Nessus
Tenable Nessus is a vulnerability assessment tool that scans IT systems to identify security weaknesses, misconfigurations, and compliance issues. It helps organizations proactively manage and mitigate risks by providing detailed reports and remediation guidance.
Nessus Installation
Download the Nessus Installer on its official website and choose the appropirate operating system, then run the installer.
After that, Nessus should be accessible on port 8834
Start the trial registration if you dont have the license
After that we can now create the administrator user account to access Nessus
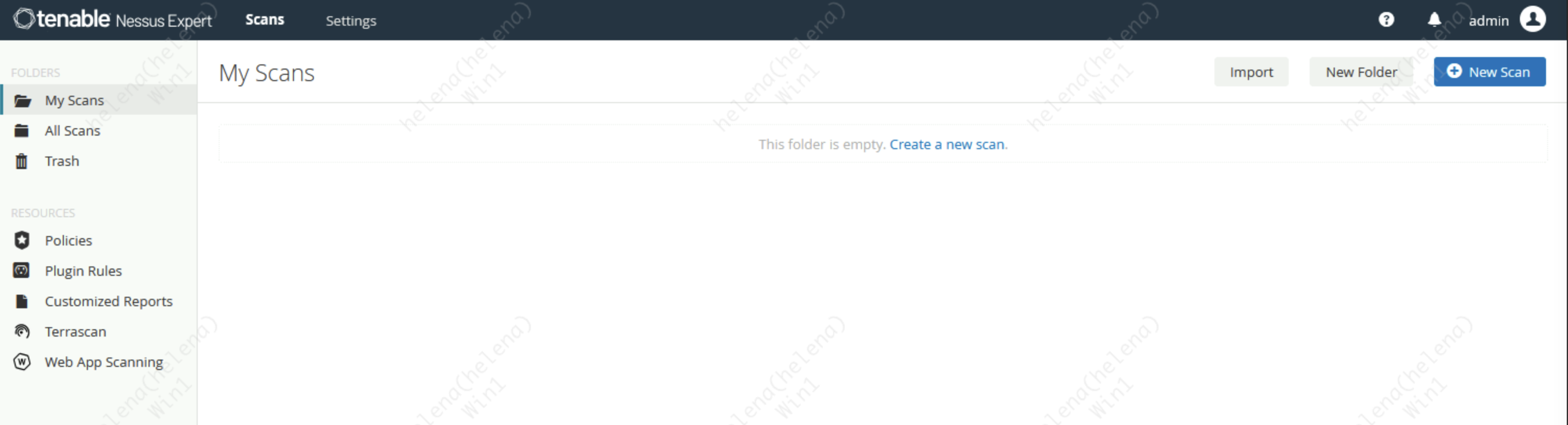
And now Nessus is up and running
Host Discovery
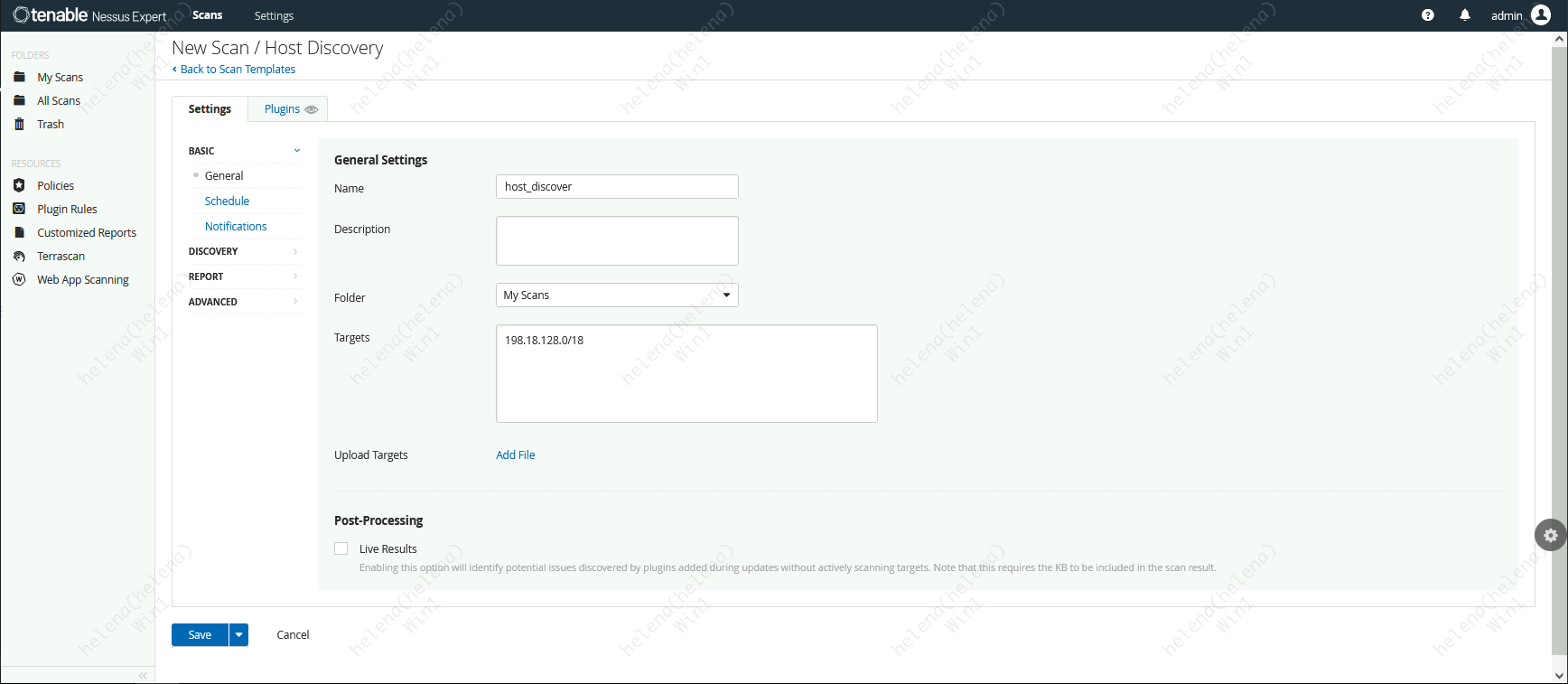
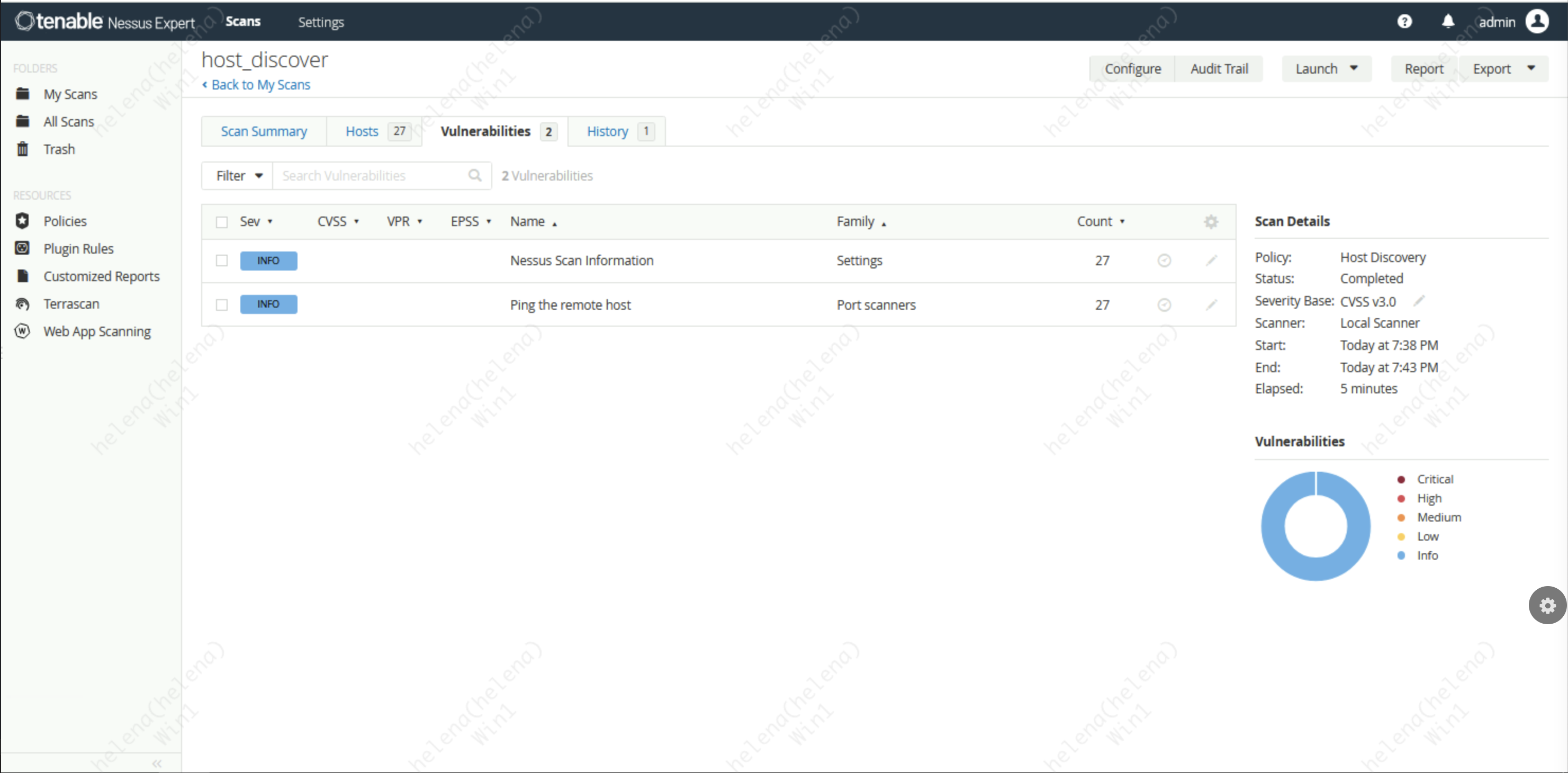
On Scanner list, lets try running the Host Discovery
We’ll call it “host_discover” and set it to scan the 198.18.128.0/18 network
