Palo Alto - SIG Tunnel to Cisco Umbrella
A Secure Internet Gateway (SIG) is a cloud-based service that provides secure and filtered access to the internet for users and devices within an organization.
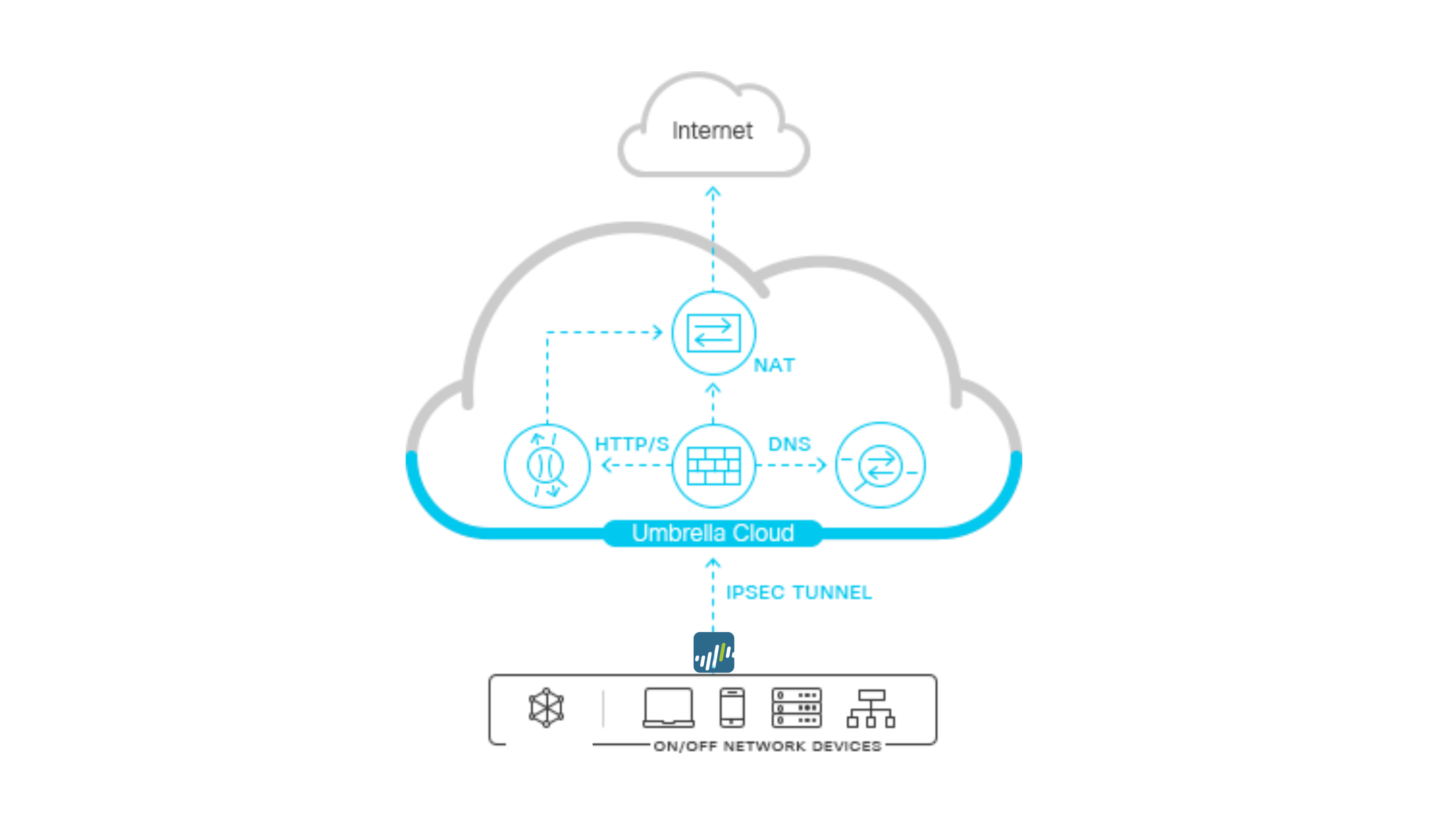
Cisco Umbrella SIG uses tunnels to establish secure connections between Palo Alto’s network and the cloud-based Umbrella service. This tunnel encrypts the traffic between Palo Alto