Cisco Duo with Palo Alto VPN
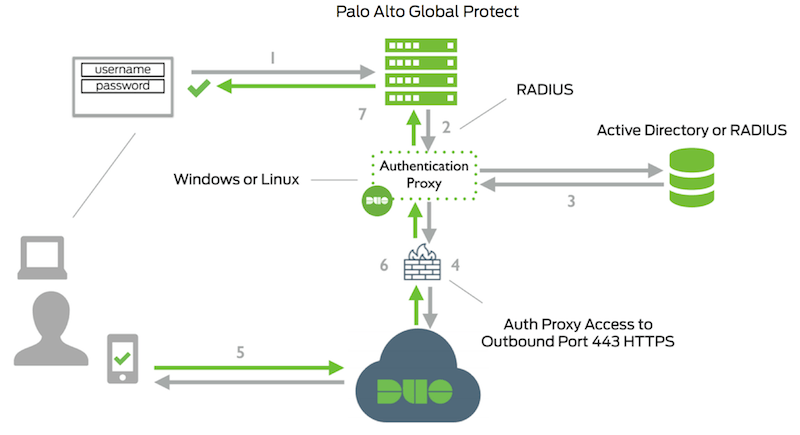
Palo Alto GlobalProtect VPN with Cisco Duo MFA adds a second layer of security to remote access. Users first authenticate with their corporate credentials through