Cisco FTD Malware & File Policy
Cisco FTD’s Malware & File Policy is designed to detect and control file transfers across the network and protect against malware. It inspects files based on type, size, and direction (upload/download), and can block, allow, or log them. When enabled with AMP (Advanced Malware Protection), it uses Cisco’s global threat intelligence (Talos) to perform reputation checks, sandbox analysis, and retrospective detection—allowing the system to detect and respond to files that later prove malicious. This helps organizations stop malware at the gateway before it reaches endpoints.
Enabling SSL Decrytion
Enabling SSL decryption is essential for inspecting HTTPS traffic, which is encrypted by design. Without decryption, FTD cannot analyze the contents of the traffic, allowing threats such as malware or data exfiltration to go undetected. By decrypting SSL, FTD can inspect encrypted sessions, enforce security policies, and detect threats hidden inside HTTPS traffic.
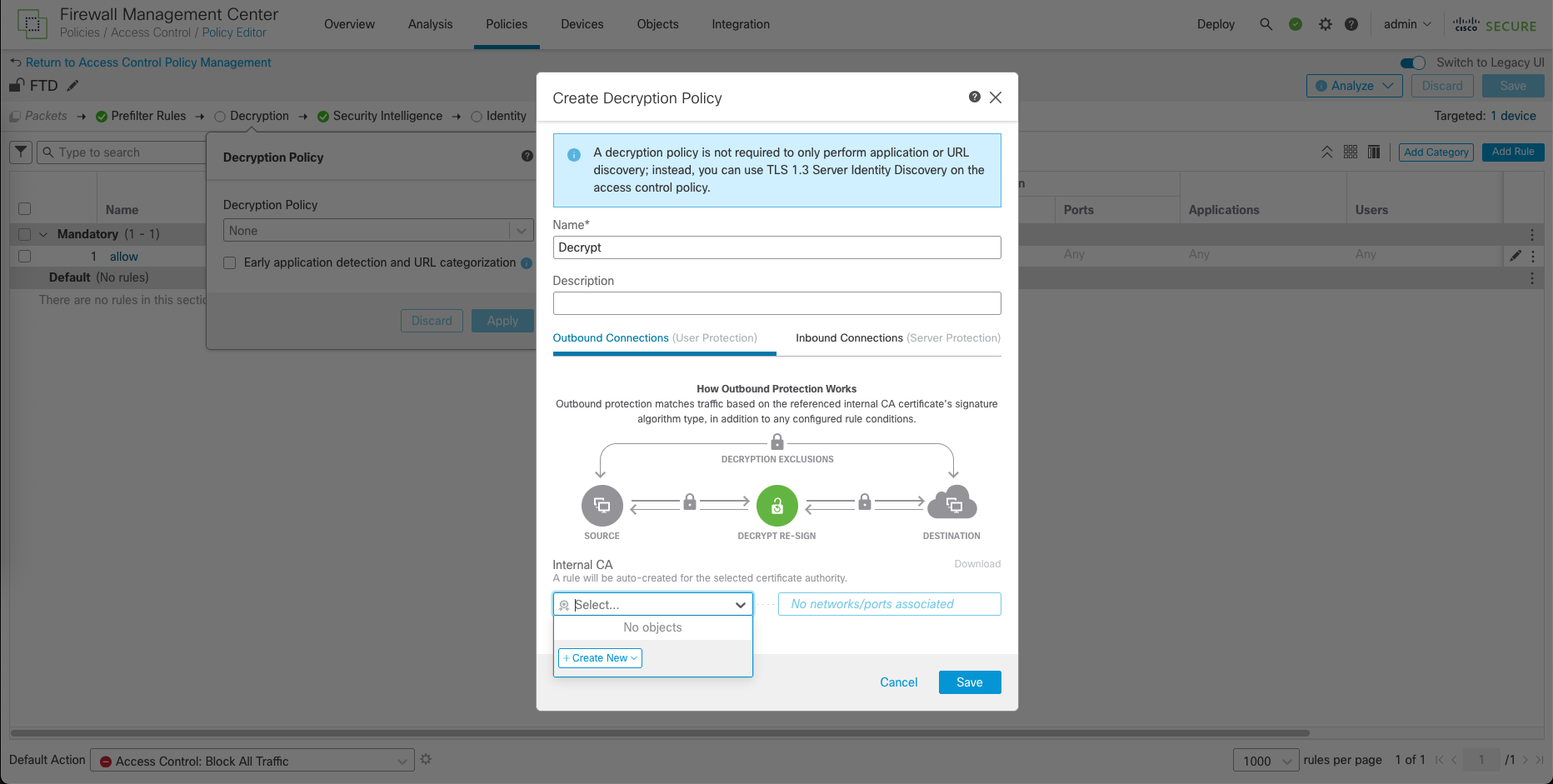
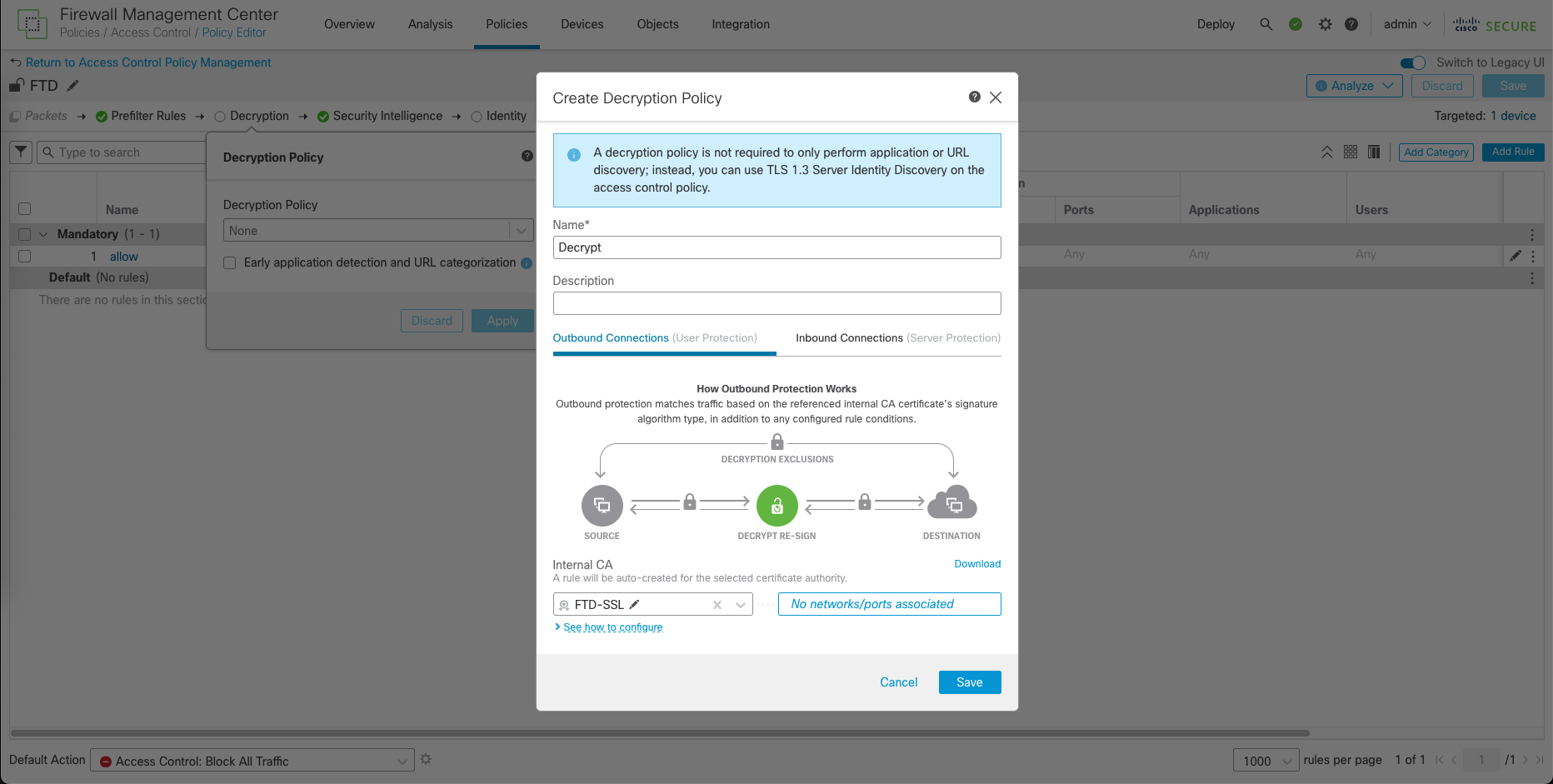