and Umbrella service, ensuring the confidentiality and integrity of data as it travels over the internet.
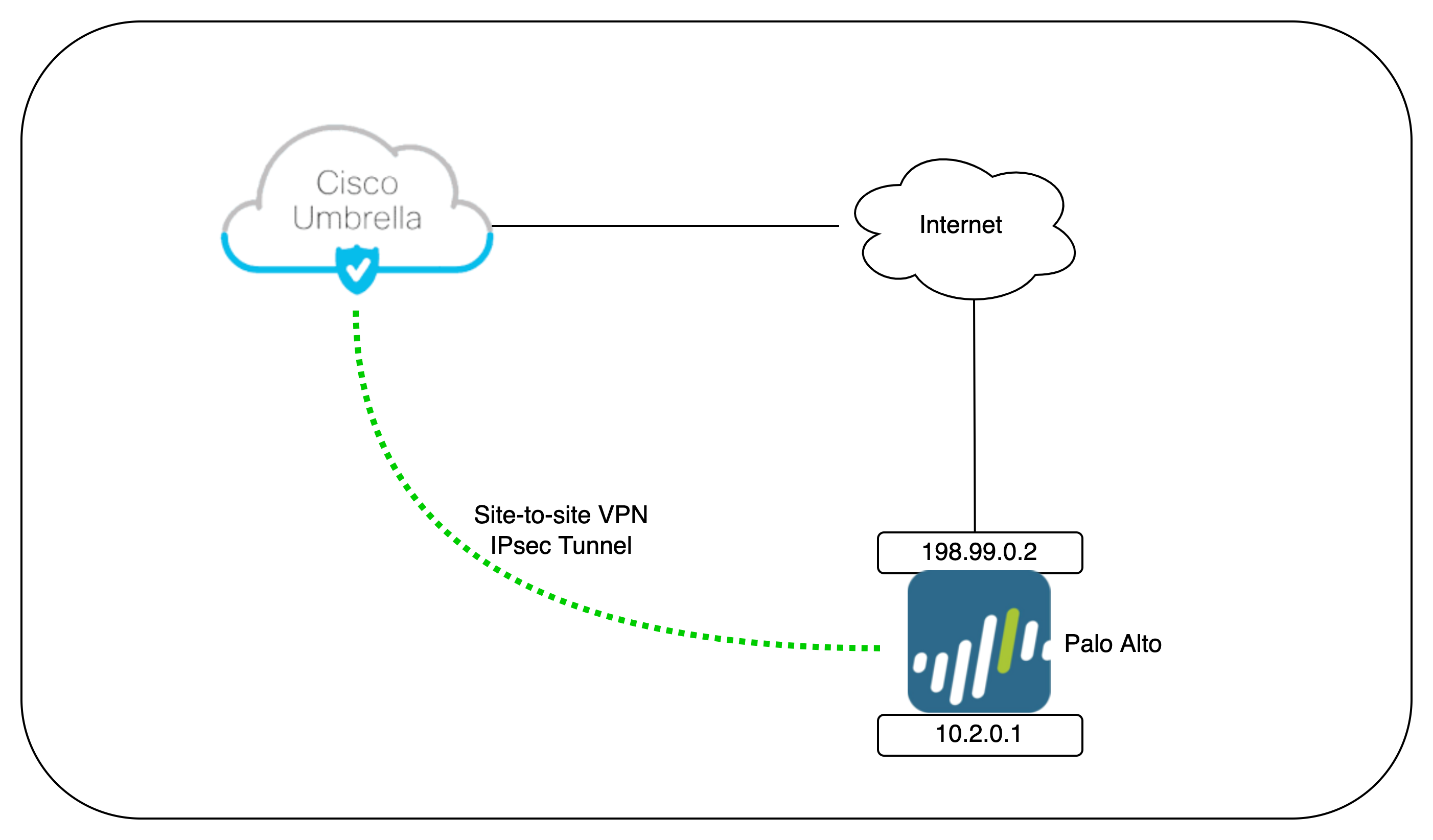
Deployment Topology
On this deployment, we will establish a Site-to-site VPN IPsec Tunnel connection between the Palo Alto and the Umbrella Cloud, making all the internet traffic coming form the Inside Segment will be routed to the Umbrella first before heading to the Internet
