Cisco ISE TrustSec with FTD
Cisco ISE integrates with FTD through FMC to leverage Security Group Tags (SGTs) for policy enforcement. ISE assigns SGTs to users and devices based on authentication, while FMC configures FTD to apply security policies based on these SGTs, enabling dynamic, identity-based access control for network traffic and enhancing visibility and security.
SGT Configurations
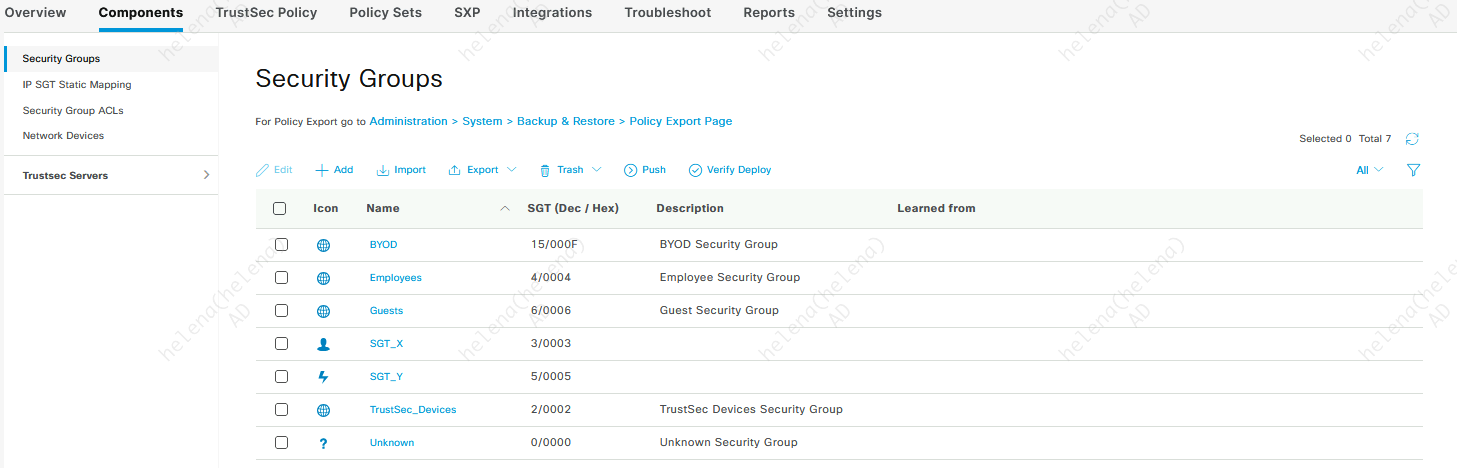
Firstly on ISE, lets create the SGT that will be used. Here the SGTs are SGT_X and SGT_Y
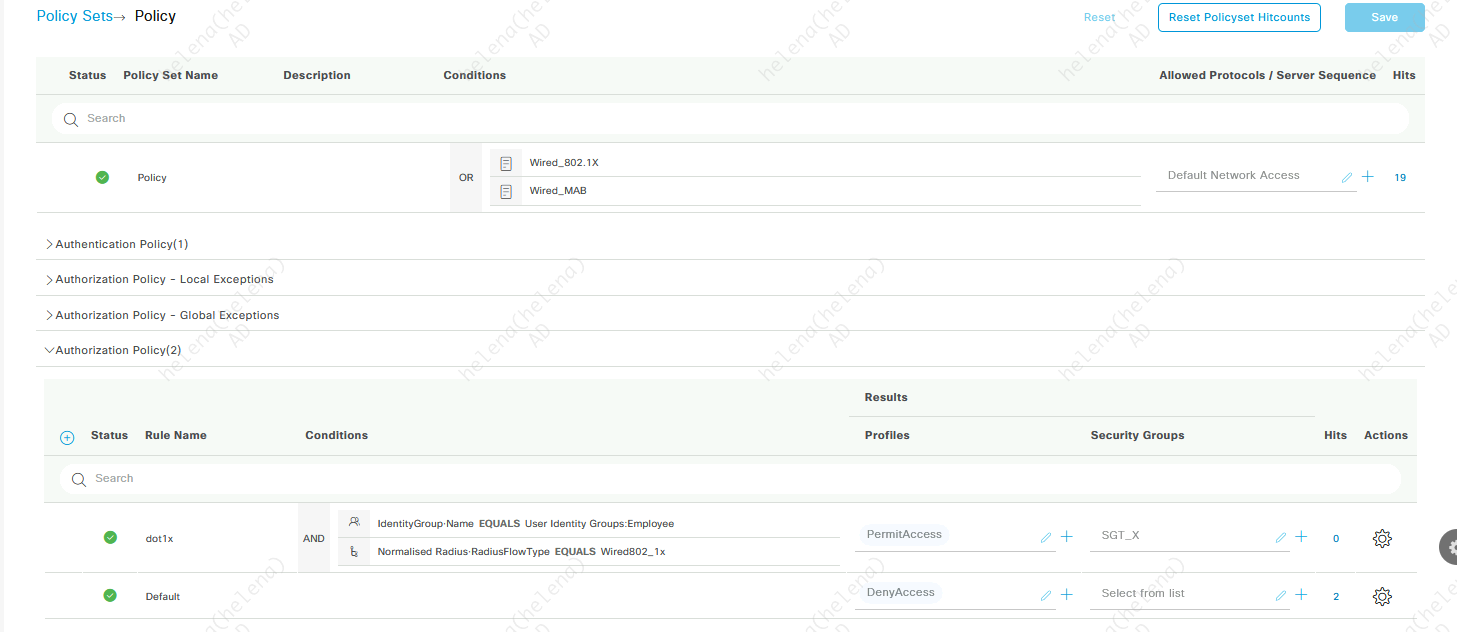
Next on Policy Sets, we set here so ISE gives dynamic SGT assignments
Certificates
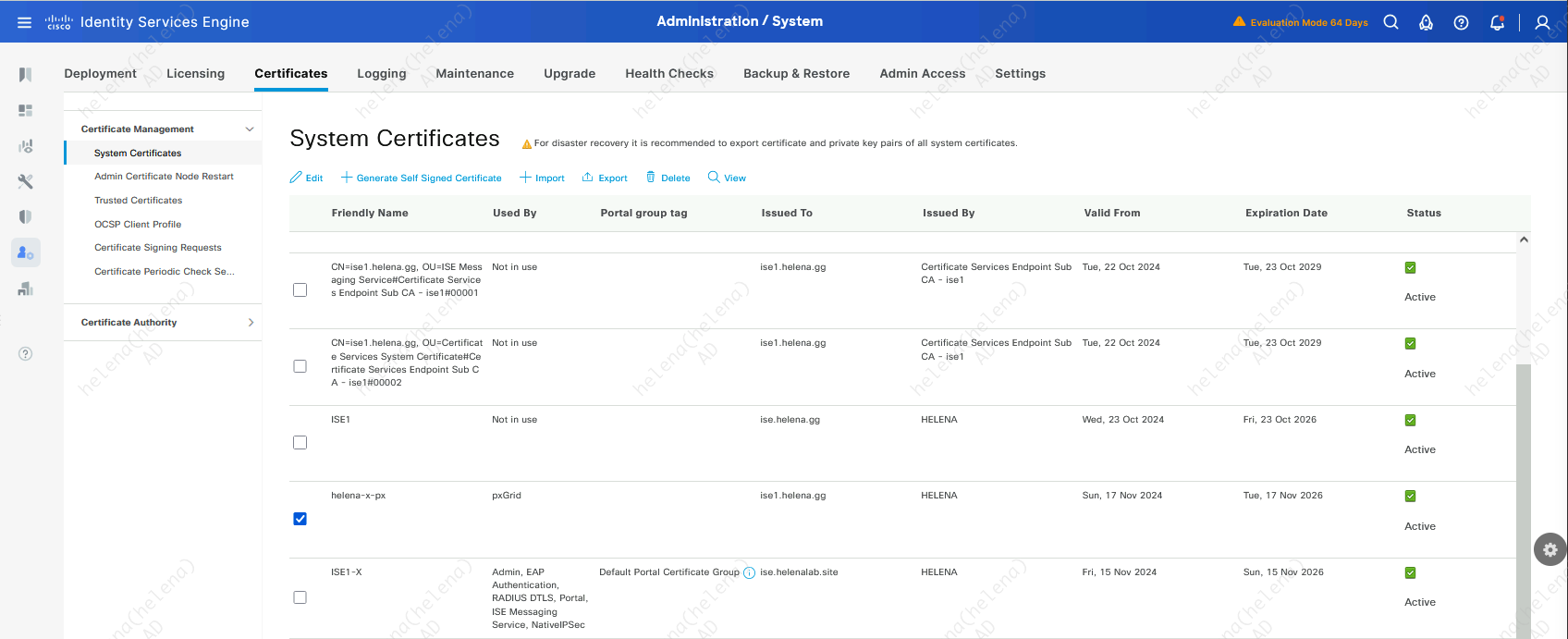
