Cisco ISE Guest Portal
Cisco ISE (Identity Services Engine) Guest Portal is a feature that provides secure network access for guest users through customizable web portals. It helps organizations manage guest authentication, user onboarding, and access policies.
- Hotspot Portal
Quick access for guests without formal registration.
Often used in public spaces for easy, one-click network access.- Registered Portal
Offers more control and tracking as guests provide details before accessing the network.
Optionally allows guests to create their own accounts with minimal input.
Hotspot Guest Portal
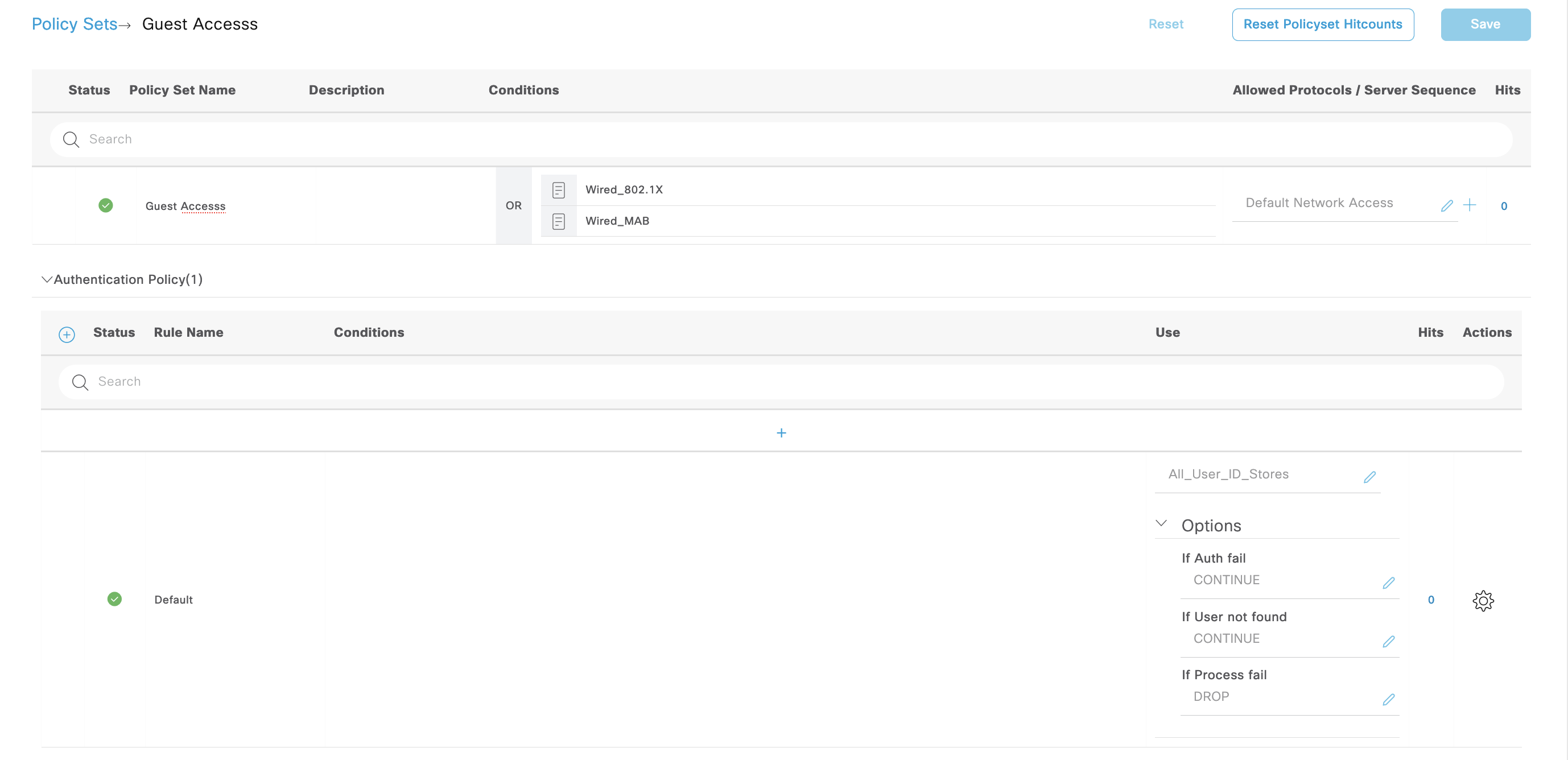
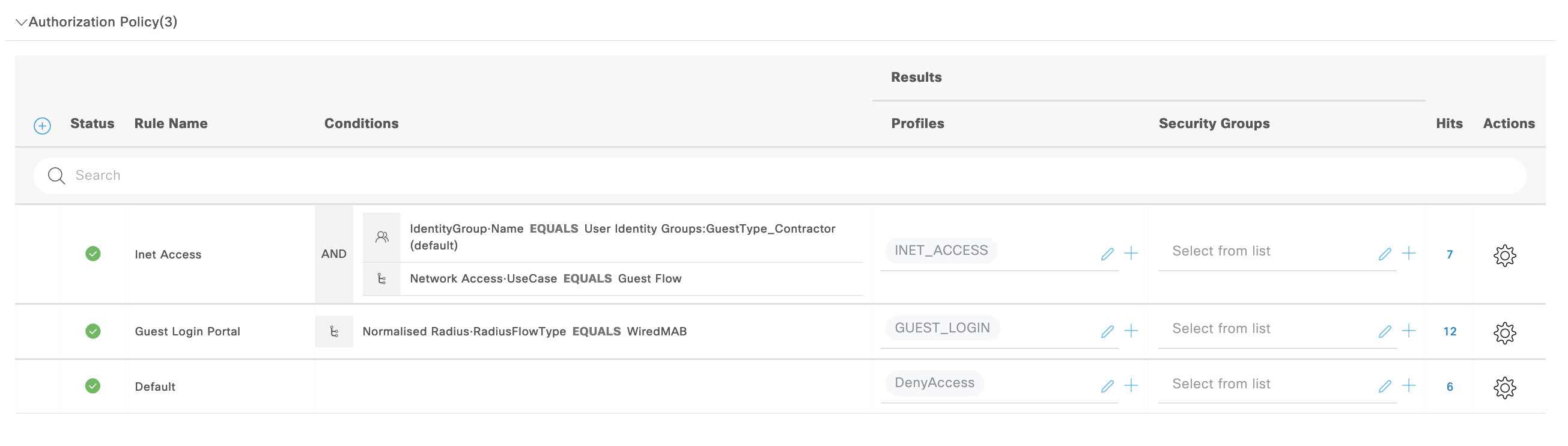
