OSPF on Firewalls
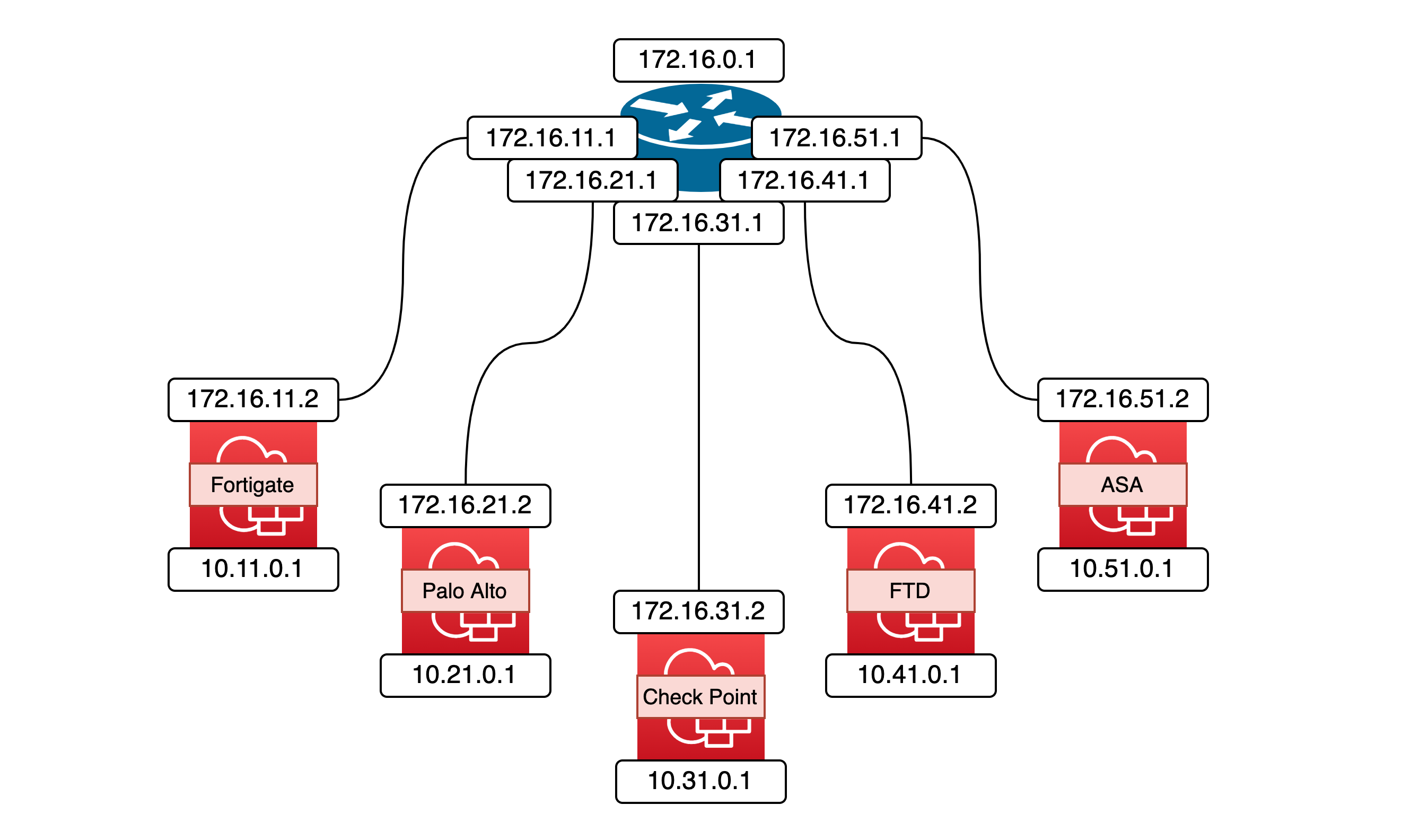
Here’s the planned topology for OSPF configuration across multiple firewalls
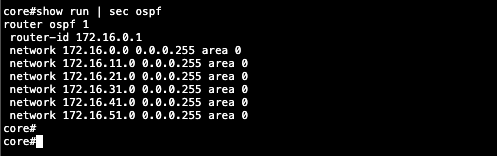
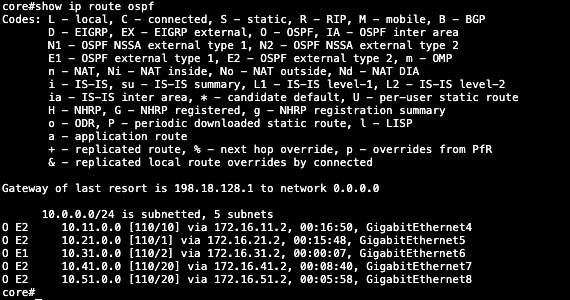
On the Core Switch side, we enable OSPF on all required interfaces
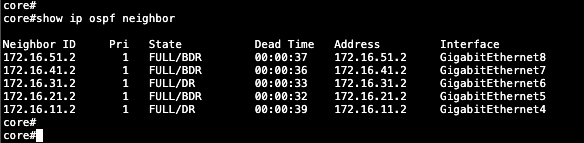
Here we can see the OSPF configuration is up and running
show ip ospf neighbor
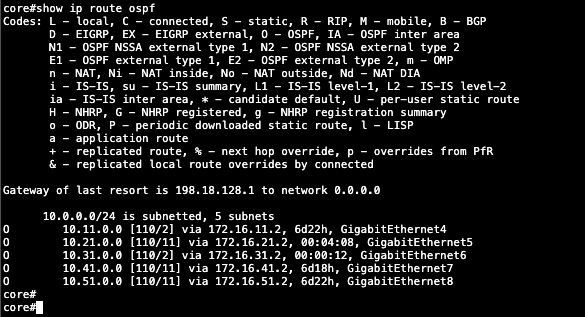
show ip route ospf
Fortigate
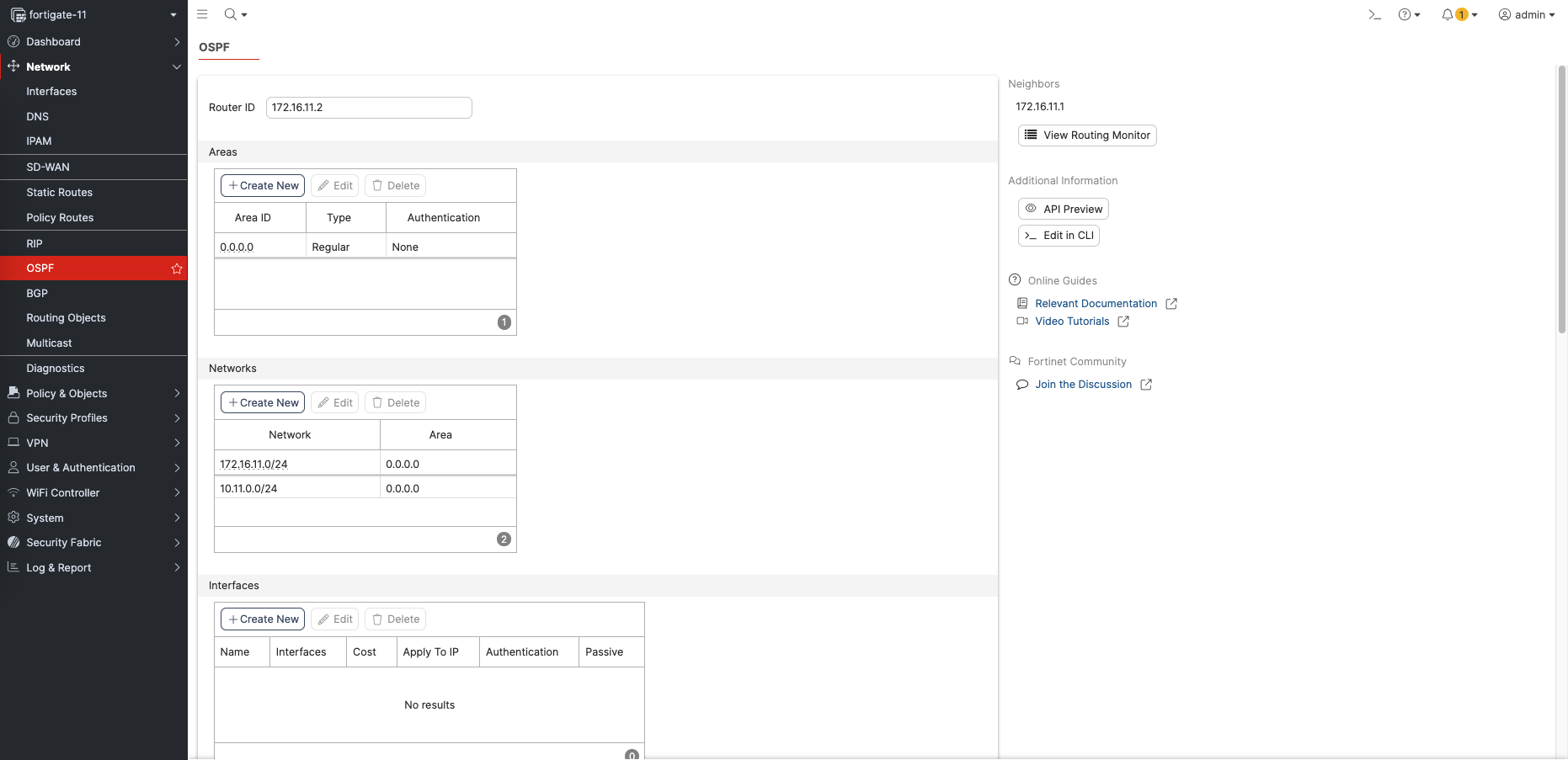
