Palo Alto HA Cluster
A Palo Alto High Availability (HA) cluster consists of two firewalls configured to provide redundancy and ensure network availability. In an active-passive setup, one firewall is active and handles all traffic, while the other remains in a standby mode, ready to take over if the active firewall fails. In an active-active configuration, both firewalls are active and share the traffic load, providing not only redundancy but also increased performance and resilience by utilizing both devices simultaneously.
Active-Passive
In an Active-Passive mode, both firewalls will take turn to take ownership of the interface based on the active/passive role
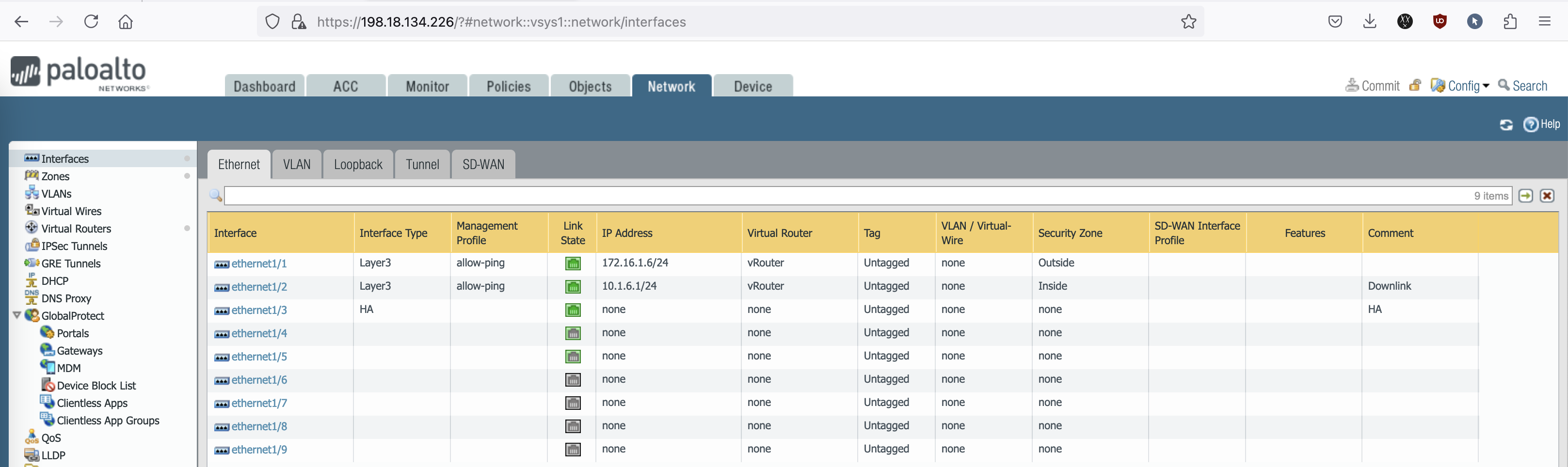
