BGP on Firewalls
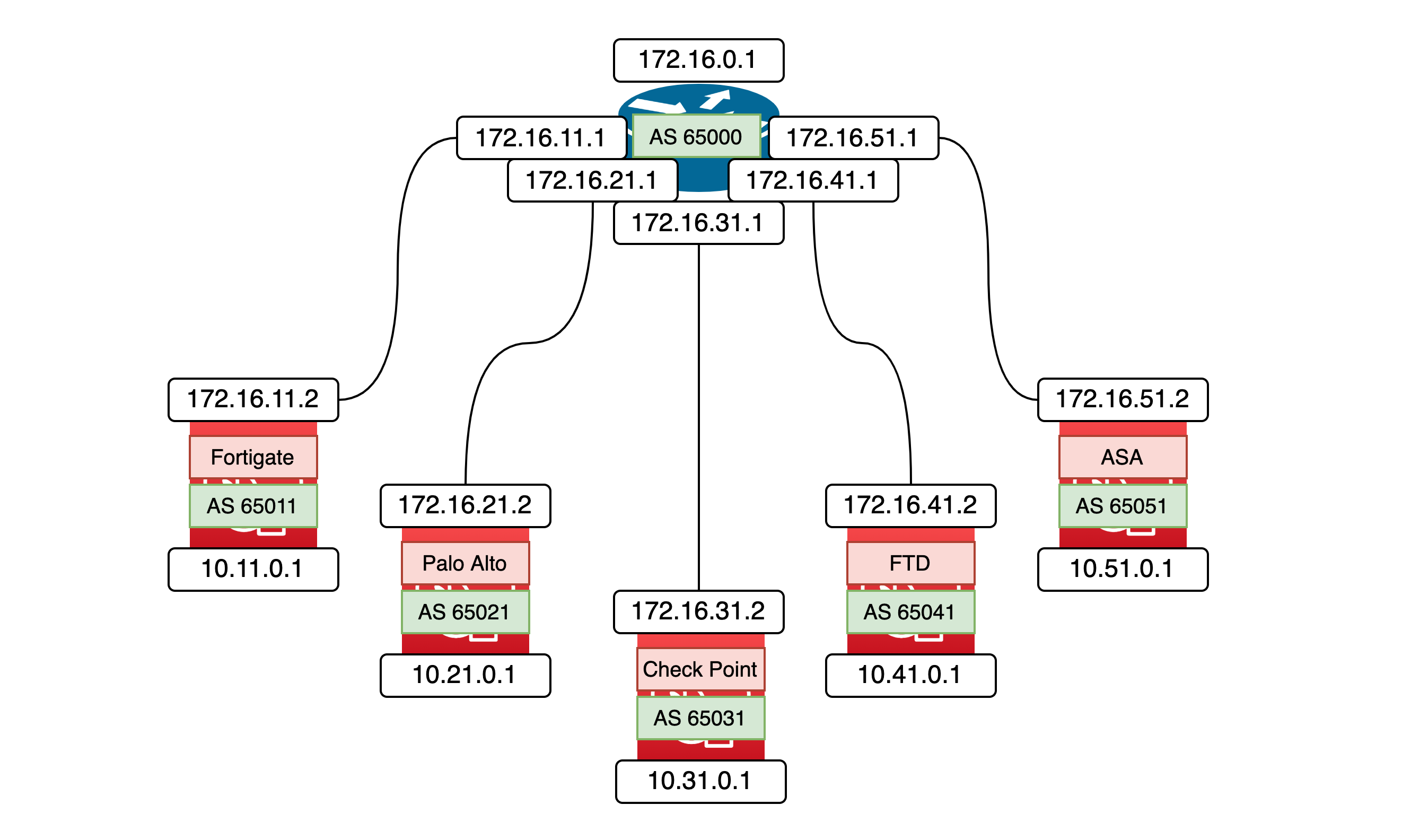
Here’s the planned topology for BGP configuration across multiple firewalls
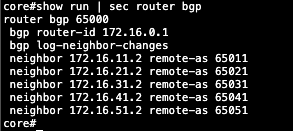
Here’s the BGP configuration on the Core Switch side
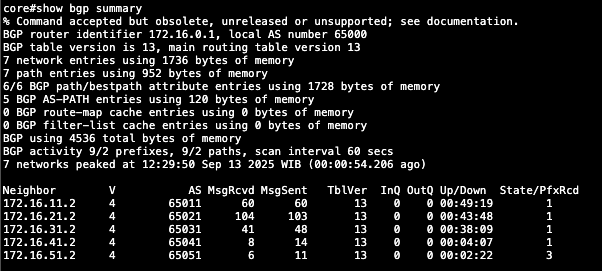
Here we can see the BGP is up and running