ISE-FMC integration requires certificate-based authentication to provide mutual trust between two devices. Here make sure PxGrid has a CA Signed Certificate with Client/Server Authentication enabled on the Certificate Template
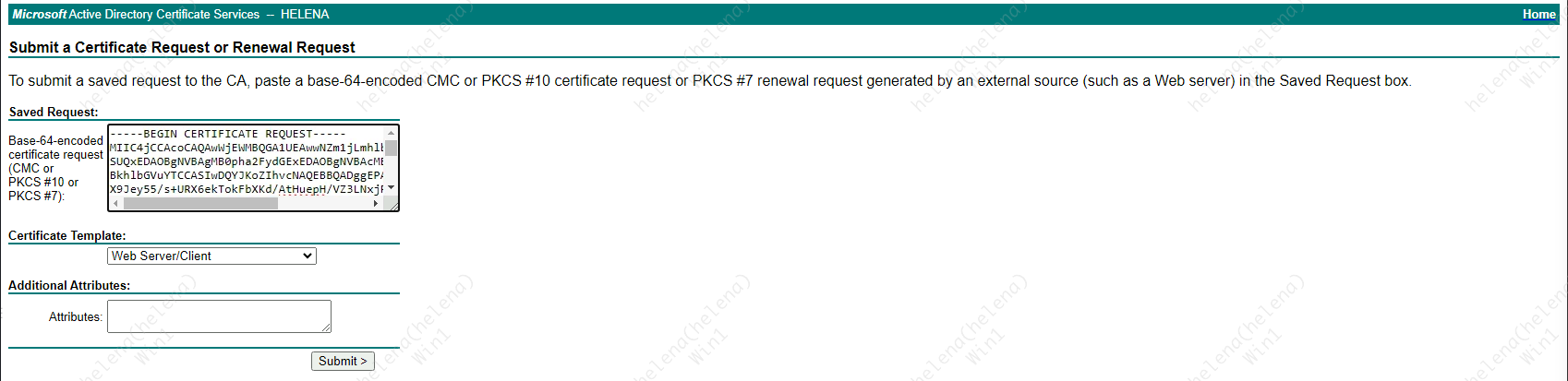
For FMC, we’re also gonna give the same type certificate, first lets create a CSR using Certtools and download the CSR & Private Key
