Palo Alto Site to Site IPSec VPN
A Site-to-Site IPSec VPN is a secure connection established between two networks, connecting different offices or branches of an organization over the internet via Palo Alto firewalls.
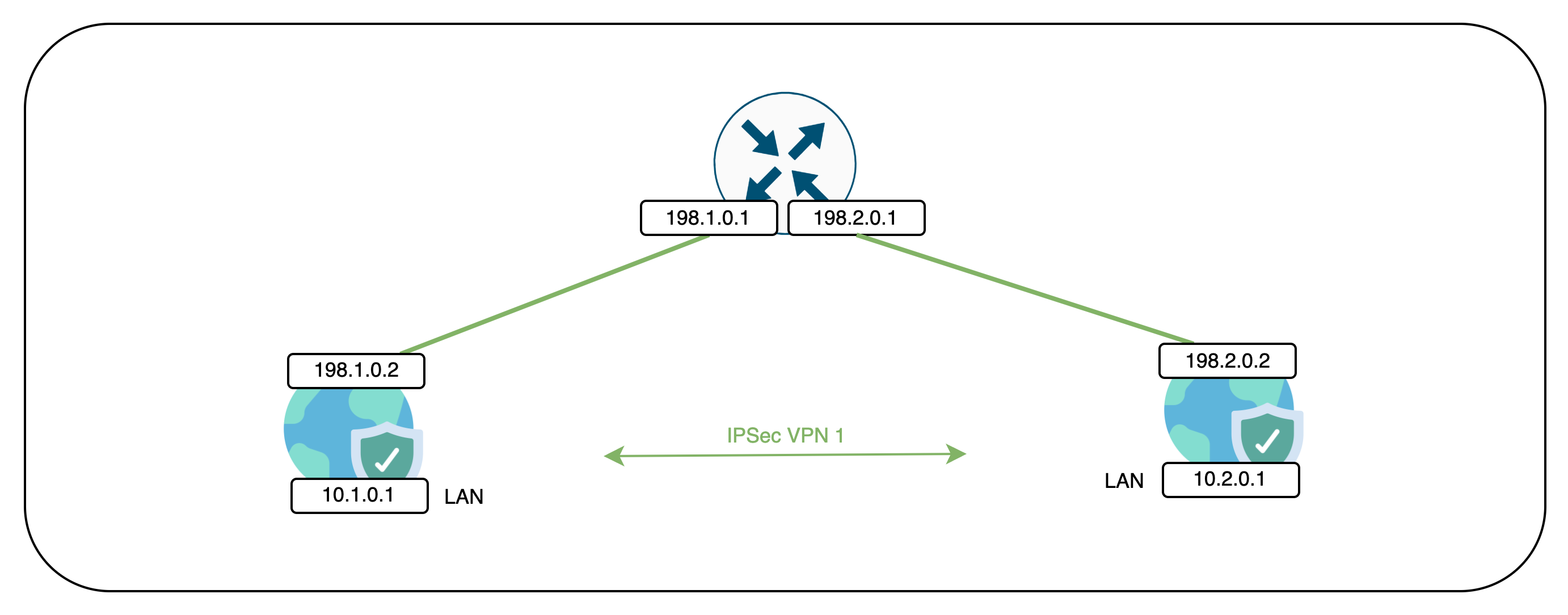
Here’s the topology of the configuration
Configuring IPSec VPN on Palo-1 device
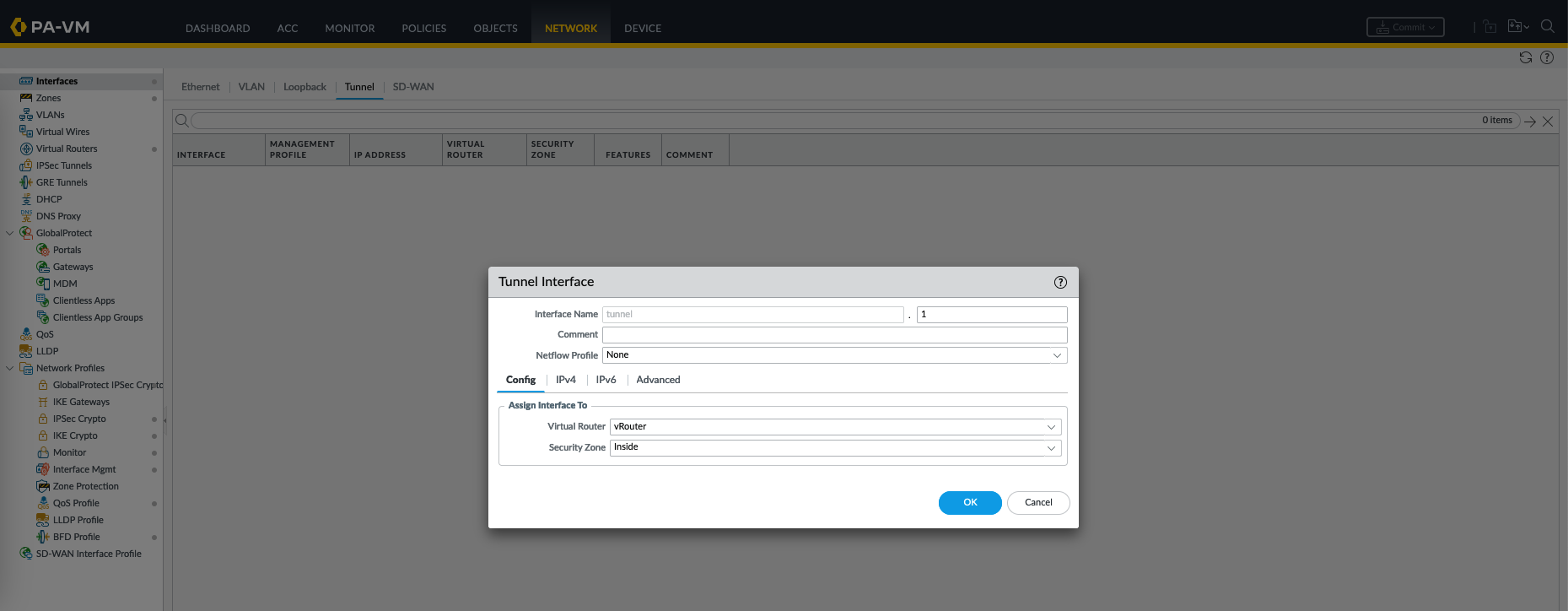
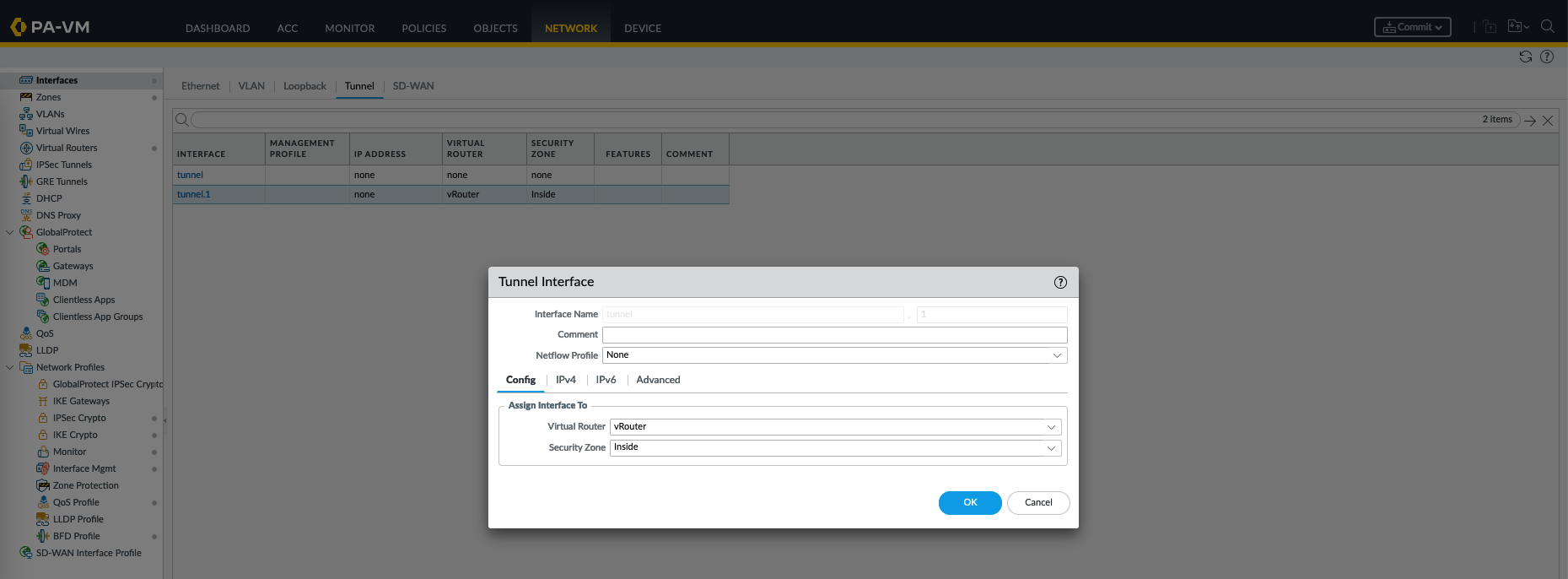