show bgp summary
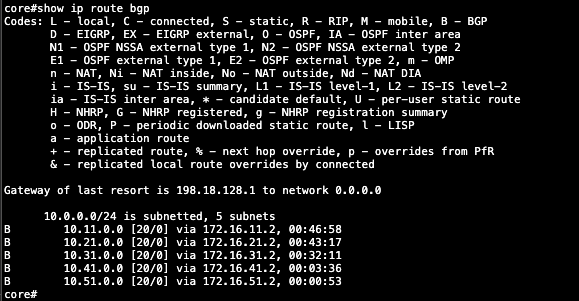
show ip route bgp
Fortigate
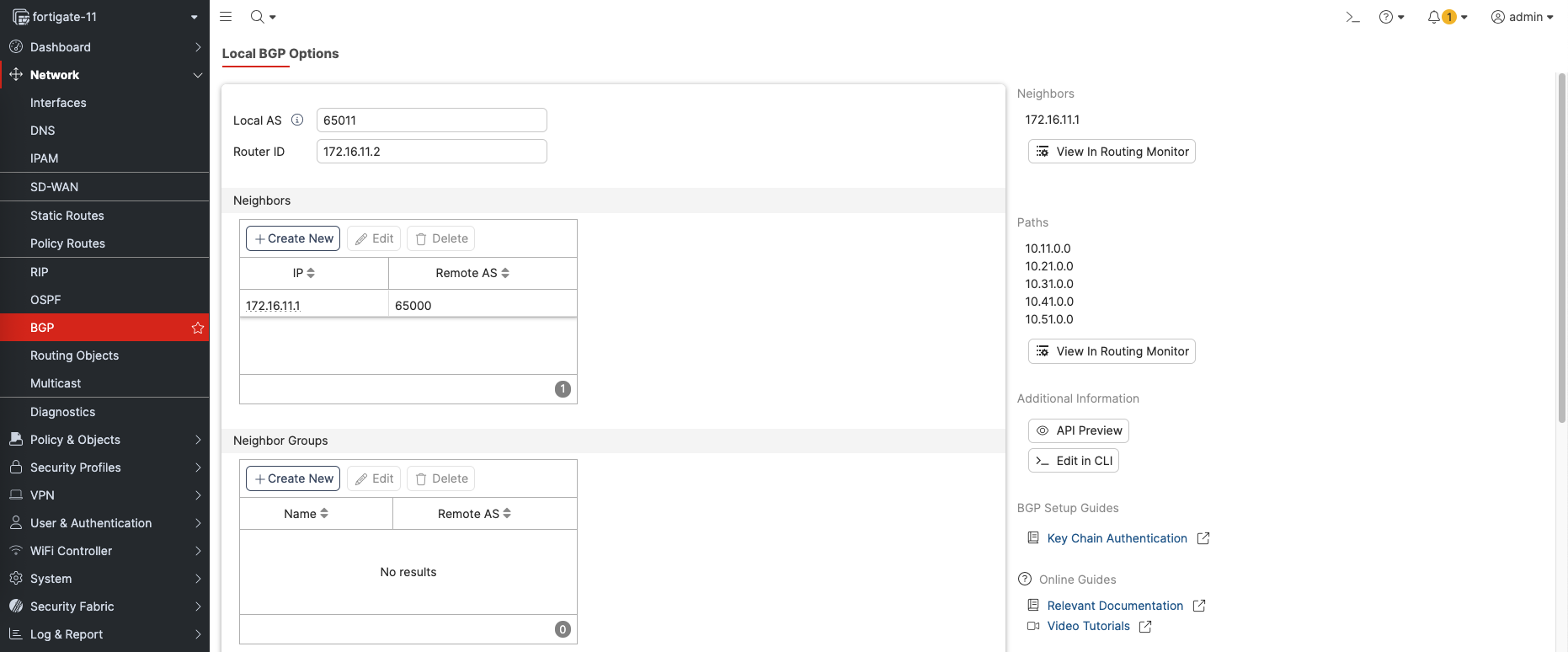
On Forti side, enable BGP by giving it AS Number, Router ID and the BGP Neighbor
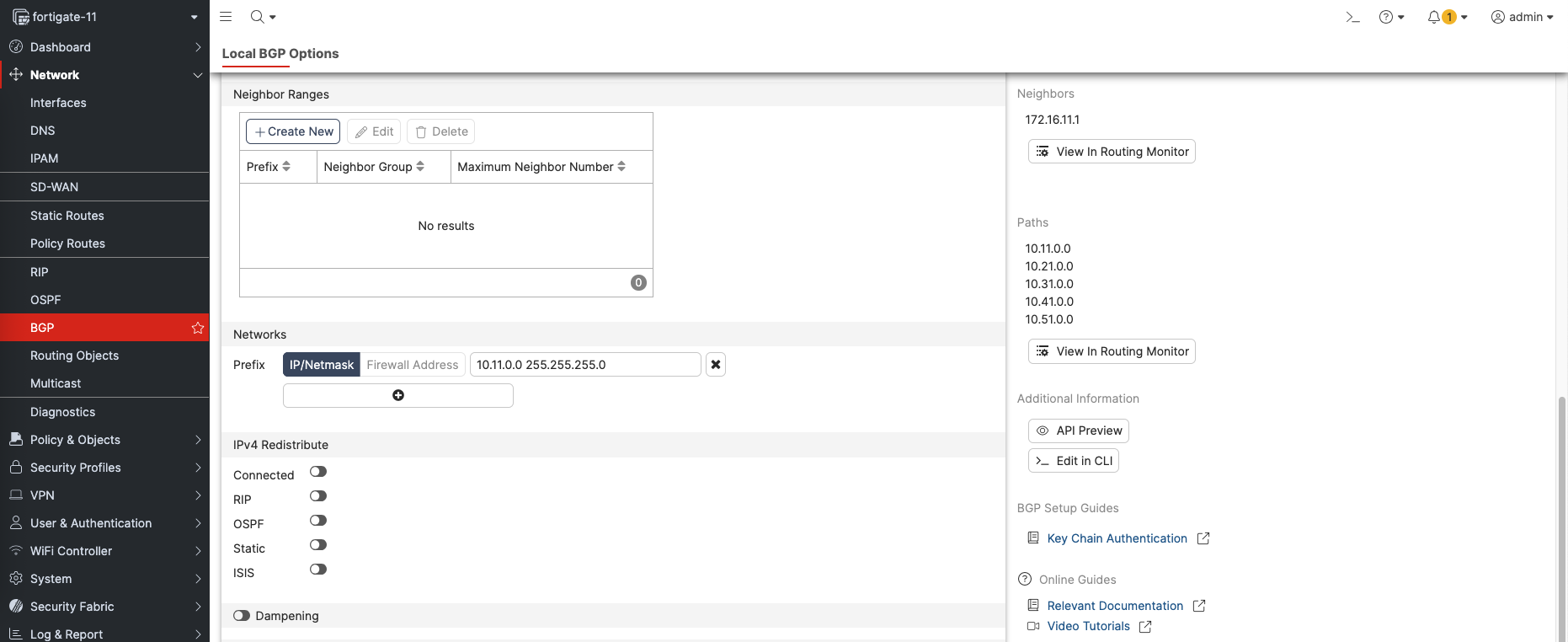
Then add the internal network to advertise
