FortiWeb WAF (Web Application Firewall)
FortiWeb is a Web Application Firewall (WAF) from Fortinet that protects web applications from threats like SQL injection, cross-site scripting (XSS), and other OWASP Top 10 attacks. It acts as a reverse proxy, inspecting and filtering incoming traffic before it reaches the backend servers. It also provides load balancing by distributing traffic from a single Virtual IP (VIP) to multiple web servers, enhancing performance, security, and availability.
Configuring FortiWeb
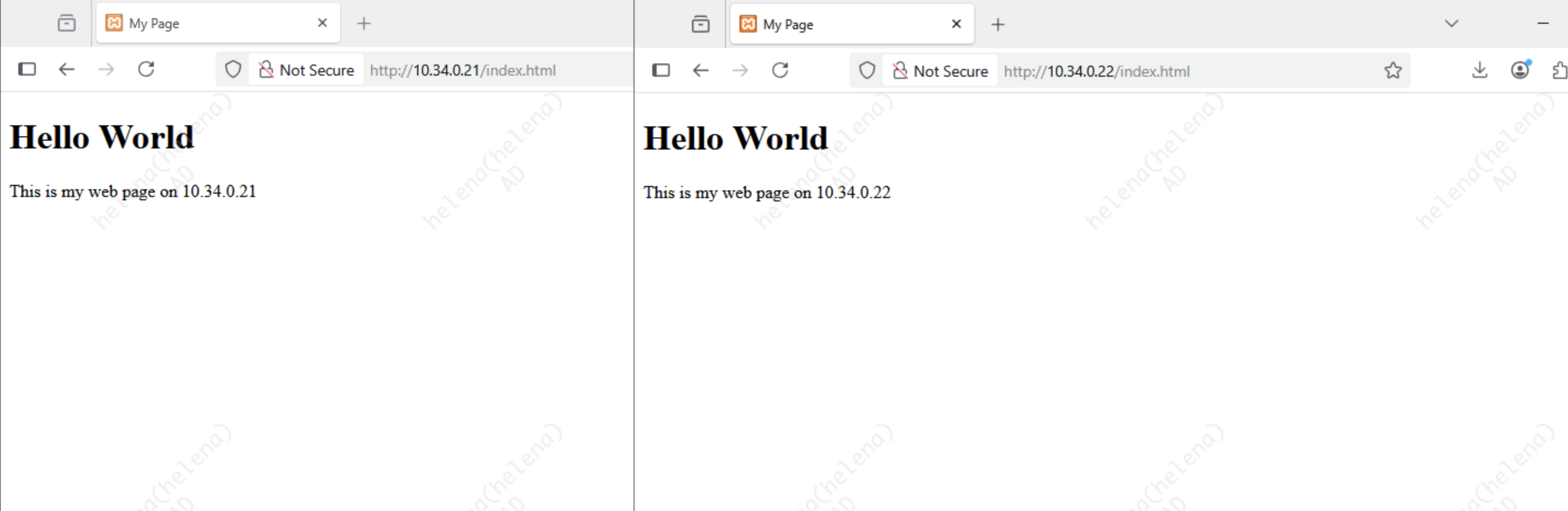
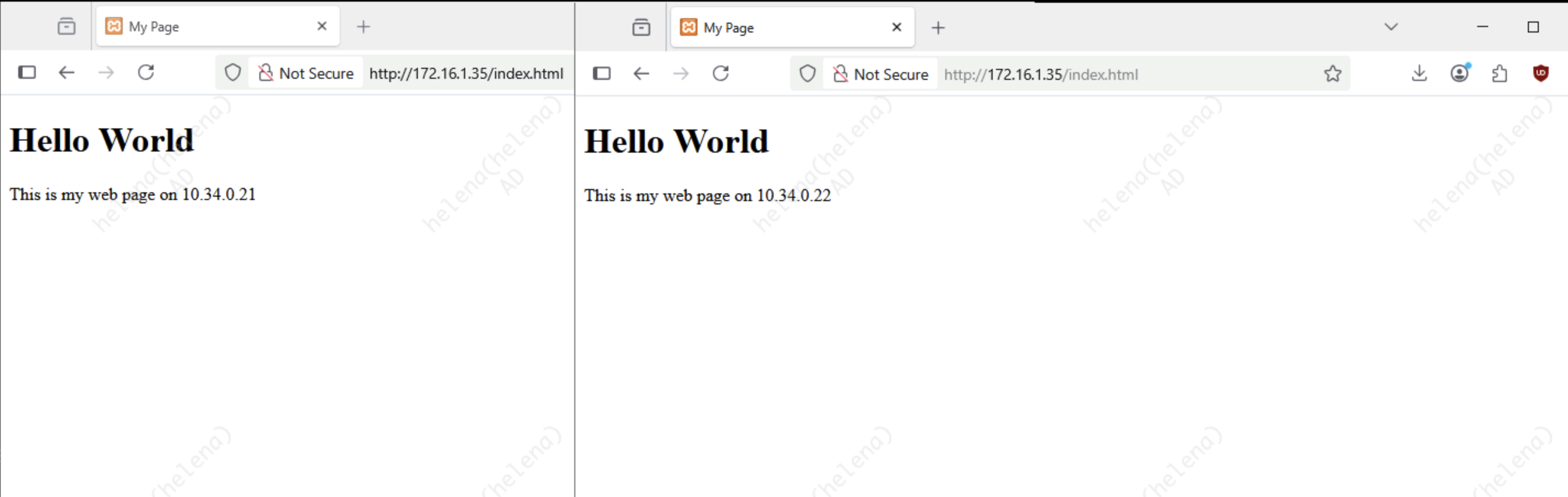
Here we have 2 web servers that we will load balance behind FortiWeb as a Reverse Proxy
Firstly we setup the FortiWeb like any other Fortinet products
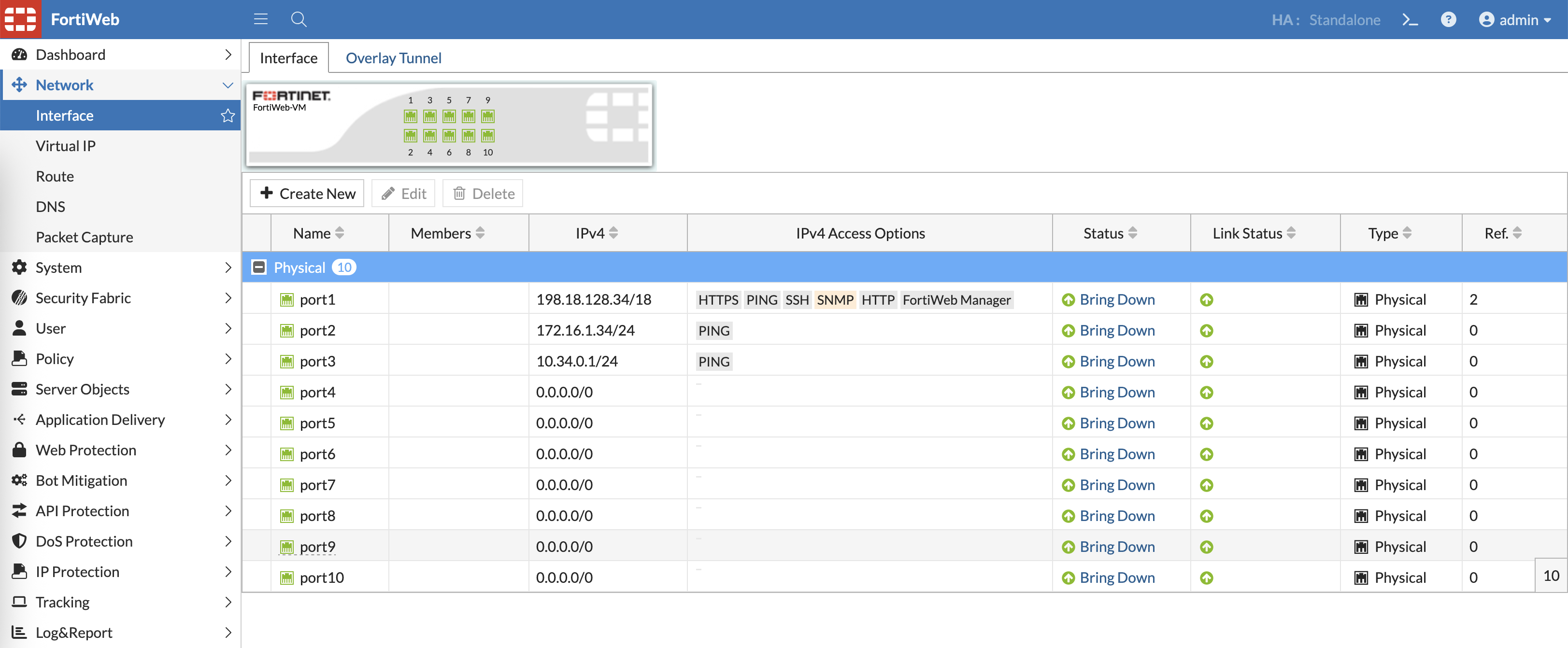
Then here we configure the interfaces for facing the web servers and also for the uplink as the Virtual IP