On the first firewall, create a new tunnel interface
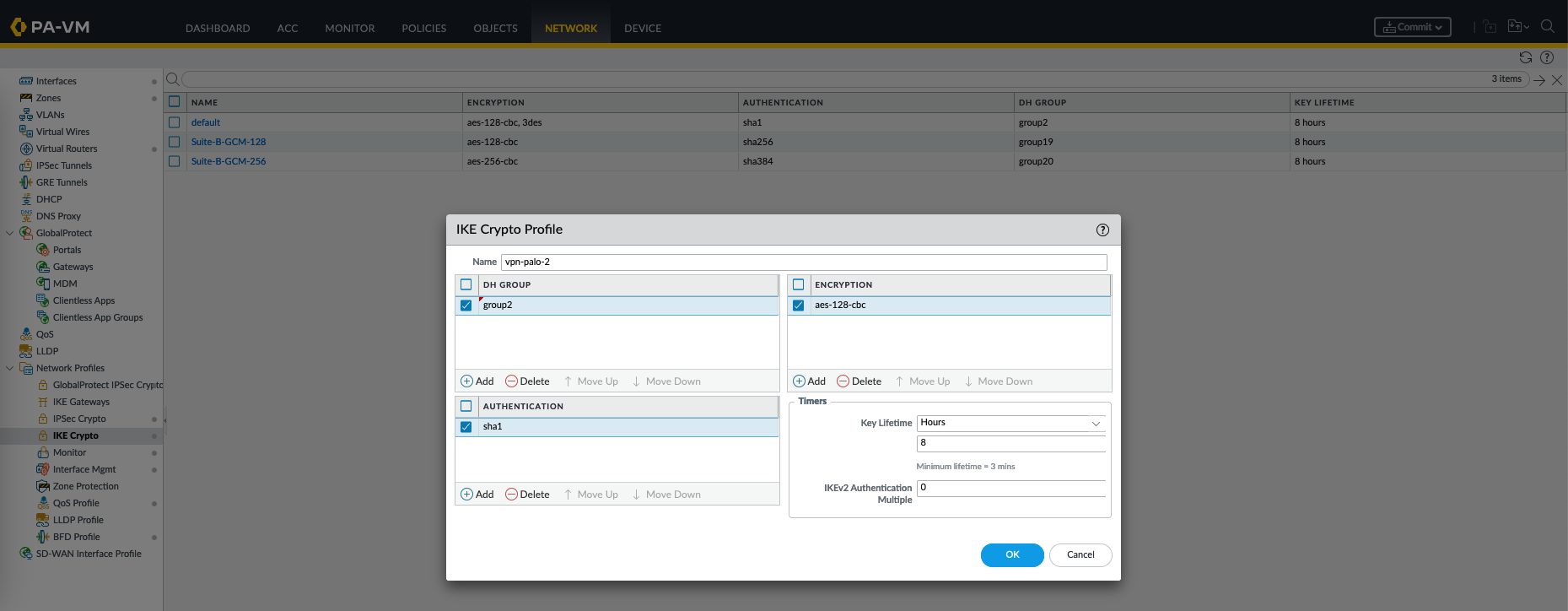
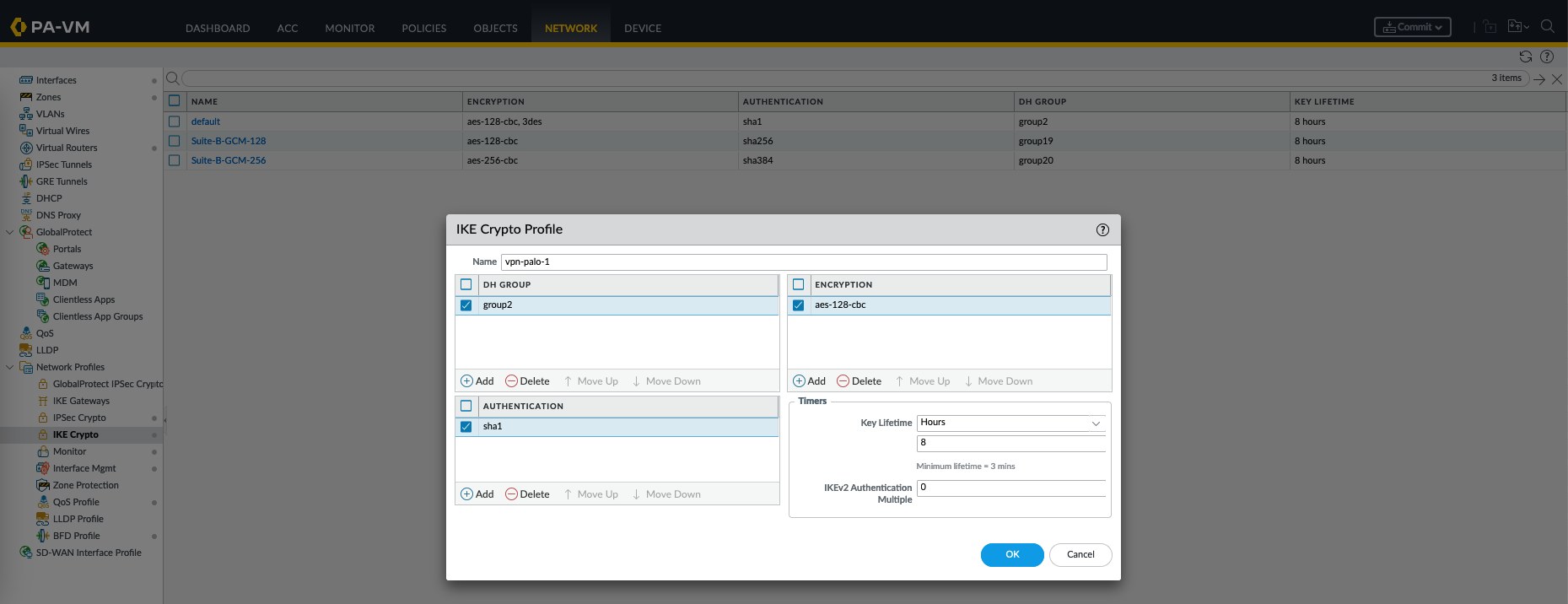
Next on Network Profiles » IKE Crypto, create a new profile
An IKE (Internet Key Exchange) Crypto Profile is a configuration that defines the parameters and settings used for the initial phase of establishing a VPN tunnel. It includes the encryption and authentication methods to be used during the key exchange process.