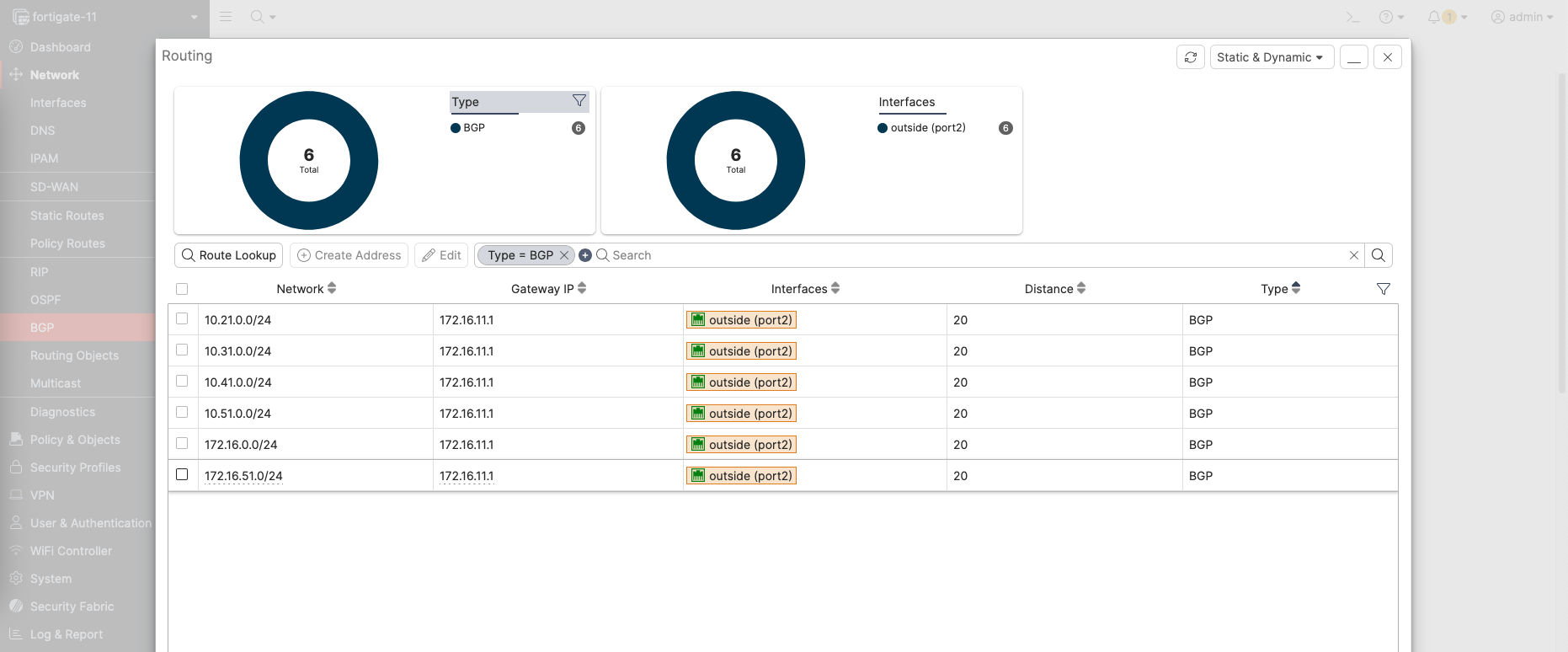
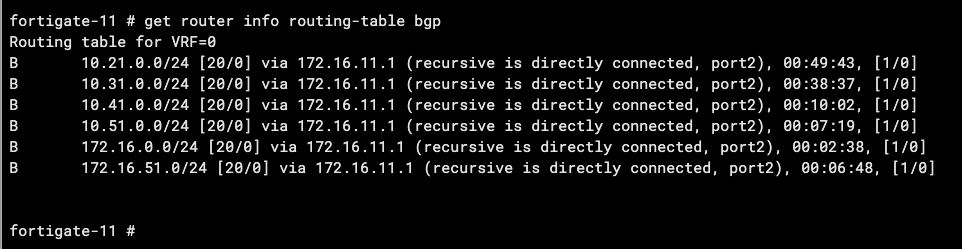
Here we can see the routes received by BGP
get router info routing-table bgp
Palo Alto
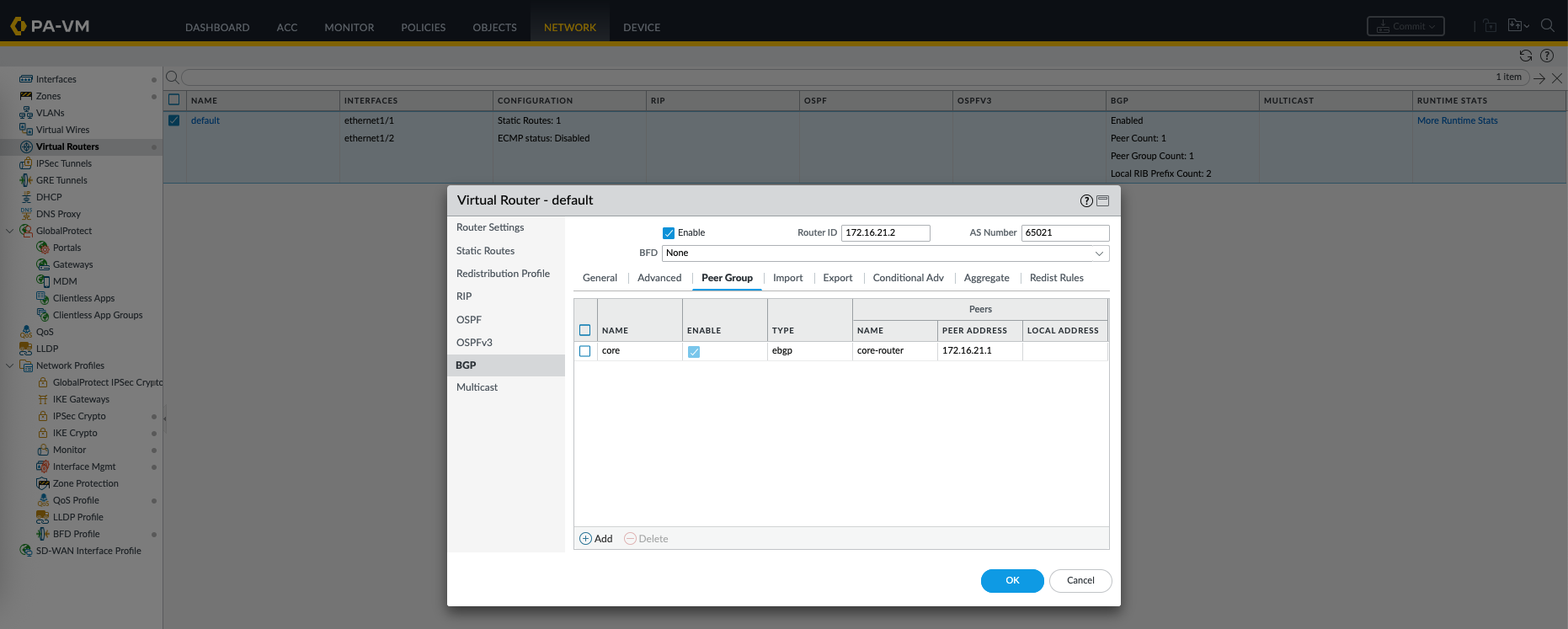
On Palo Alto, we enable BGP on the Virtual Router, here we enable the process, add AS Number, and define the BGP neighbor