GlobalProtect, then Duo provides multi-factor authentication before granting VPN access, ensuring only verified users can connect securely.
Enabling Duo MFA
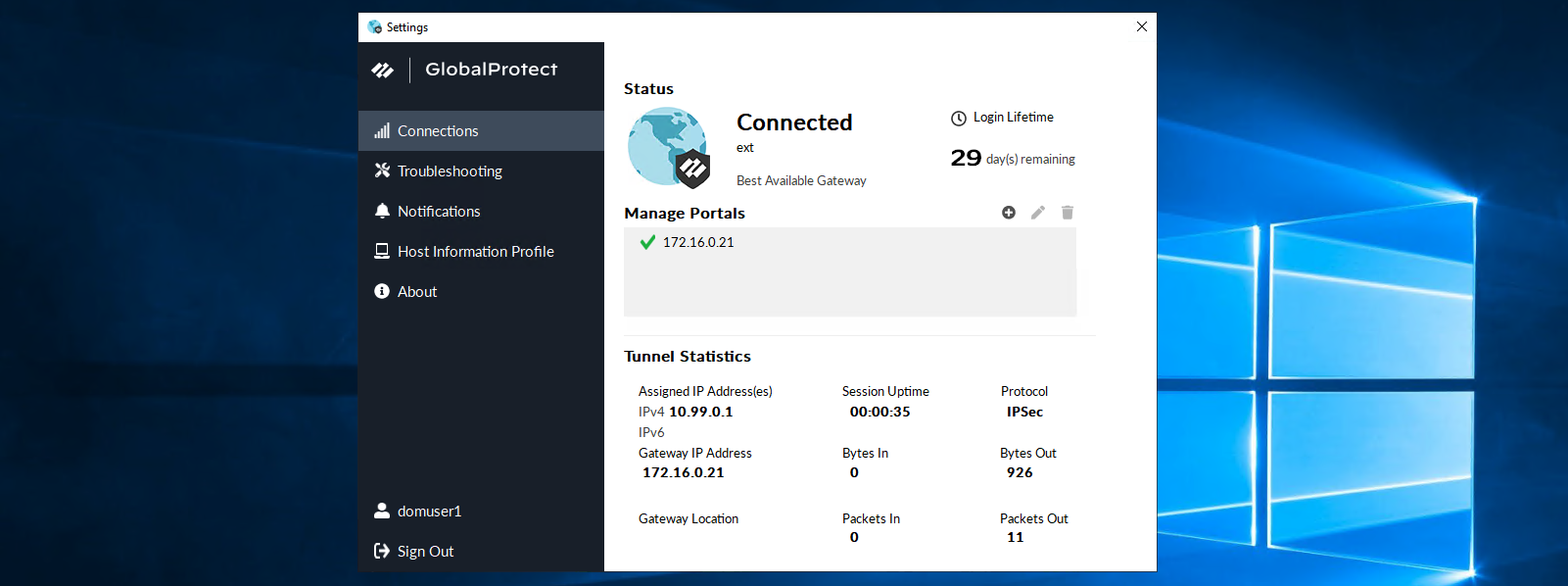