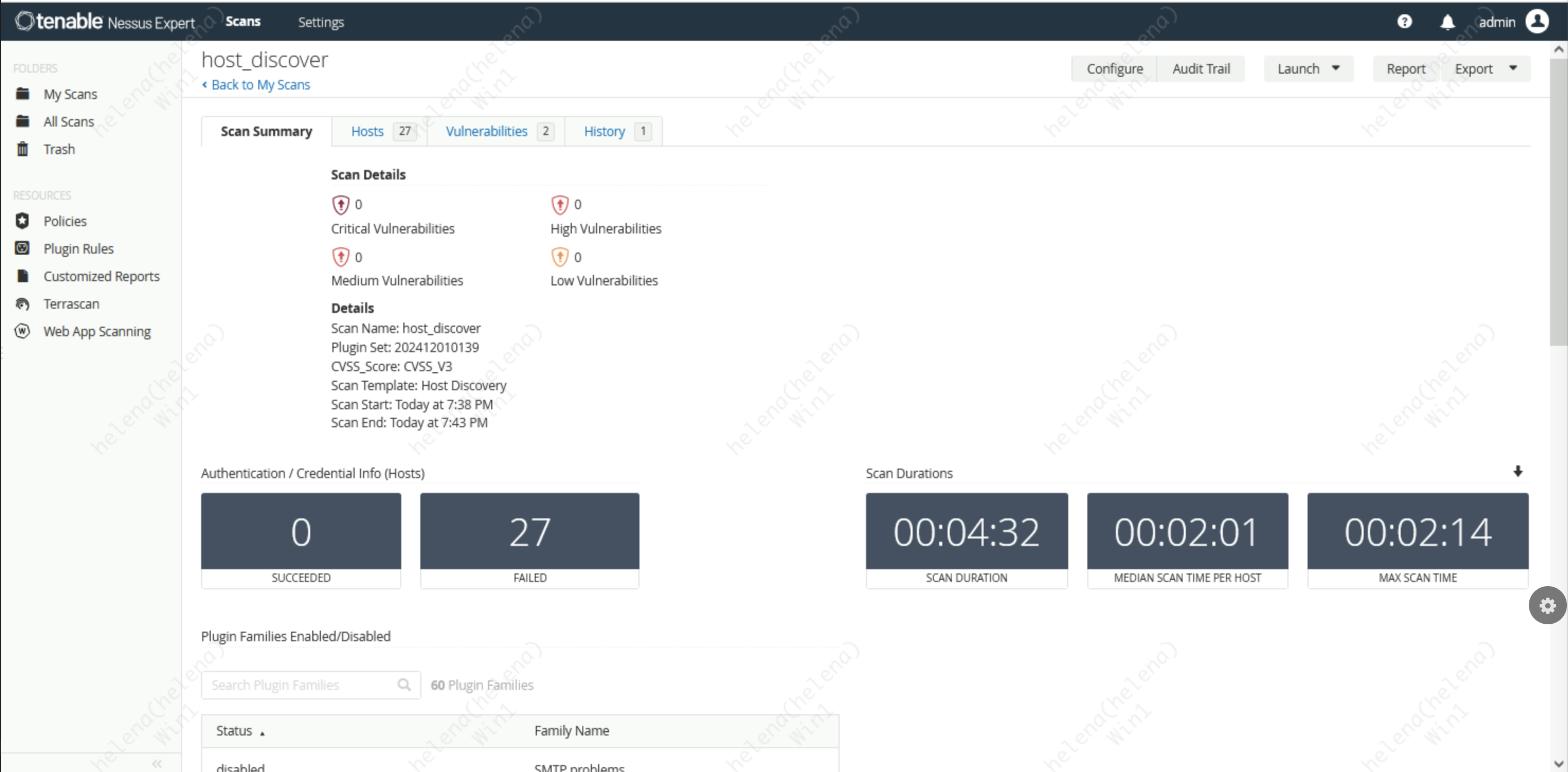
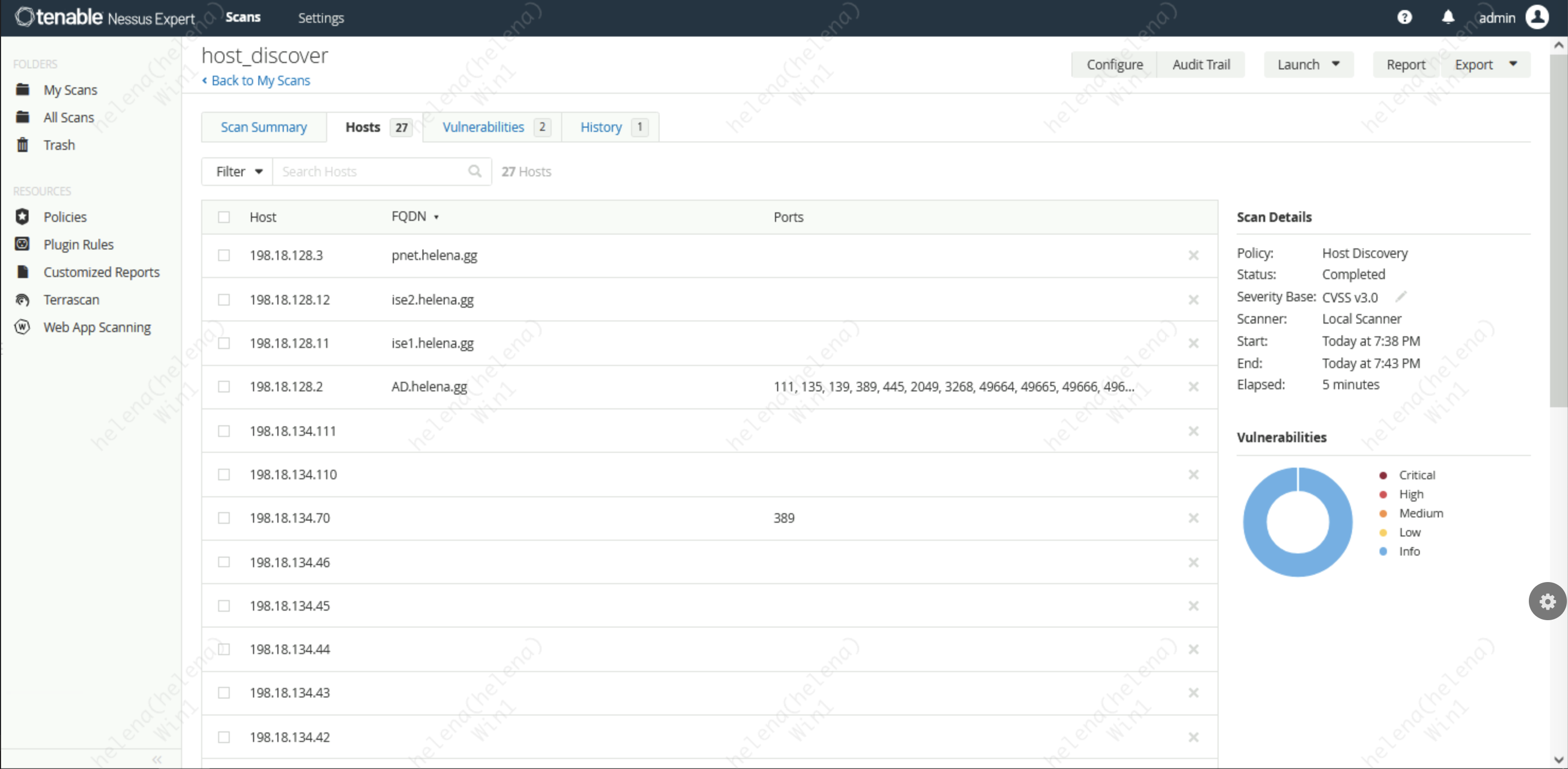
After around 4 minutes of scanning, it has found 27 hosts in my private network
It also runs a simple vulnerability assessment towards the discovered hosts
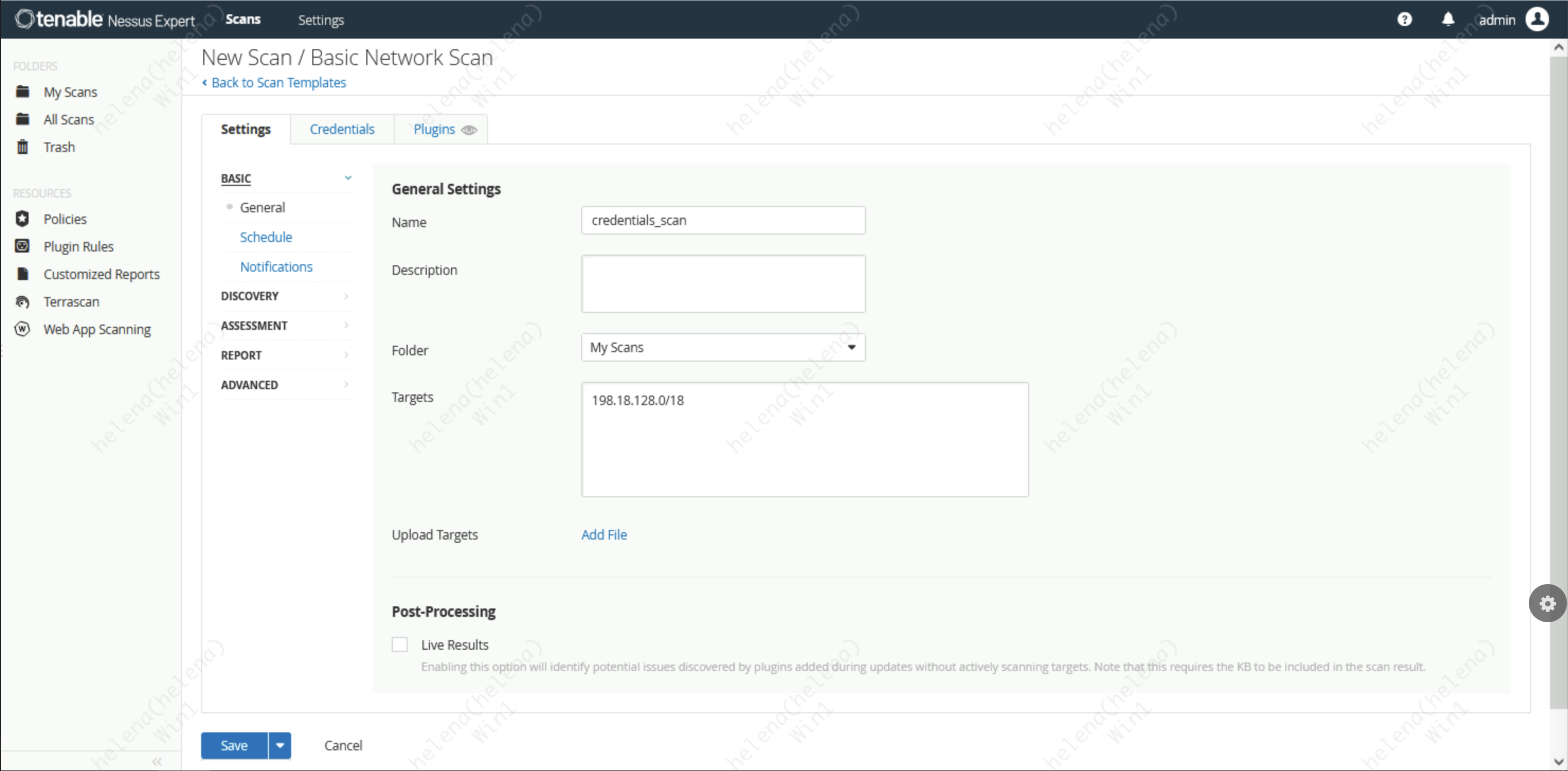