On the Palo-1, we configure the uplink and downlink interfaces, along with one HA link. We actually need two HA links but the other one we’ll use the management interface
On Palo-2, we configure nothing but the management interface and one HA interface
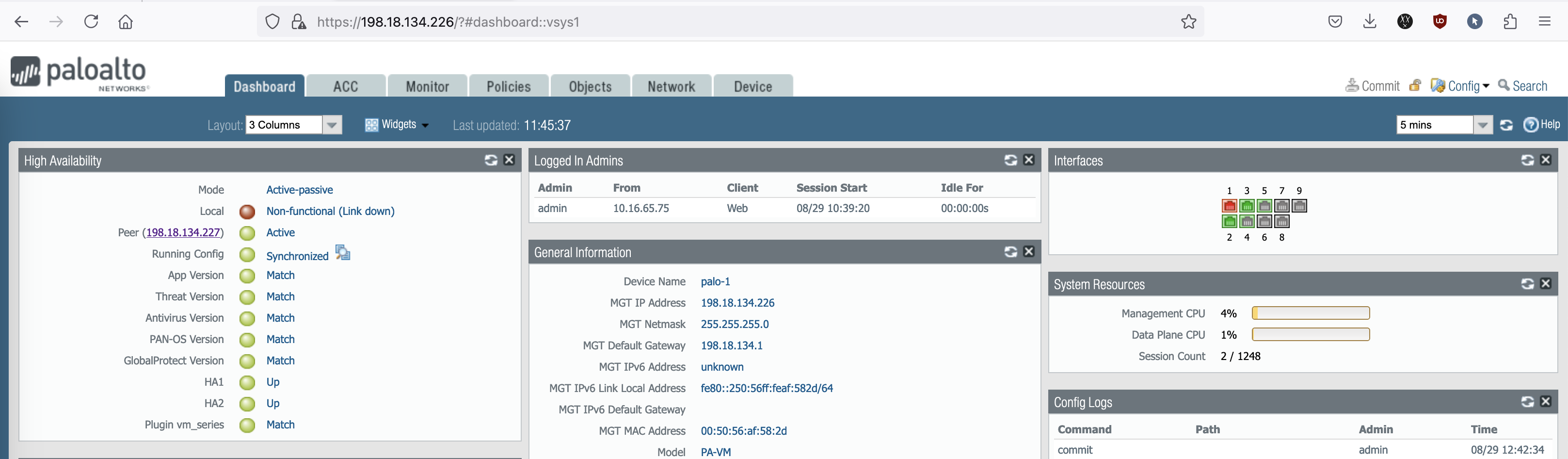
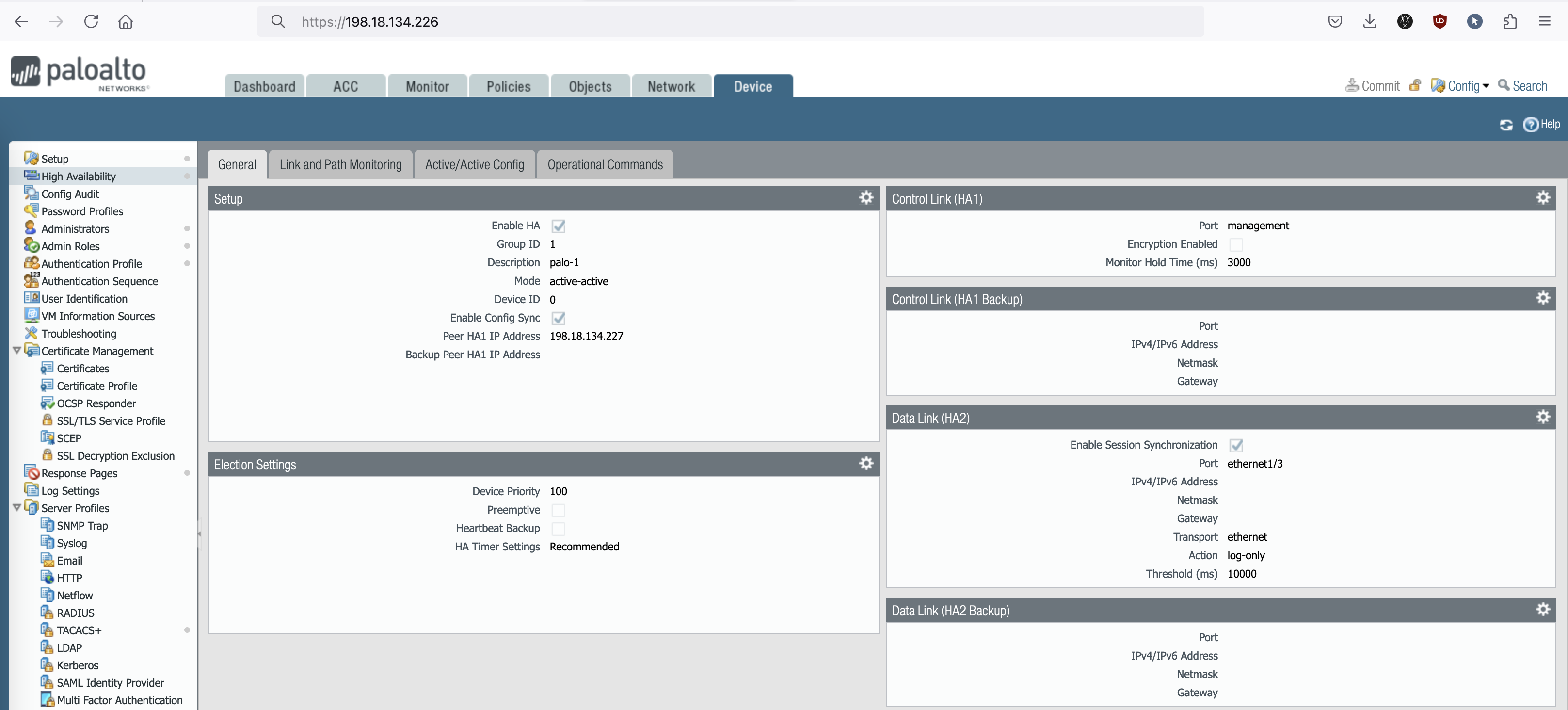
Back on Palo-1 on Device » High Availability, here we setup the HA configurations
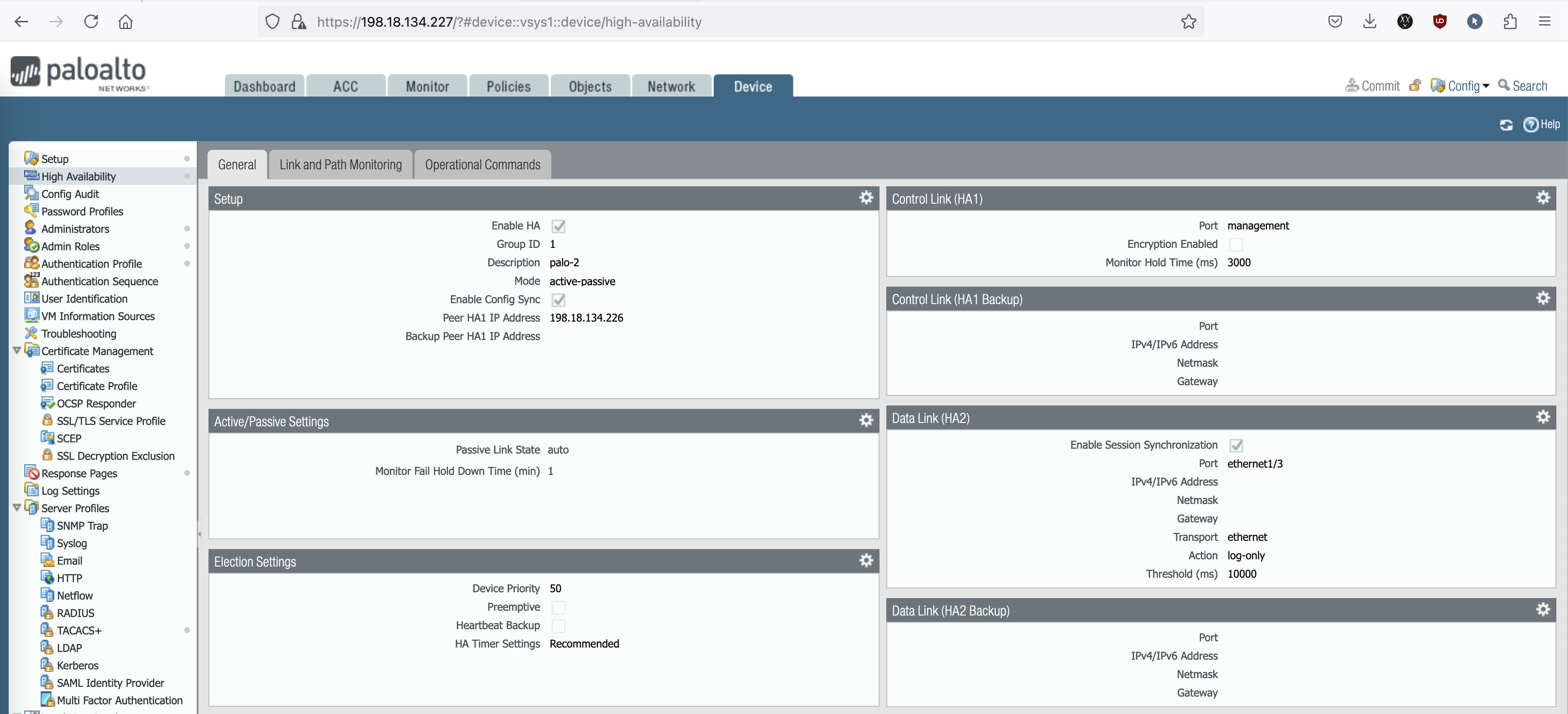
- Setup
Here we enable the Group ID which has to match on both nodes, then the mode to be active-passive, and the Palo-2 HA1 address, which in this case we’ll be using the management interface- Active/Passive Settings
For Passive Link State, we set to auto so the interface on the passive node will always be on Active Status so the failover happens a bit more quickly.- Election Settings