Then sign it on CA Server with Client/Server Authentication Template
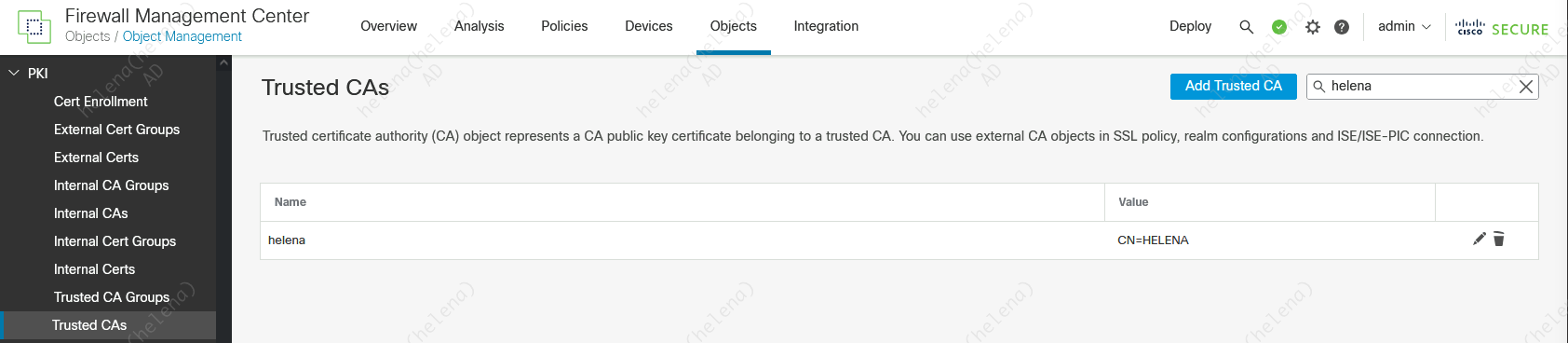
On FMC » Objects » PKI » Trusted CAs, import the Root-CA so we can trus the PxGrid certificate which was issued by thie CA
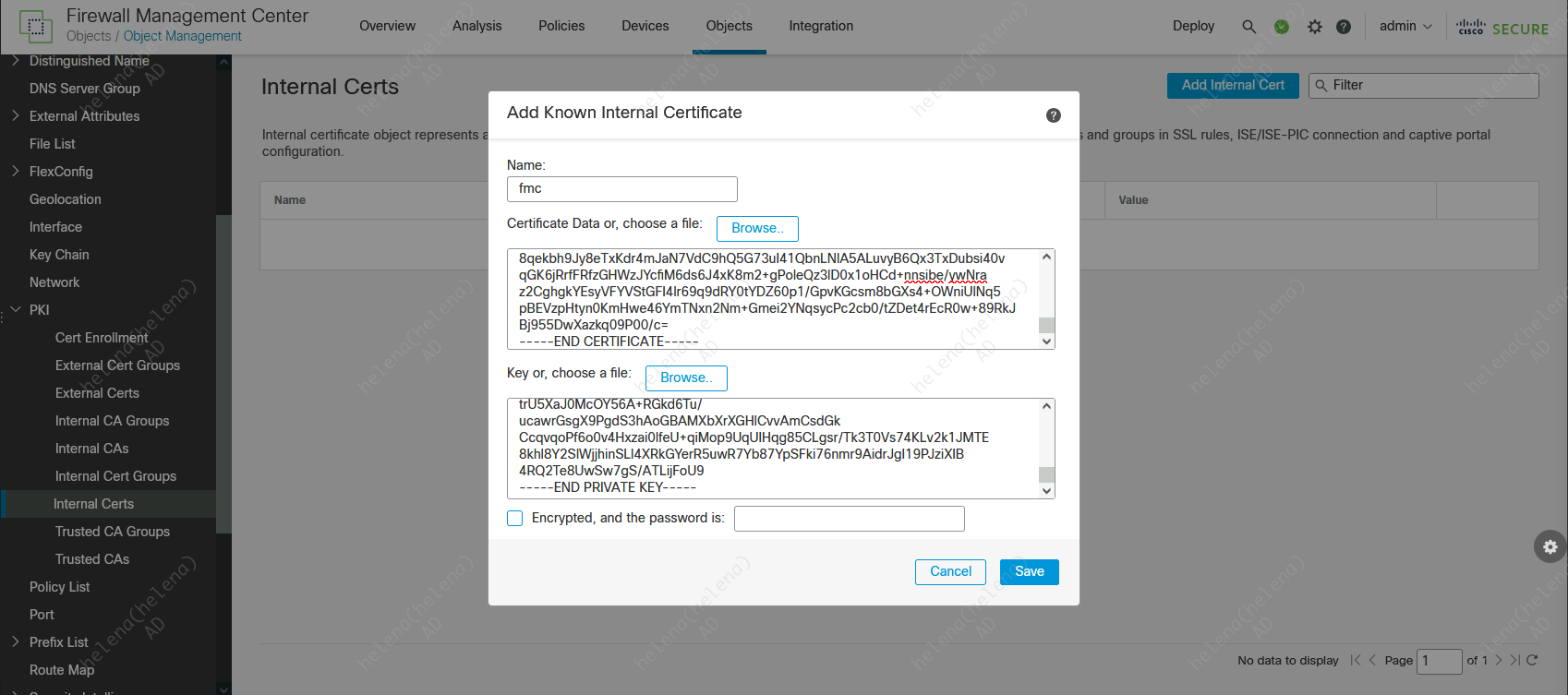
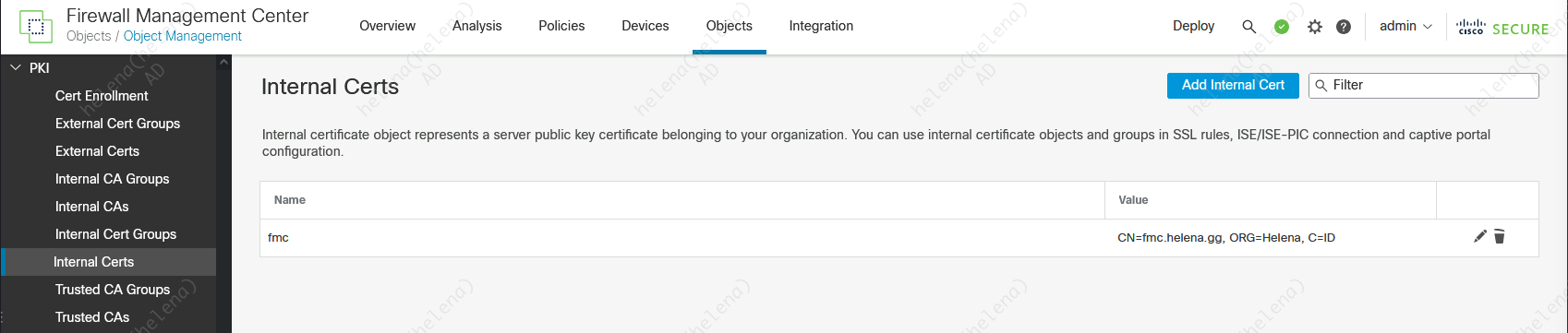