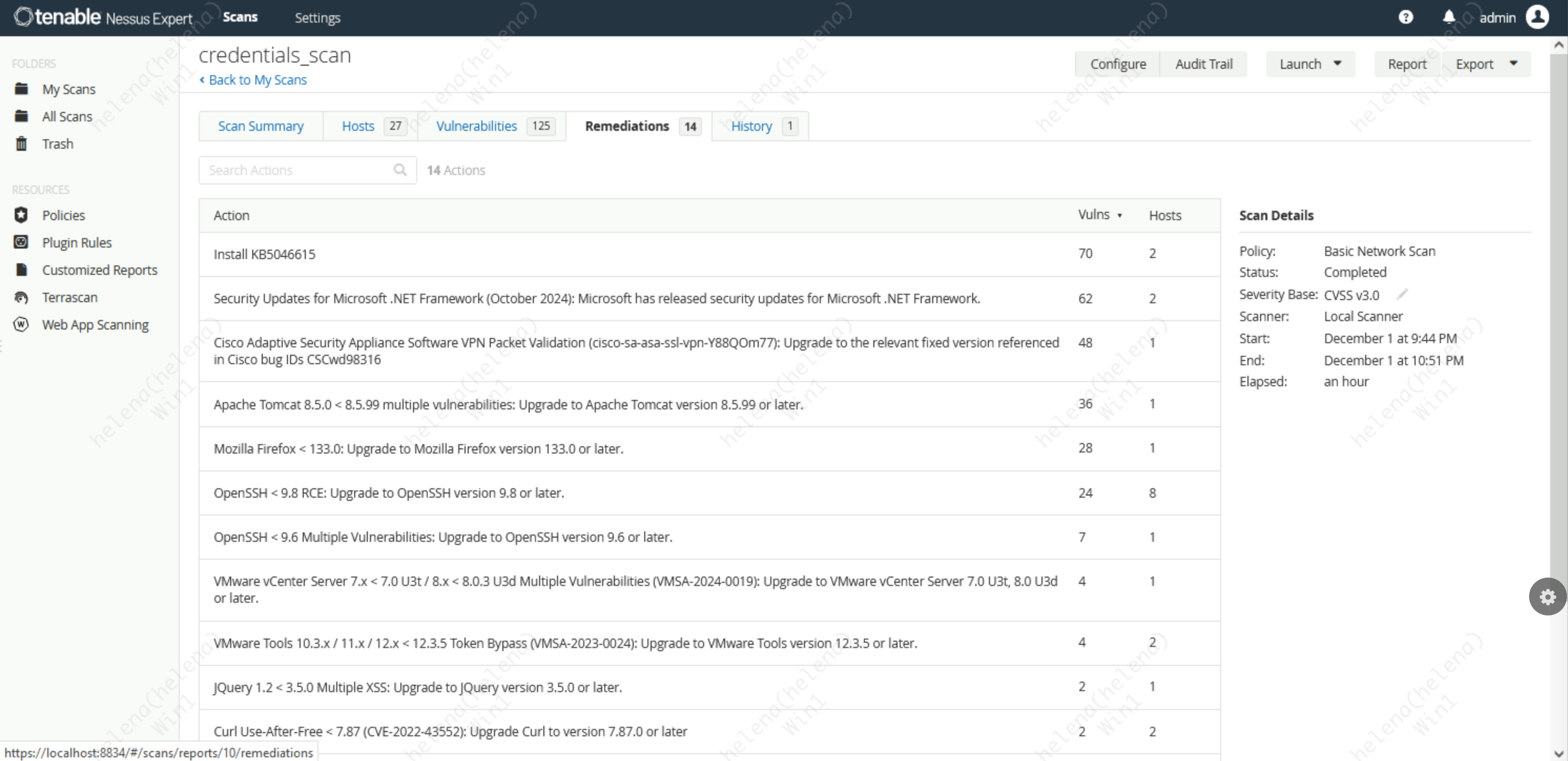
Credentials Scan
Now lets try a more advanced scan under “Basic Network Scan”, here we’ll once again scan the 198.18.128.0/18 network
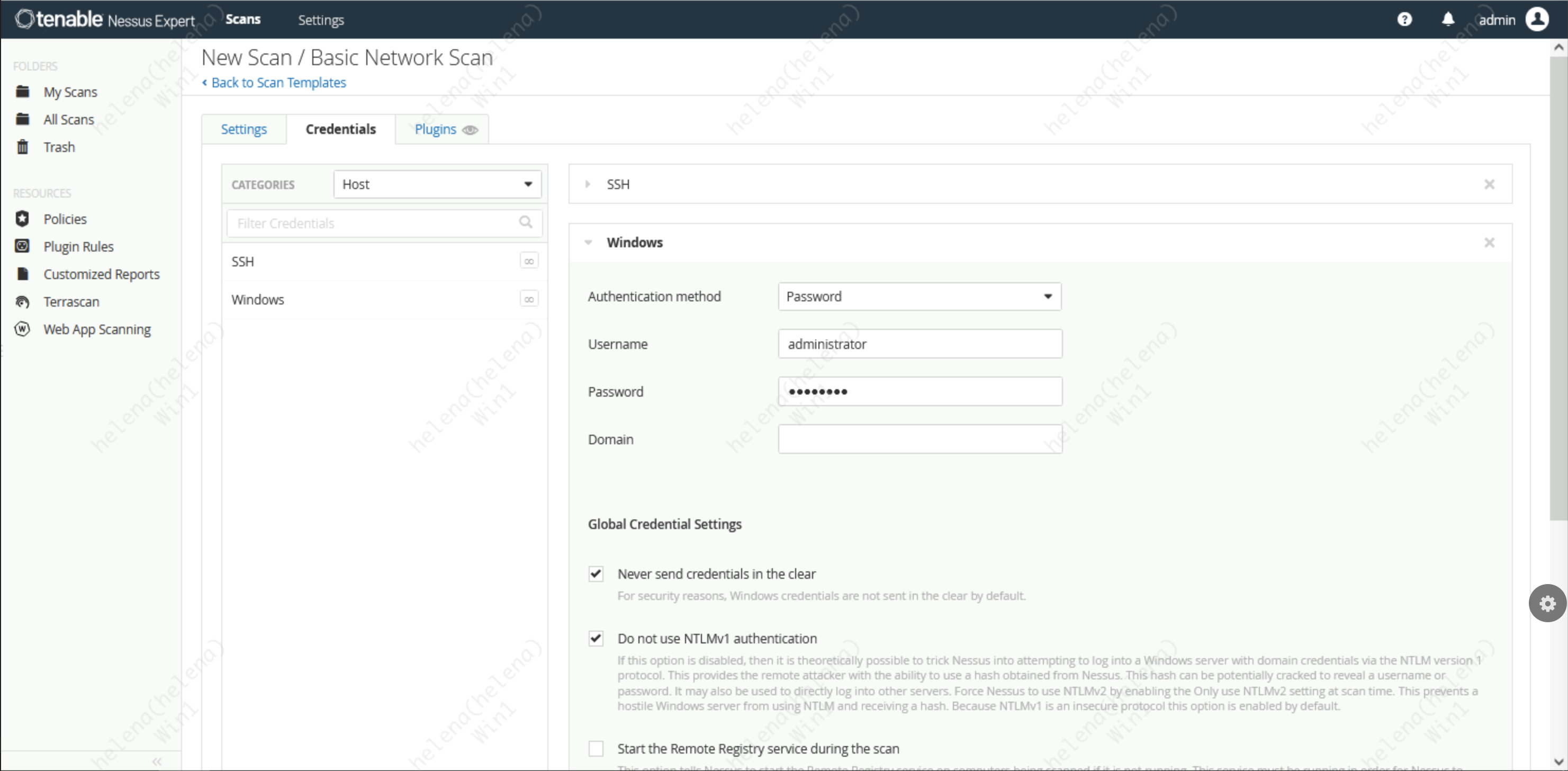
But the difference is now we’ll provide the credentials for Nessus to be able to login to the discovered