To enable SSL Decryption, on Policies » Access Control » Decryption, create new policy
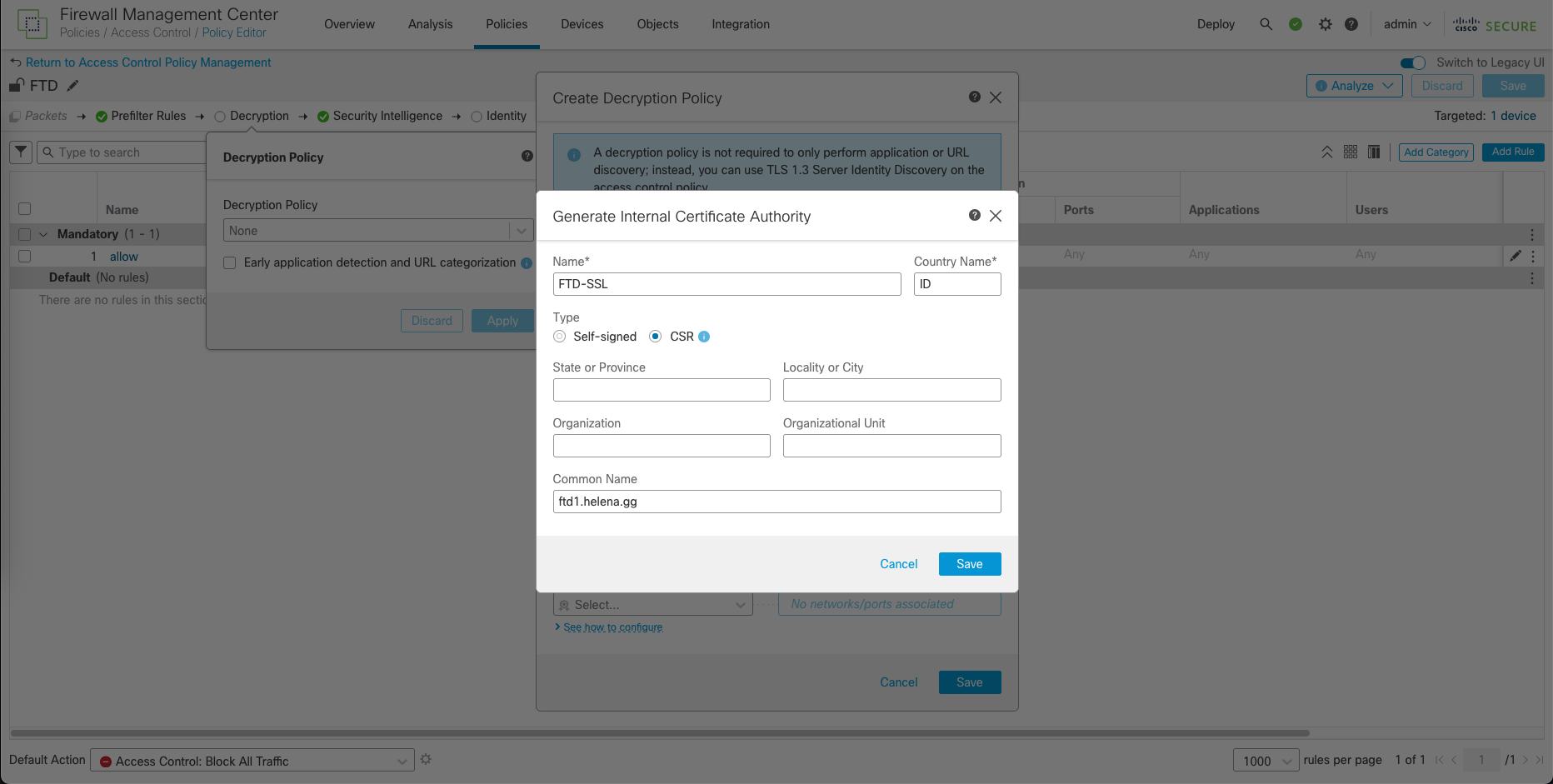
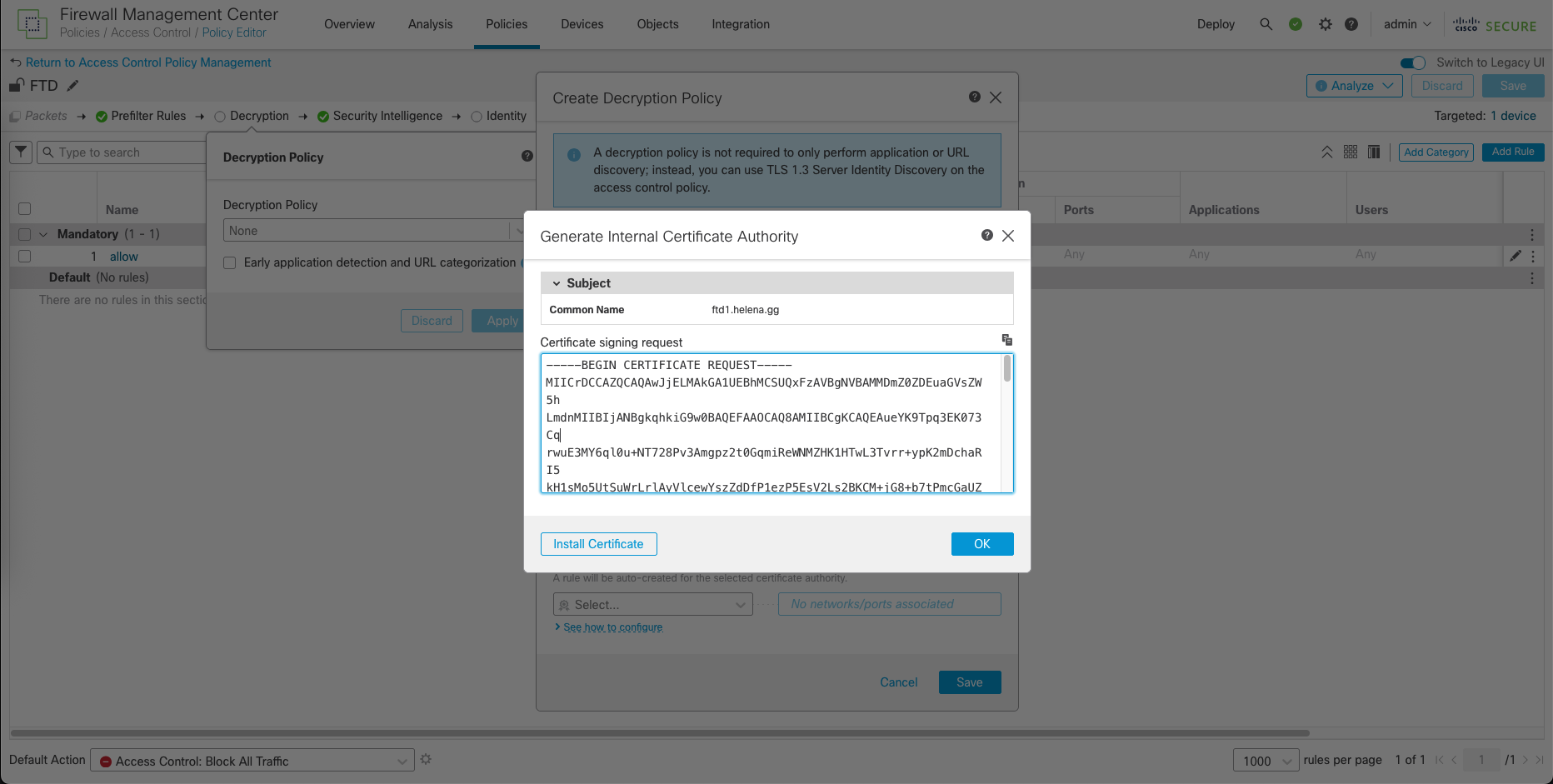
Here we will generate a new CSR for Certificate
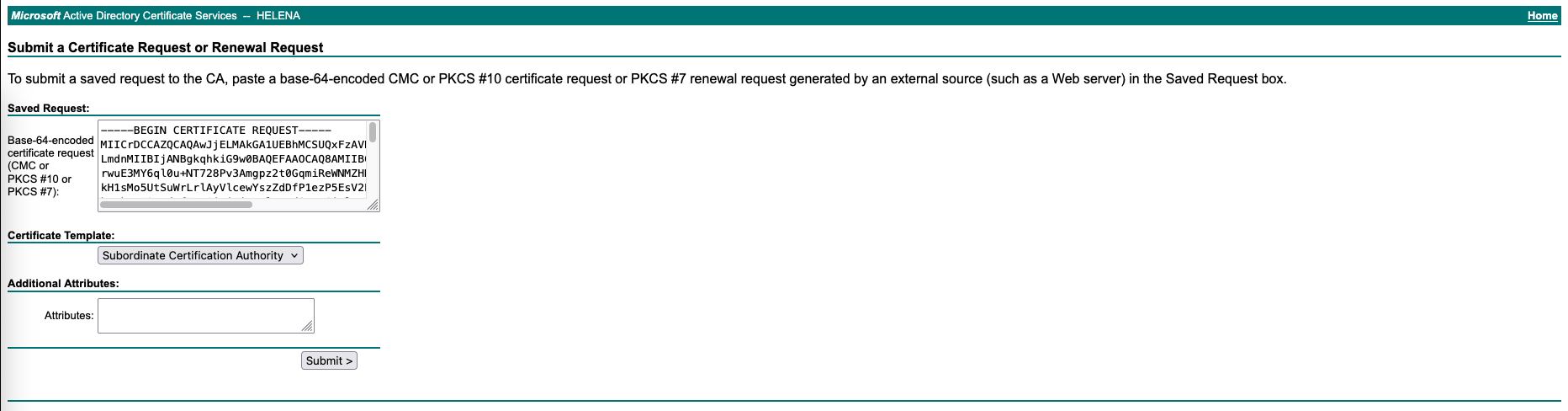
Sign the CSR on CA Server with template Subordinate Certificate Authority
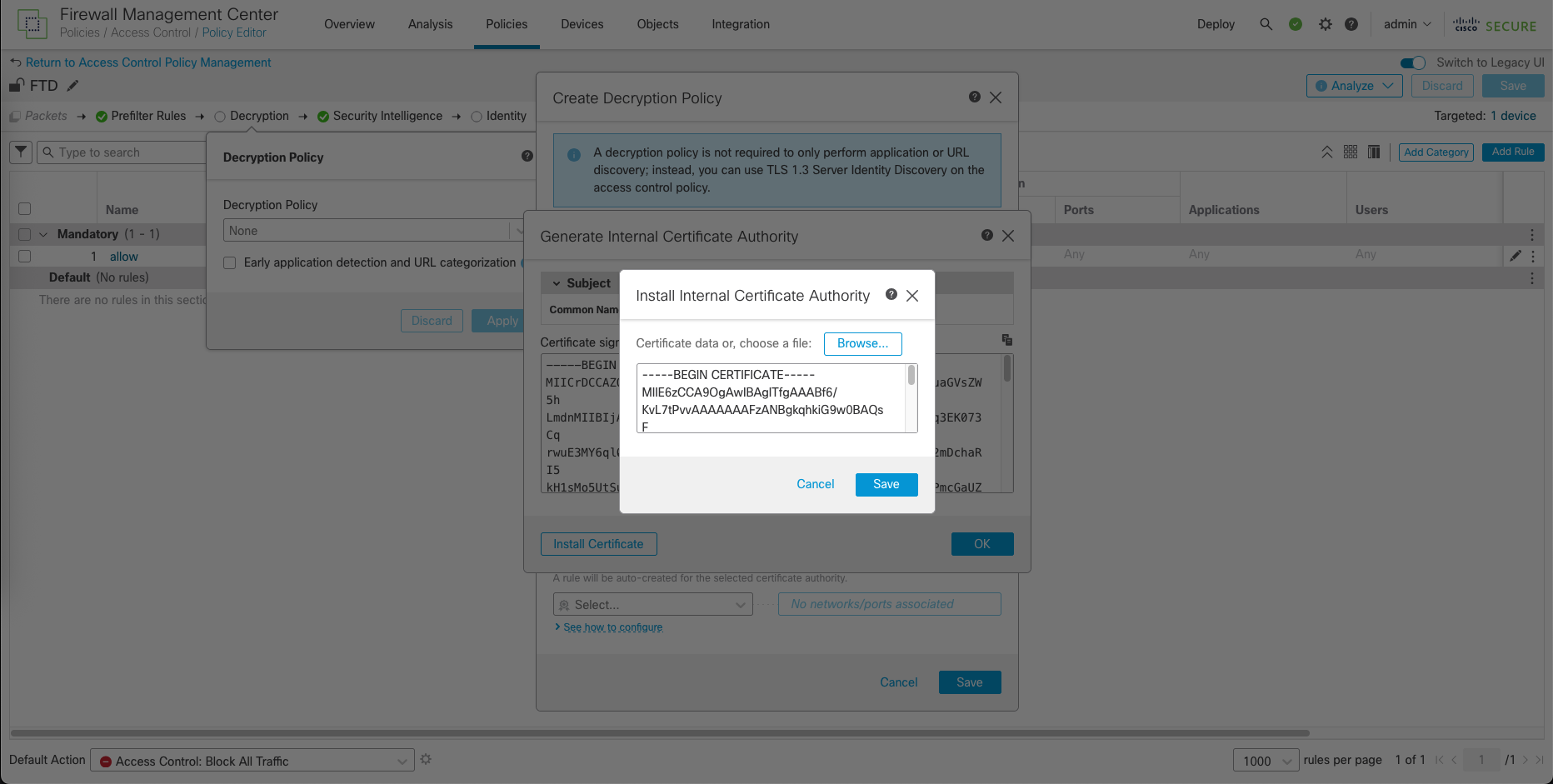
Then install the signed certificate
And now we have a working and running Decyption Policy
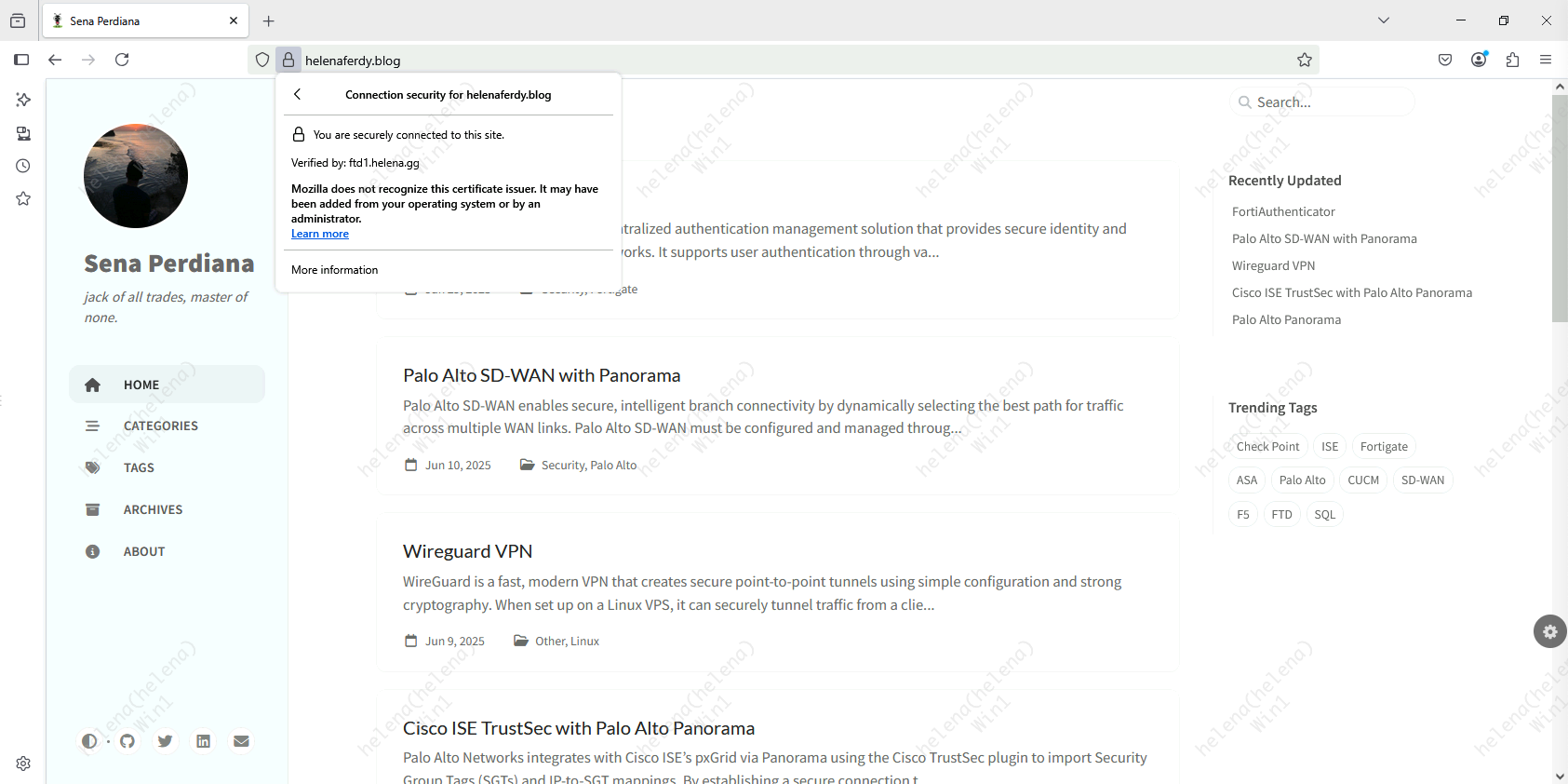