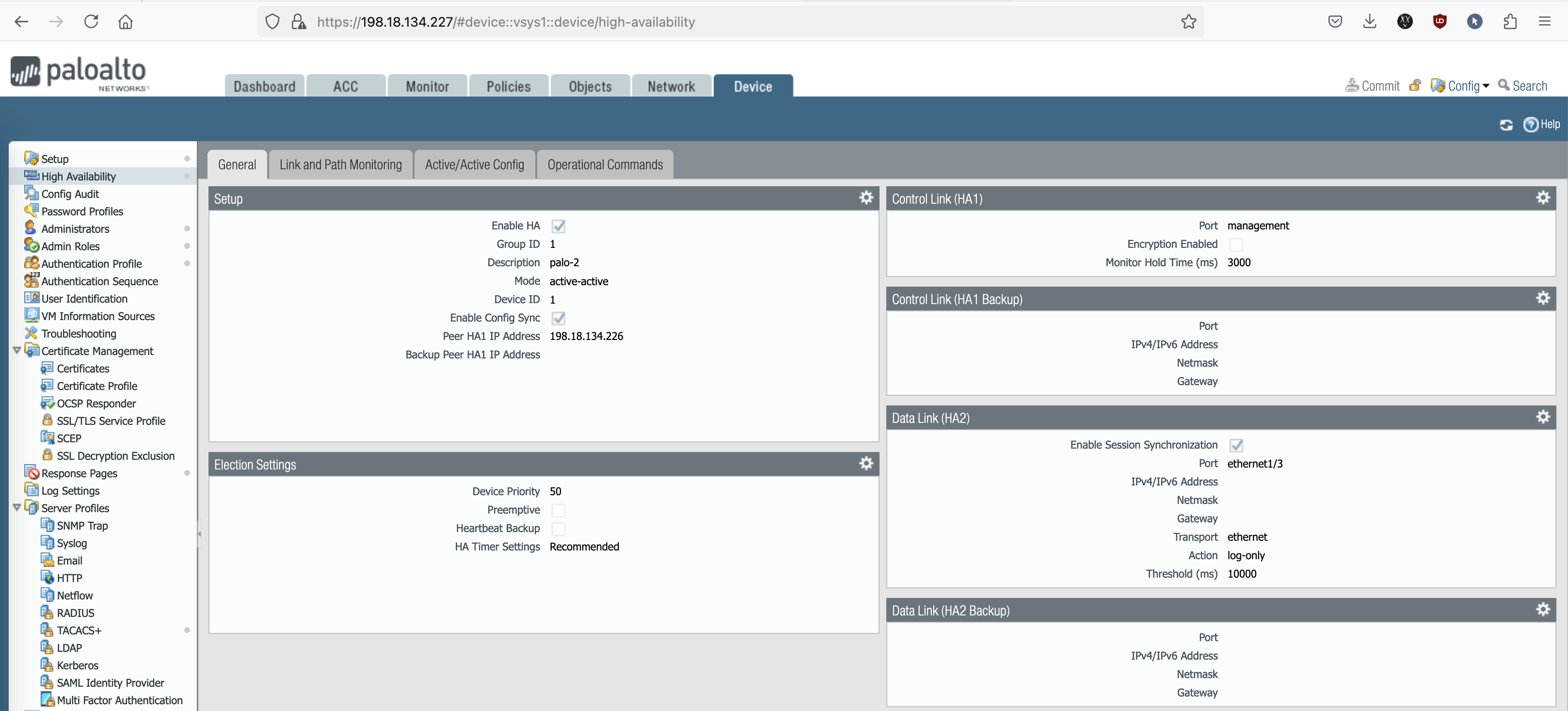
We set this Palo-1 to have a higher priority (100) so it is preferred to be the active node.- Control Link (HA1)
We can use dedicated HA link & IP Address for this but for simplicity we’re using the Management Interface. This link is used for exchanging heartbeats and configuration updates between the firewalls in the HA pair.- Data Link (HA2)
For HA2 we have to use a different link than the HA1, so here we add a blank interface with no IP because we’re using the transport type of ethernet. This link is responsible for synchronizing session and forwarding information between the two firewalls. It allows the other firewall to have the same session and state information, enabling seamless failover and session continuation in a failover.