hosts, here we give it credentials for SSH and RDP
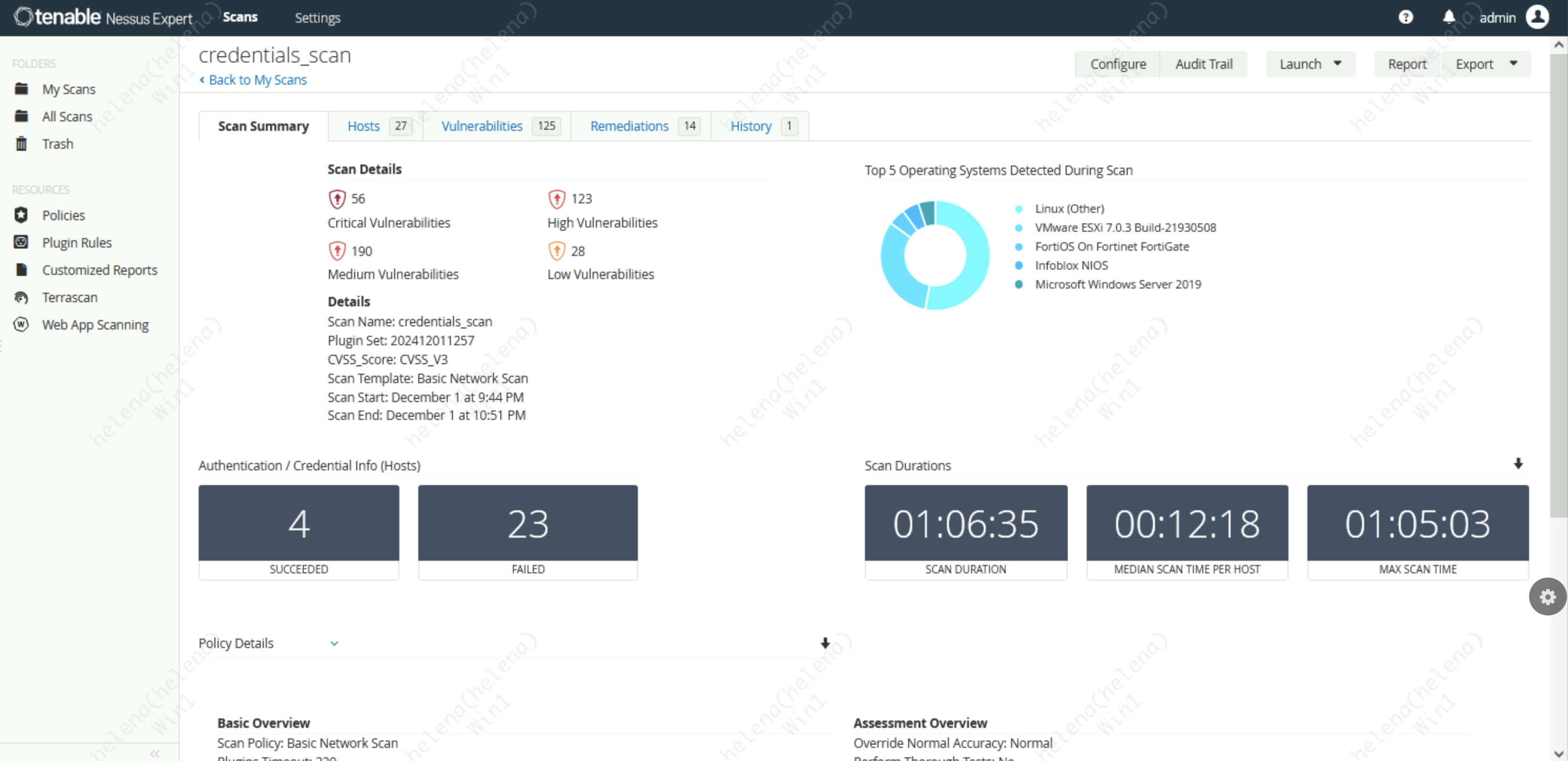
And after running for over an hour, Nessus has successfully logged in to 4 hosts and ran a lot of vulnerability assessments
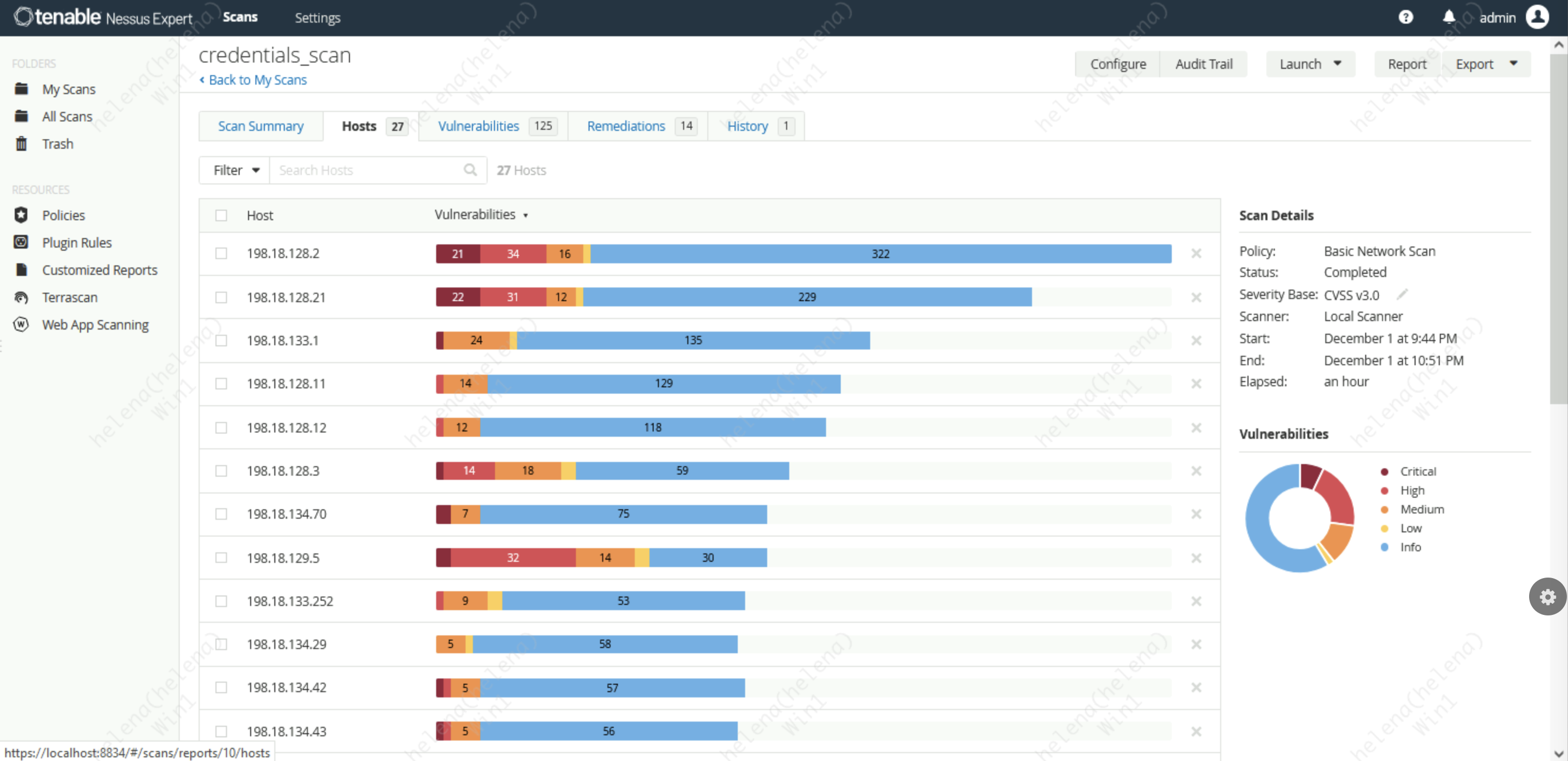
Here we can see the VA results per scanned host
