Palo Alto Panorama
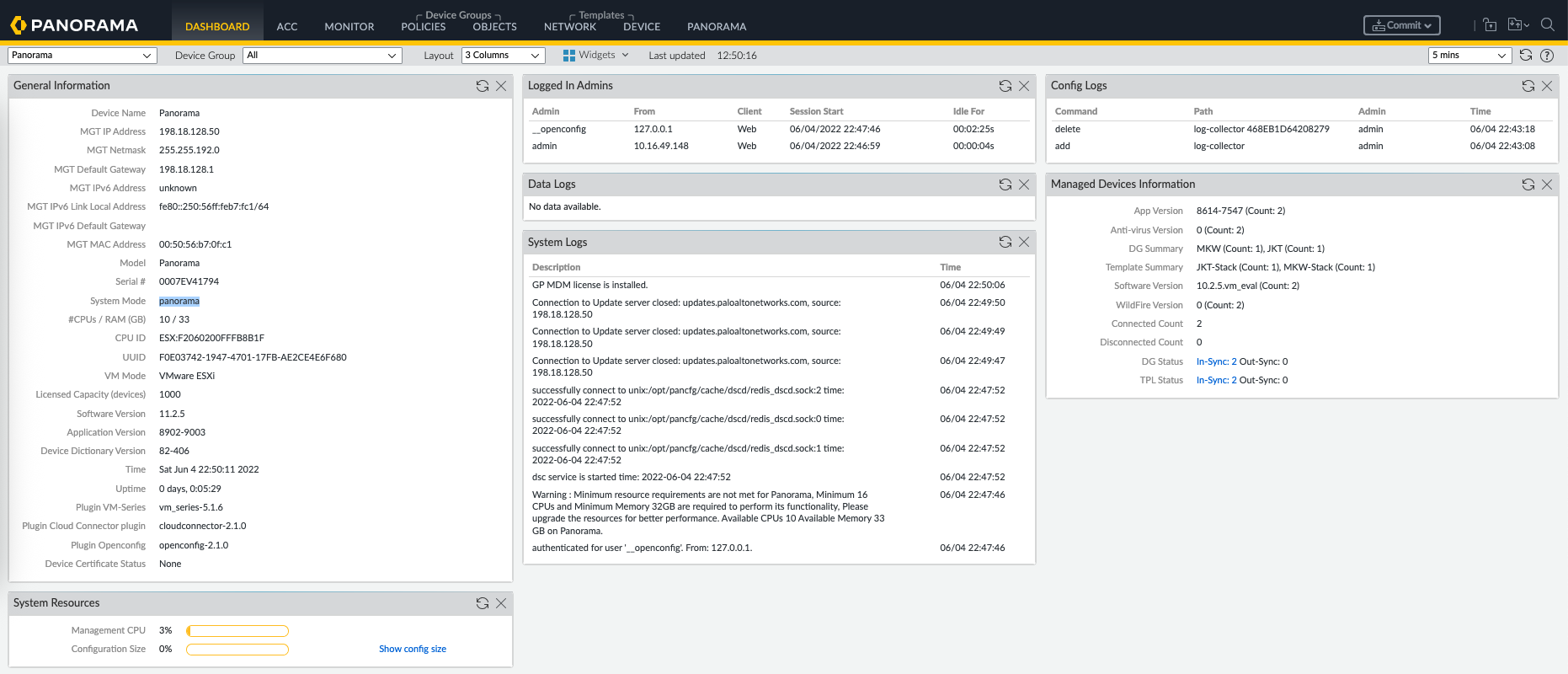
Panorama is Palo Alto Networks’ centralized management solution that allows administrators to manage multiple Palo Alto firewalls from a single interface. It provides centralized configuration, policy management, visibility, logging, and reporting, making it easier to enforce consistent security policies across large and distributed environments.
Installing Panorama