Next on Internal Certs, import the Certificate and Private Key for FMC
PxGrid Integration
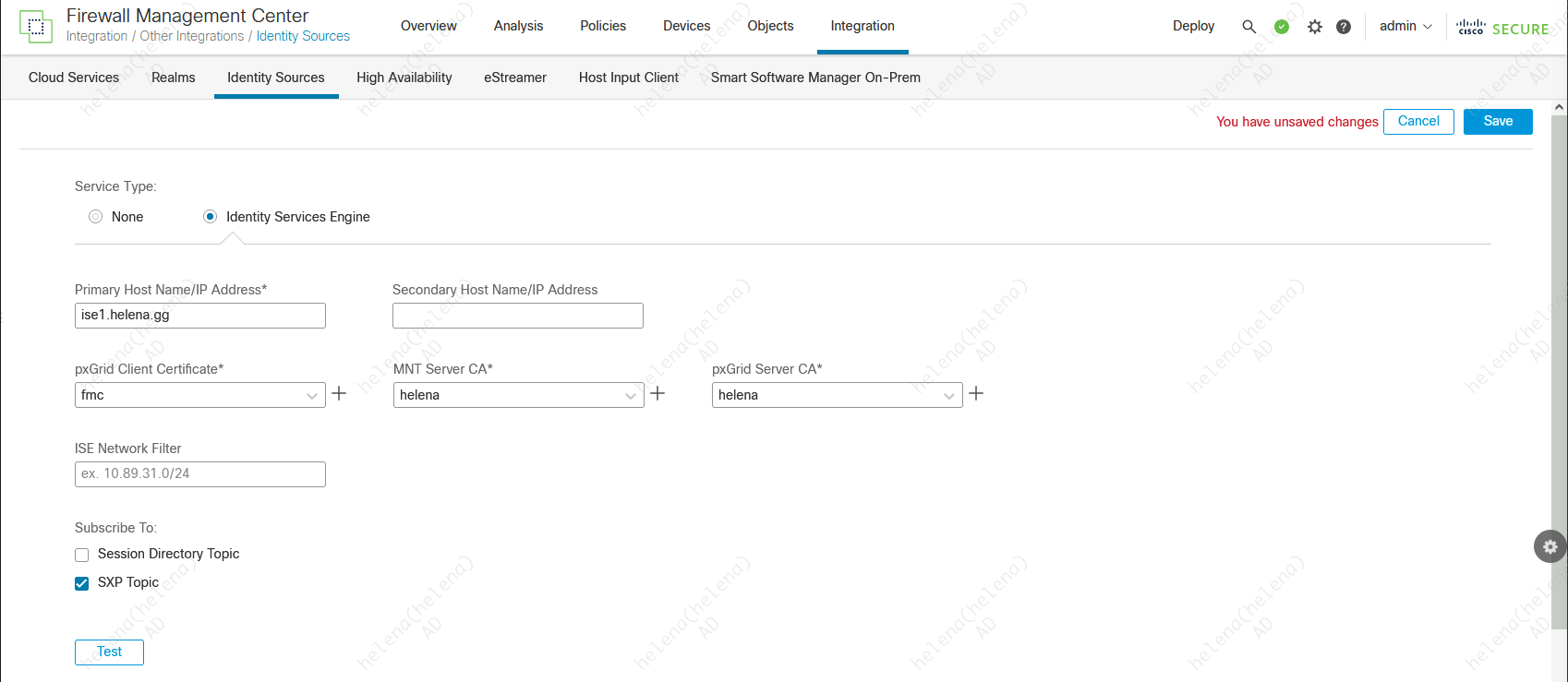
On FMC » Integration » Identitiy Sources, select ISE and fill in the details
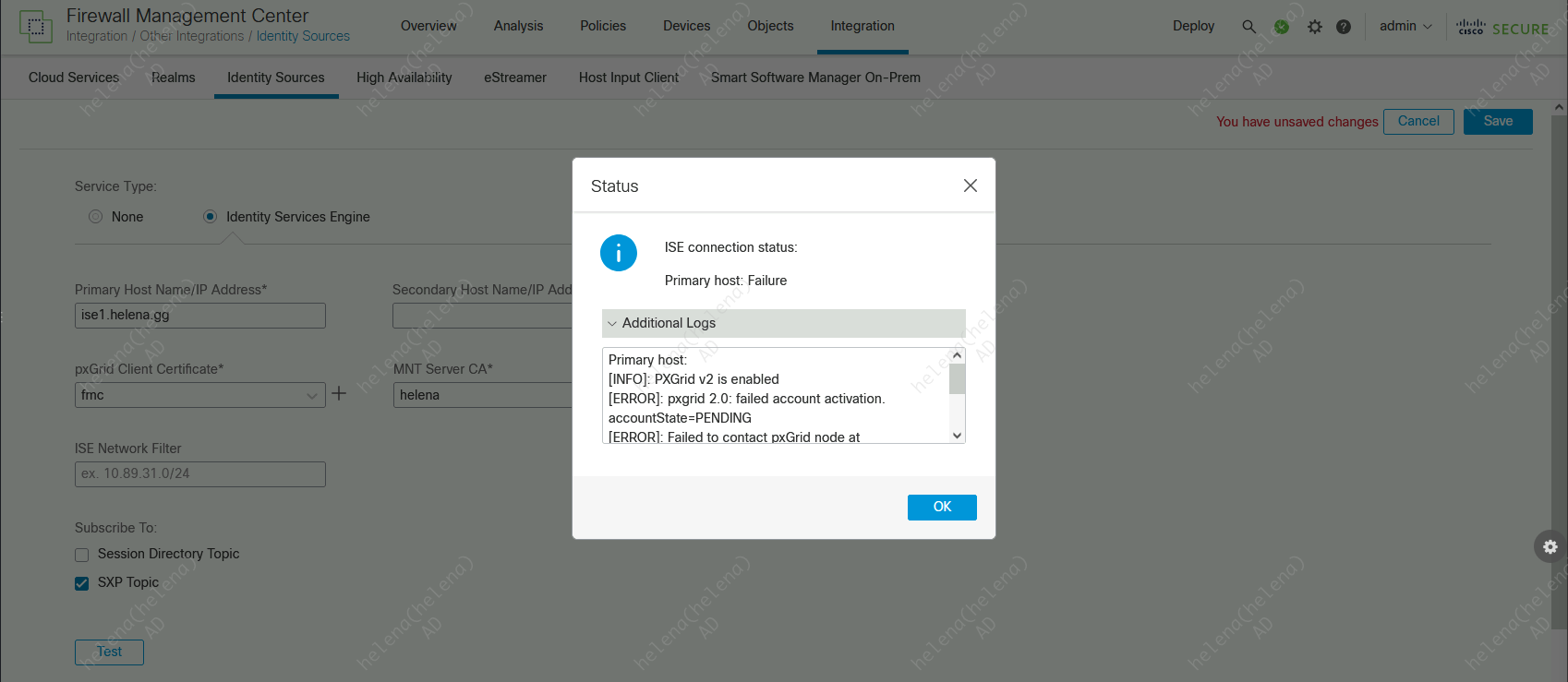
When running the Test, we’ll get an error saying its in pending state
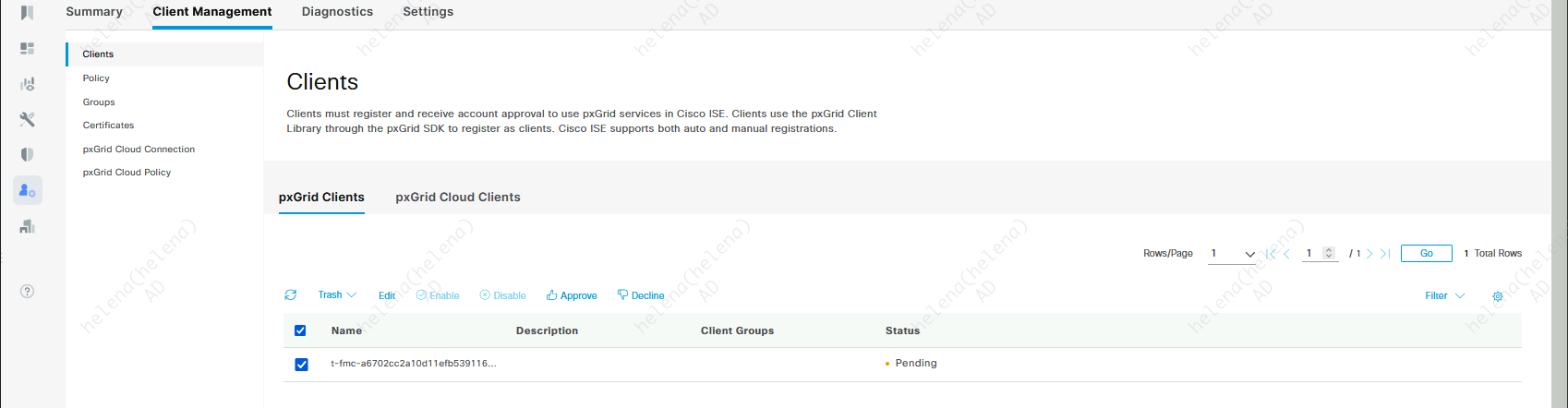
