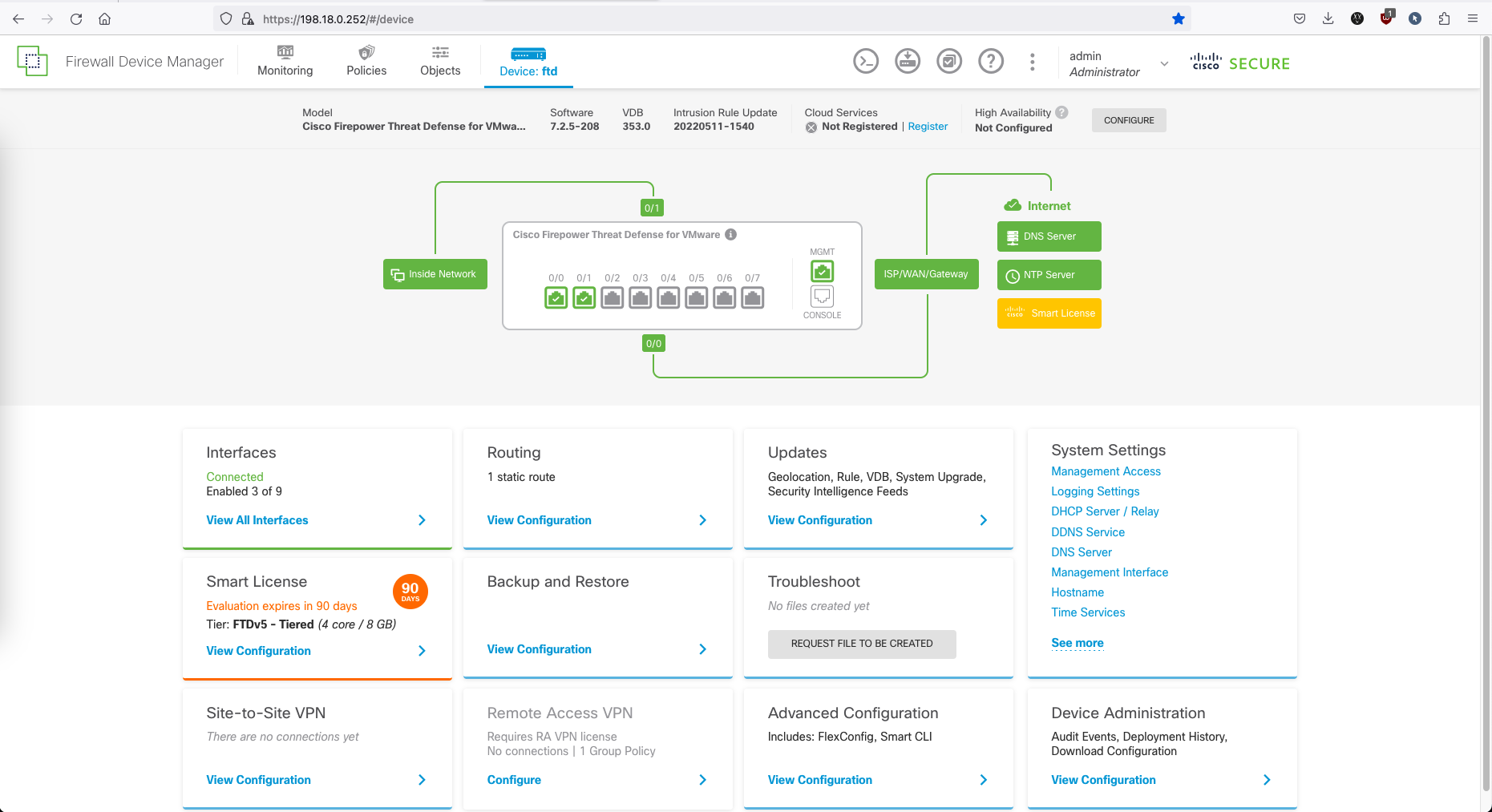
Cisco Firepower Threat Defense (FTD)
Cisco Firepower Threat Defense (FTD) is a security product offered by Cisco Systems. It combines firewall capabilities with advanced threat detection and prevention features. FTD is designed to protect networks and data centers from a wide range of cyber threats, including viruses, malware, intrusions, and other security risks.
Network Topology
Here’s the topology for this FTD deployment
Installing Firepower Threat Defense
First, download the installer on Cisco Download Central
Deploy the OVA, configure the management access
set the admin password
configure the management interface
Then boot up the VM
Accessing Firepower Threat Defense
After a minutes, the GUI should be accessible on the management interface
Configure the outside interface that has an access to internet
Configure the NTP
Then select the licensing type
Lastly, choose the deployment type, in this case we’ll use standalone
Now Cisco Firewall Threat Defense is up and running
Configuring Interfaces
On Interface, edit and configure the inside interface
This is the interface configuration for now
Deploy the config
Now if we try accessing both the Outside or Inside Interface from their respective network, they should all be accessible
Configuring NAT for Internet Access
On Policies » NAT, add new to allow dynamic translation from inside network to the outside interface
Then on Policies » Access Rules, add new rule to allow traffic from the inside to outside zone
Now on client’s PC on the inside network, we should have an internet connection
On Monitoring » Events, we can see the traffic from inside host to the internet
Clicking on the events show more details regarding the traffic
We can also see other monitoring stats which is pretty neat and handy
Configuring Static Destination NAT
Now we’re setting up a destination NAT so the inside host can be accessed using the outside public IP Address
On Policies » NAT, add a new Static NAT coming from outside to inside with the specified destination IP address
Then on Policies » Access Rules, add new rule to allow traffic from the outside to inside zone
Now if we try accessing the public IP, we should be connected to the inside host
And on Monitoring » Events, we can also see the translated traffic coming from outside here