Cisco ISE TACACS+ with F5 Virtual Server
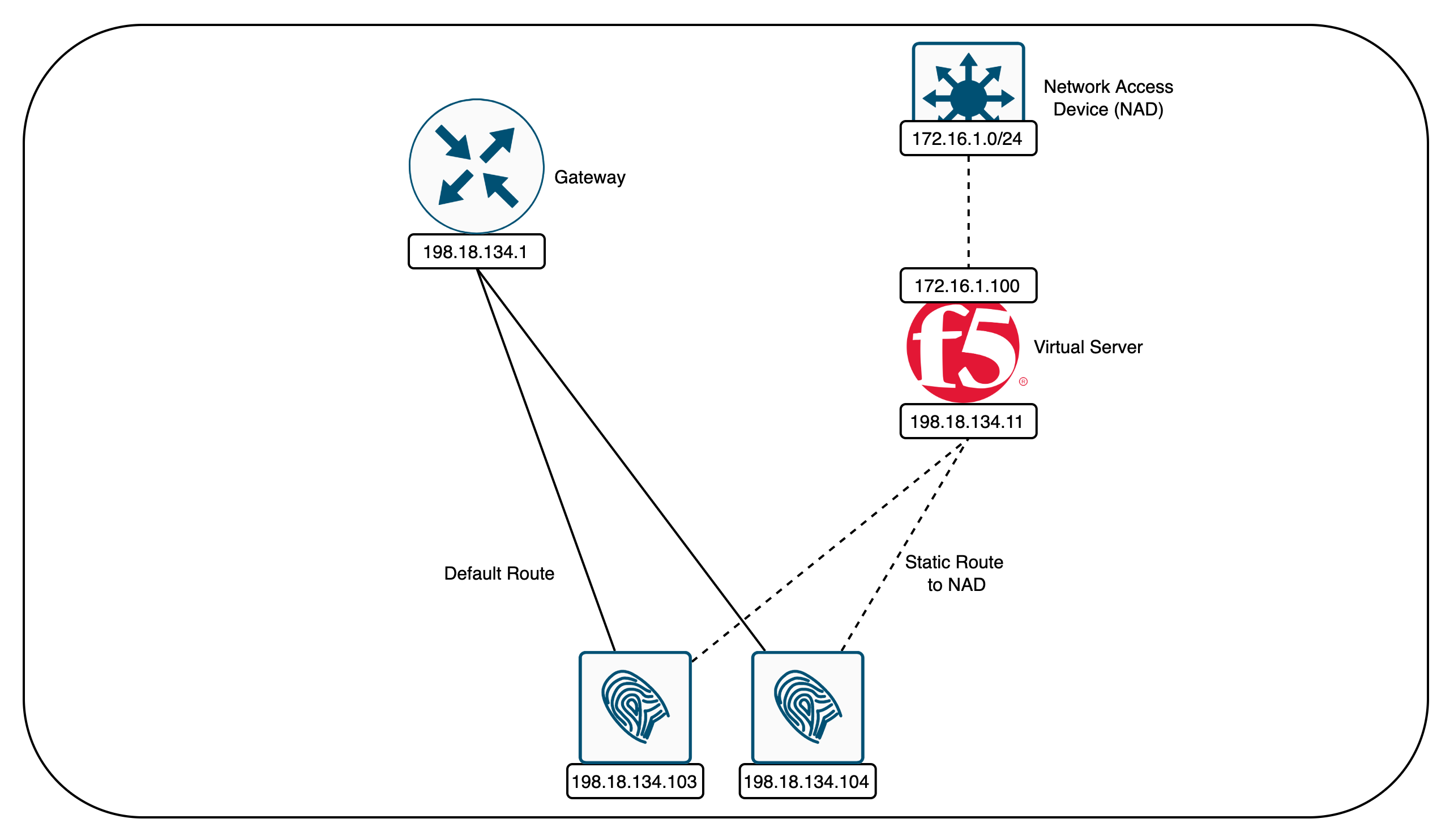
This configuration examines the use of an F5 Virtual Server as a load balancer for Cisco ISE TACACS+ servers. By configuring the F5 to balance TACACS+ traffic, it optimizes resource utilization and enhances fault tolerance across Cisco ISE instances, ensuring reliable and efficient management of network device access and security policies.