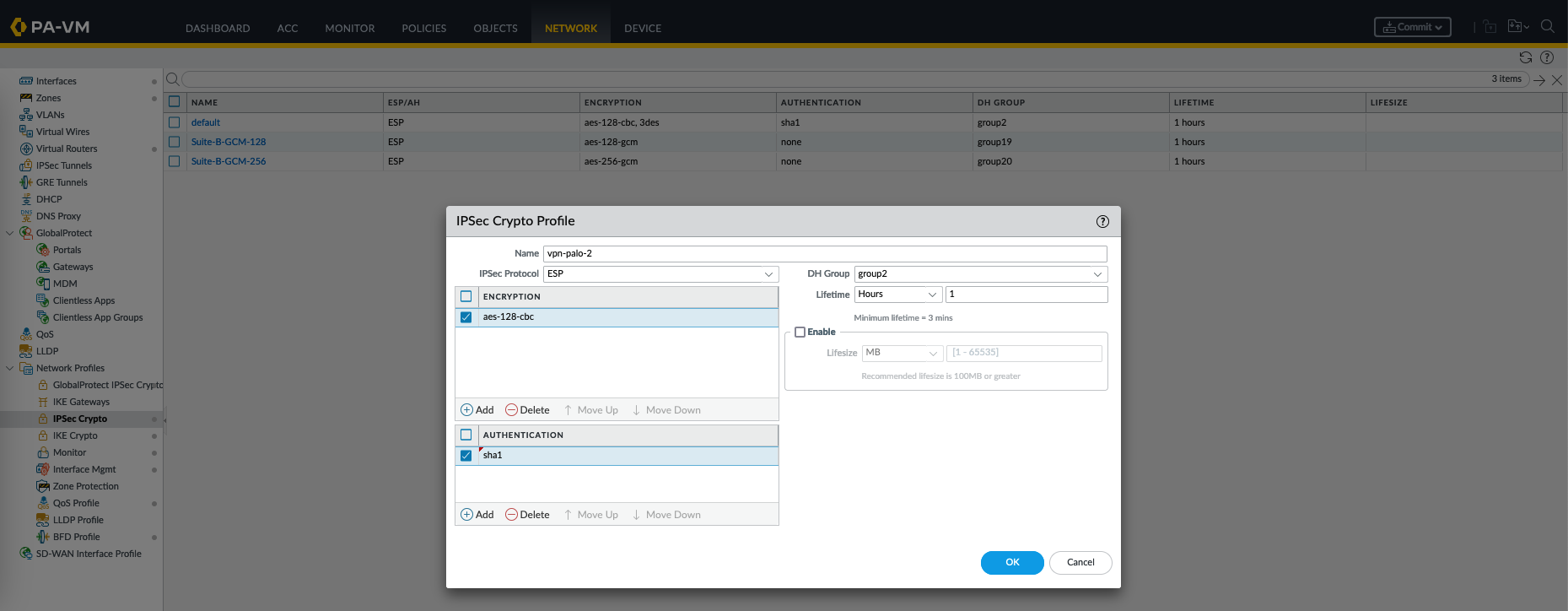
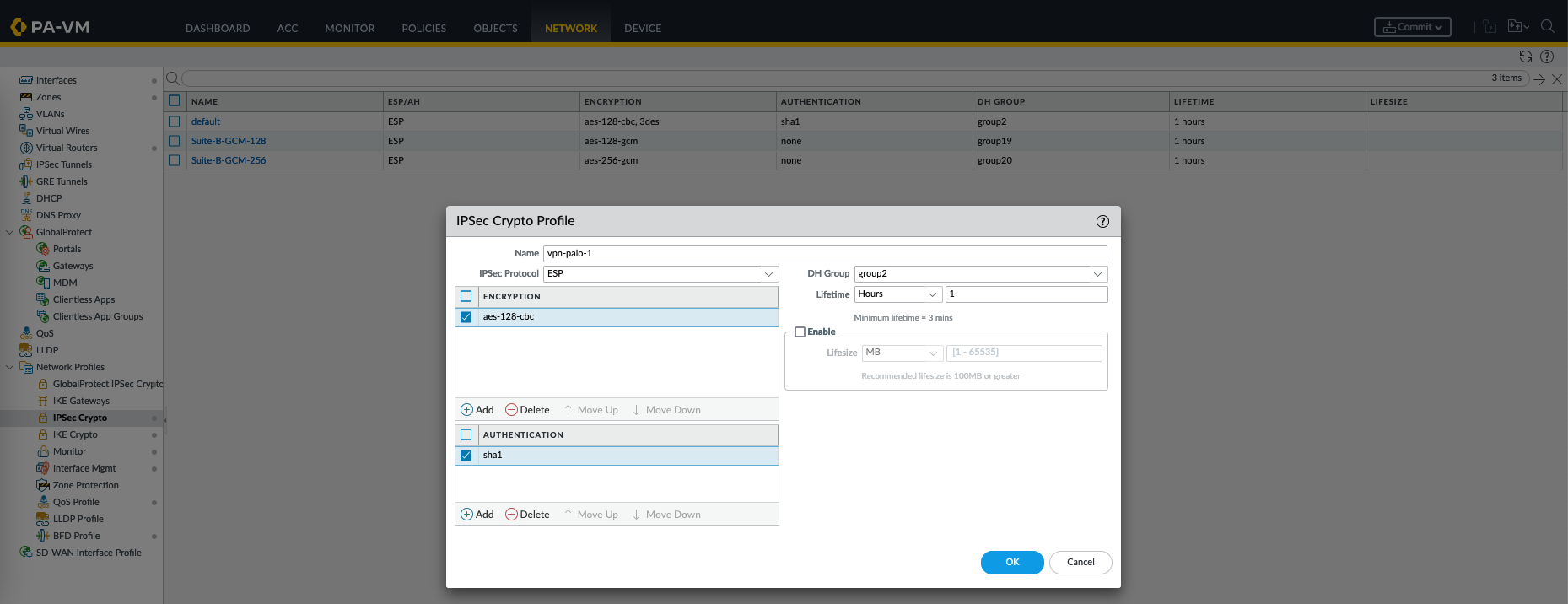
Next on IPSec crypto, alo create a new profile
An IPSec Crypto Profile is a configuration that defines the parameters and settings used for the second phase of establishing a VPN tunnel, which involves securing the data traffic between two sites. It specifies the encryption and authentication methods for protecting the actual data transmitted over the VPN tunnel.