Configuring Network Tunnel on Umbrella
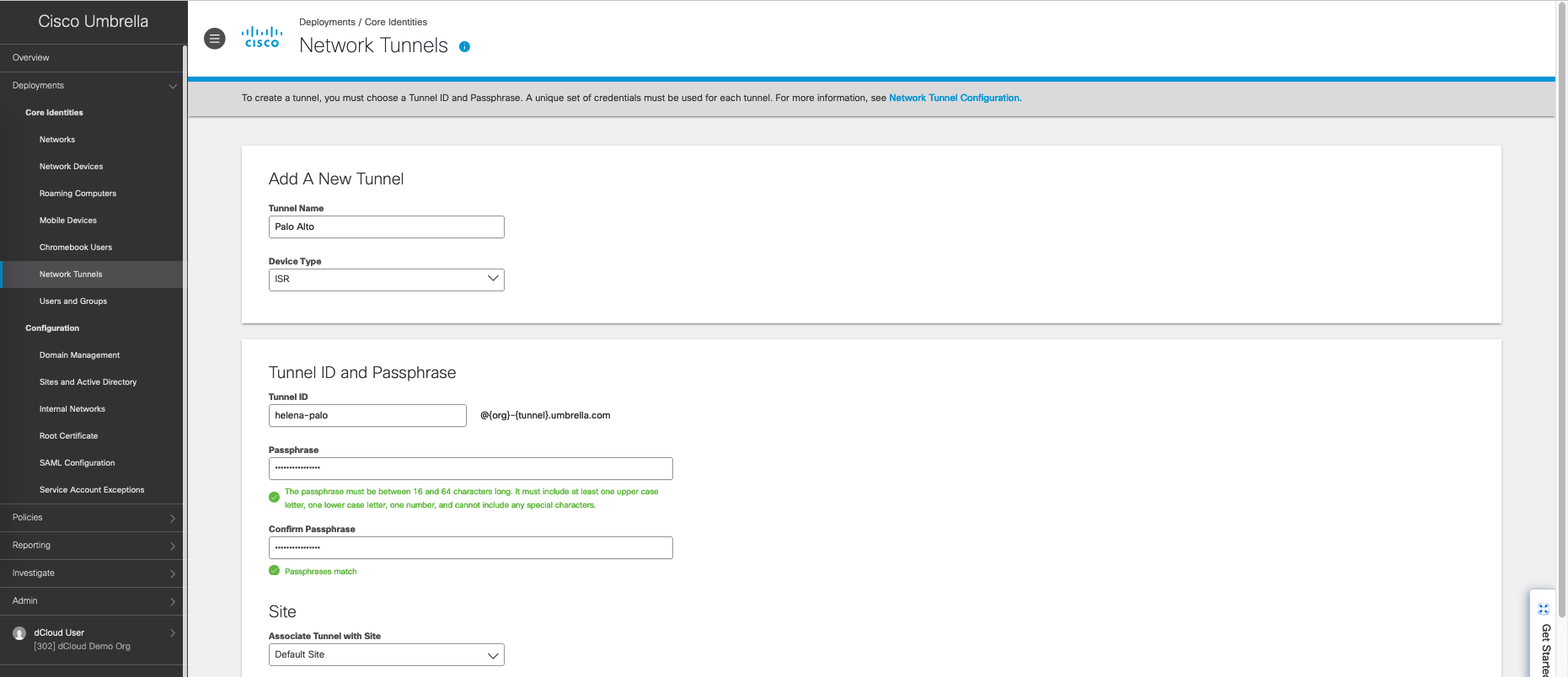
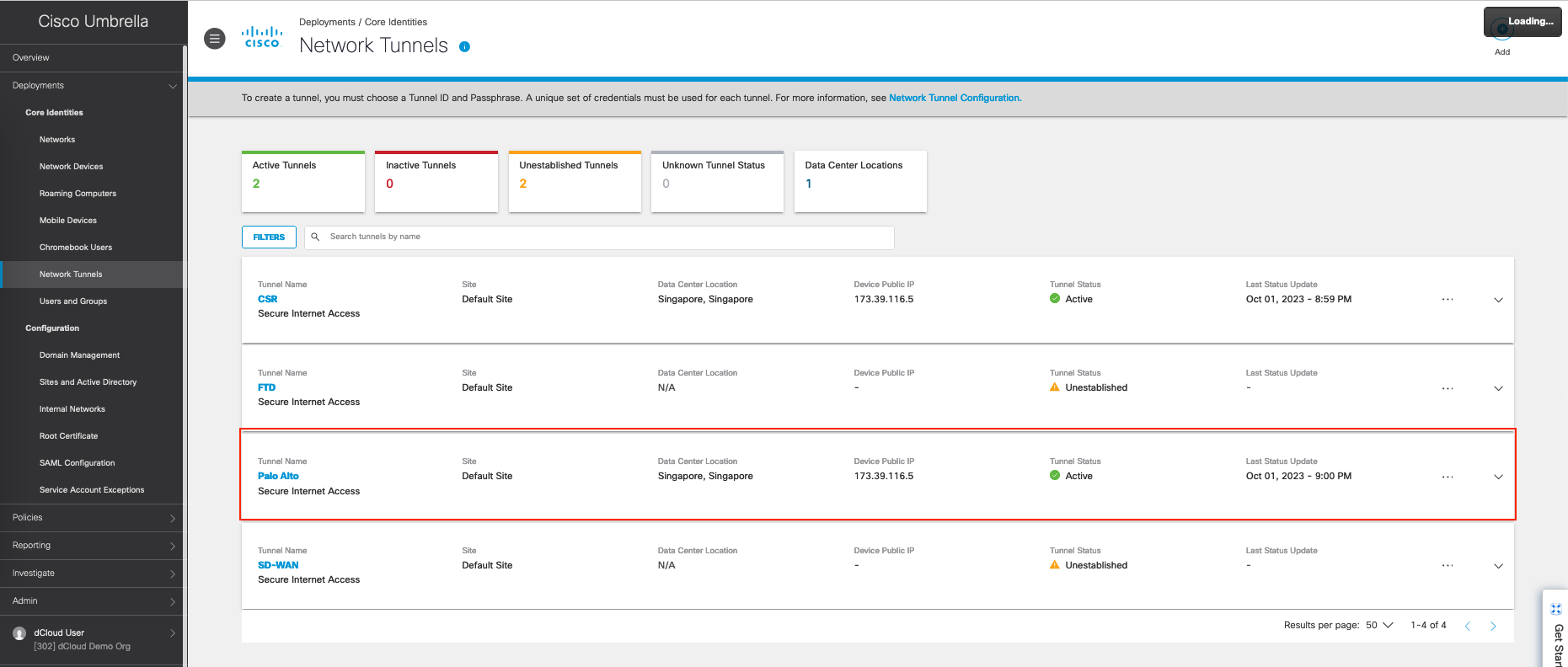
On Cisco Umbrella, go to Deployments » Network Tunnels, add new for Palo Alto
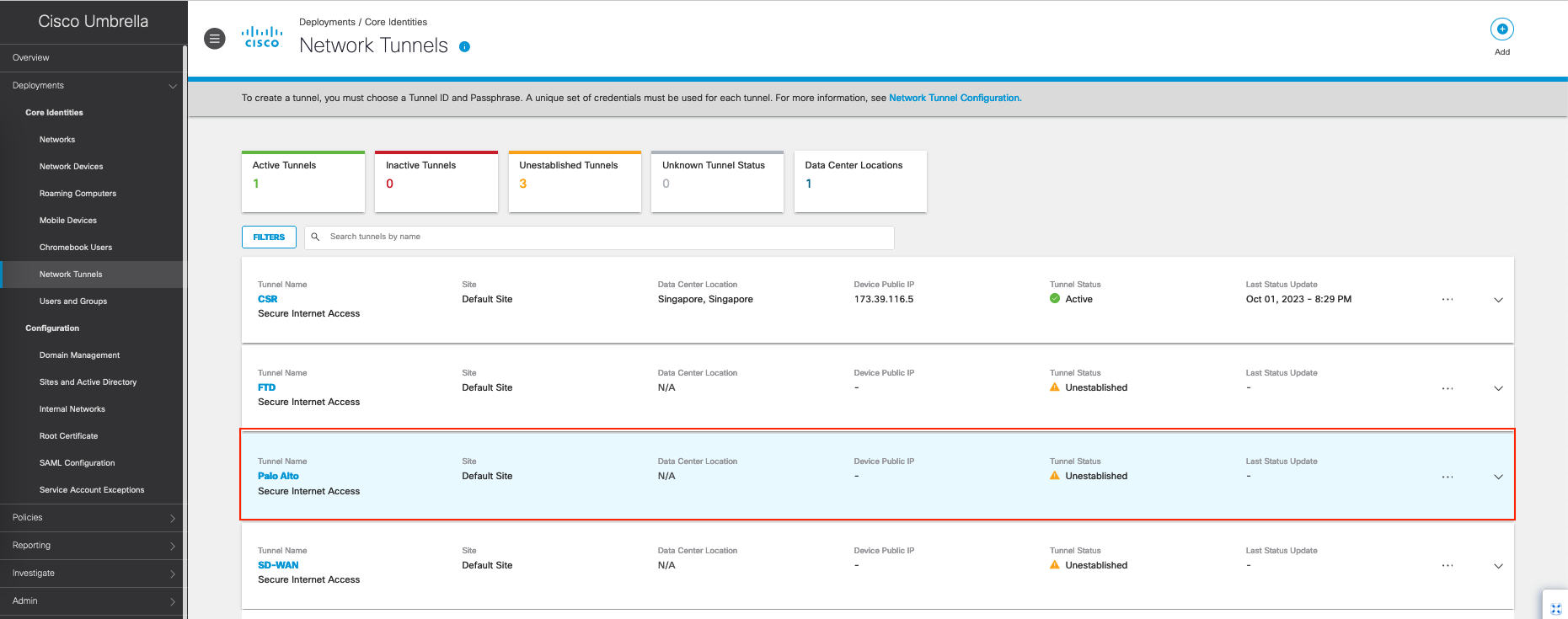
Here’s after the tunnel added, the entry is present with status of Unestablished
Configuring Network Tunnel on Palo Alto
Cisco provides a decent deployment guide here to configure tunnel on Palo Alto
