Cisco ISE TrustSec with ASA
Cisco ISE TrustSec enables dynamic and scalable network segmentation by assigning Security Group Tags (SGTs) to users and devices based on their identity and policies. When integrating Cisco ISE with Cisco ASA, SXP (Security Group Tag Exchange Protocol) is used to propagate these SGTs from ISE to the ASA, even if the ASA doesn’t have direct Layer 2 adjacency to the tagged devices.
In this setup, ISE assigns SGTs to endpoints based on authentication and authorization policies. The ASA, acting as an SXP peer, receives these SGT mappings through SXP. With this information, the ASA can enforce fine-grained security policies, such as allowing or denying traffic based on the SGT of the source and destination, enabling context-aware access control and micro-segmentation across the network.
Configuring TrustSec
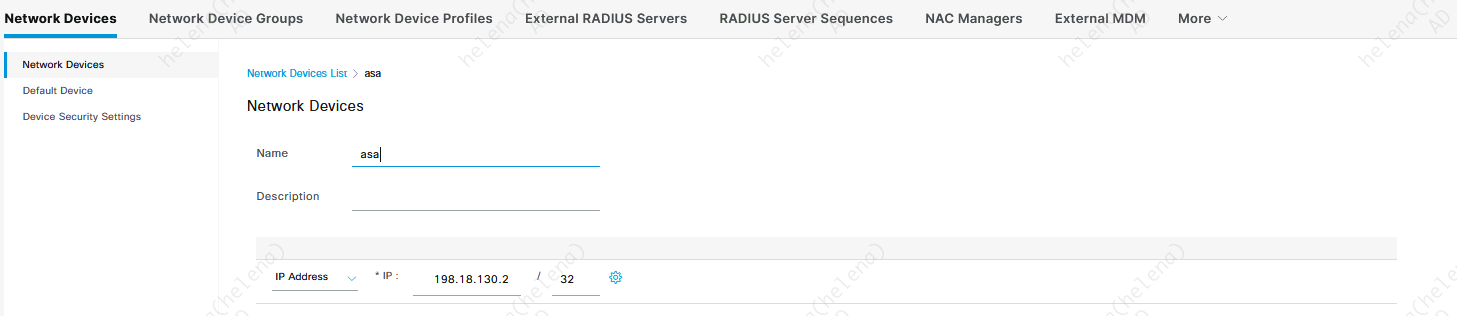
On ISE, first we add the ASA as a Network Access Device (NAD)
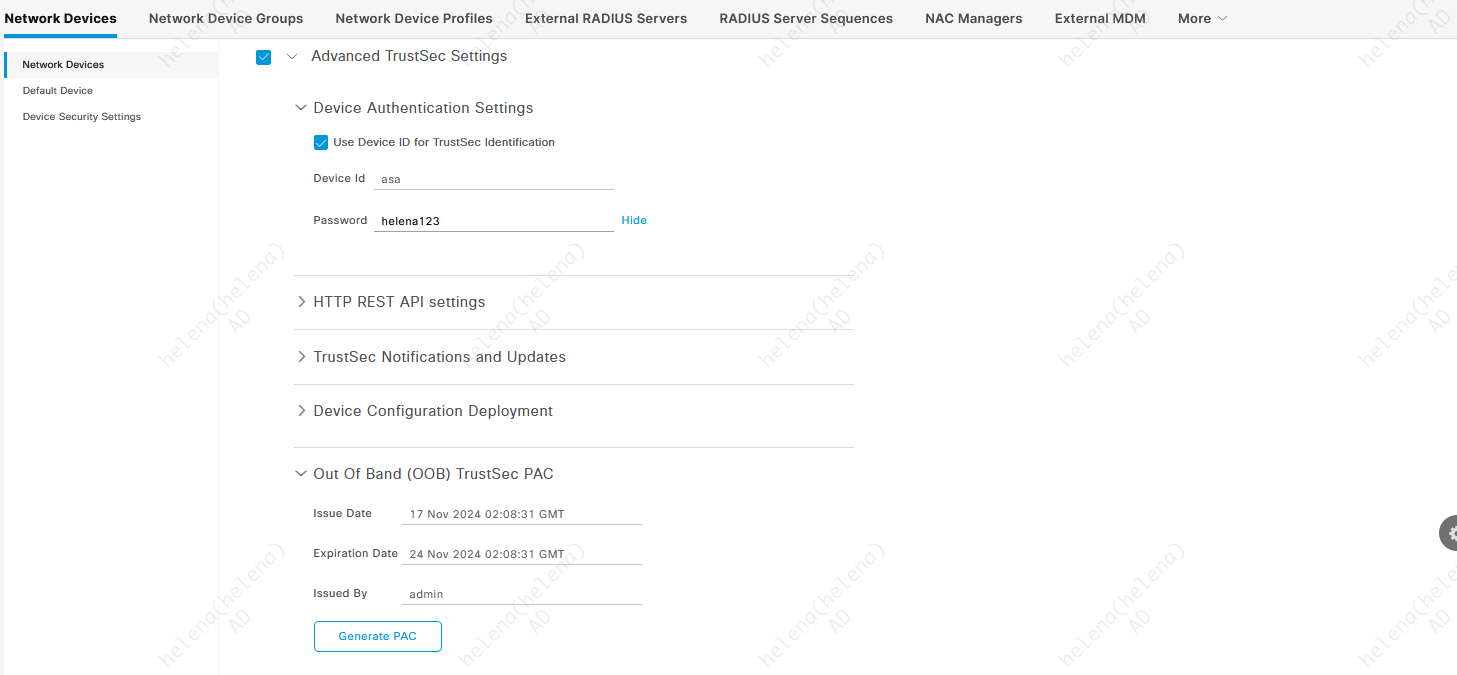
Enable Advanced TrustSec and download the PAC
The TrustSec PAC (Provisioning and Authentication Credential) is a cryptographic credential used for establishing secure communication between ASA and ISE within the Cisco TrustSec architecture. It ensures mutual authentication and encryption between TrustSec components, such as SXP peers.