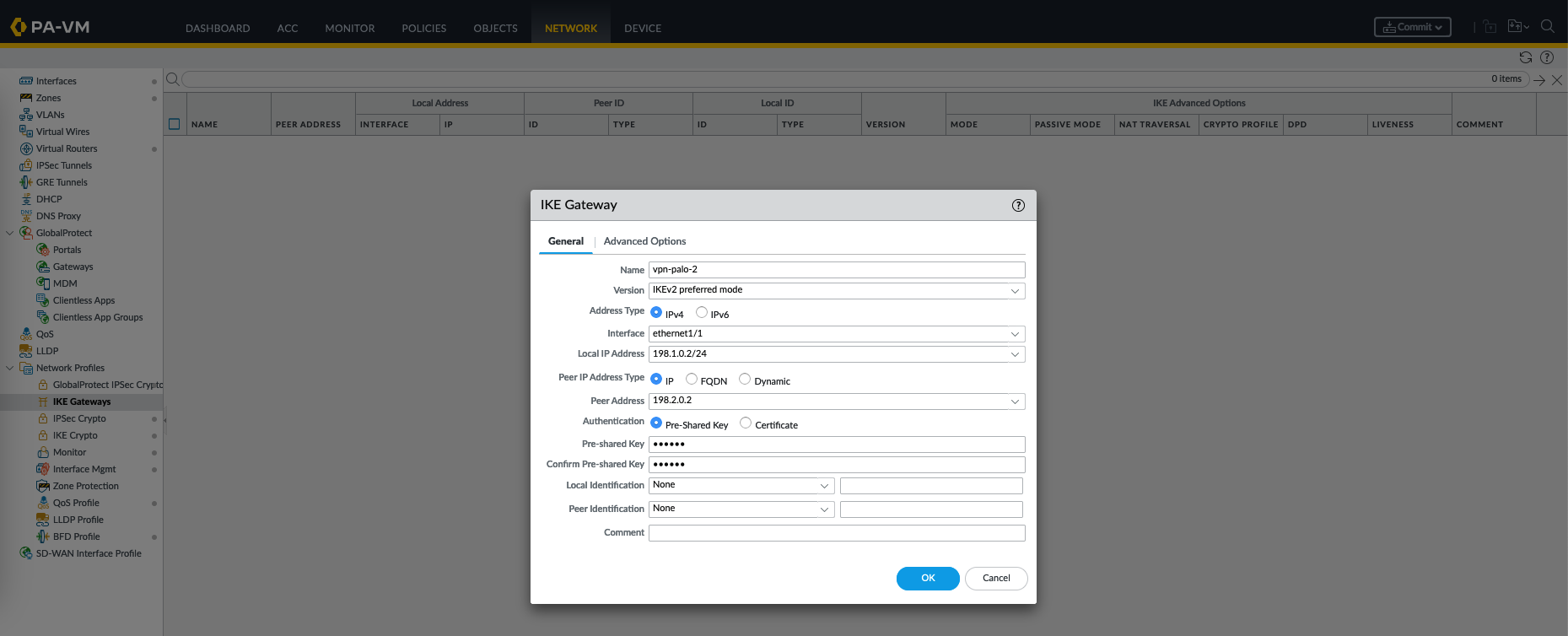
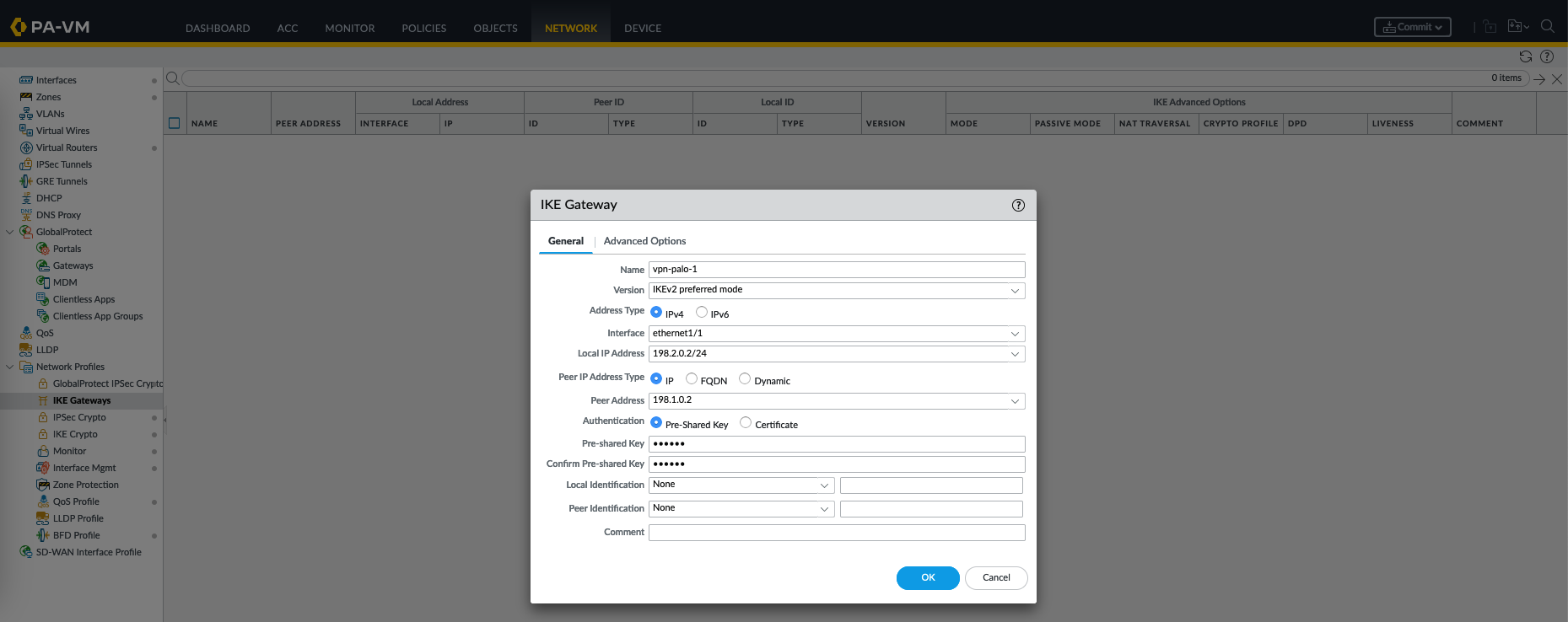
After that, on IKE Gateways create a new gateway
An IKE (Internet Key Exchange) Gateway is a configuration that defines the properties of a remote peer or site with which the firewall will establish a VPN tunnel. It includes information such as the remote peer’s IP address, pre-shared key, and the specific IKE Crypto Profile to be used for key exchange.