Here we have a working Global Protect SSL VPN using local users to log in
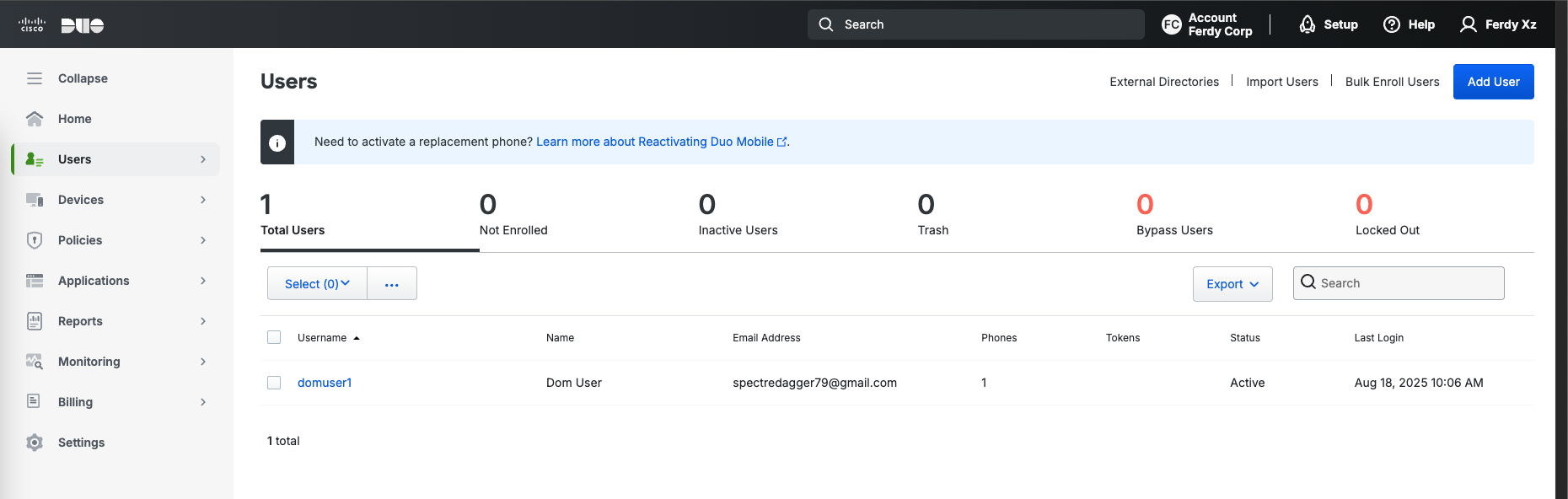
To enable Duo, we’ll pretty much follow a similar implementation as this one, first we make sure the user is present on Duo with same username as the one on AD
