Cisco ISE Active Directory Integration
Active Directory (AD) integration allows organizations to leverage their existing AD infrastructure for authentication and authorization purposes within the Cisco ISE environment.
Adding Active Directory Server
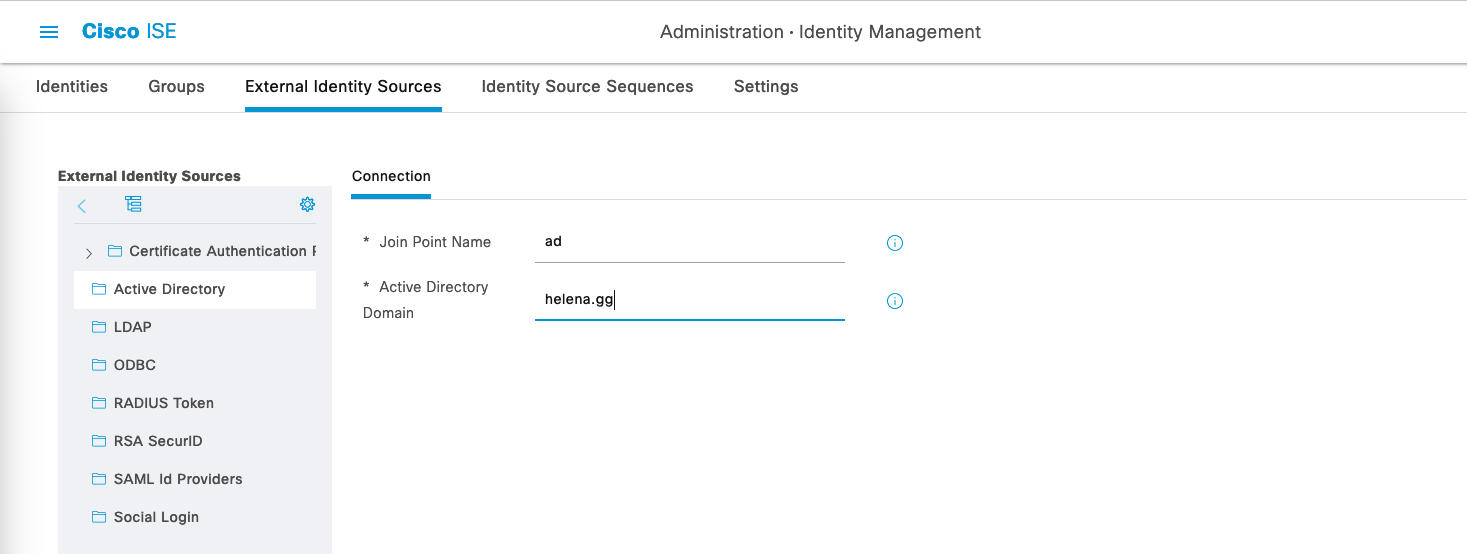