To configure a hotspot guest portal, first lets create new Policy Sets where any failure of authentication results in continuing to authorization
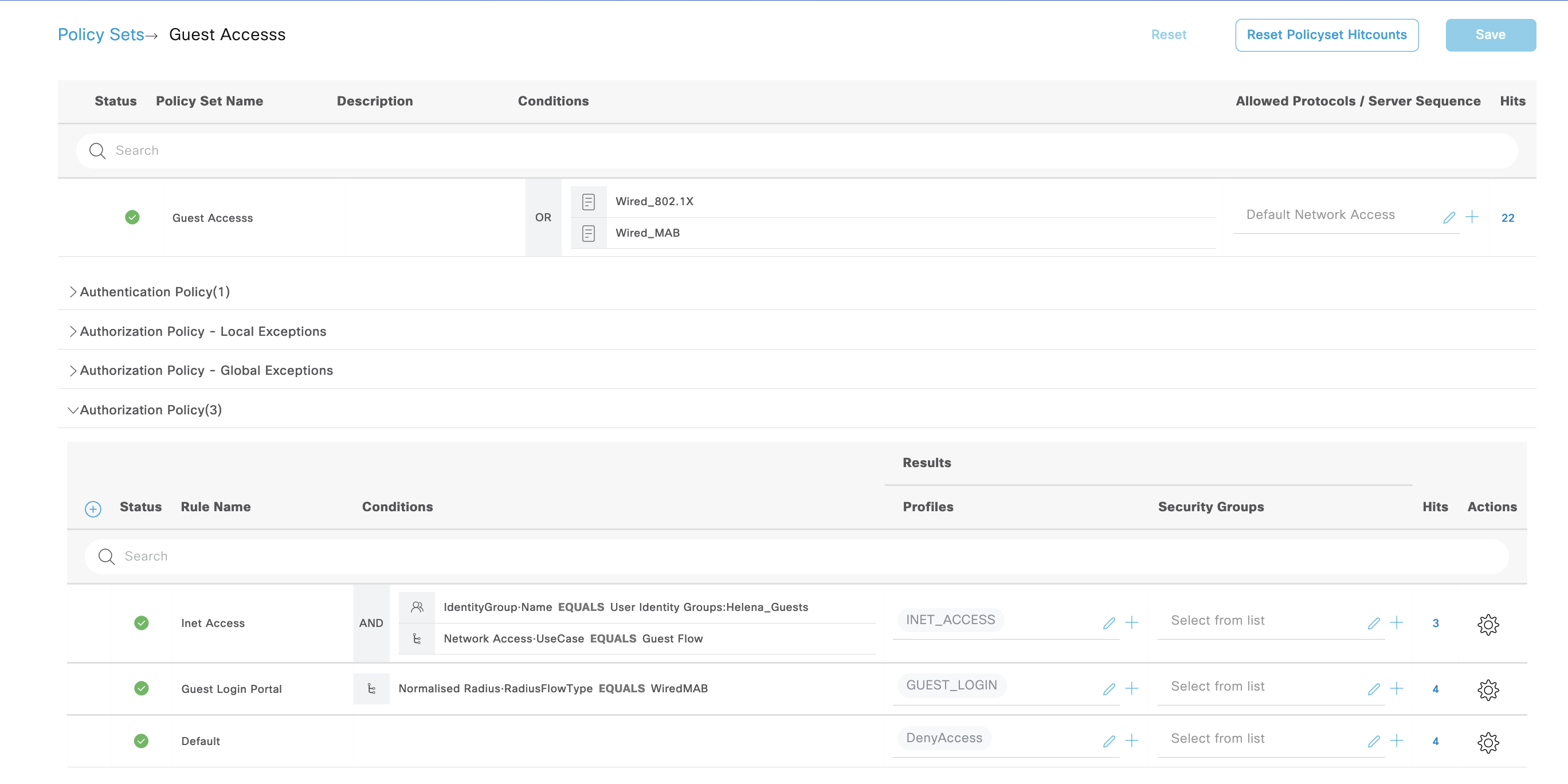
Next create two authz rules, one is for portal redirect and the other is for internet access after the guest has gone through the portal
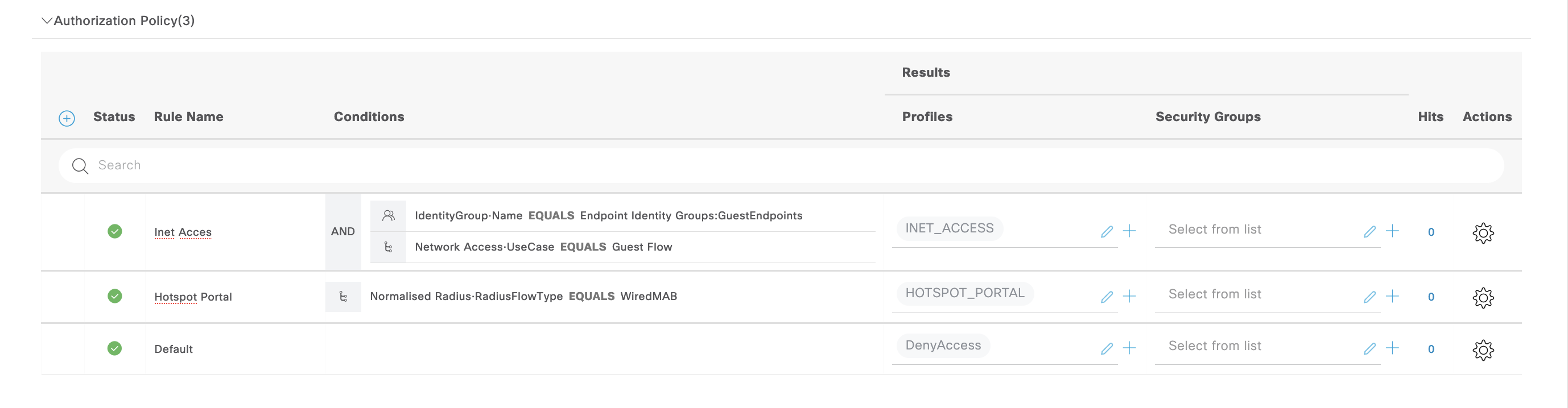
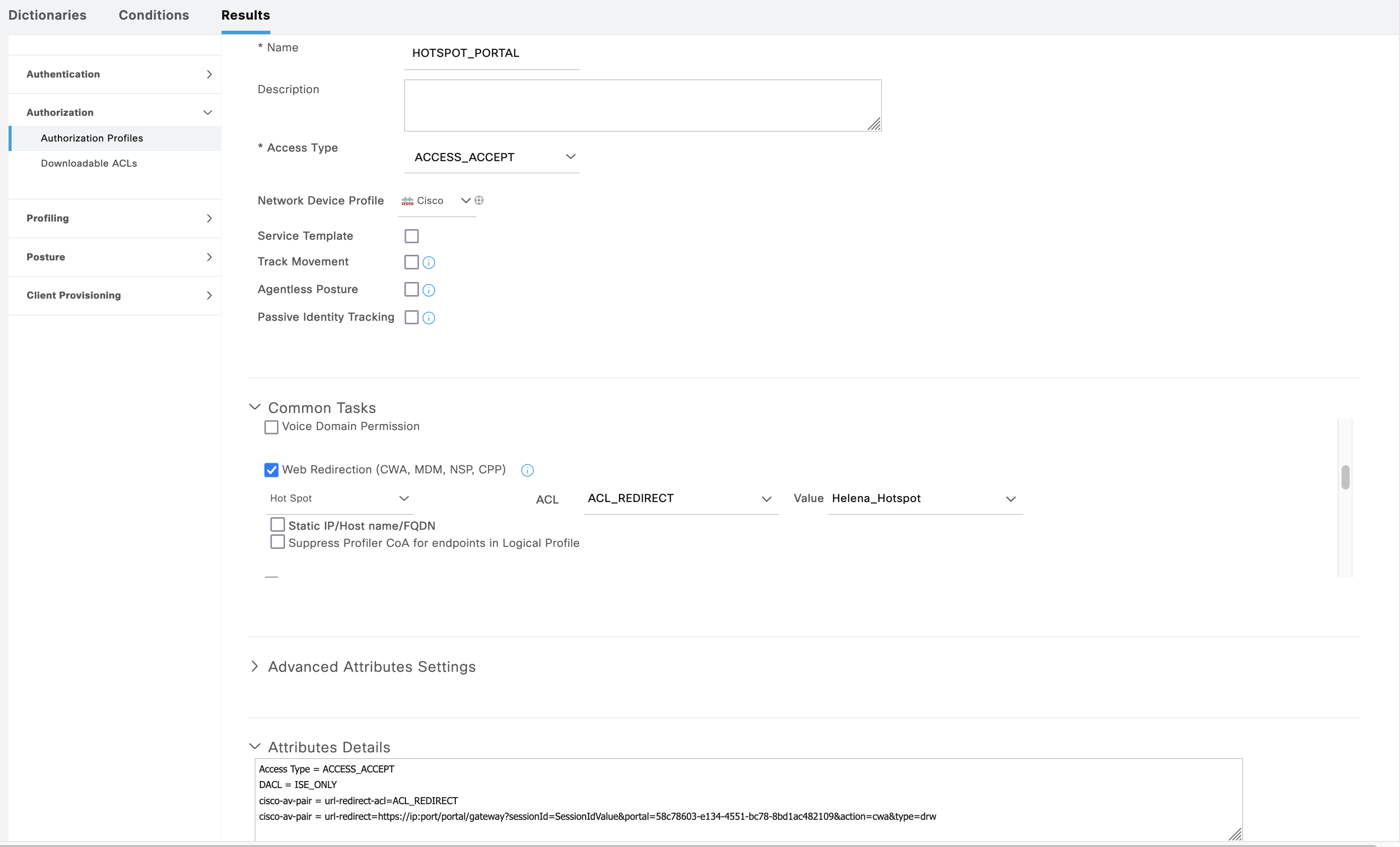
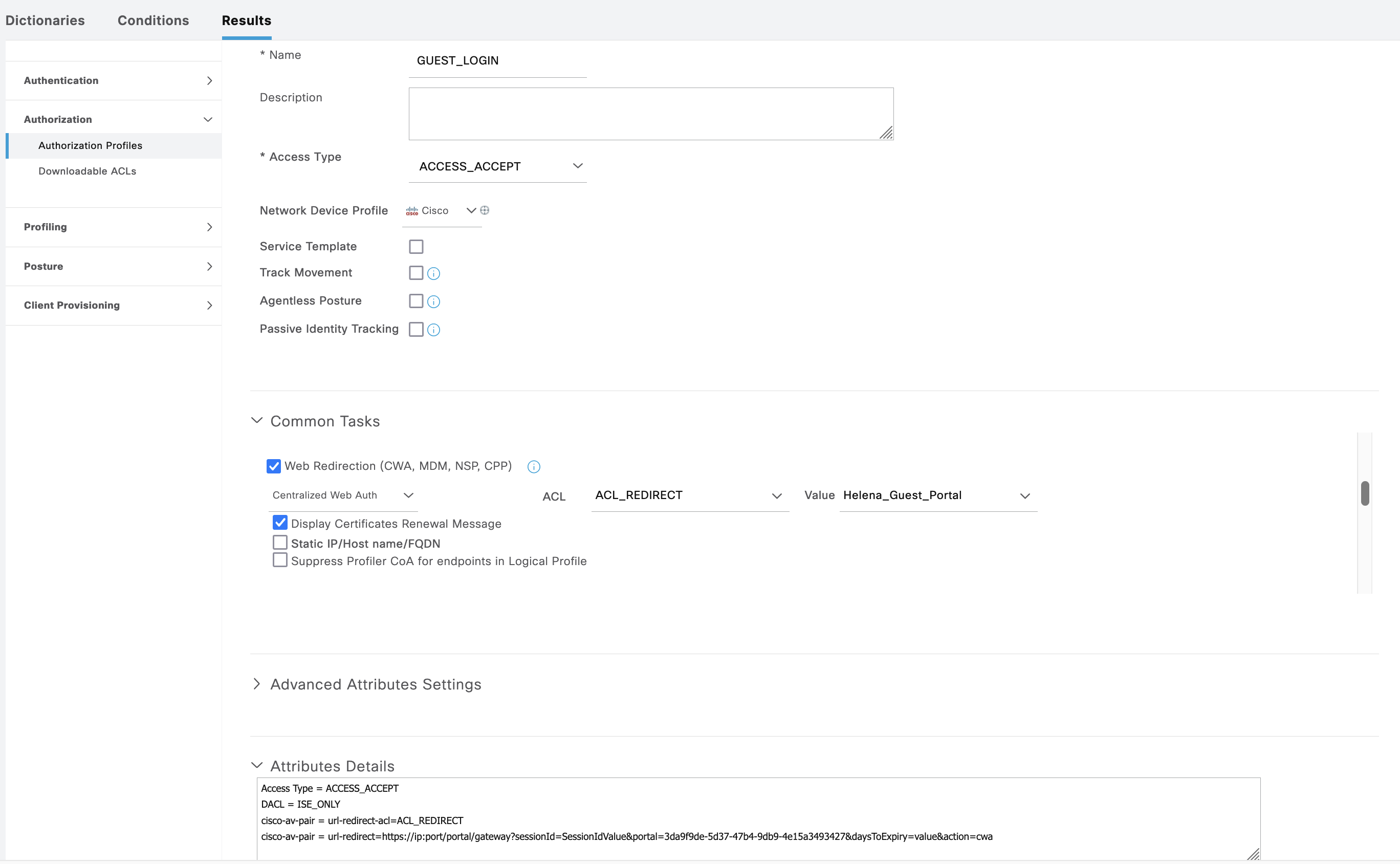
The “Hotspot Portal” AuthZ rule points to “HOTSPOT_PORTAL” Profile, which here contains a DACL to only allow ISE access and a Web Redirection to redirect users to the Hotspot Portal
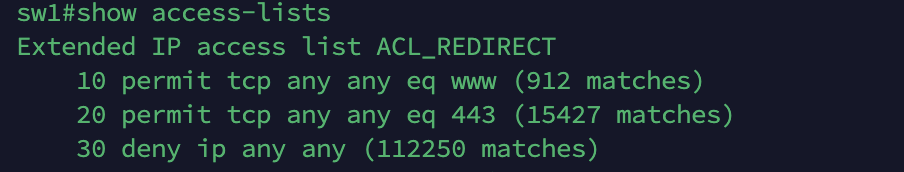