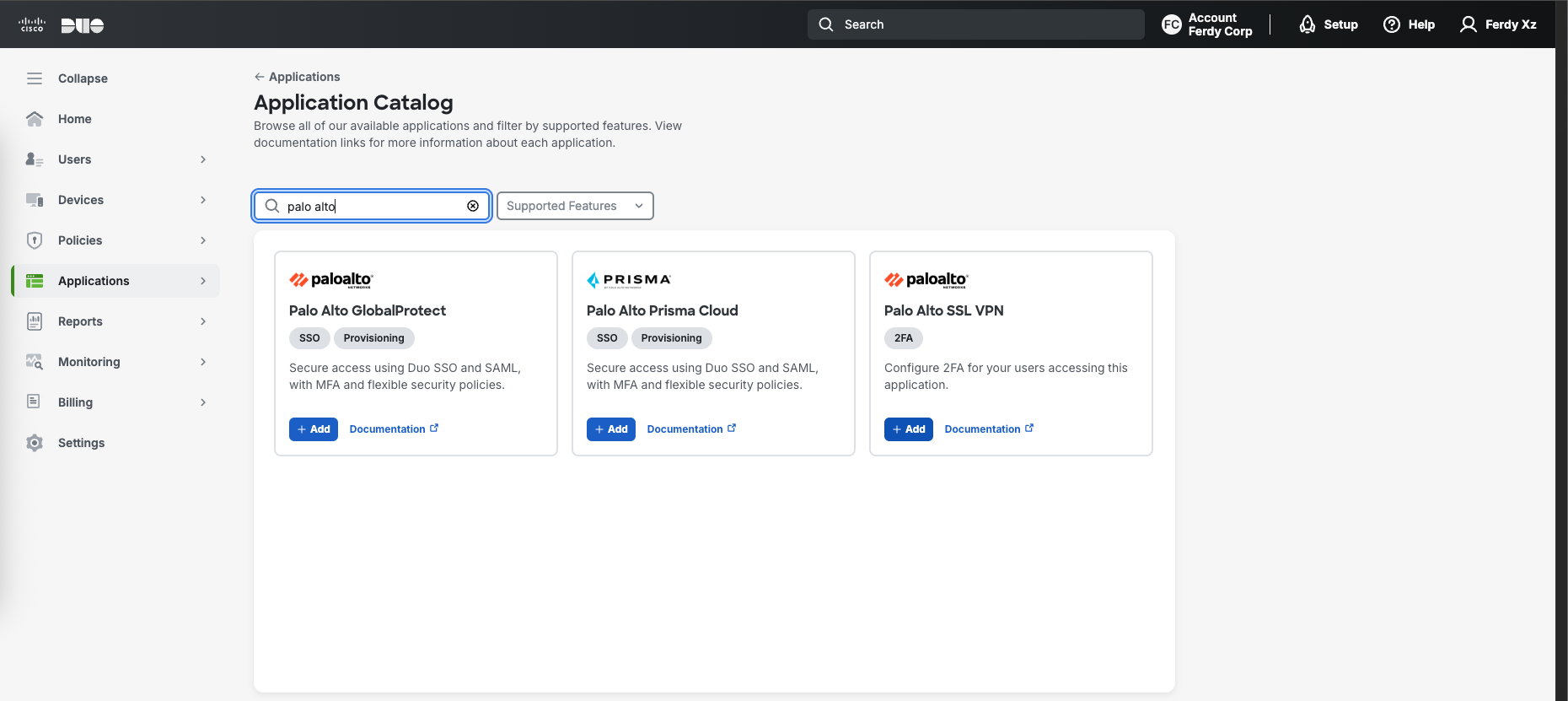
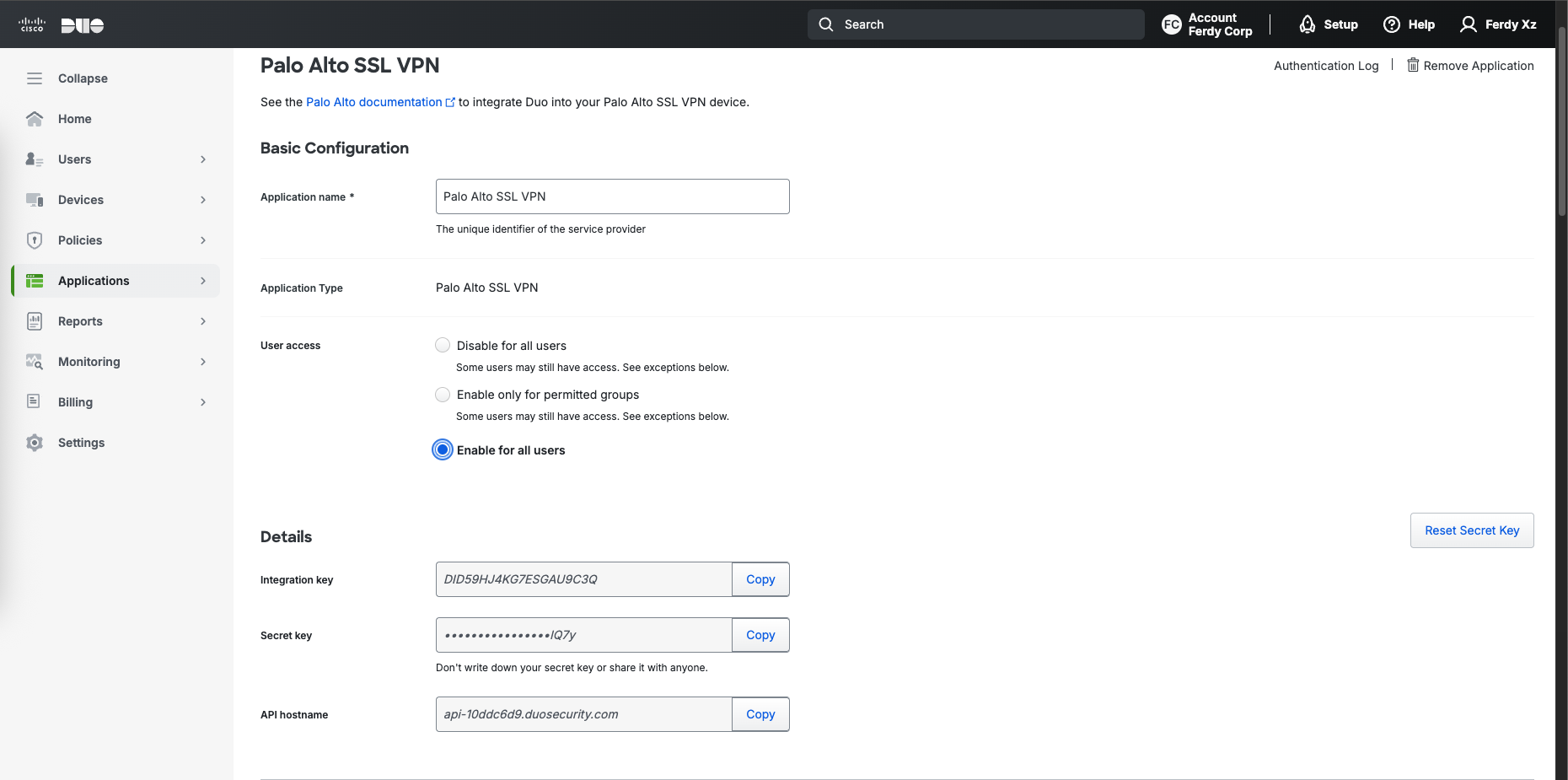
Then we add a Protected Application, Duo already provides a template for Palo Alto SSL VPN so lets use that
Copy all the necessary credentials