On client side, when we try accessing internet now the certificate will show verified by FTD
Configuring Malware & File Policy
Right now we dont have any Malware & File Policy enabled, allowing clients to download any malware on the internet
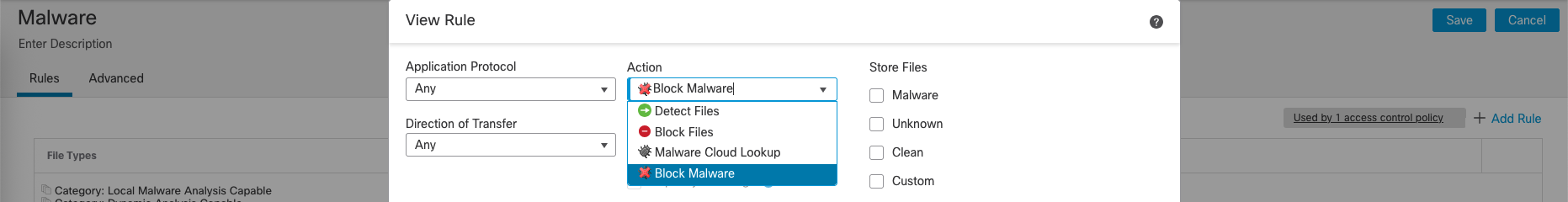
Create a new Malware Policy, here FTD has 4 main modes for action, we will select ‘Block Malware’ here
- “Detect Files” is for visibility and logging without intervention.
- “Block Files” is for preventing specific file types from being transferred, regardless of whether they are malicious.
