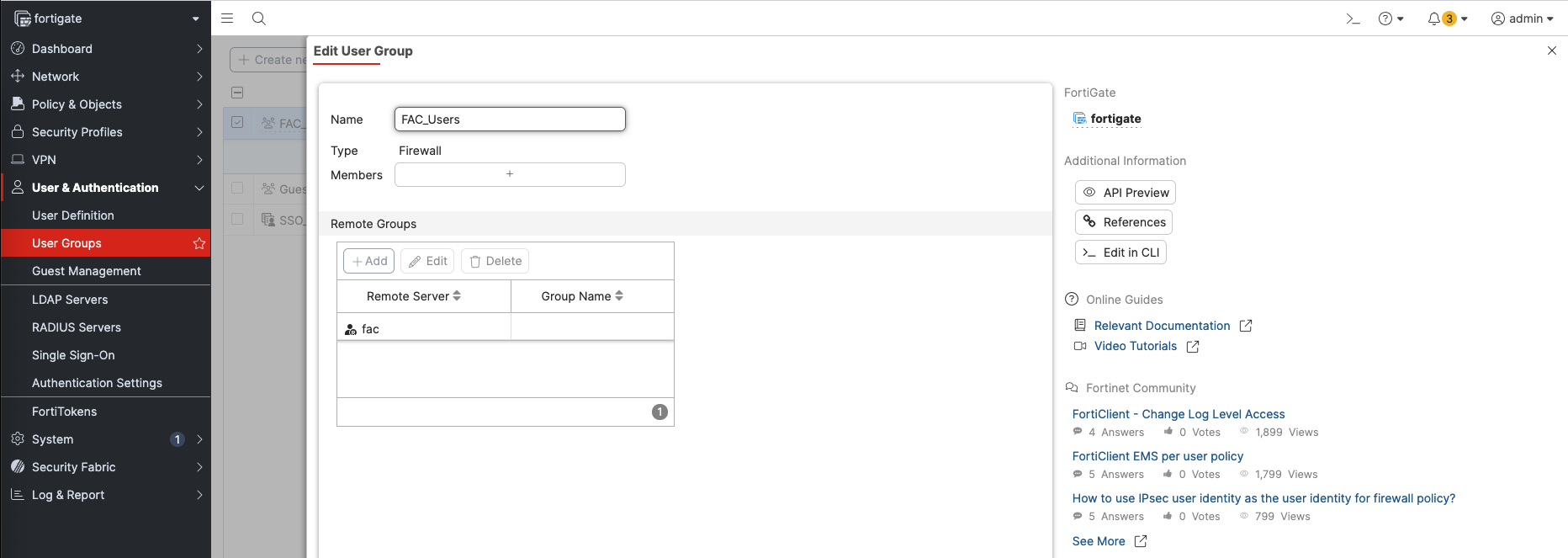
Next on Fortigate, create a new User Groups that points to the Radius Server created
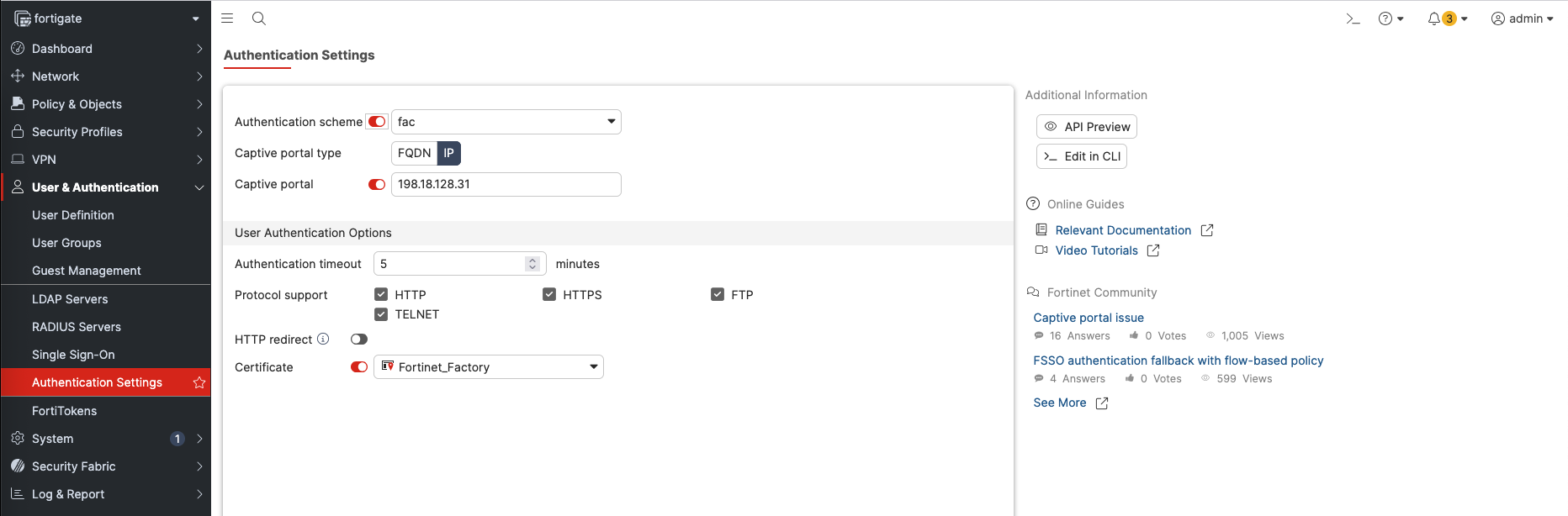