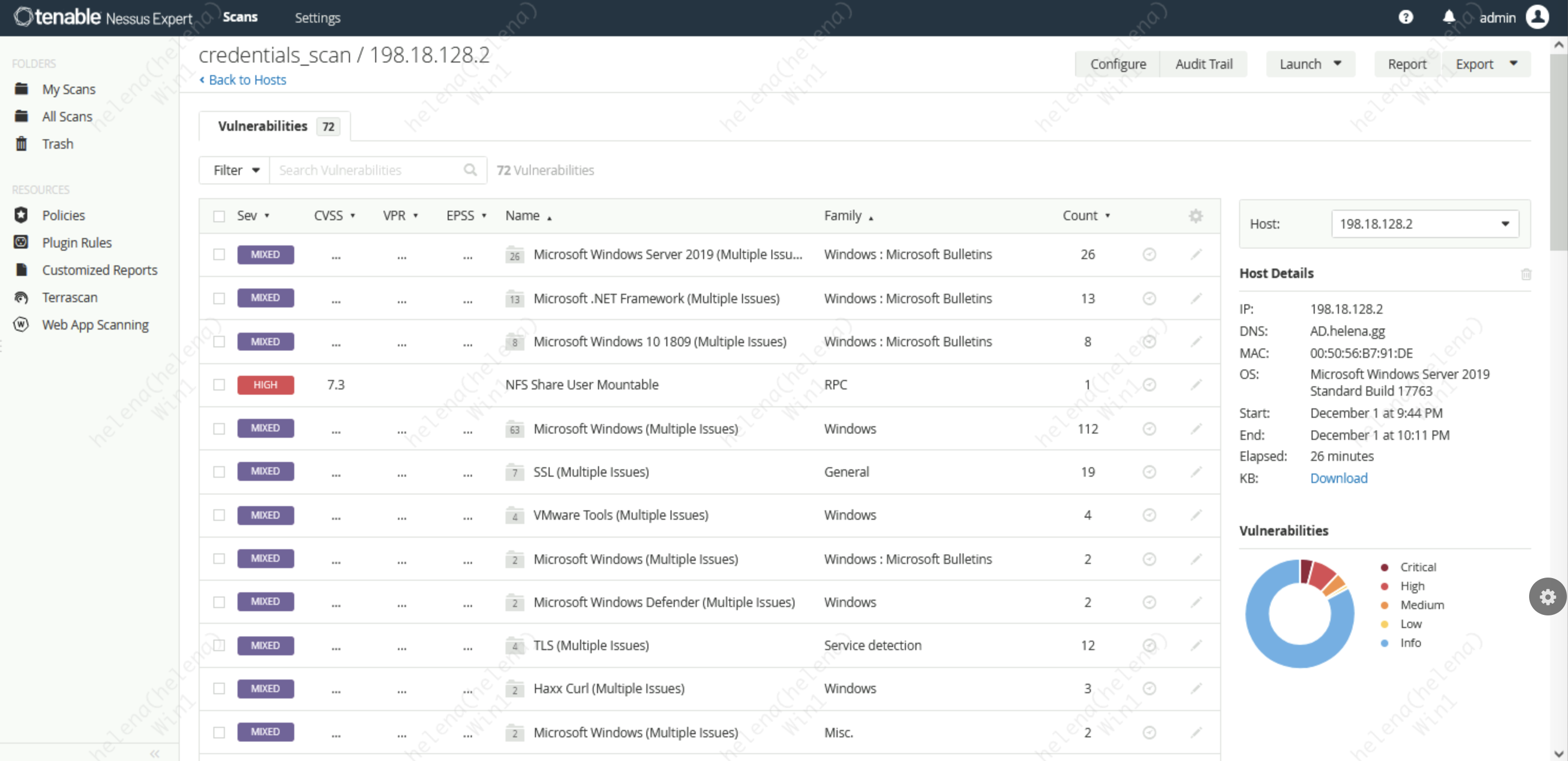
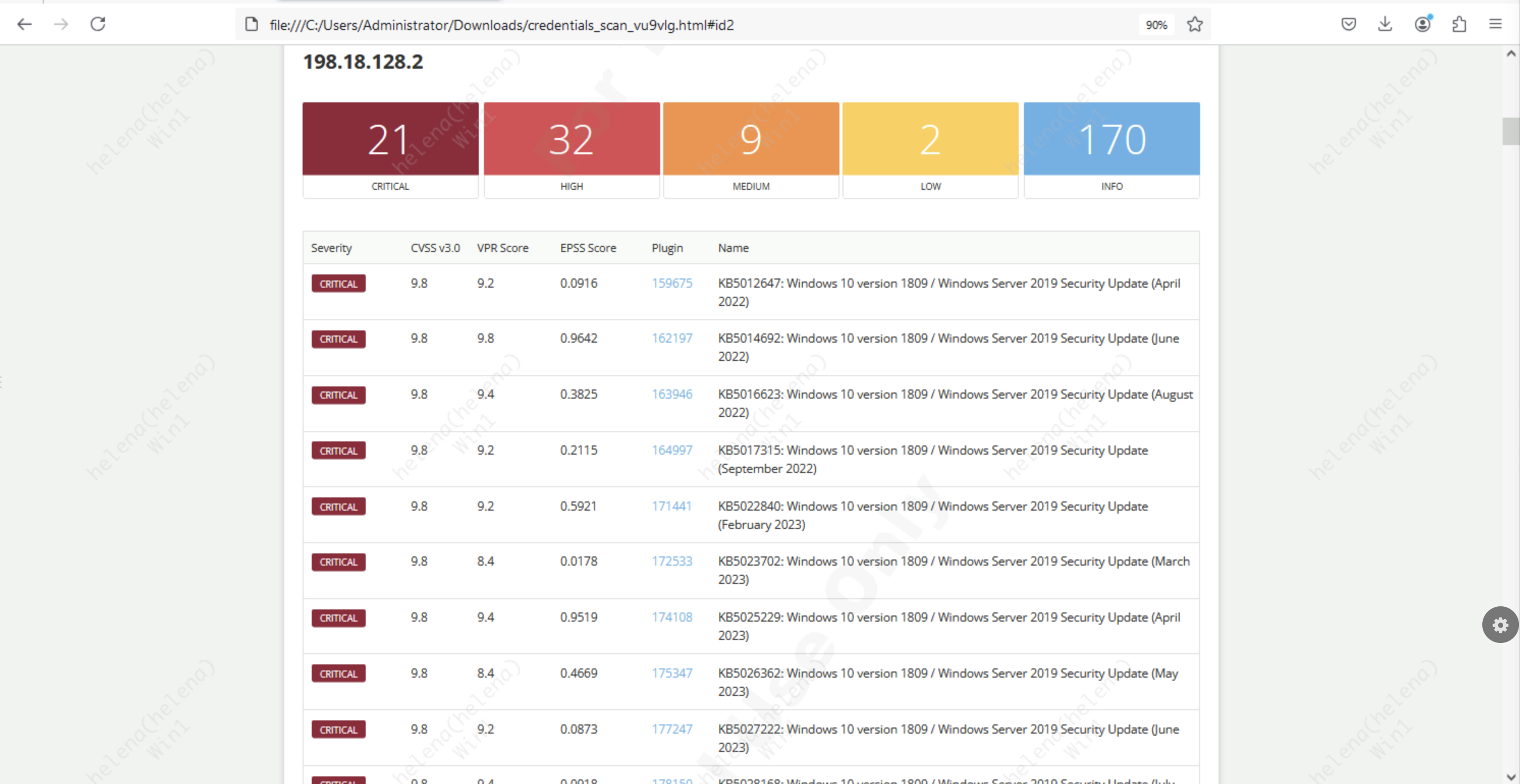
Here’s the detailed VA result of the 198.18.128.2 host, which is my domain controller in this network
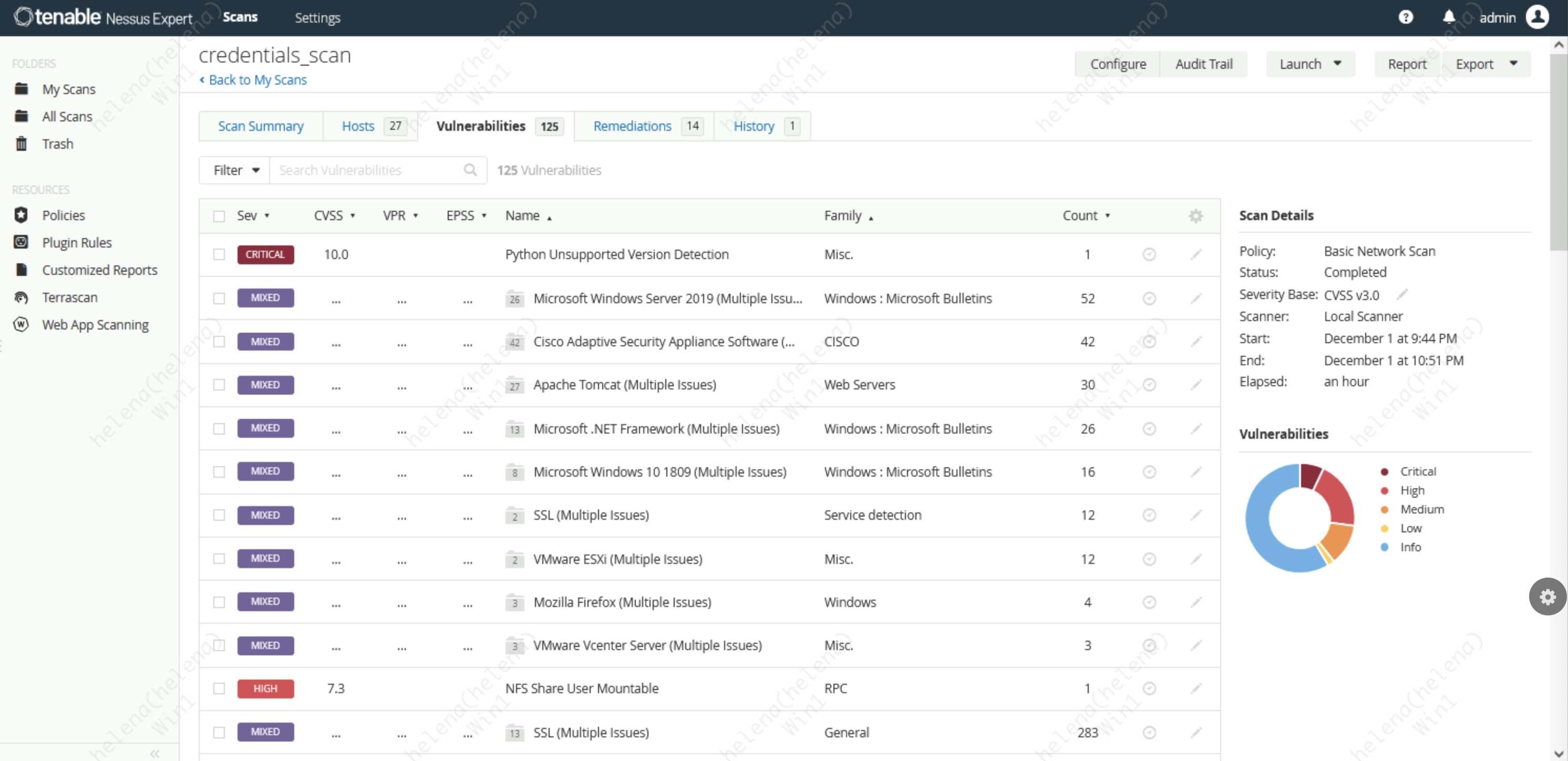
We can also sort the results by the VA scans
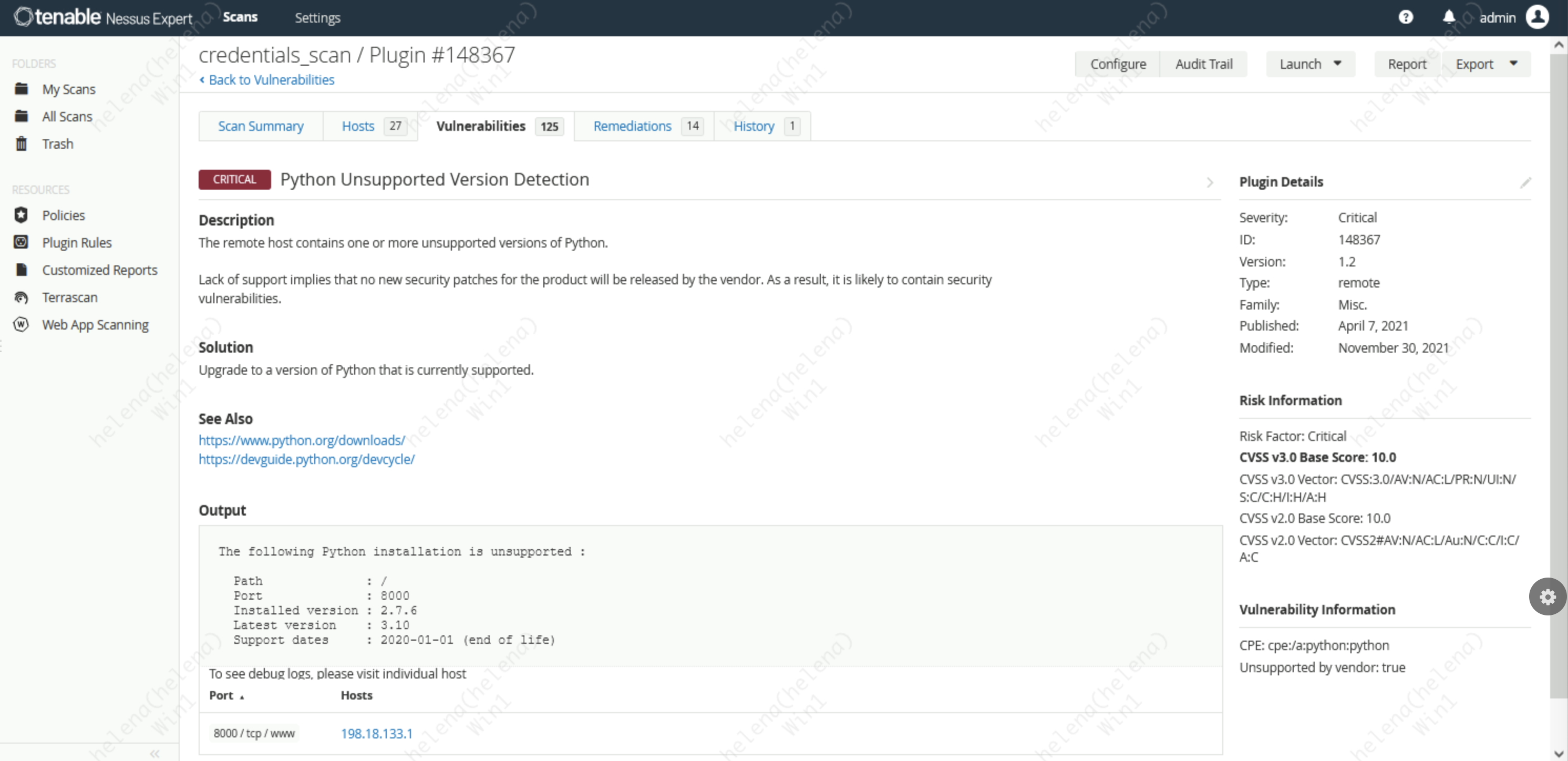