Configuring F5 Virtual Server
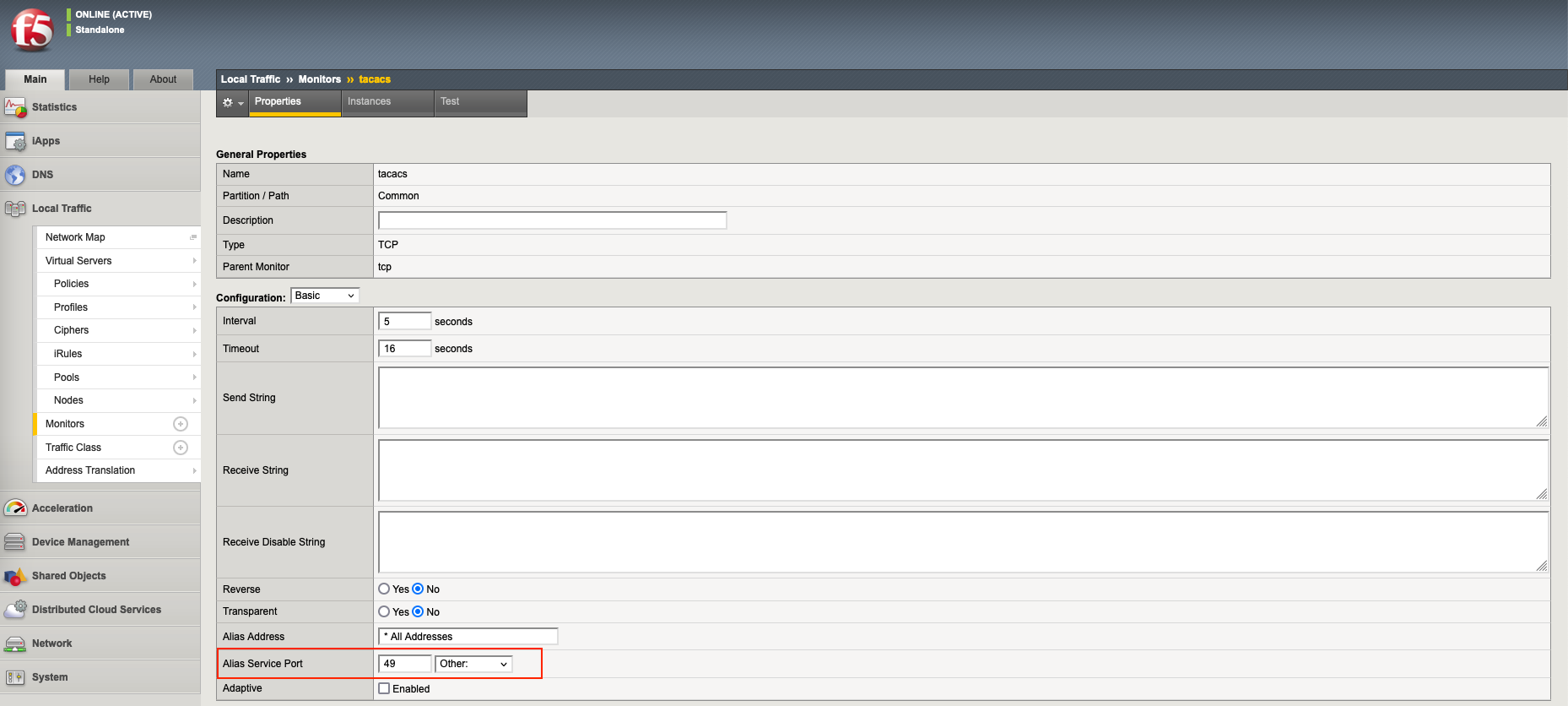
First lets configure a new Health Monitor to monitor the ISE’s tacacs service on port 49, on Local Traffic » Monitors create a new one
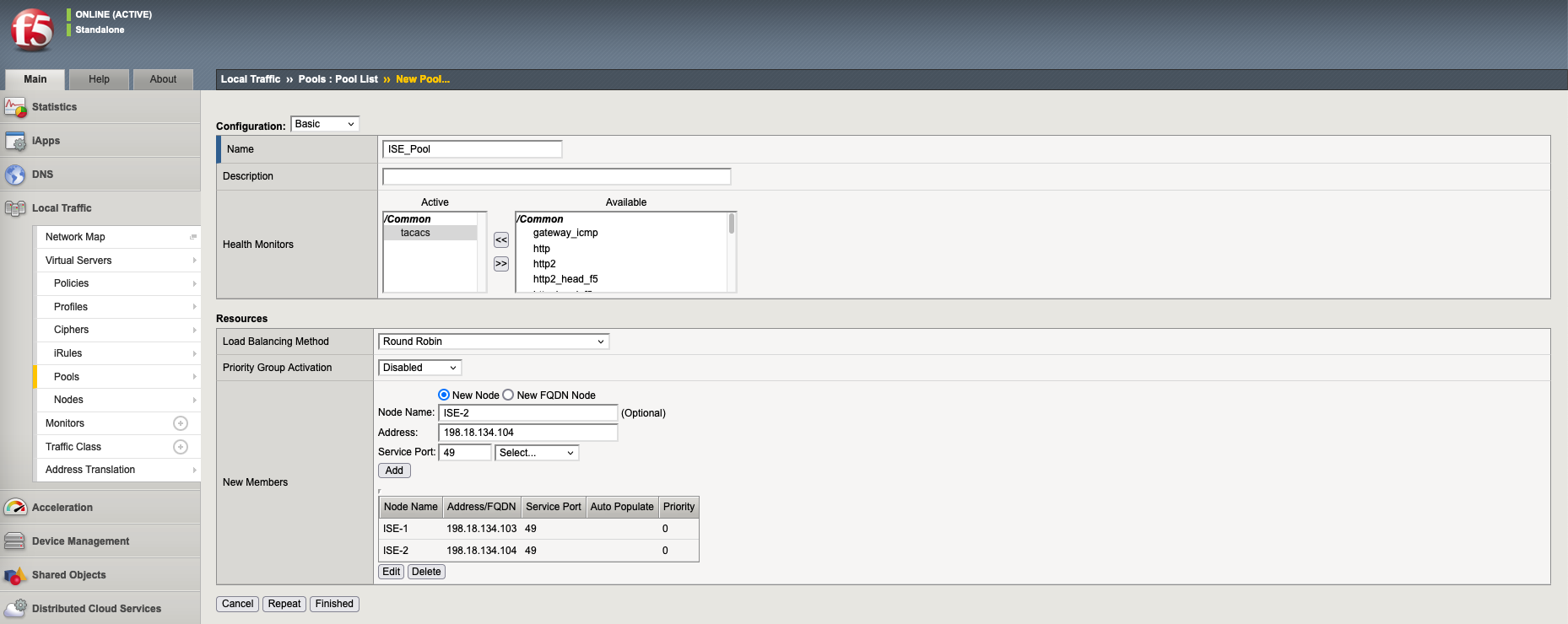
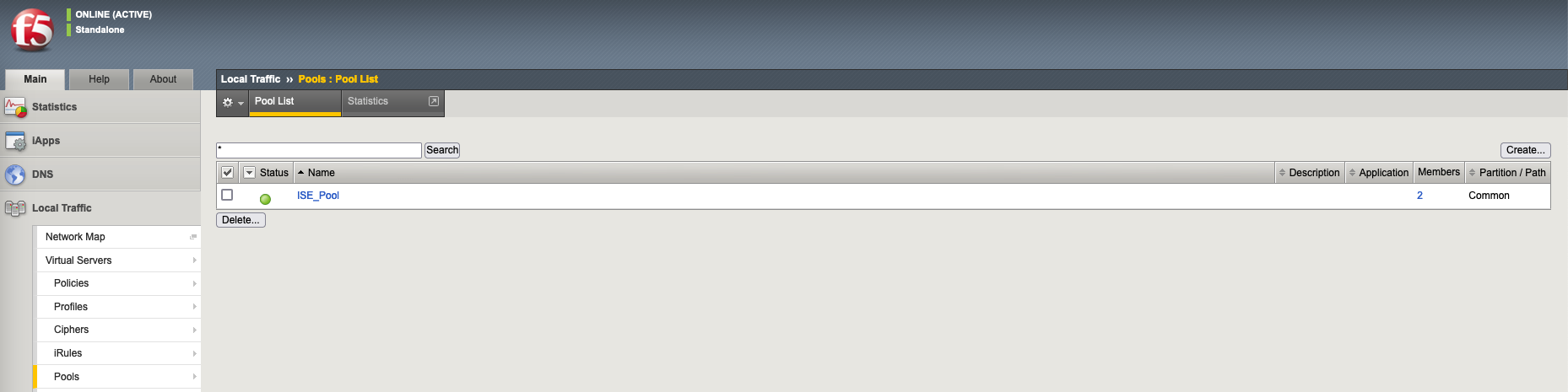
Next create a Pool containing the 2 ISE Servers with service port on port 49 and using the Health Monitor created