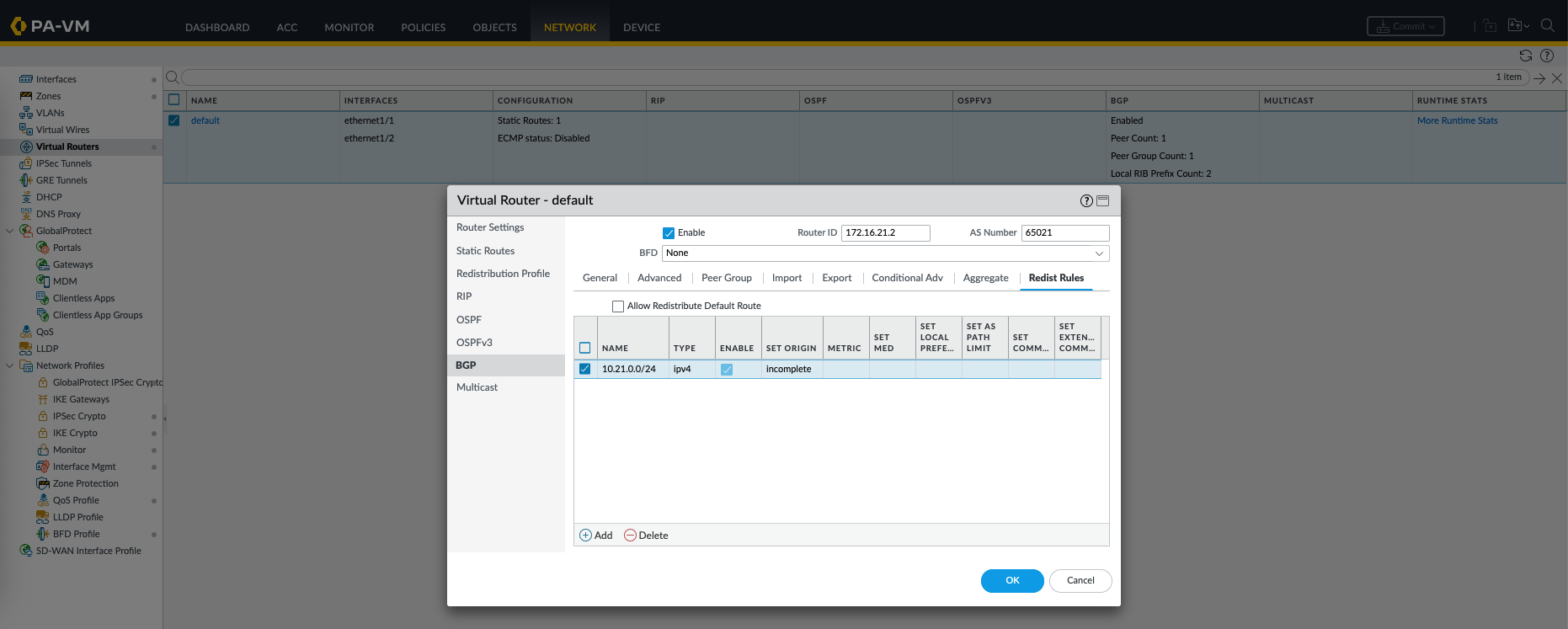
Then on Redist Rules, we add the internal network to advertise
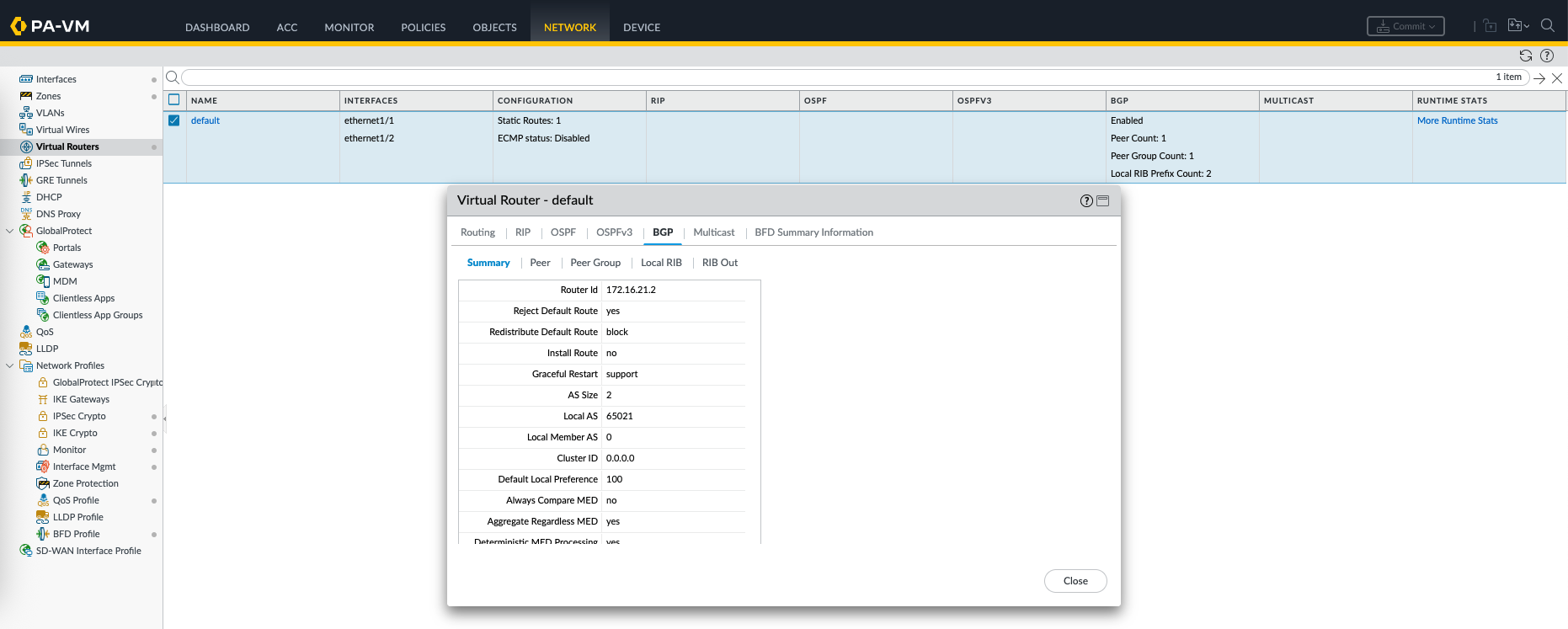
On Runtime Stats we can see the BGP process is up
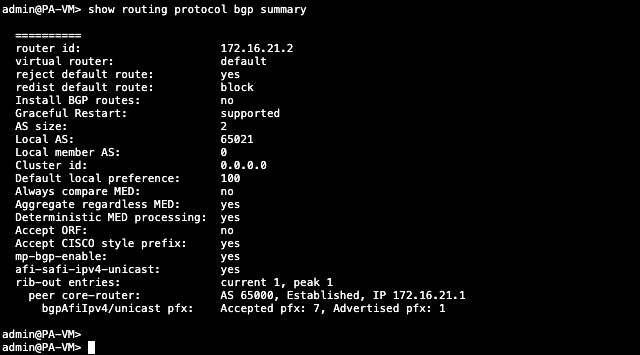
show routing protocol bgp summary