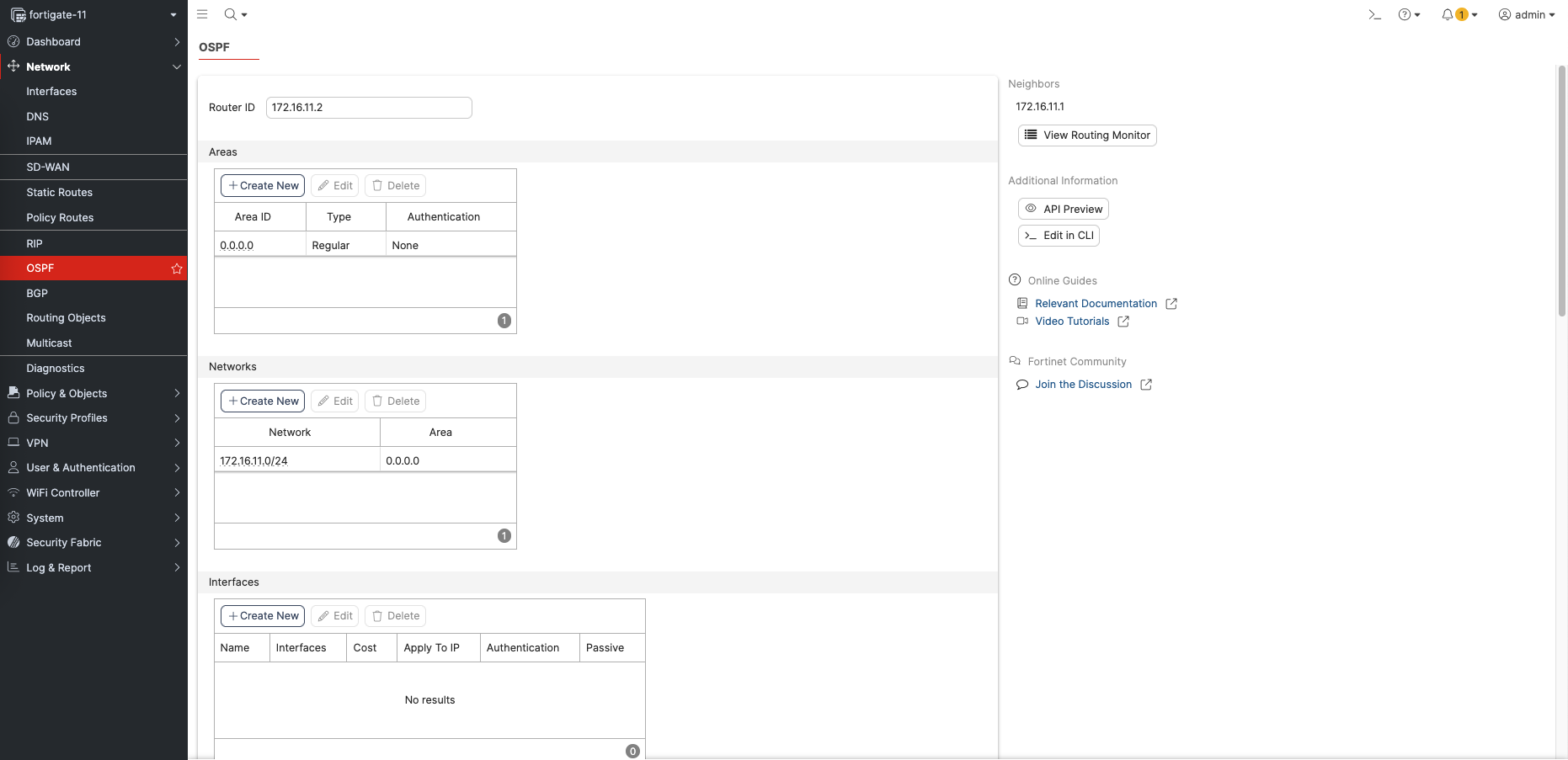
On fortigate side, enable OSPF on Network » OSPF. Here we give it Router ID, Area 0, and networks to join the OSPF neighborship
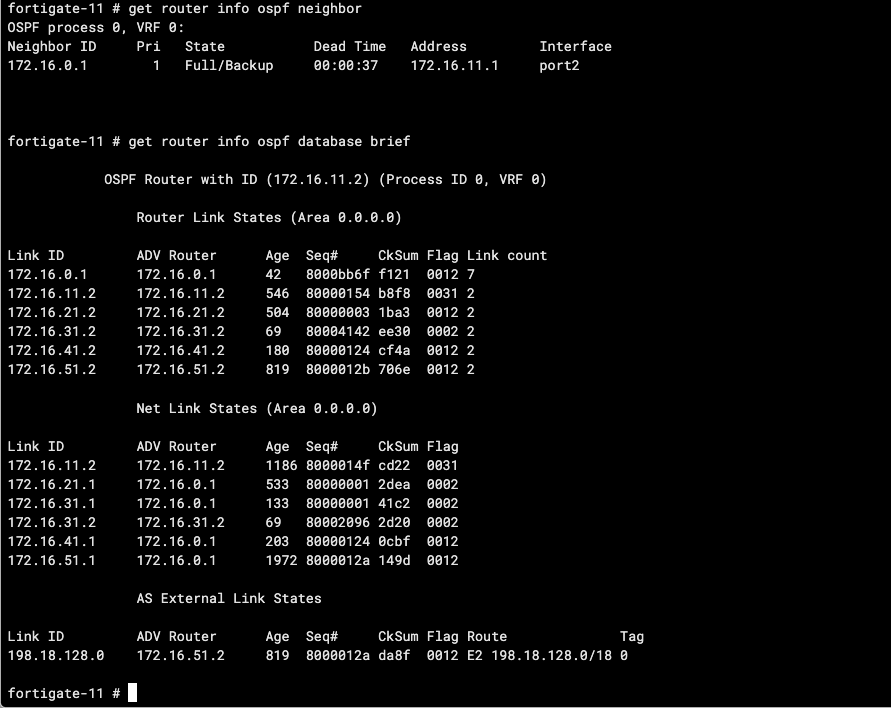
Run this command to show OSPF neighborship on CLI
get router info ospf neighbor
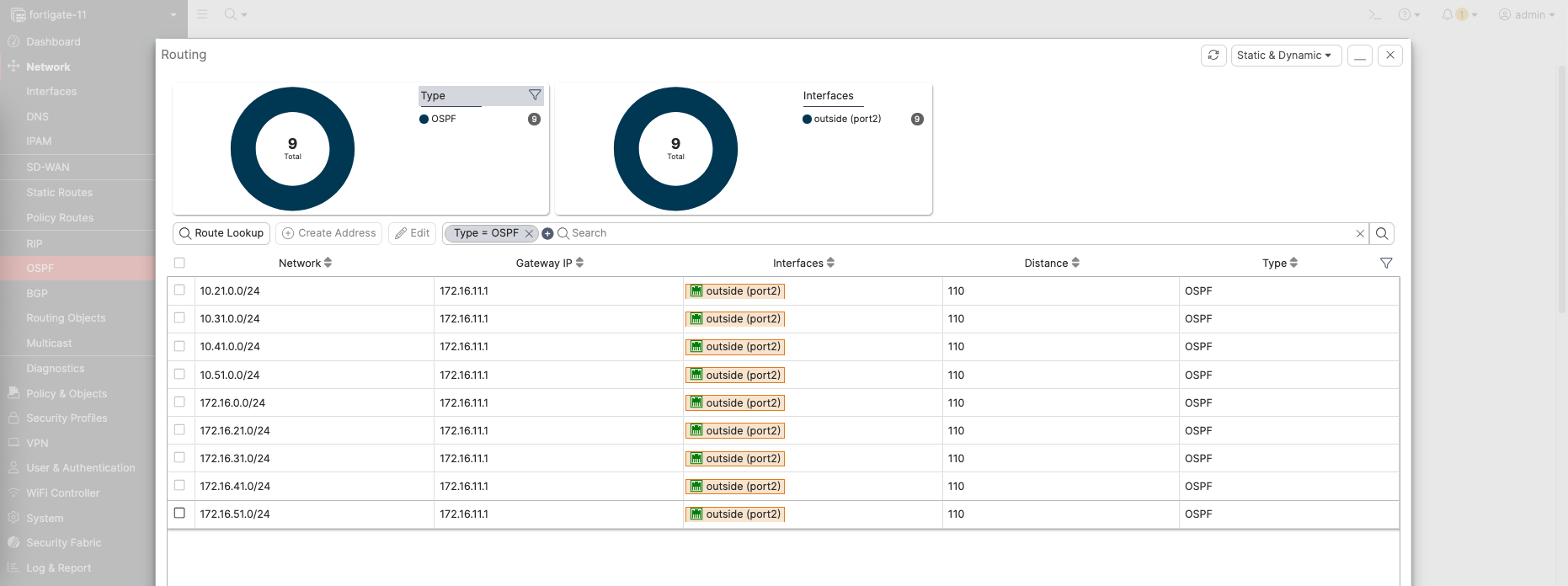
We can also see the advertised routes that we receive from OSPF on Routing Monitor
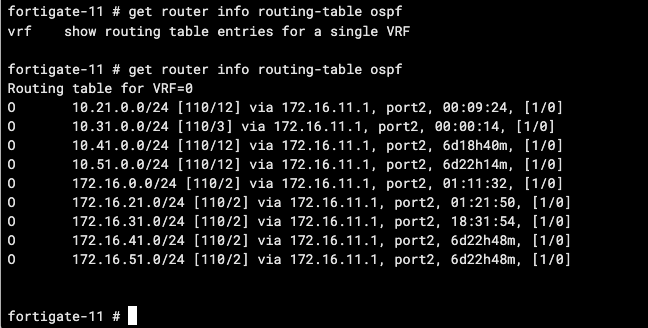
get router info routing-table ospf
Palo Alto