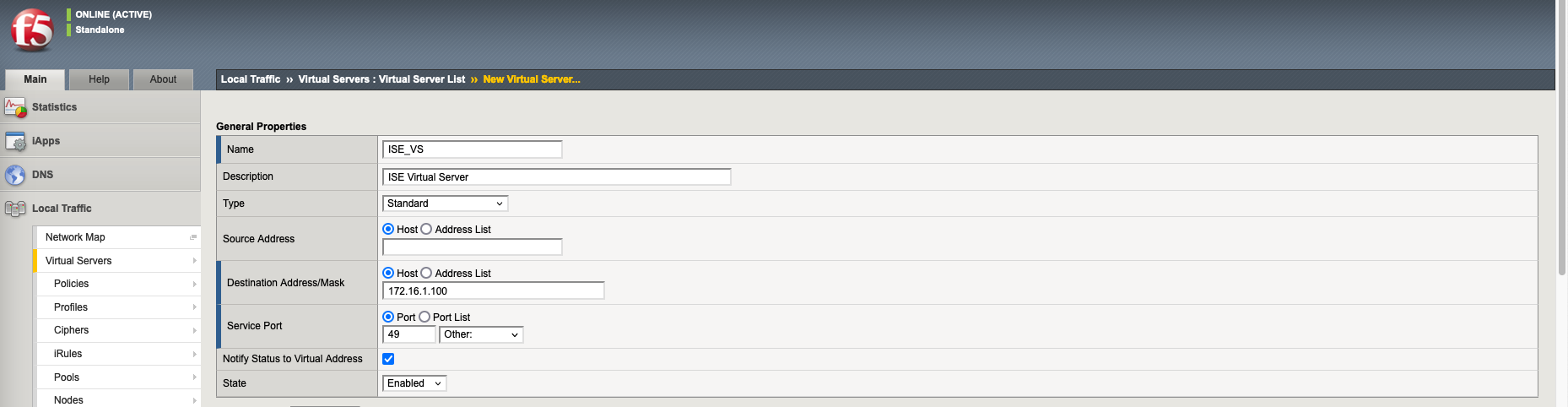
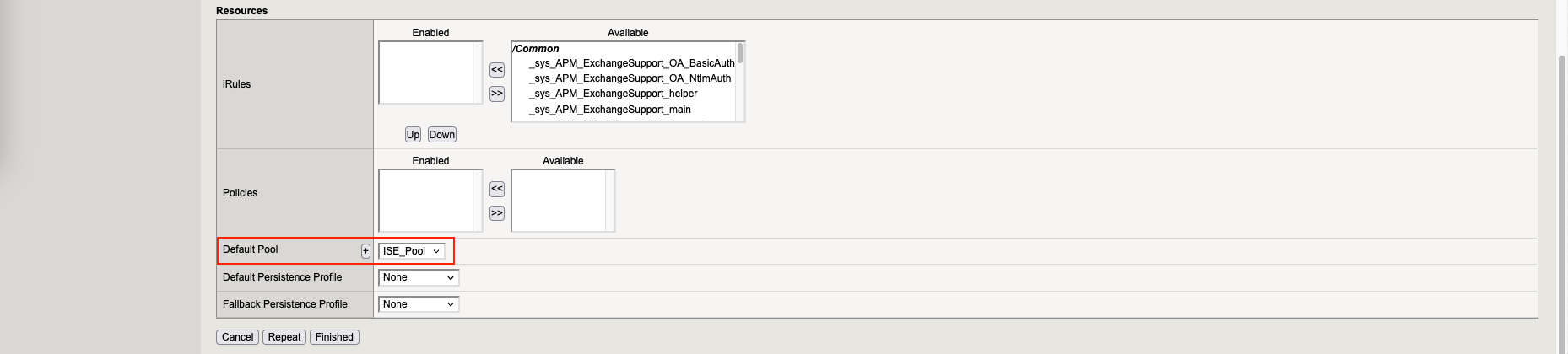
Then we create a new Virtual Server pointing to the Virtual IP with member being the ISE Pool
Testing Virtual Server
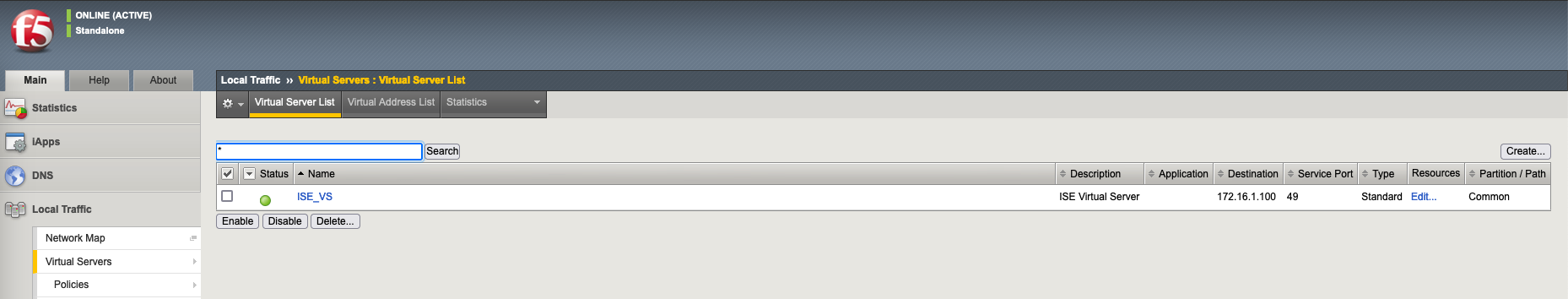
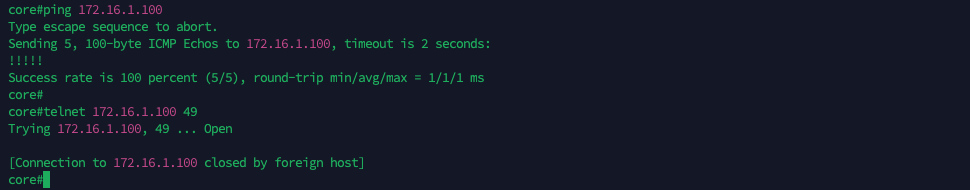
Now the Virtual IP should be accessible on port 49
Configure the tacacs on the NAD to point to the Virtual IP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