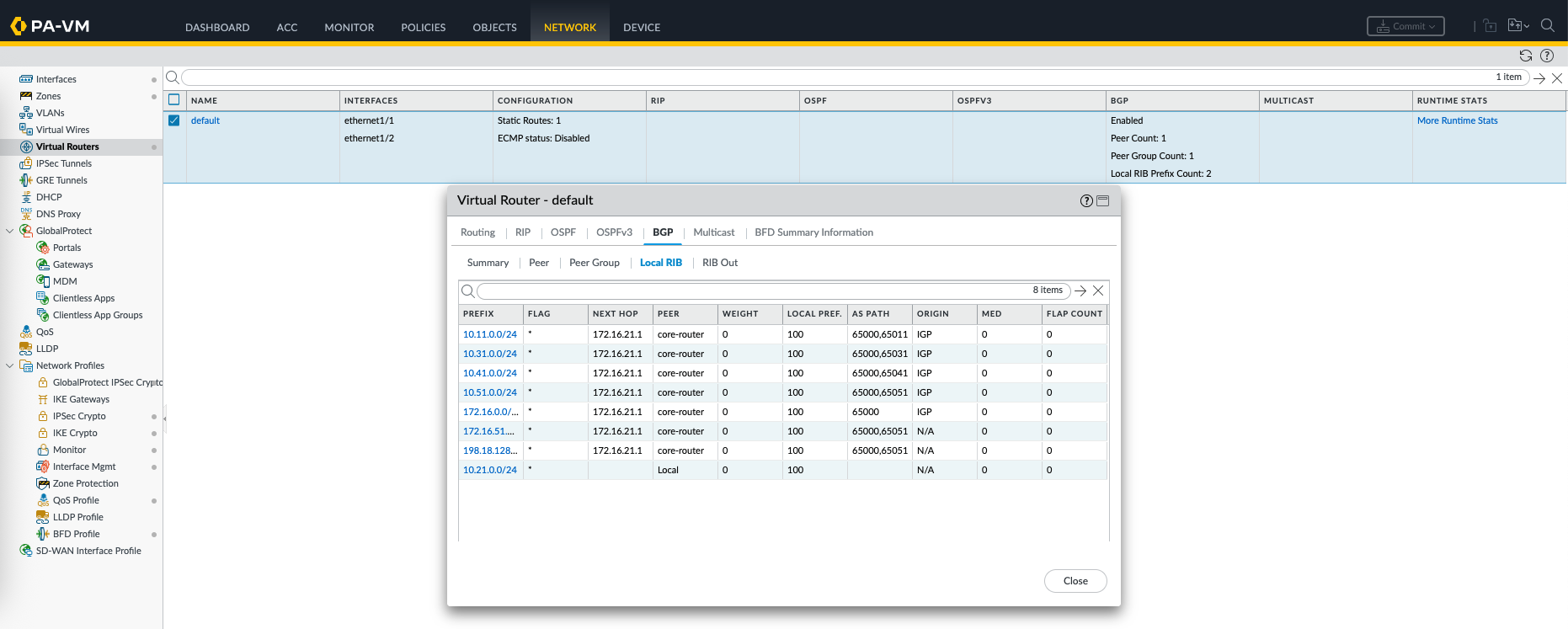
On Local RIB we can see the routes that we receive from BGP
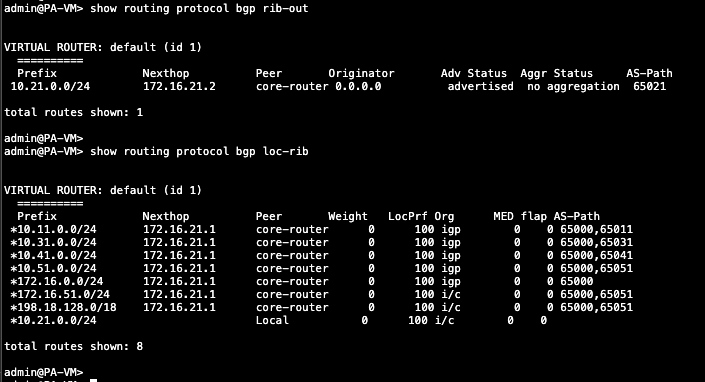
show routing protocol bgp
Check Point
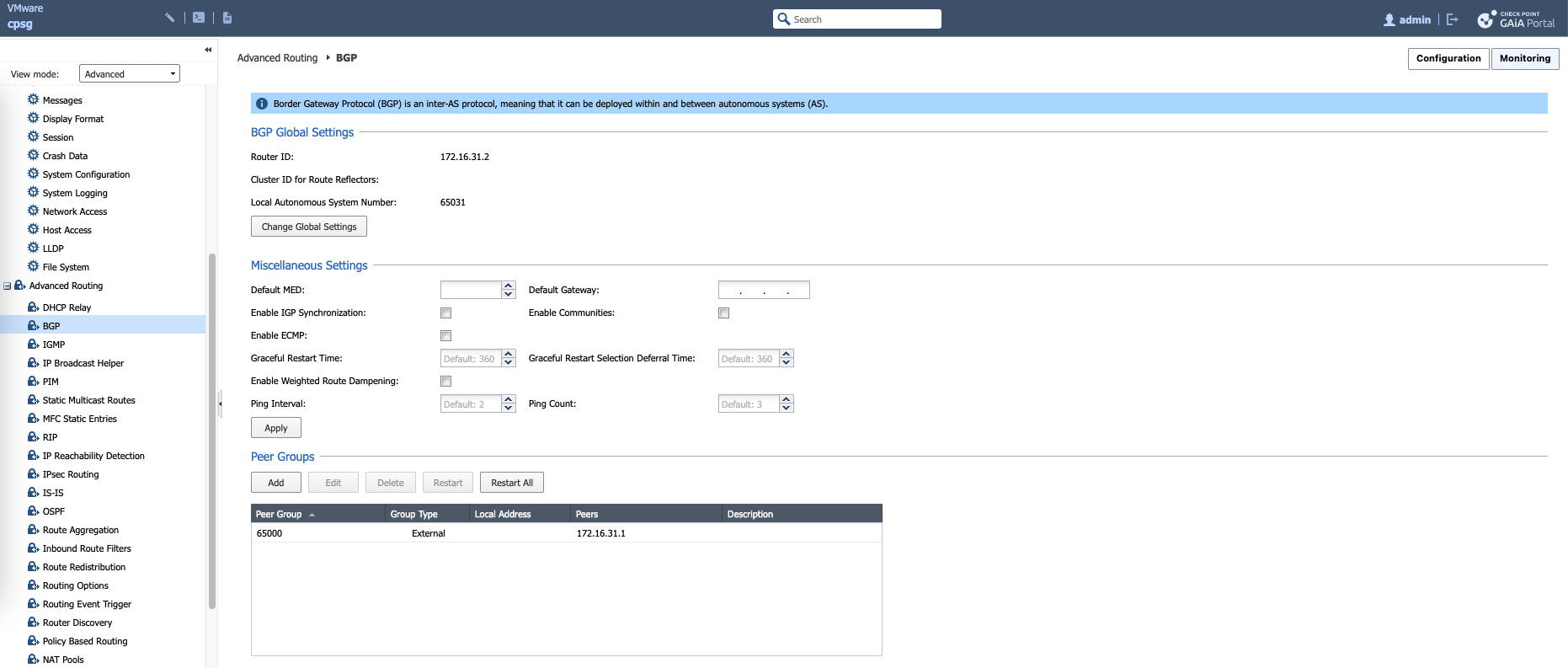
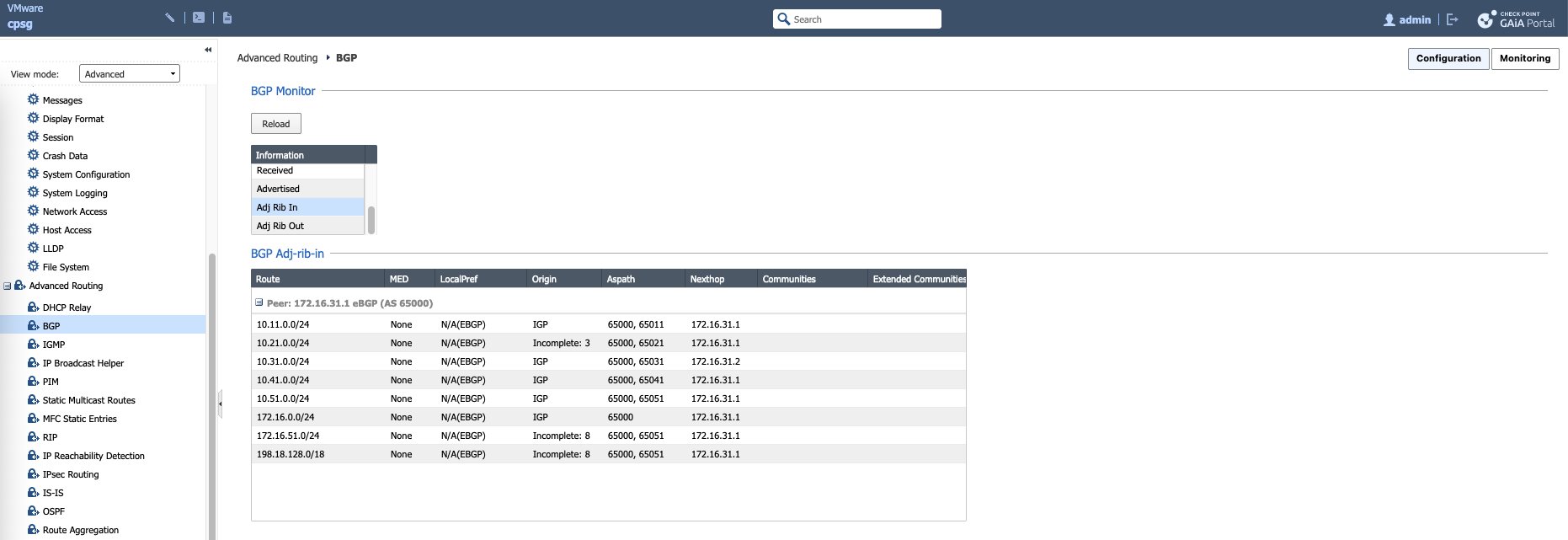
On Check Point, we enable BGP by configuring Router ID, AS Number, and Peer Groups