And on the Authentication Settings, we configure the Captive Portal to point to the same Radius Server, this portal will be used for users to enter their credentials
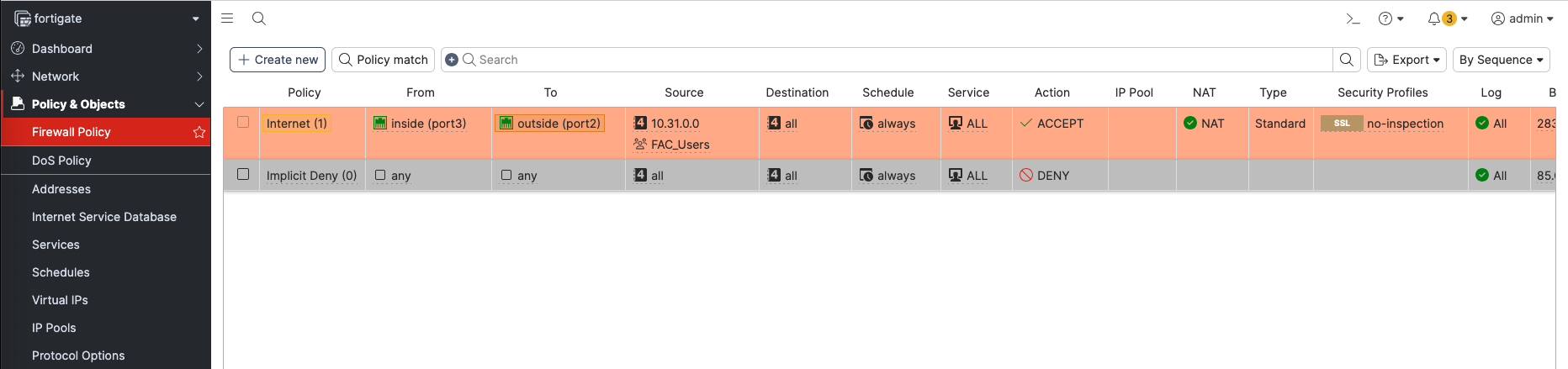