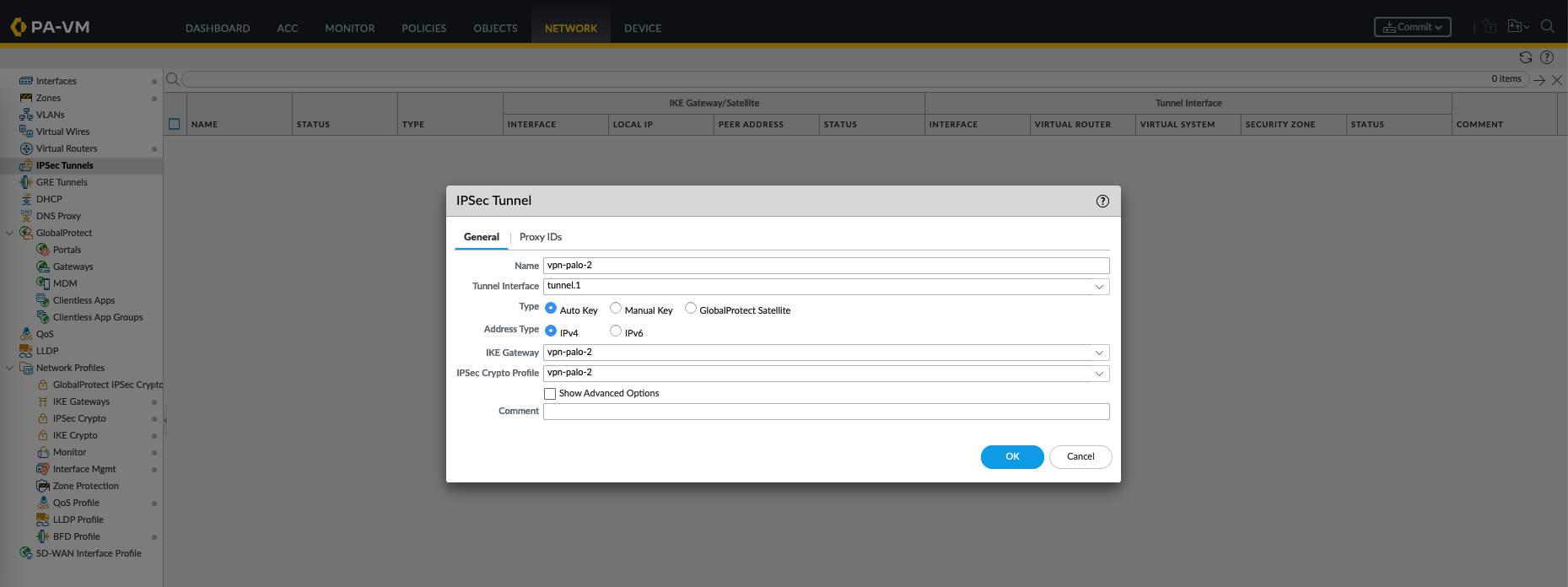
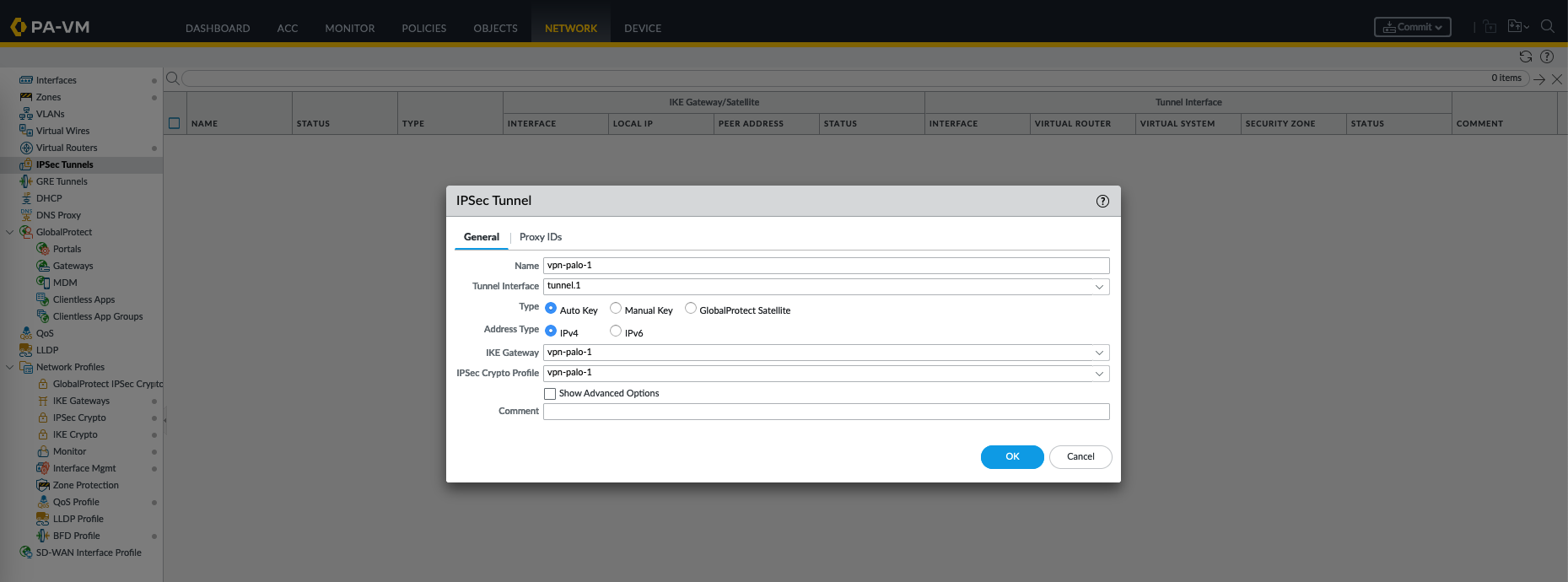
Next, create the IPSec tunnel using all the profiles created earlier
IPSec tunnel is the actual secure communication channel established between the Palo Alto and remote device, which is the other Palo Alto device.