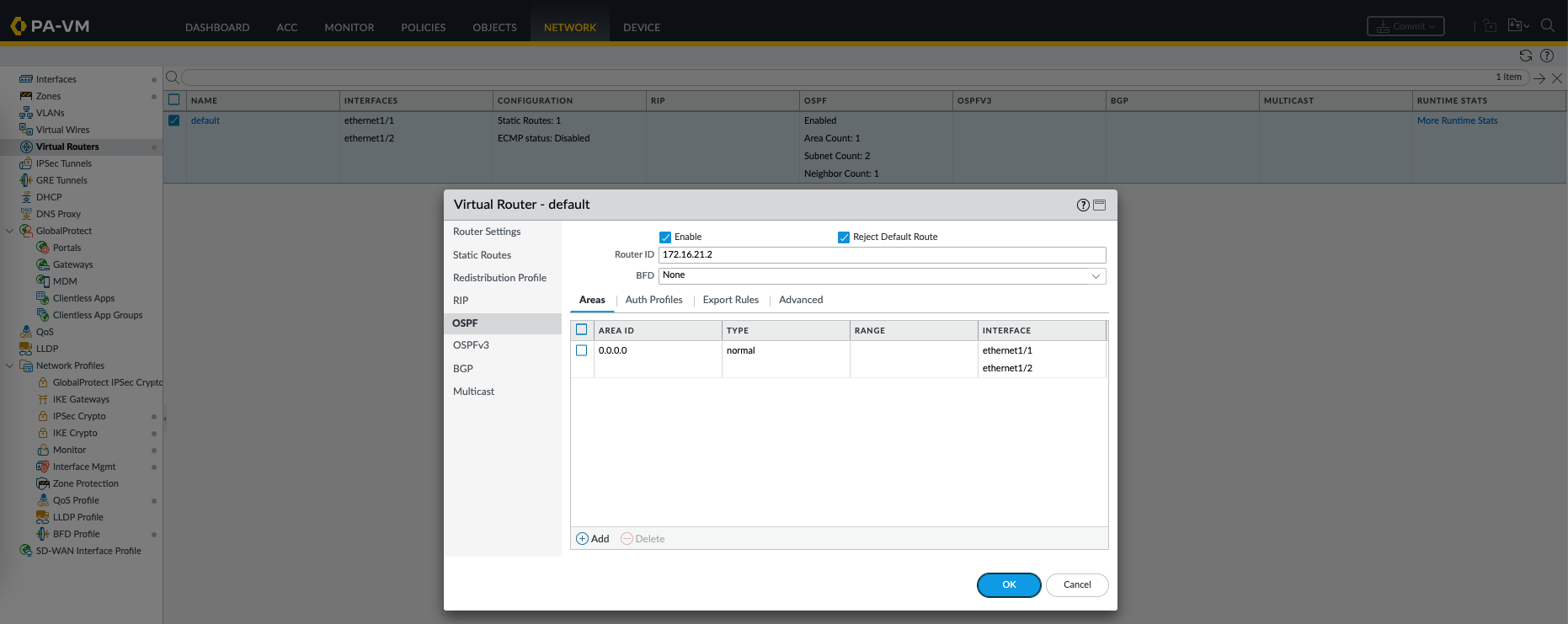
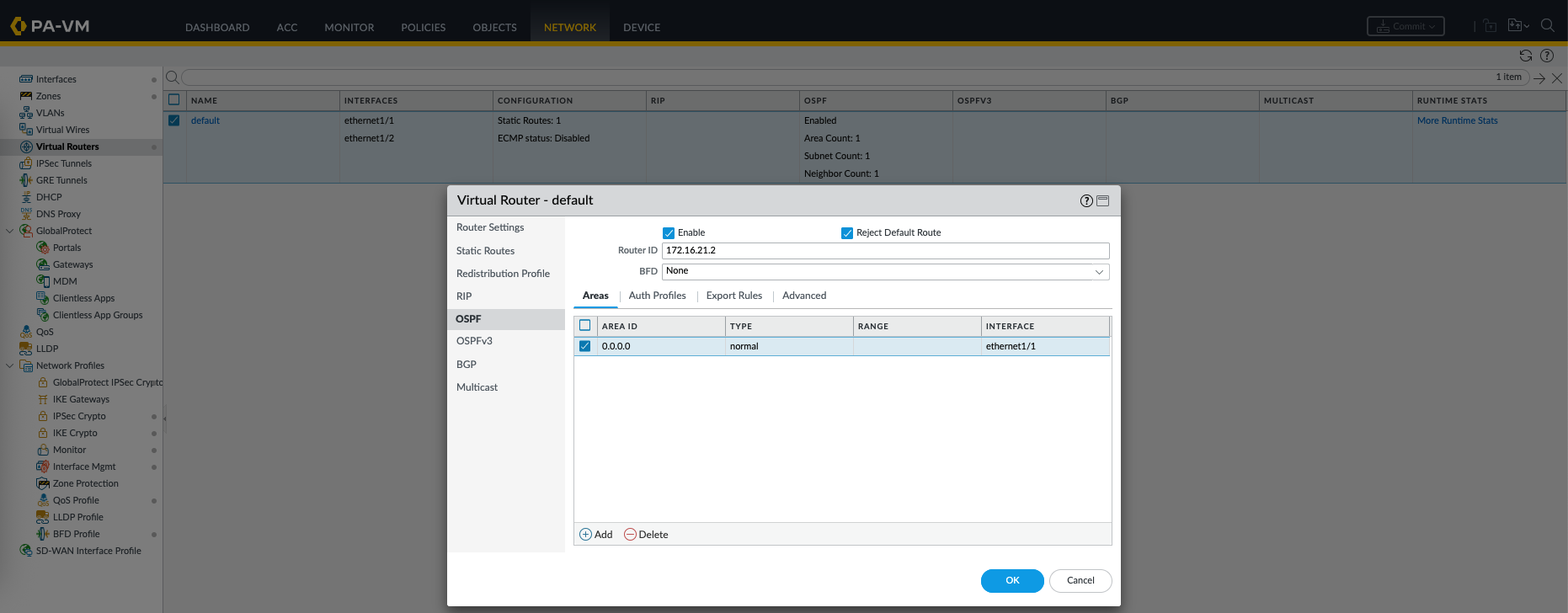
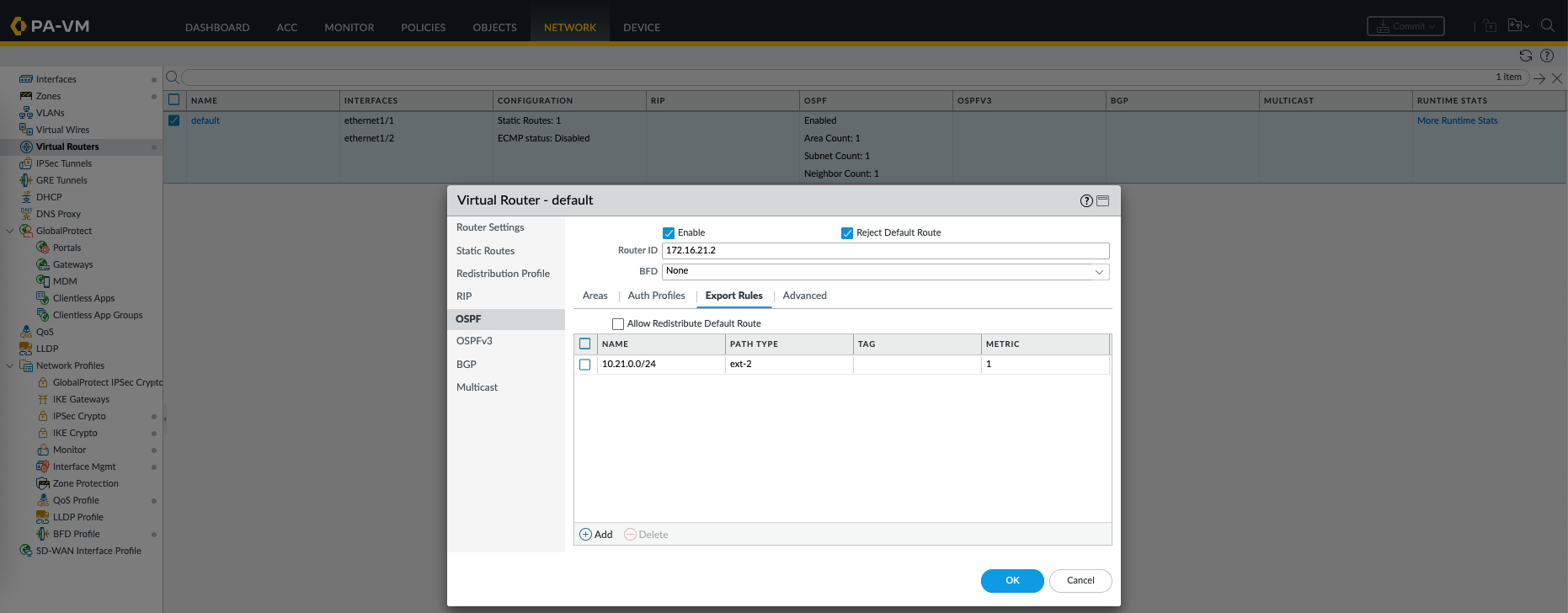
On Palo side, we configure OSPF on the Virtual Router, here we enable OSPF, give it Router ID, Area 0, and interfaces to be part of neighborship
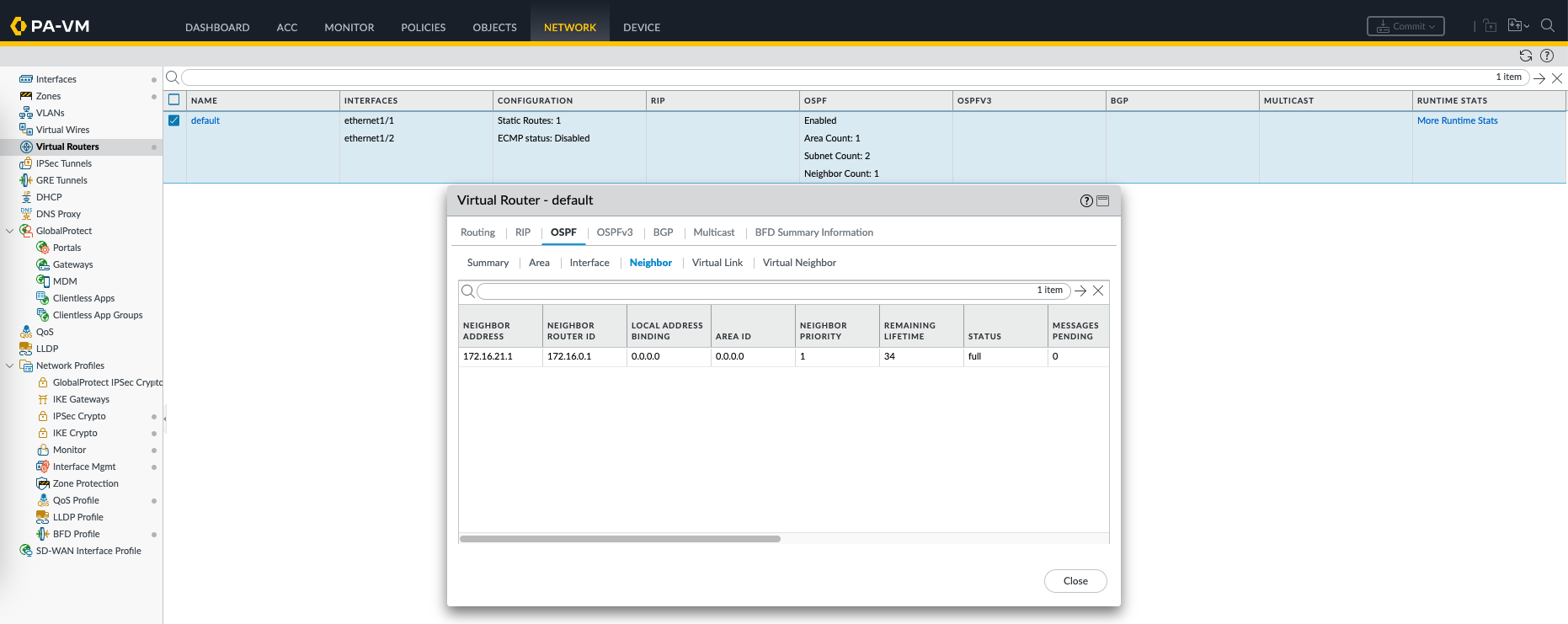
Now on the runtime stats we can see the OSPF process is up and running
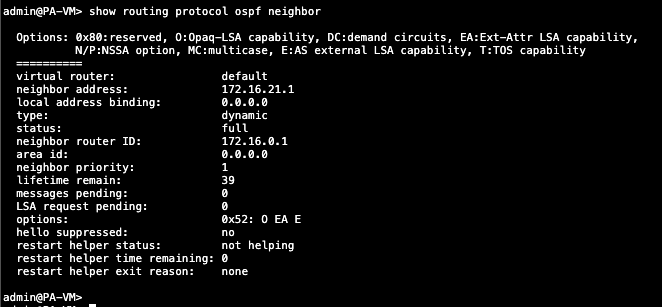
show routing protocol ospf neighbor
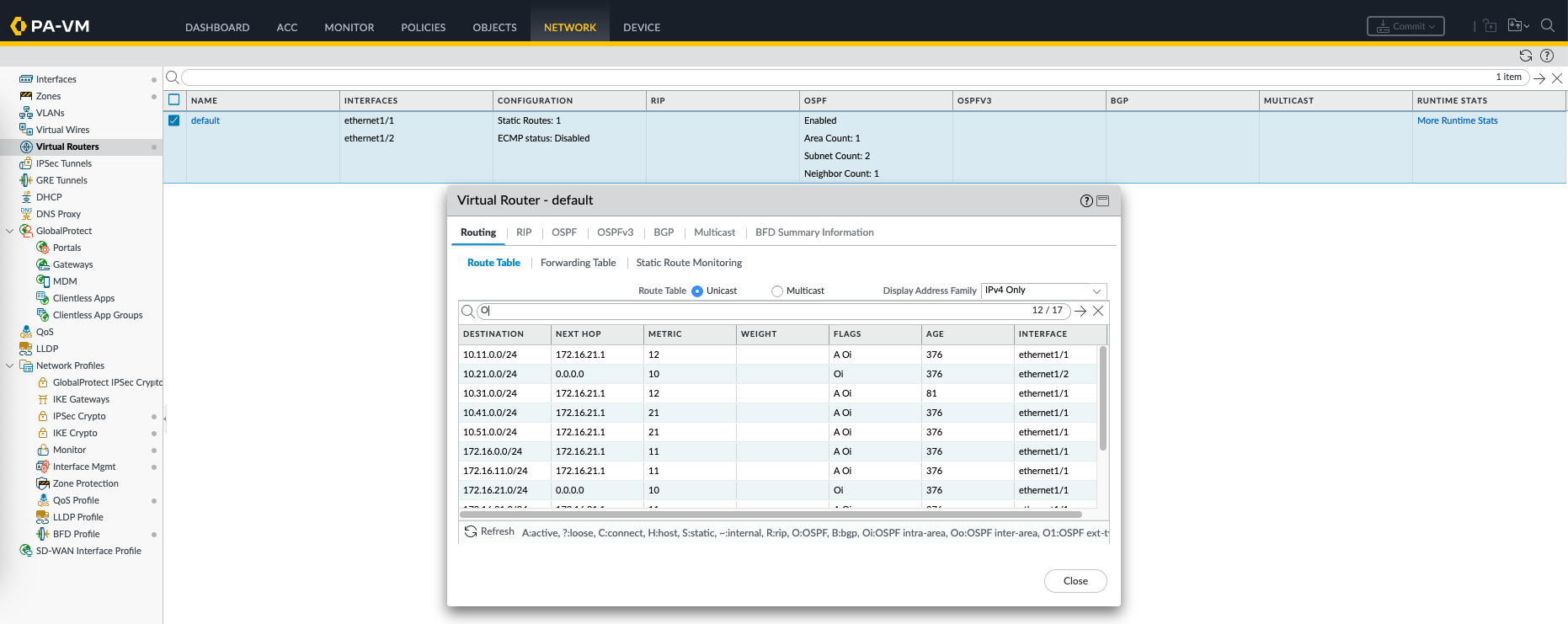
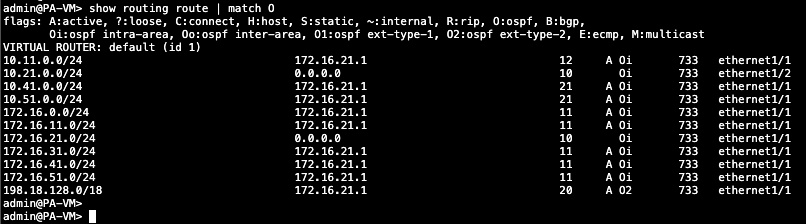