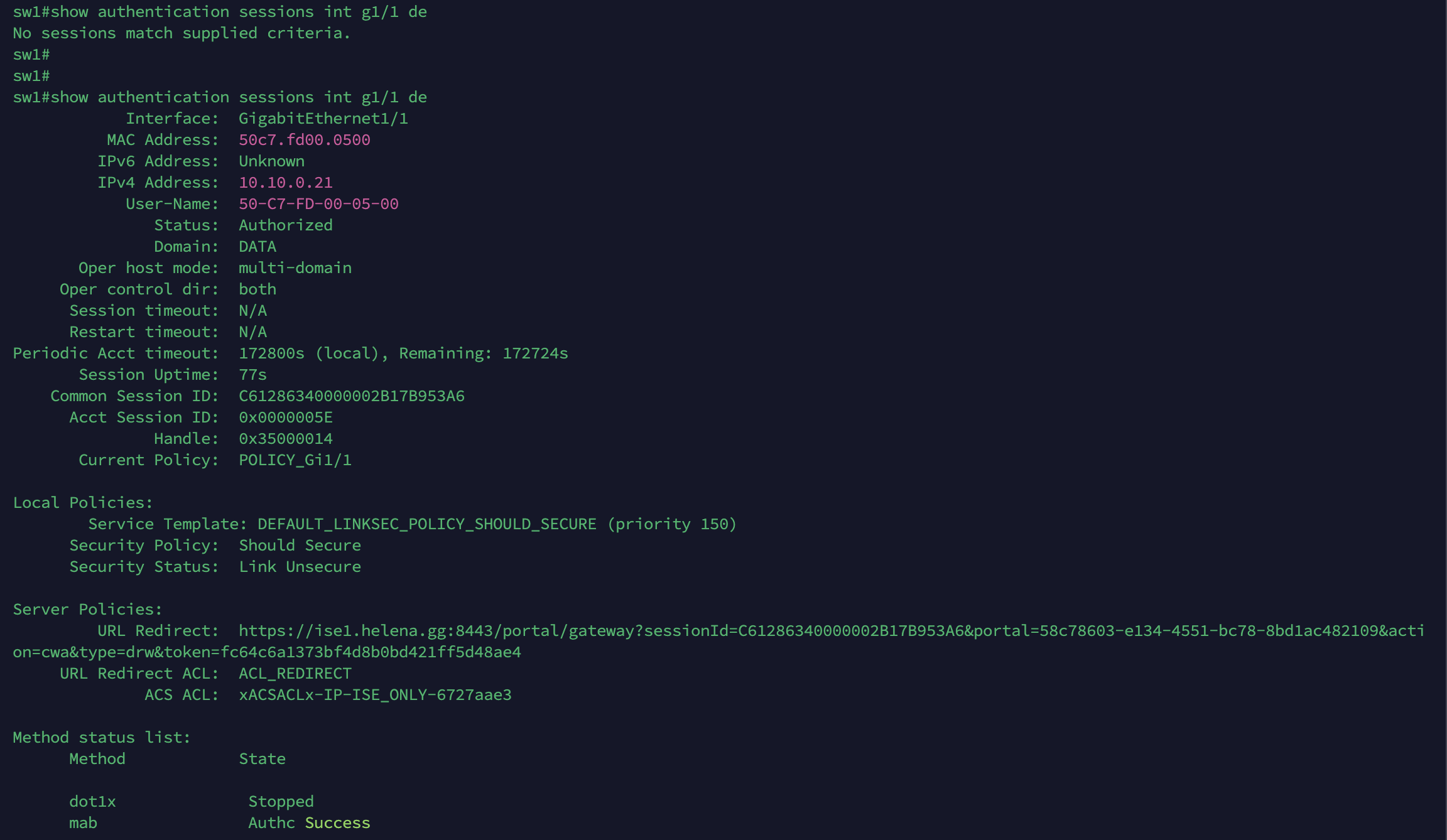
The redirection task uses an ACL named “ACL_REDIRECT”, this has to be present on the NAD, unlike the DACL that will be pushed independently
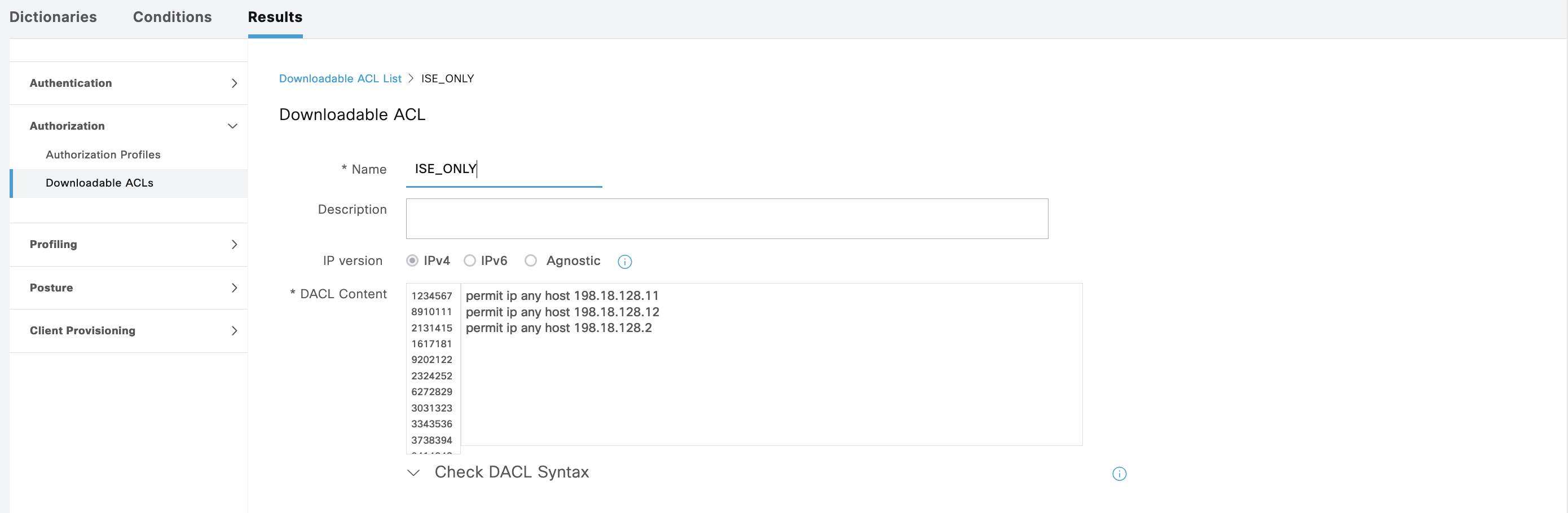
We also configure a “ISE_ONLY” DACL to limit user’s access to only ISE Servers and some neccessary servers, like DNS
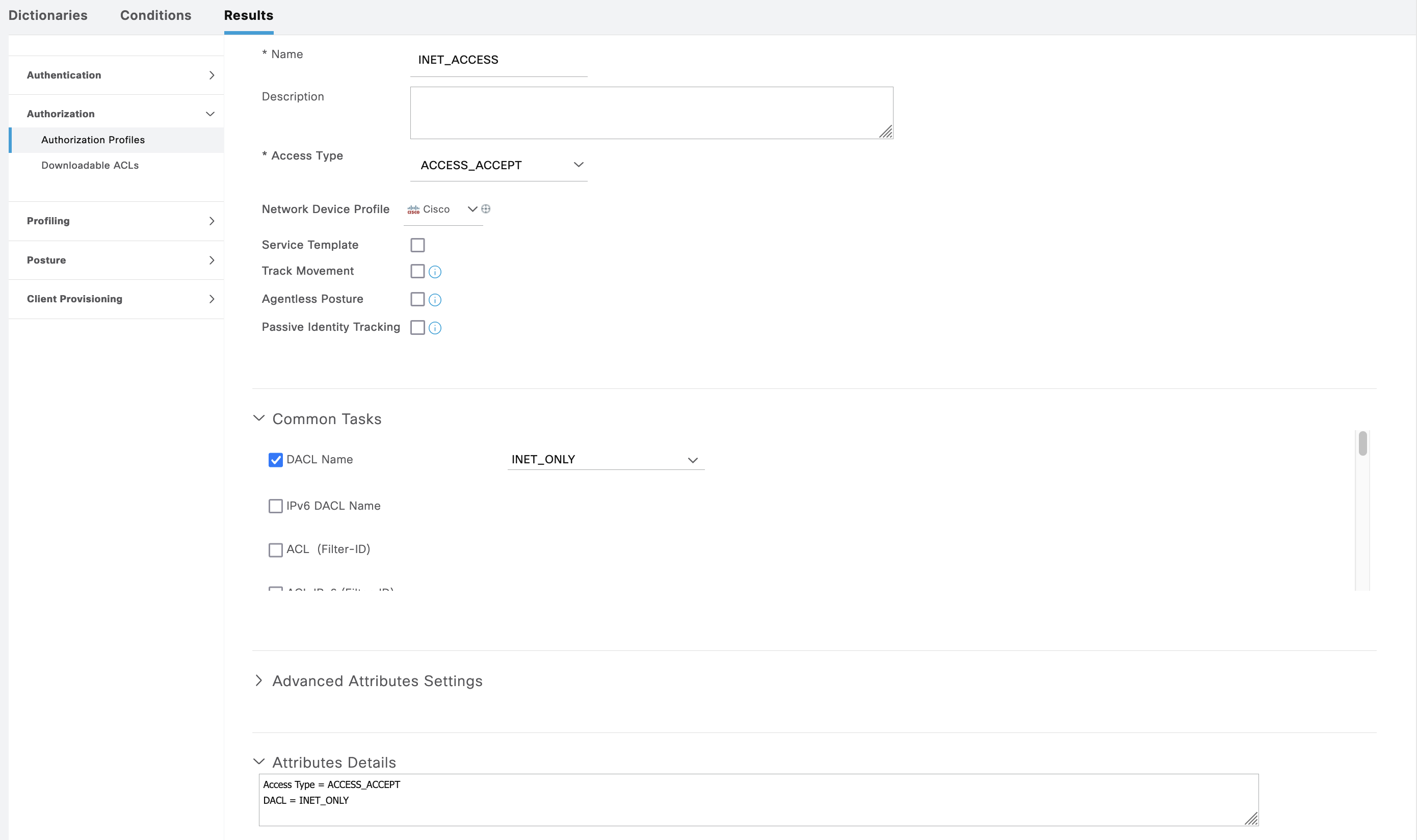
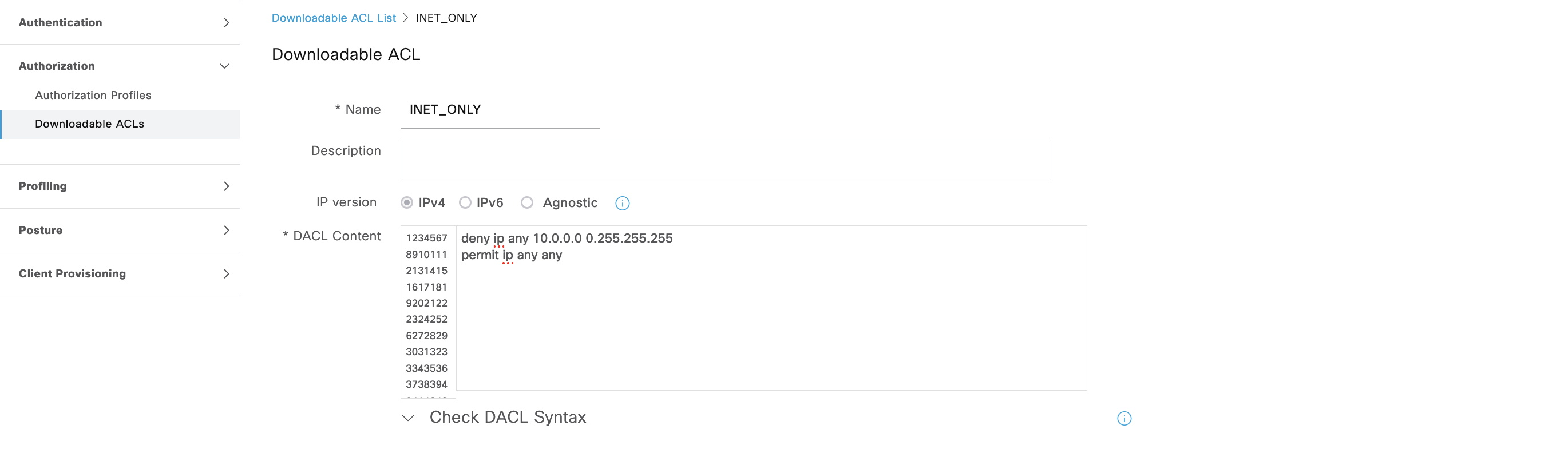
Next the other “Inet Access” AuthZ Rule points to “INET_ACCESS” Profile. This profile only contains a DACL to allow internet access
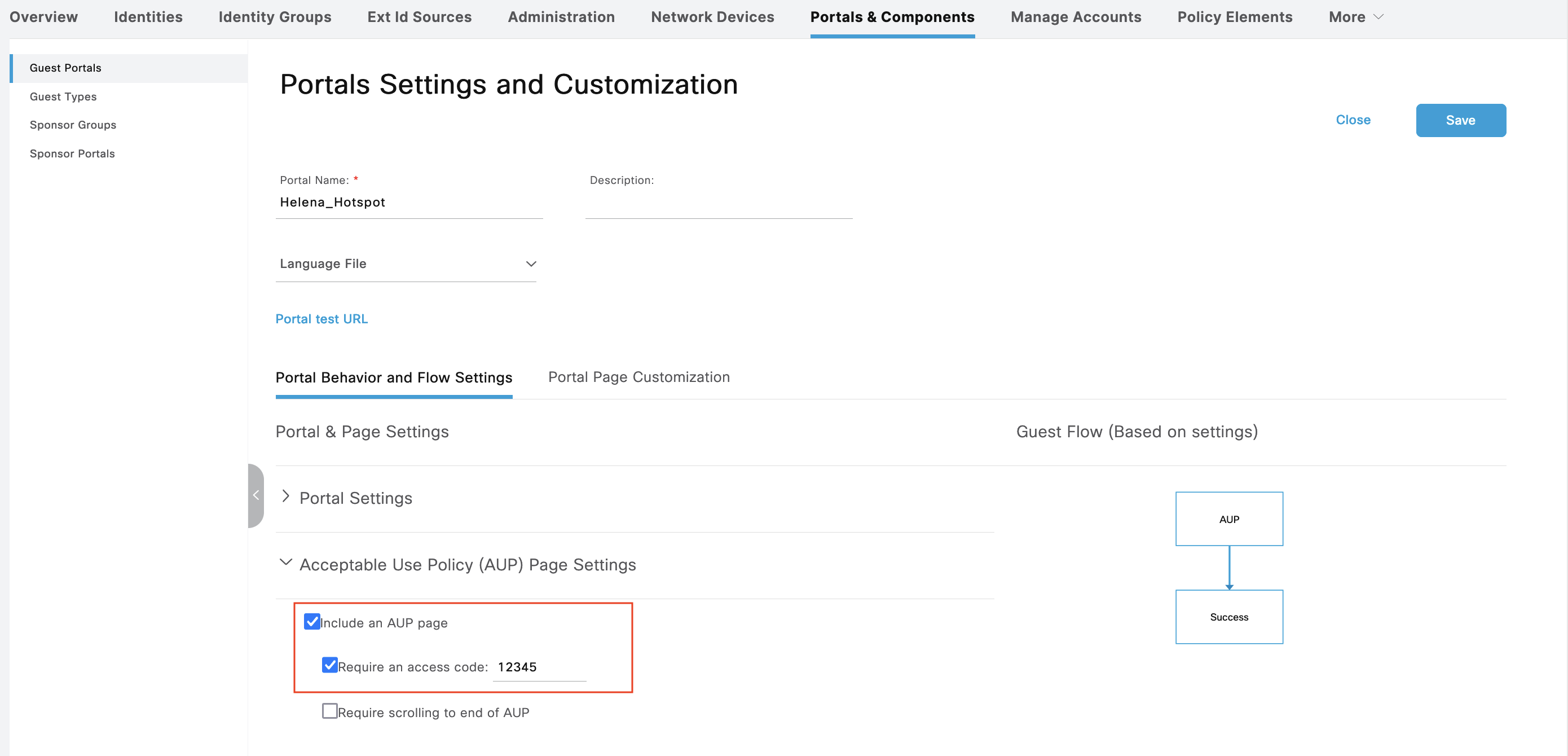
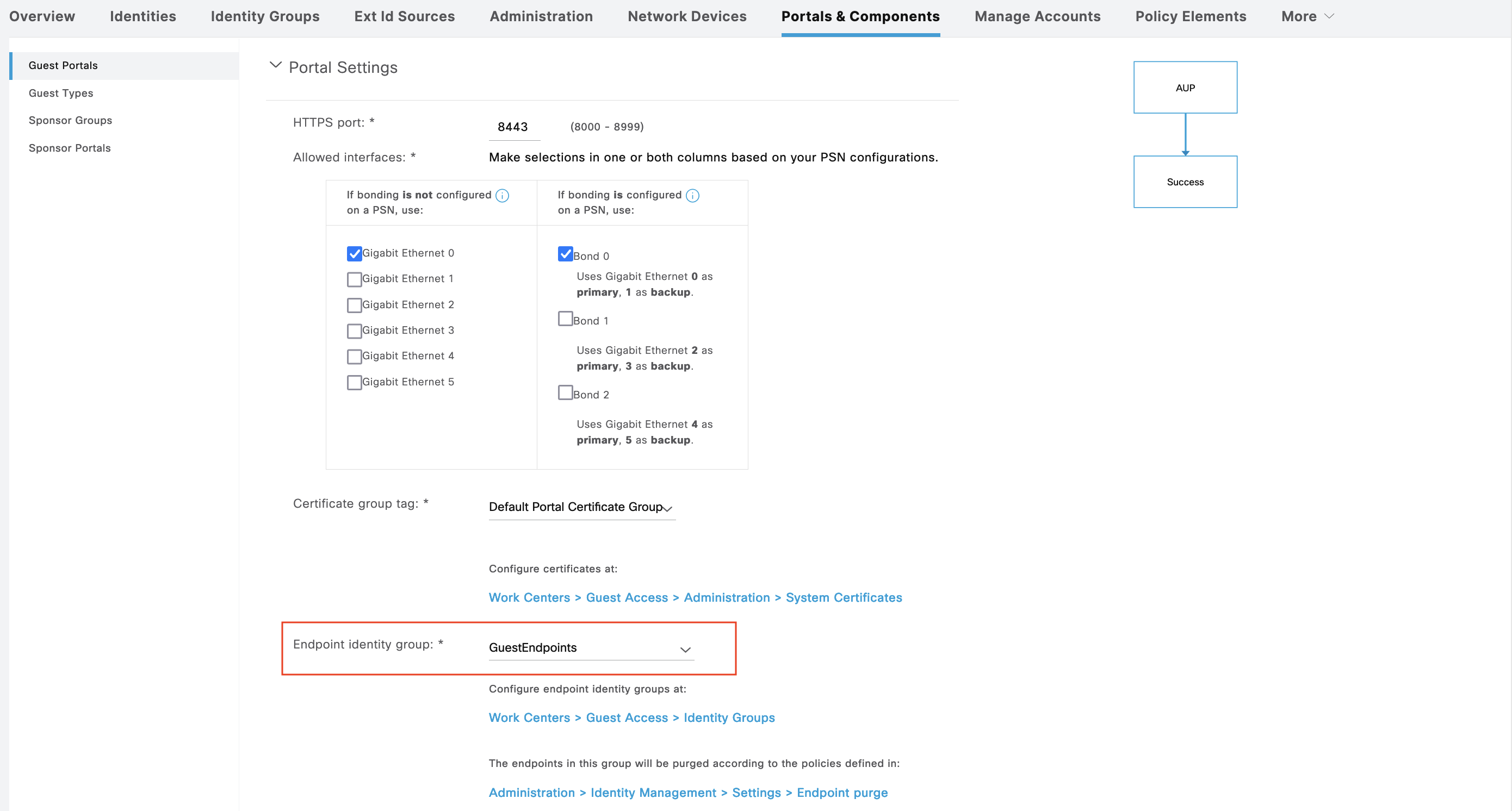