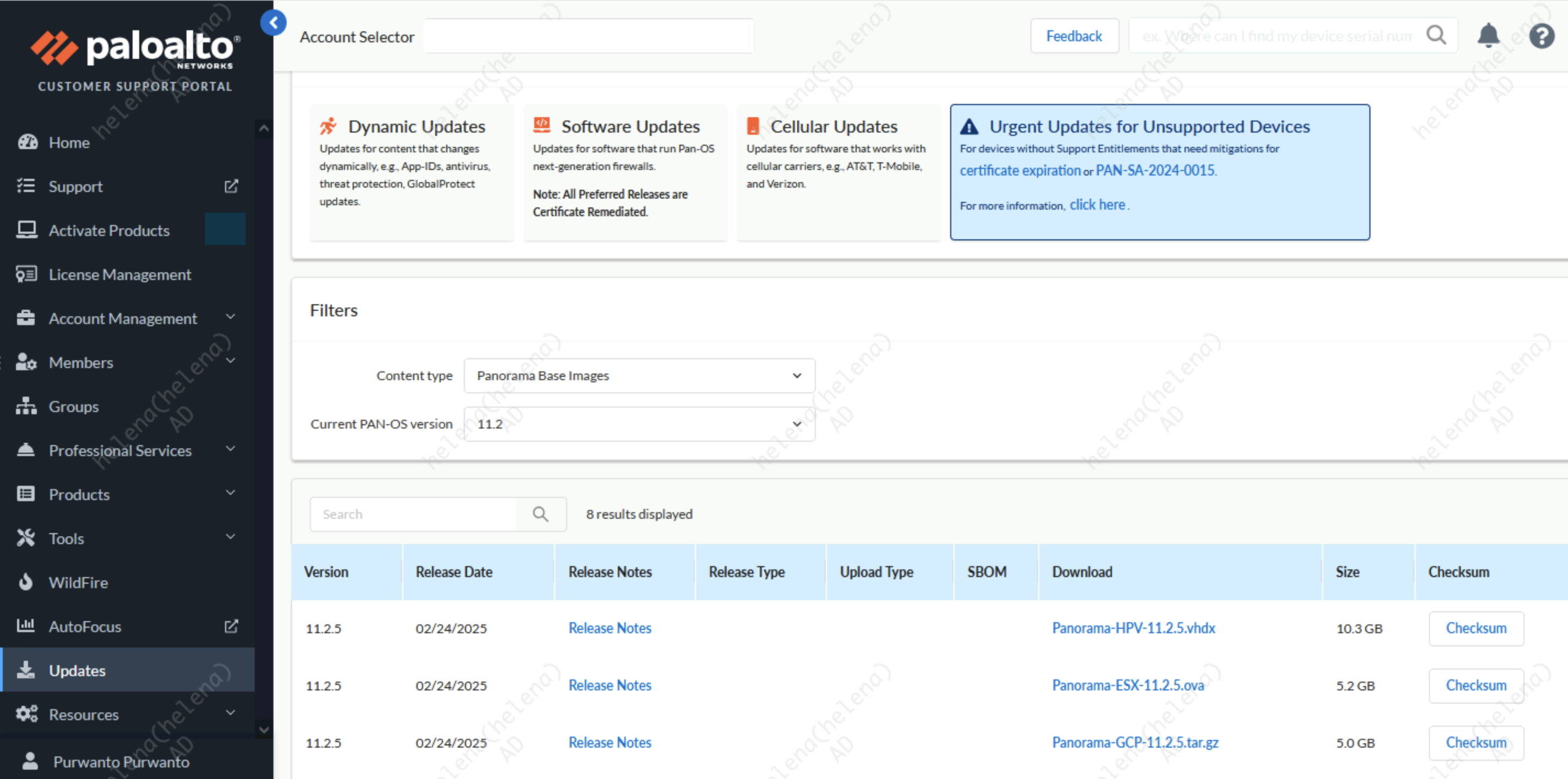
To download Panorama, you do need a customer support account
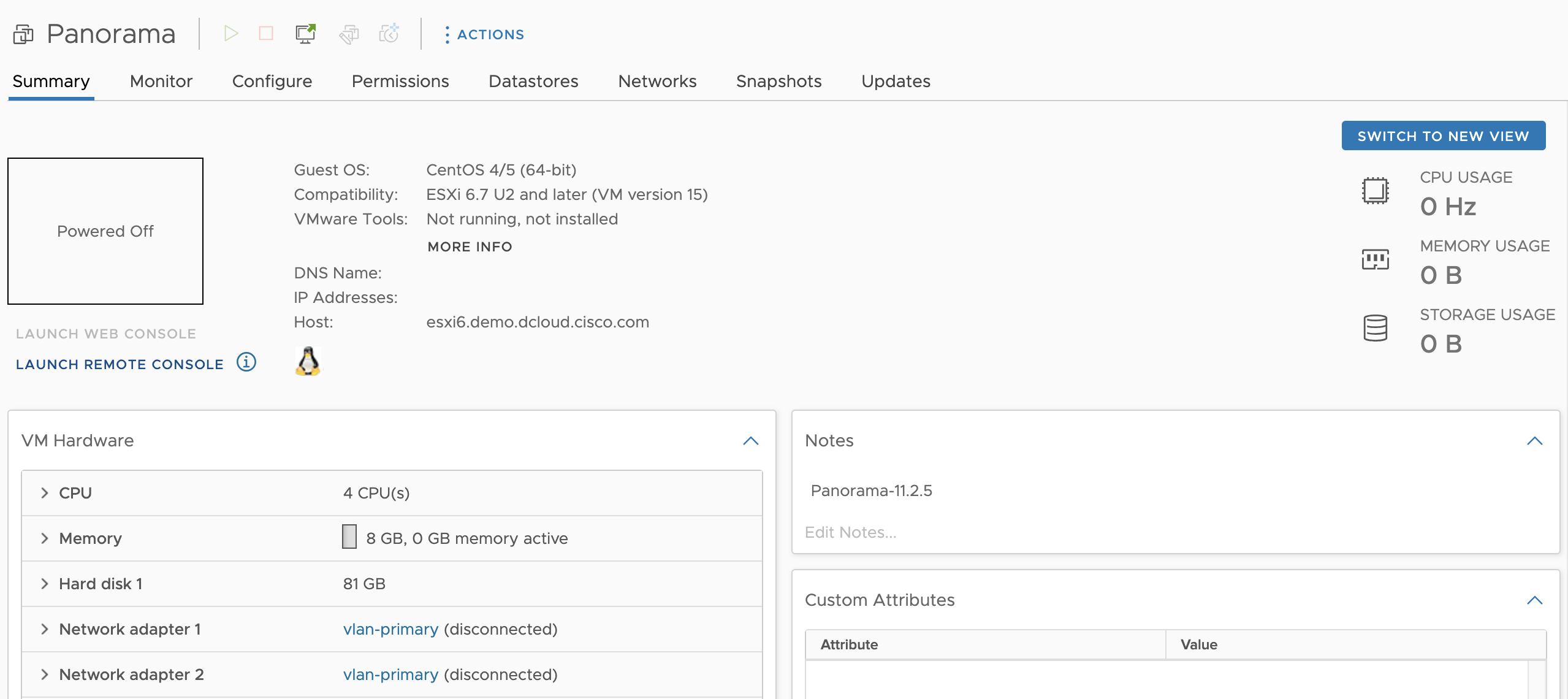
Then we can deploy the ova and boot it up
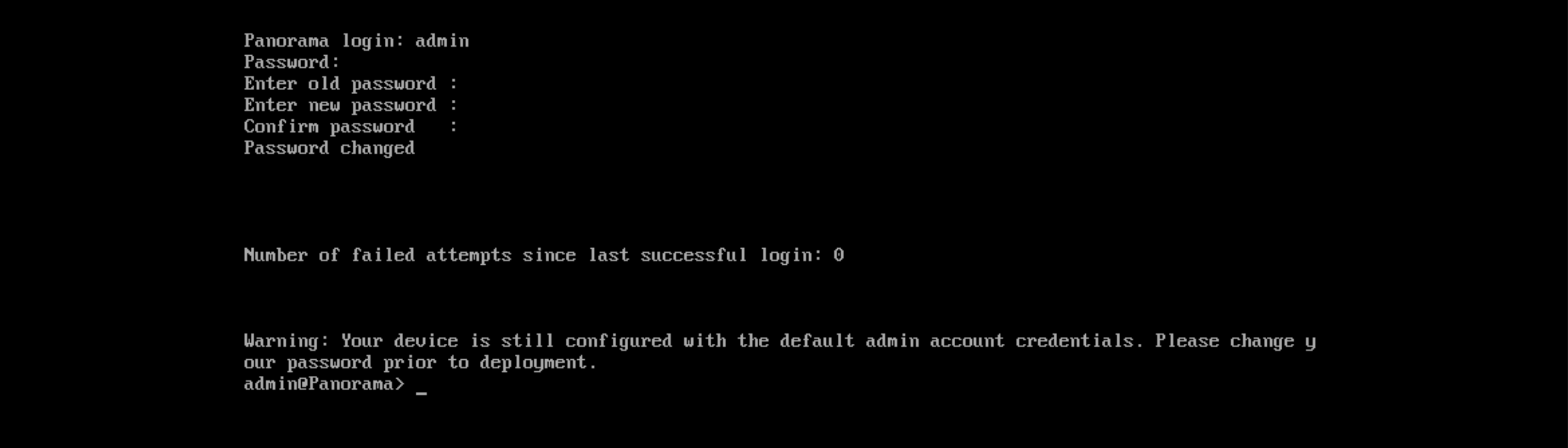
After the installation finishes, login with the default credential admin/admin
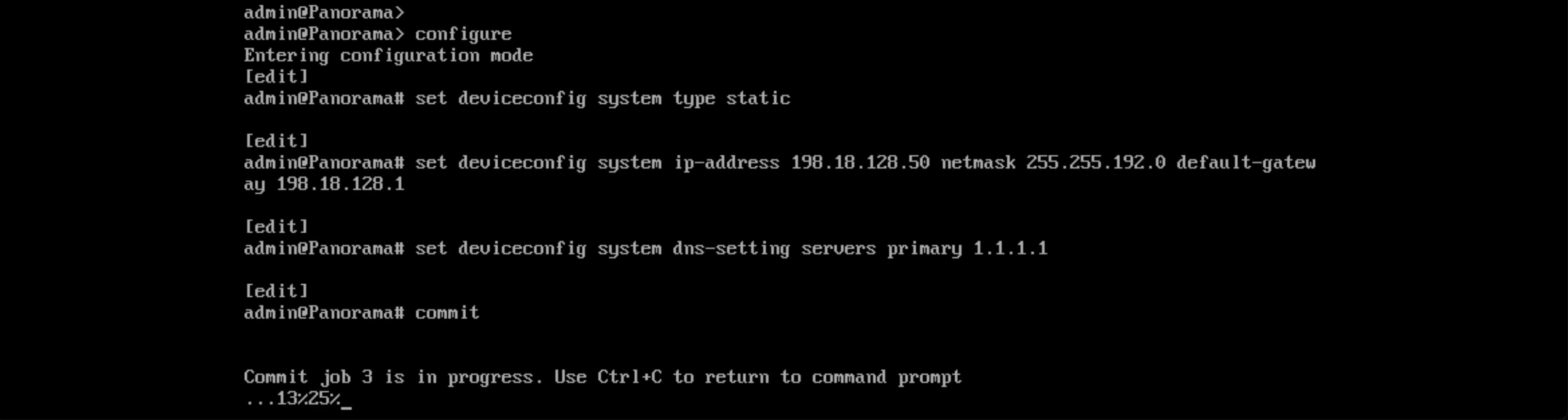
Next configure the management ip address
1
2
3
4
5
configure
set deviceconfig system type static