First lets add an AD server, on Cisco ISE go to Administration » External Identity Sources
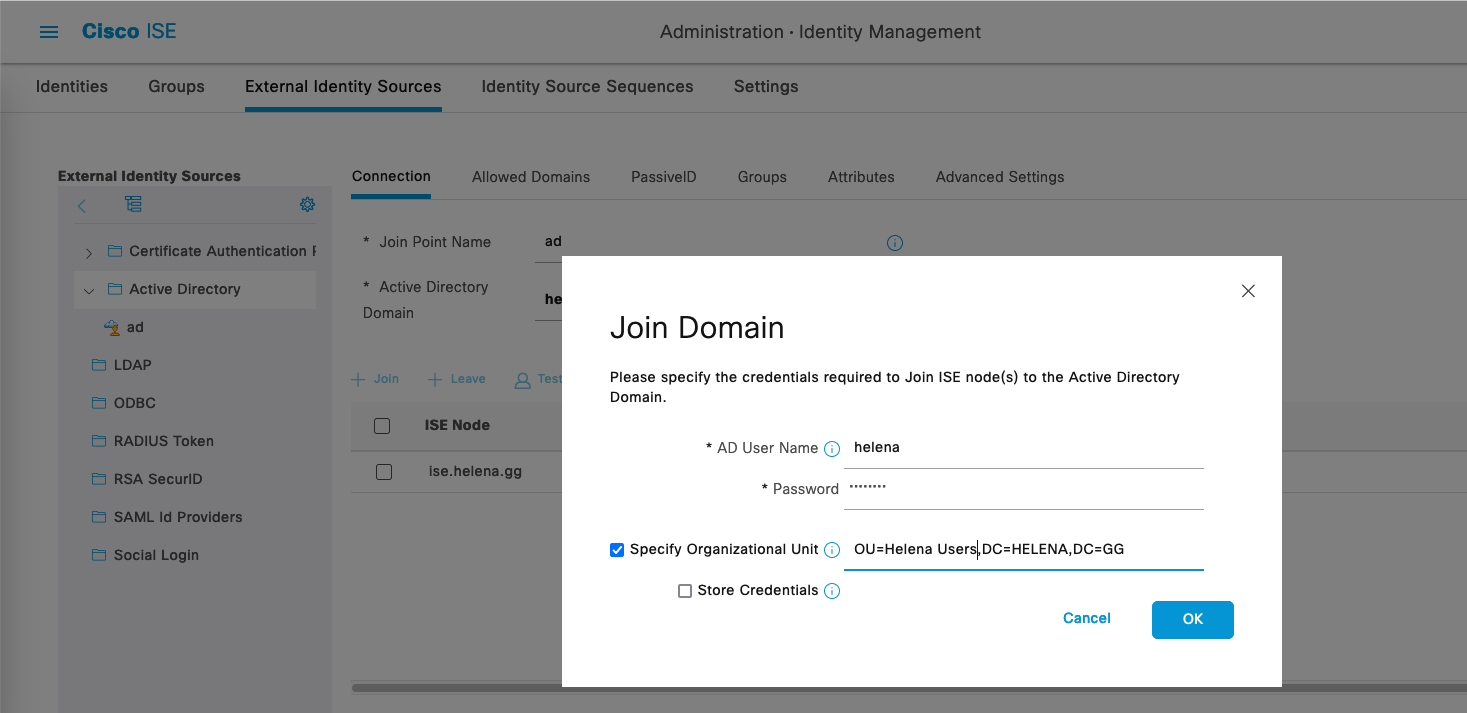
Enter the Domain Credentials and optionally the targeted OU
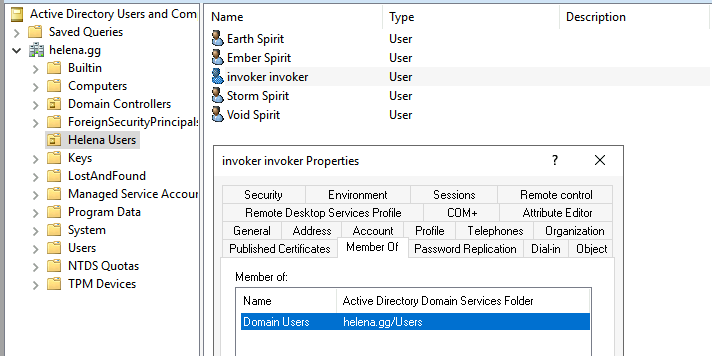
Here’s what the Helena Users OU contains, which it has 5 users that we will use for auth
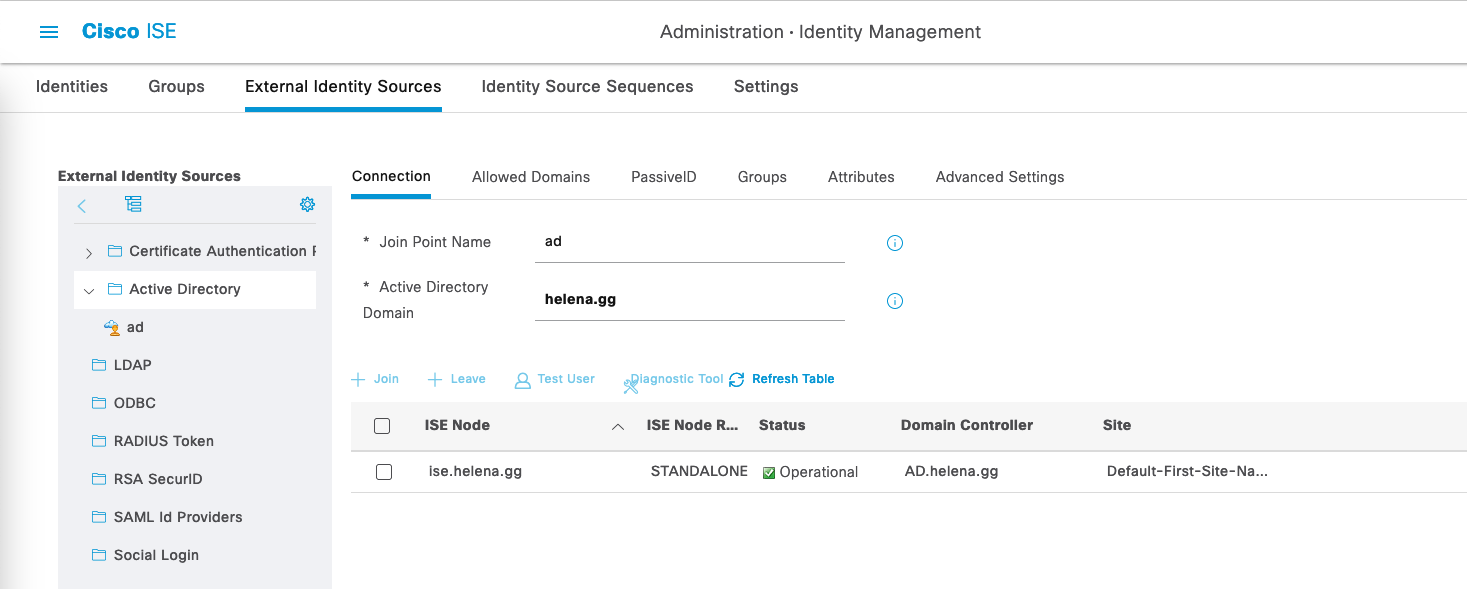