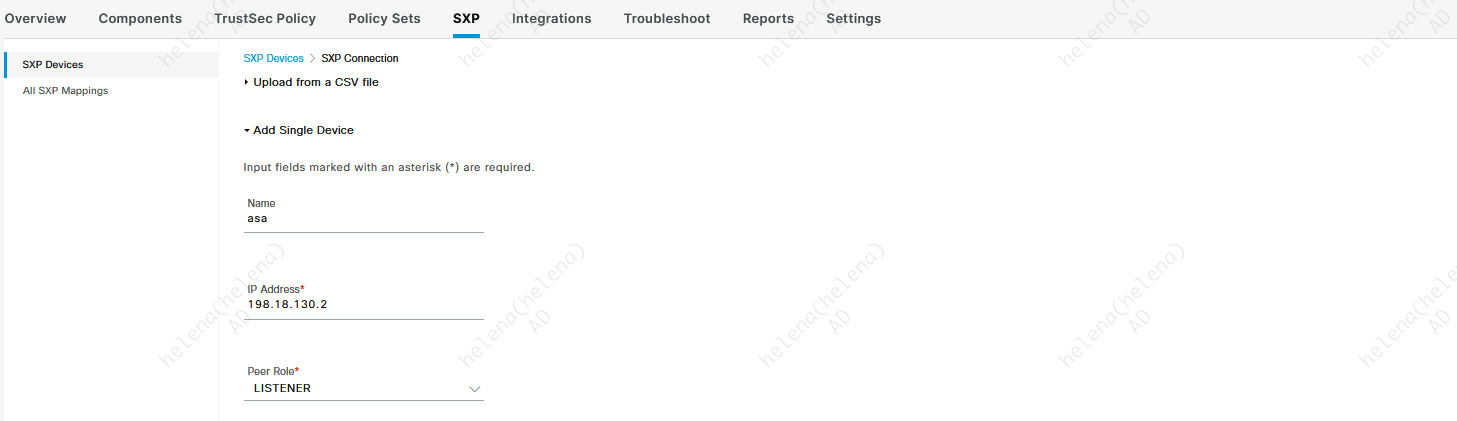
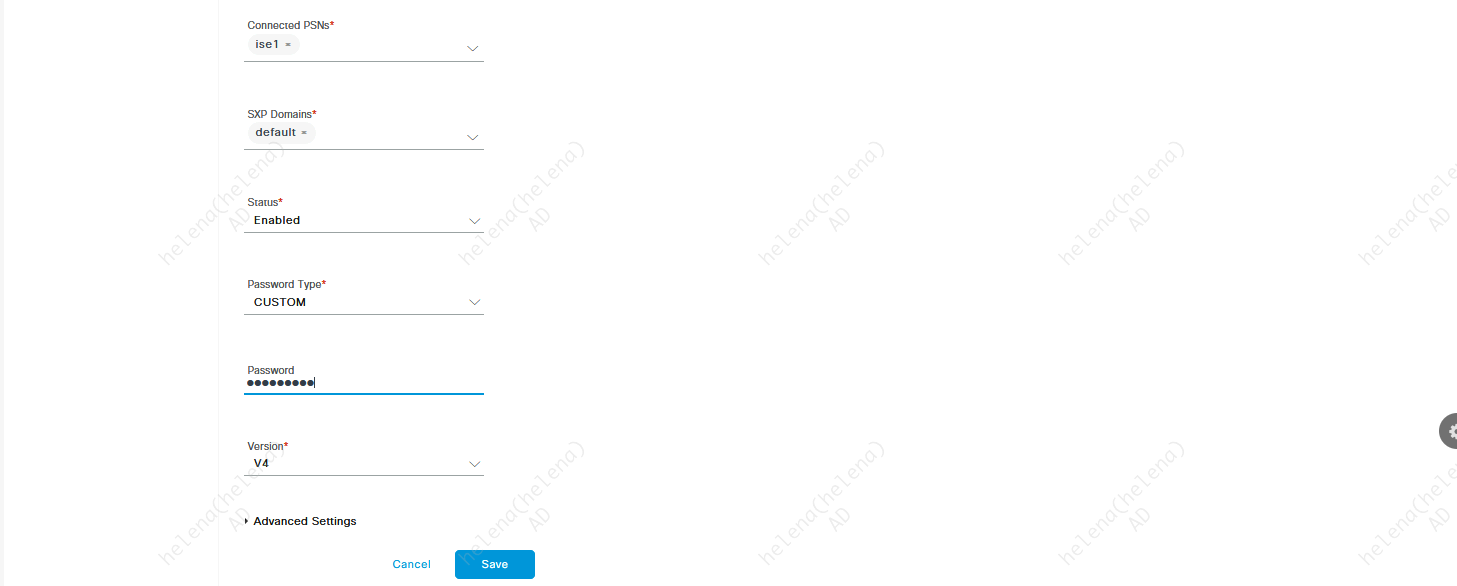
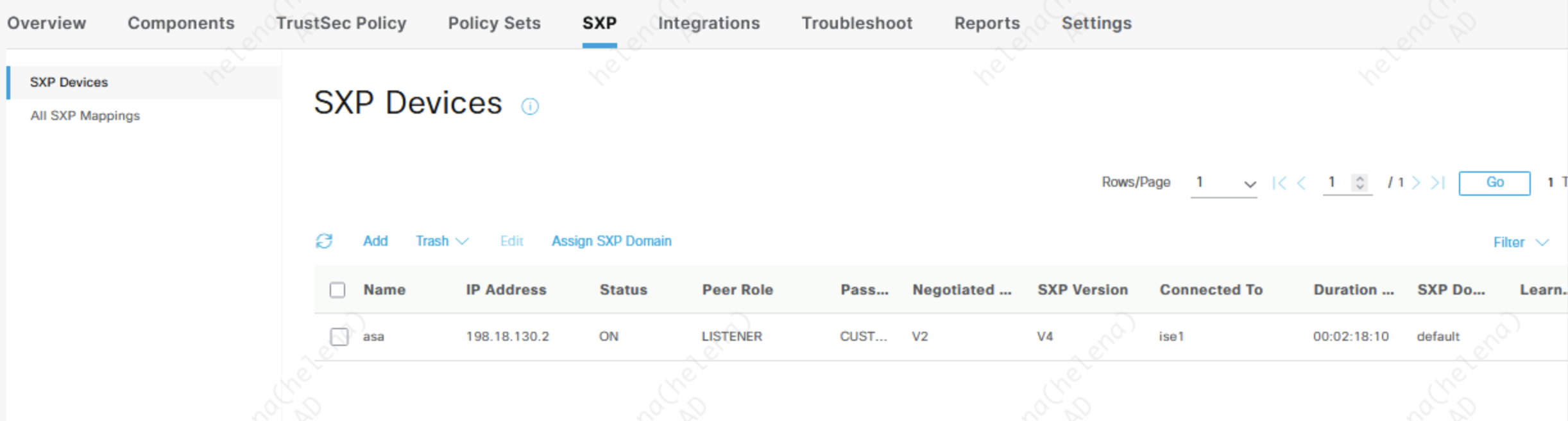
Next we add the ASA as an SXP Peers on Work Centers » SXP » SXP Devices
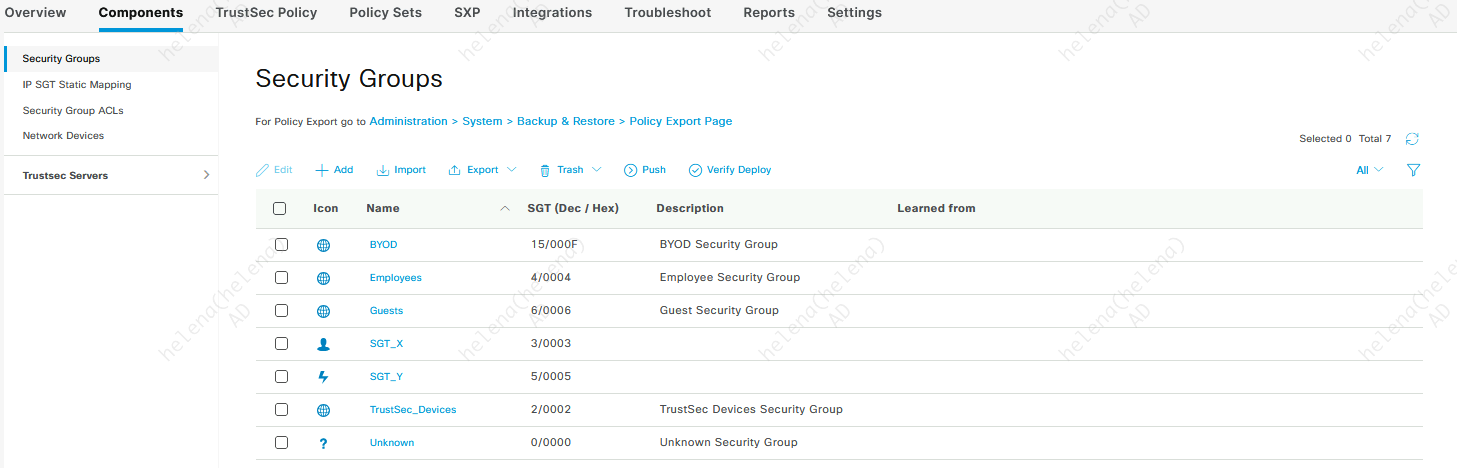
Then we configure the SGTs to be used, here we will utilize SGT_X and SGT_Y