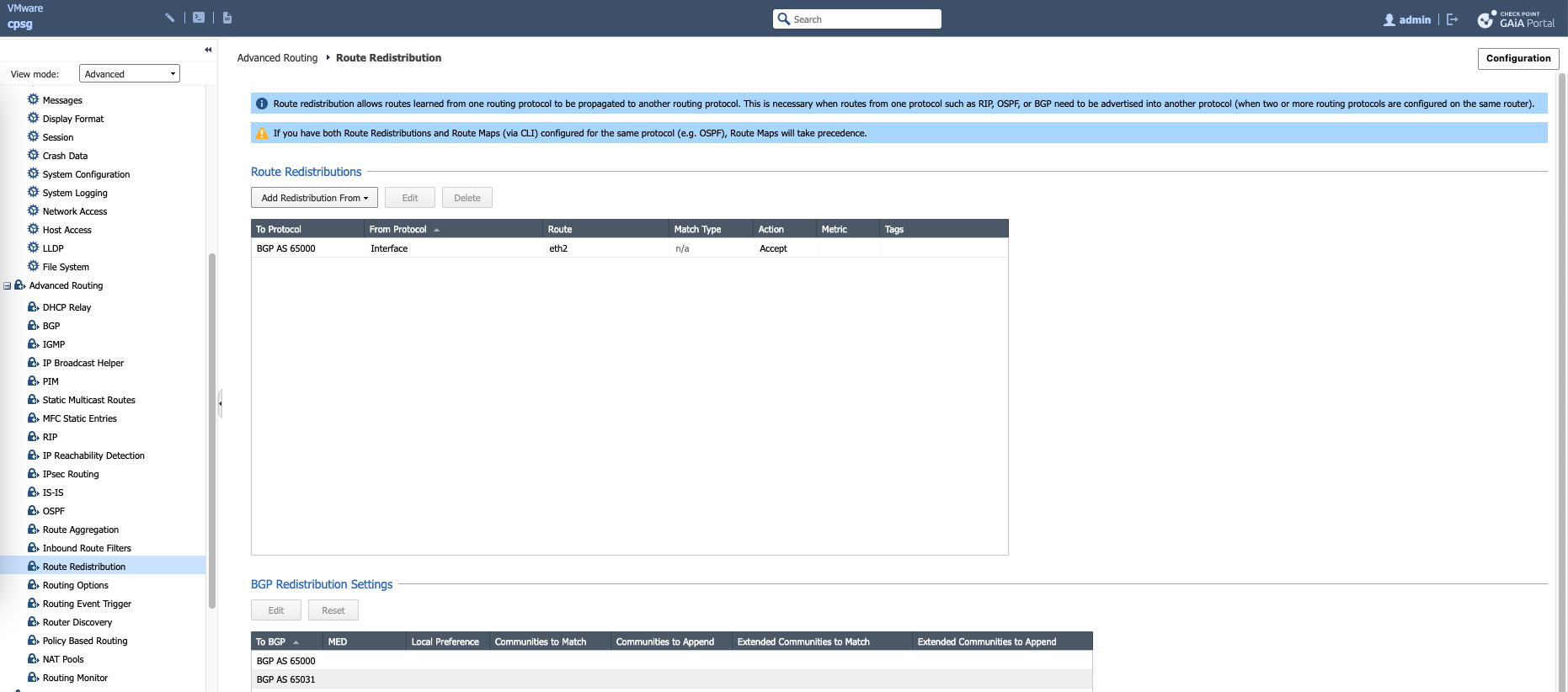
On Route Redistribution, we add the internal interface to be advertised
We can see the BGP process on the monitoring tab
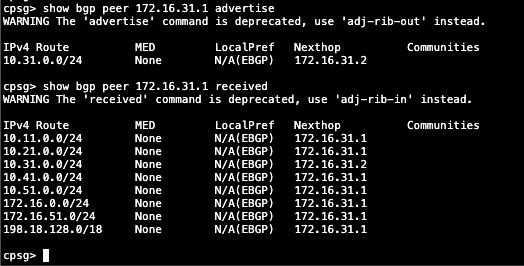
show bgp peer
Cisco FTD
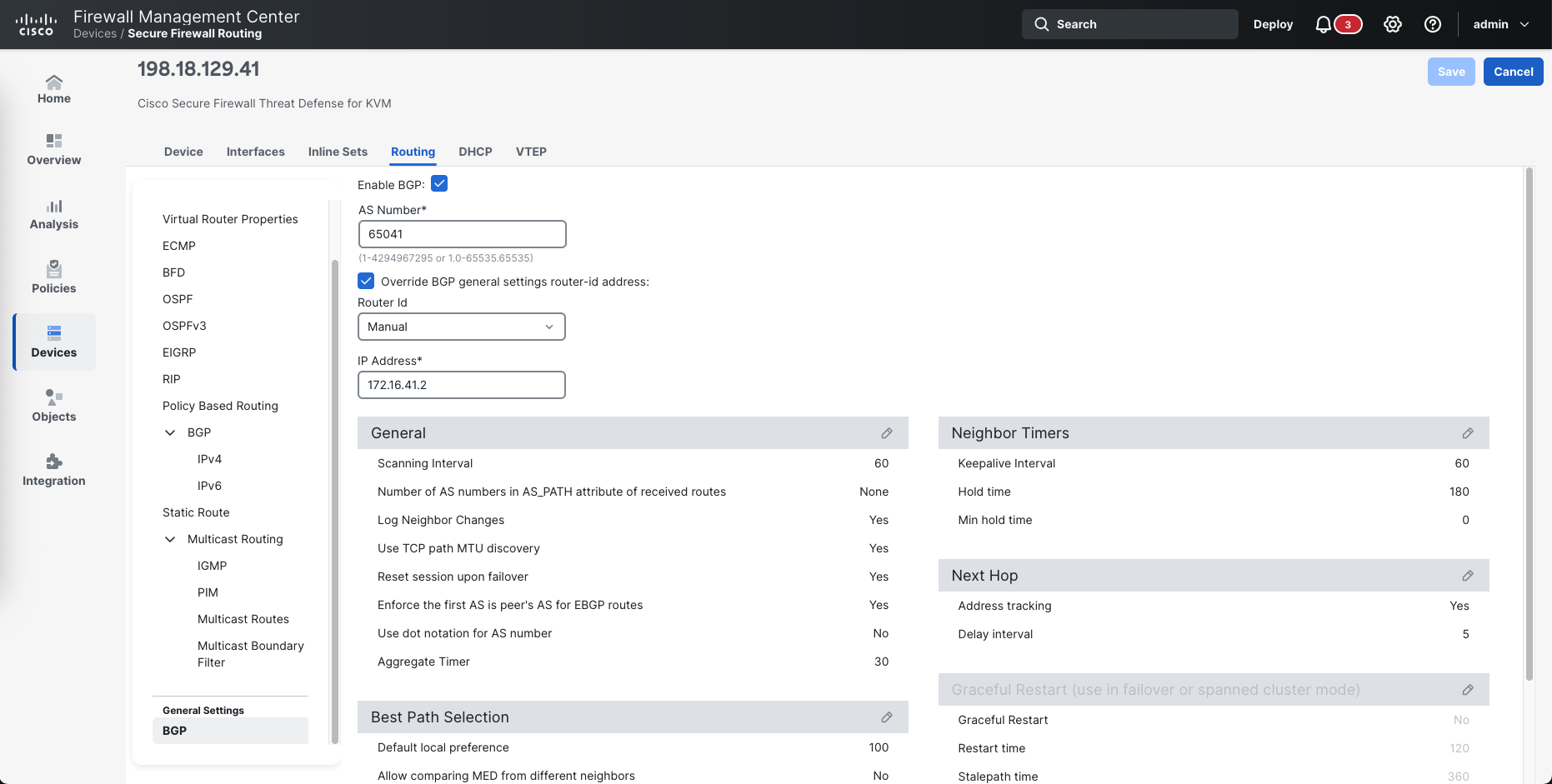