set deviceconfig system ip-address 198.18.128.50 netmask 255.255.192.0 default-gateway 198.18.128.1
set deviceconfig system dns-setting servers primary 1.1.1.1
commit
After that the Web UI should be accessible
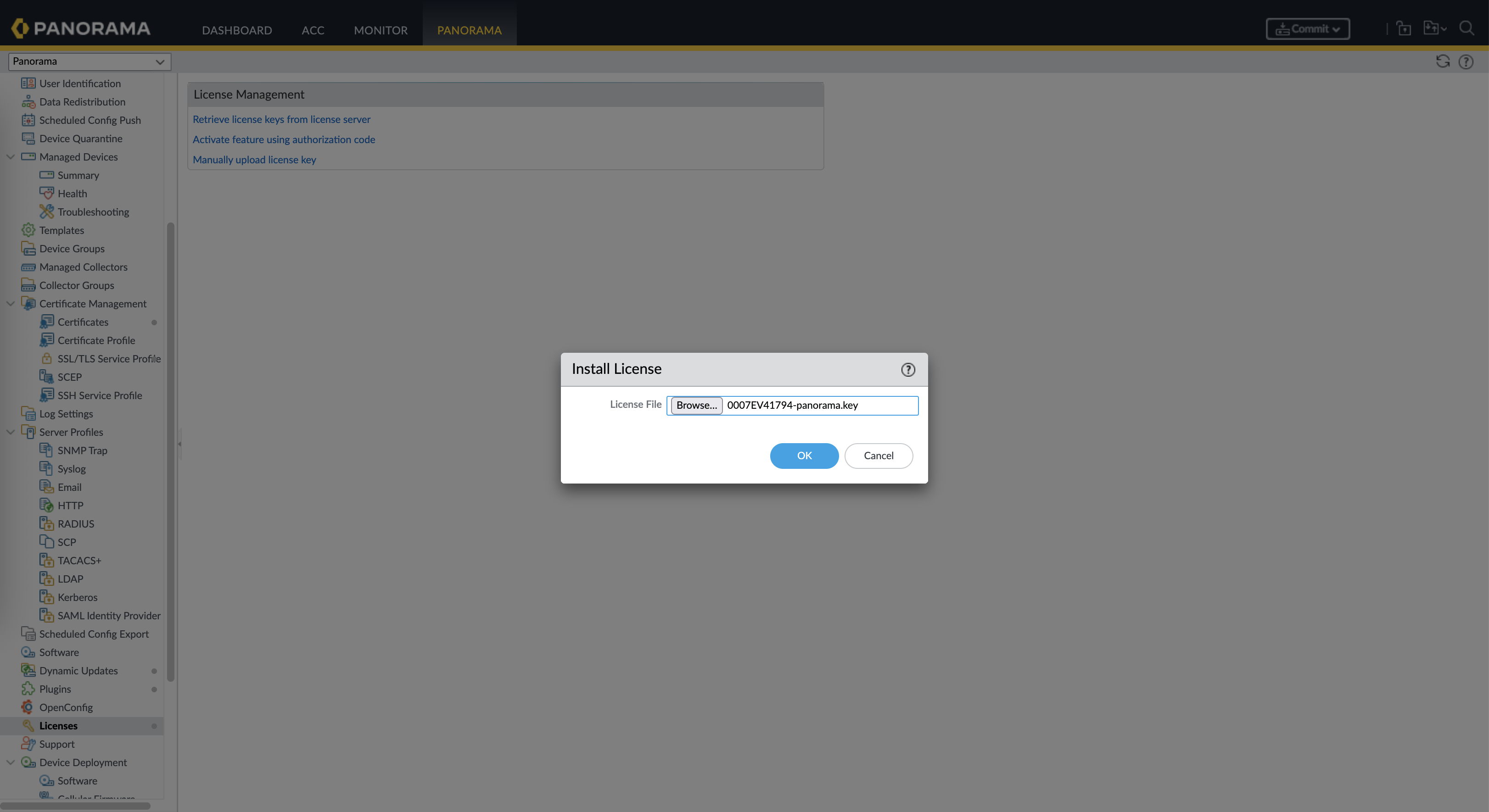
Inject the license so we can start using panorama
Adding Firewalls
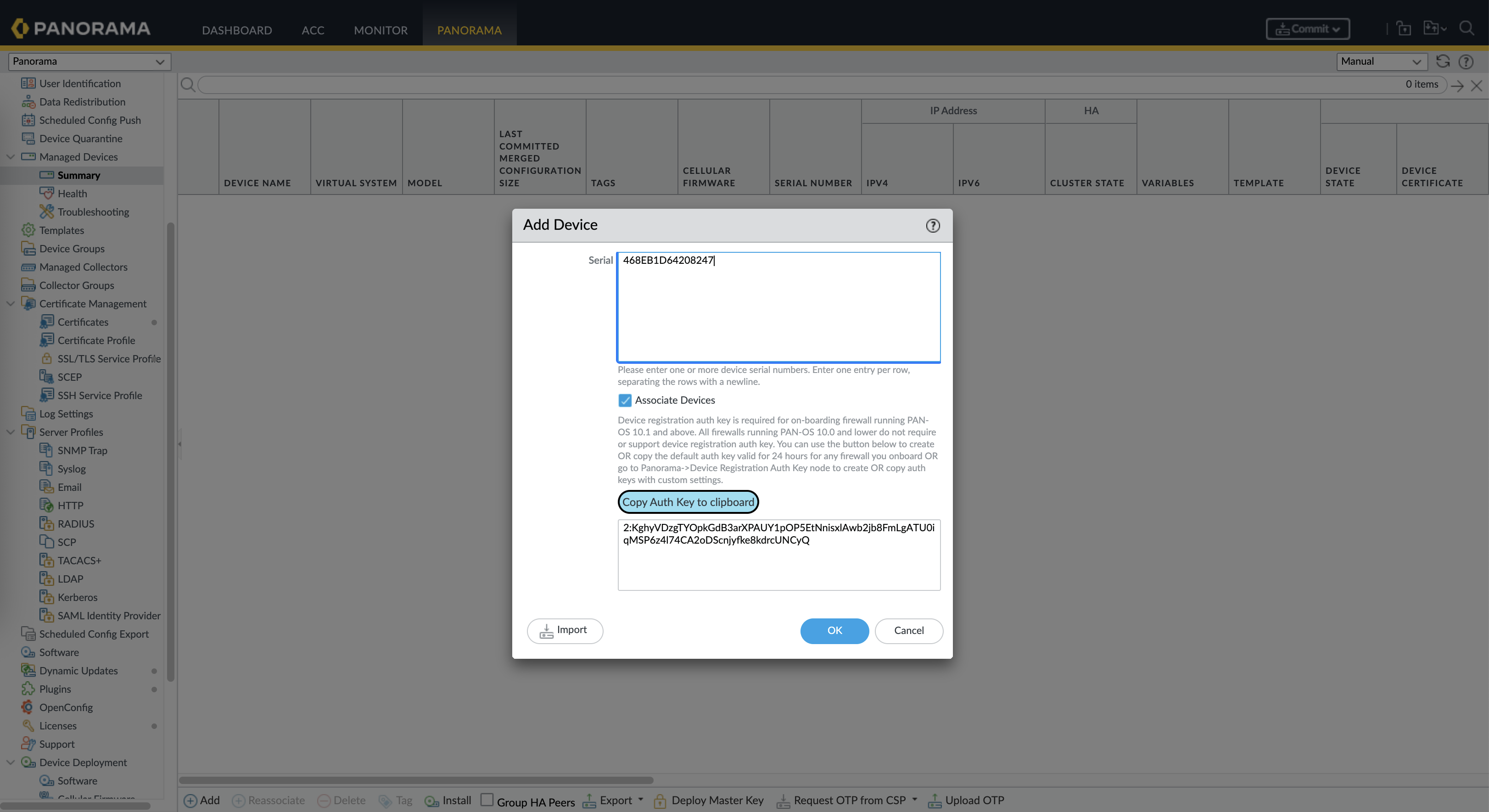
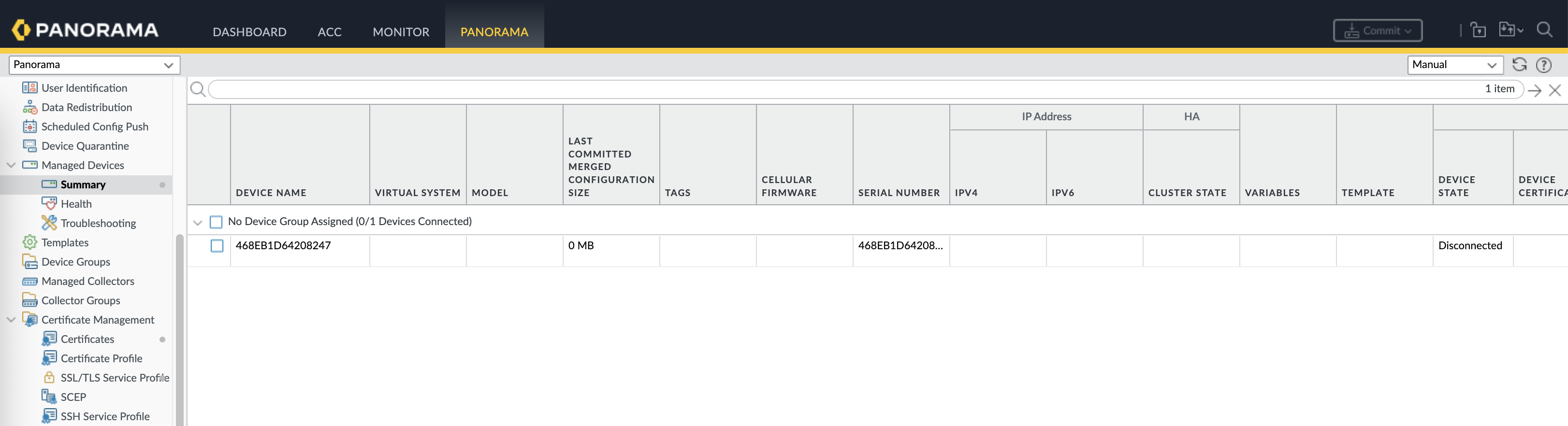
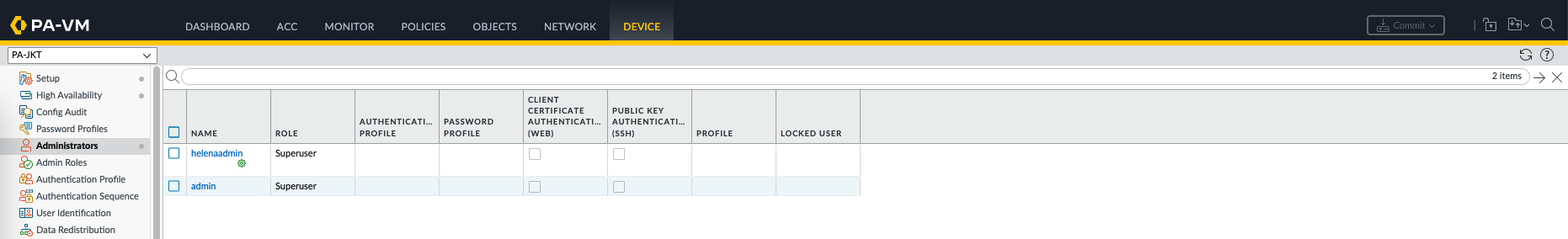