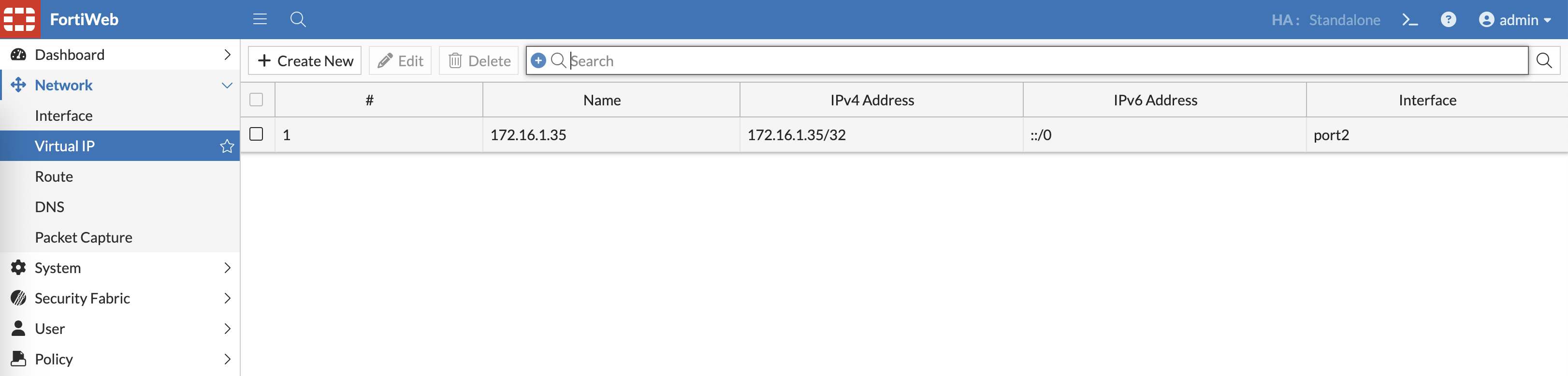
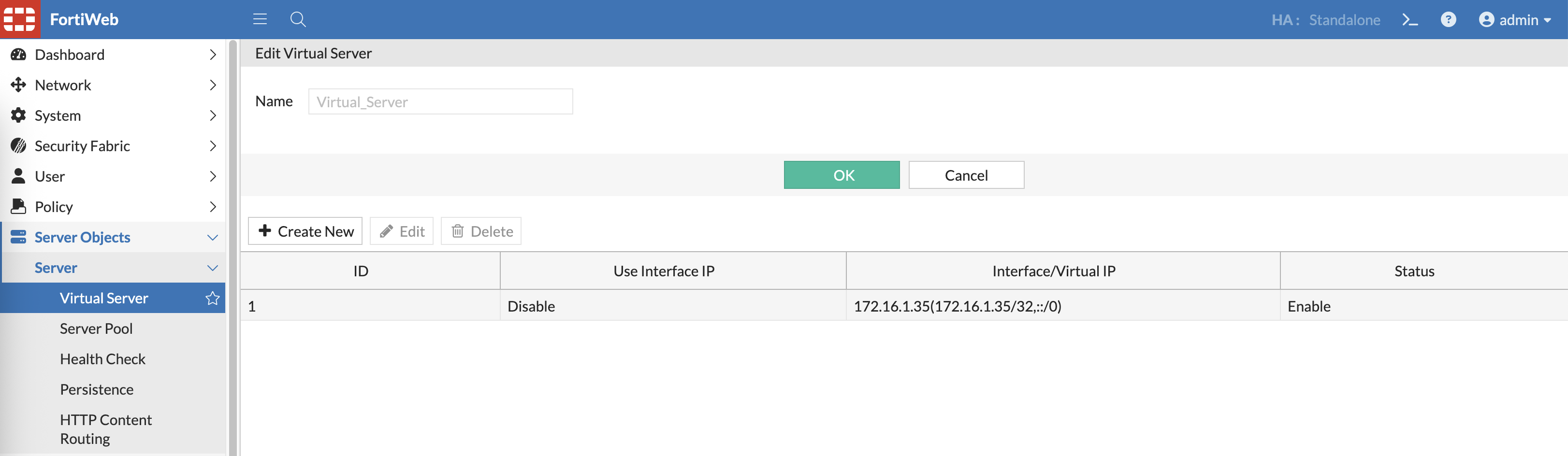
And we create the Virtual IP for the Web Server we’re about to configure
Next on Virtual Server, add the Virtual IP here
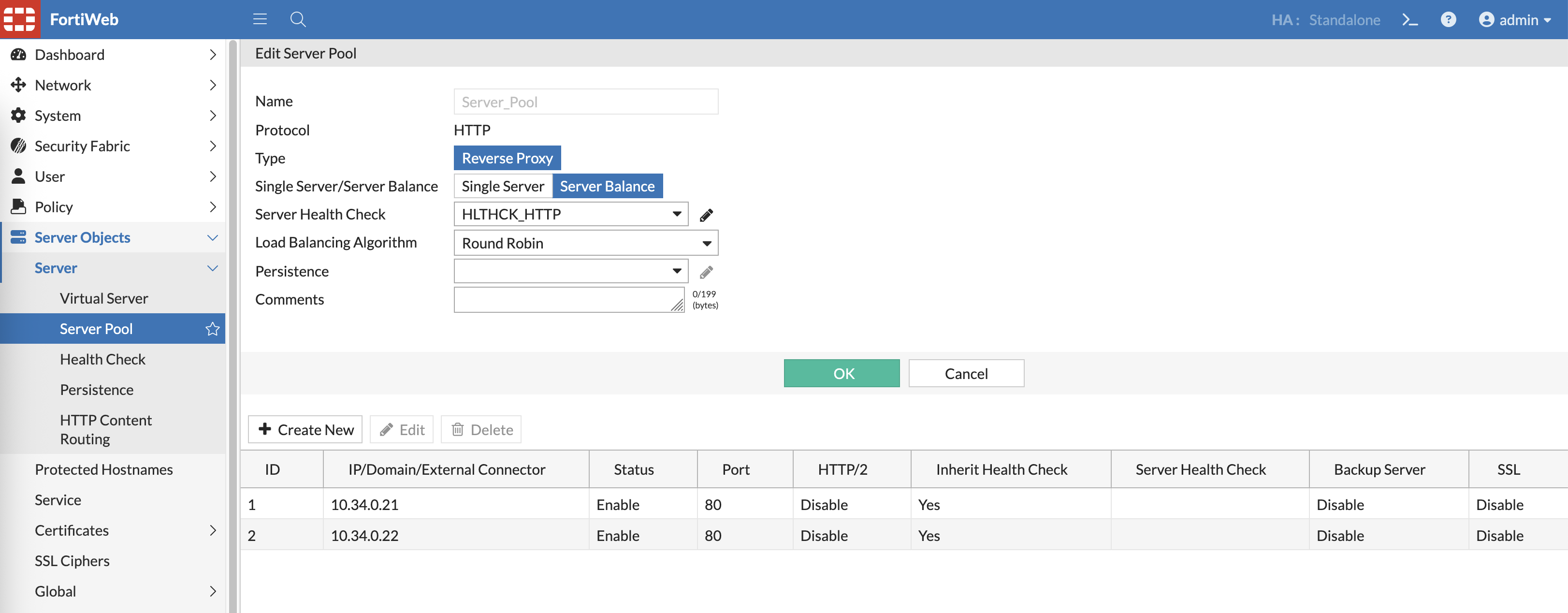
After that on Server Pool, add the 2 web severs to here to be load balanced with round robin algorithm
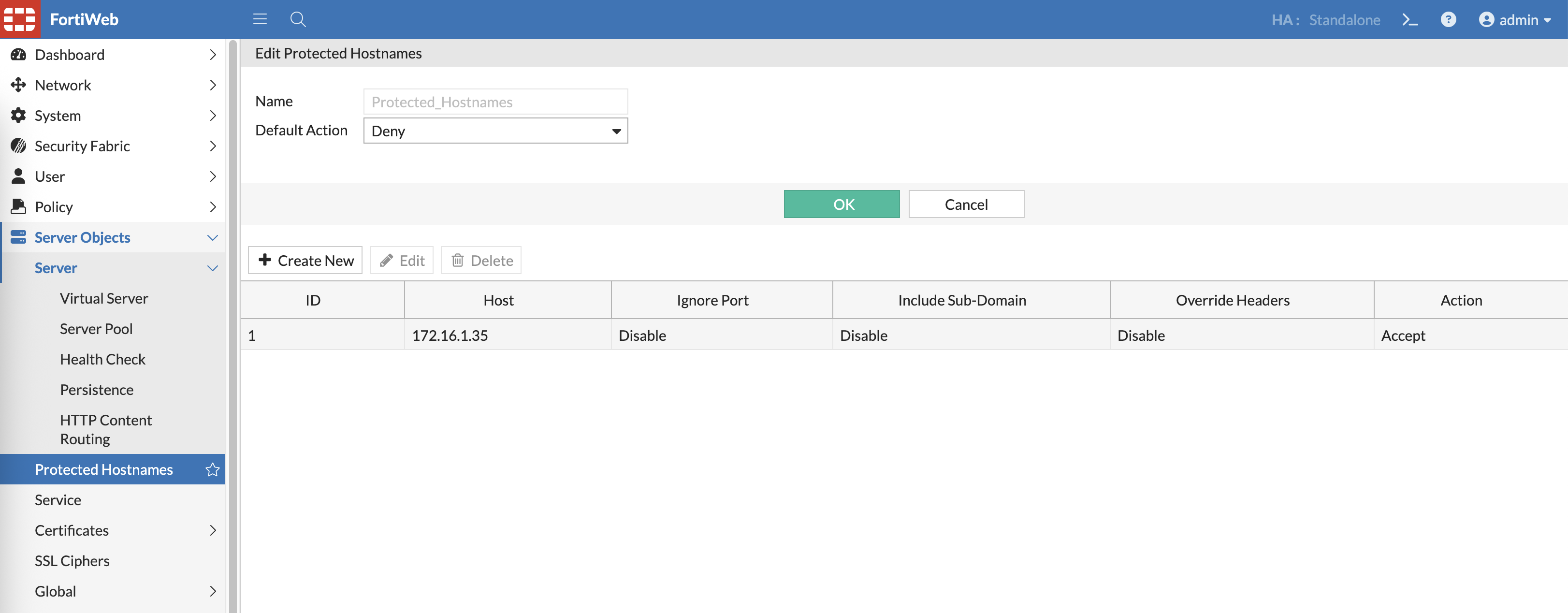
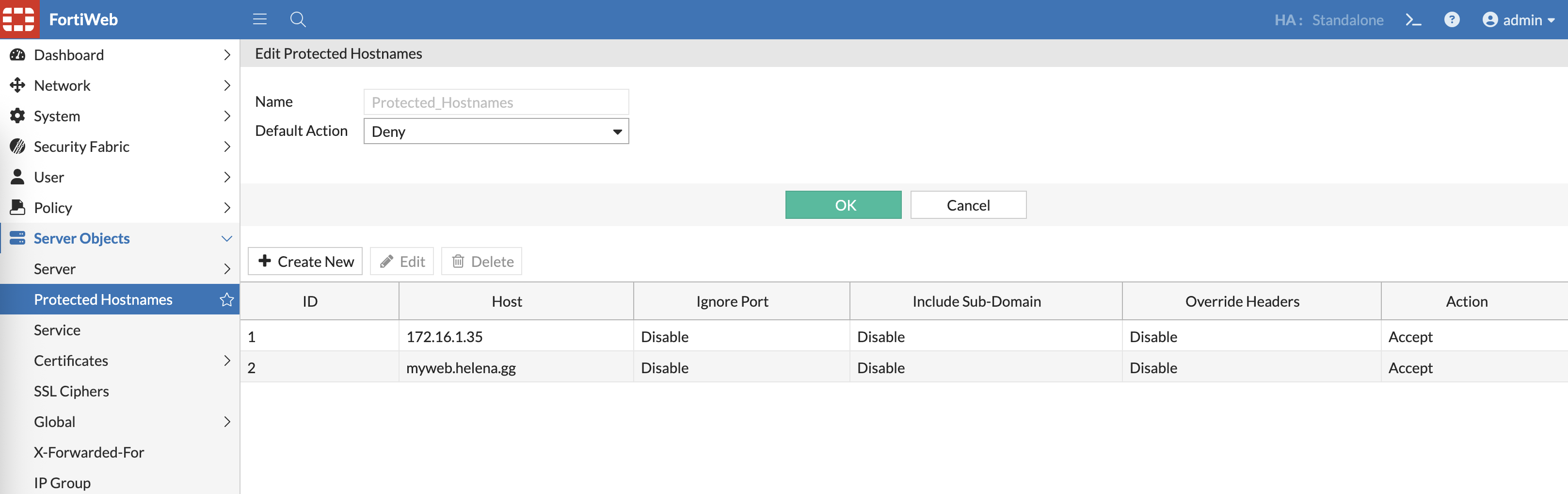