- “Malware Cloud Lookup” is for identifying known malware using cloud intelligence.
- “Block Malware” is for actively preventing known malicious files from being transferred, often leveraging cloud intelligence for identification.
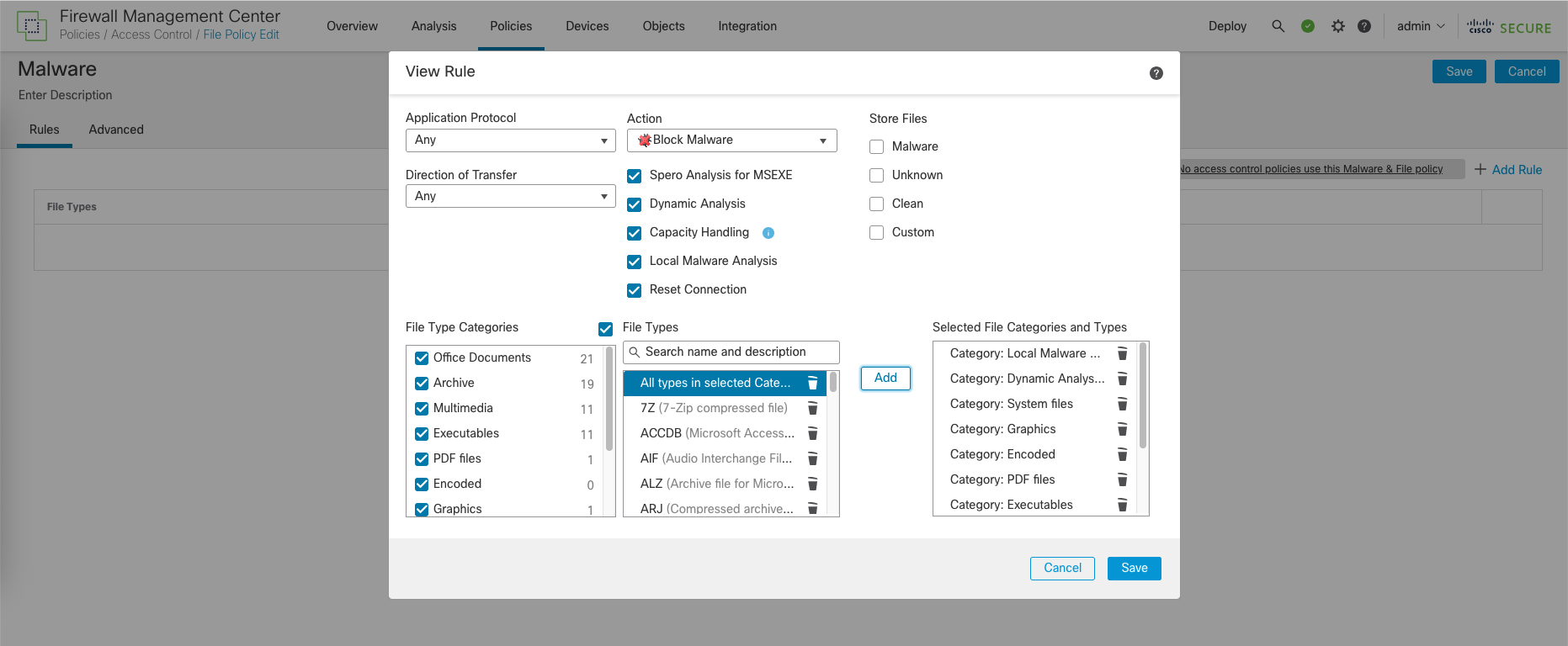
We will enable all submenu of actions and select all types of file categories