We can also see all the advertised routes we receive from OSPF
show routing route
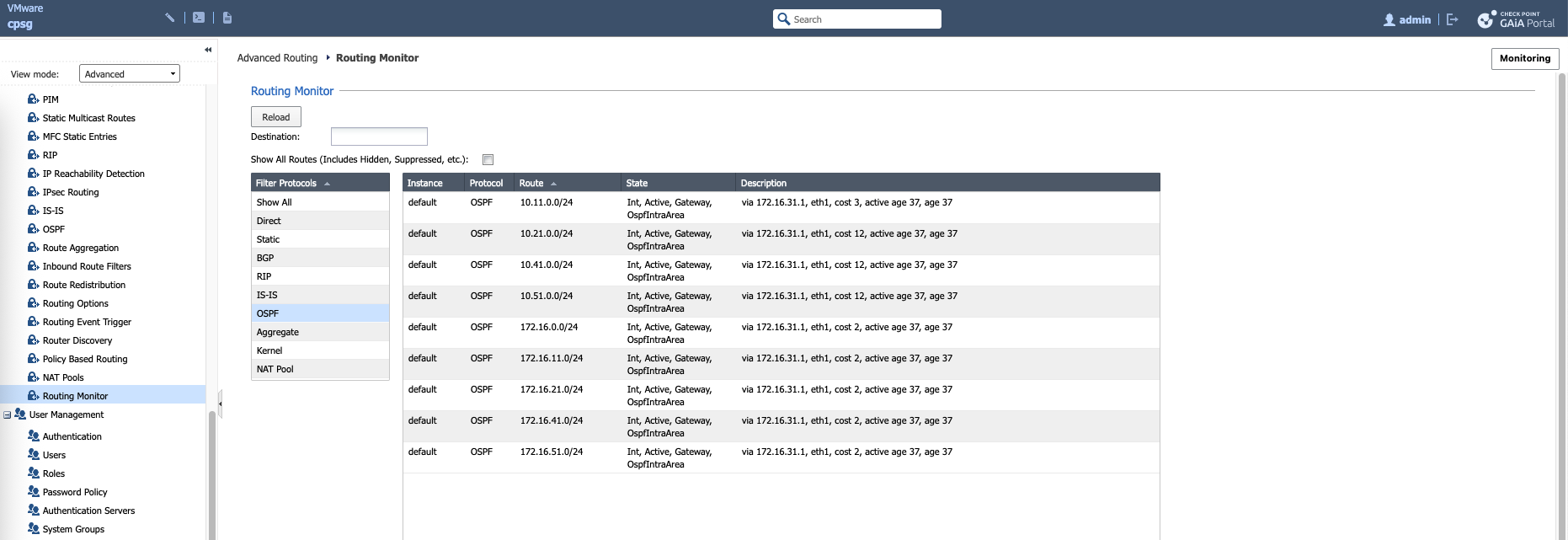
Check Point
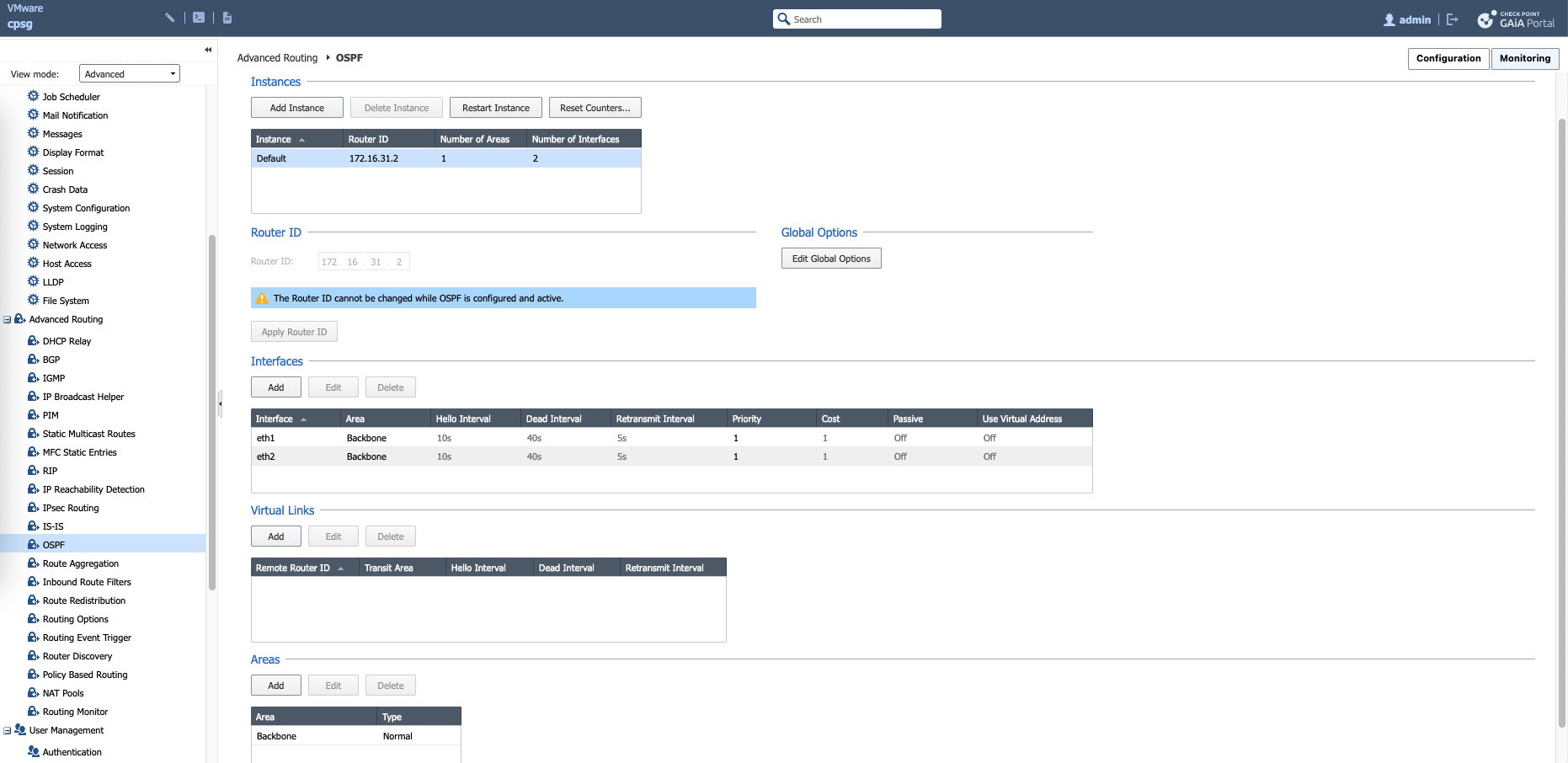
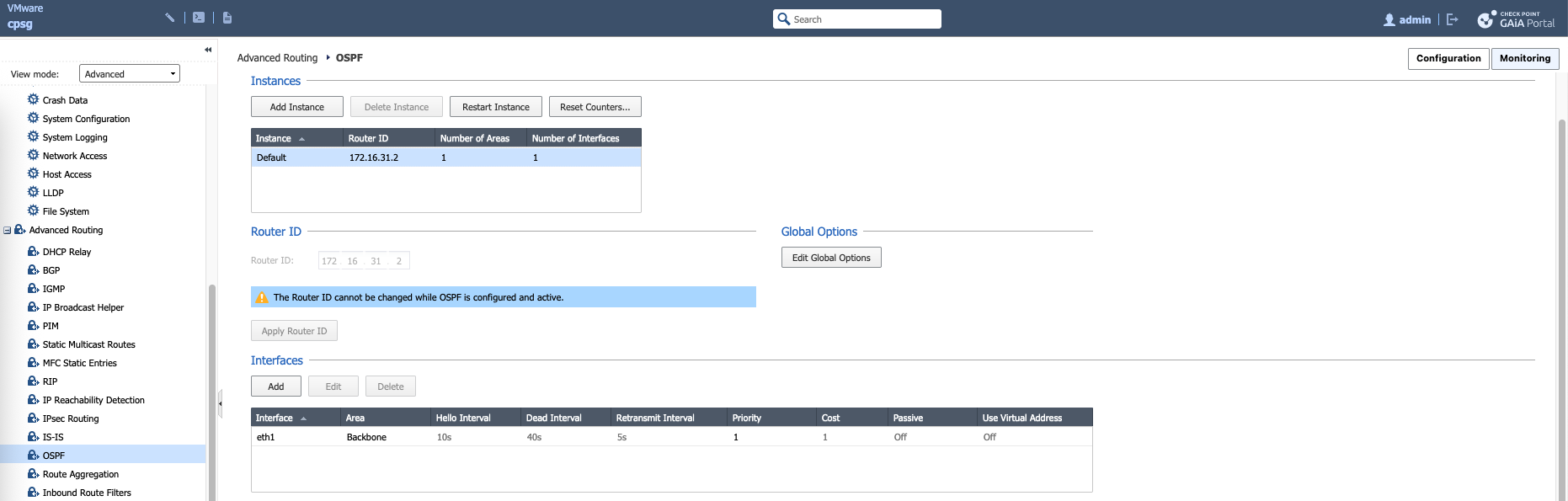
On Check Point side, we configure OSPF through GAIA, here we create an Area 0 (Backbone), give it Router ID, and add the interface members
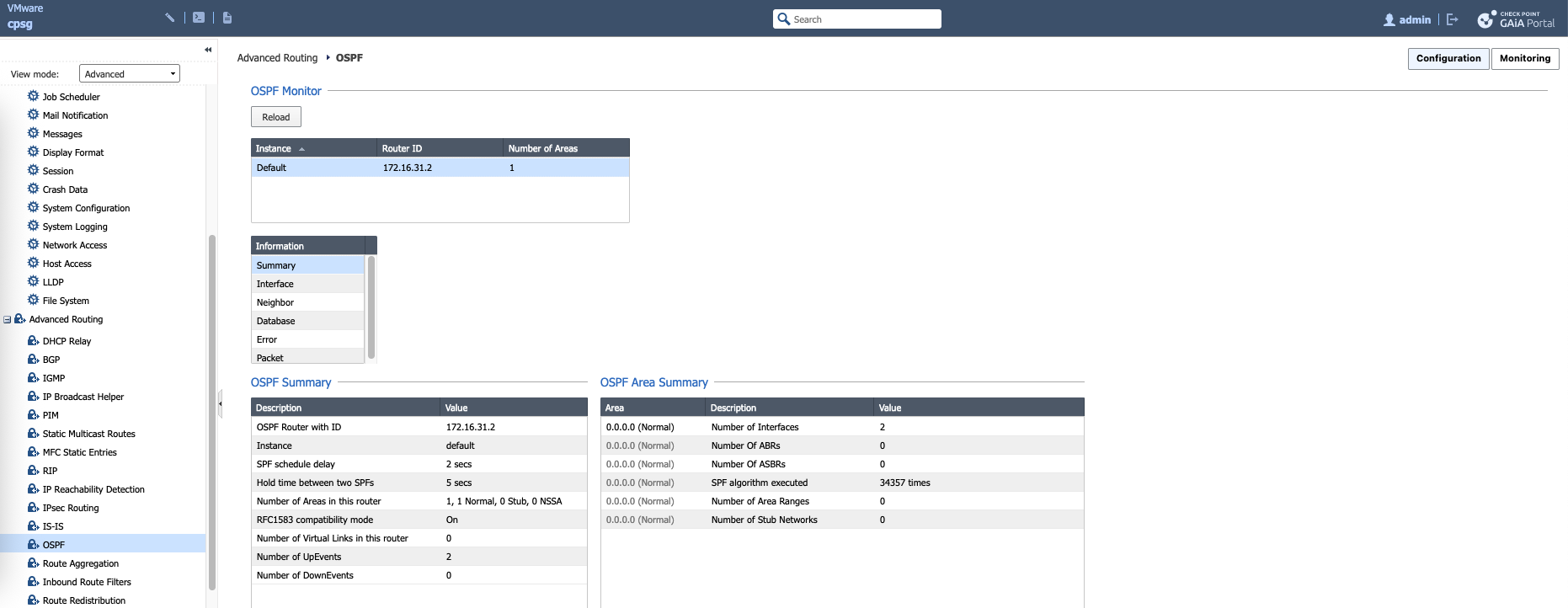
On Monitoring tab, we can see the OSPF process is now running
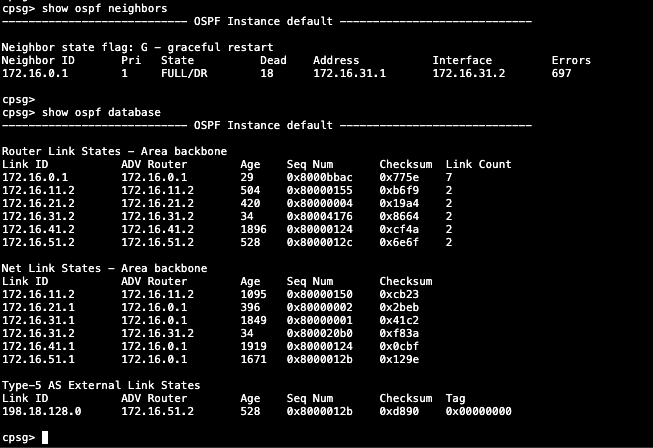