Back on ISE, make sure the ISE is connected and Operational for its integration to the AD Server
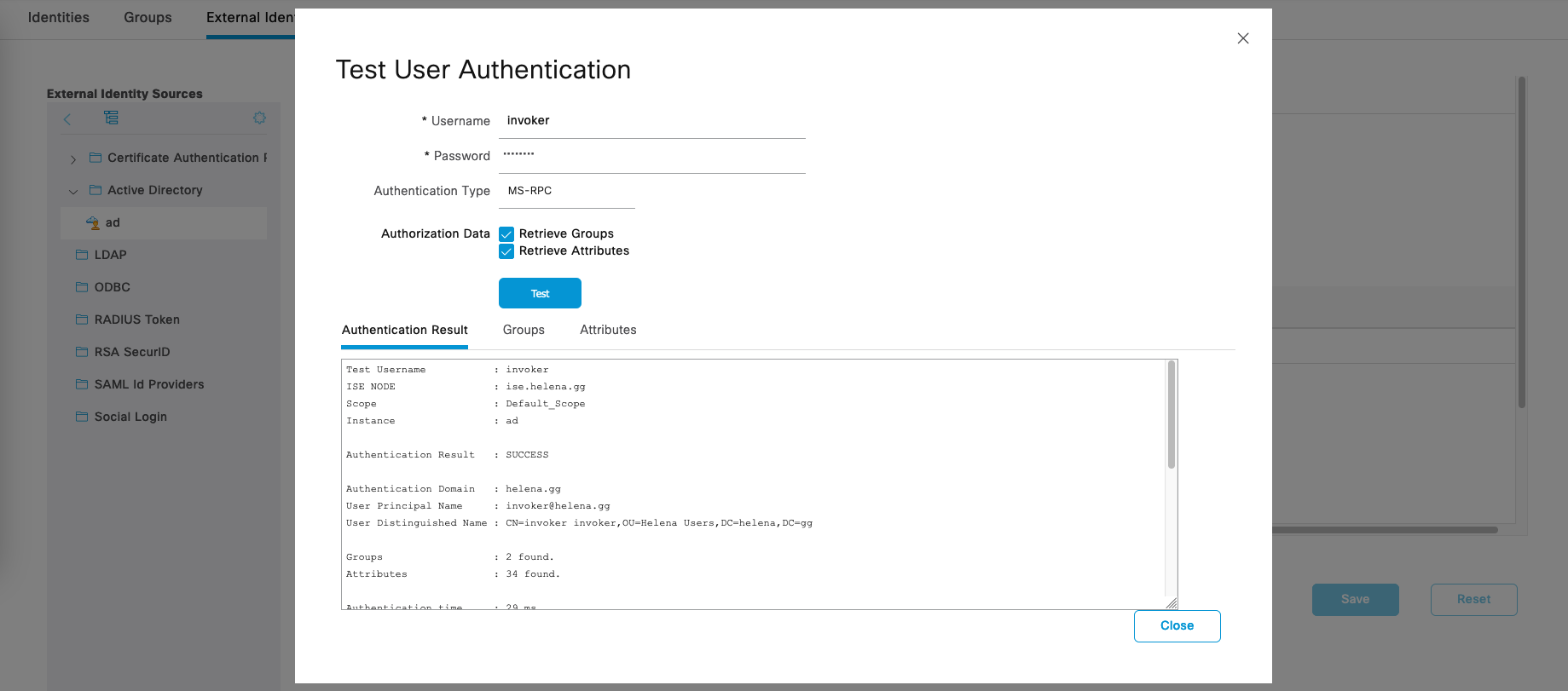
Select Test User to make an auth test with the users within the AD’s OU
Importing Domain Groups
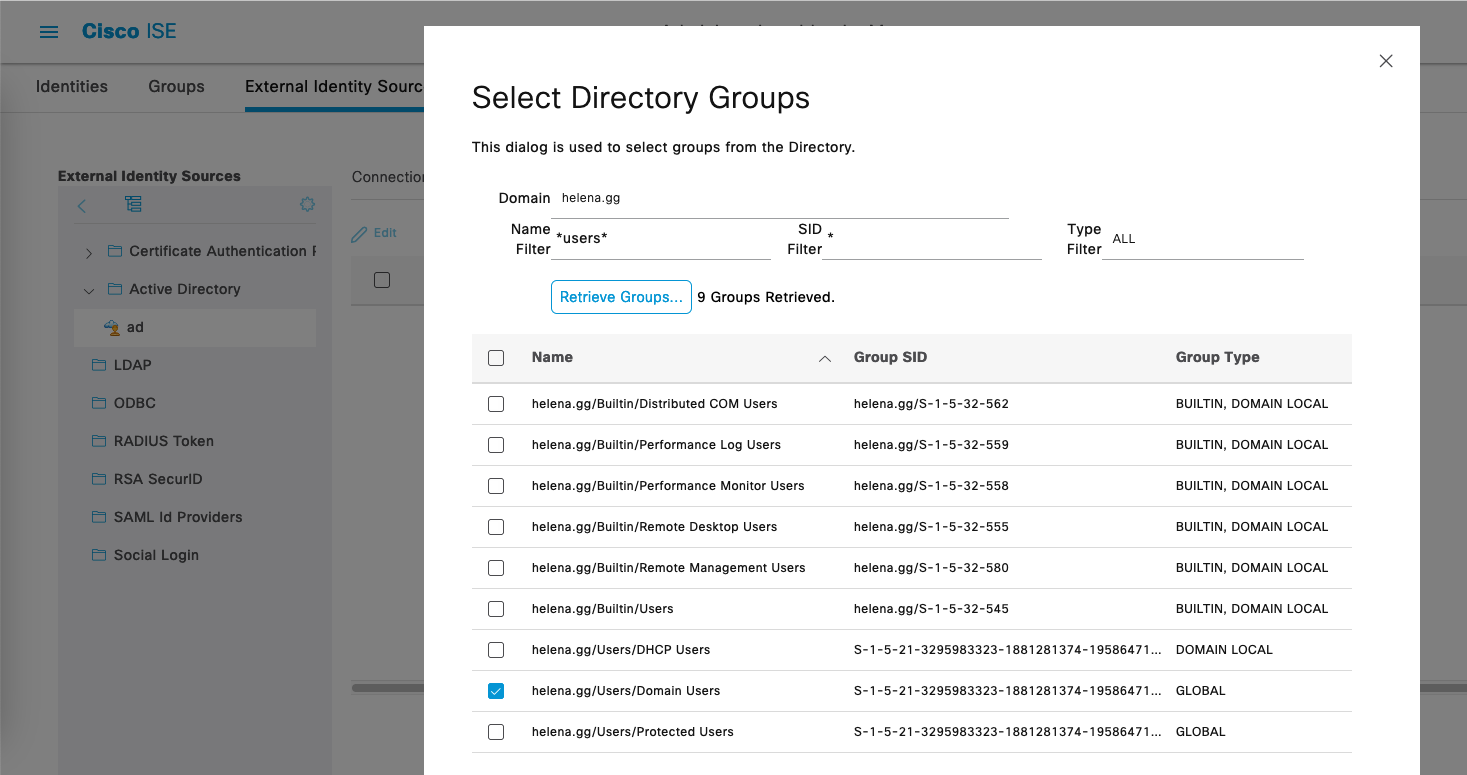
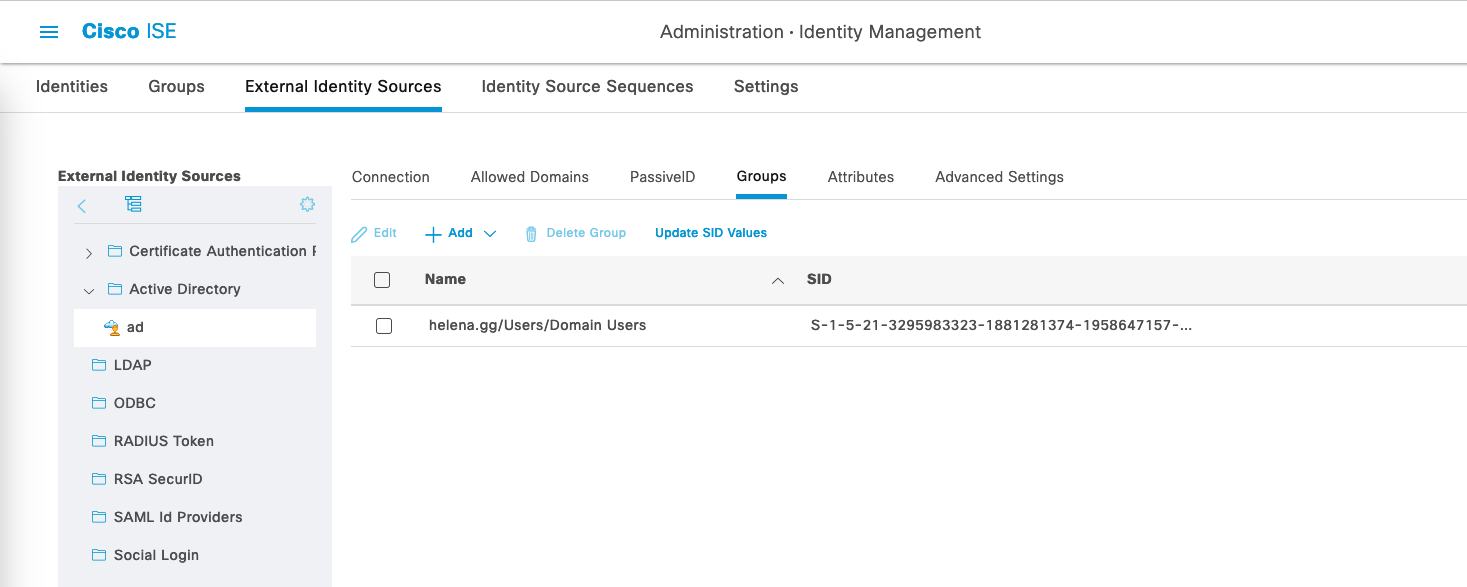