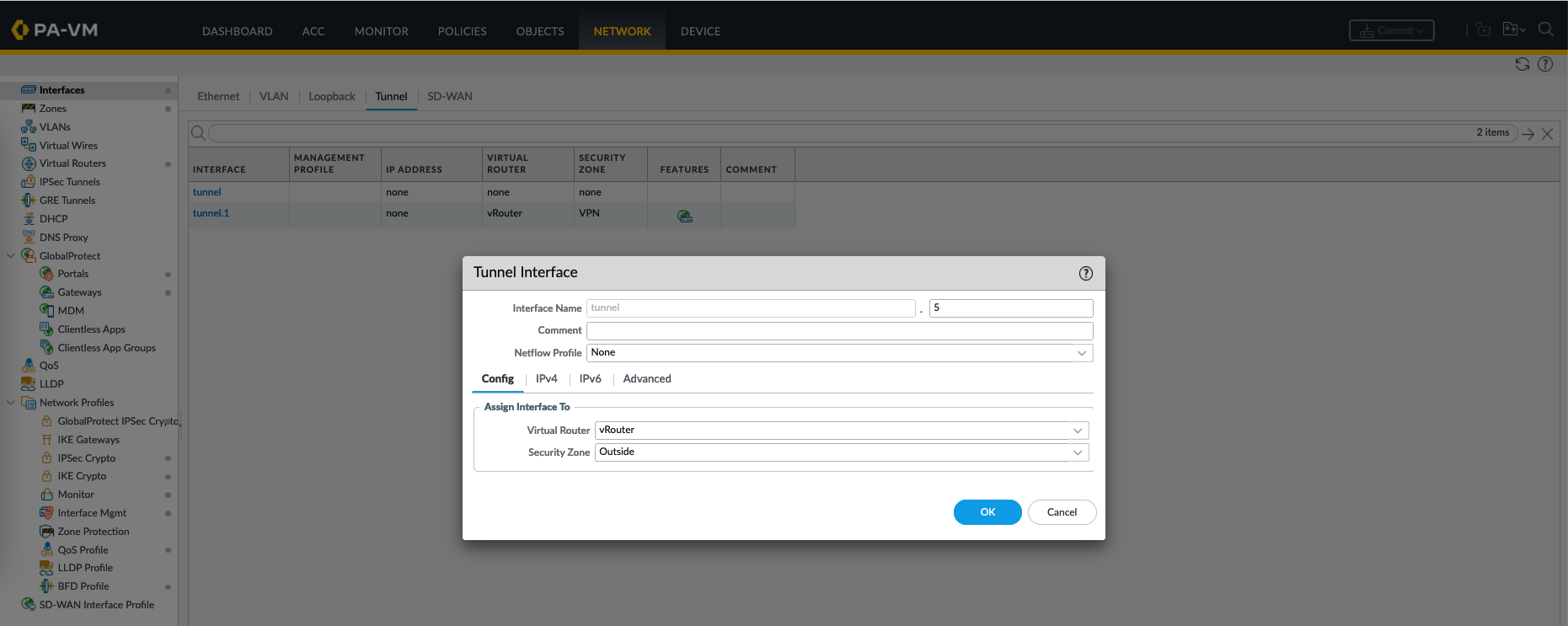
First creata a new Tunnel Interface
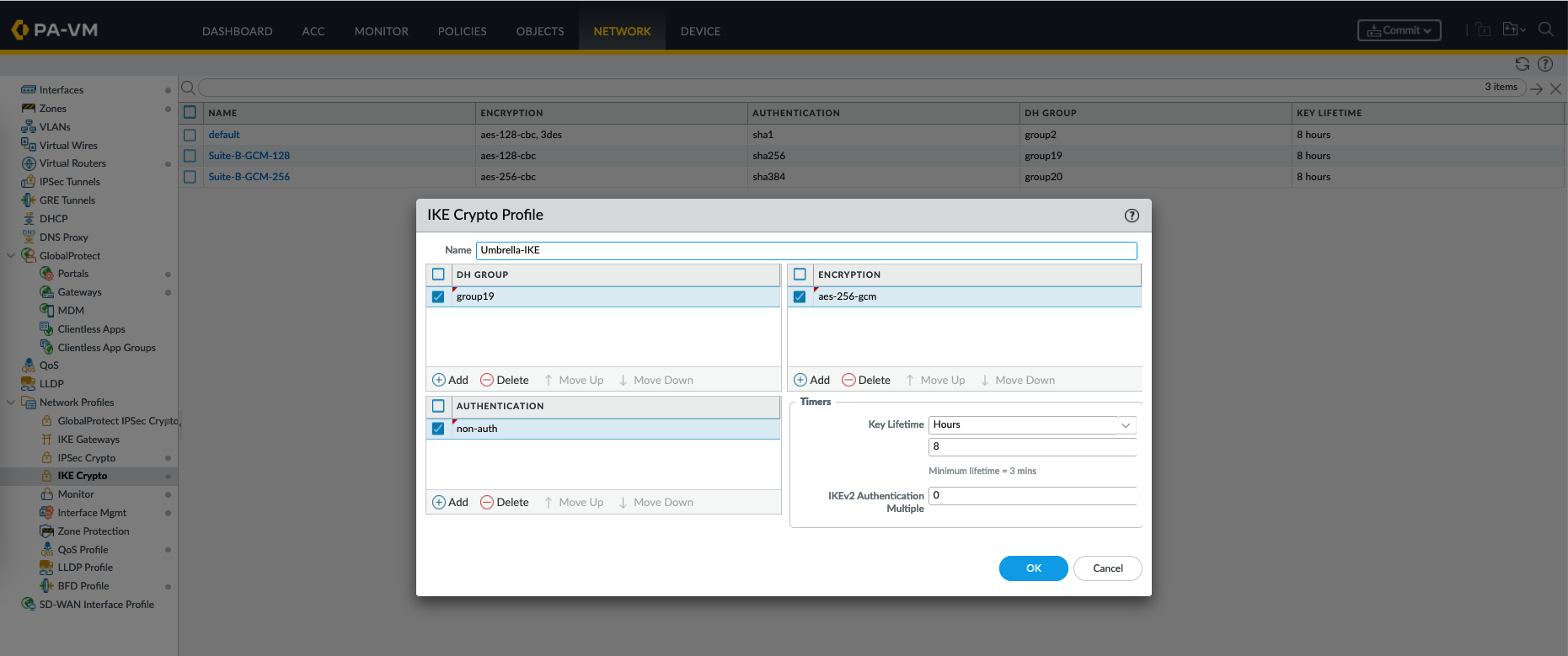
Next create a IKE Crypto Profile
An IKE (Internet Key Exchange) Crypto Profile is a configuration that defines the parameters and settings used for the initial phase of establishing a VPN tunnel. It includes the encryption and authentication methods to be used during the key exchange process.