Go to ISE » Administration » Client Management » PxGrid Clients, hit approve on the pending client
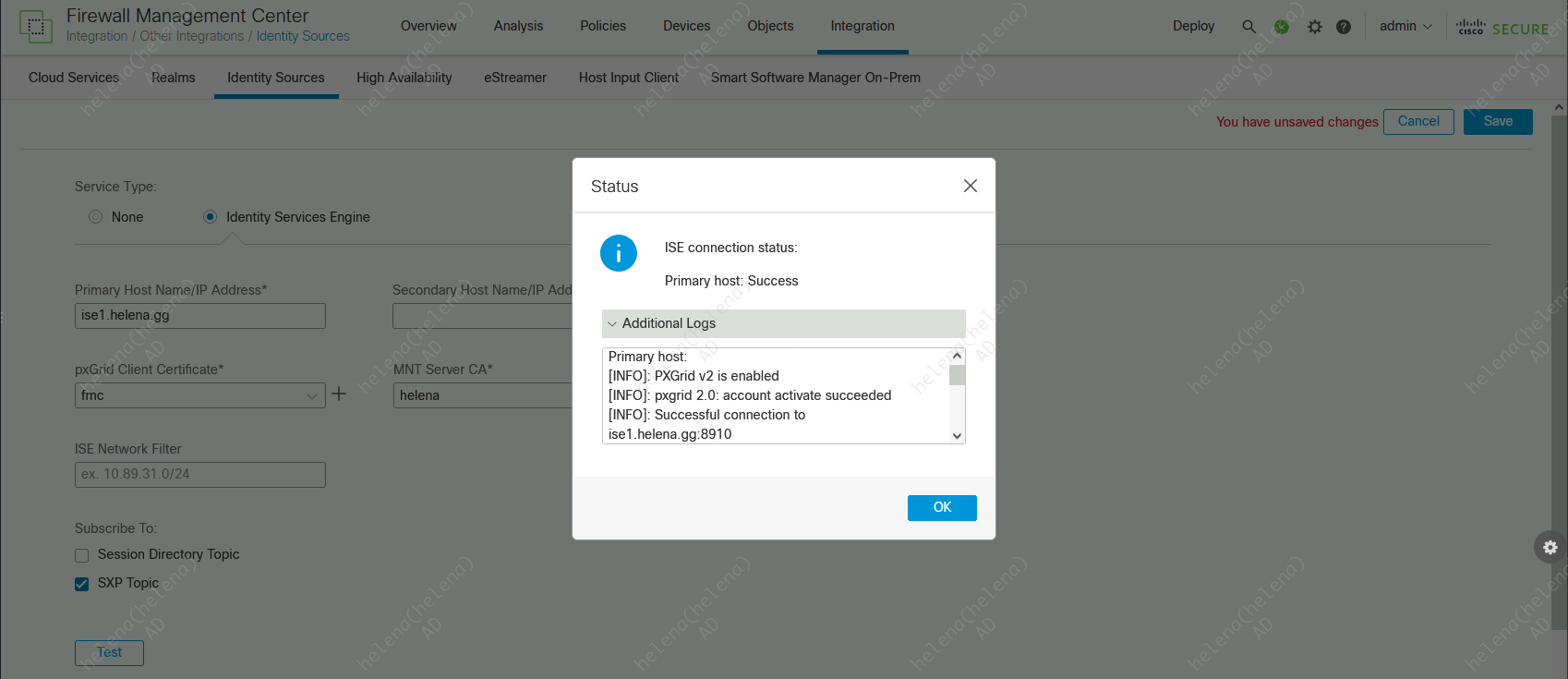
Now bac on FMC, redoing the test will result in a success
Configuring SGT on ACP
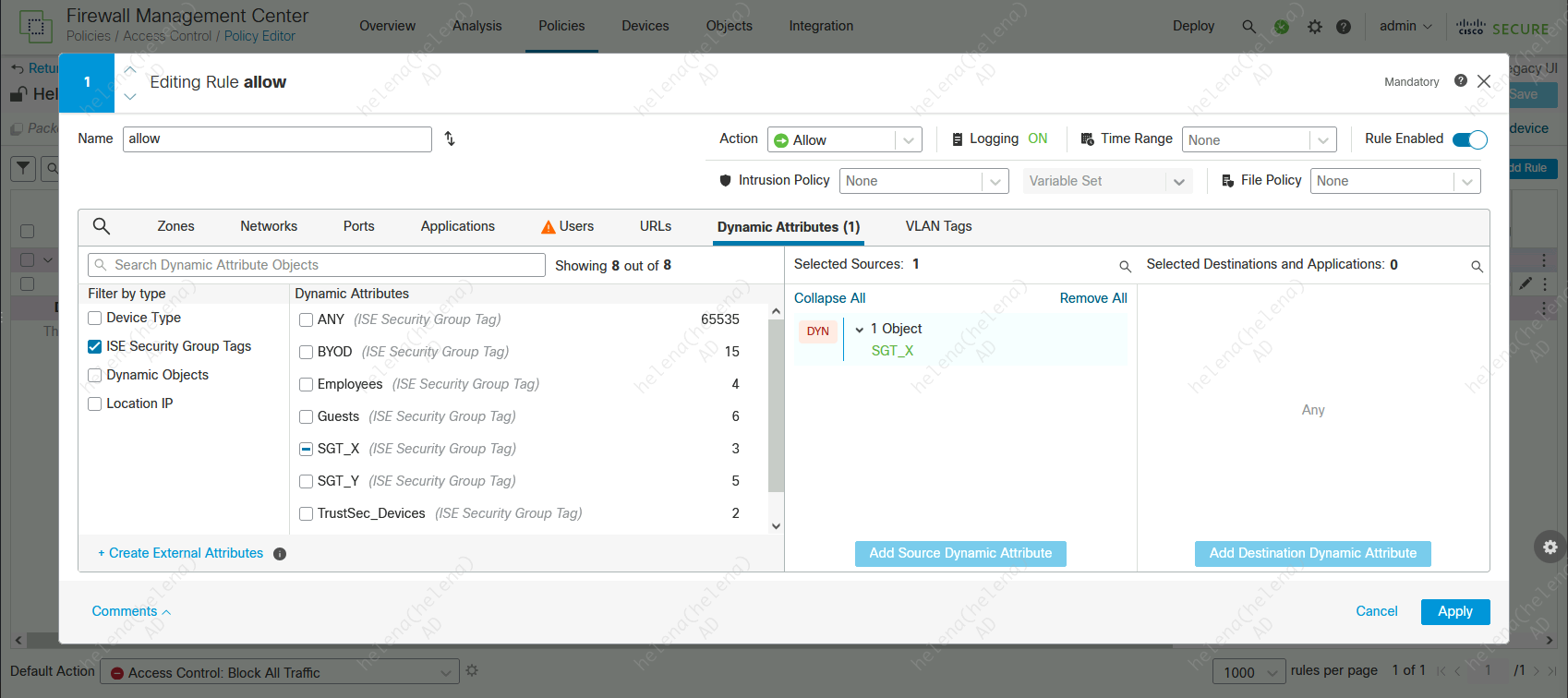
After the integration is complete, we can now use the SGT on the Access Control Policy
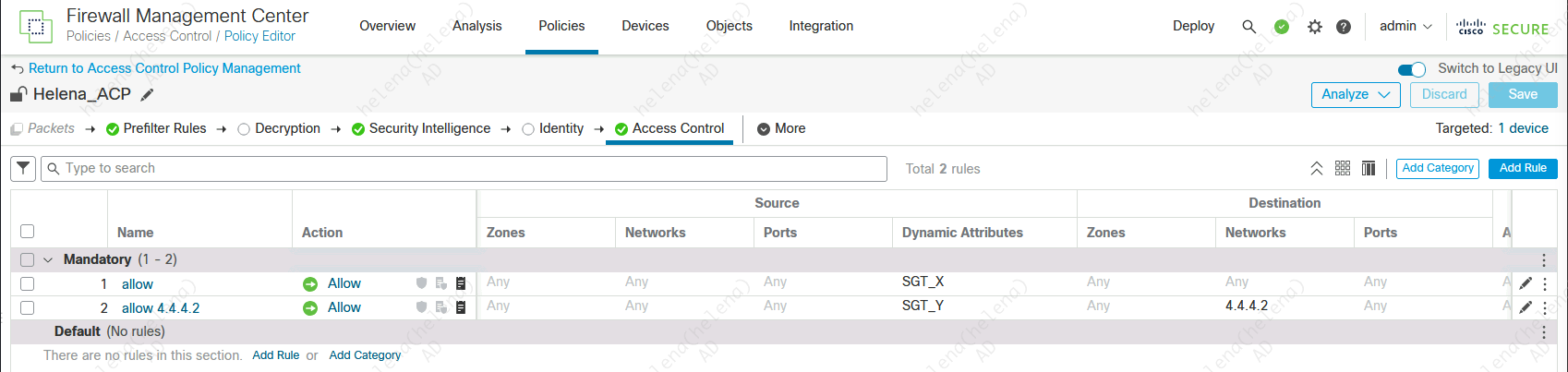