On Panorama » Managed Devices » Summary, add the SN of the firewall and generate the Auth Key
On the Firewall side, go to Device » Setup » Panorama Settings, enter the Panorama IP Address and the Auth Key
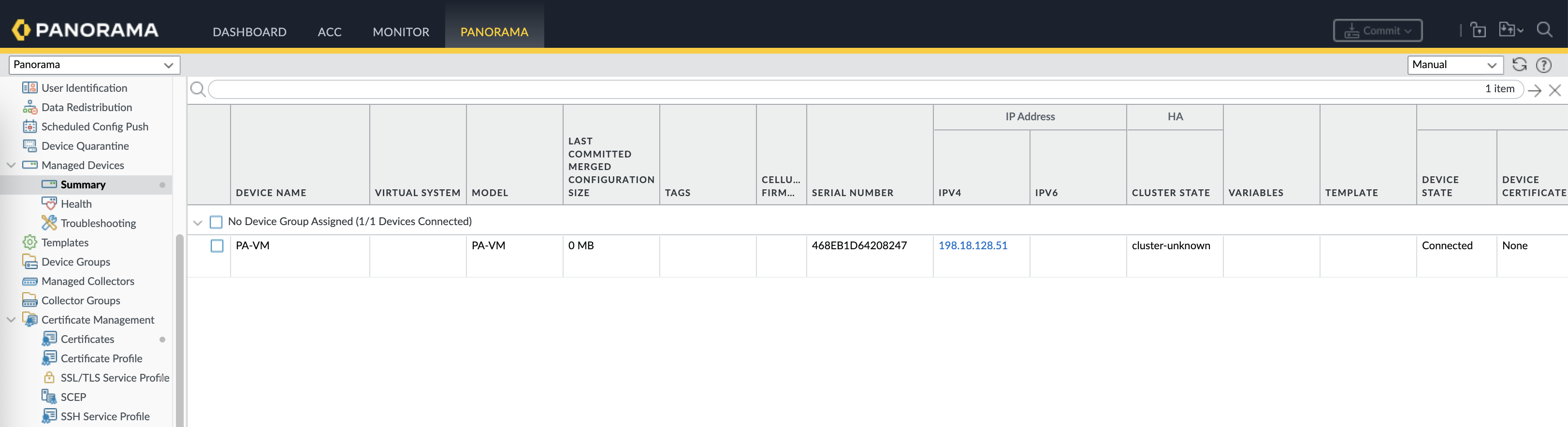
Back on Panorama, we should see the firewall is now registered
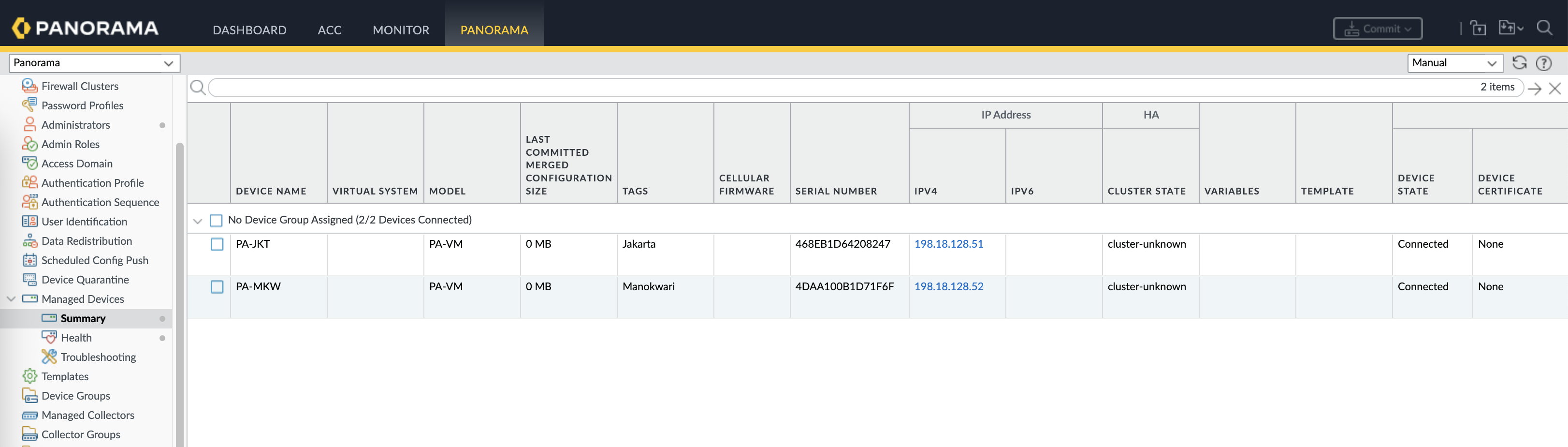
Lets add one more firewall, change the hostnames and give them tags