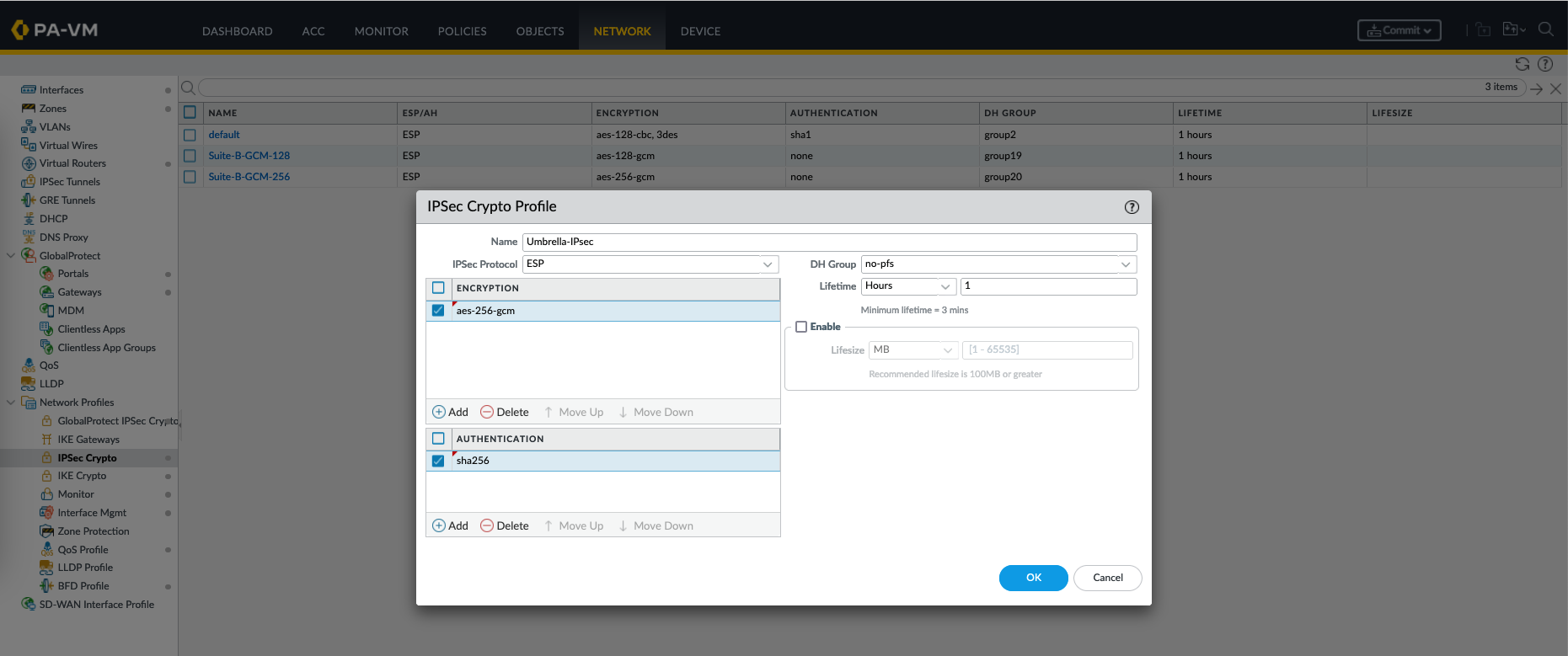
Next create an IPSec Crypto Profile
An IPSec (Internet Protocol Security) Crypto Profile is a configuration that defines the parameters and settings used for the second phase of establishing a VPN tunnel, which involves securing the data traffic between two sites. It specifies the encryption and authentication methods for protecting the actual data transmitted over the VPN tunnel.