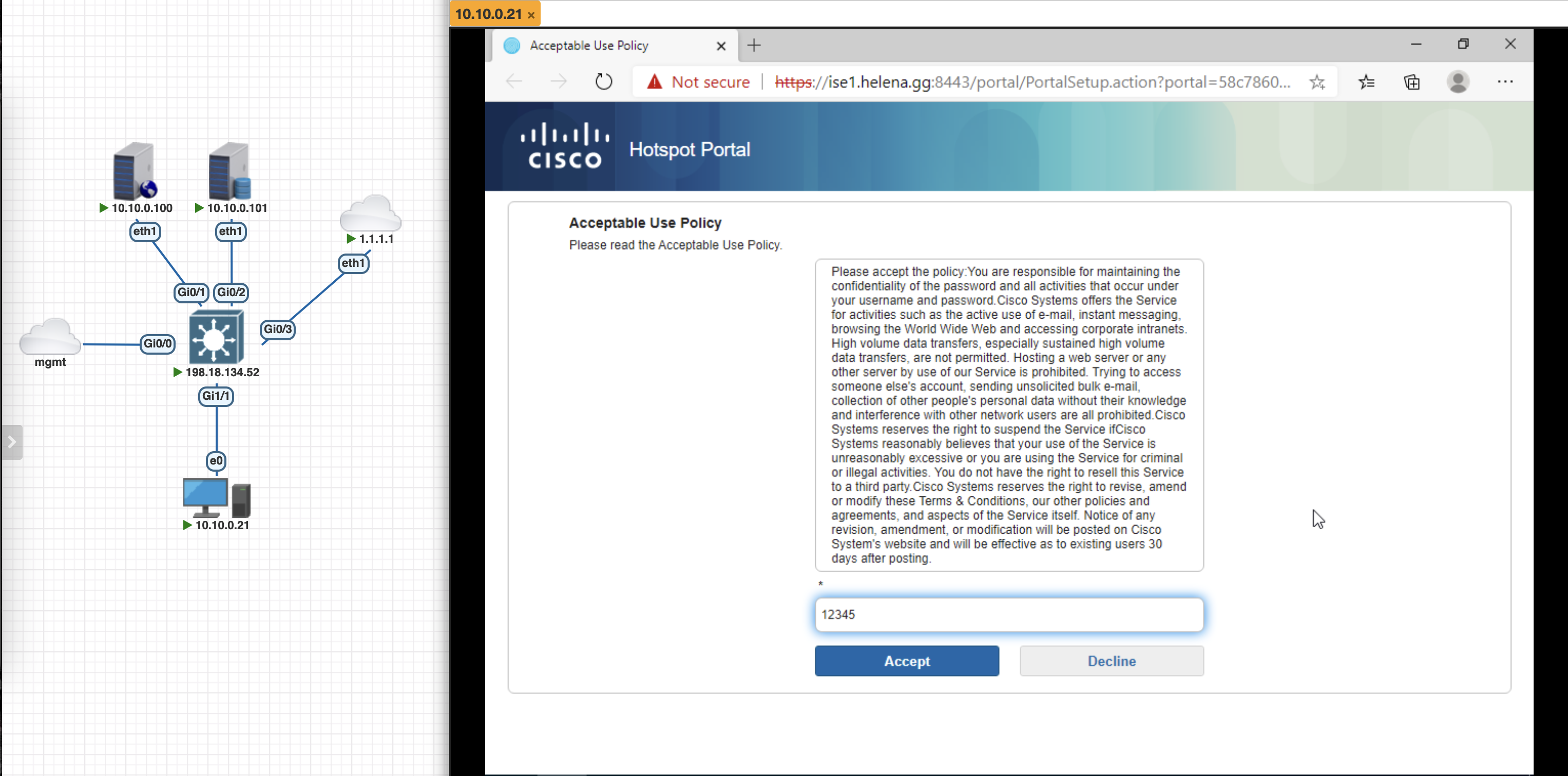
After that, we configure the Hotspot Portal, here we set a Code of “12345” for the internet access
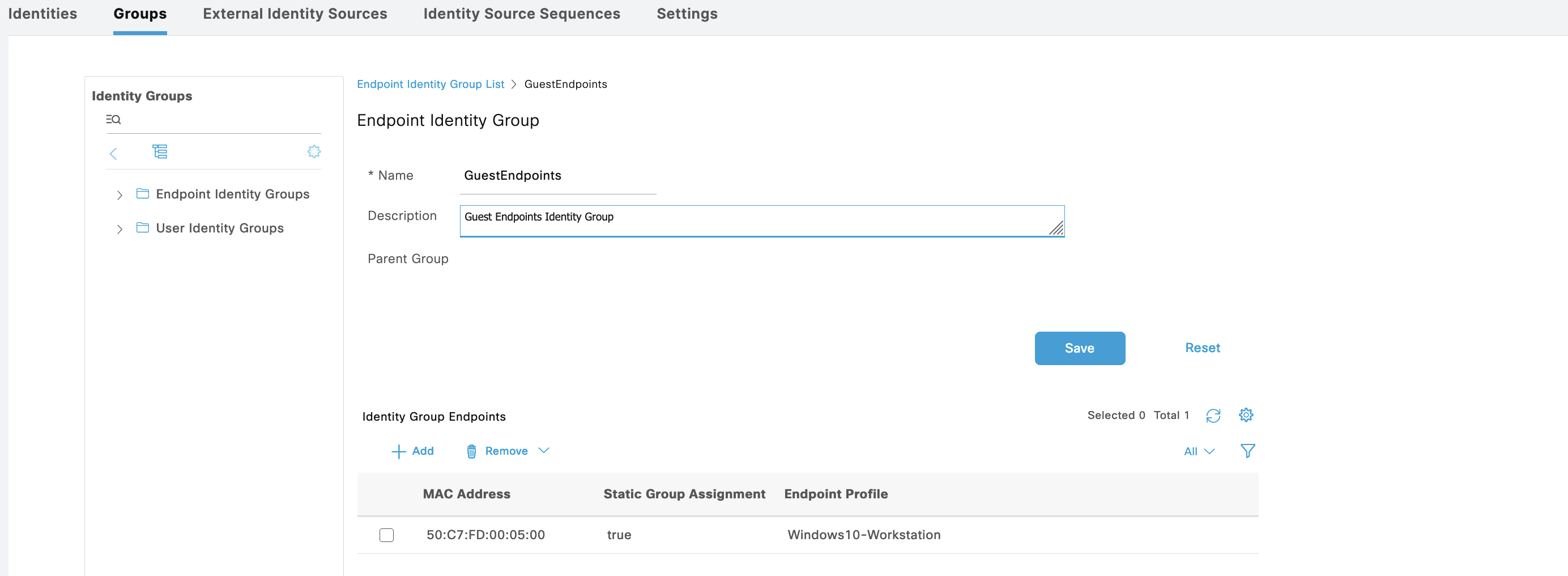
Then we also configure for any endpoint that has gone through the portal, add it to the “GuestEndpoints” Endpoint Identity Group
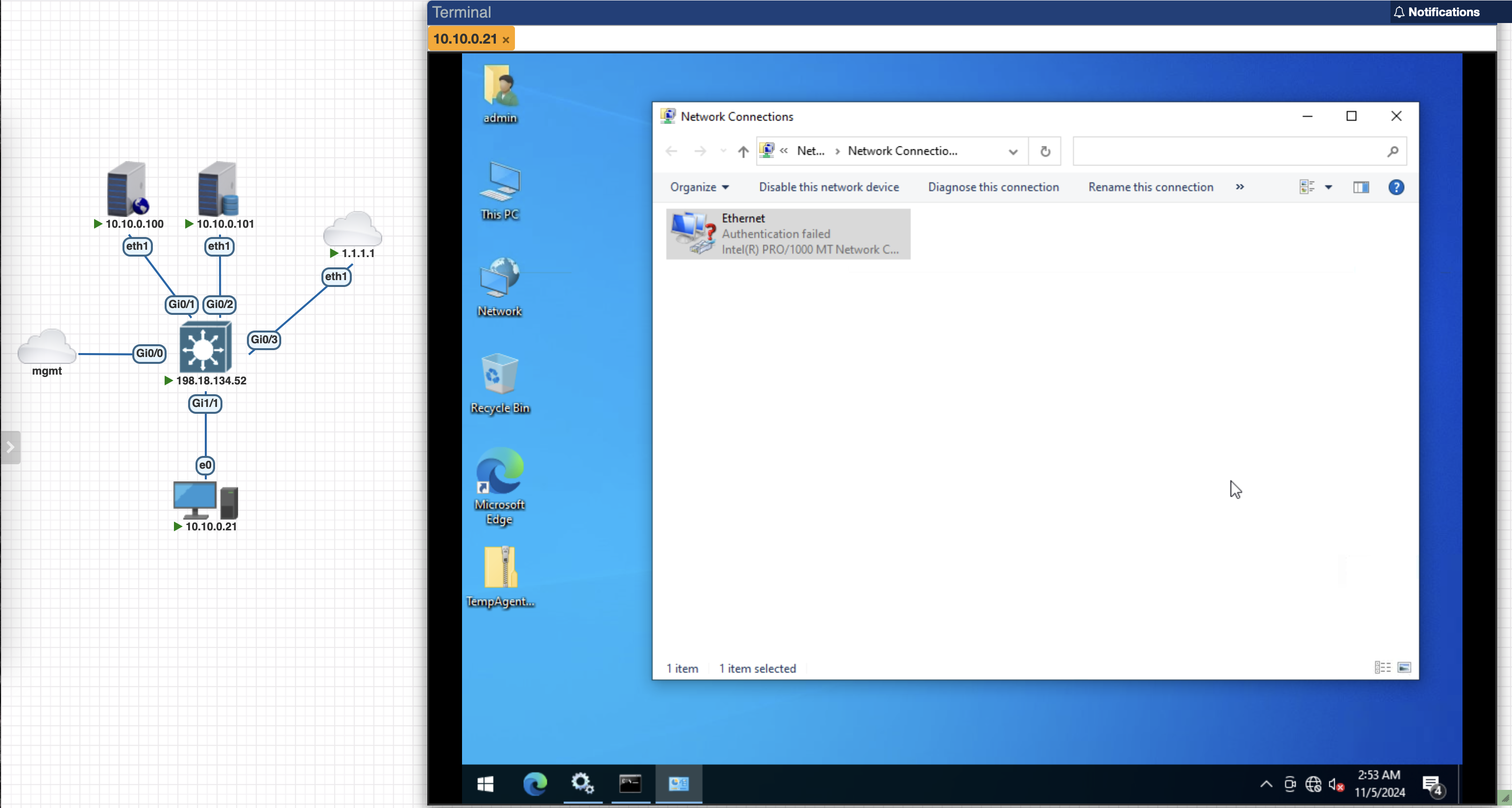
Now lets try accessing the network
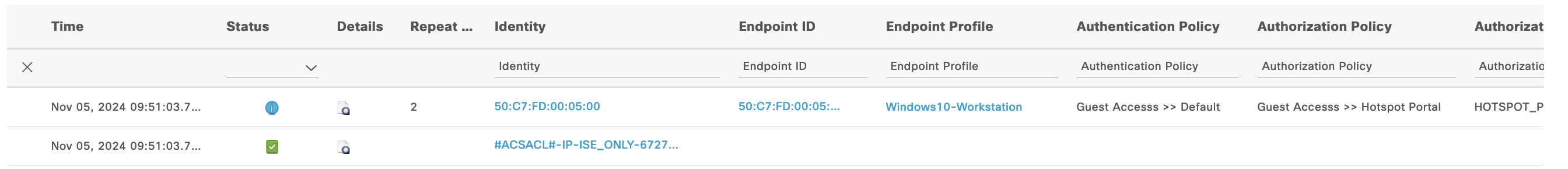
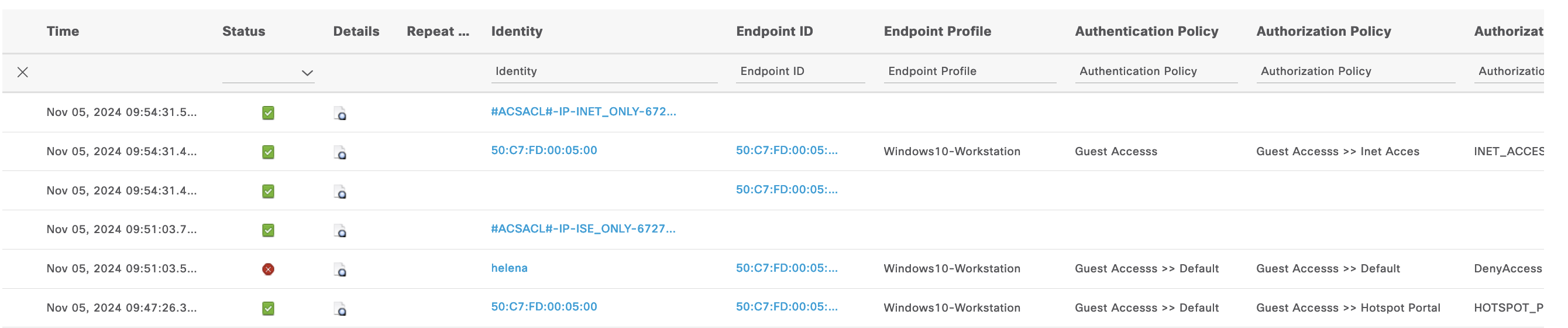
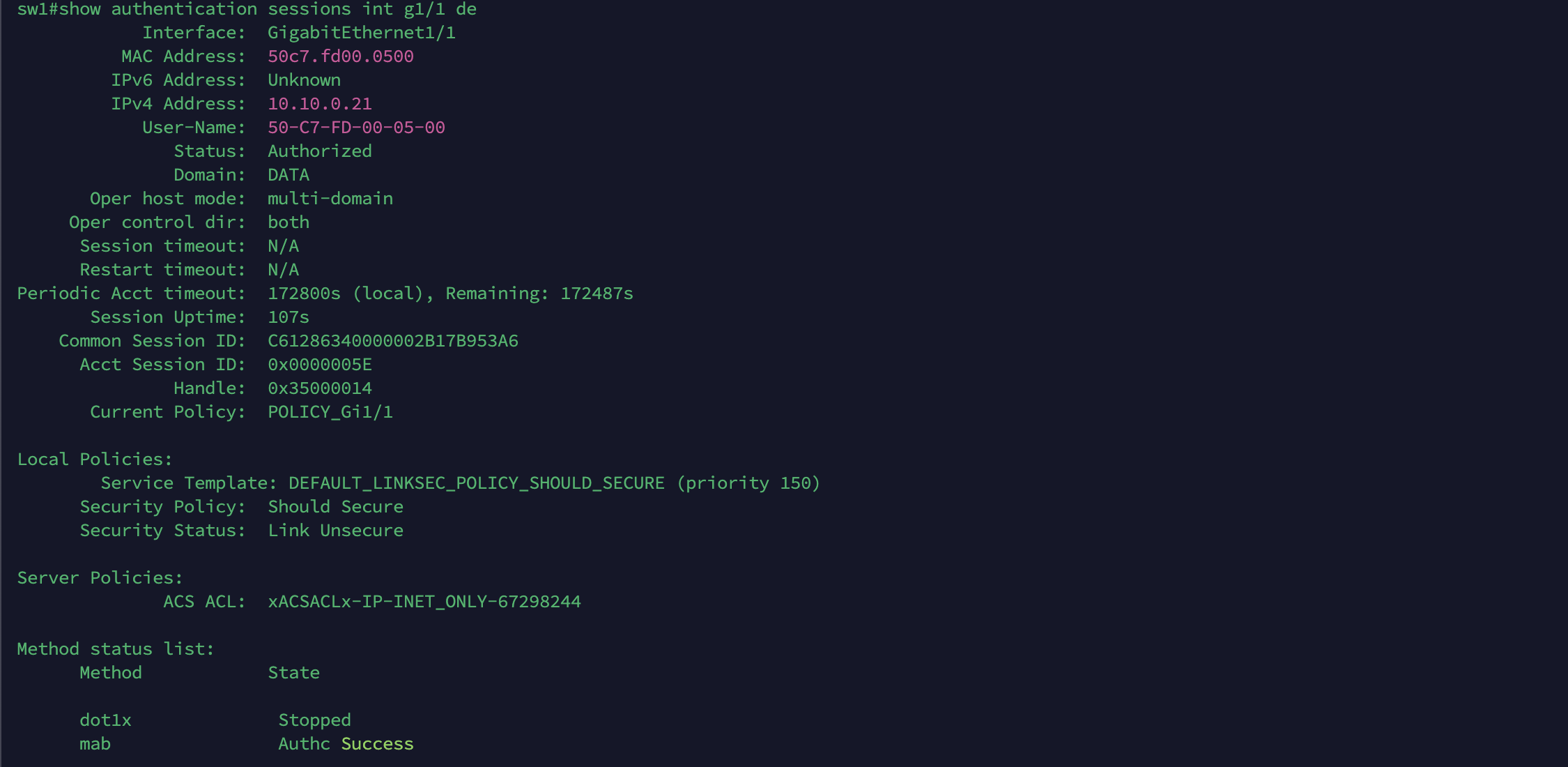
On the Live Radius Logs, we can see the endpoint is given the “Hotspot Portal” AuthZ rule with DACL “ISE_ONLY”
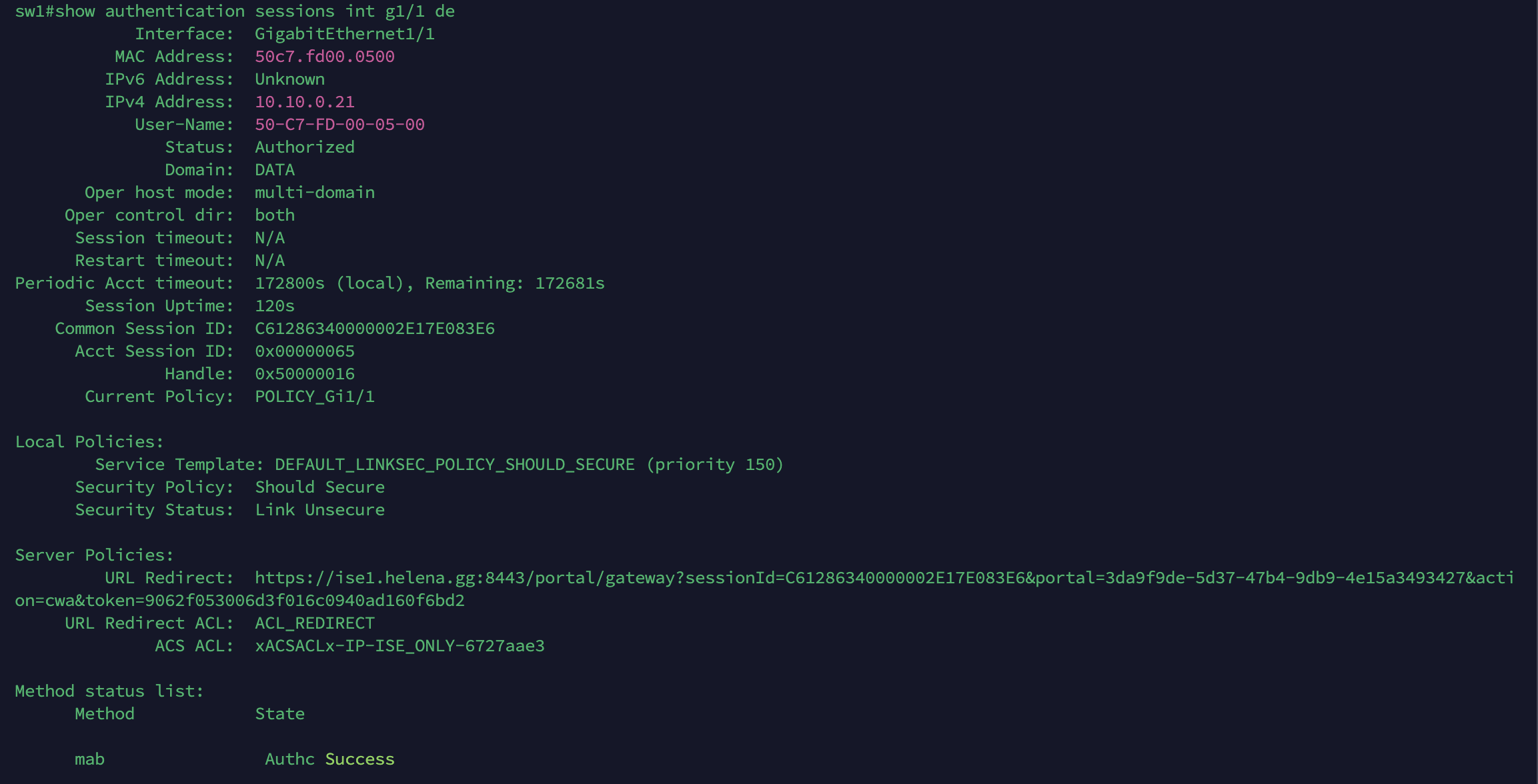