Finally, we can use the User Groups on the Firewall Policy
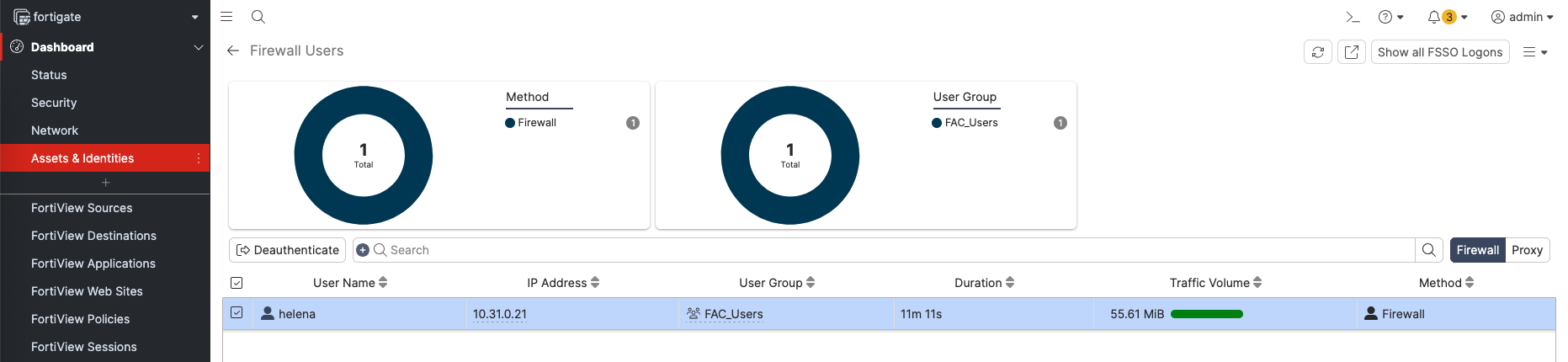
User Testing
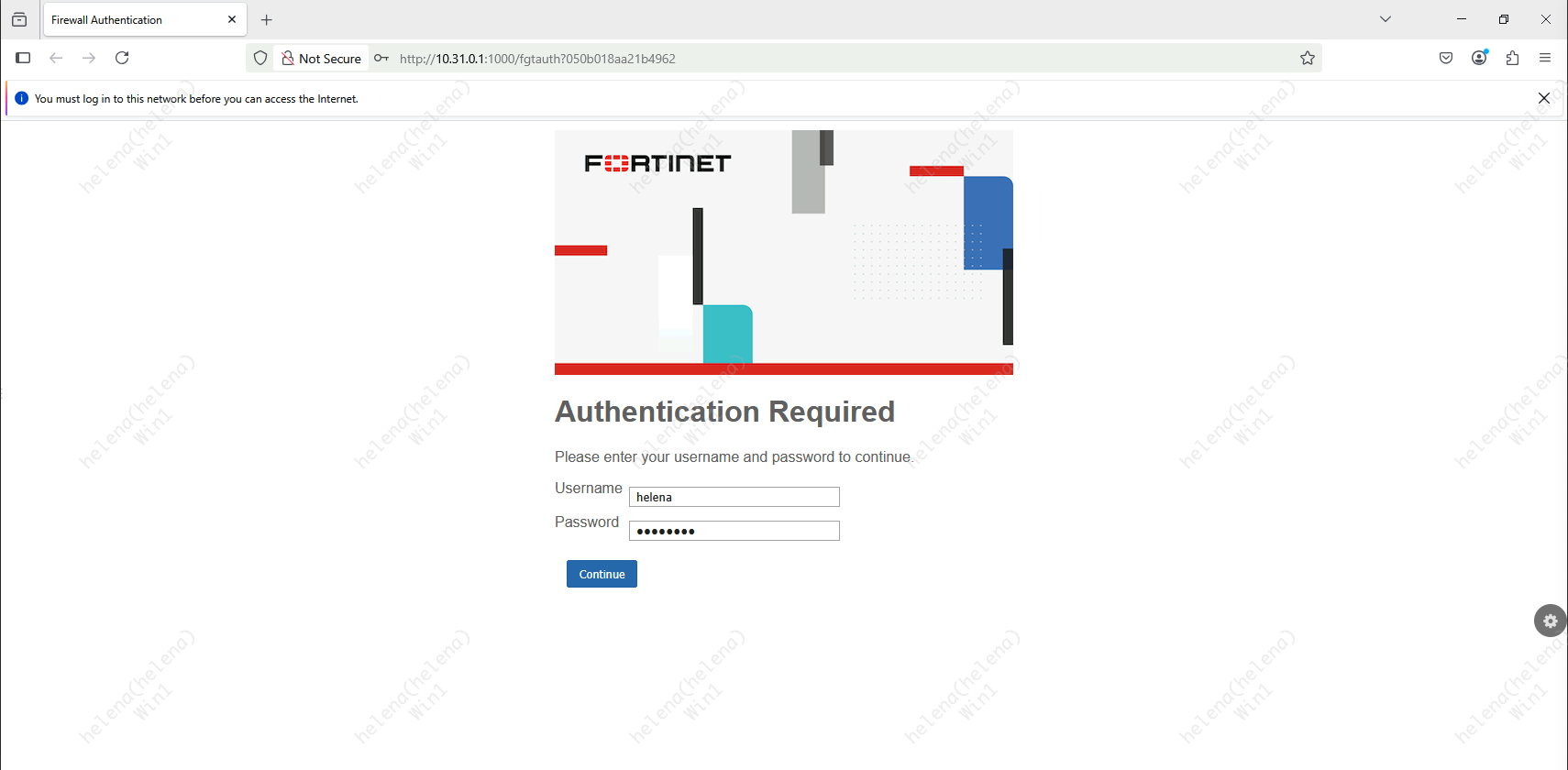