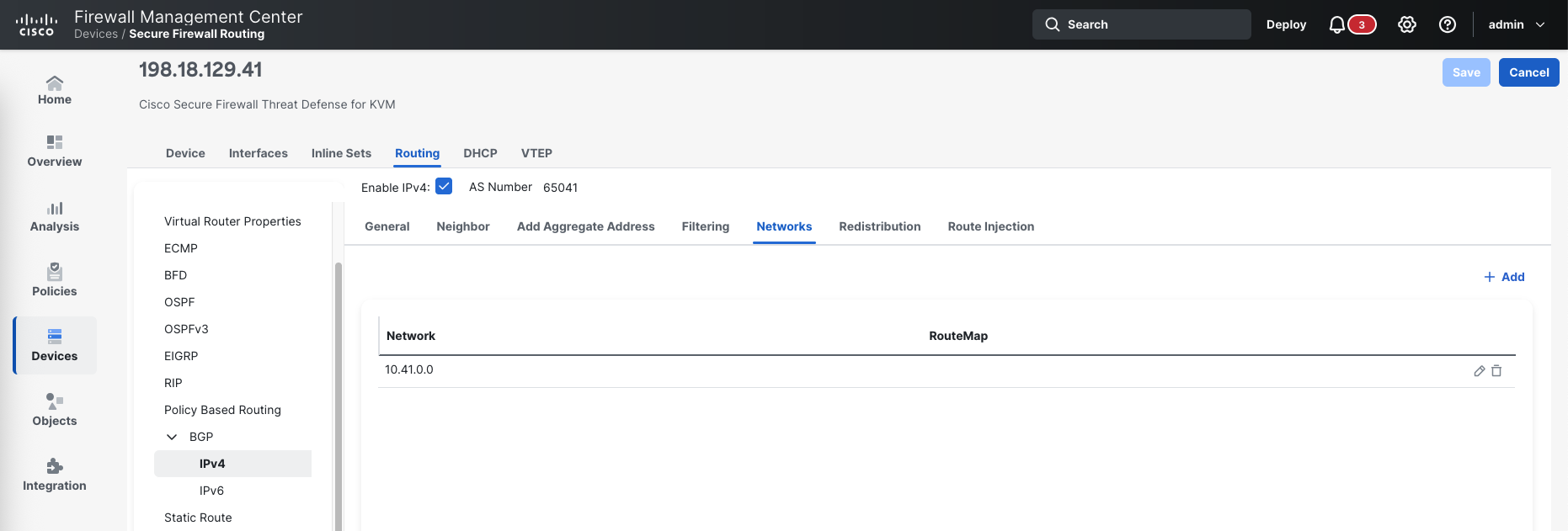
On FTD managed by FMC, first we enabel BGP and give it AS Number
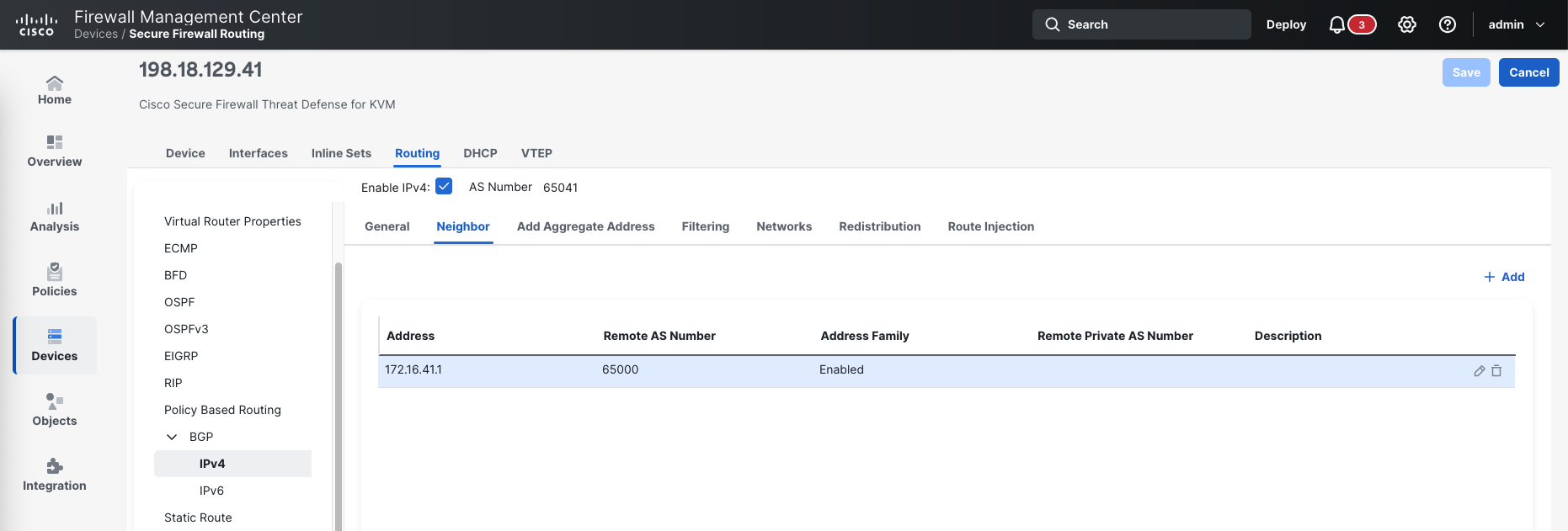
Then we add the BGP neighbor
And we also add the internal network to be advertised
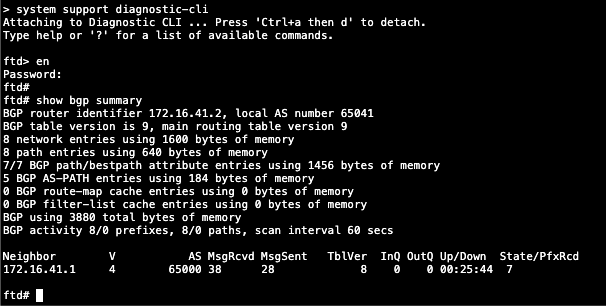
Run this command to see the BGP process