show ospf neighbors
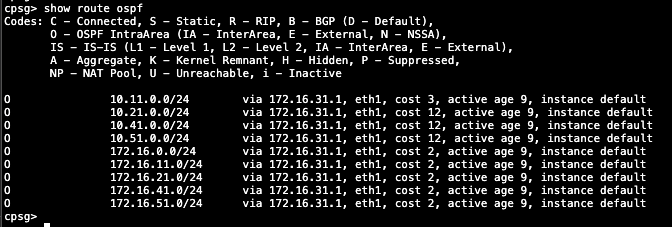
On routing monitors we can also see the received routes
show route ospf
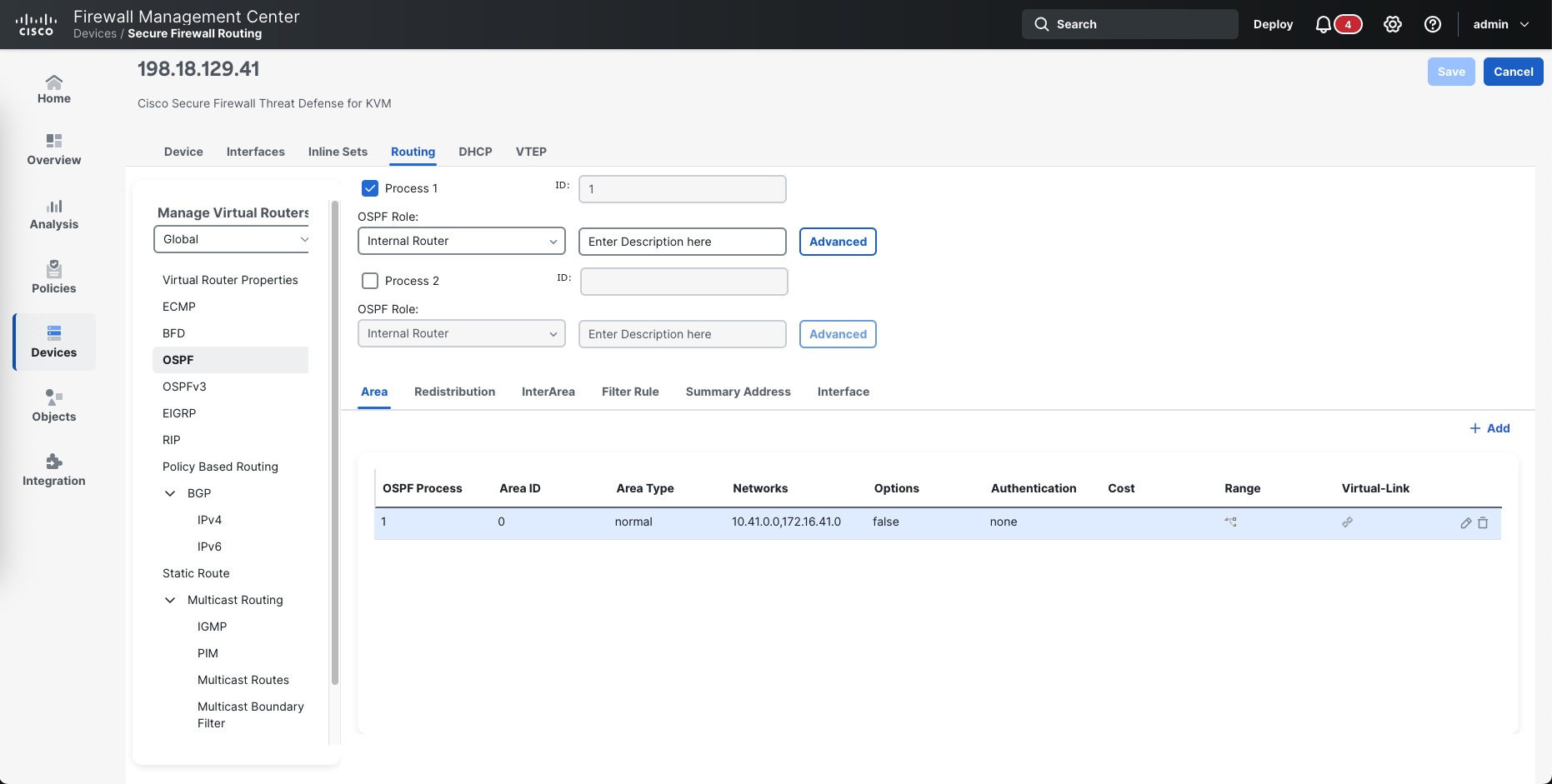
Cisco FTD
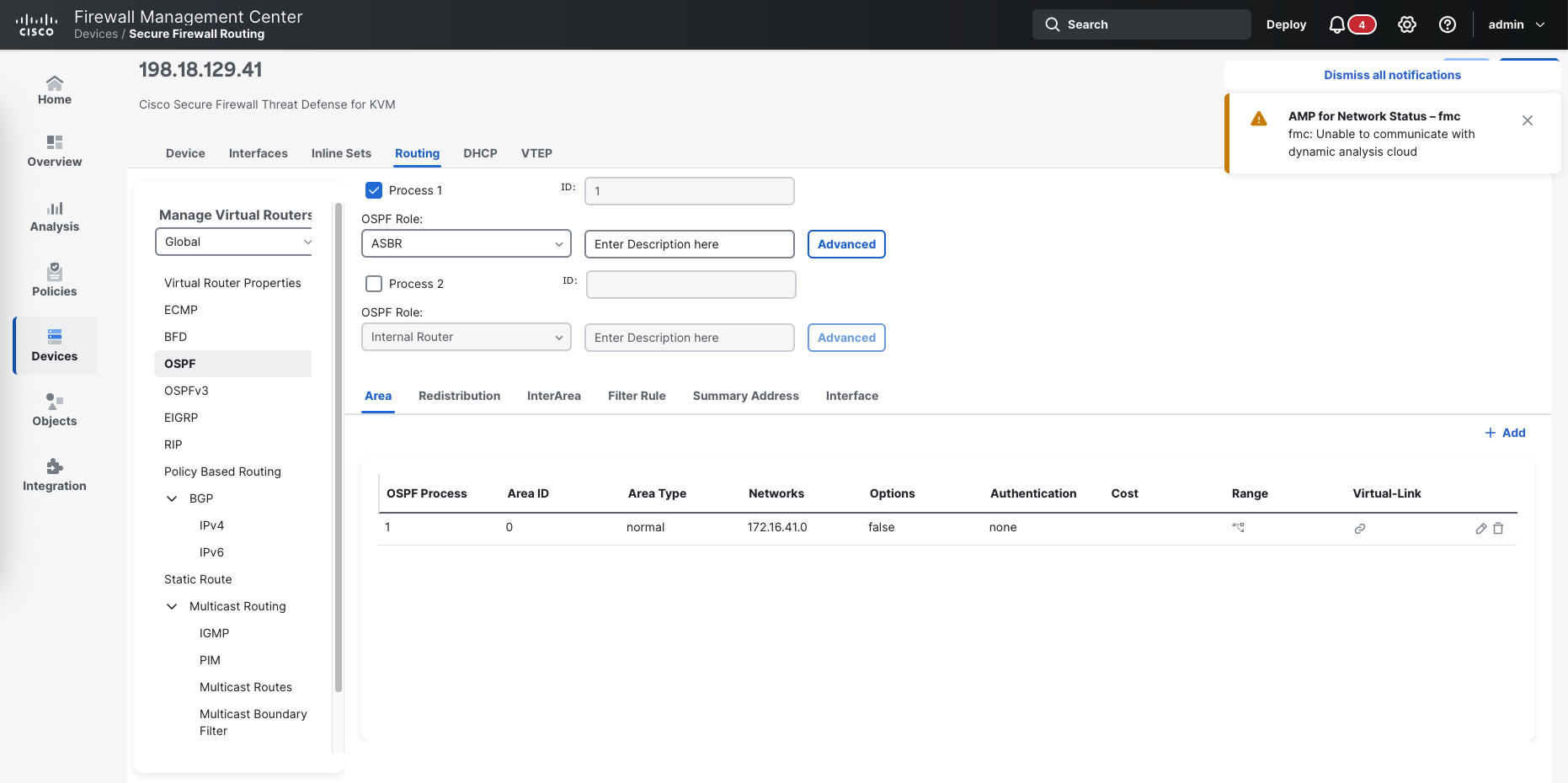
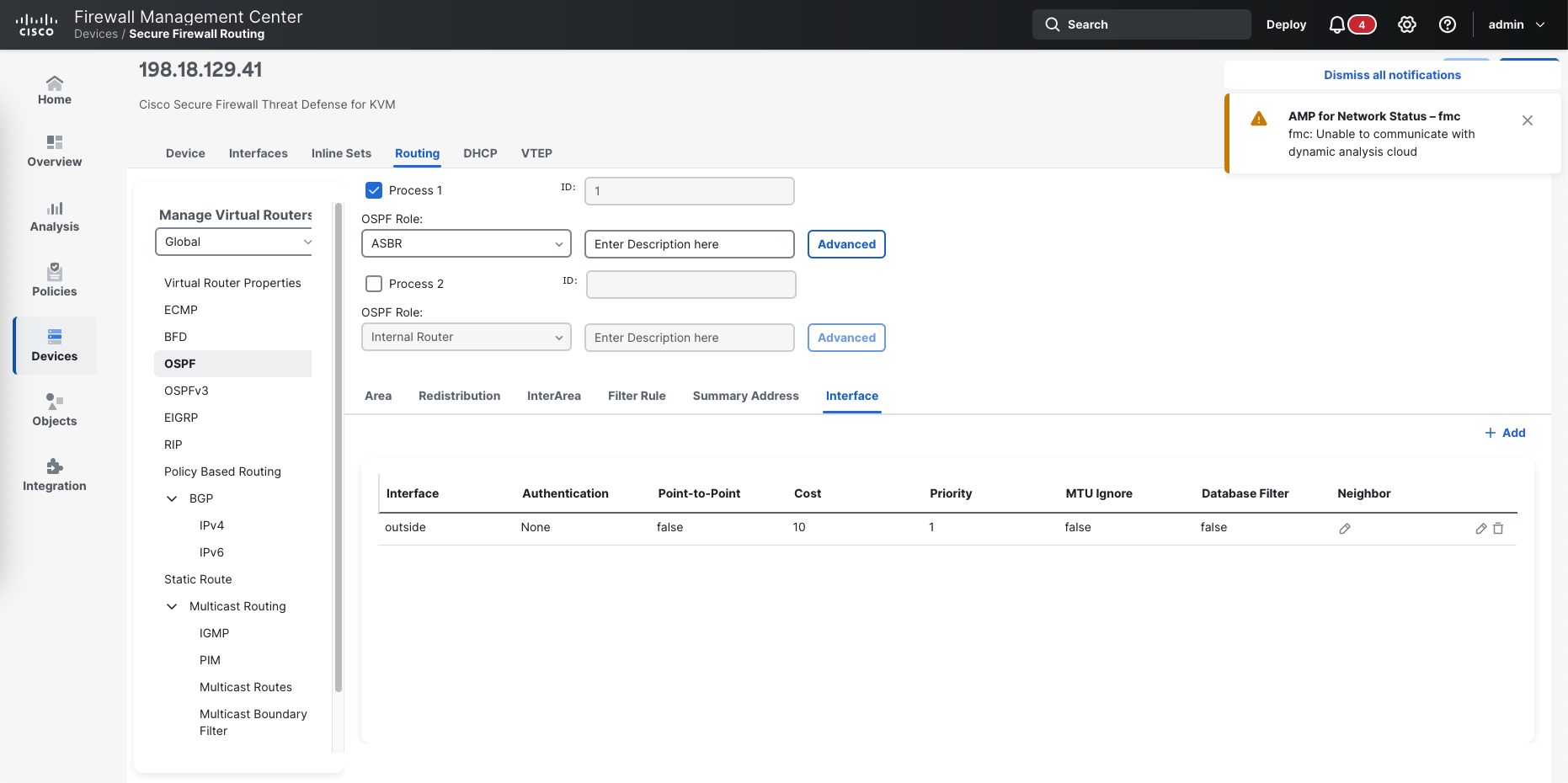
On FTD managed by FMC, we can enable OSPF on the Routing tab, here we enable the OSPF process as Internal Router, then add the Area 0 with the networks that we wish to be advertised
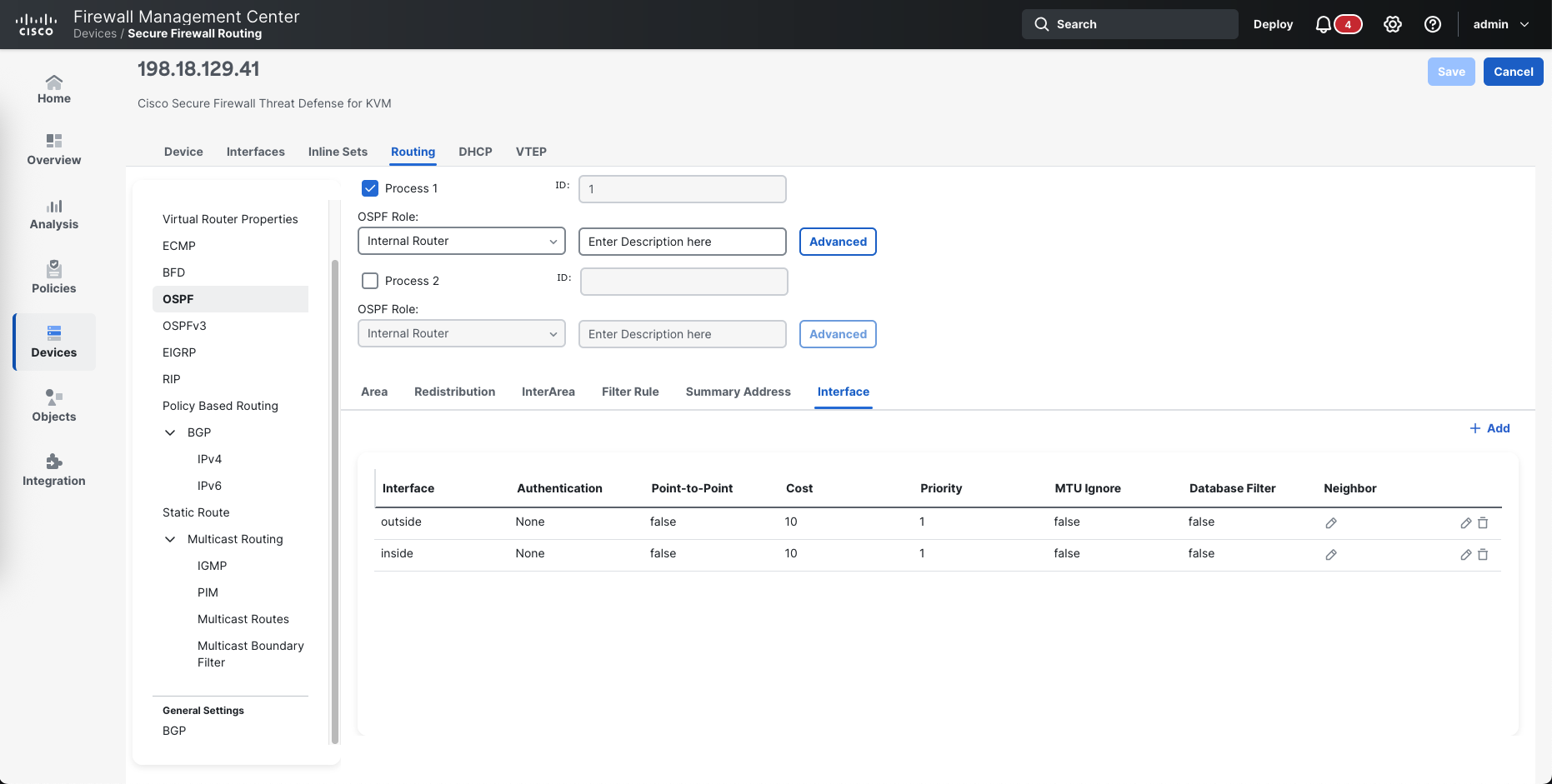
Then on Interface, add the interface members