And taking a closer look to the found vulnerability
On top of that, Nessus also gives us a remediation recommendation for the vulnerabilities found
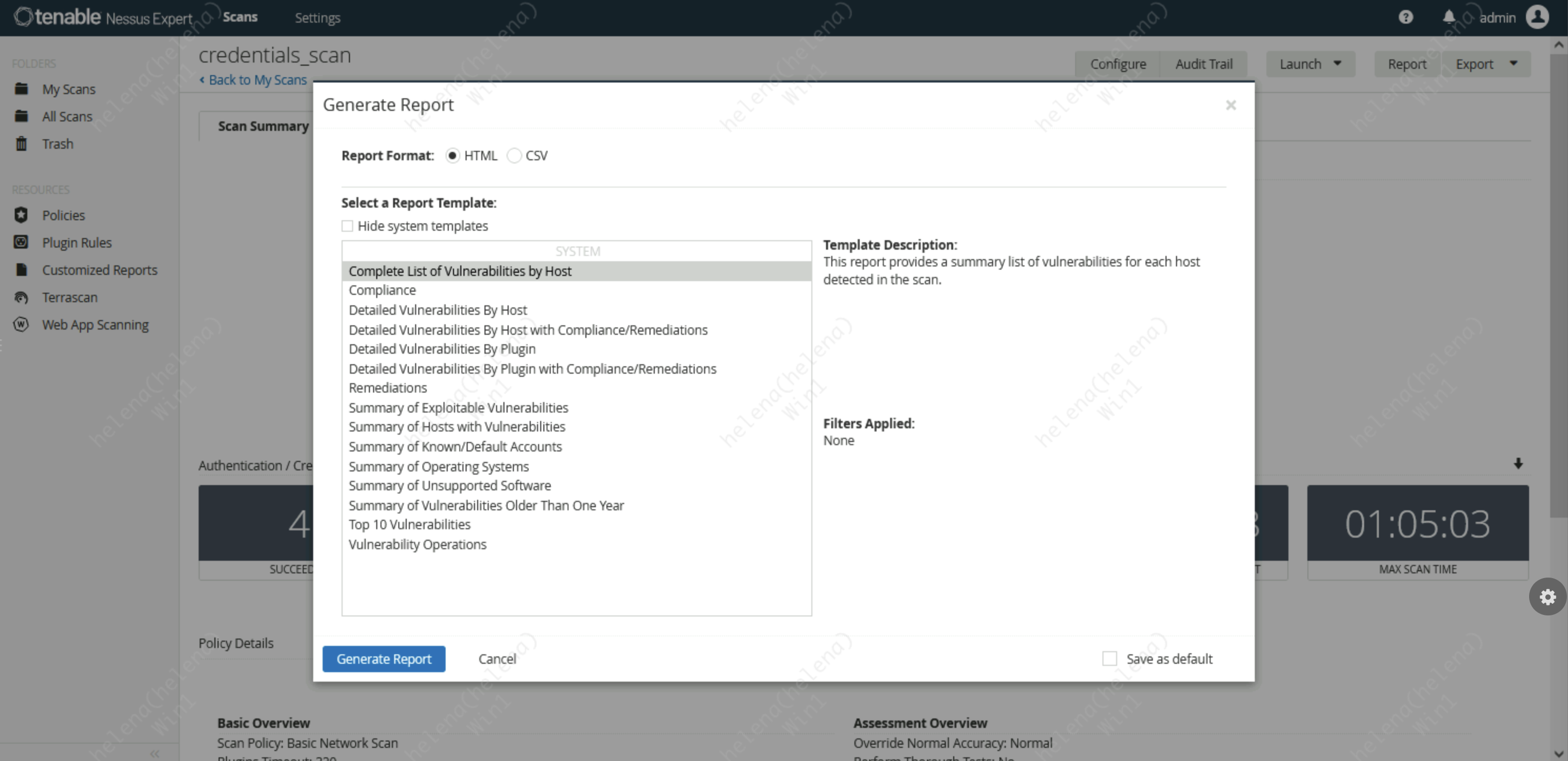
Exporting Scan
The scan that was run on Nessus can easily be exported to be used as a VA report