On the NAD, the same can be observed, including the redirection link to the portal
Back on the endpoint, we’re now redirected to the Hotspot Portal where we can enter the code for internet access
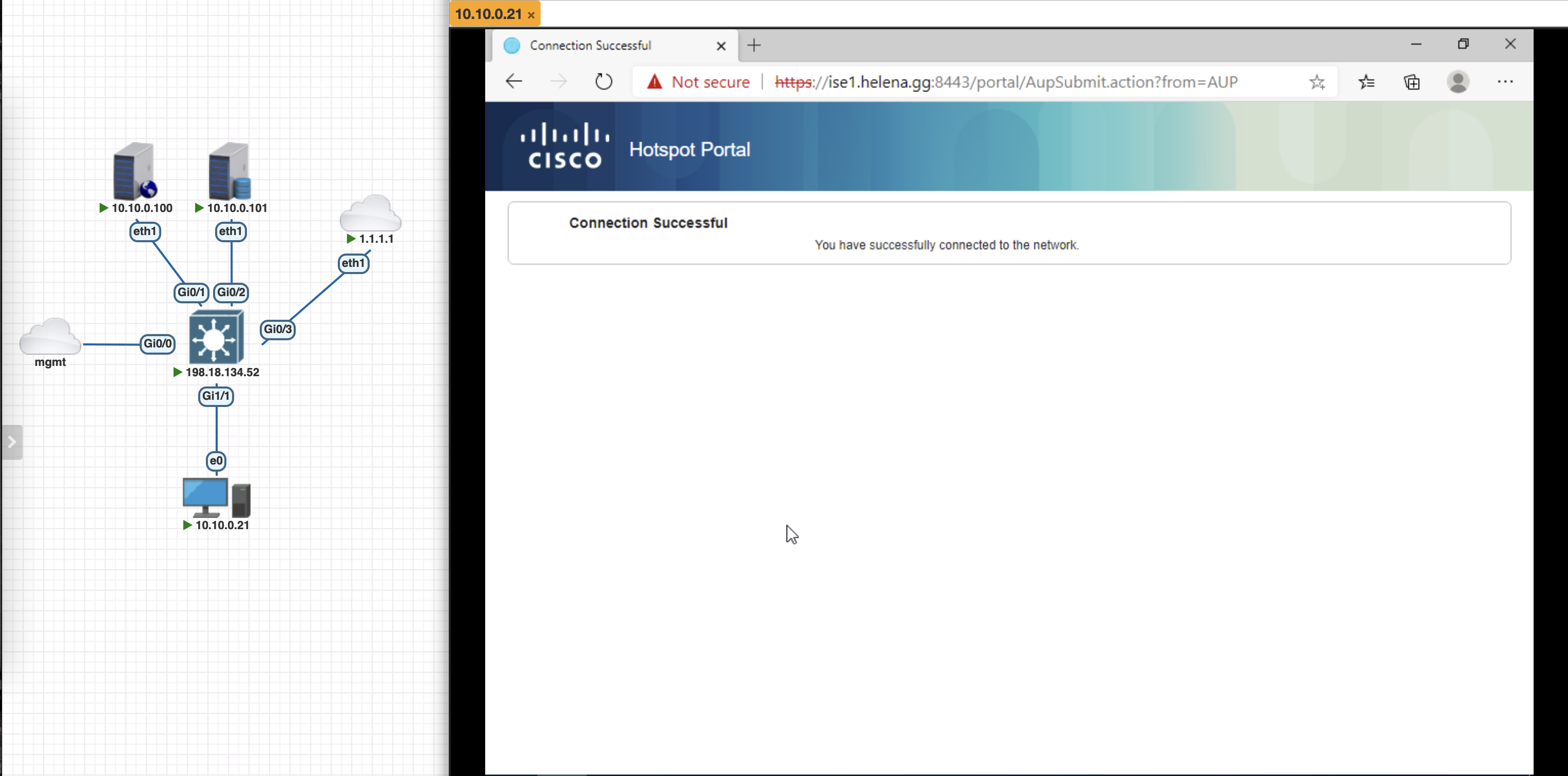
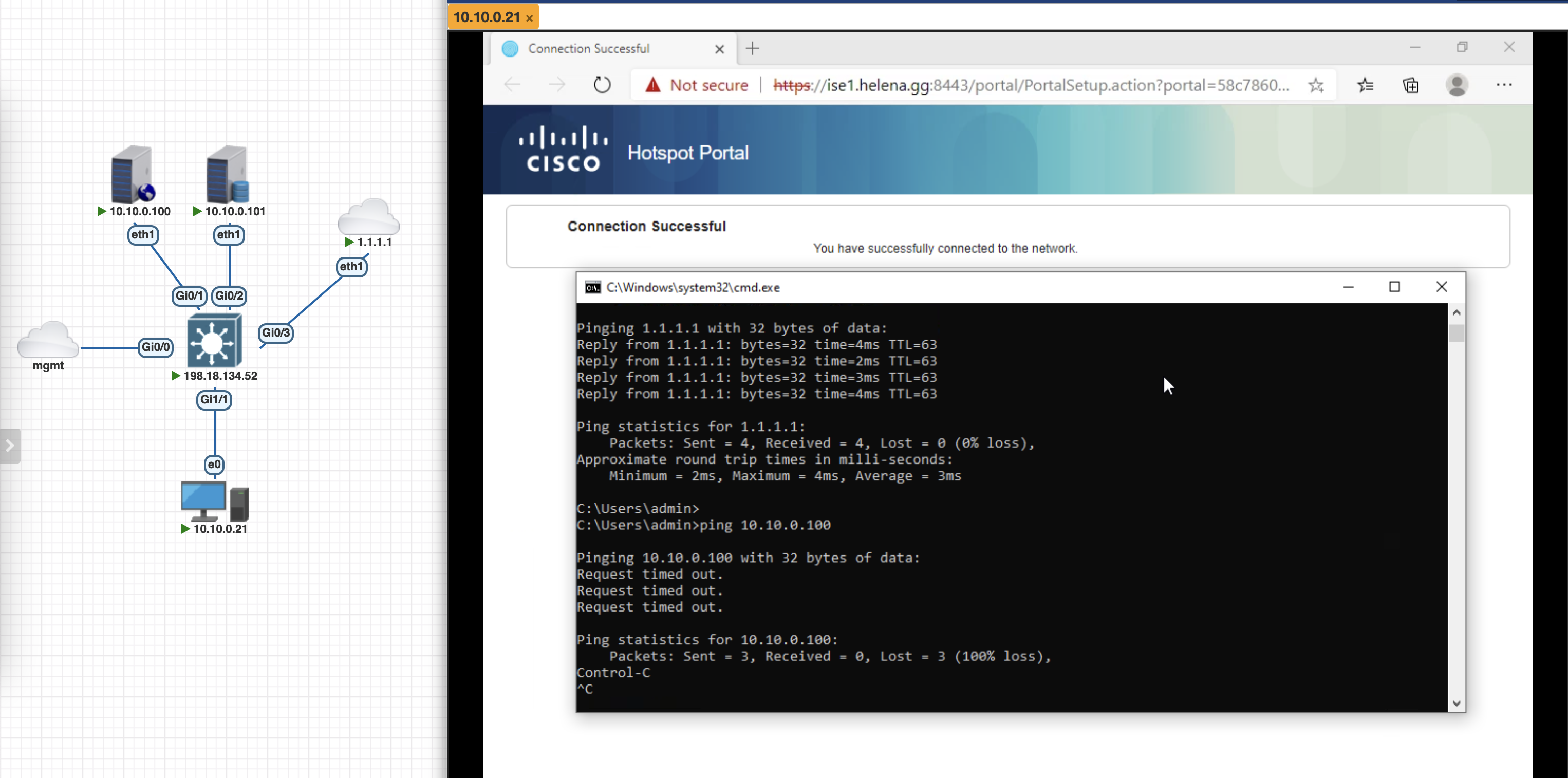
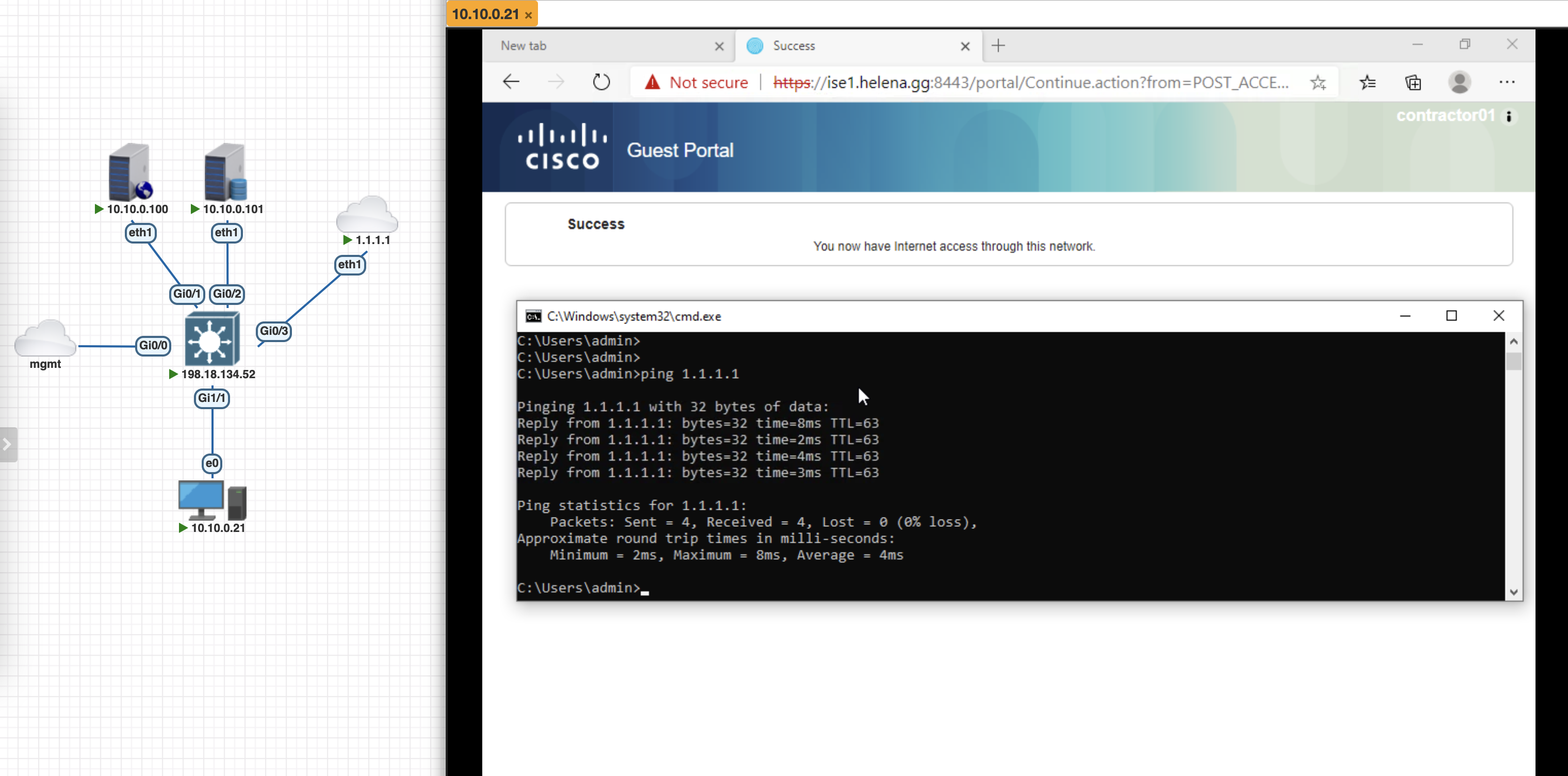
And after it was successful, we can now access the network
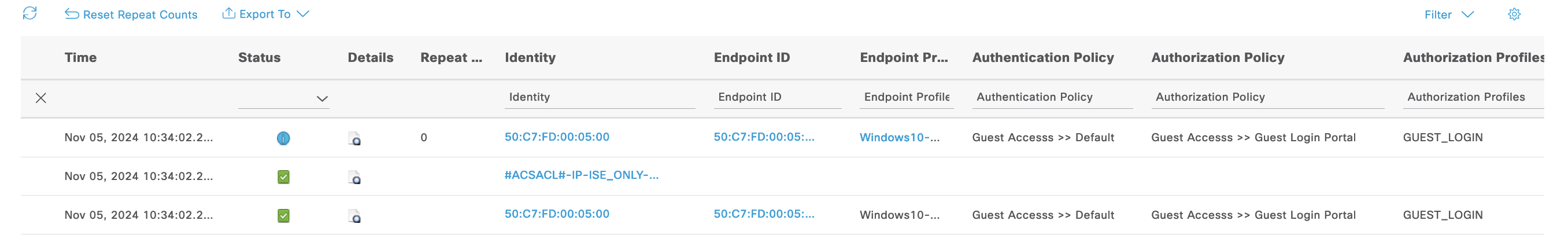
On the Live Logs, we see the CoA (Change of Authorization) is sent to change the AuthZ from “Hotspot Portal” to “Inet Access” aloing with its DACL
And the endpoint is now added to the “GuestEndpoints” group
On the NAD, we can see the “INET_ONLY” DACL is now pushed allowing endpoint to access internet