- Spero Analysis for MSEXE: Statically analyzes Microsoft executable files for malware indicators.
- Dynamic Analysis: Executes suspicious files in a safe, isolated environment to observe their behavior.
- Capacity Handling: Manages analysis queue load to prevent system overload while prioritizing security.
- Local Malware Analysis: Performs on-device malware detection using built-in signatures and intelligence.
- Reset Connection: Terminates the network connection immediately when malware is detected and blocked.
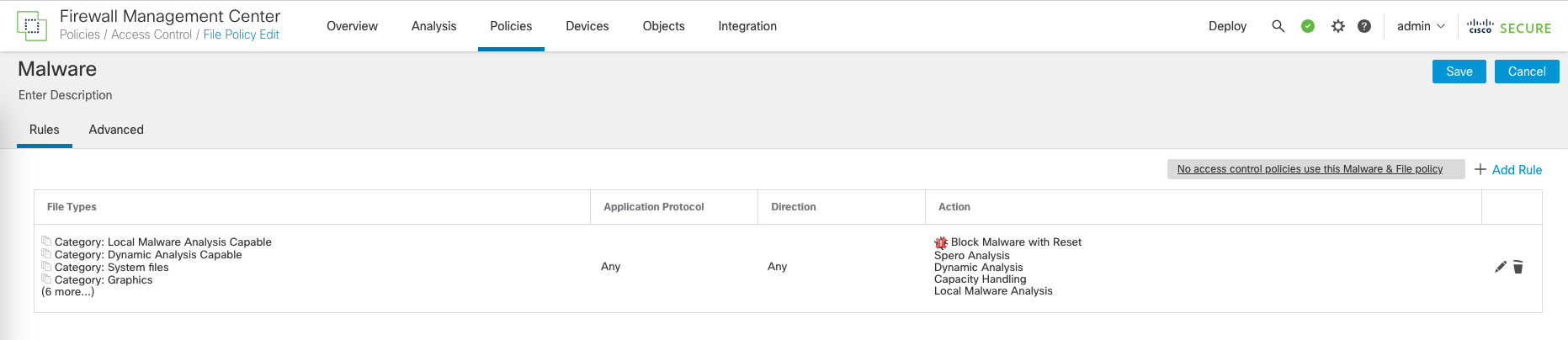
Here’s how the policy end up looking
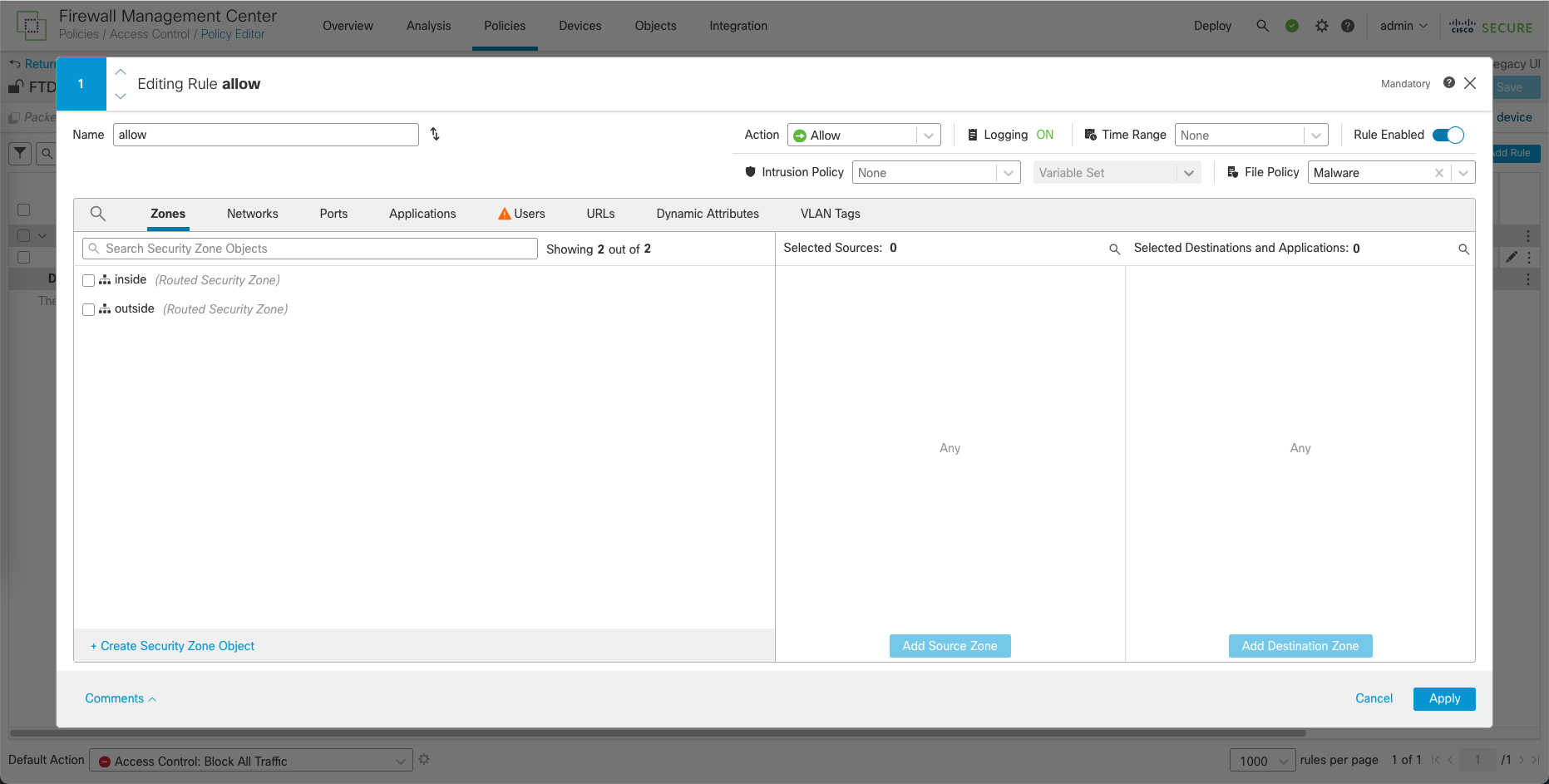
Finally we can attach the Malware Policy inside a Policy Rule
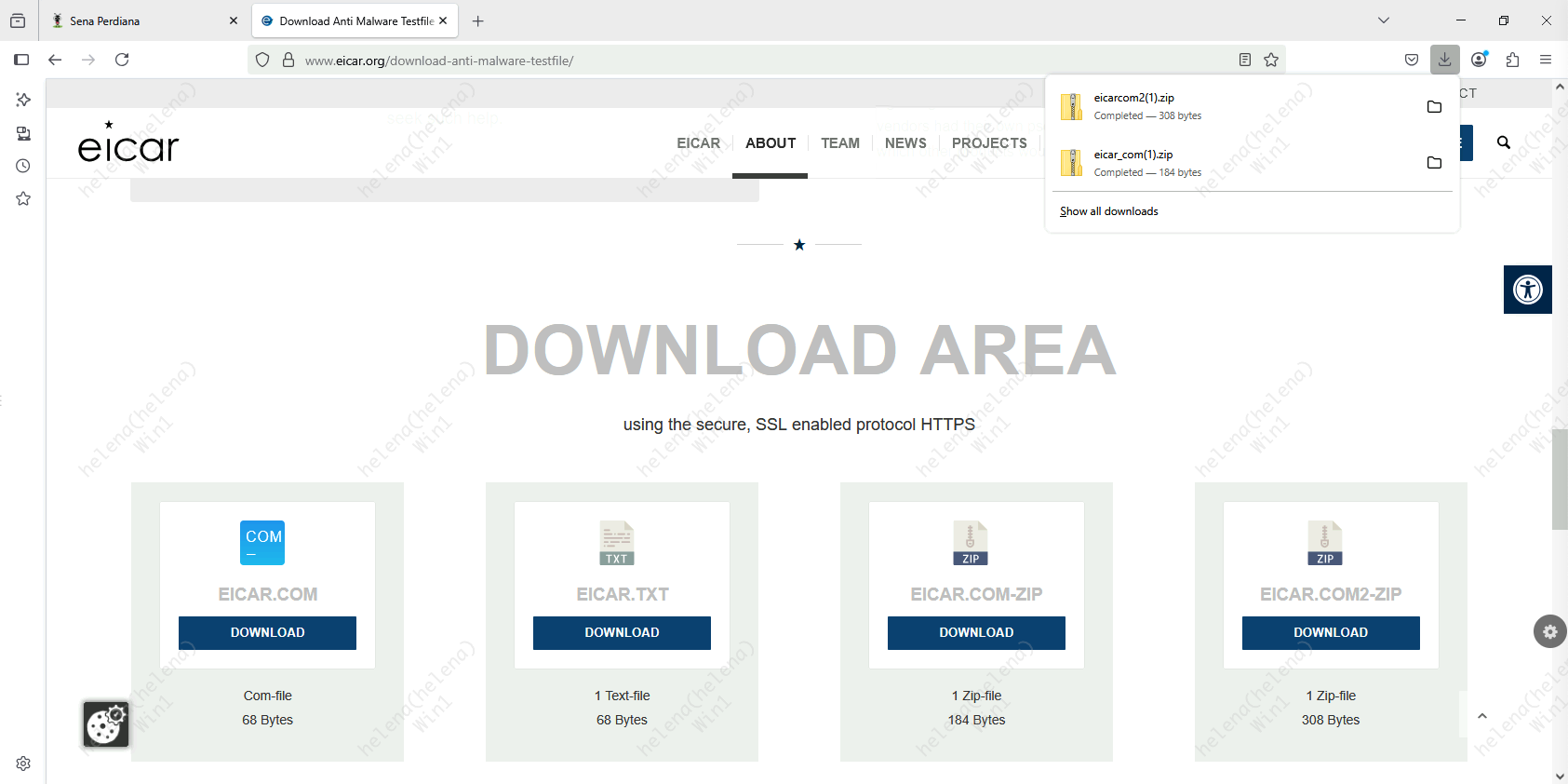
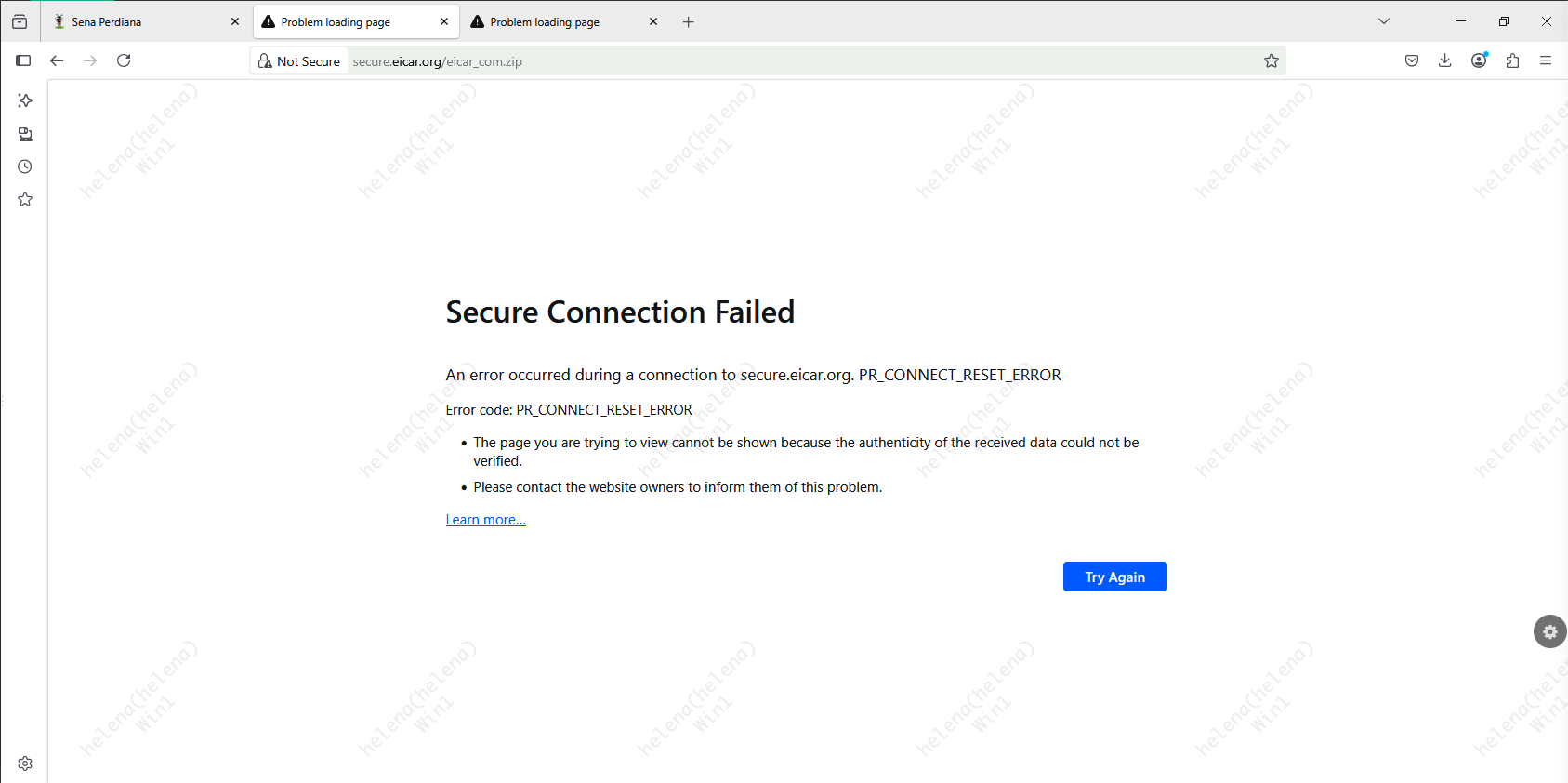
Now if we try to download the same malware, we will get a connection reset