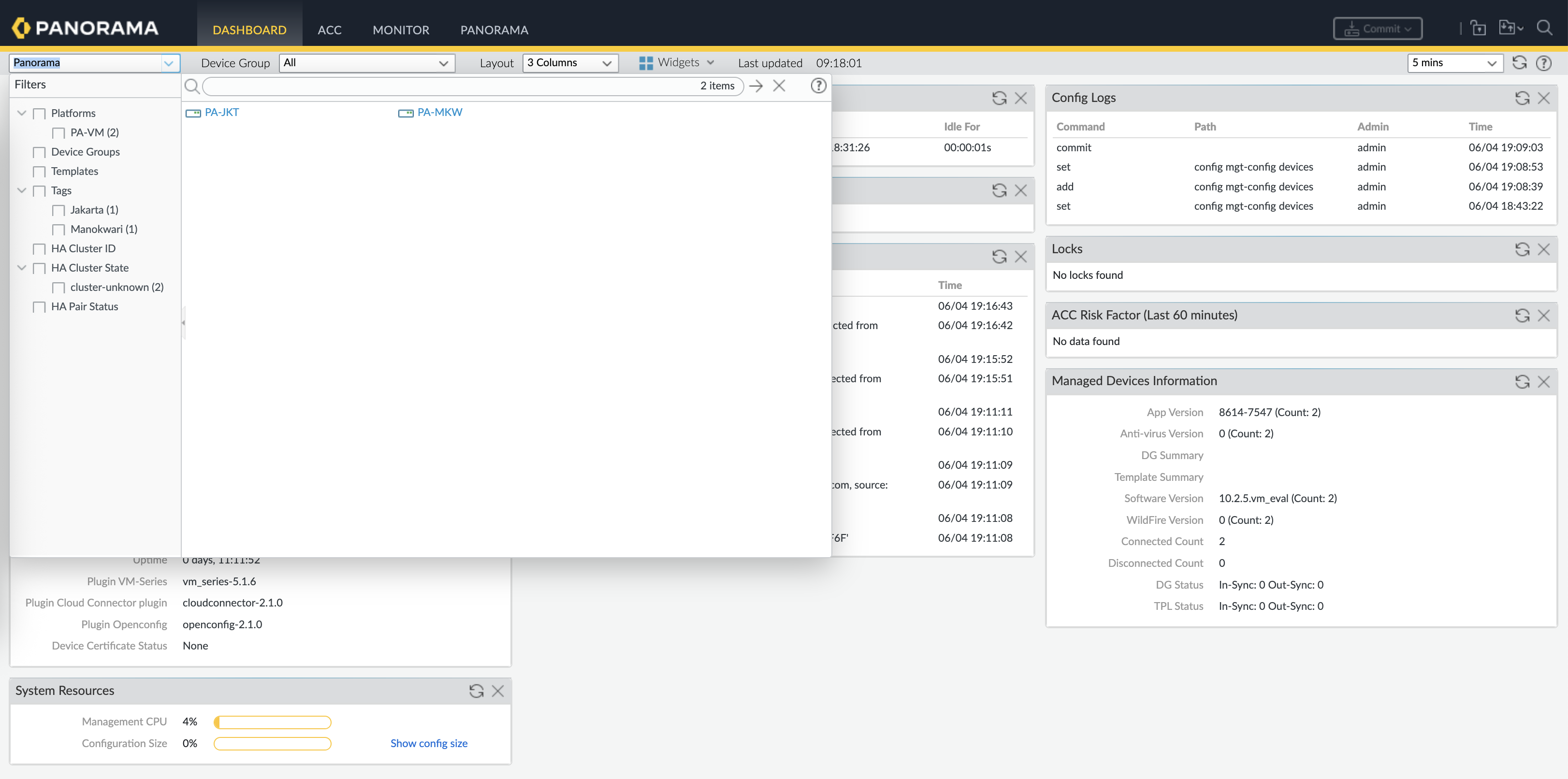
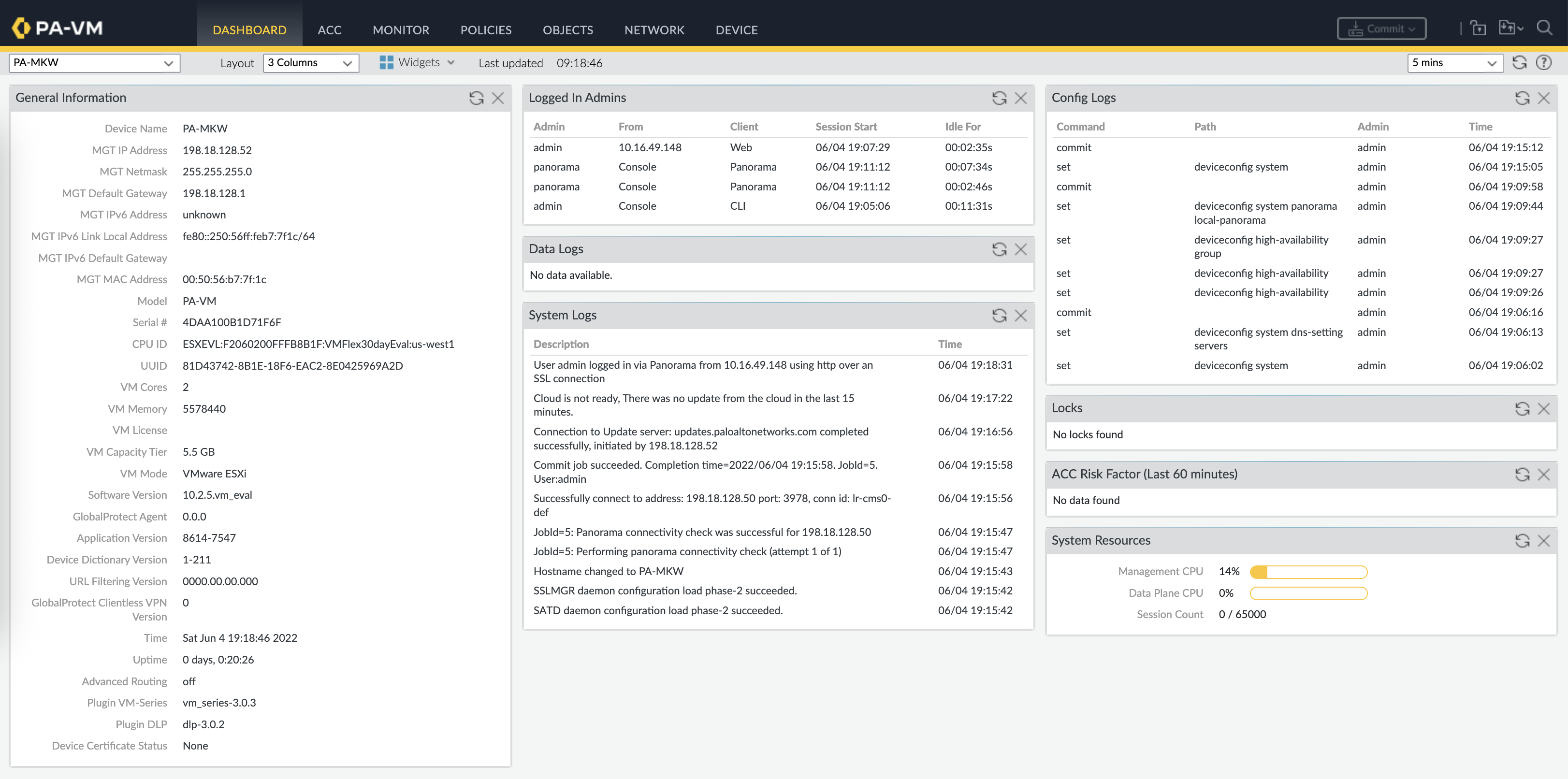
Now from the Panorama Dashboard, we can easily connect to the registered firewalls
Templates
Panorama templates are used to centrally configure and push device-specific settings—like interfaces, routing, and system settings—to managed Palo Alto firewalls.
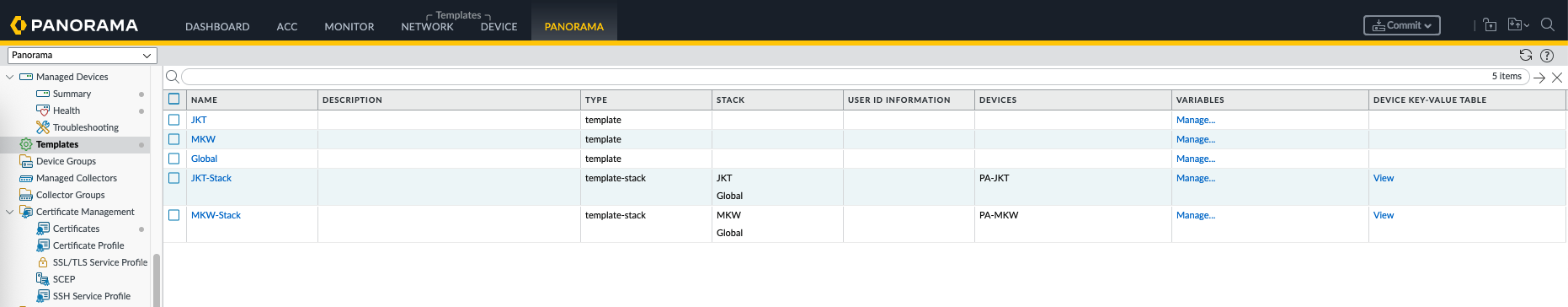
On Panorama » Templates, here we add some device specific and global templates, and then stack them for each site