Registered Portal
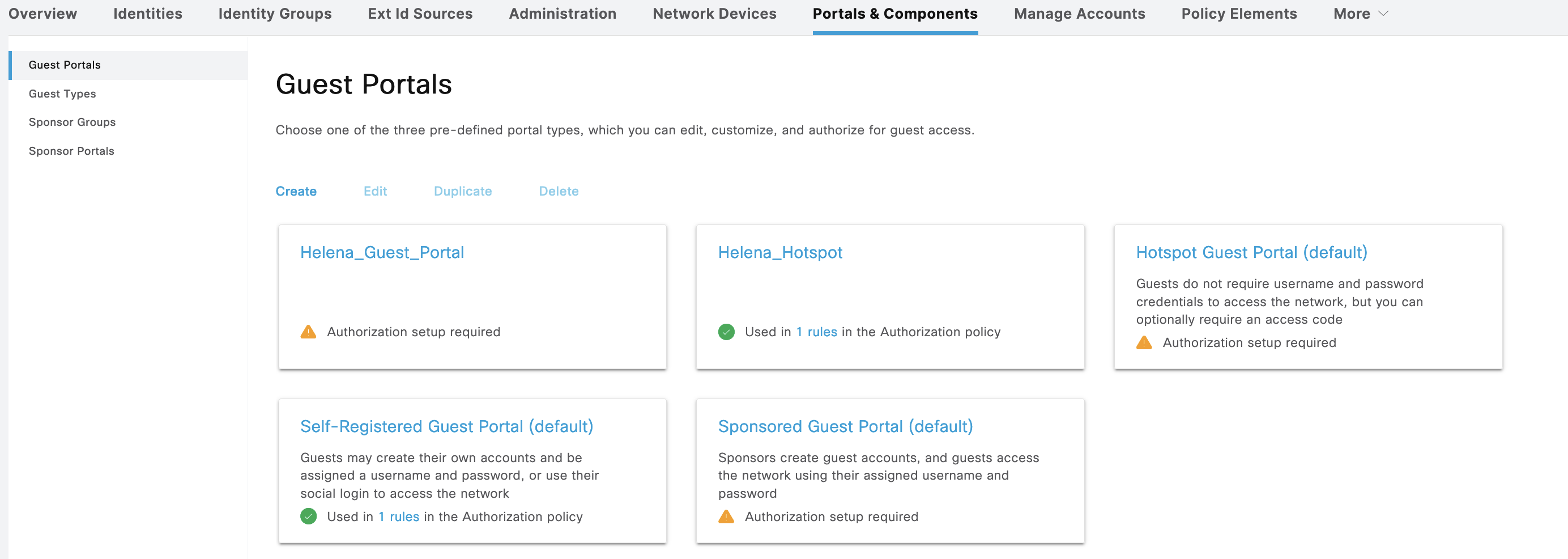
Register Portal is used for guests to access the network using the pre-registered user, to configure that lets create a new Self-Registered Guest Portal named “Helena_Guest_Portal”
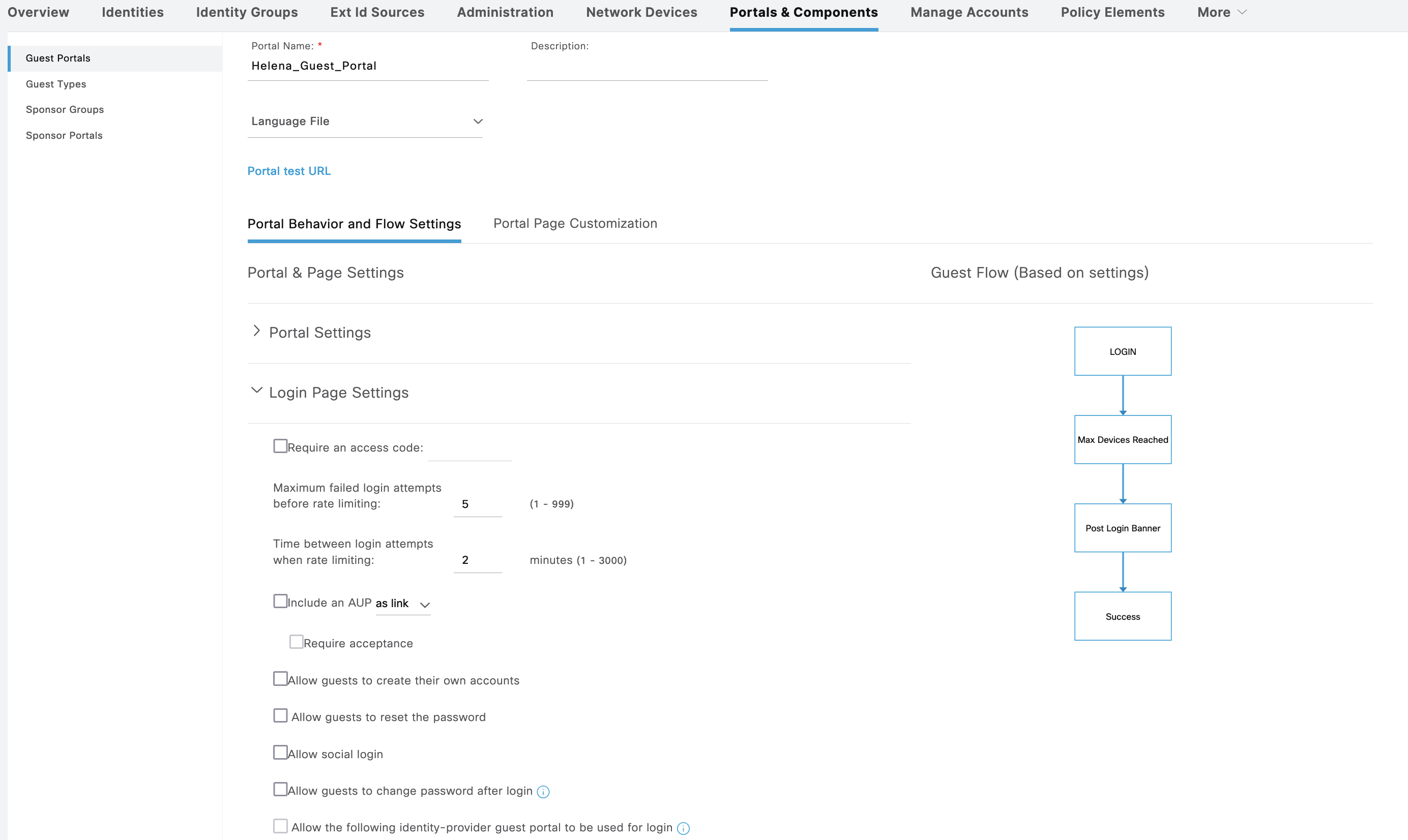
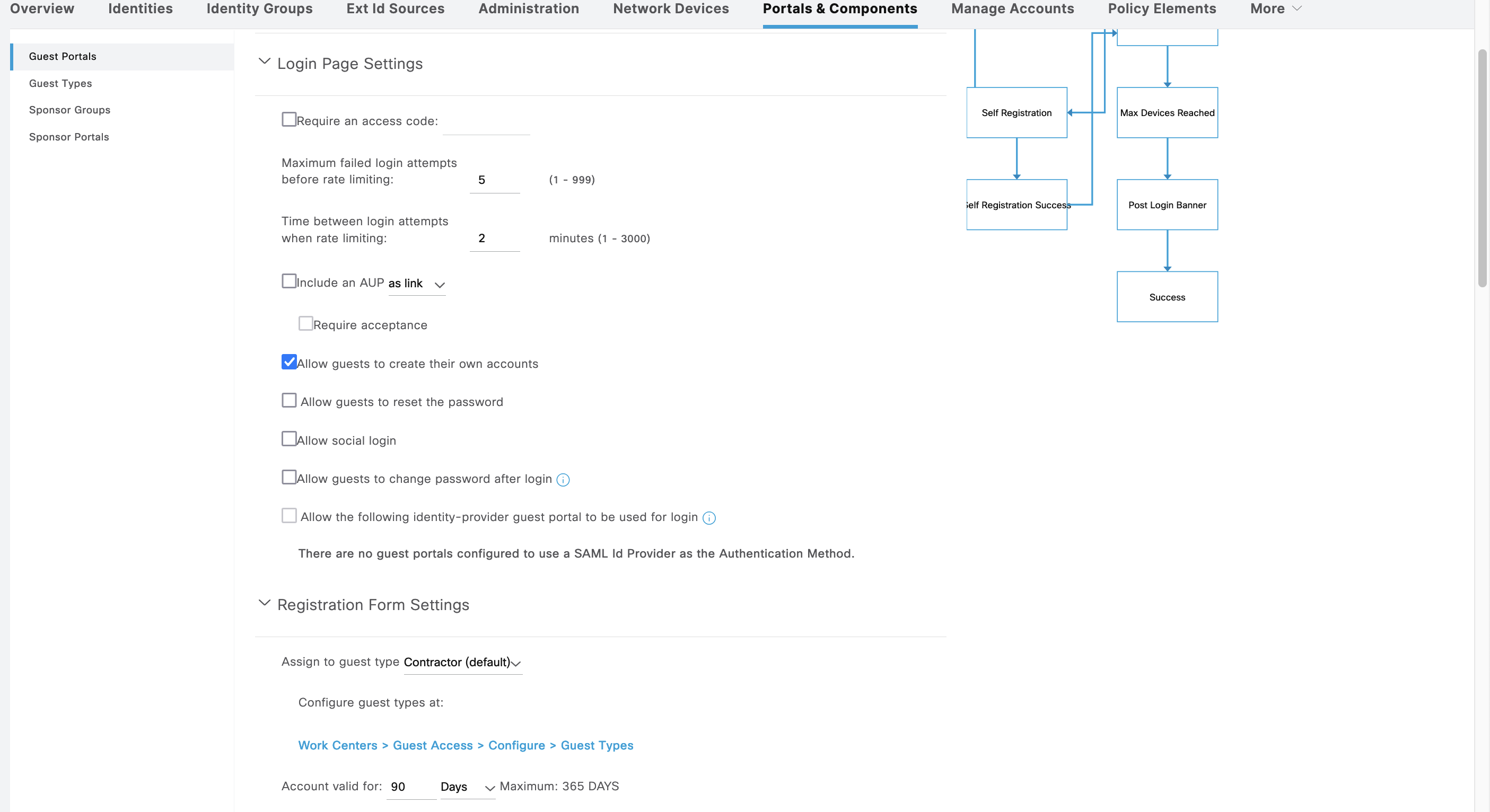
For the Login Page configuration, we’ll uncheck everything just to make it as simple as possible
Next modify the Policy Sets to point the Login Portal to the “GUEST_LOGIN” Authz Profile
This Authz Profile contains a web redirection pointing to the Guest Portal created just now
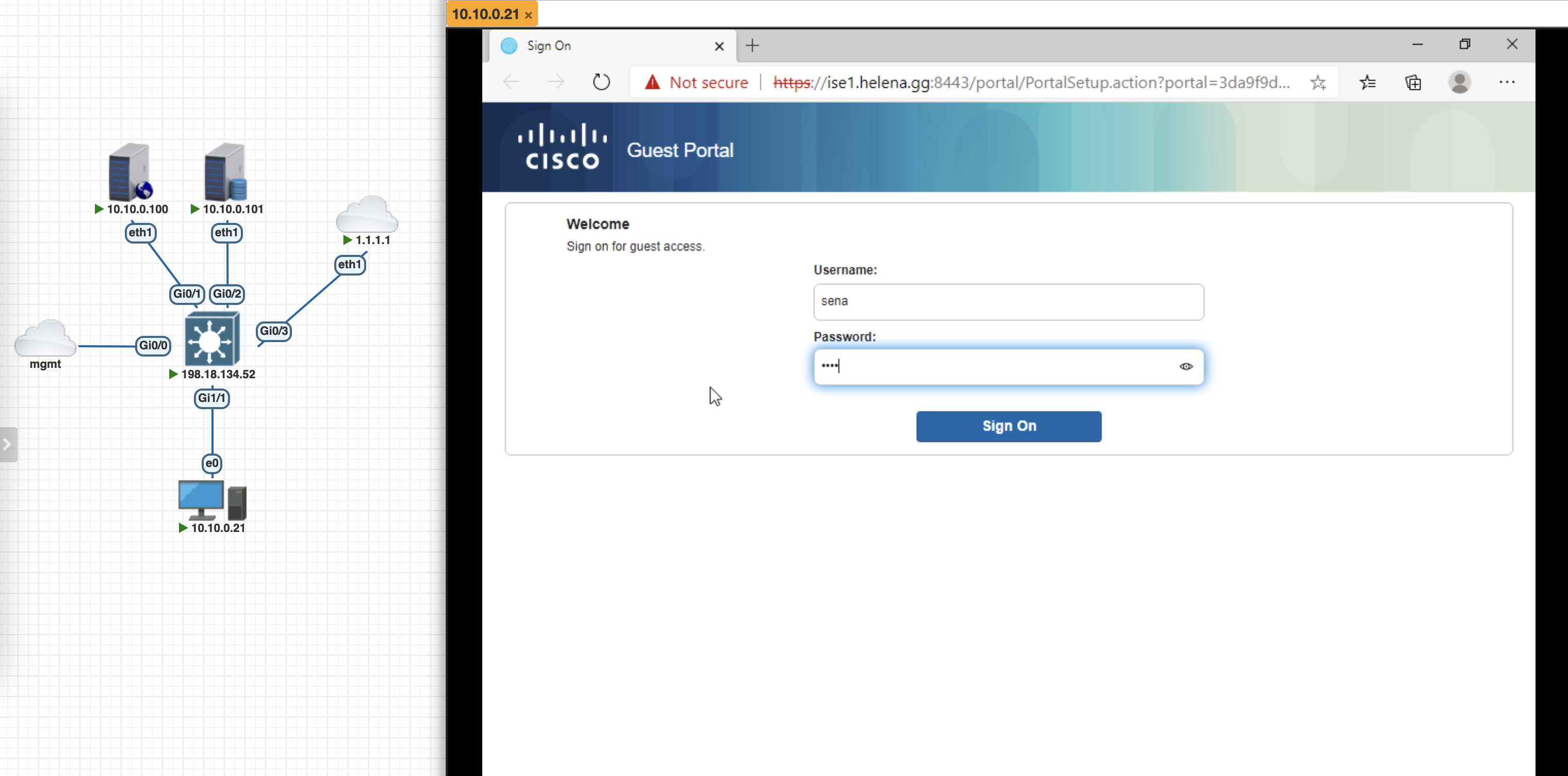