Next on Link and Path Monitoring, here we speicify the links that we’d like to monitor to trigger the failover
On the Palo-2, we configure pretty much the mirrored configuration with slight differnces in IP Addressing and Device Priority
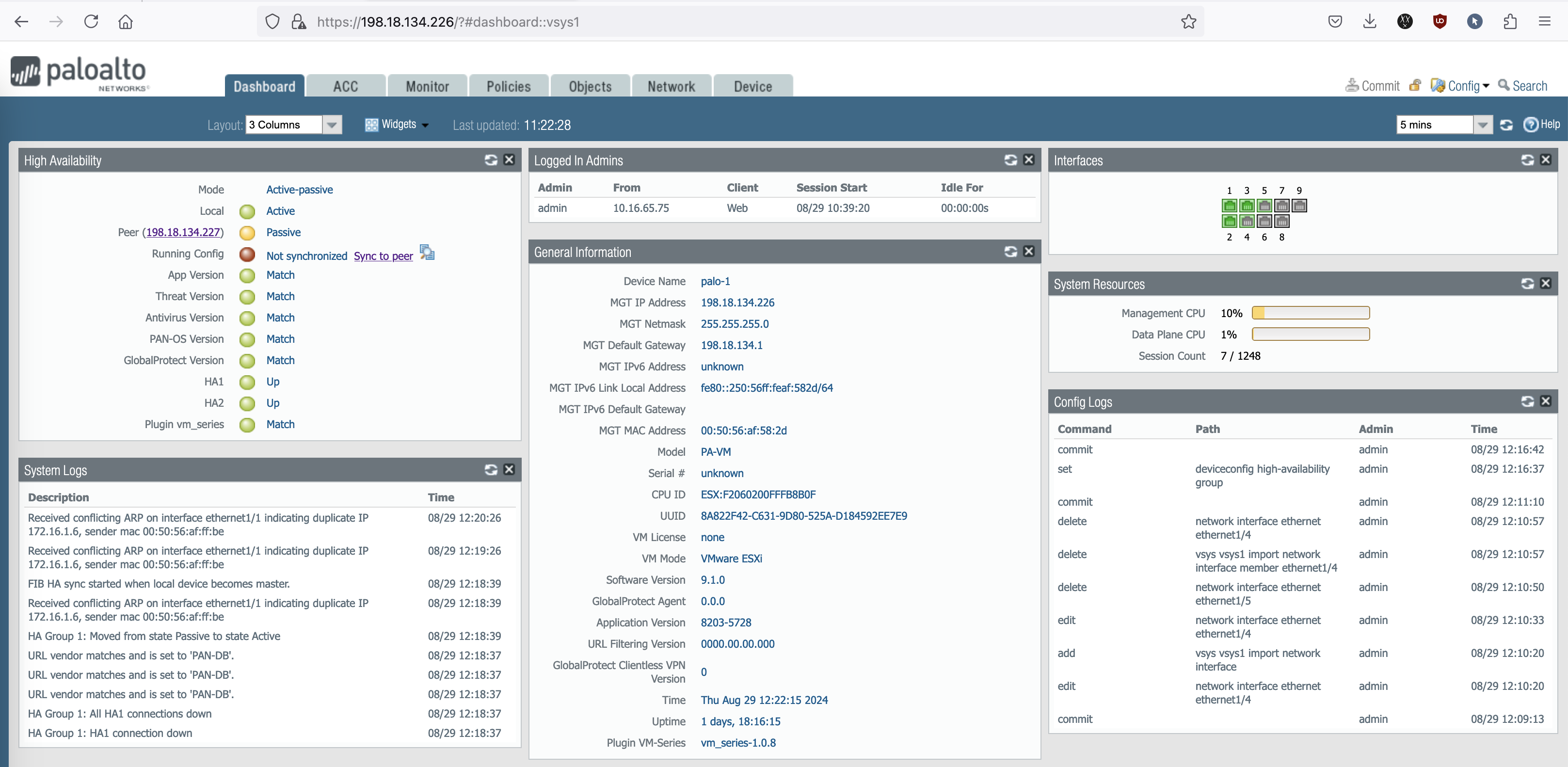
That should do it for the HA configuration, now on the HA Widget, we can see HA Cluster is active but not yet synchronized. Hit Sync to peer to start copying Palo-1 configurations to also exist on the Palo-2
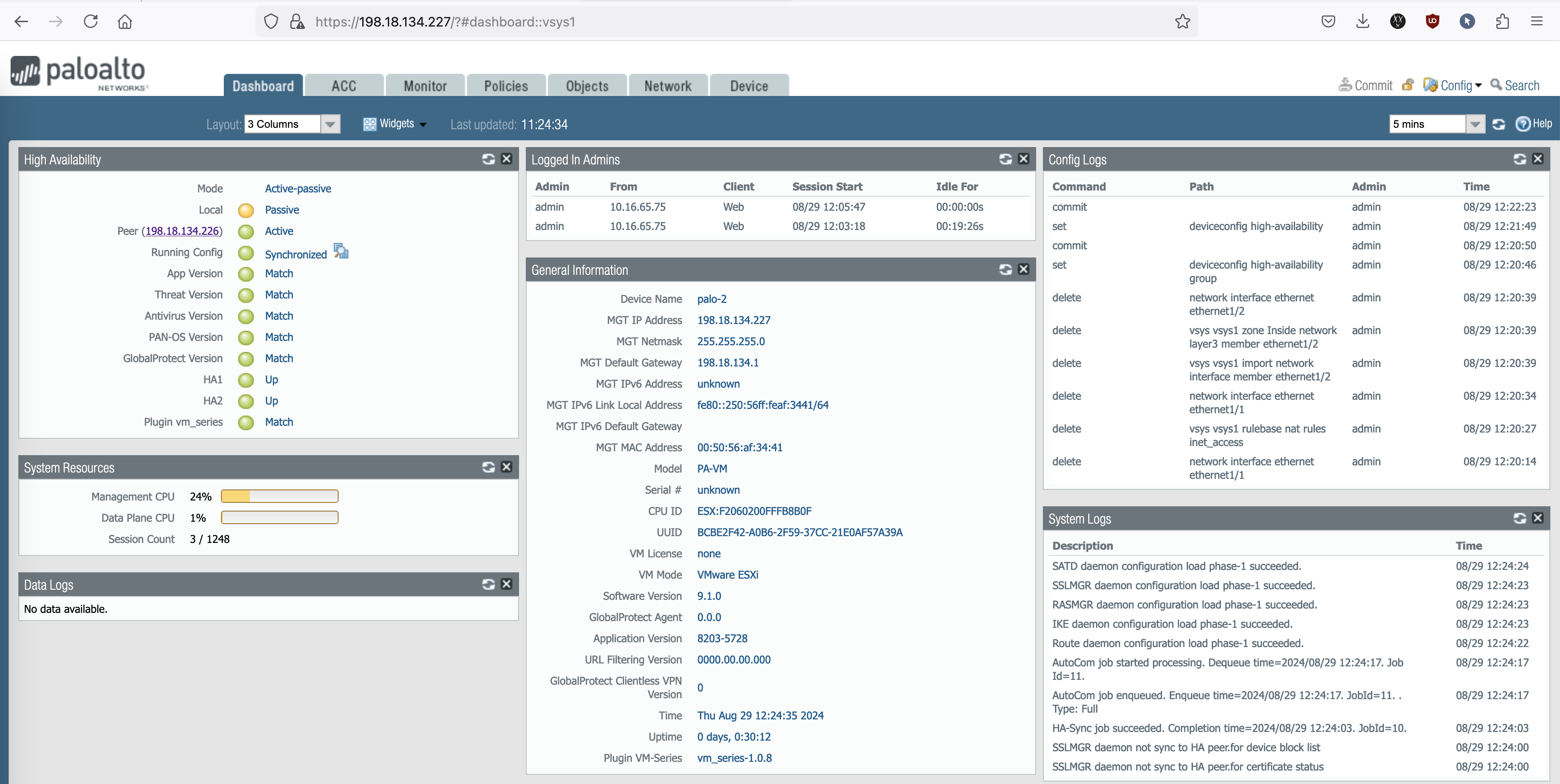
Now the HA cluster is fully configured
Palo-1
Palo-2
And on Palo-2, all the Palo-1’s configurations is synced to this node, including the IP Address configurations
Failing Over
Now if there’s a failure on the uplink or downlink interface on Palo-1, the cluster will failover to make the Palo-2 the Active Node
Palo-1
Palo-2