Still on the same page, go to Groups and select Add » Select Groups from Directory, and then select the desired groups
Configuring Authentication Search List
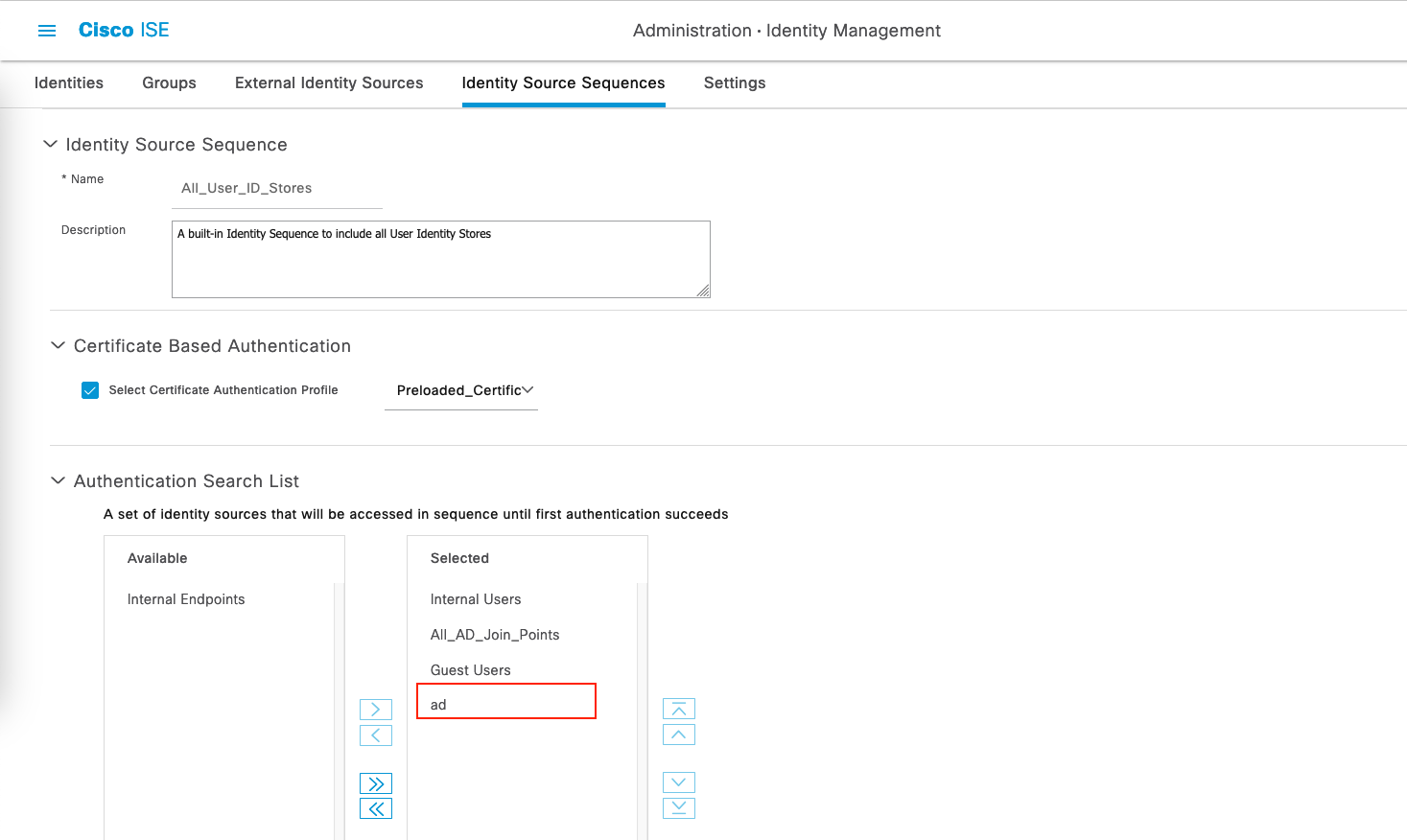
On Administration » Identity Source Sequences, create a new profile or just edit the default “All_User_ID_Stores” and add the “AD” identity to it