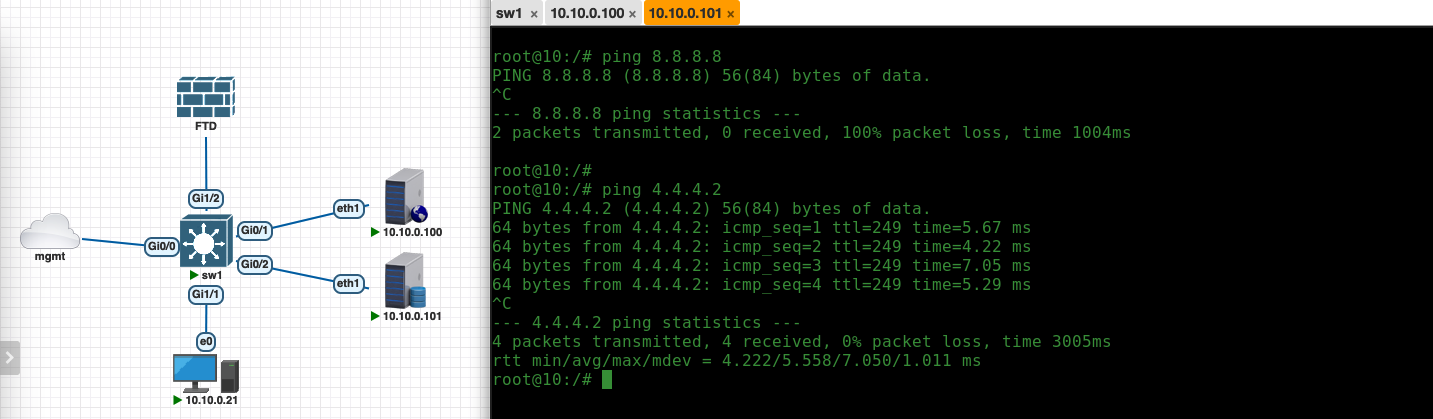
Here we create two rules, SGT_X can access anything on internet while SGT_Y can access 4.4.4.2
Dynamic SGT
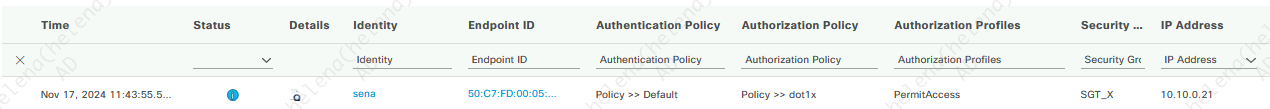
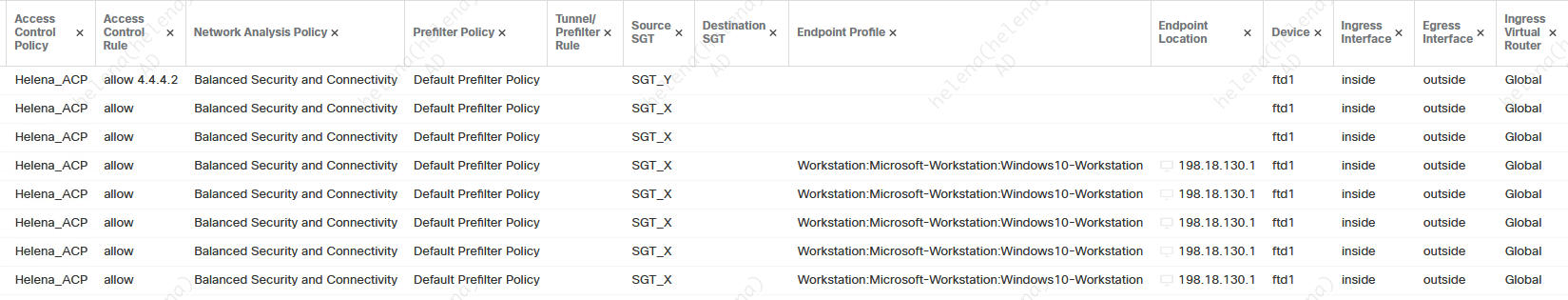
When an endpoint accesses the network, ISE will dynamically assign an SGT based on the Policy Sets rule, in this case the endpoint got SGT_X