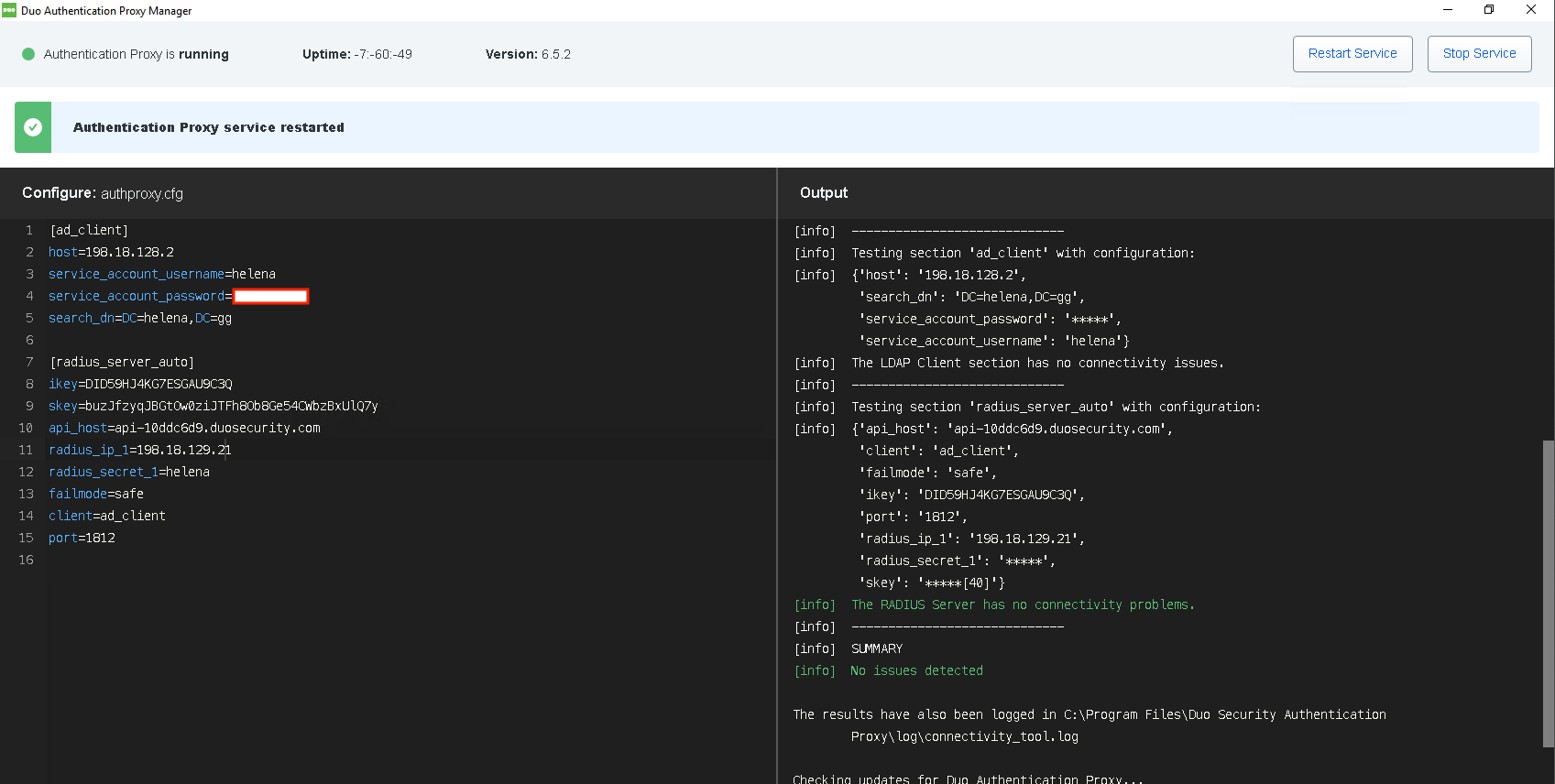
And configure it on the Duo Proxy Server
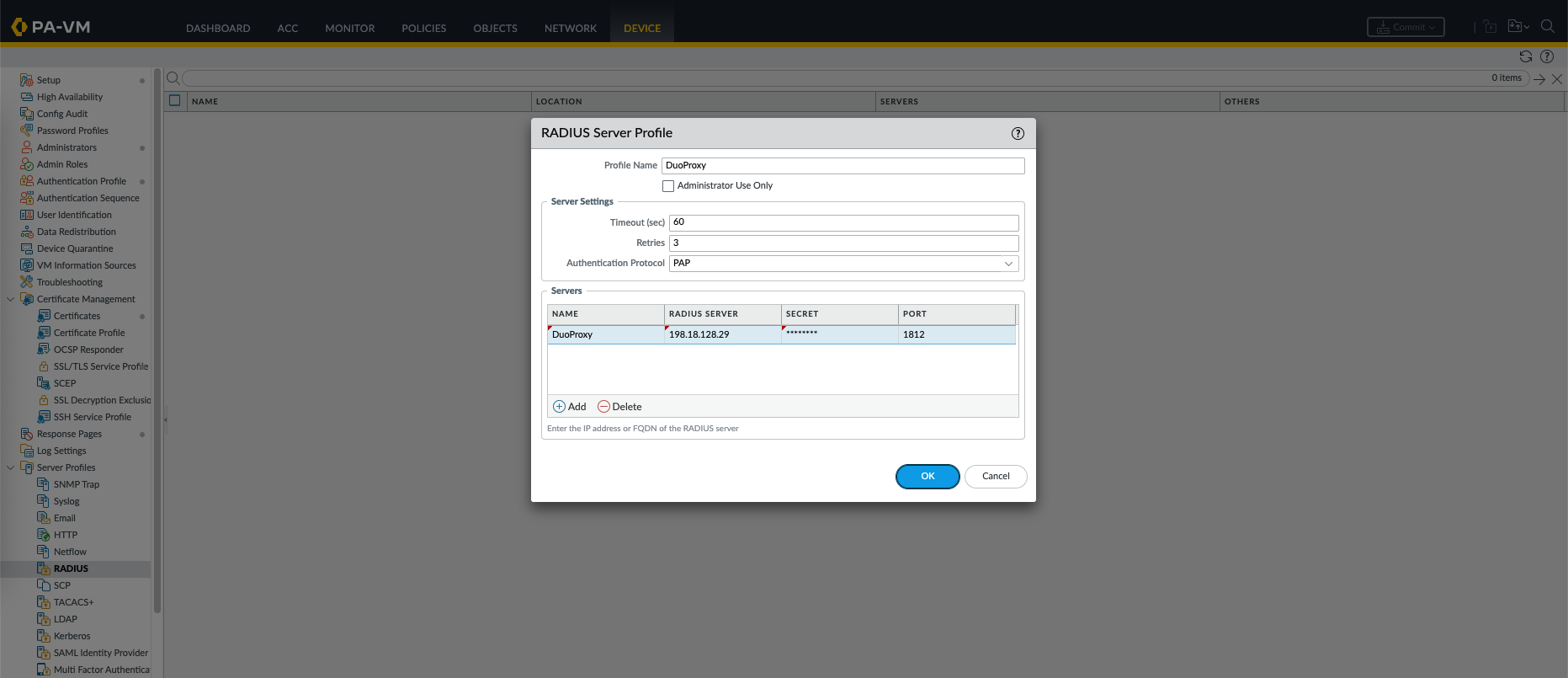
Next on the Palo side, create a new Radius Server Profile pointing to the Duo Proxy