Configuring RADIUS
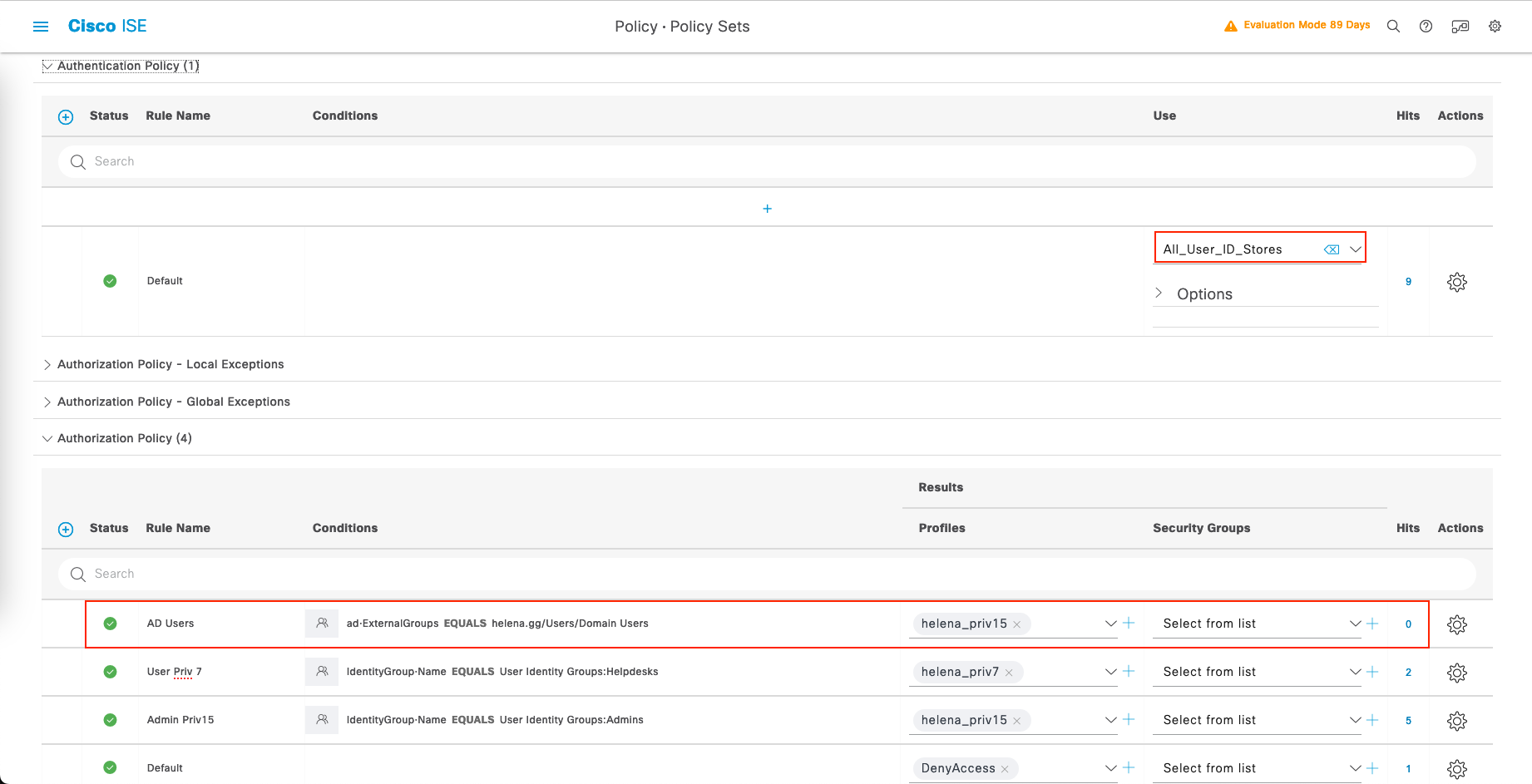
Now we configure RADIUS to use the AD users to authenticate, on Policy » Policy Sets, select the existing policy and add the expression to allow AD Users to authenticate
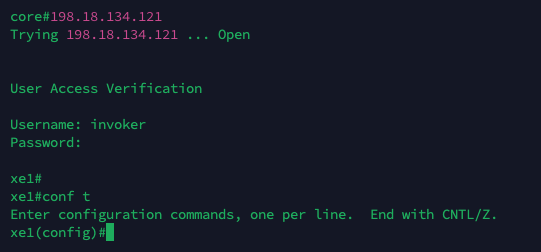