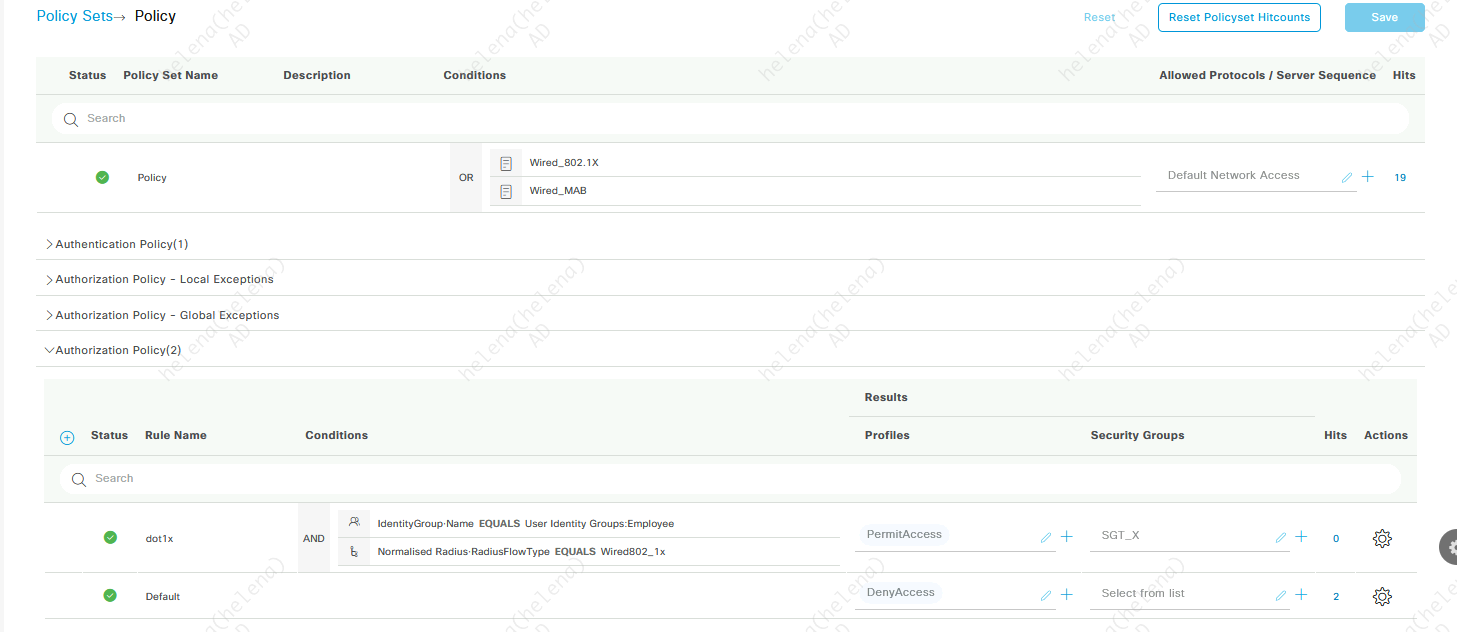
After that we configure a Policy Sets that will assign an SGT for endpoint connecting to the network
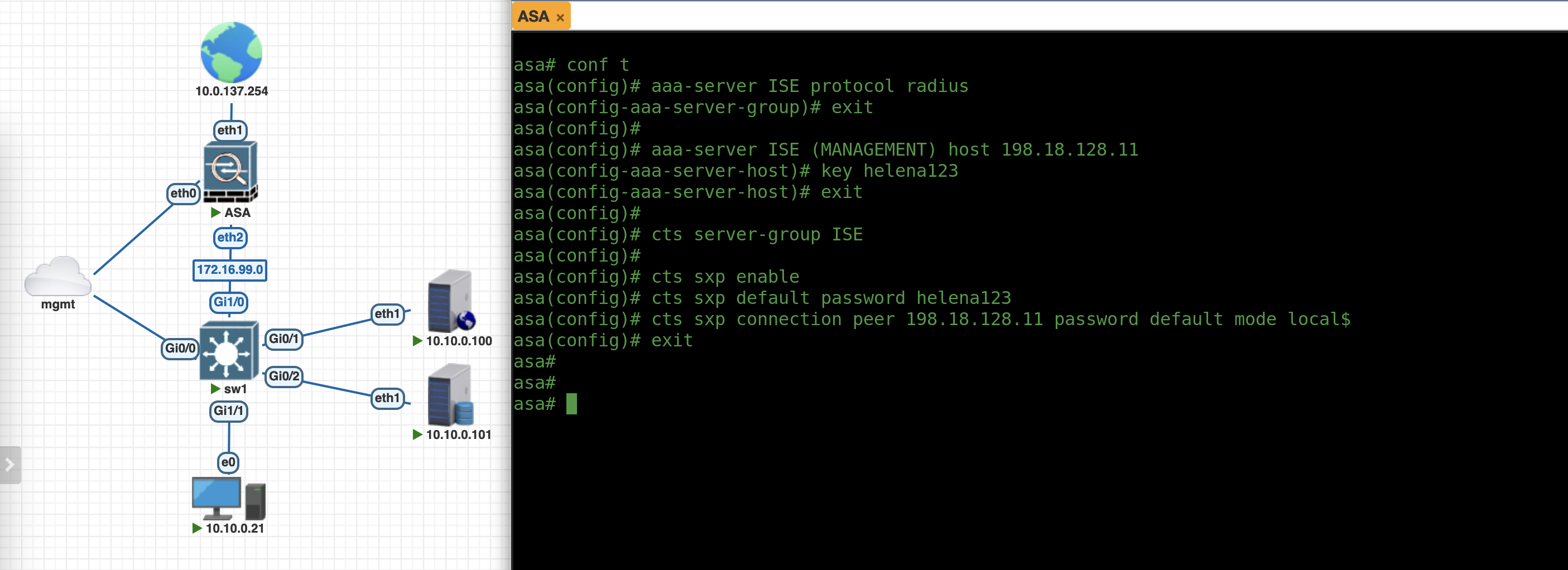
Next on ASA, lets make the CTS Configuration
1
2
3
4
5
6
7
8
9
aaa-server ISE protocol radius
aaa-server ISE (MANAGEMENT) host 198.18.128.11
key helena123
cts server-group ISE
cts sxp enable
cts sxp default password helena123
cts sxp connection peer 198.18.128.11 password default mode local listener
CTS configuration on an ASA involves enabling Cisco TrustSec, importing a PAC for authentication with ISE, and configuring SXP to exchange SGT-to-IP mappings for dynamic policy enforcement.