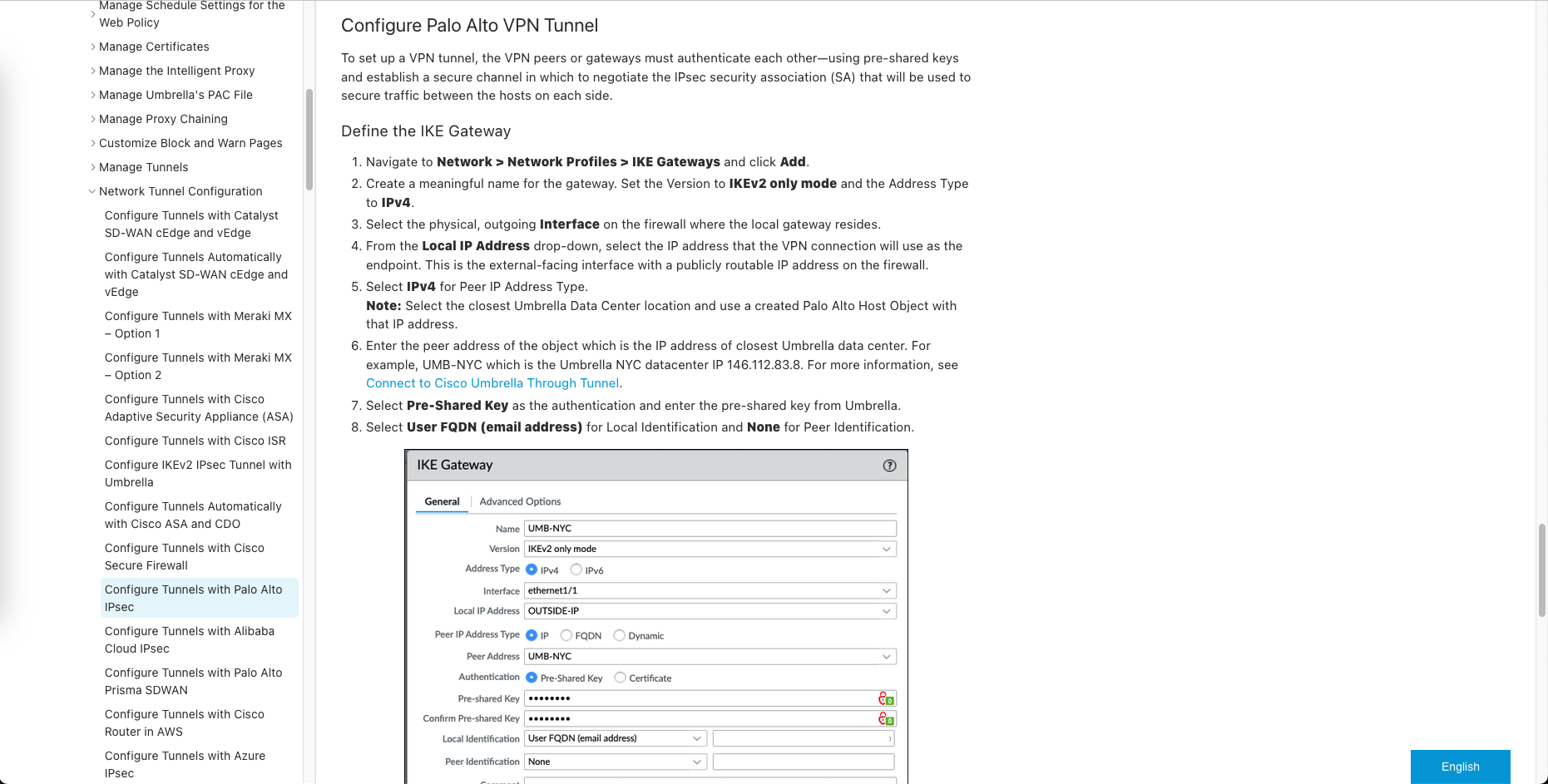
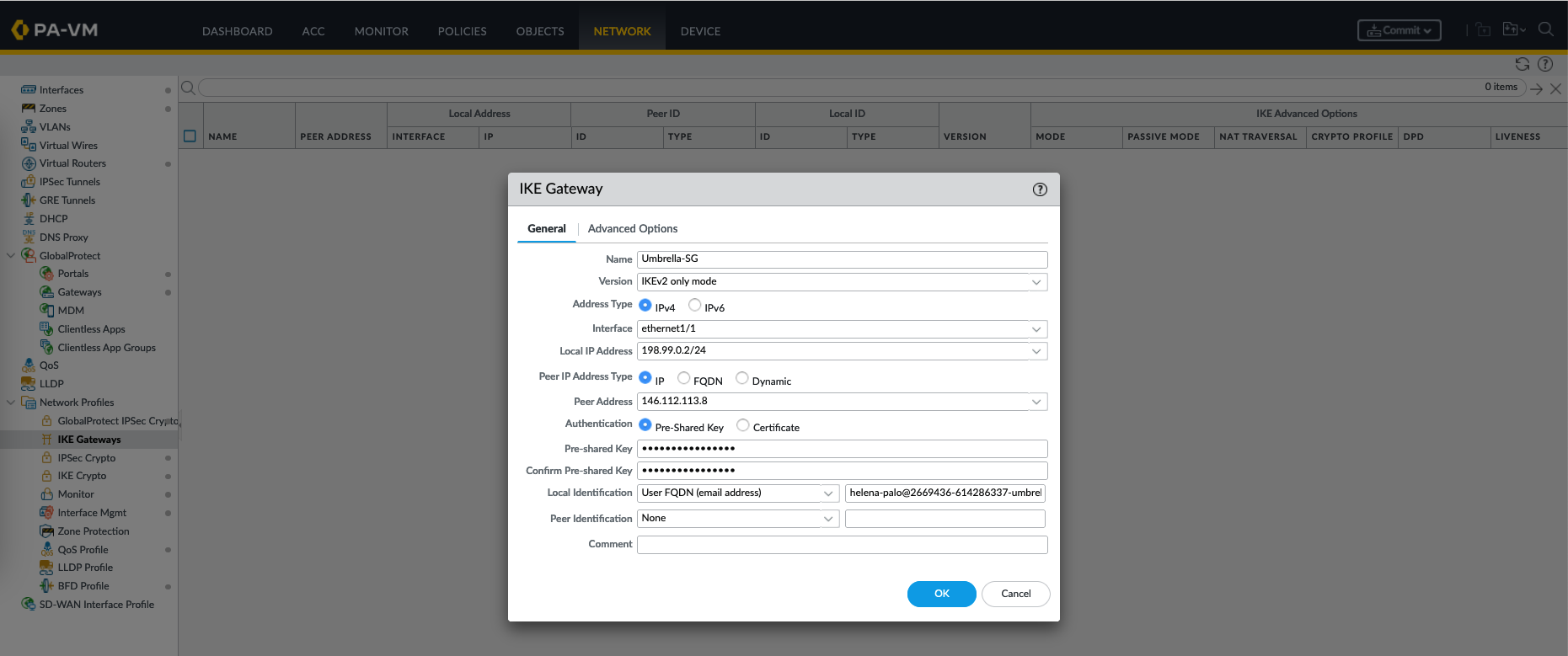
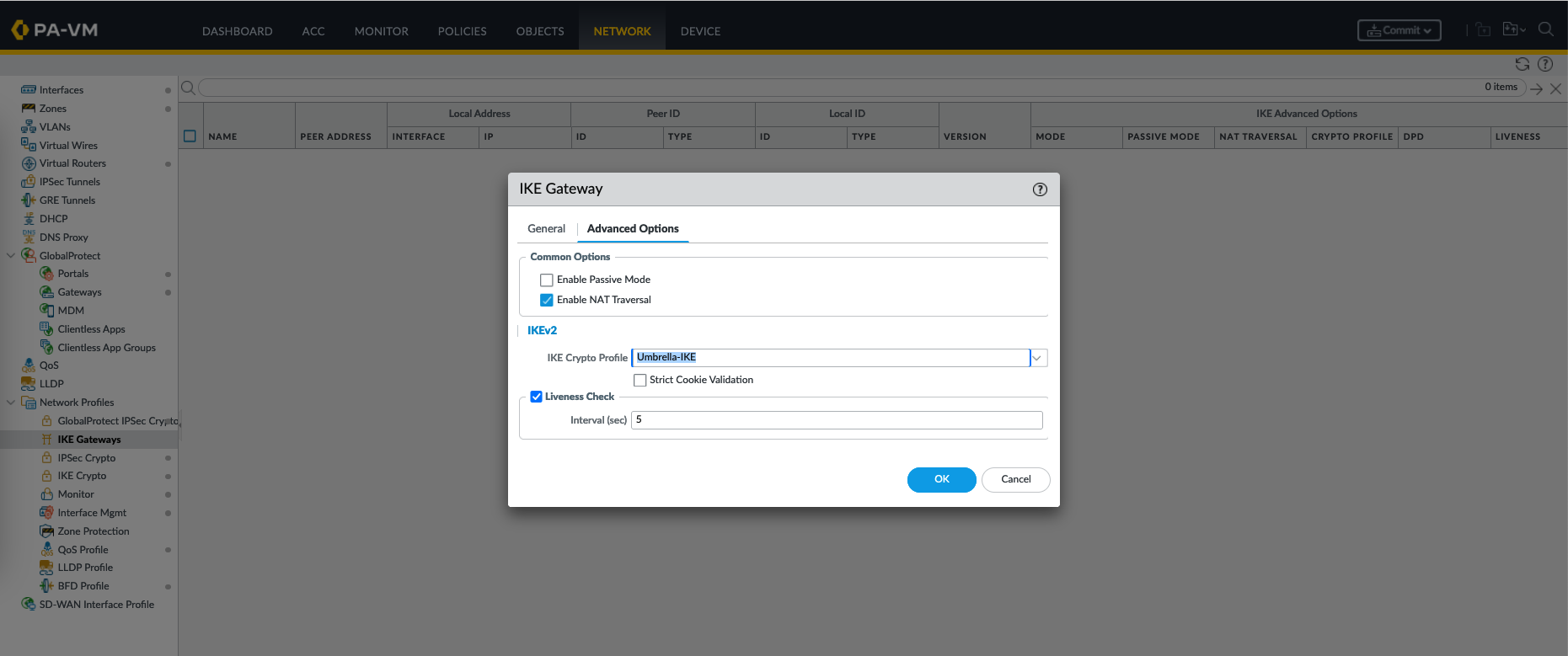
After that create an IKE Gateway
An IKE (Internet Key Exchange) Gateway is a configuration that defines the properties of a remote peer or site with which the firewall will establish a VPN tunnel. It includes information such as the remote peer’s IP address, pre-shared key, and the specific IKE Crypto Profile to be used for key exchange.