On the user end, when we try to access internet we will be redirected to the Captive Portal to authenticate
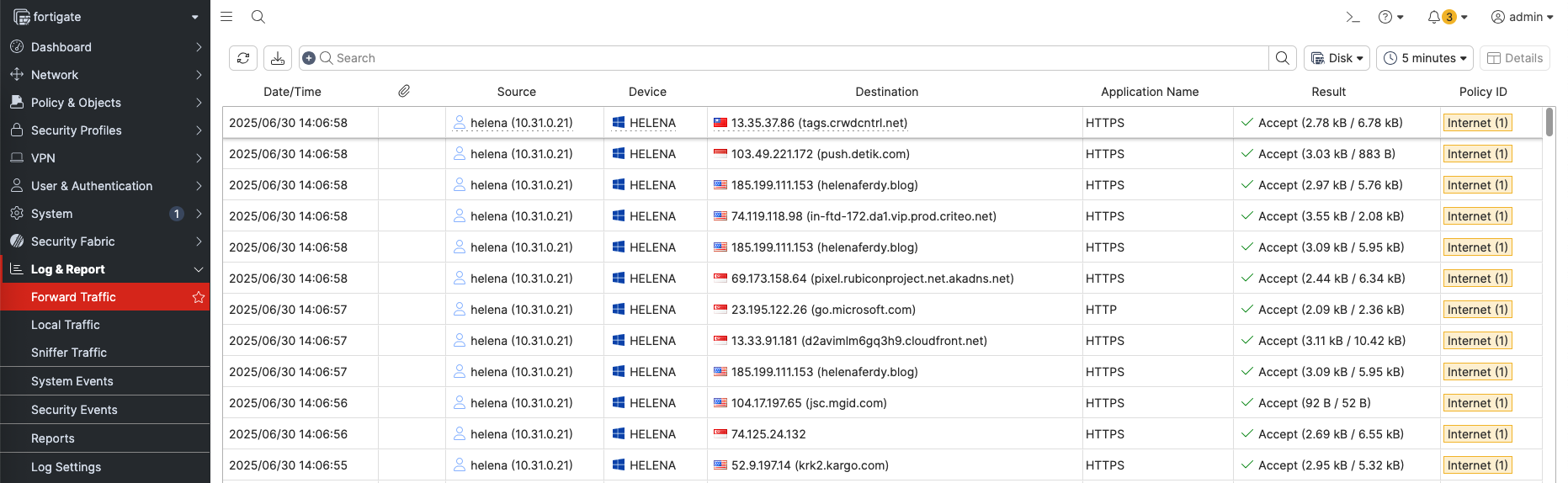
Once successfully authenticate, user is now granted access