And optionally, we can add Protected Hostnames to whitelist the allowed hostnames / ip addresses to be accessed
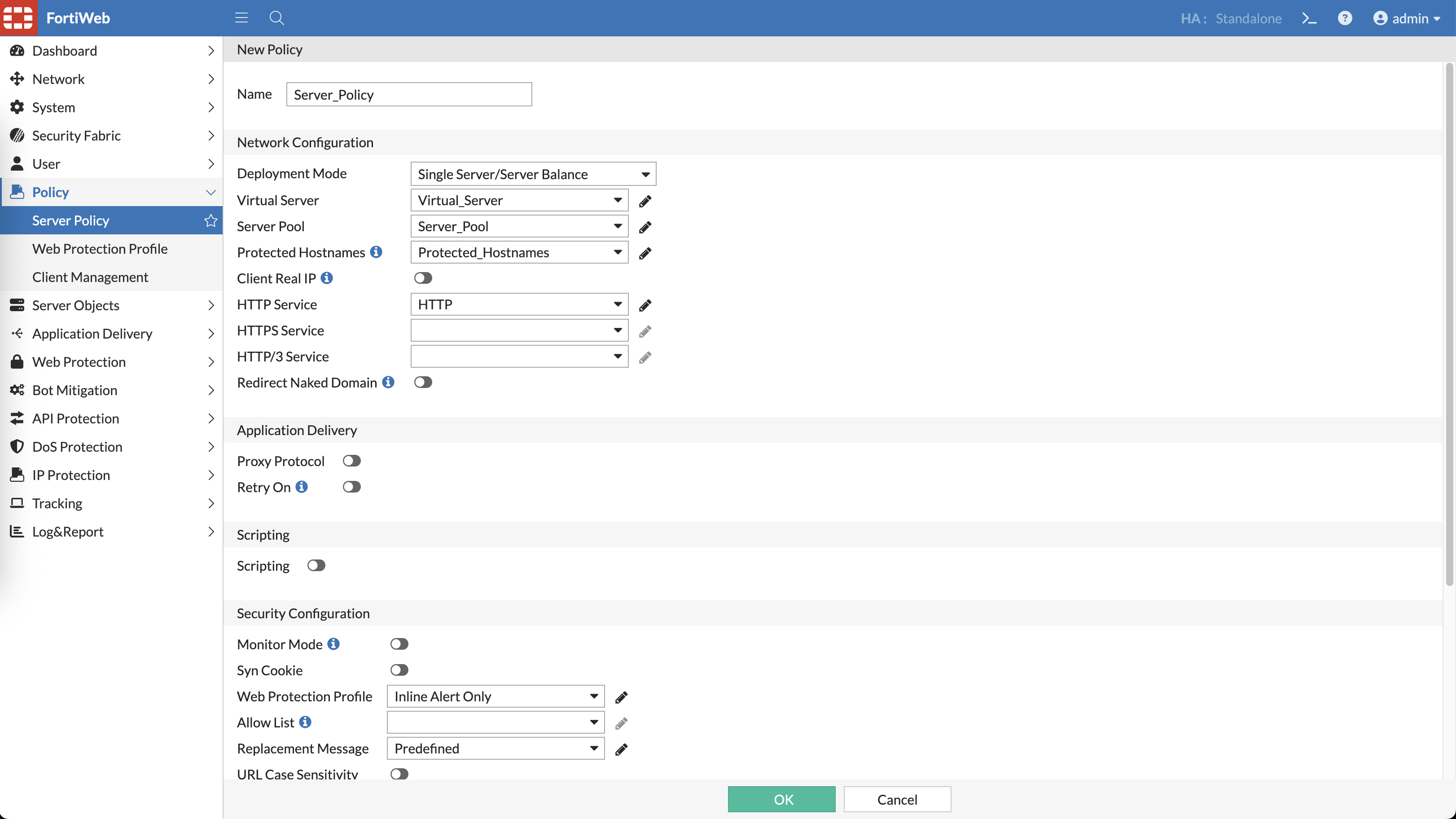
Now we can use all the configured parameters inside a Server Policy, here we only enable HTTP for now, and for simplicity we will use predefined ‘Inline Alert Only’ for Web Protection Profile
That’s pretty much it, the web servers are now served and load balanced behind FortiWeb’s Virtual IP