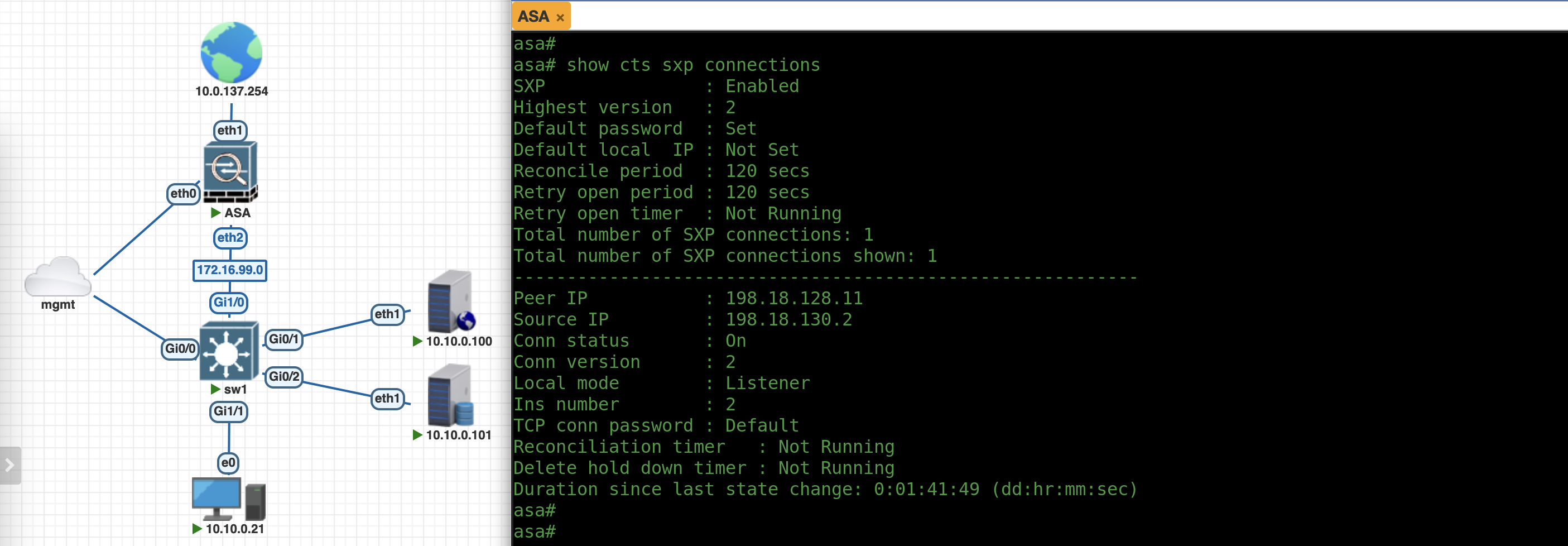
Run “show cts sxp connections” to see the CTS configuration
On ISE side, we can see on the SXP Devices that ASA is up and running
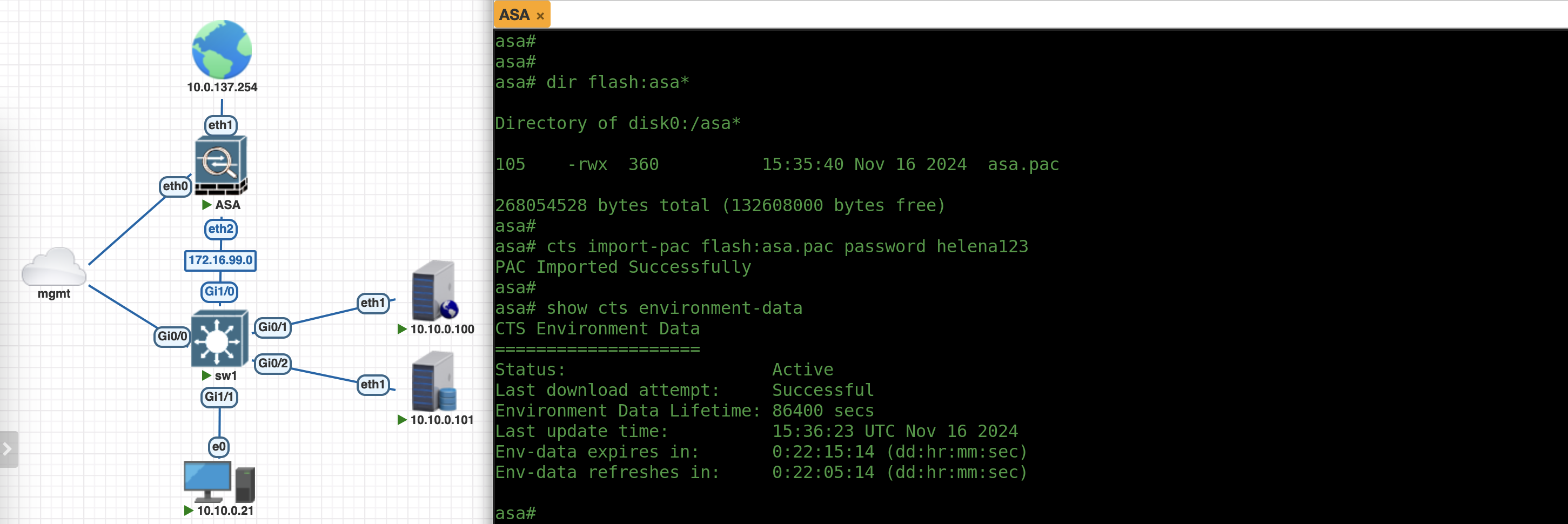
Next we’ll import the PAC to ASA, first copy it to the flash: directory and run the import command
1
cts import-pac flash:asa.pac password helena123
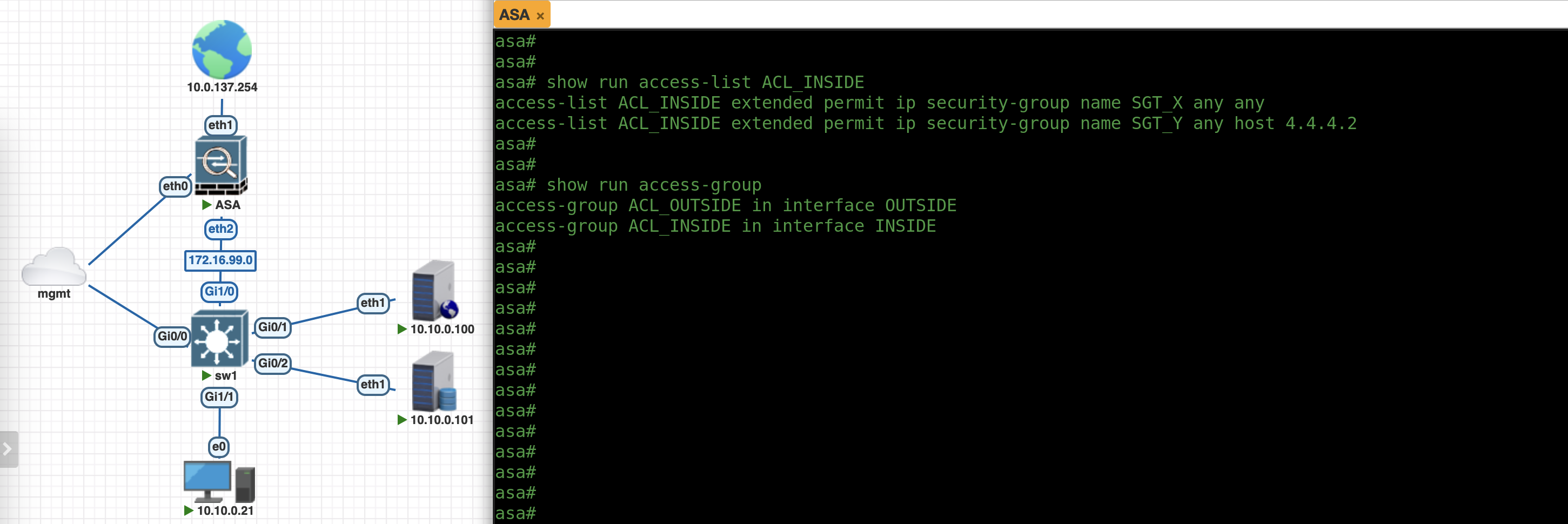
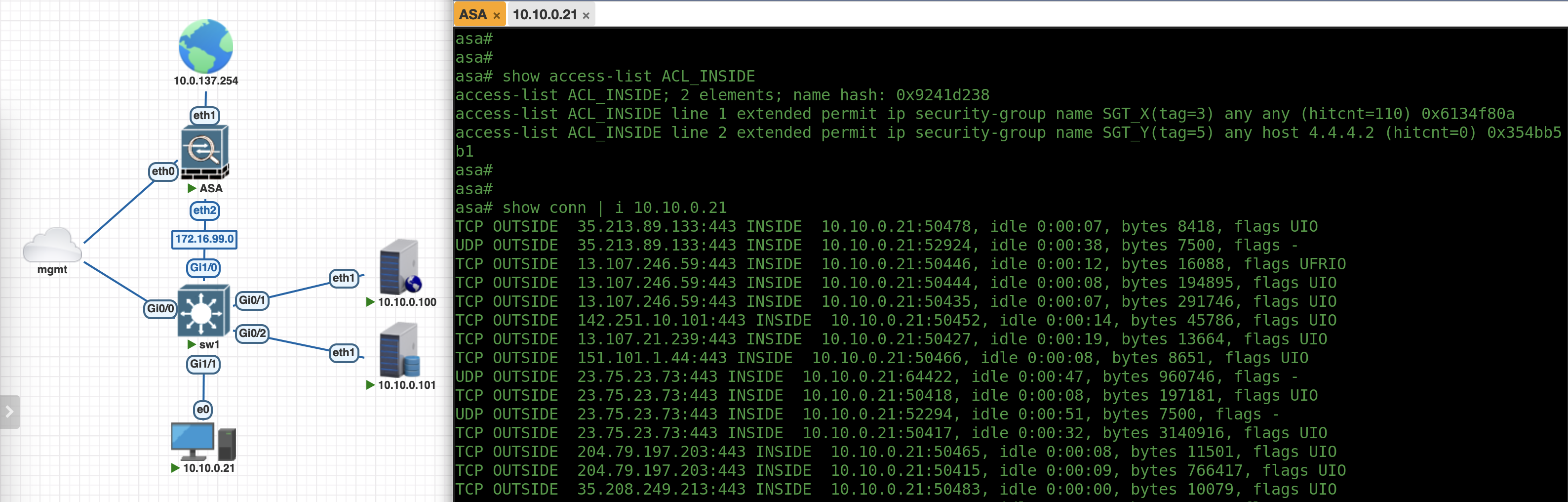
Now we can use the SGT to create our firewall policies, here we enable SGT_X to