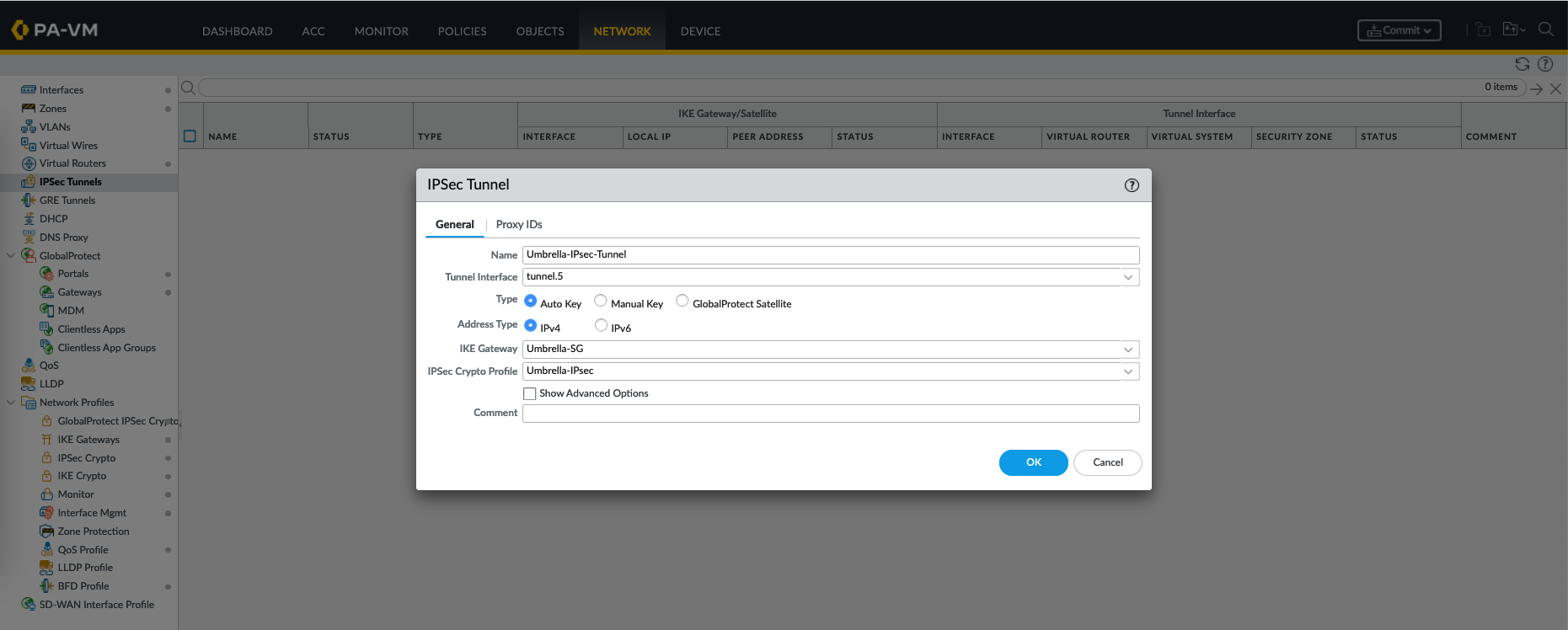
Finally create the IPSec Tunnel
IPSec tunnel is the actual secure communication channel established between the Palo Alto and remote device (Umbrella), using the profiles configured earlier
Commit the changes.
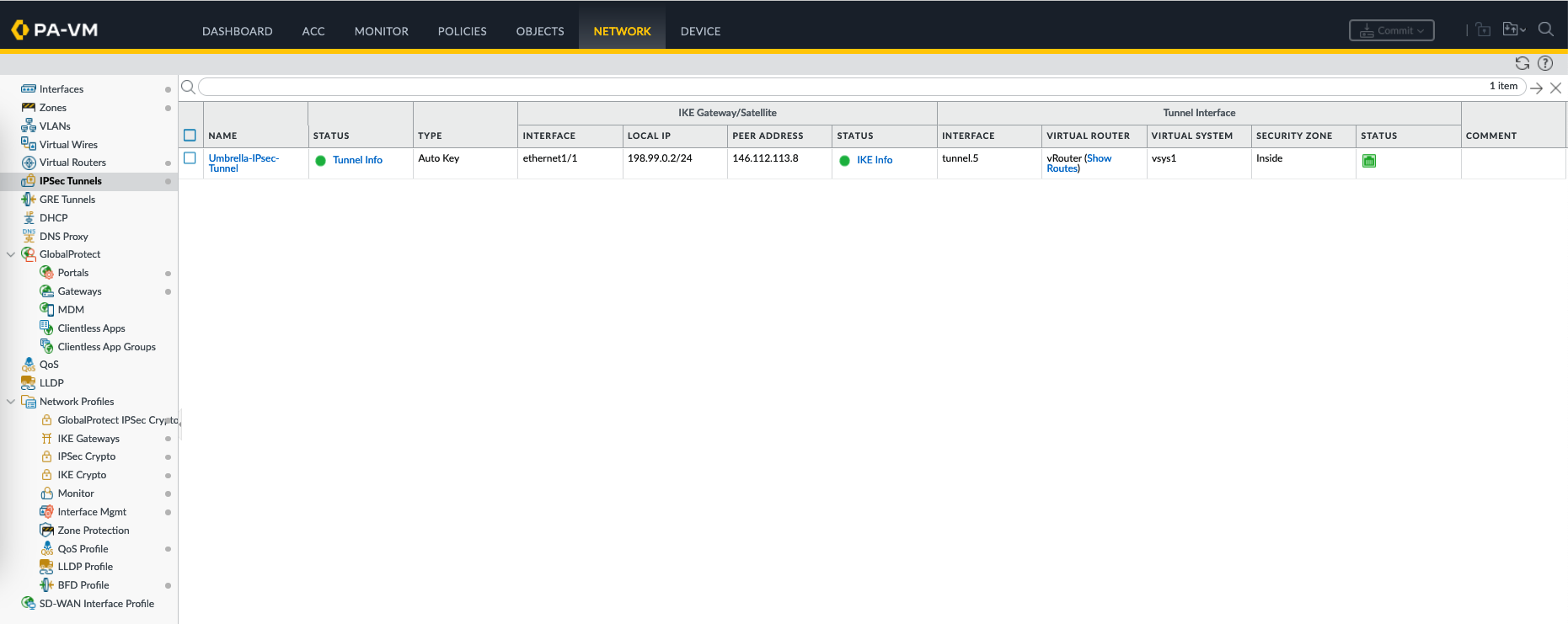
Verfying the Tunnel Connection
After commited, now the IPSec tunnel status on Palo Alto should be Up
Over on the other end on Umbrella, the Network Tunnel can also be seen Up and Active