Now on the Network Devices, we should be able to use AD Users to authenticate through RADIUS
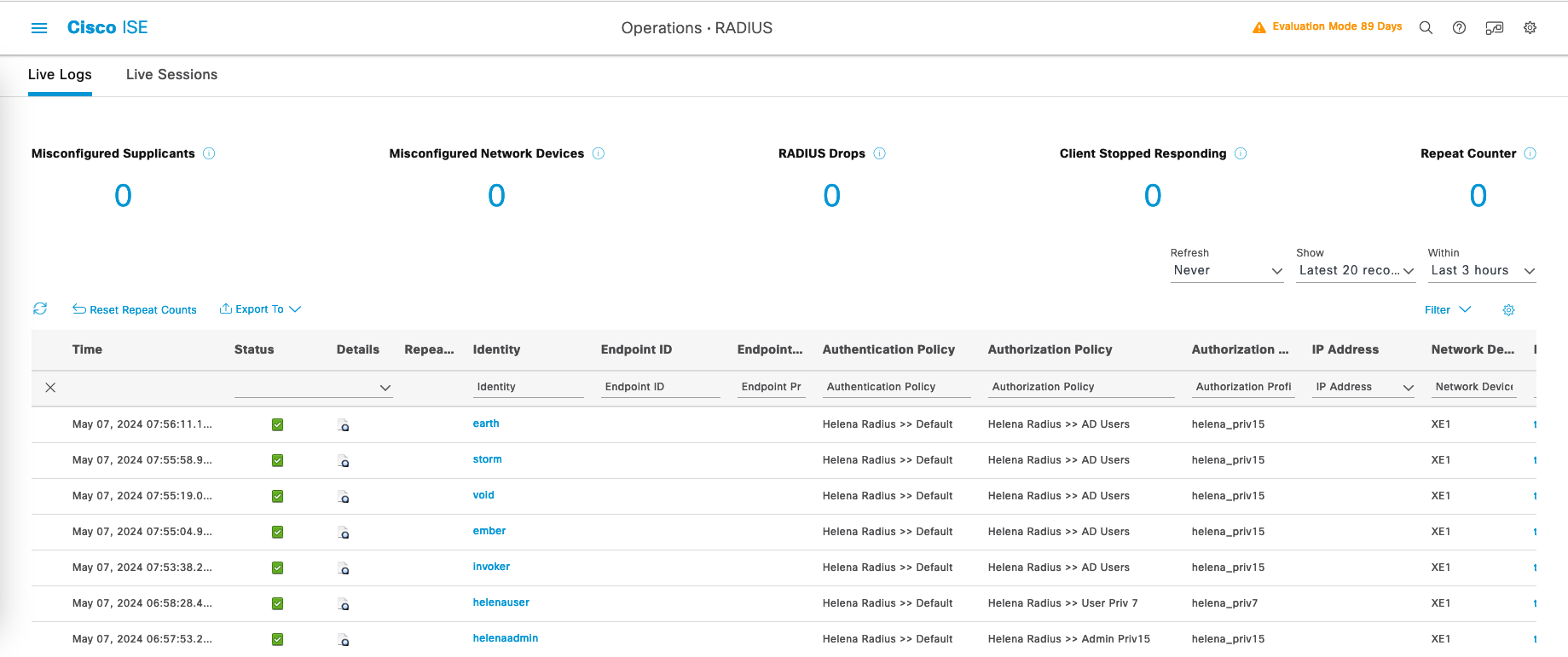
On RADIUS Live Logs, we can see all the AD Users that authenticate to the network devices
Configuring Admin Login
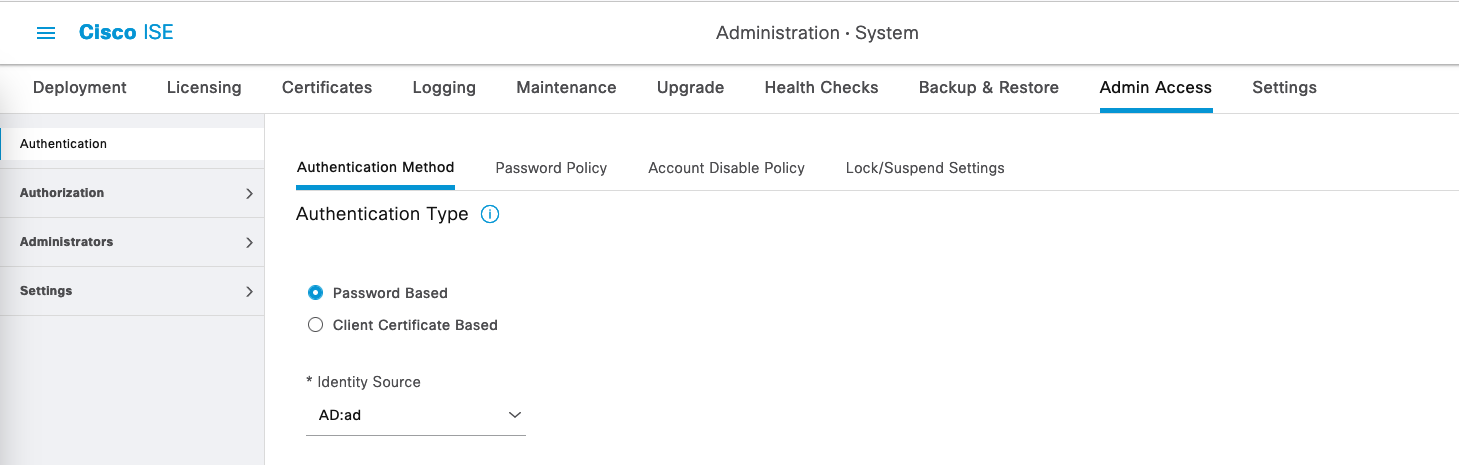