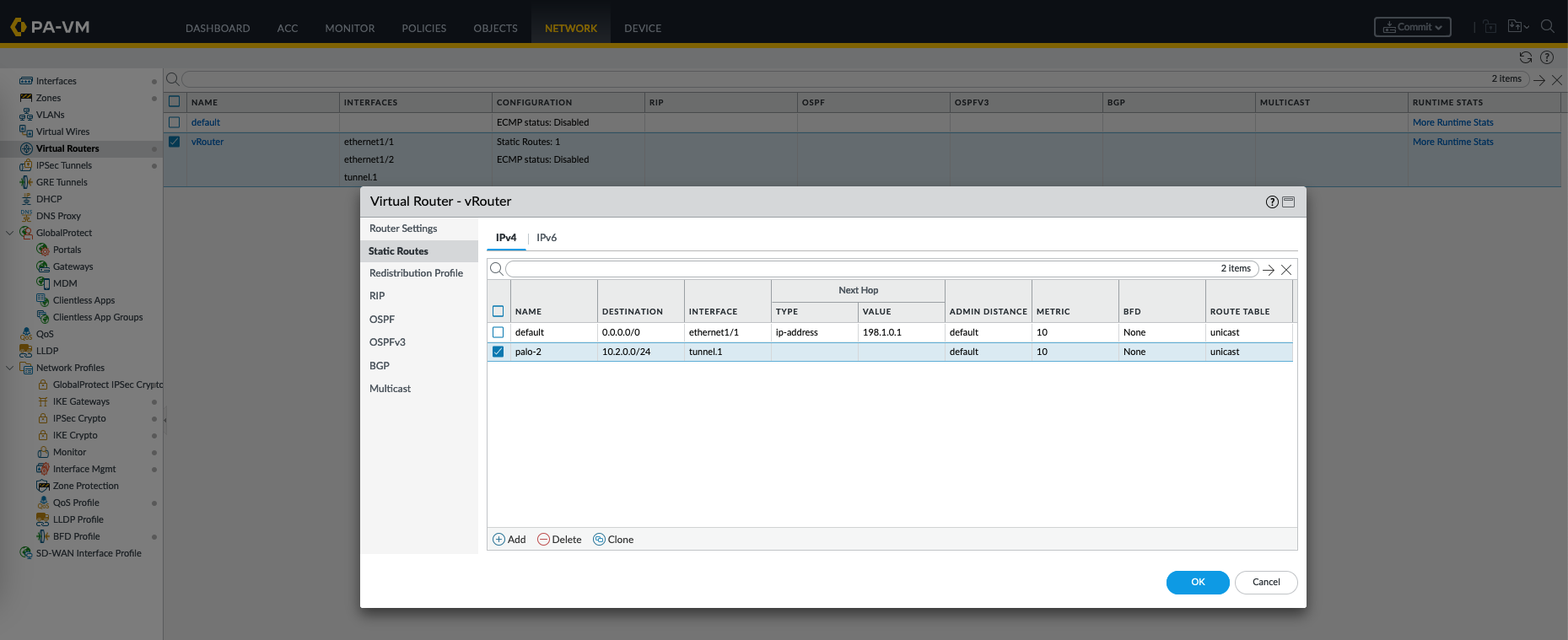
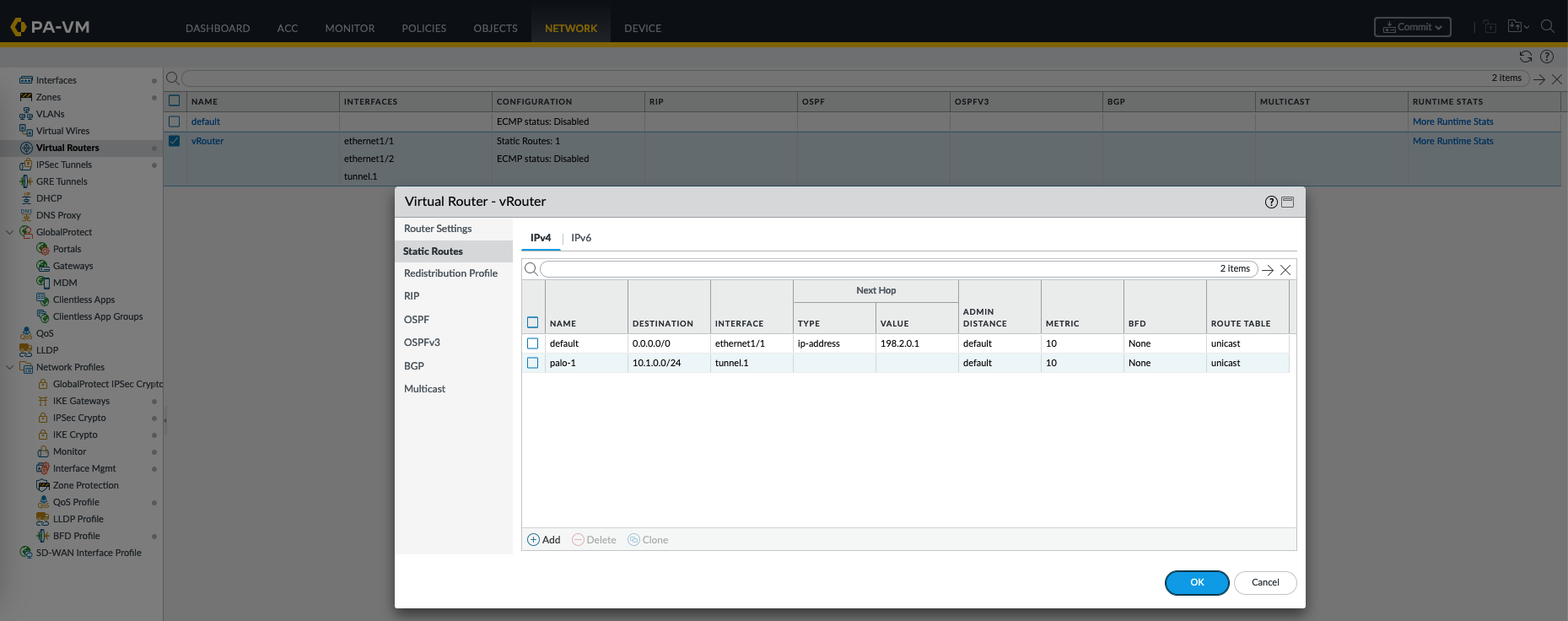
Lastly, create a routing rule to forward the designated traffic to the tunnel interface
Configuring IPSec VPN on Palo-2 device
On the other end device (Palo-2), we just pretty much mirror the entire configuration from the Palo-1
Validating S2S IPSec VPN