Device Template
A Device Template in Panorama defines settings like logging, SNMP, and device management for firewalls.
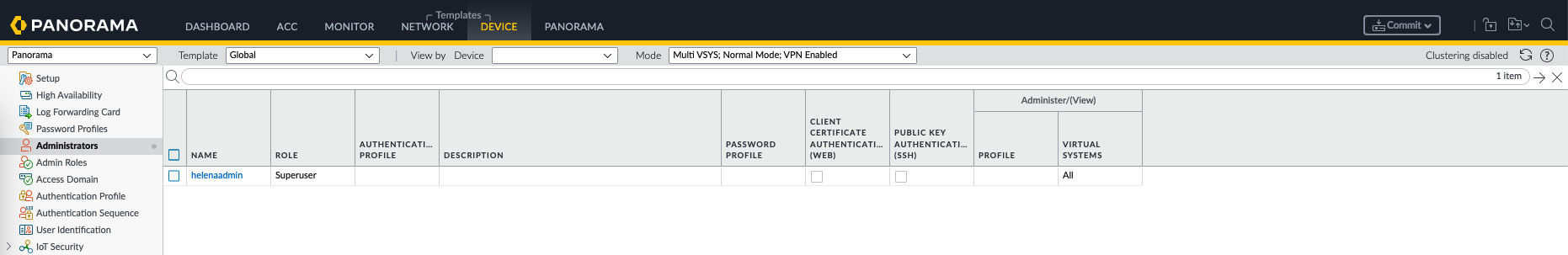
Here on Global template we will add an admin user that will be pushed to all devices
Network Template
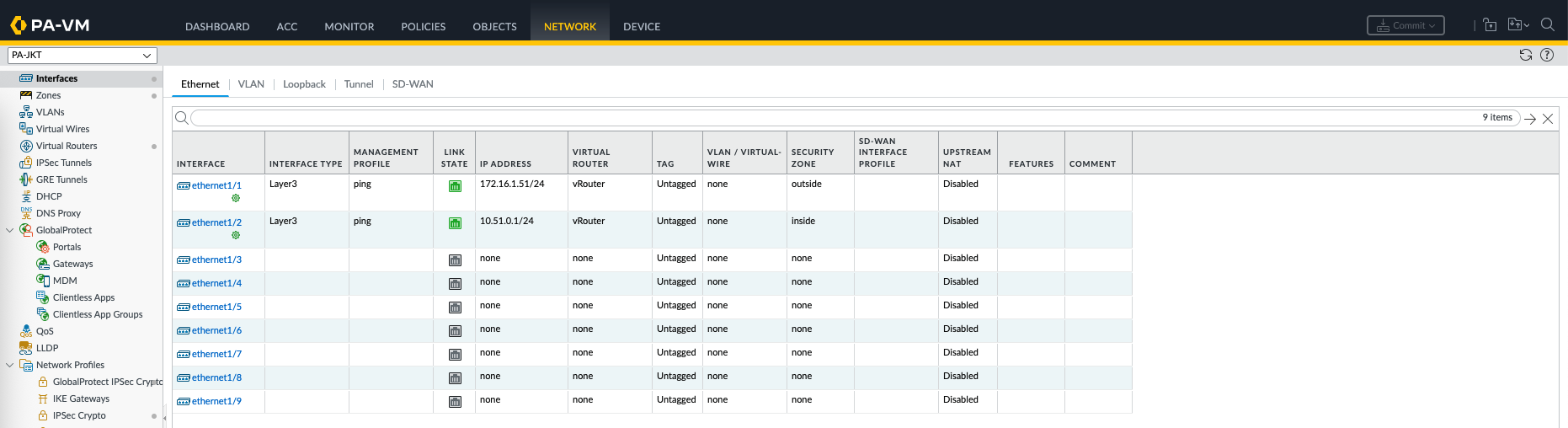
A Network Template configures networking elements such as interfaces, virtual routers, and VLANs.