No significant impact to be observed on the client side when the failover is taking place
If we restore network functionality on Palo-1, it will just sit in Passive Node until there’s failure happening on Palo-2
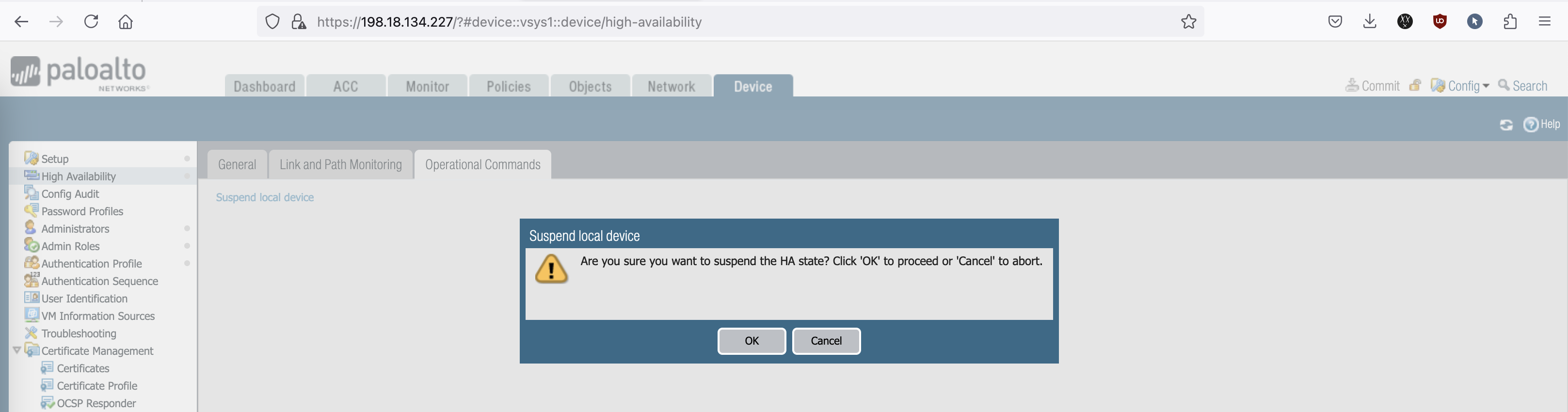
One way to simulate a failure is by suspending the HA operation on Device » High Availability » Operational Commmands
Now the Palo-1 has the Active Node ownership again
Active-Active
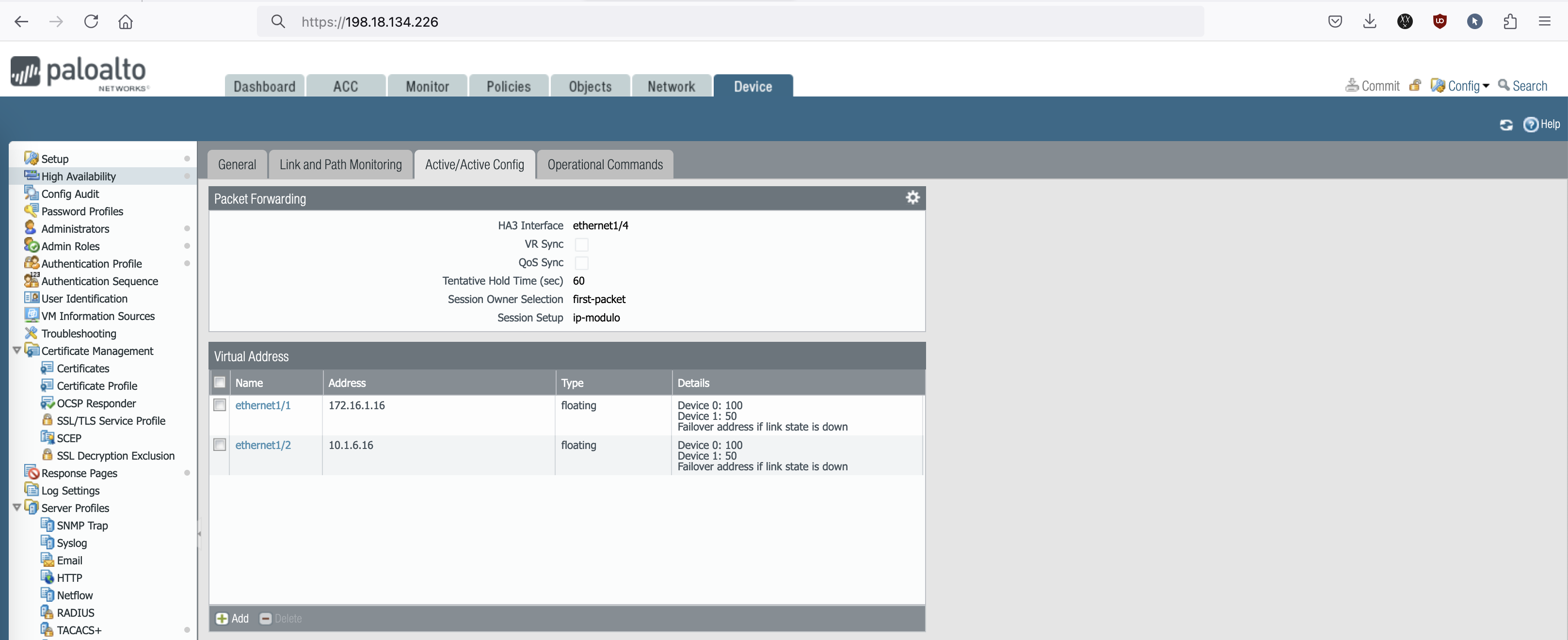
In the Active-Active node, each firewall needs to have its own IP Address configuration which then we put a floating Virtual IP on top of that to enable load balancing to both nodes, and we also need an additional HA link (HA3) for asymmetric traffic forwarding
Here’s the interface configurations on both nodes
Palo-1
Palo-2
On Palo-1, we configure the HA cluster with the mode of Active-Active, other than that the rest of configurations is pretty much the same as previously
Next on Link and Path Monitoring, we’ll again monitor the uplink and downlink interfaces
Then on Active/Active Config, we add another HA link (HA3) and we also configure the Virtual IP Address for the uplink and downlink interfaces
- The HA3 link enables the firewalls to share and forward session information and data packets that belong to the same session but arrive at different firewalls. This is crucial in an active-active setup because it allows both firewalls to process traffic simultaneously. If a packet arrives on one firewall but the session is owned by the other firewall, the HA3 link forwards the packet to the correct firewall for processing. This ensures that session integrity and state information are maintained across both devices, allowing seamless traffic handling in the active-active deployment.