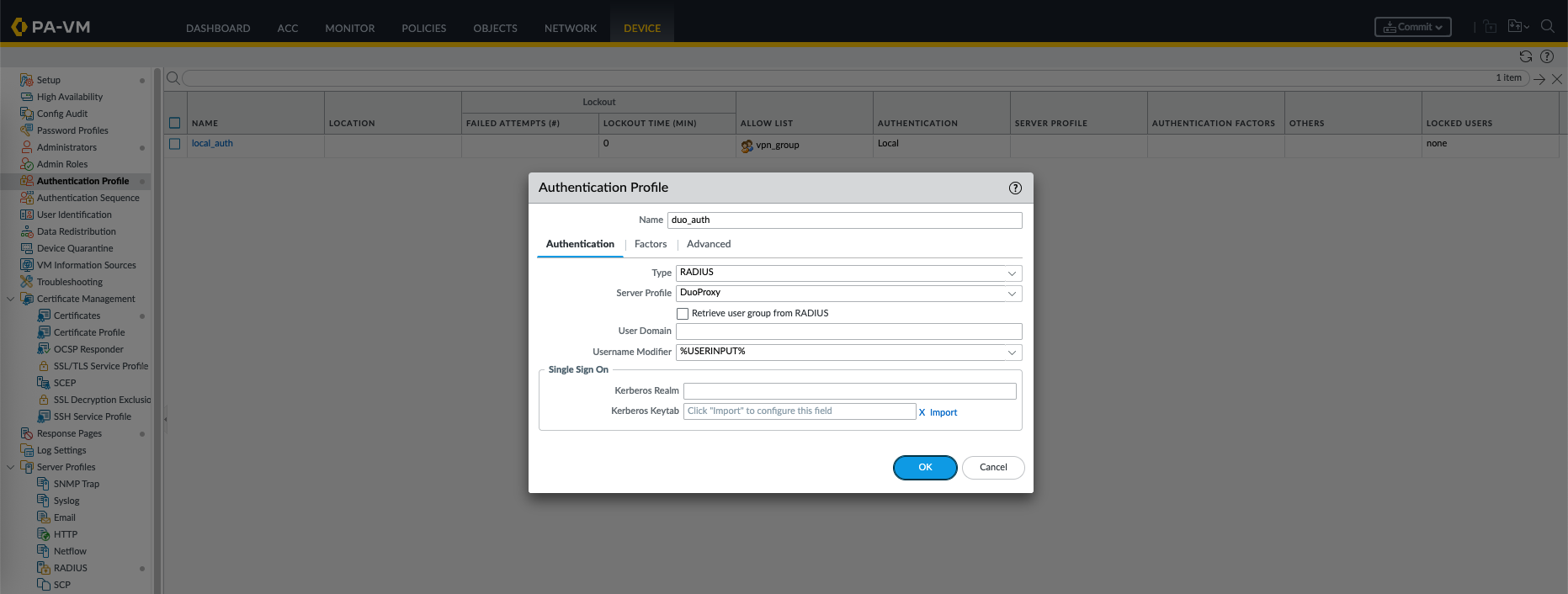
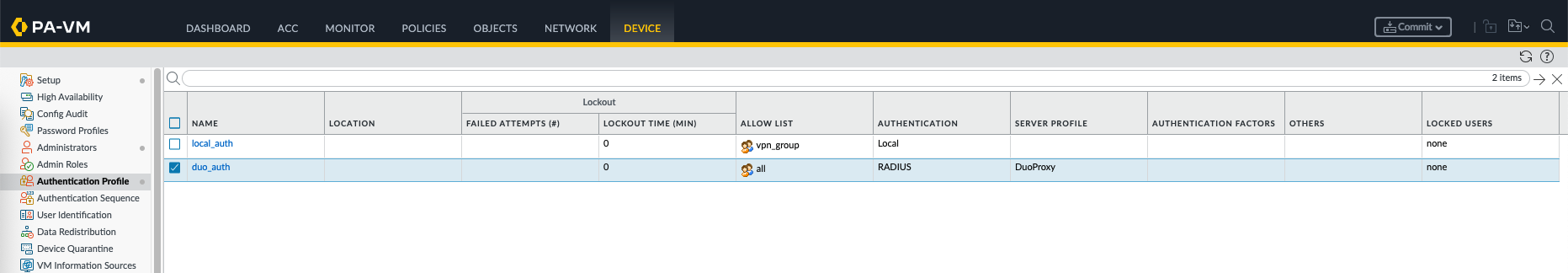
Then create a new Authentication Profile that uses the newly created Duo Proxy Server Profile
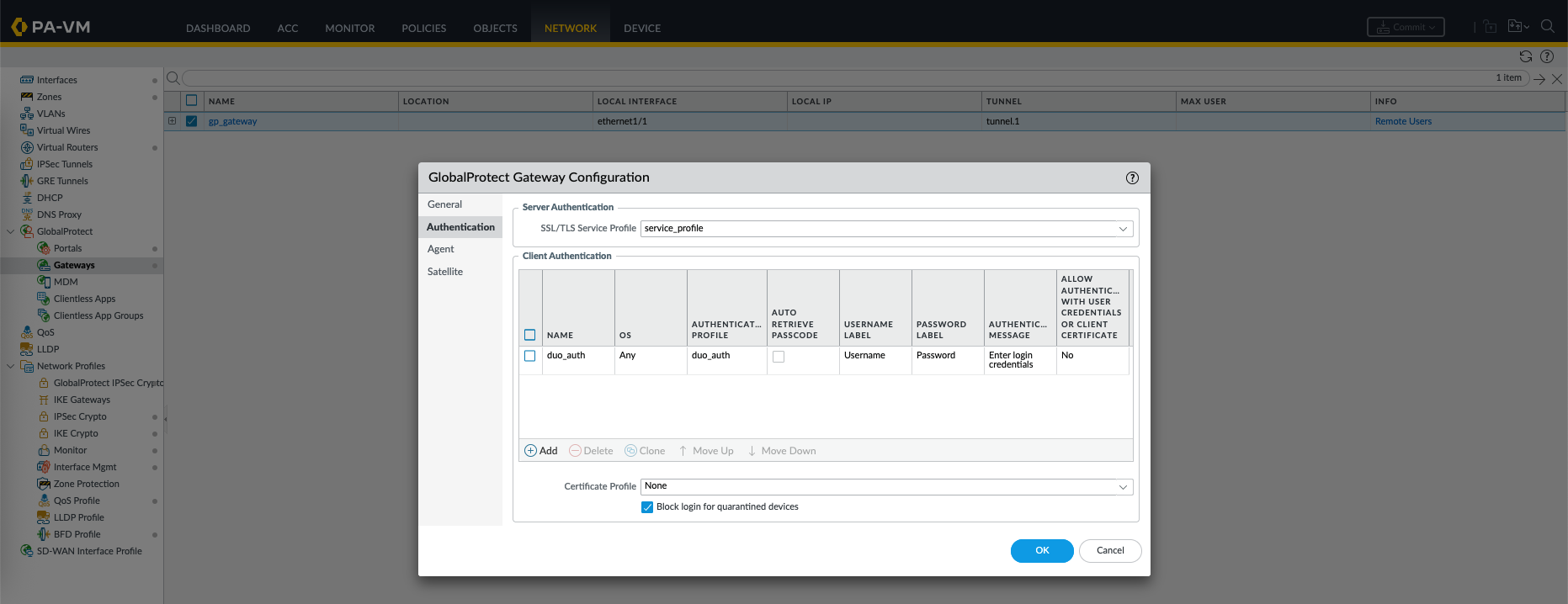