Now we will also use AD Users as admin logins to the ISE, on Administration » Admin Access, select the AD Server as the Identity Source
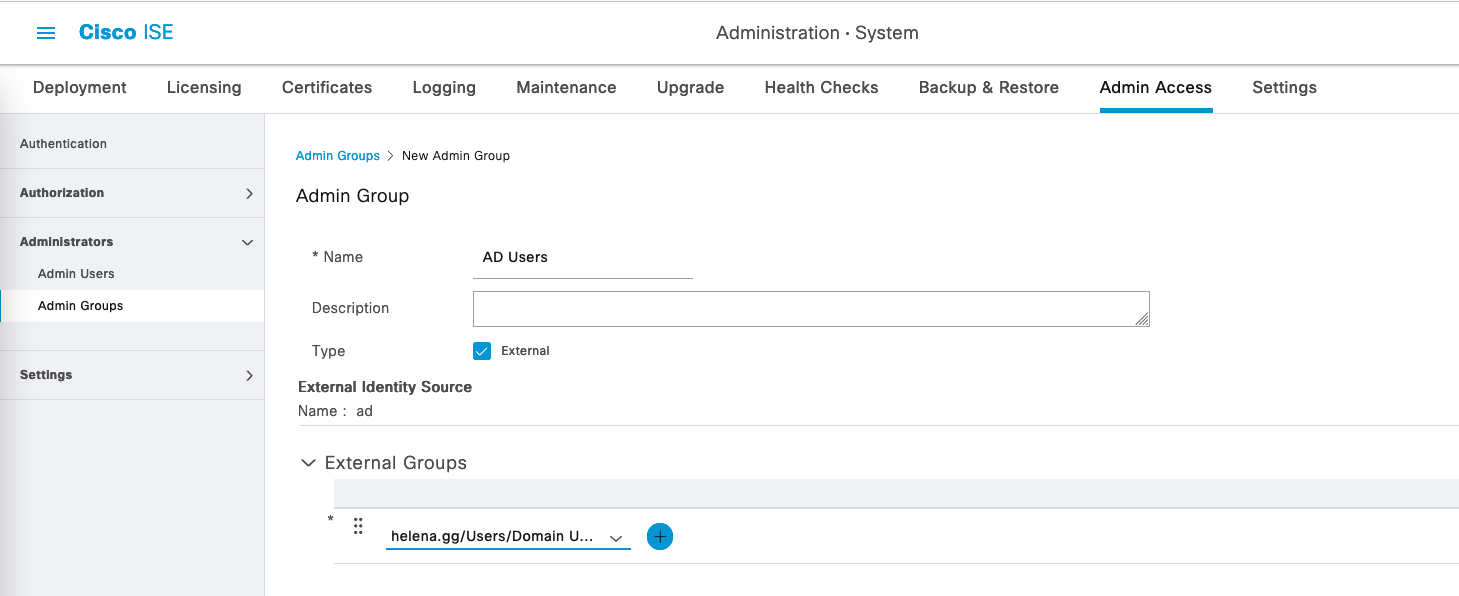
Next on Administrators » Admin Groups, create a new group pointing to the AD’s Domain Users
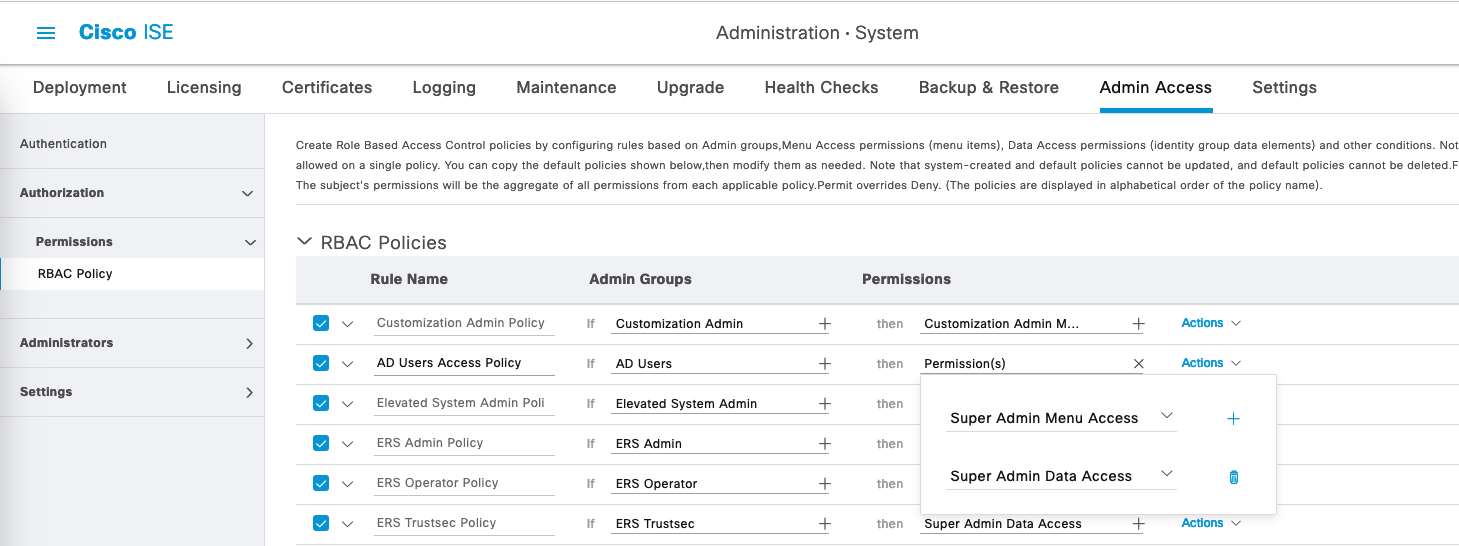
Then on Authorization » RBAC Policy, create a new policy