access anything on the Internet while SGT_Y can only access specific host of 4.4.4.2
Dynamic SGT
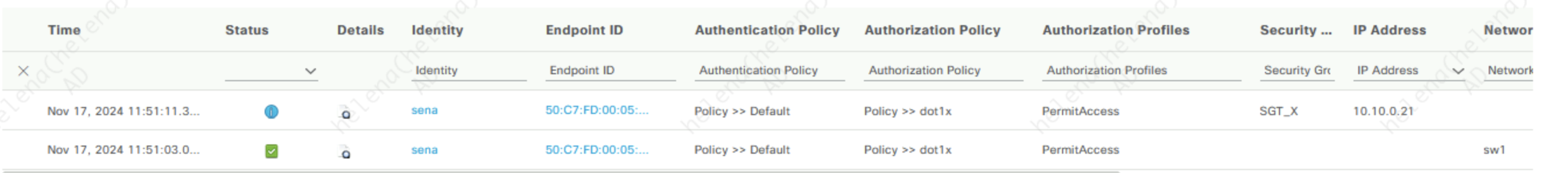
After connecting endpoint to the network, ISE now has given it an SGT of “SGT_X”
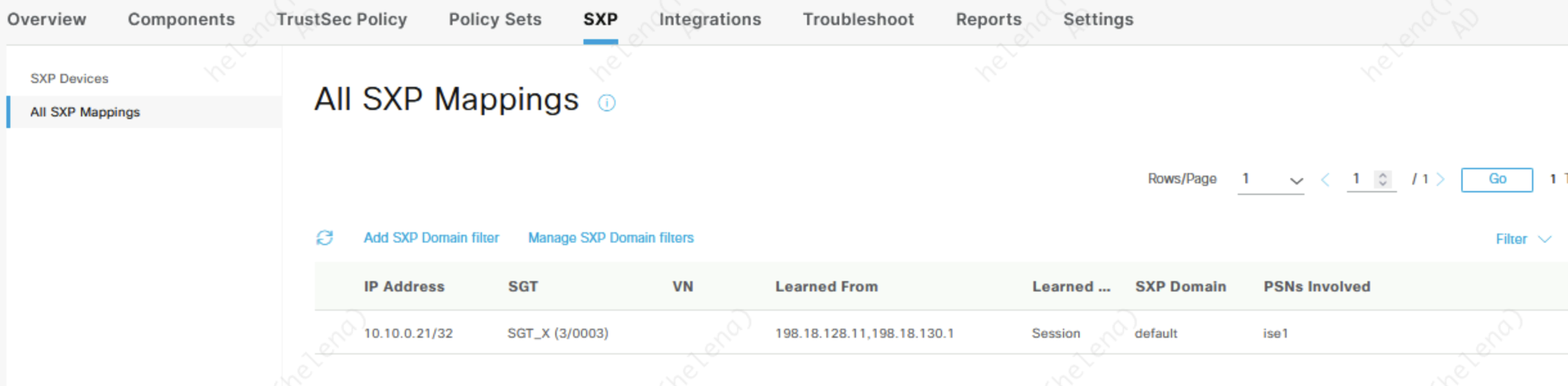
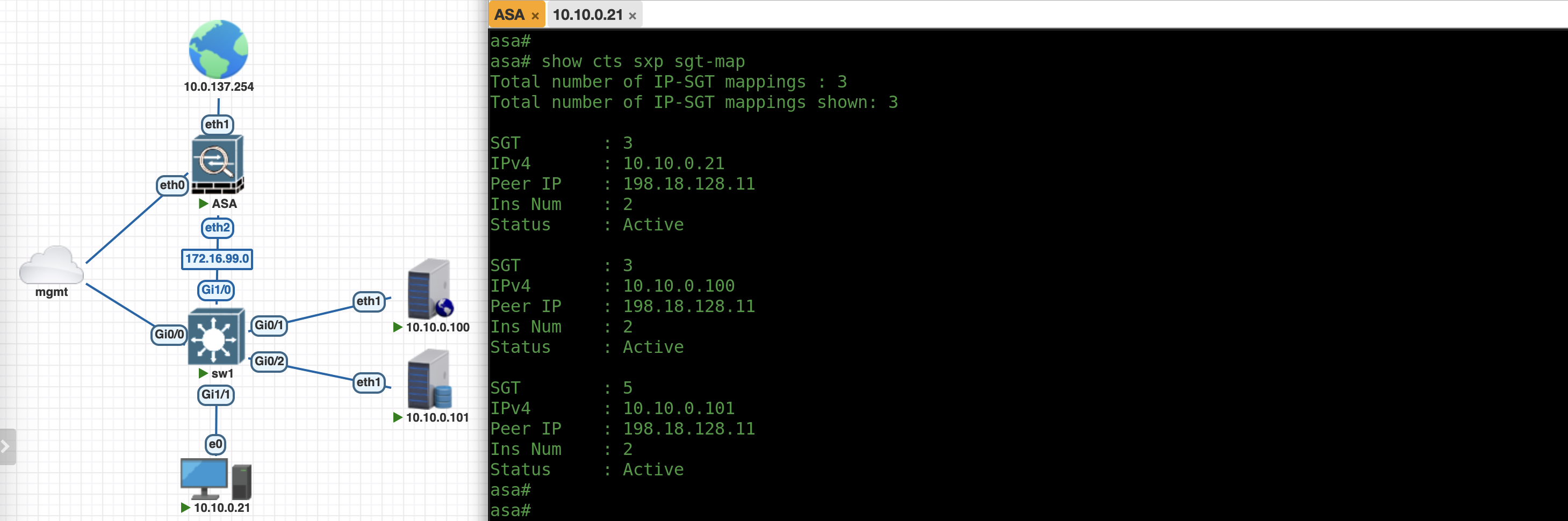
On the SXP Mappings, we can see now this endpoint is mapped with an SGT
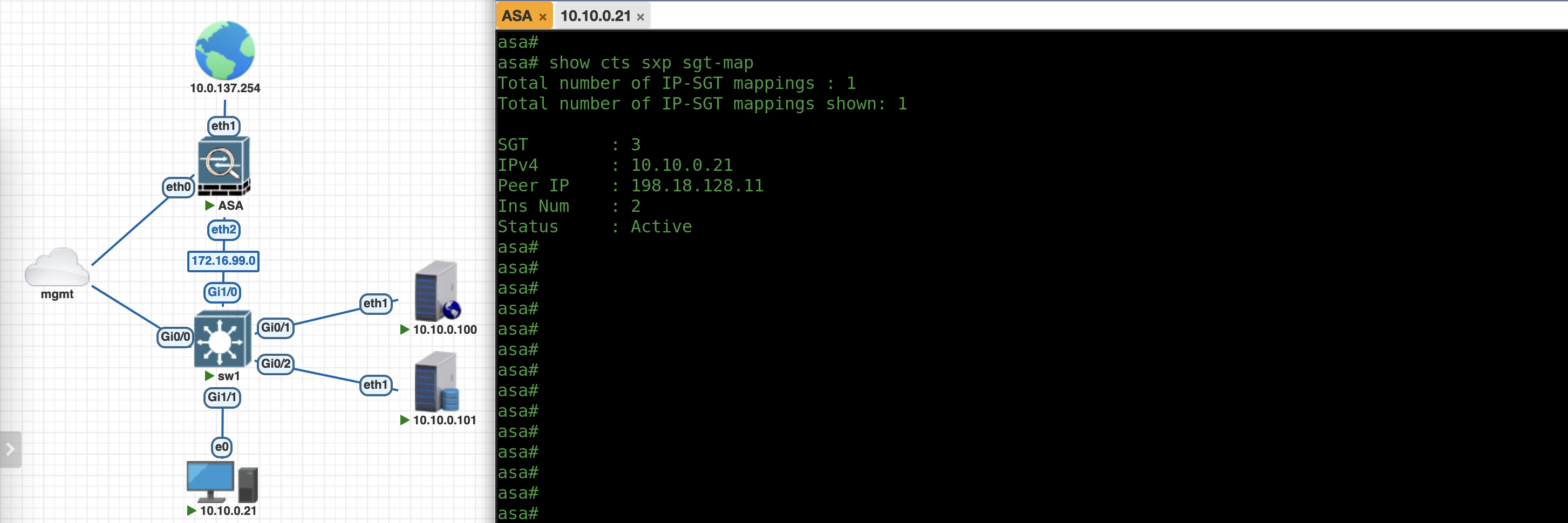
This mapping is propagated to ASA through SXP, allowing ASA to also has the very same IP-to-SGT mappings