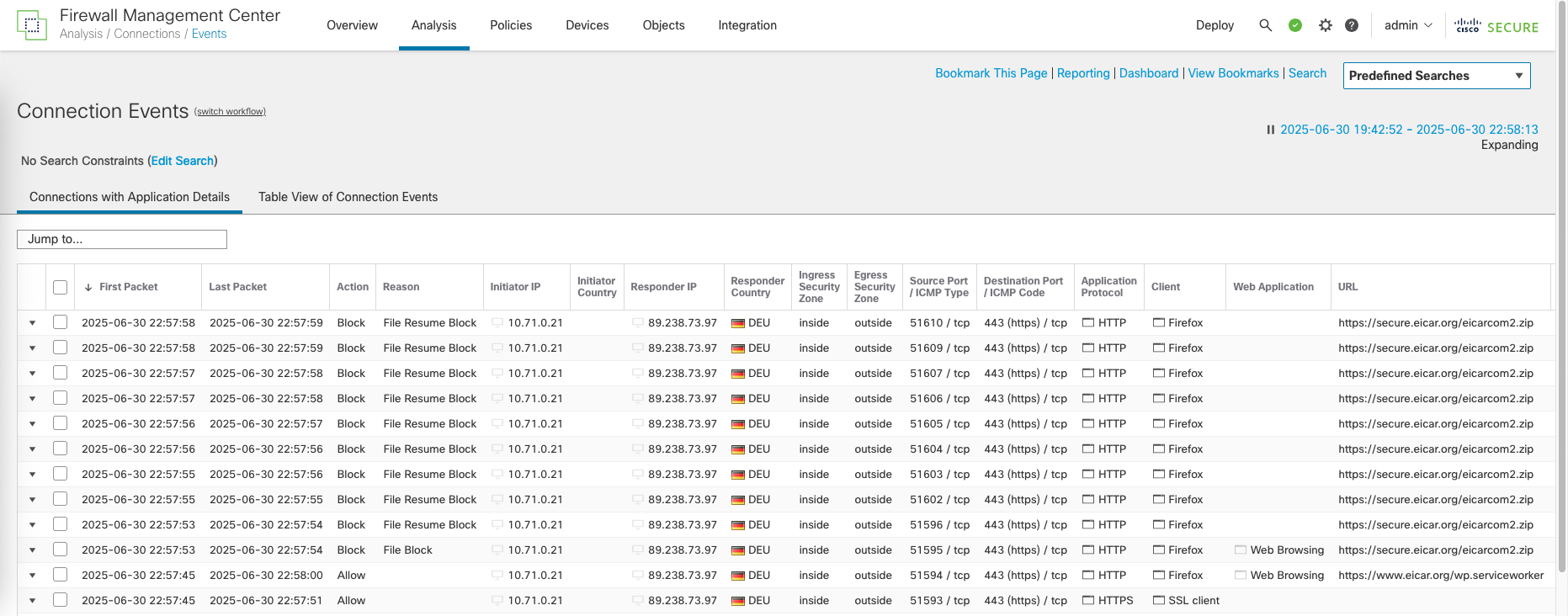
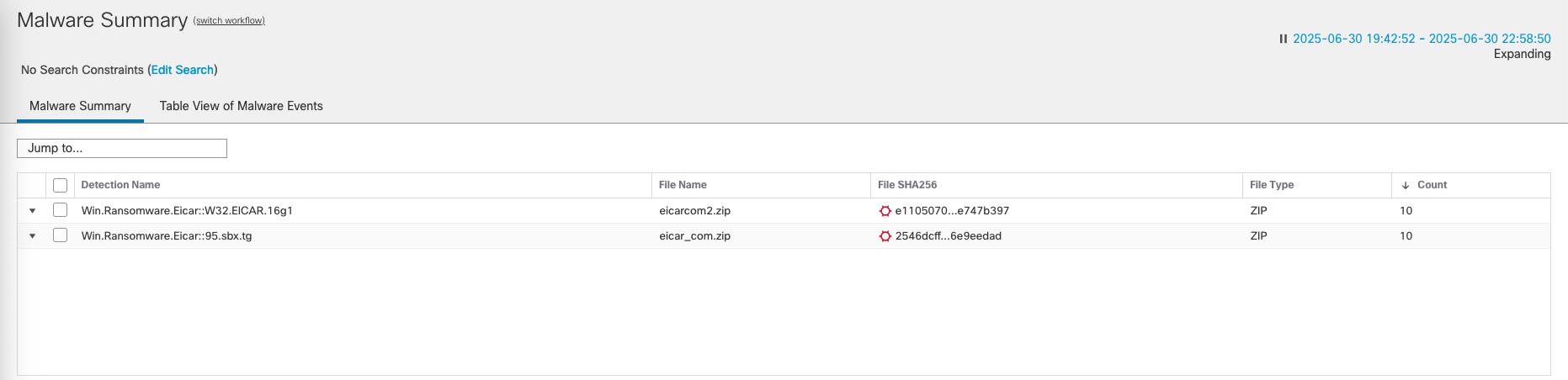
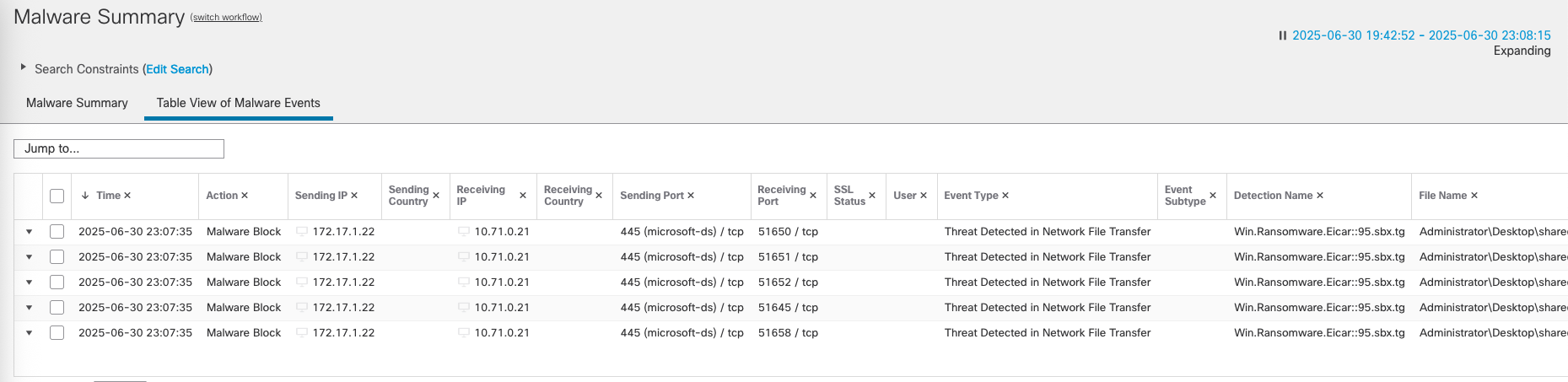
We can see the connection event and malware summary for the blocked traffic
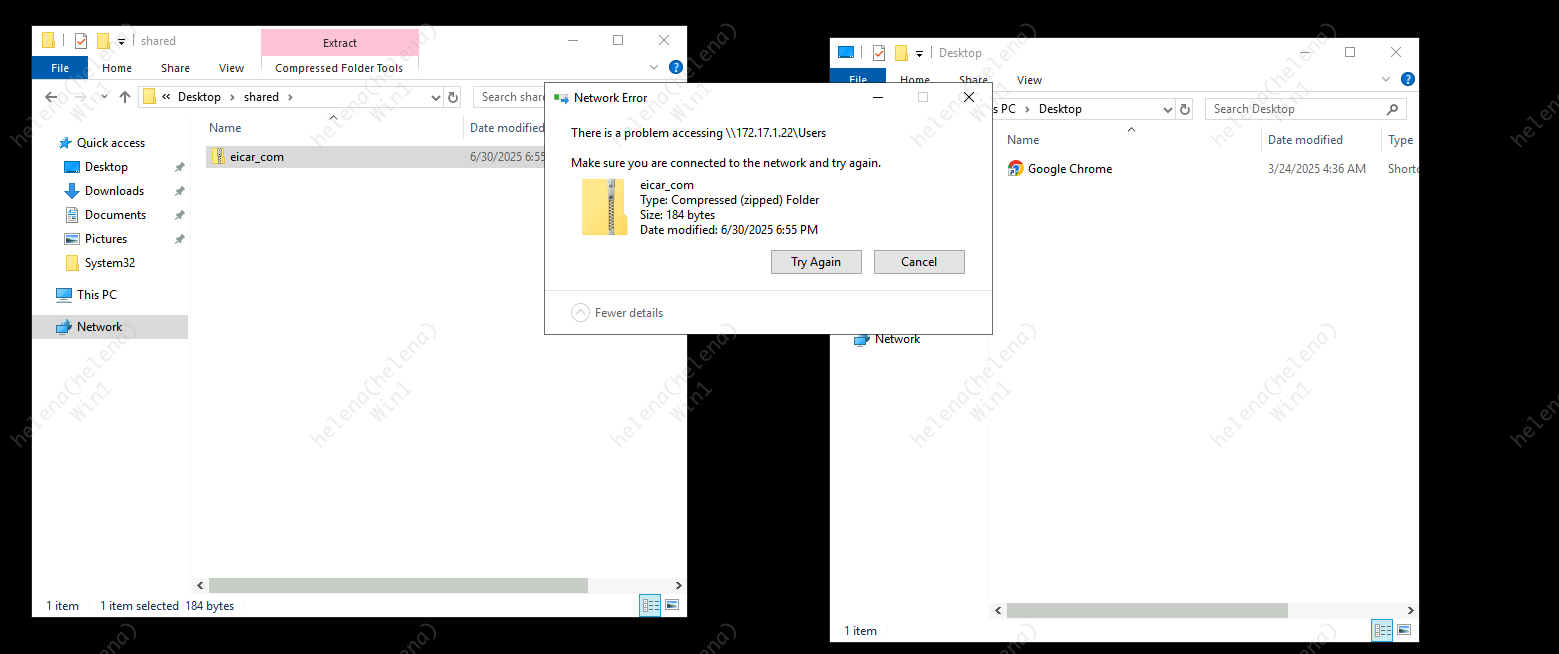
Other than web traffic, this policy will also block any other traffic that contains malware, including file share transfer over SMB