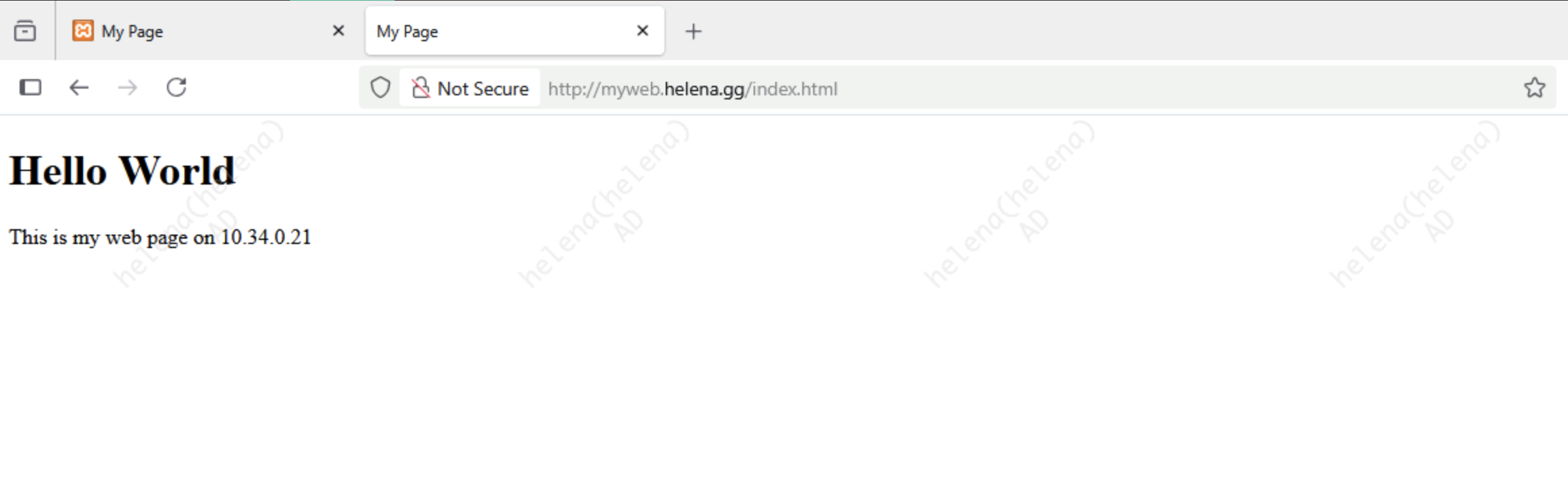
Now we also want to access it using FQDN, lets whitelist it on Protected Hostnames
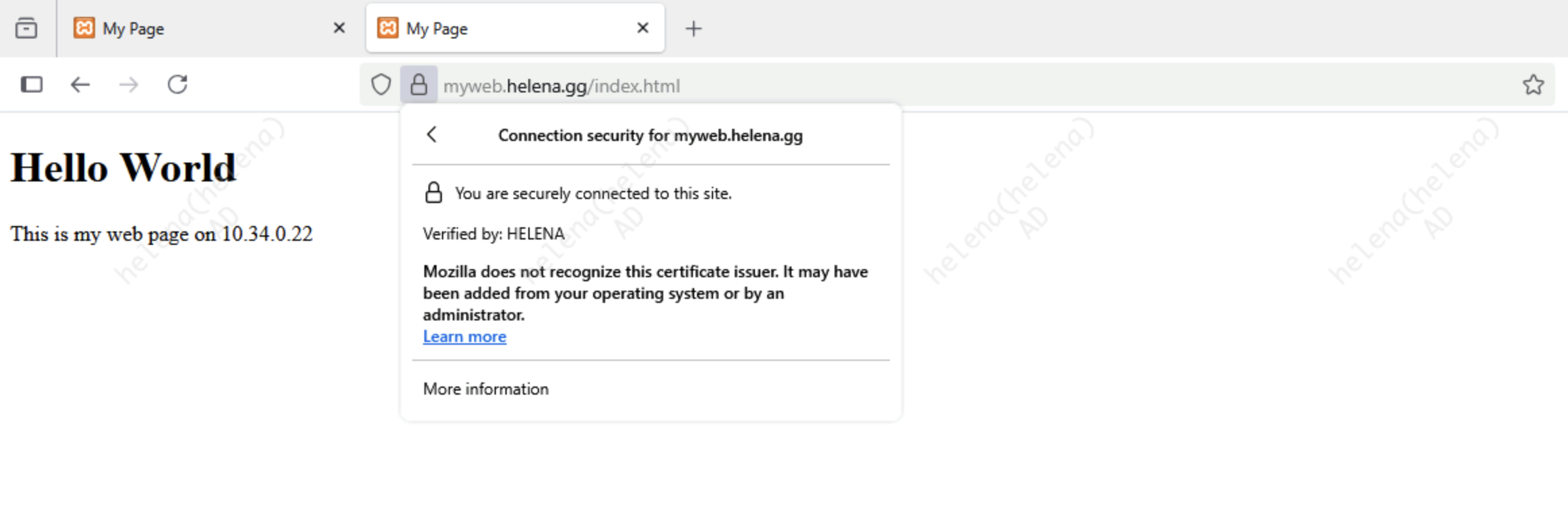
And its now accessible using FQDN as well
Configuring HTTPS for SSL Offloading
SSL offloading on FortiWeb means it handles SSL/TLS encryption and decryption, reducing the load on backend servers. It allows FortiWeb to inspect HTTPS traffic for threats before forwarding it to the web servers.