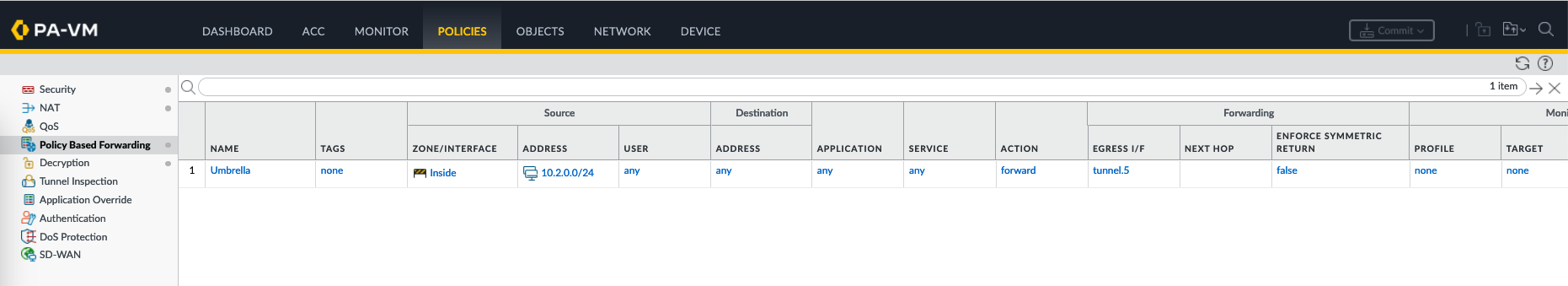
Lastly before testing the traffic, create a Policy Based Forwarding (Policy-based Routing/PBR) to send traffic from client’s segment to the tunnel
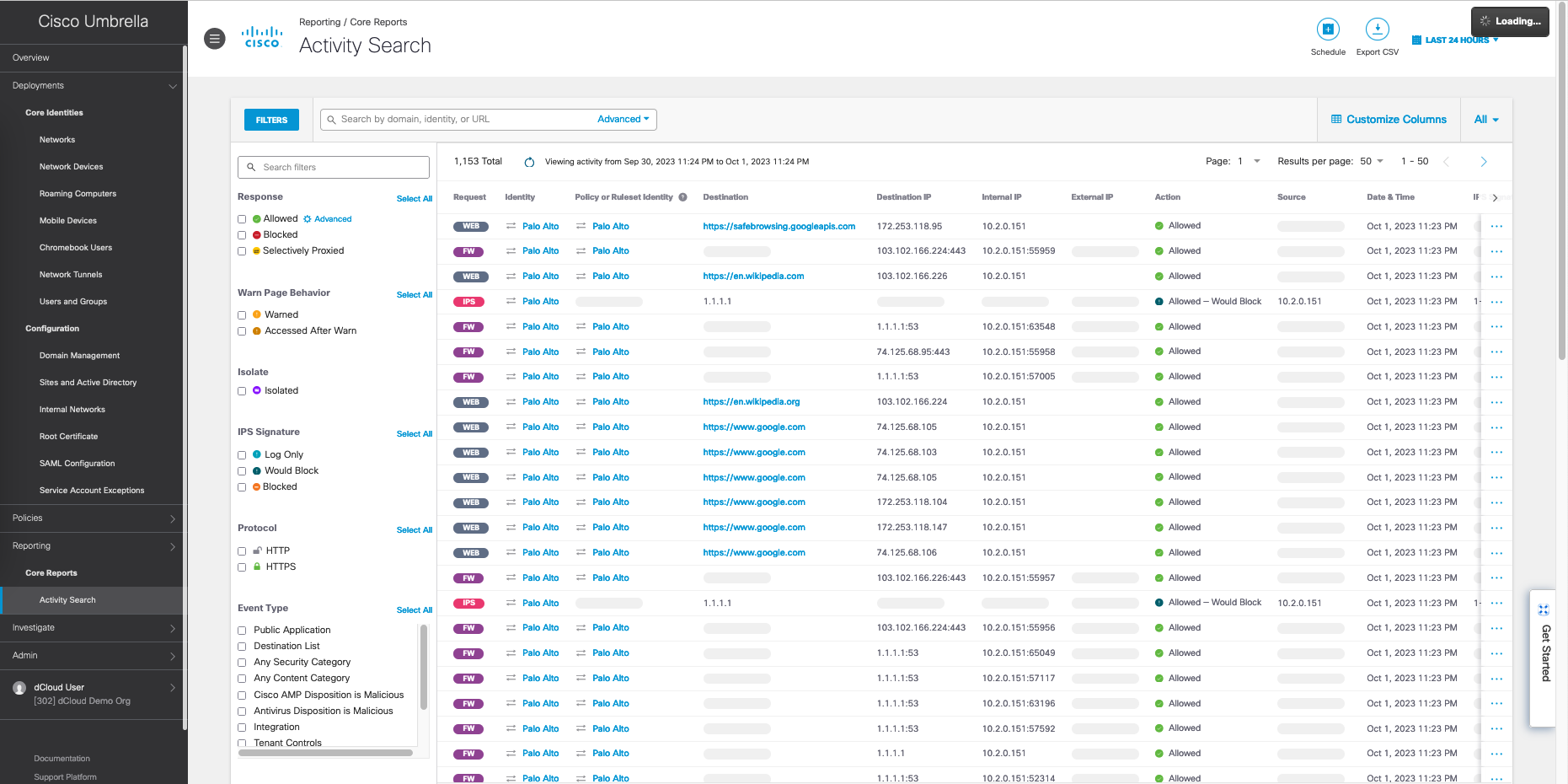
And now all internet traffic will be proxied by Umbrella, acting as the Secure Internet Gateway
Here we can see the reports of the traffic coming from the palo’s internal segment is inspected before being forwarded to the actual destination on the internet