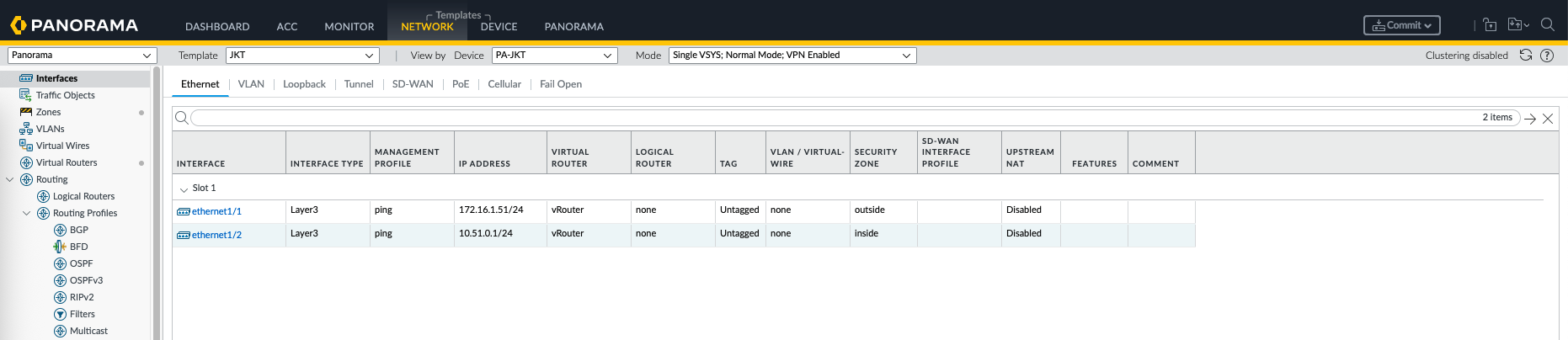
Here on JKT template we will configure the interface configurations specific to this site
Pushing Templates
After a commit & push, now we can see these configurations are present on the firewalls. This one is from the Global Device Template
And this one is from JKT Network Template
Device Groups
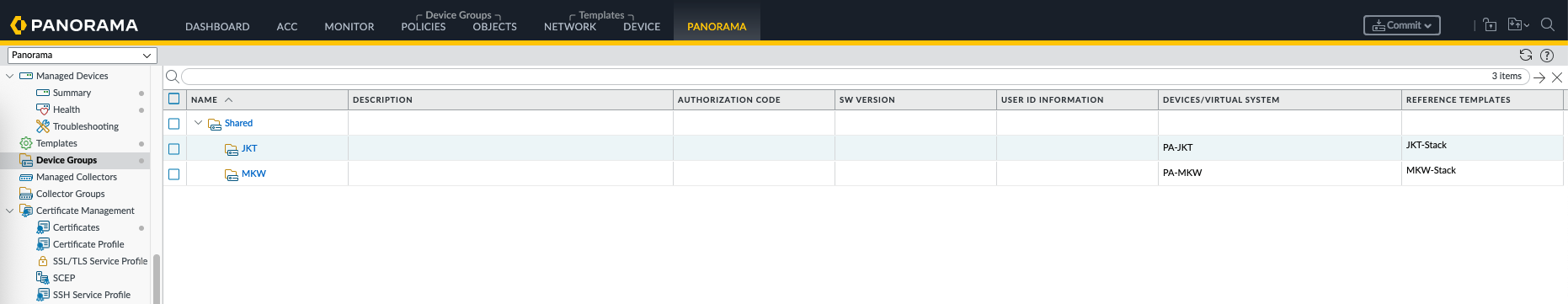
Device Groups in Panorama are used to centrally manage and push security policies, objects, and application settings to groups of firewalls that share similar policy requirements.
On Panorama » Device Groups, here we create a device group for each site
Objects
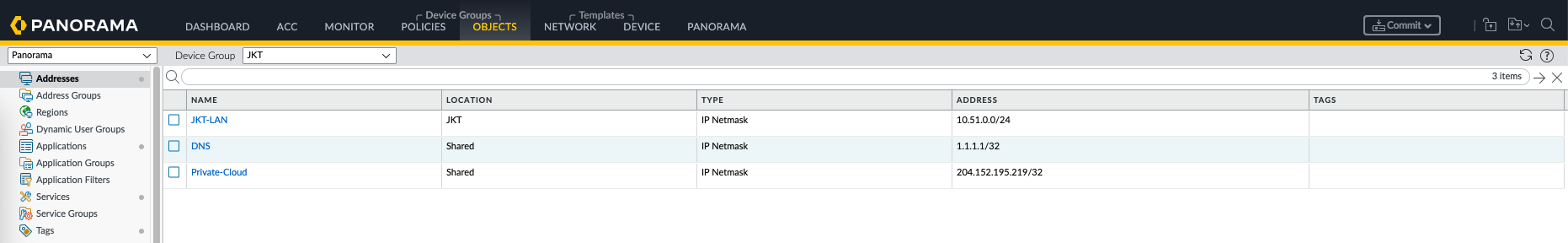
Objects are reusable elements like address objects, service ports, and application definitions that help simplify and standardize policy creation.
On JKT Objects, we create one JKT-specific object and two shared objects
Policies
Policies are the security, NAT, decryption, and other rule sets that control traffic behavior on the firewalls managed by the device group.