aaa new-model
tacacs server ISE_VS
address ipv4 172.16.1.100
key helena
aaa group server tacacs+ TACACS_SVR
server name ISE_VS
aaa authentication login default group TACACS_SVR local
aaa authentication enable default group TACACS_SVR enable
aaa accounting update newinfo
aaa accounting exec default start-stop group TACACS_SVR
aaa accounting commands 0 default start-stop group TACACS_SVR
aaa accounting commands 1 default start-stop group TACACS_SVR
aaa accounting commands 15 default start-stop group TACACS_SVR
aaa authorization config-commands
aaa authorization exec default group TACACS_SVR local if-authenticated
aaa authorization commands 0 default group TACACS_SVR local if-authenticated
aaa authorization commands 1 default group TACACS_SVR local if-authenticated
aaa authorization commands 15 default group TACACS_SVR local if-authenticated
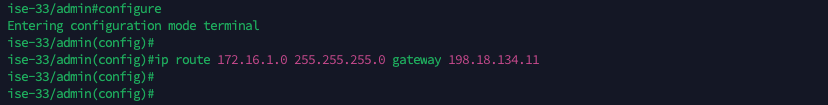
On both ISE Servers, because the default gateway is not pointing to the F5, we need to engineer the traffic coming from NAD though F5 to be returned back to F5 with static routes
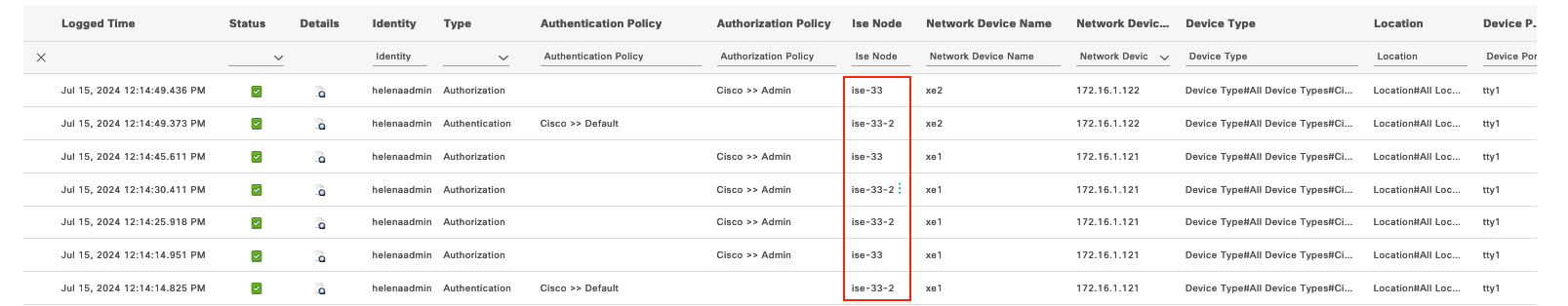
Now if we try to authenticate to the NAD, F5 will load balance the request to both ISE Servers
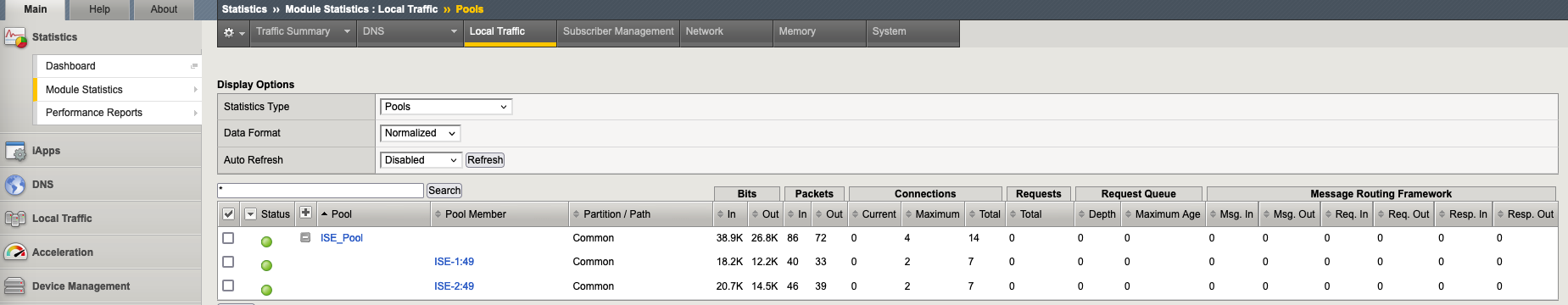