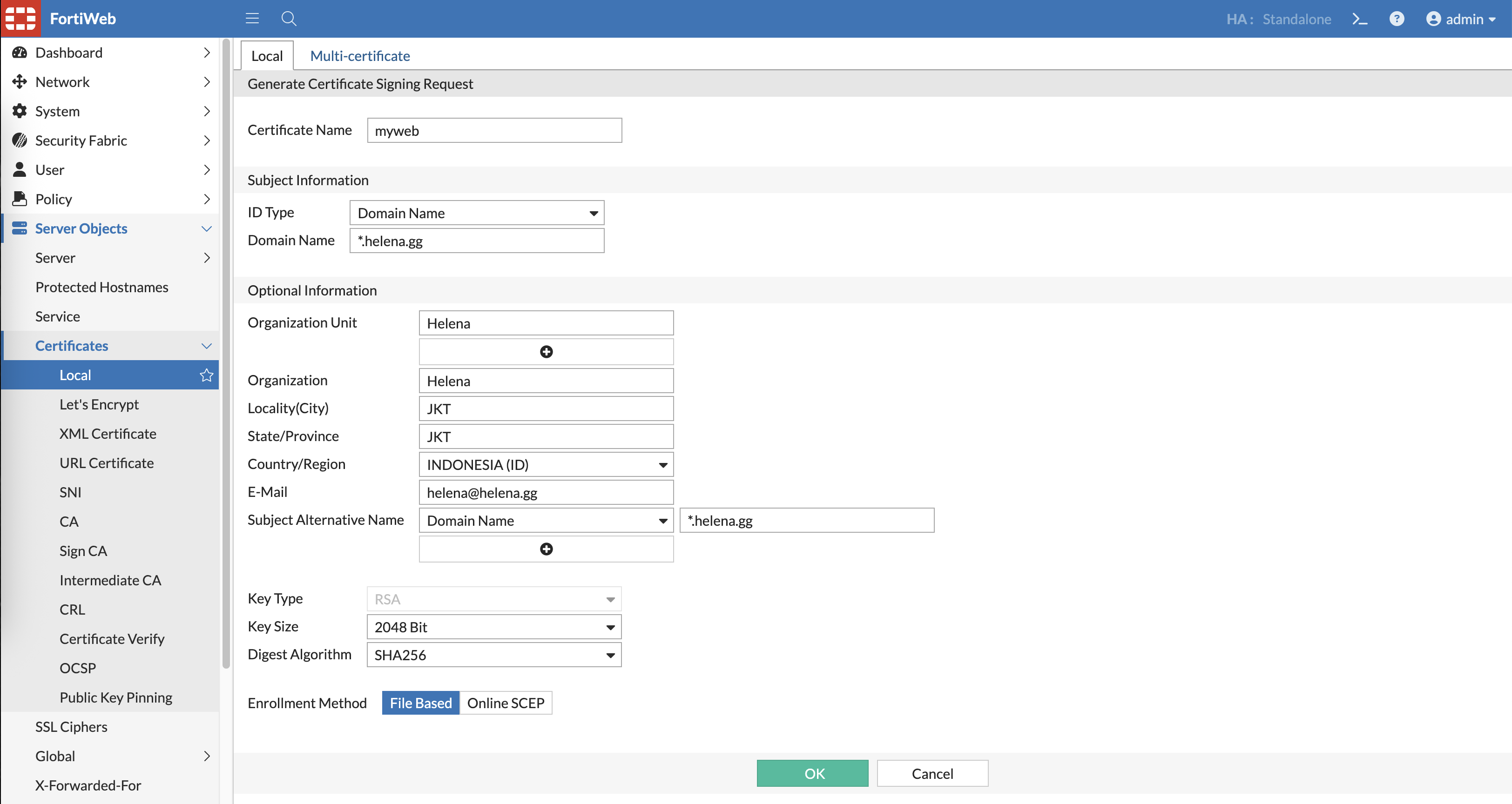
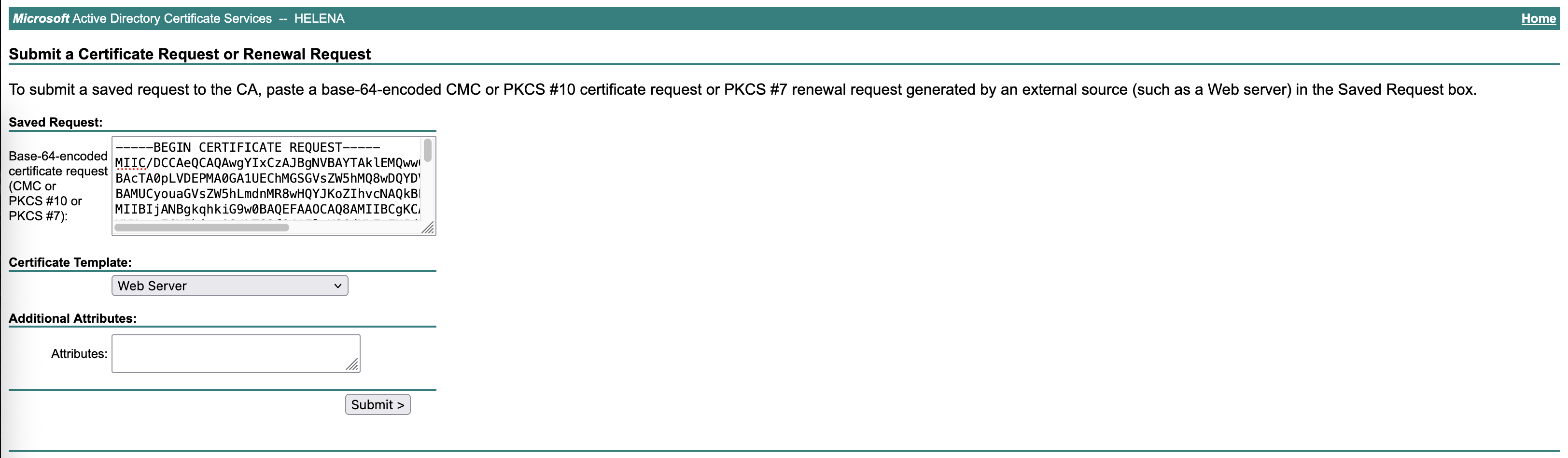
First we need to generate a CSR for Certificate Signing, we’ll use a wildcare domain name so it can be