that gives AD Users permission to Super Admin Menu and Data Access
RBAC means Role Based Access Control
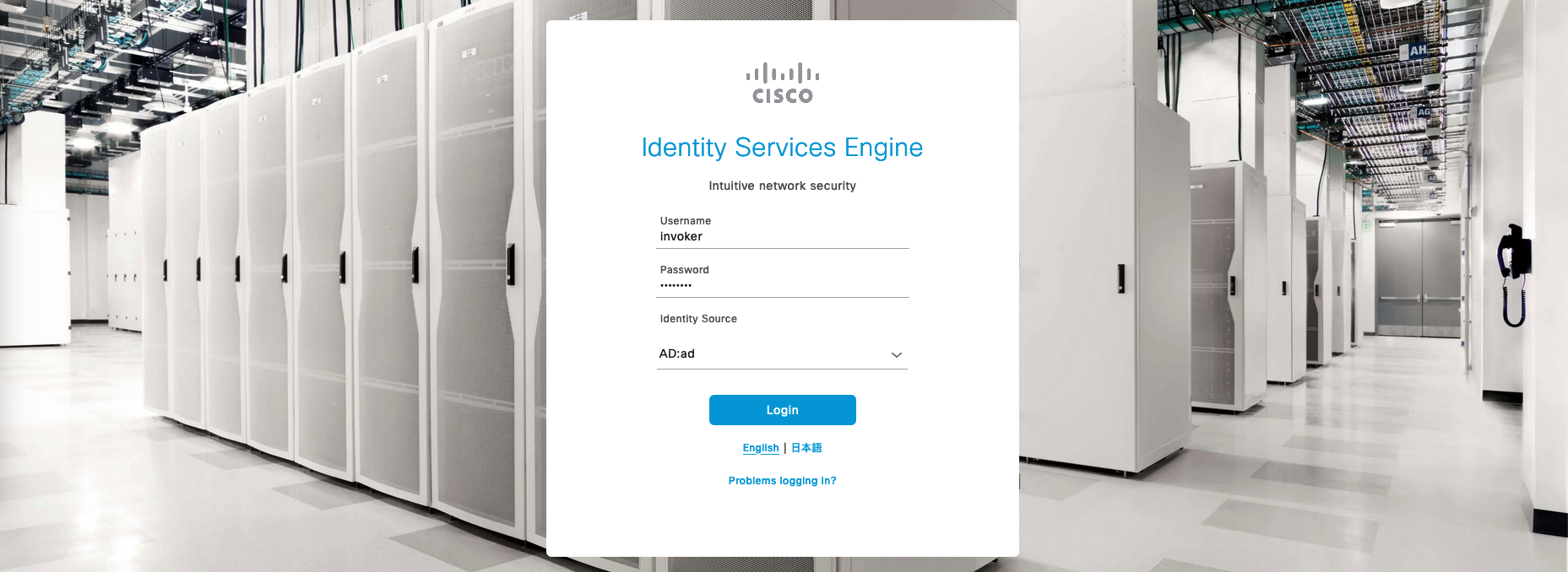
Now on the main login page, we should see an option to login from mulitple Identity Sources, which in this case is the existing Internal Users and the newly configured AD Users