Finally on Gateway Configuration, replace the old local authentication to duo proxy radius
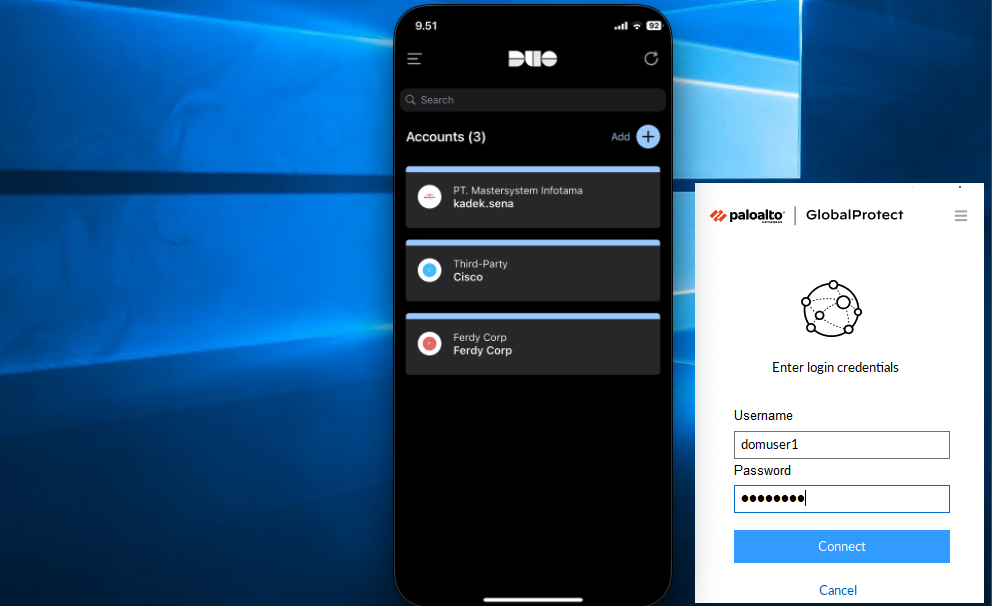
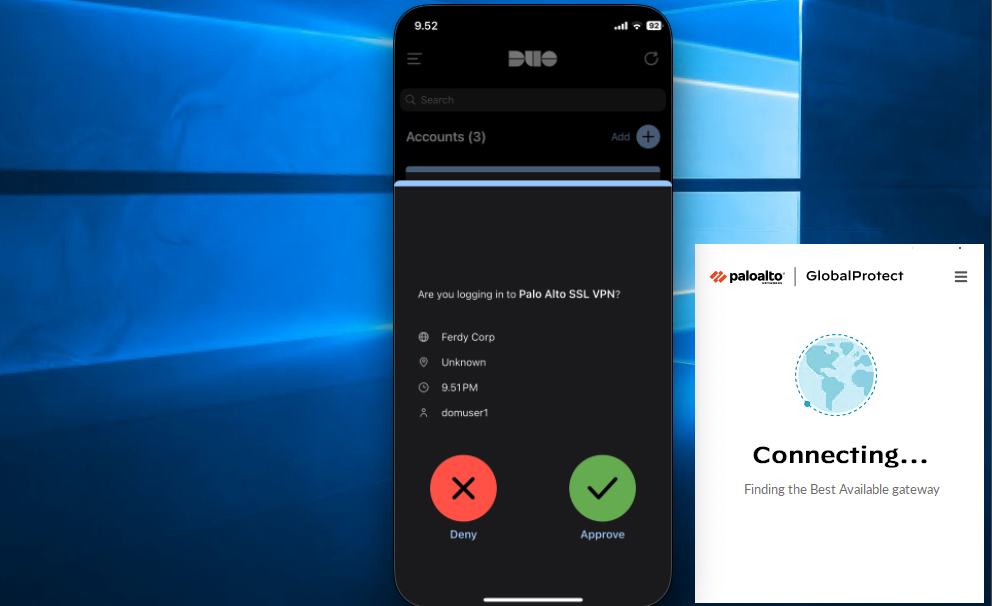
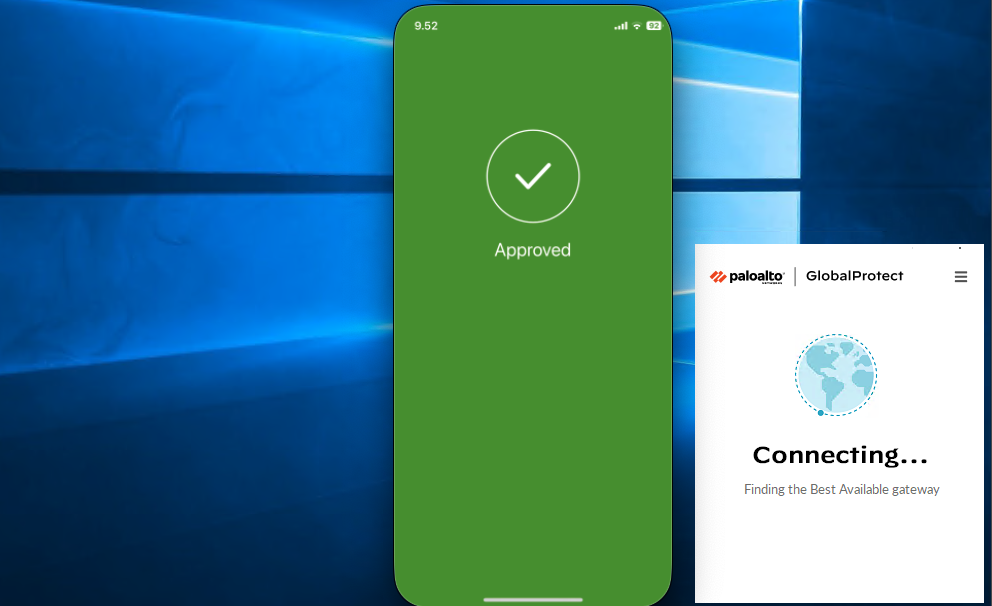
That’s pretty much it, now if we log in to VPN