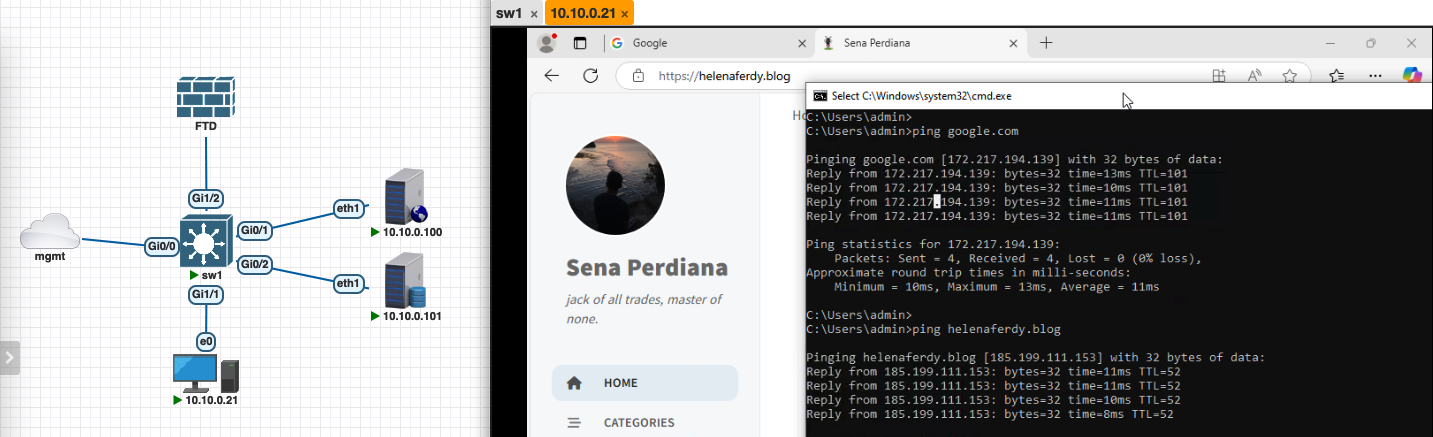
Therefore its allowed to access internet with no restriction
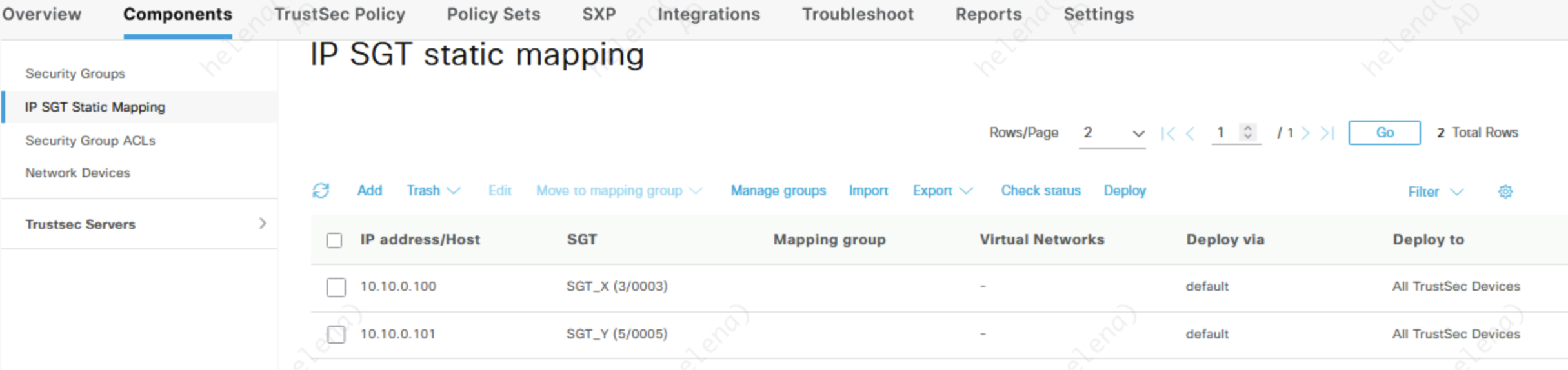
Static SGT
Beside getting SGT mapped from Policy Sets, we can also statically assign an SGT to an IP Address on ISE
Here the endpoint with SGT_Y can only access 4.4.4.2
And here’s the connection events on FMC