To verify OSPF process, run the cli commands
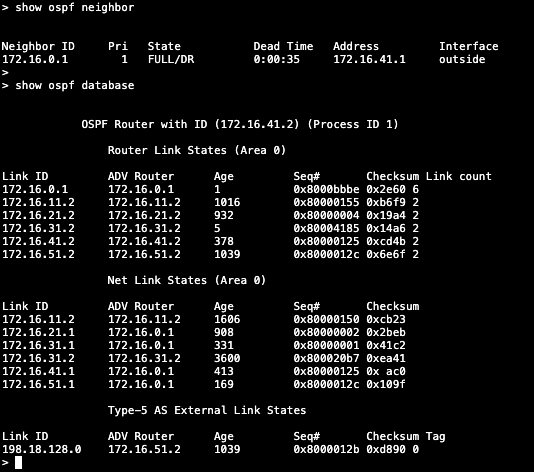
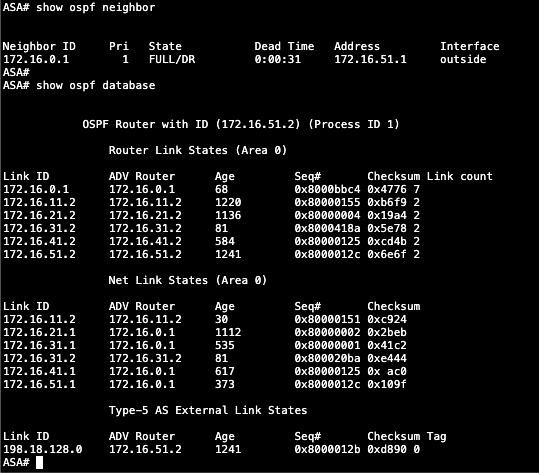
show ospf neighbor
show ospf database
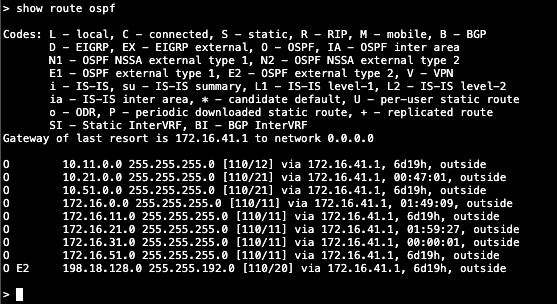
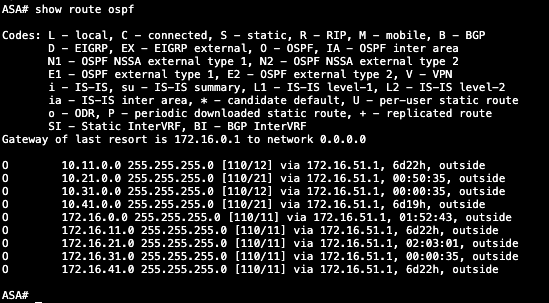
show route ospf
Cisco ASA
Below is the OSPF configuration on the ASA side
1
2
3
4
router ospf 1
router-id 172.16.51.2
network 10.51.0.0 255.255.255.0 area 0
network 172.16.51.0 255.255.255.0 area 0
Run the commands to verify OSPF process
show ospf neighbor
show route ospf
Redistribute
The configuration above enables OSPF process on all interface members to advertise their networks, even though not all interface is pointing to another OSPF neighbor. Here we will clean up the configuration by only enabling OSPF process on the needed interface, and redistribute the connected network so it can be advertised.
After configured, the advertised network will look like this
- Type 1 (E1) = external cost + internal OSPF cost.
- Type 2 (E2) = external cost only (default).