used for multiple web servers for future use
Then sign it on CA Server
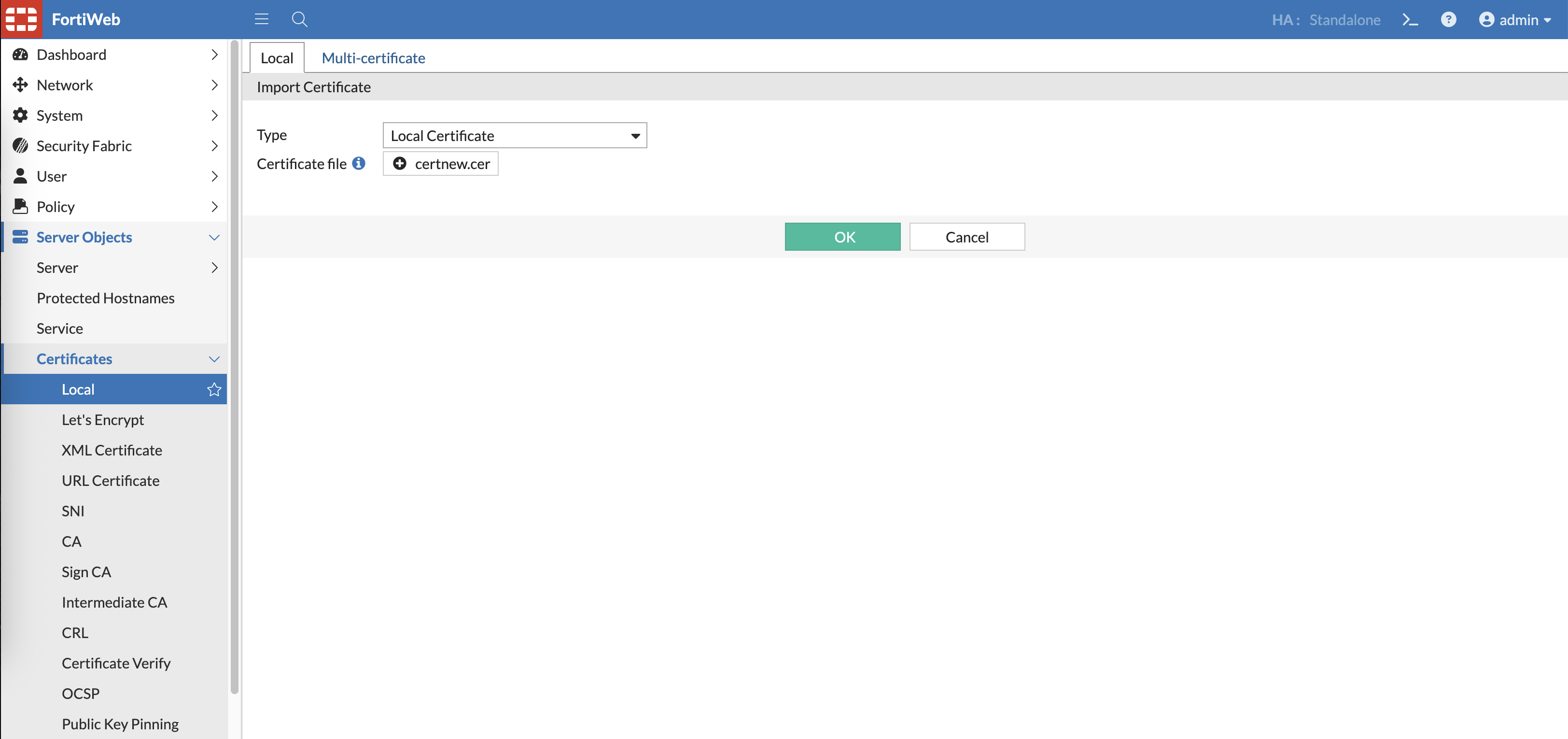
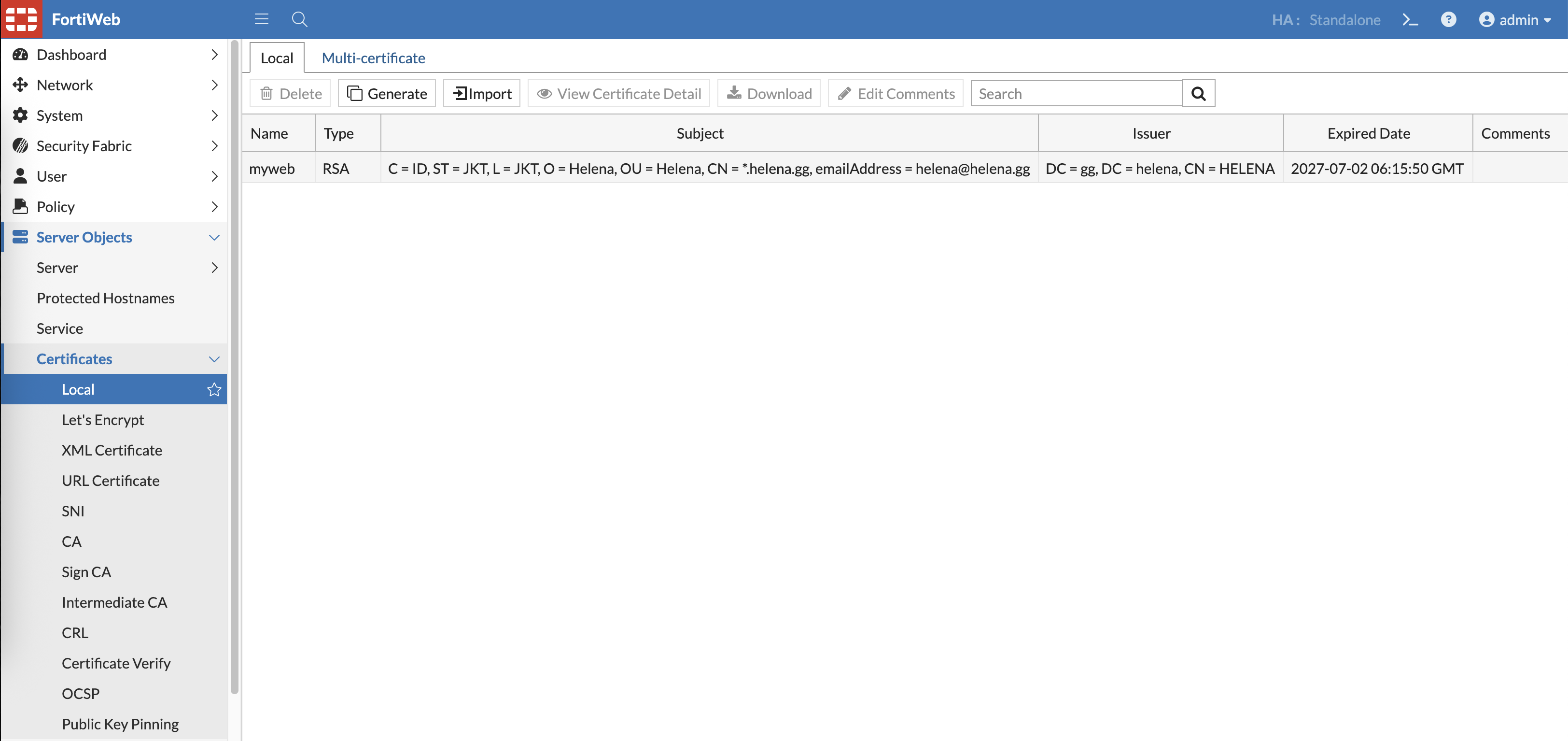
And import it as Local Certificate