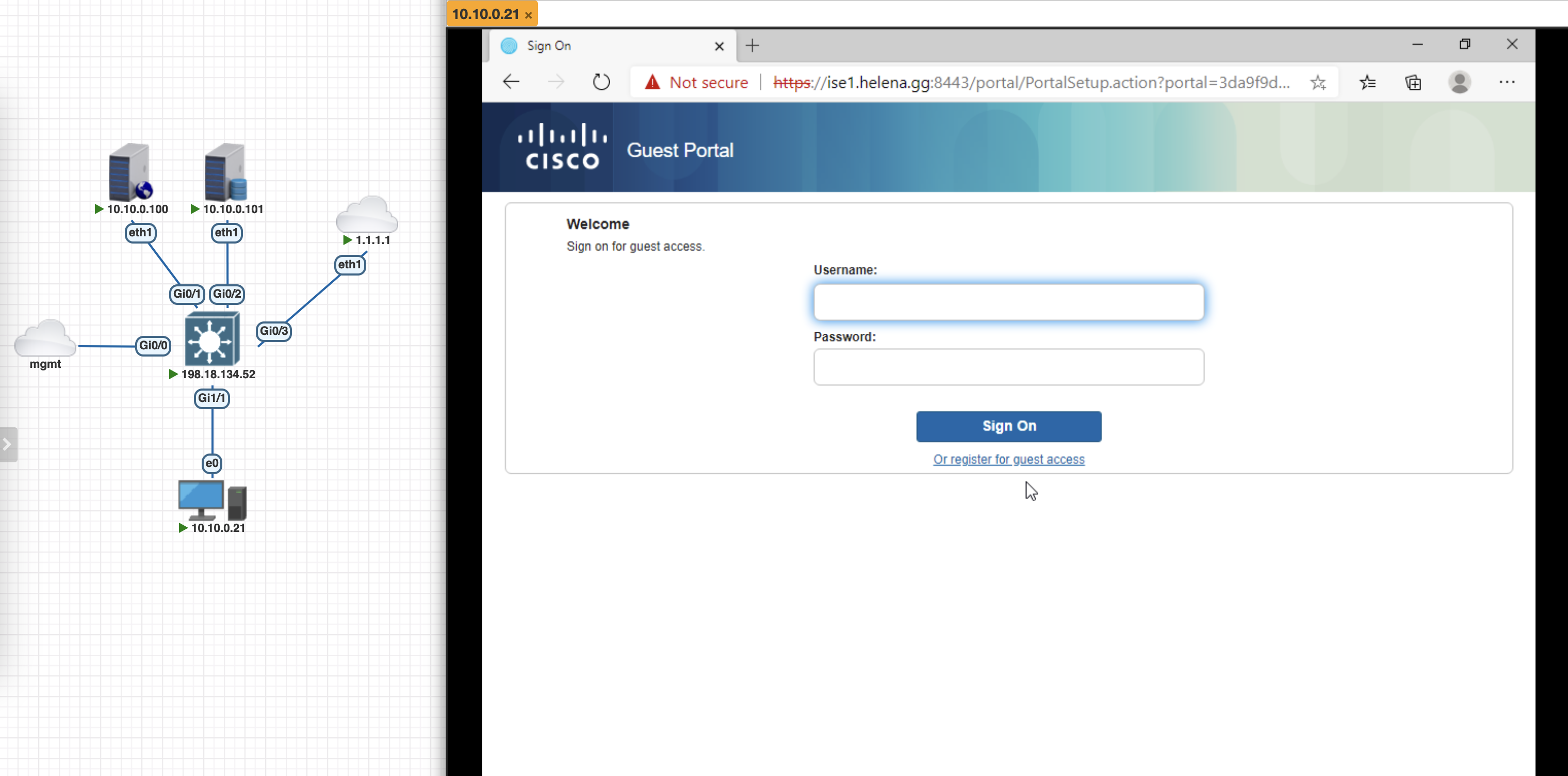
Now lets try connecting the endpoint to the network, here we can see we’re given the Guest Login Portal Authz Rule
On the NAD, we can also see the DACL and Web Redirection URL pointing to the portal
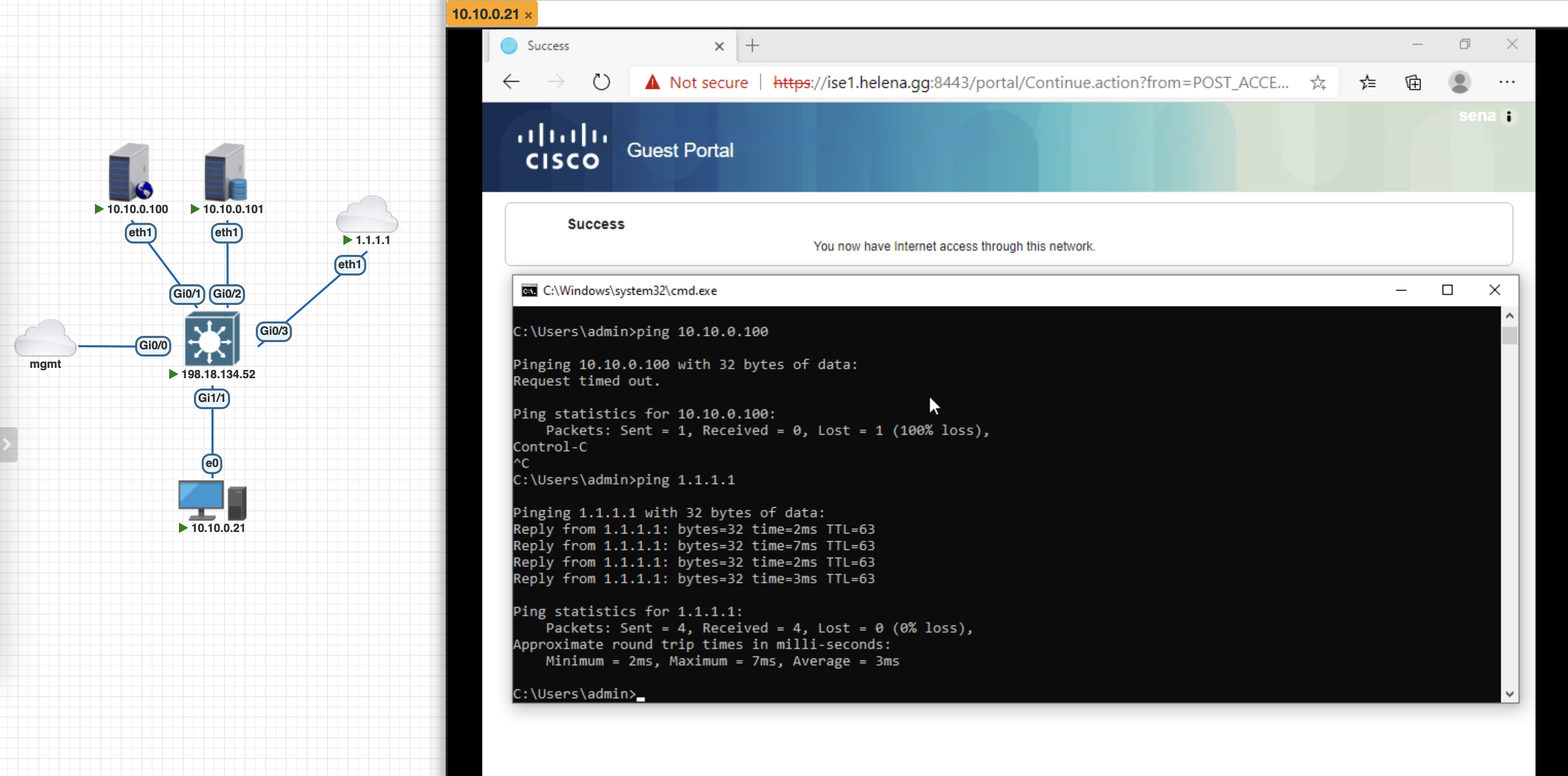
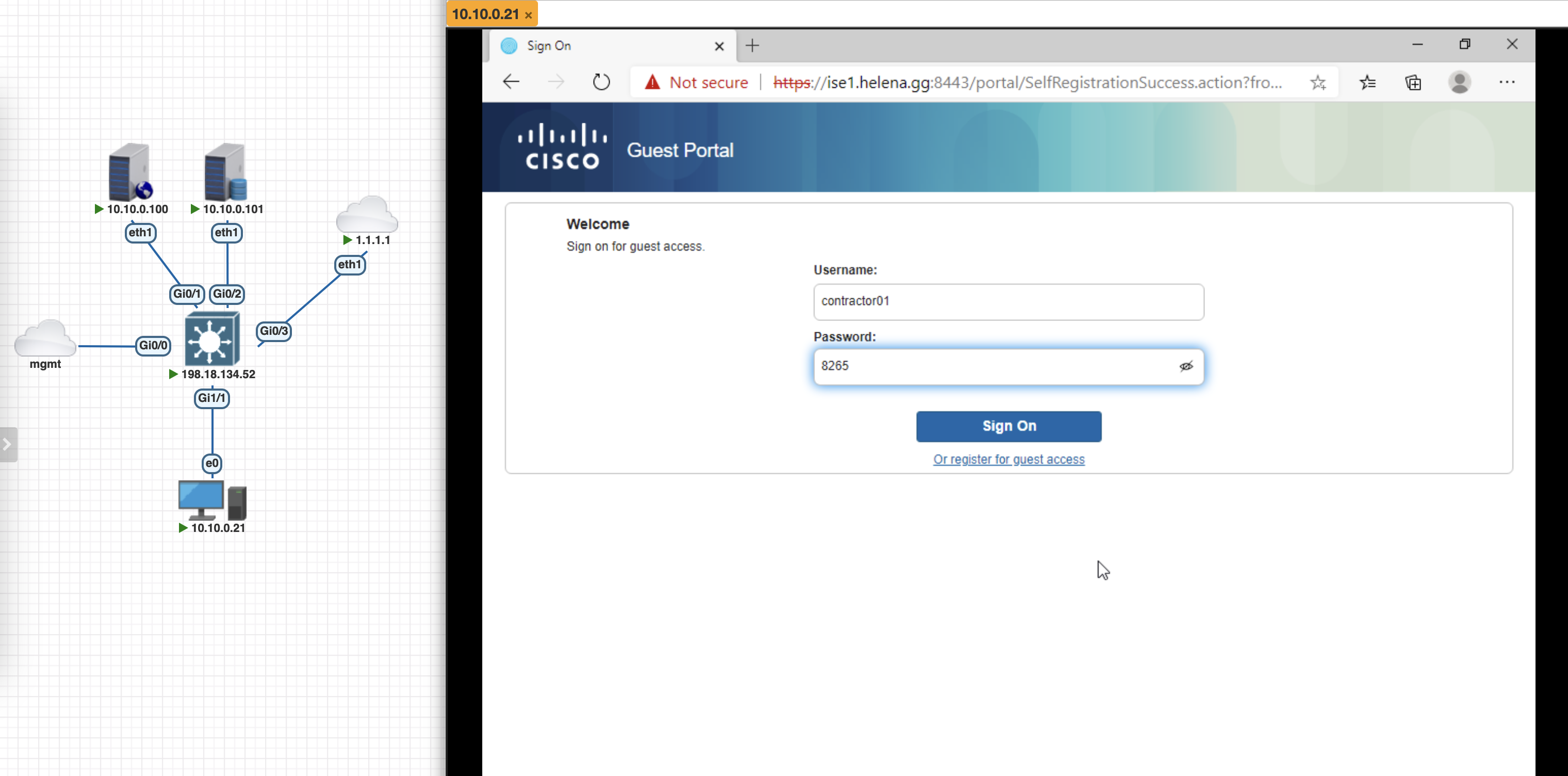
On the Endpoint, we’ve been redirected to the portal and now we can use a registered user to login to the network
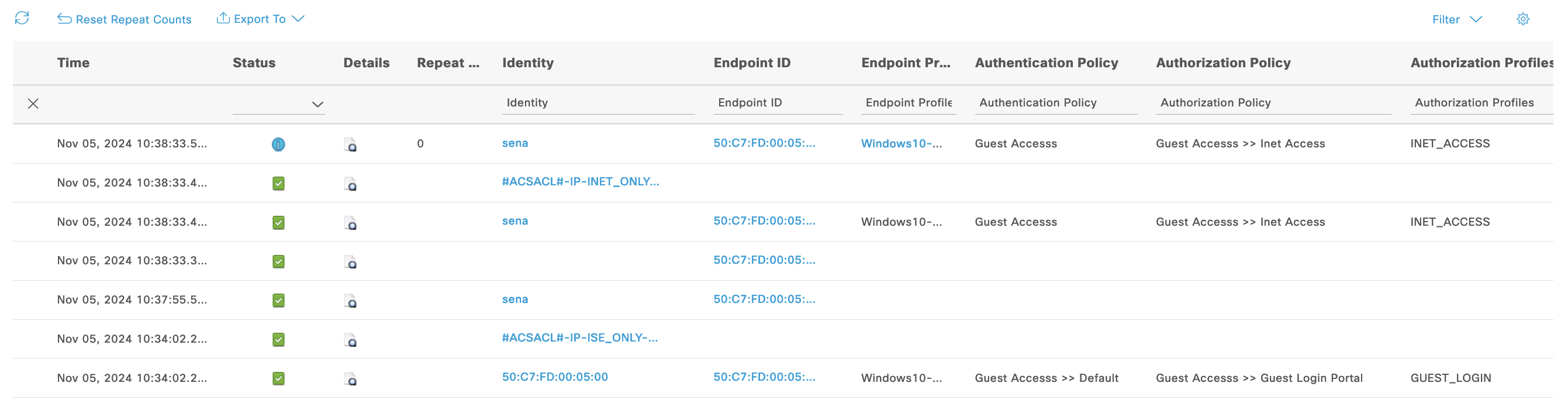
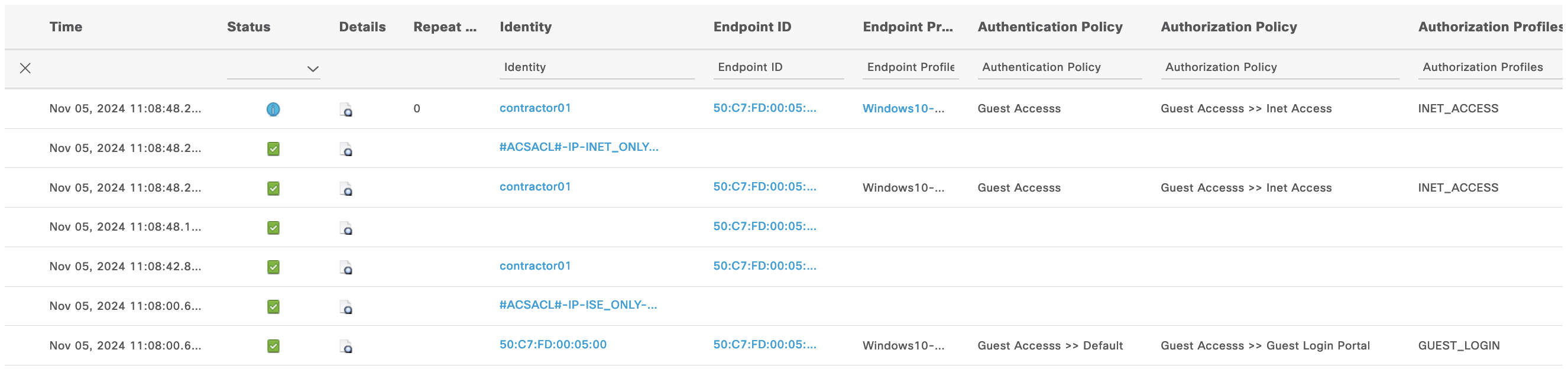
On the Live Logs we can see the Login rule, CoA and then the Inet Access rule being hit by the endpoint
Self-Registering