system support diagnotic-cli
show bgp summary
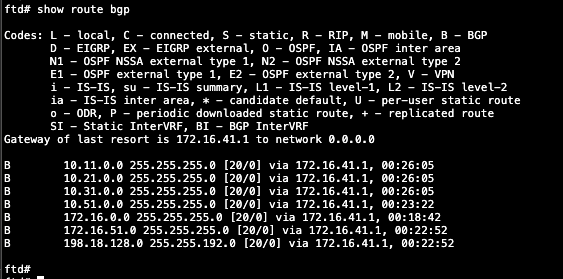
show route bgp
Cisco ASA
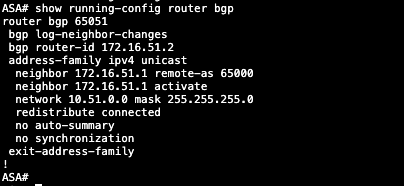
Here’s the BGP configuration on ASA side
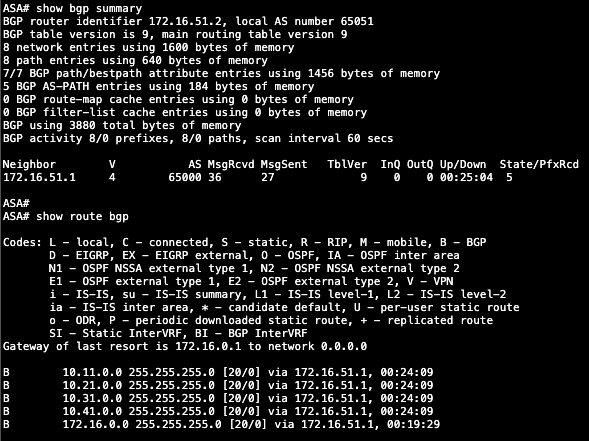
Run this command to verify the BGP process
show bgp summary
show route bgp