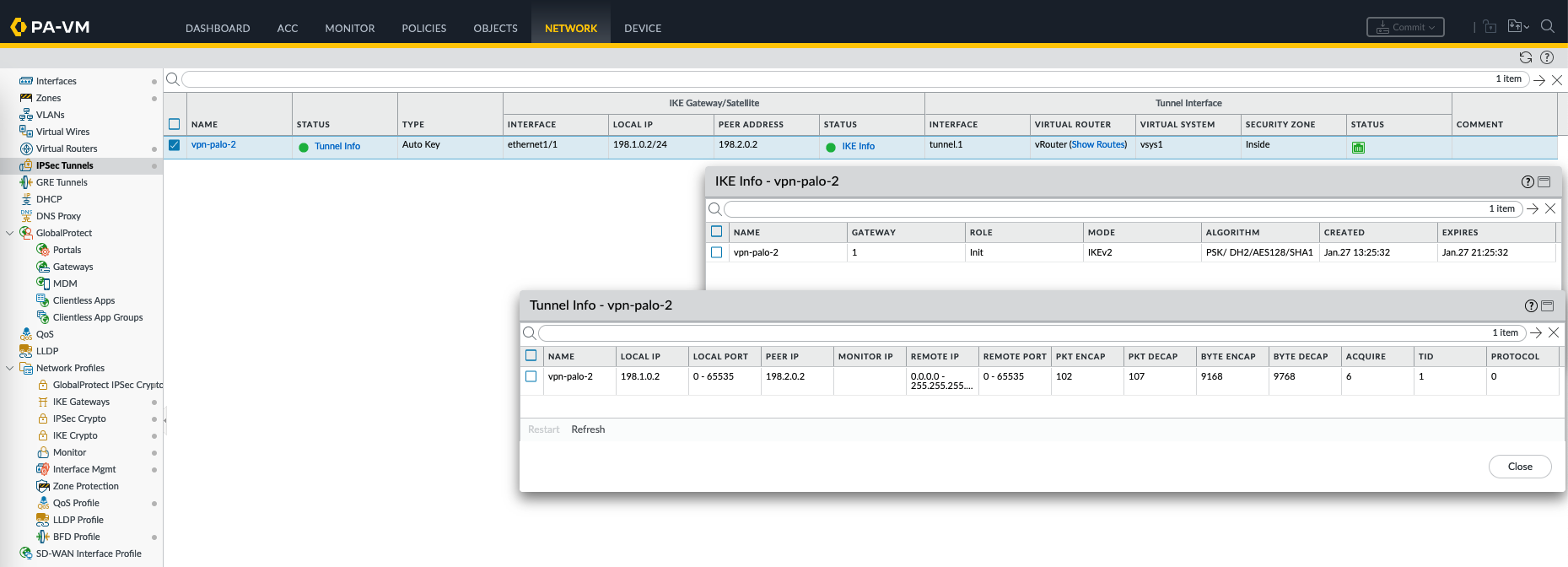
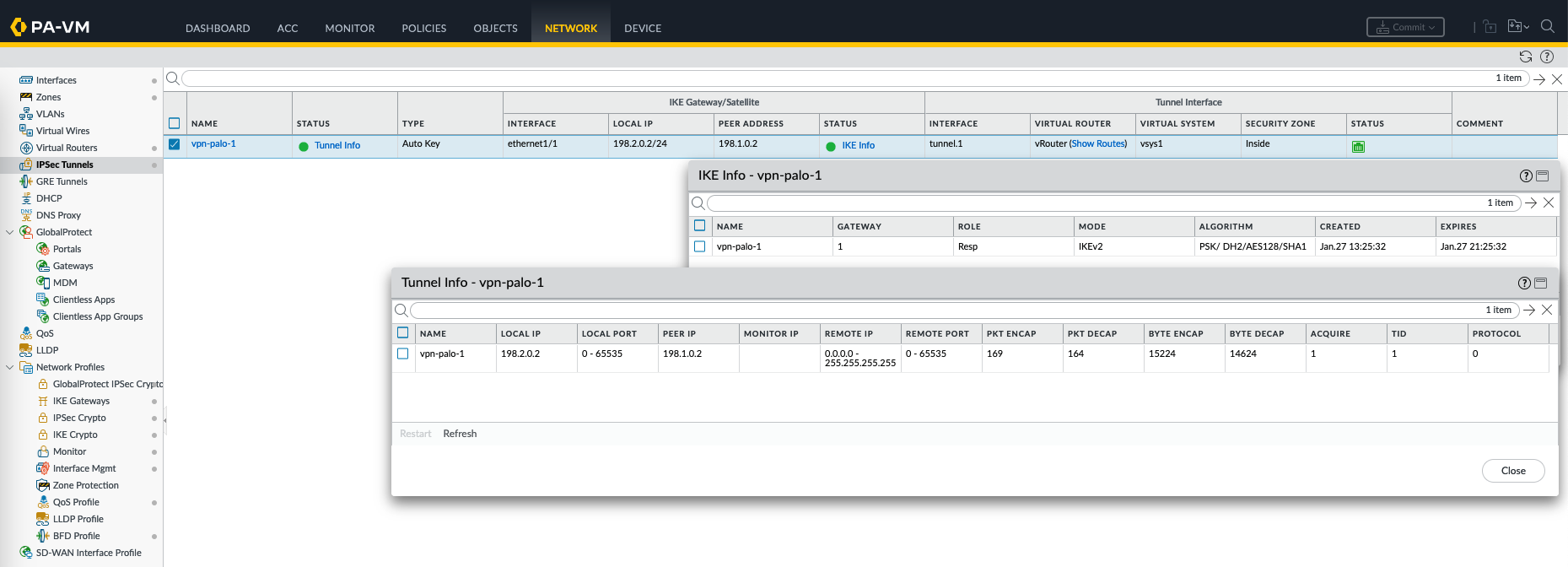
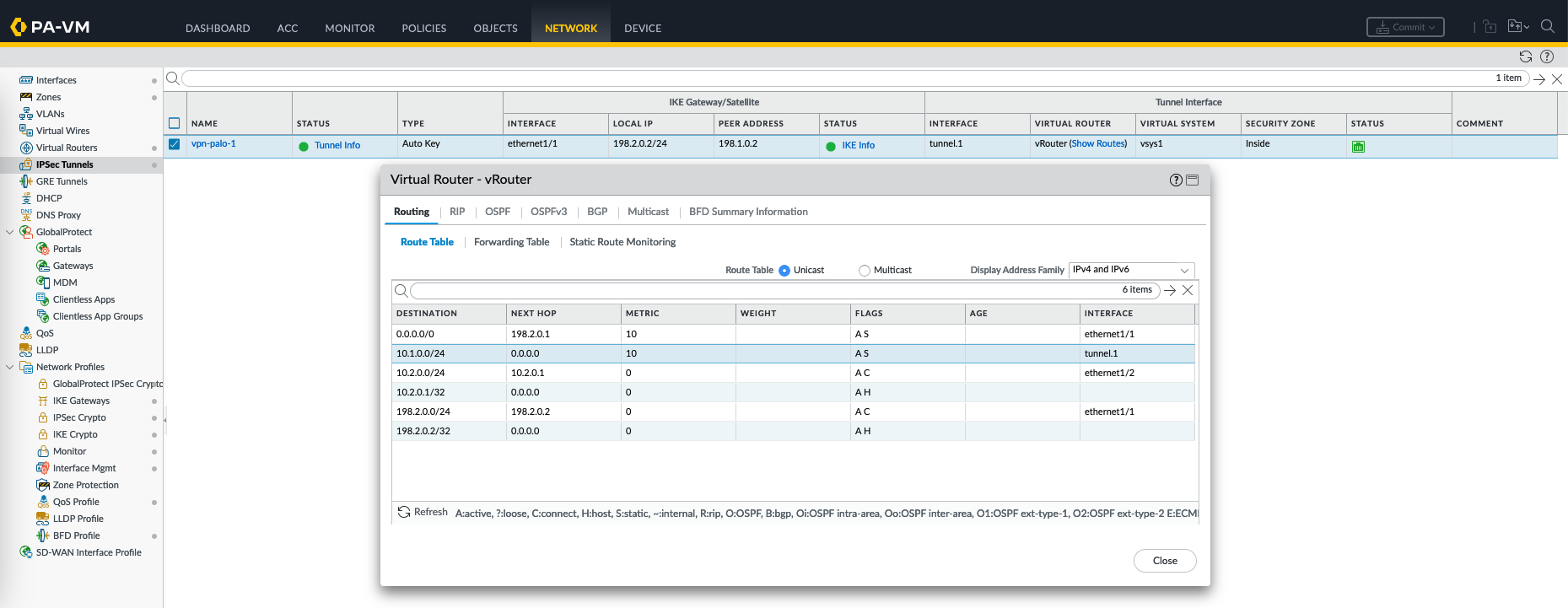
Now on IPSec tunnel on Palo-1, we should see the IPSec tunnel being established
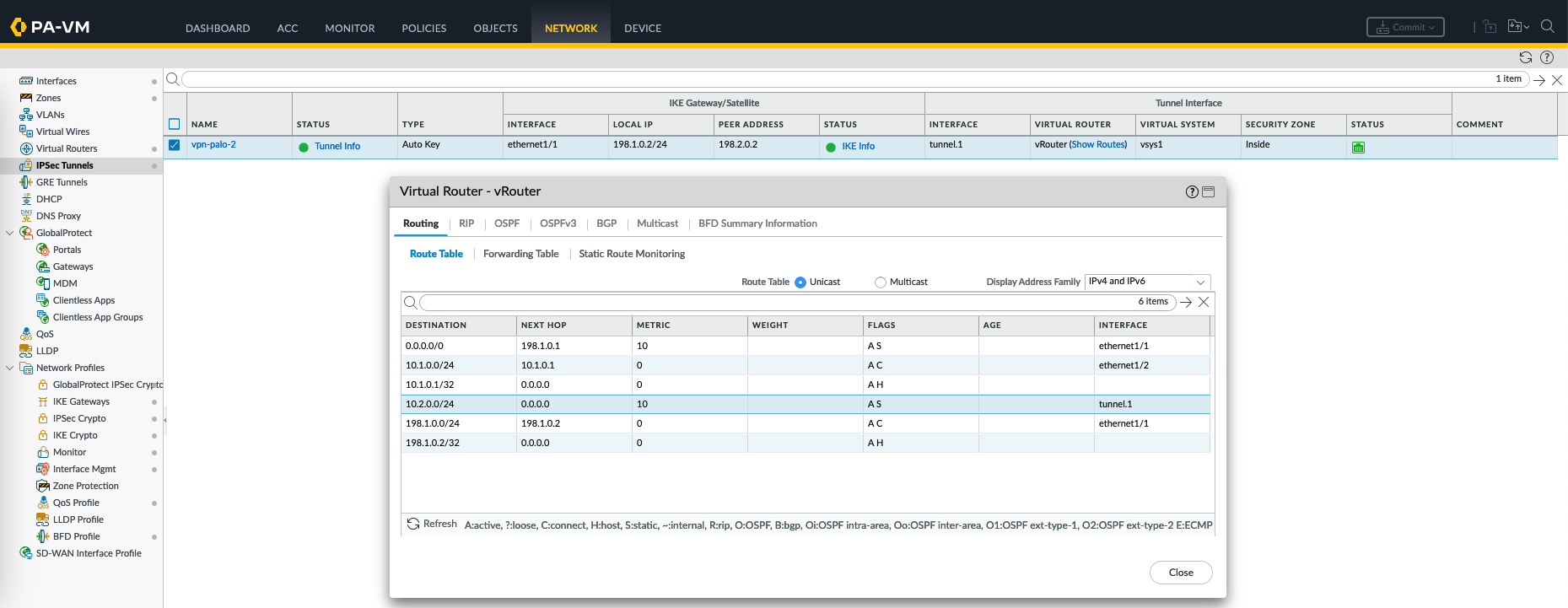
On the routing table, we can validate the 10.2.0.0 is forwarded to the tunnel interface