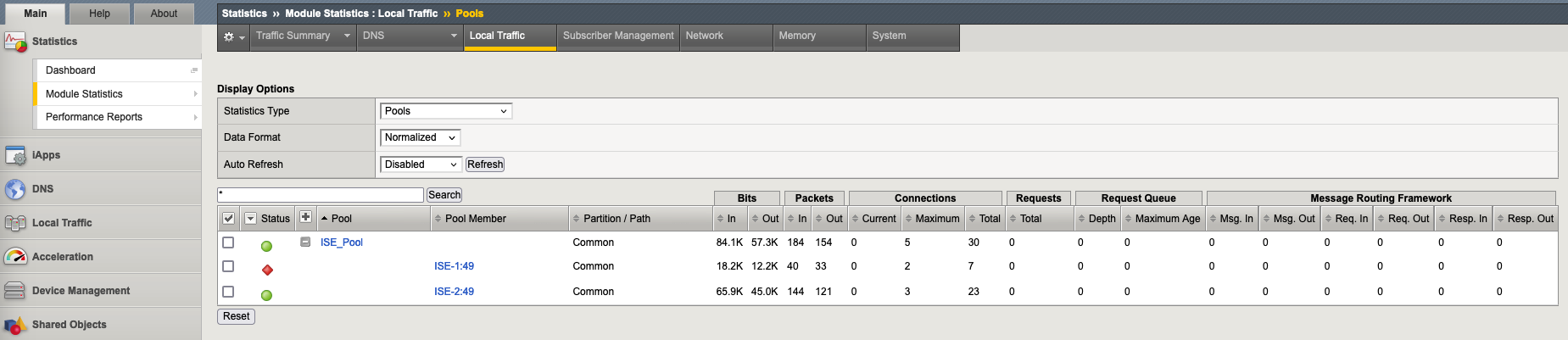
The status of both ISE server can also be monitored on F5
Shutting Down ISE Service
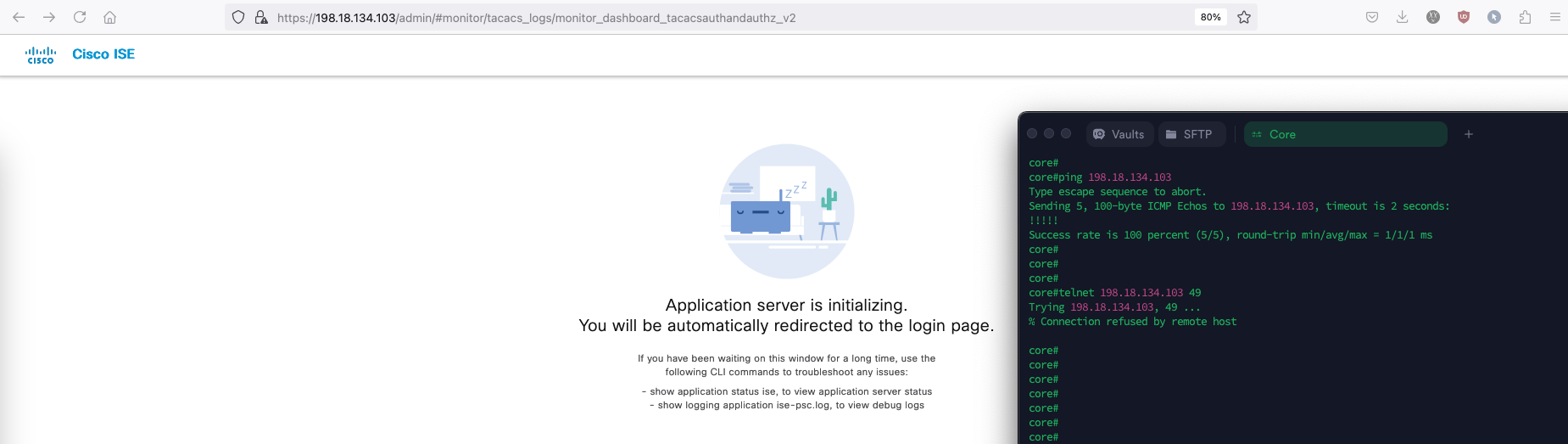
If we shutdown the ISE service, this will make the First Node to be inaccessible on port 49 but is still ping-able
On F5 monitor we can see that the node is detected down
And for that, F5 will forward the traffic to only the second node