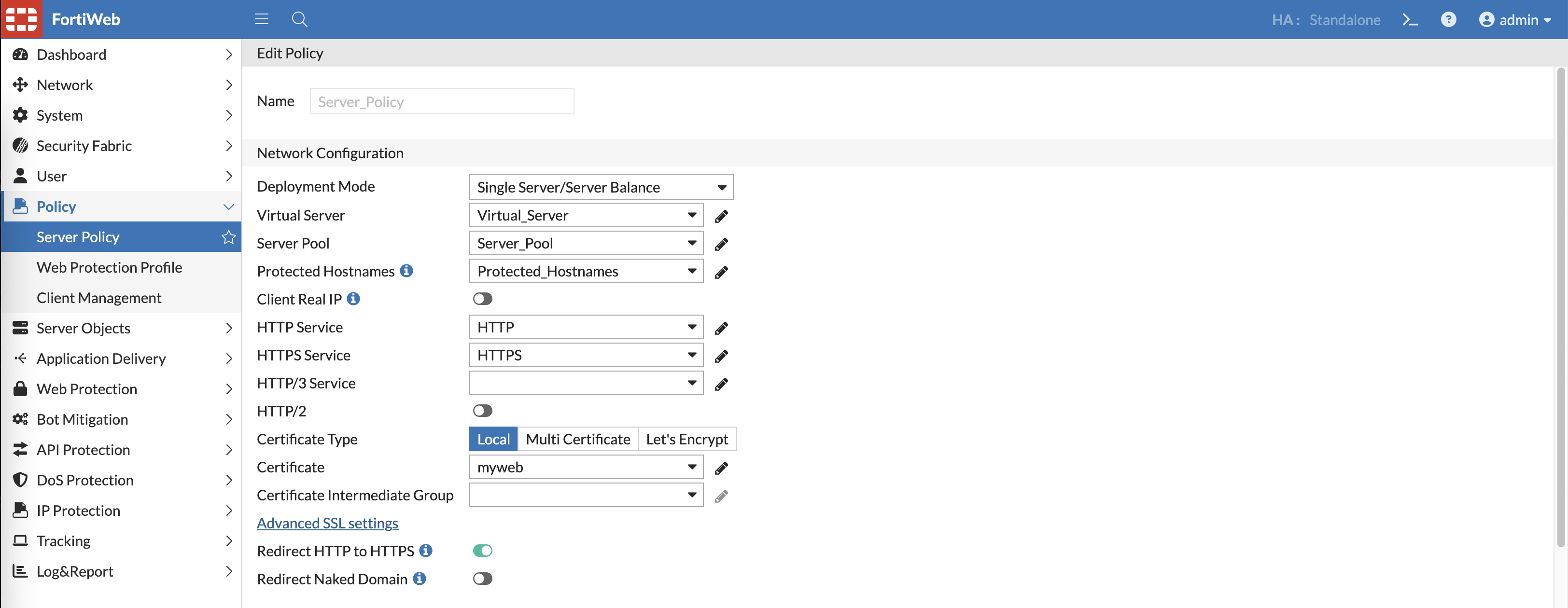
Back on Server Policy, now we can enable HTTPS and use the Local Certificate
And the traffic is now secured with HTTPS with valid certificate