Same goes on the Palo-2
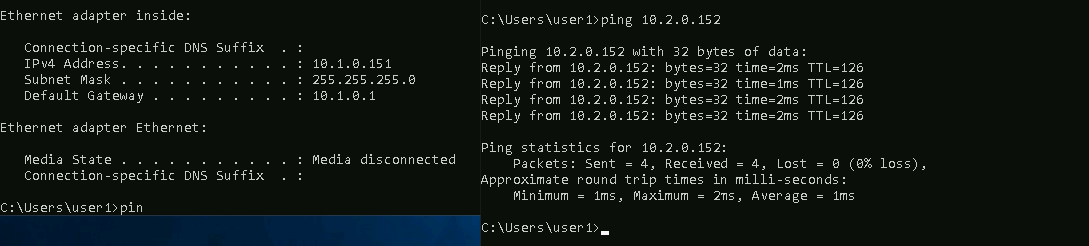
On a pc client on Palo-1, we can confirm that the traffic is going though to Palo-2
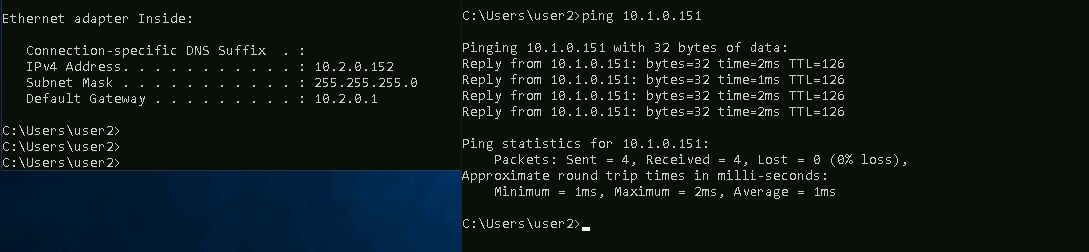
Same goes the vice versa
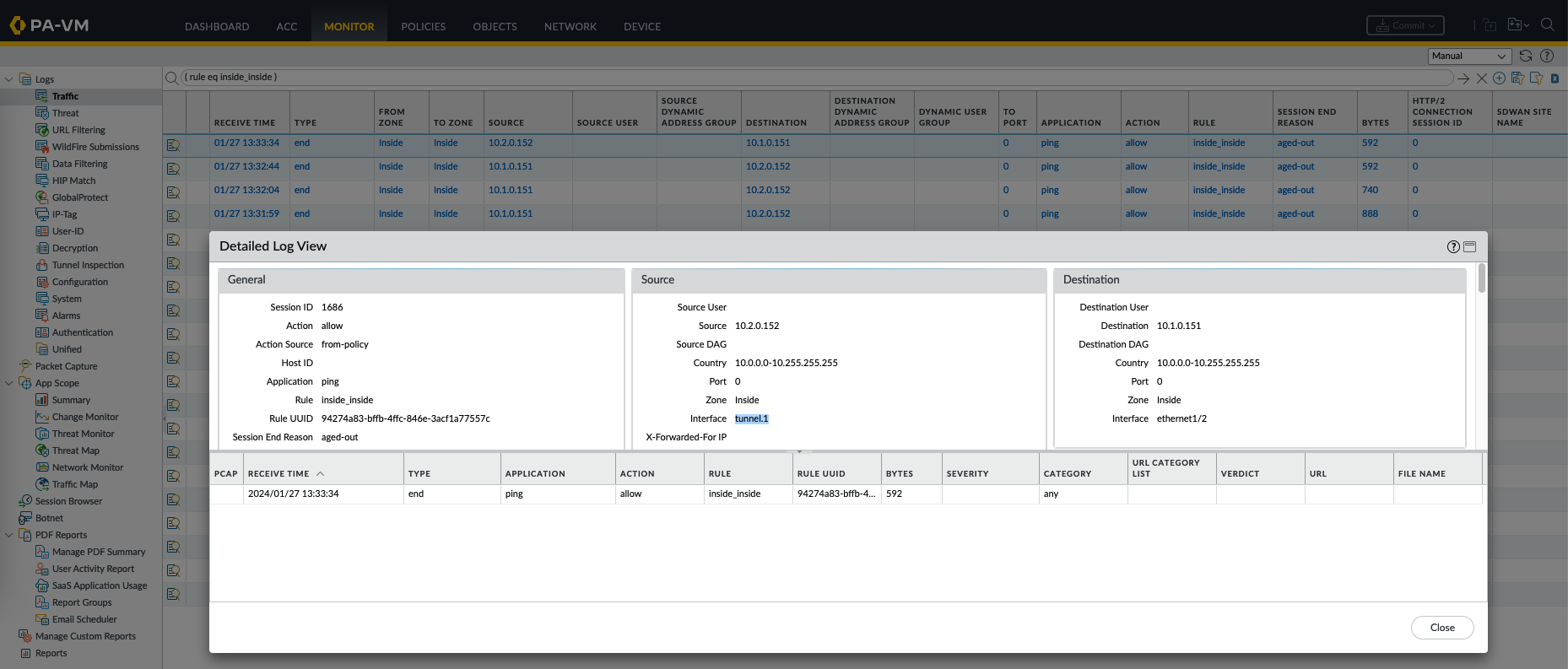
Monitoring the traffic, we can see that the traffic is indeed going though the tunnel interface