On Palo-2, we pretty much mirror the configurations
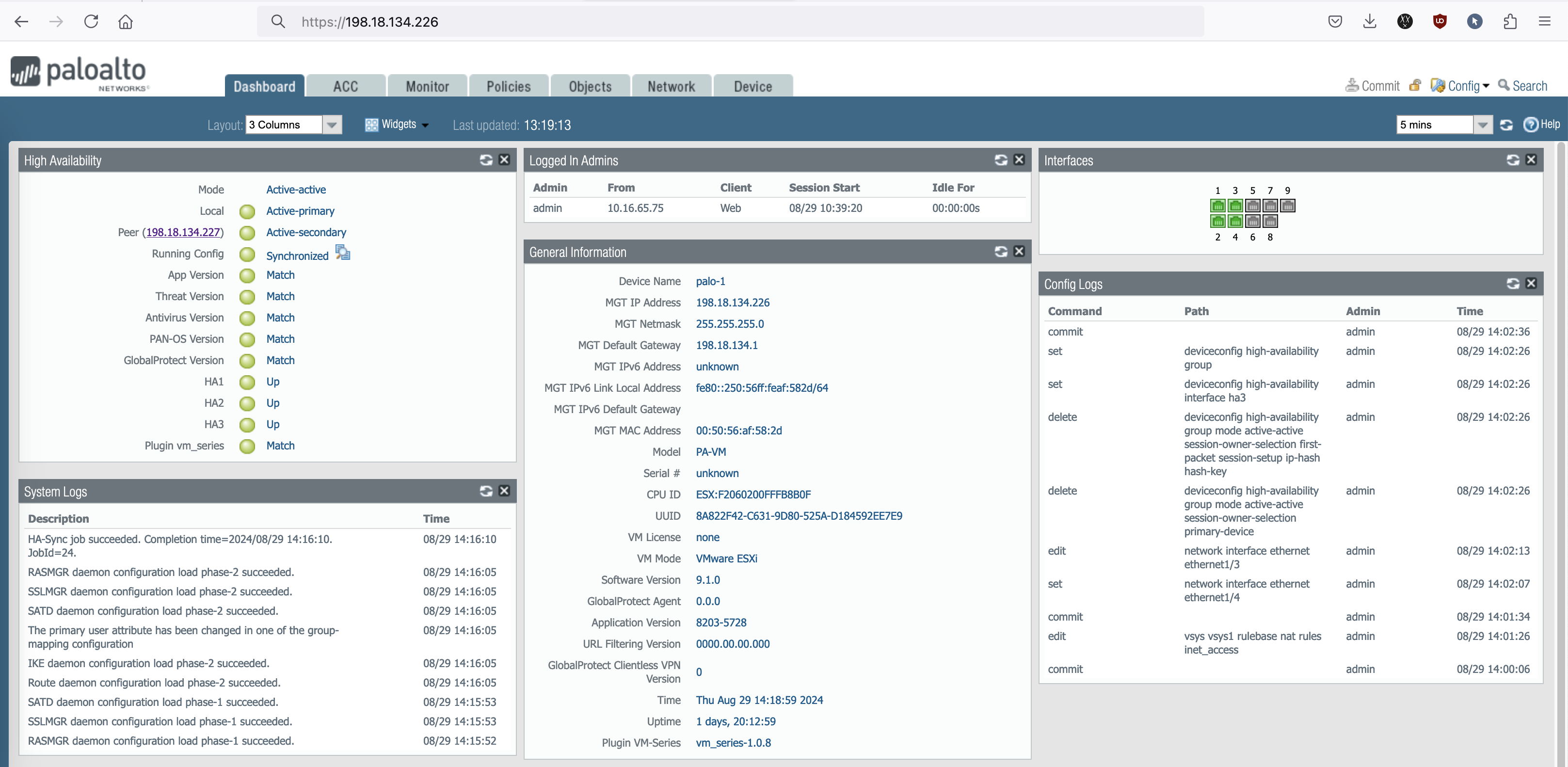
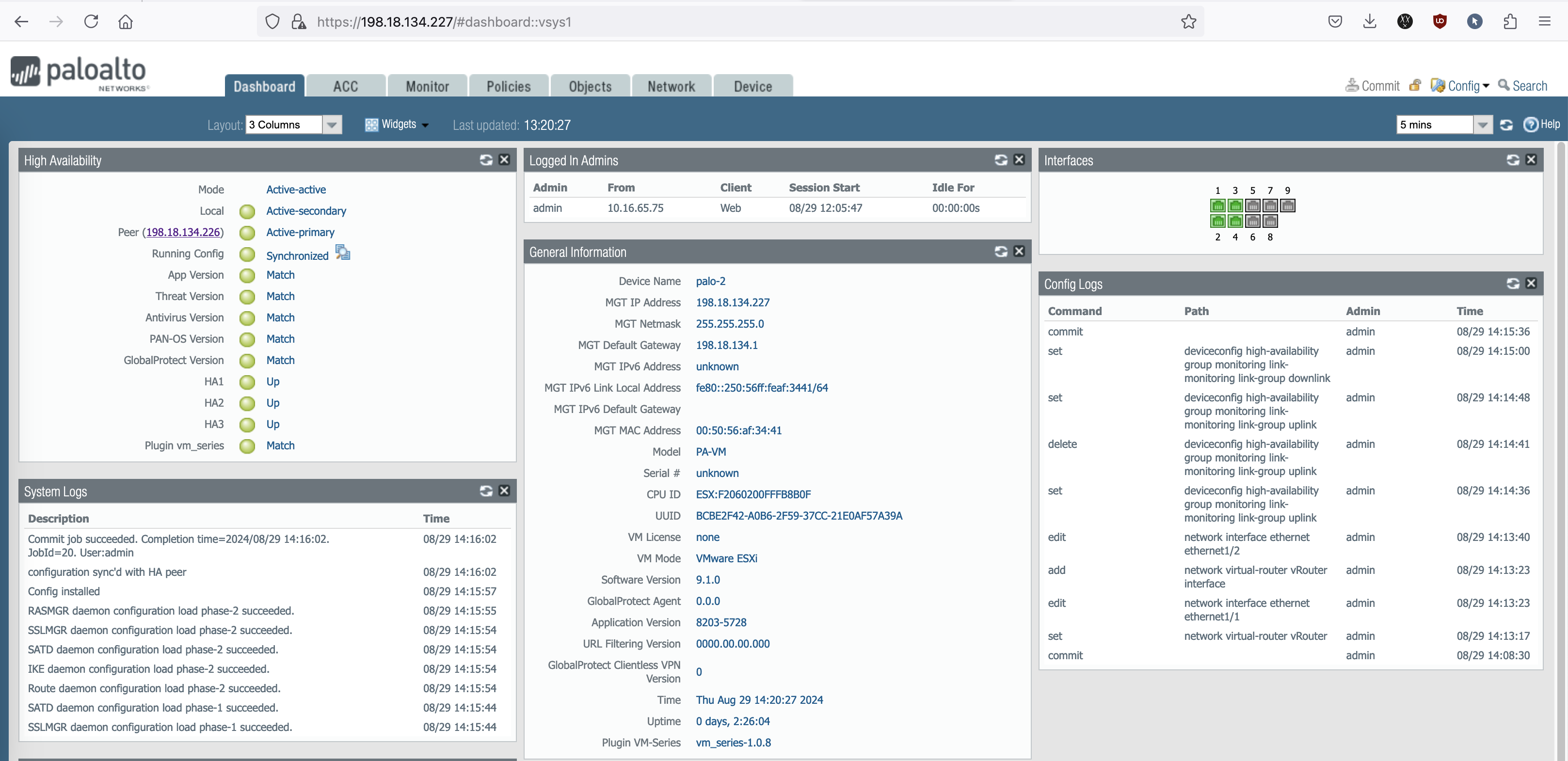
Now the Active-Active HA Cluster is up and running
Palo-1
Palo-2
Failing Over
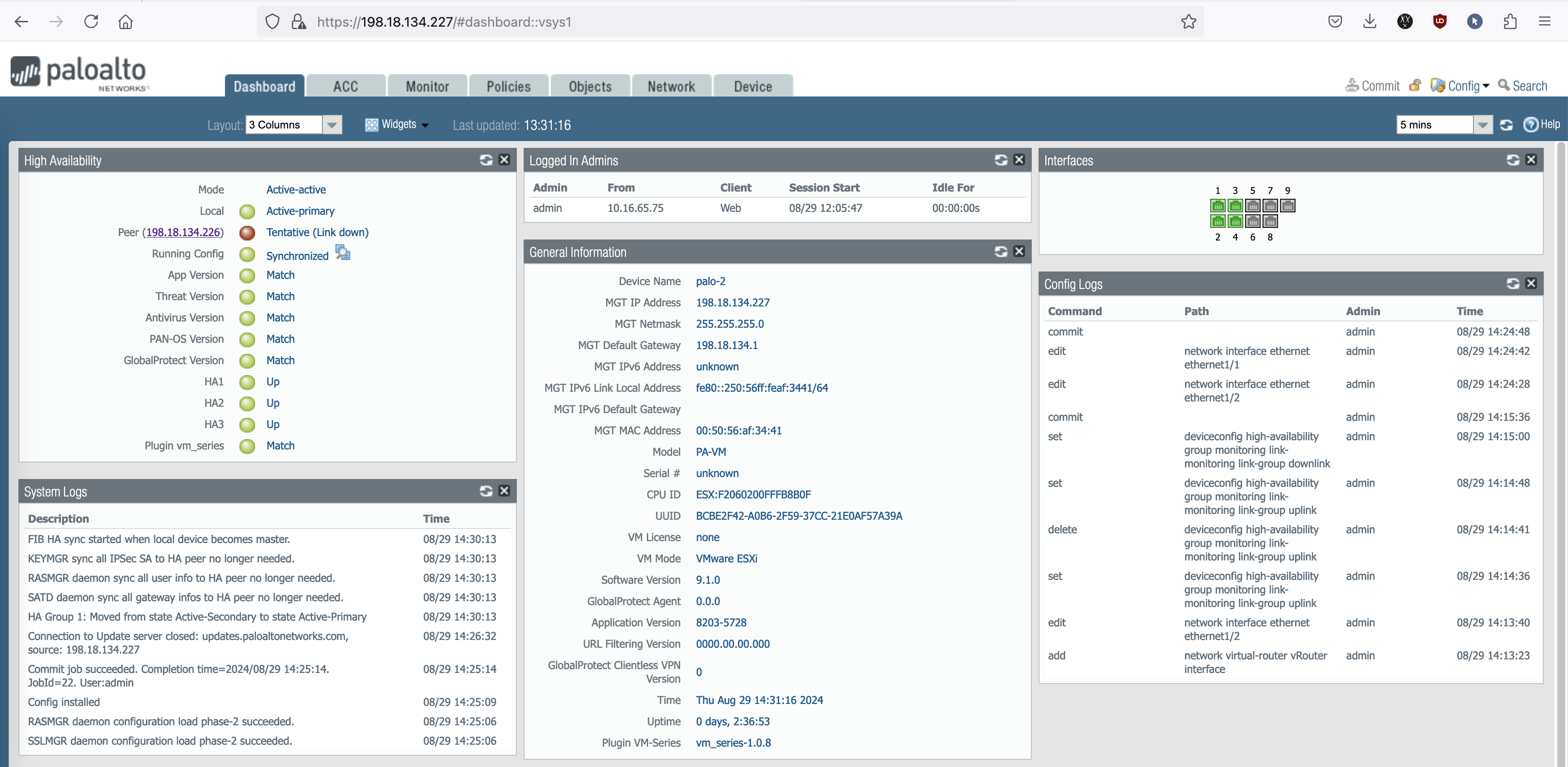
If we create a link failure on Palo-1, the node will be deactivated from the cluster and the Palo-2 will take the Active-Primary role
Palo-2
Restoring the network connectivity on Palo-1 will make the Palo-1 become the Active-Secondary where the Primary will still be on the Palo-2
Palo-1
Simply suspend the Palo-2 or simulate a network failure to make the Palo-1 the Primary again
Palo-1