And because this endpoint has SGT_X, it can access the internet without restrictions
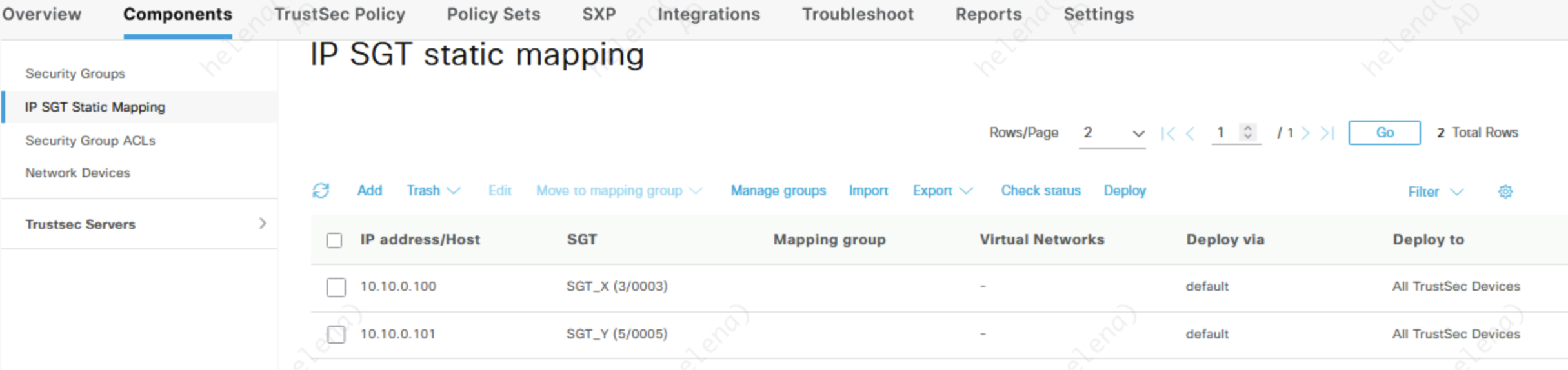
Static SGT
Beside getting SGT mapped from Policy Sets, we can also statically assign an SGT to an IP Address on ISE
This SGT mappings are reflected on the ASA as well
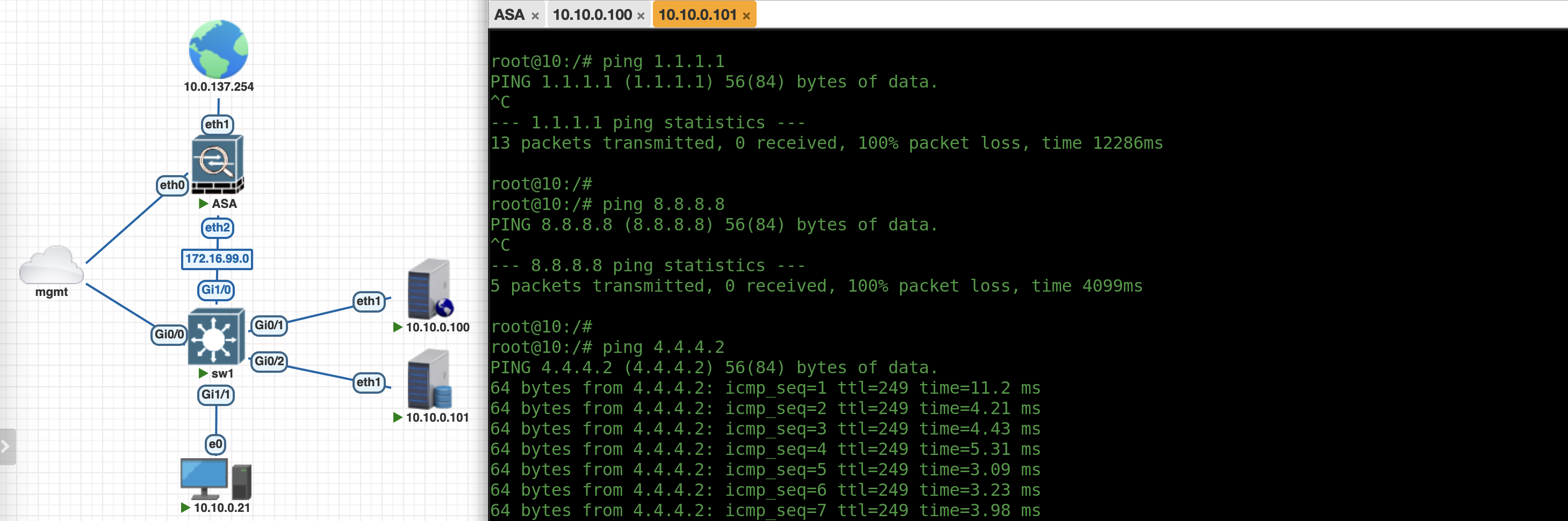
Now if we try accessing the internet with endpoint with SGT_Y, we can only access 4.4.4.2
Here’s the radius configuration on switch side
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
radius server ISE
address ipv4 198.18.128.11 auth-port 1812 acct-port 1813
key helena
aaa group server radius ISE_GROUP
server name ISE
aaa new-model
aaa authentication dot1x default group ISE_GROUP
aaa authorization network default group ISE_GROUP
aaa accounting dot1x default start-stop group ISE_GROUP
dot1x system-auth-control
interface range GigabitEthernet1/1
switchport host
switchport access vlan 10
authentication host-mode multi-domain
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
mab
dot1x pae authenticator