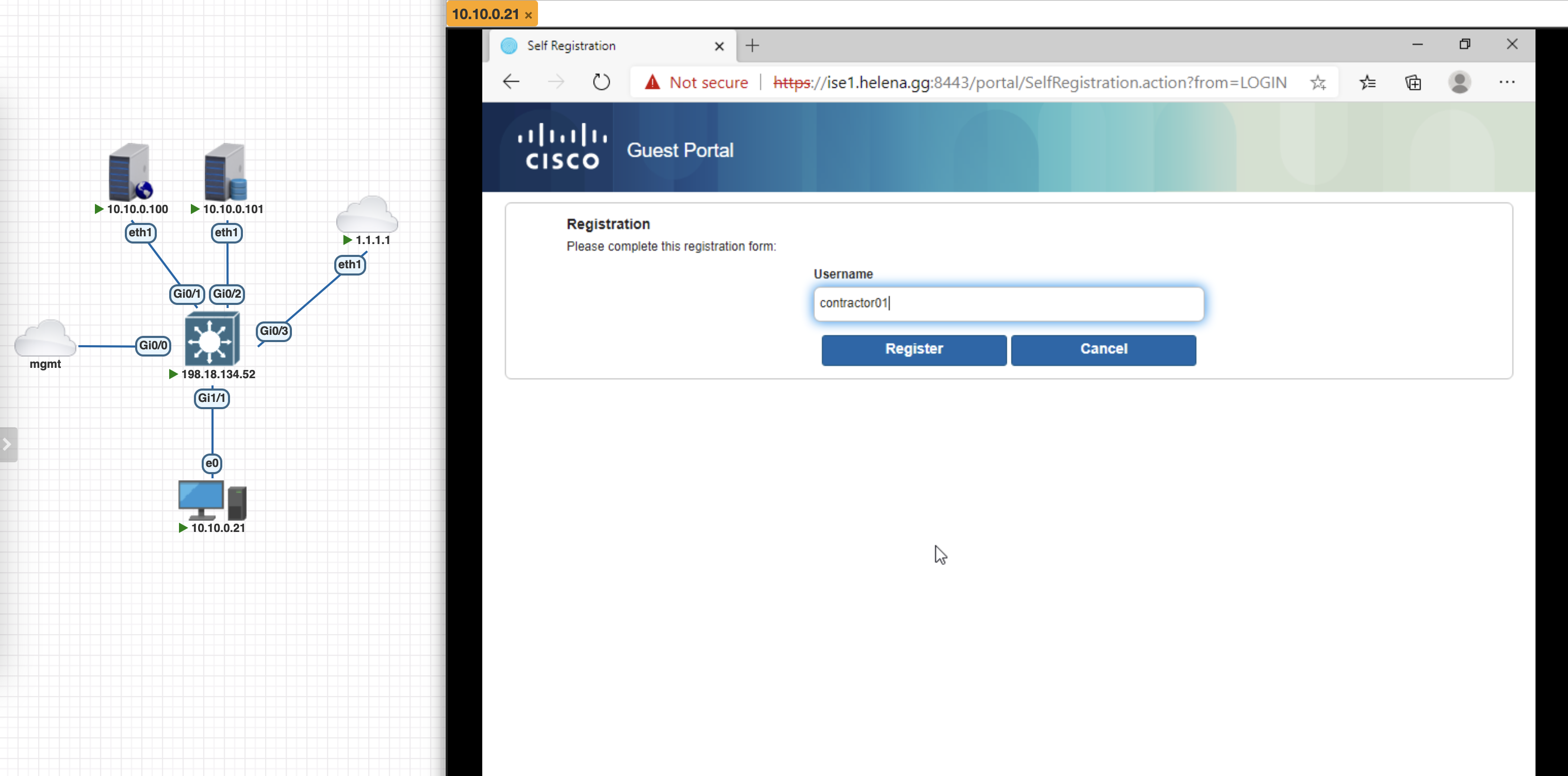
This Portal also has an option to allow user to create account for themselves, we can enable it here and put the registered user into Identity Group Contractor
Here we catch the registered user using the Contractor Identity Group to give them internet access
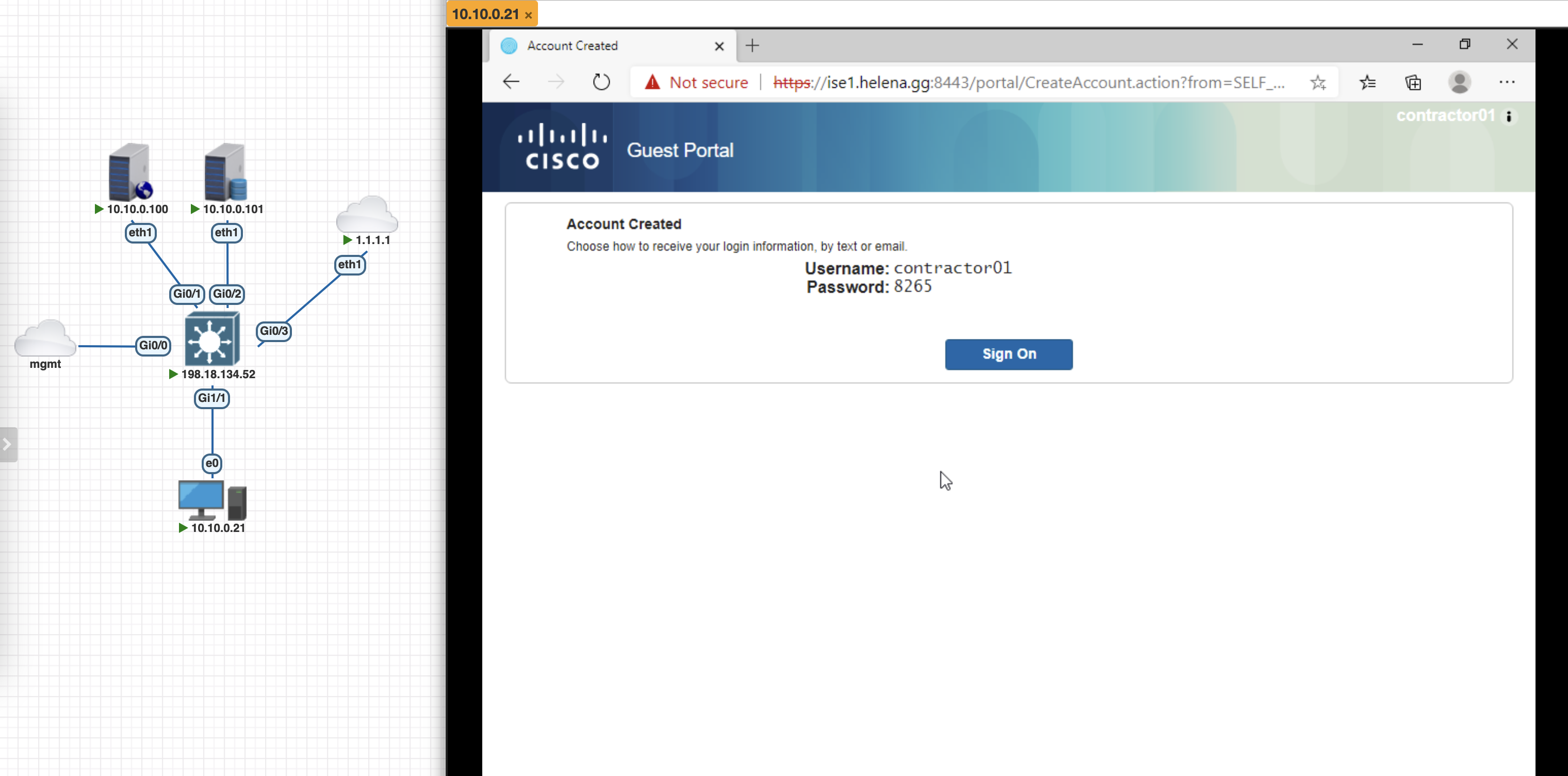
Now when we access the portal, additional option to register for an account is visible and we can create the user
Now we can use the created user along with the generated password to login
Here’s the Live Logs showing the entire process
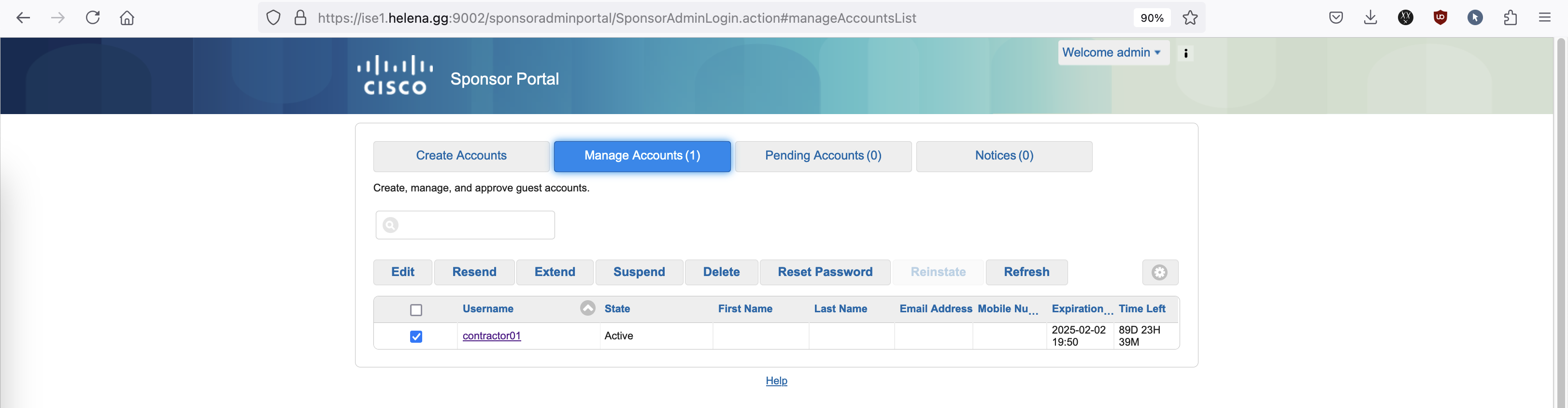
And the created guest users can be seen on the Sponsor Portal