Fortigate
Here we deleted the inside network
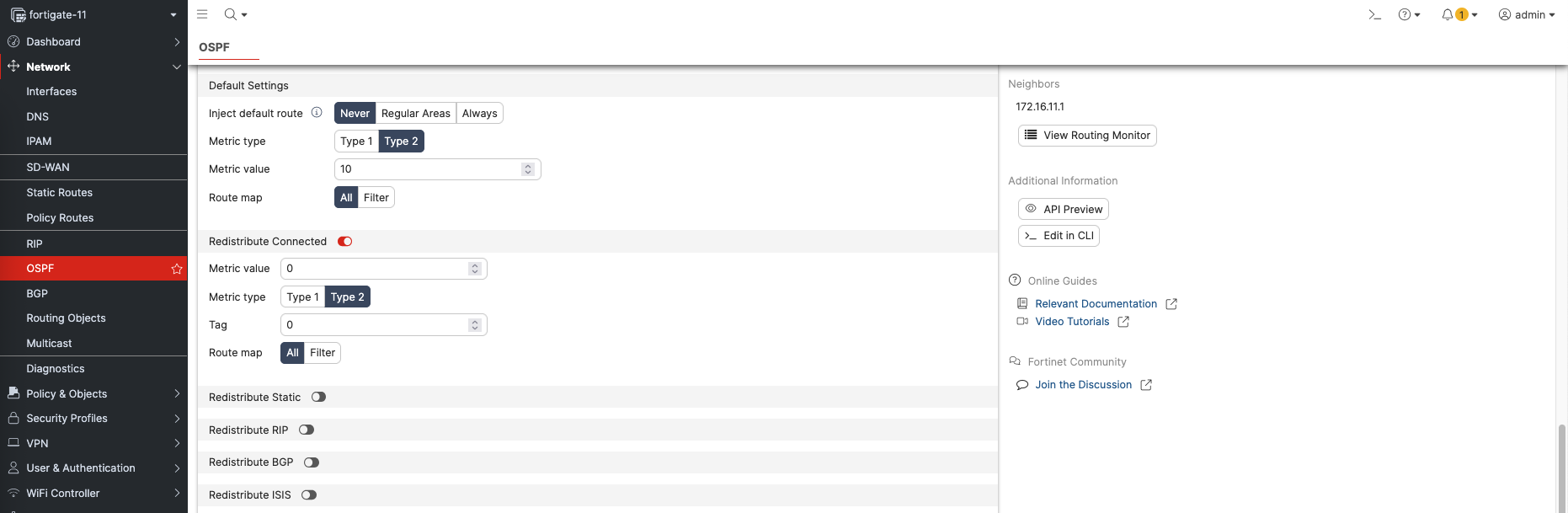
Then we enable the Redistribute Connected option
Palo Alto
On the Area 0, we remove the internal interface
And on the Export Rules, we add the network that we’d like to redistribute
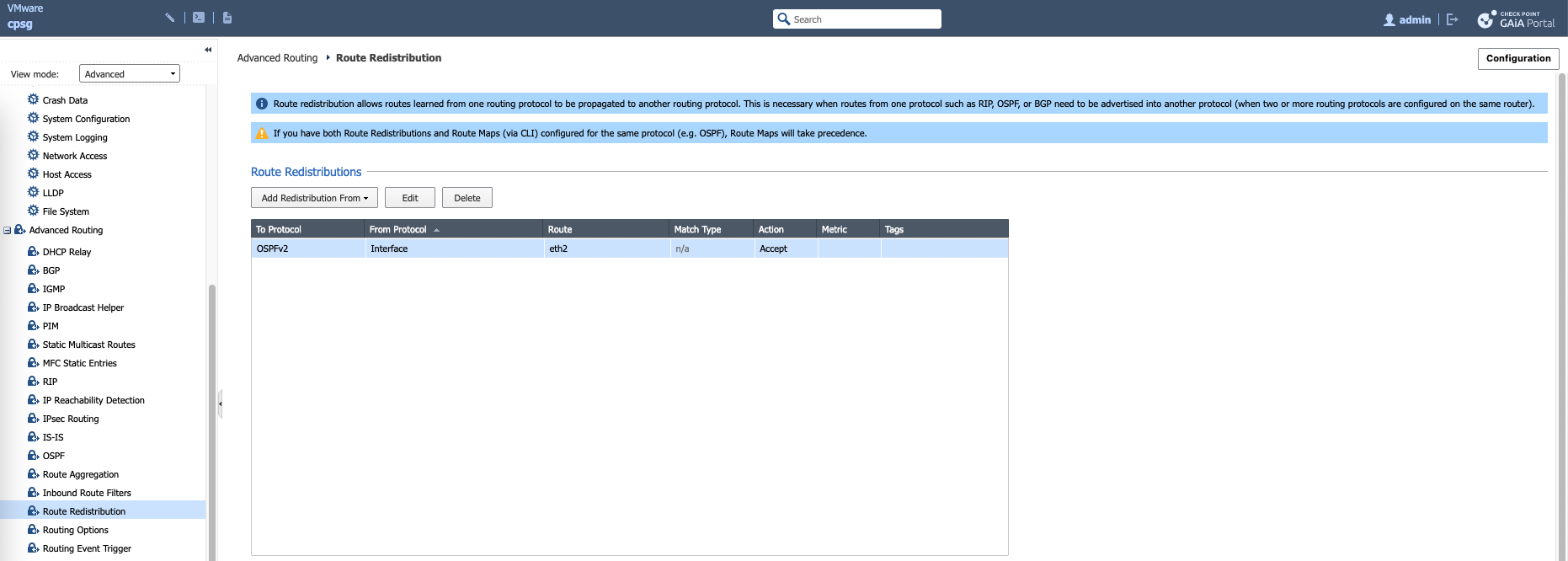
Check Point
Here we remove the internal interface
Then on Route Redistribution, add a new redistribution from the same interface
Cisco FTD
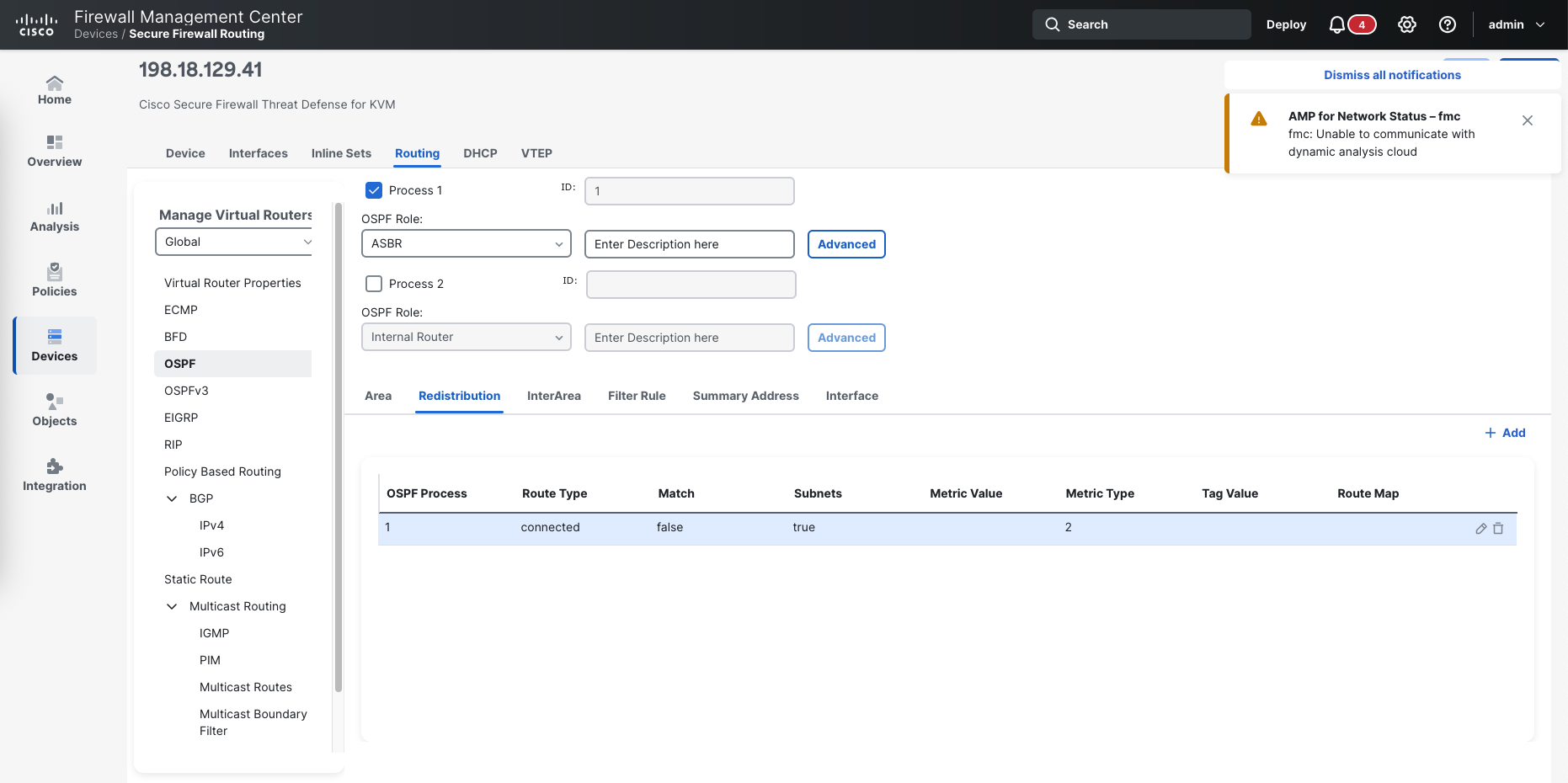
Here we need to change the OSPF role from Internal Router to ASBR to enable route redistribution, then delete the network from the OSPF process
We also remove the inside interface
Then on Redistribution, we add one with connected route type
Cisco ASA
Here’s the configuration on ASA side
1
2
3
4
router ospf 1
router-id 172.16.51.2
network 172.16.51.0 255.255.255.0 area 0
redistribute connected subnets