using AD users, we’ll be prompted a Duo MFA
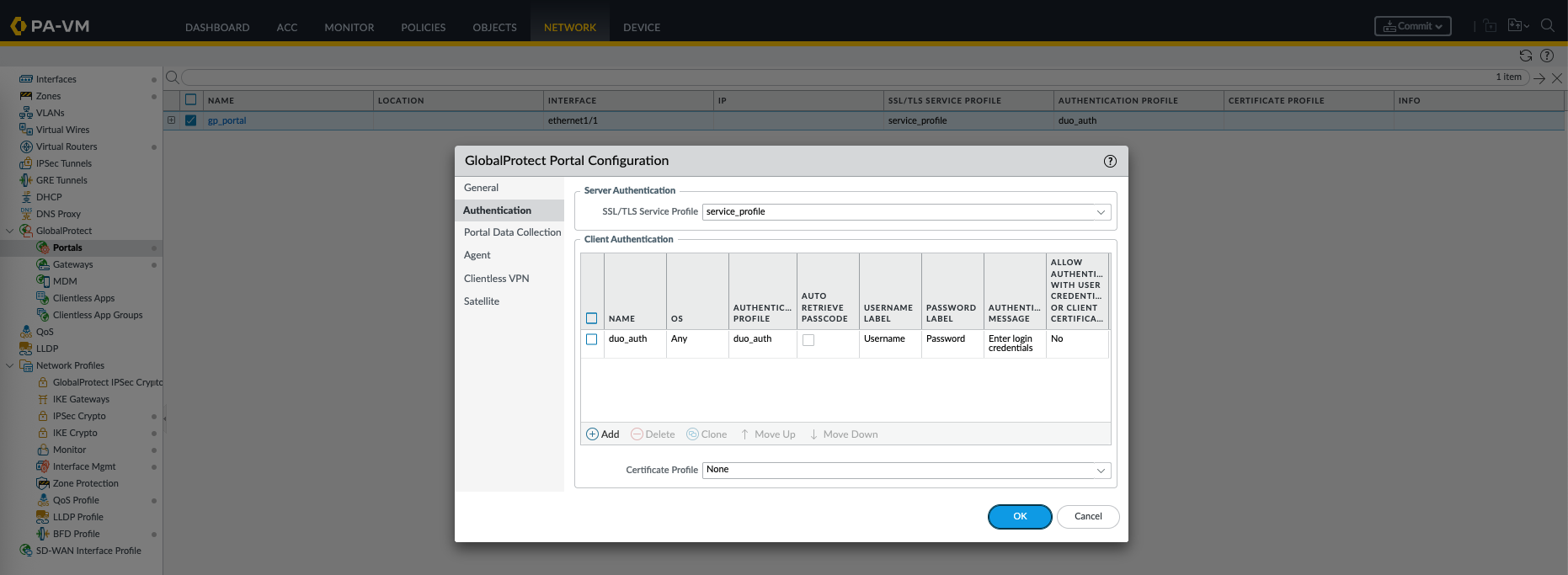
Optionally, if we’d like to also use MFA for Global Protect Portal, we can do the same configuration here
And now the portal will use MFA as well