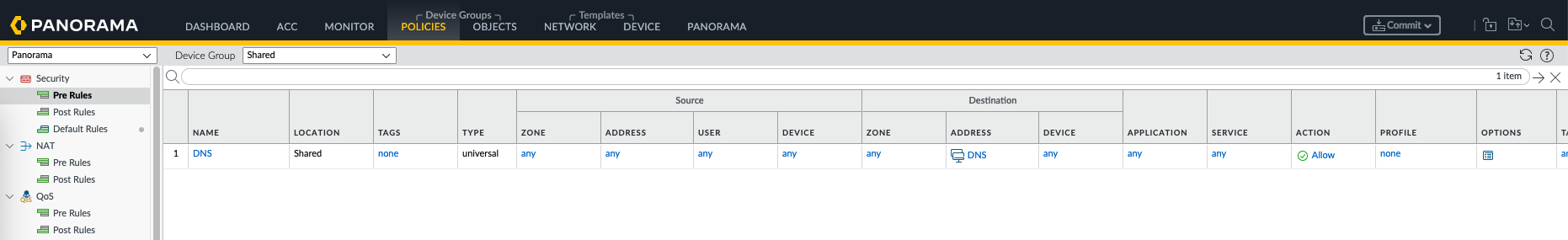
First on the Shared Policies, we create a generic rule to allow DNS traffic
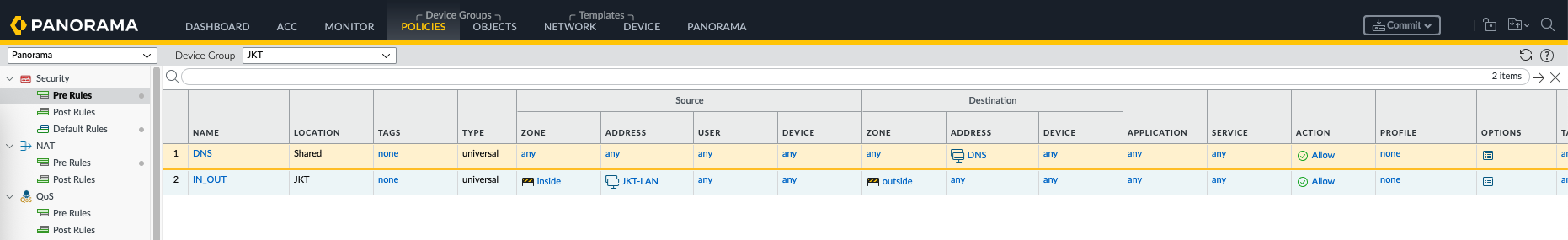
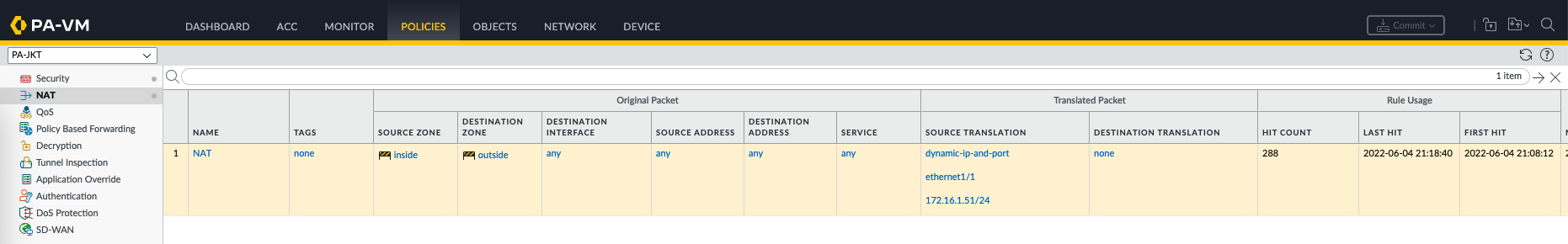
Next on JKT Policies, here we create a specific rule that allows JKT LAN users to access internet
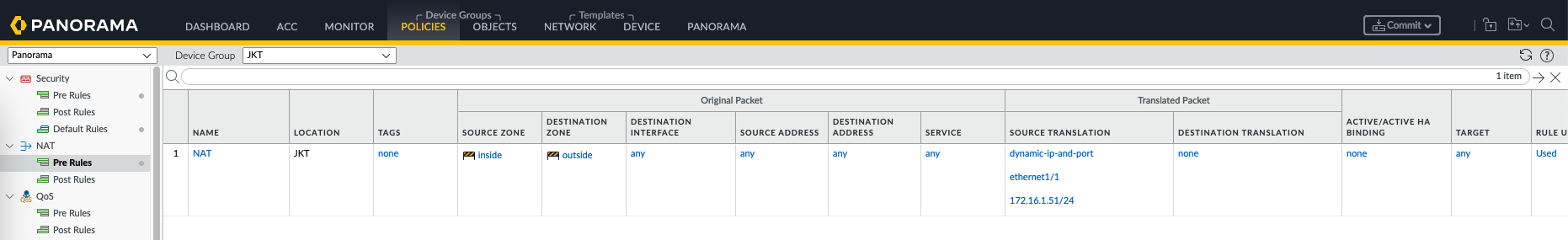
We also add a NAT rule to accomodate users accessing internet
Pushing Device Groups
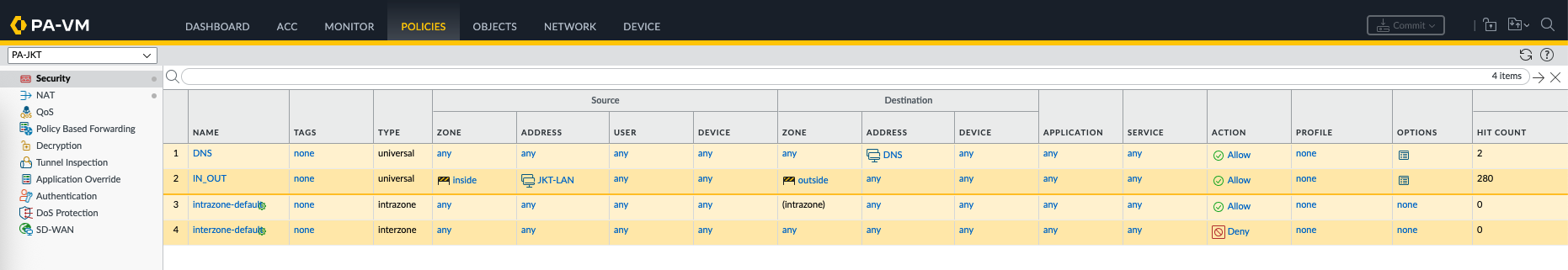
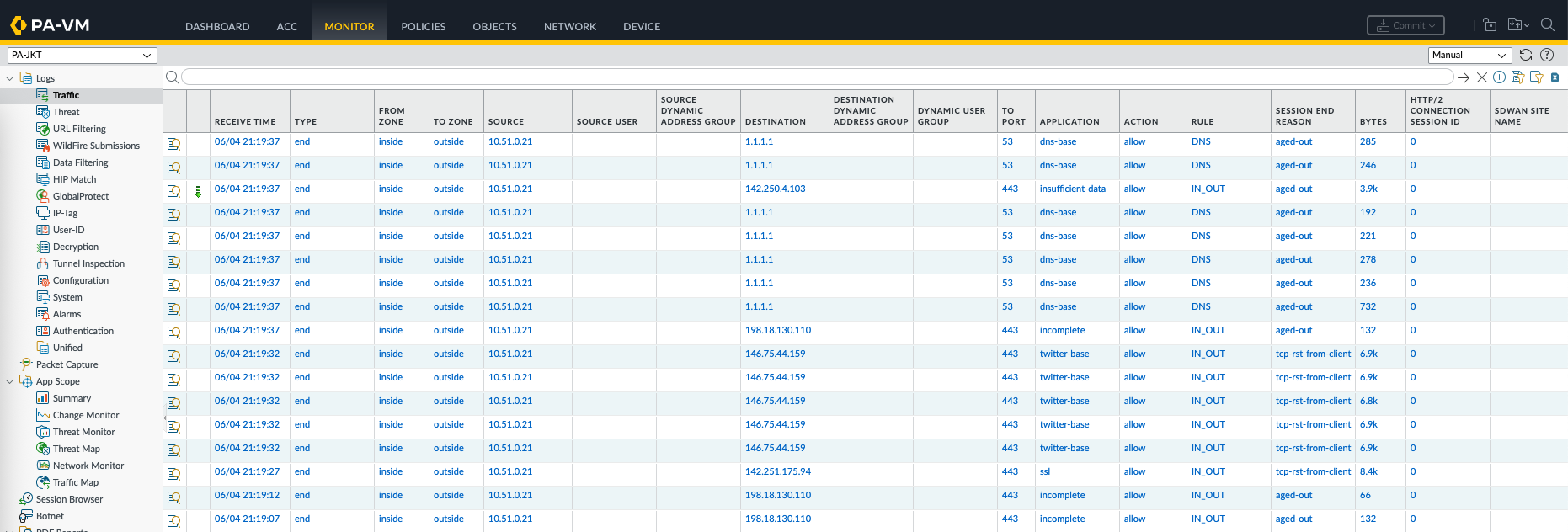
After a commit & push, we can see the objects and policies created from panorama are pushed to the firewalls
Enabling Panorama Mode
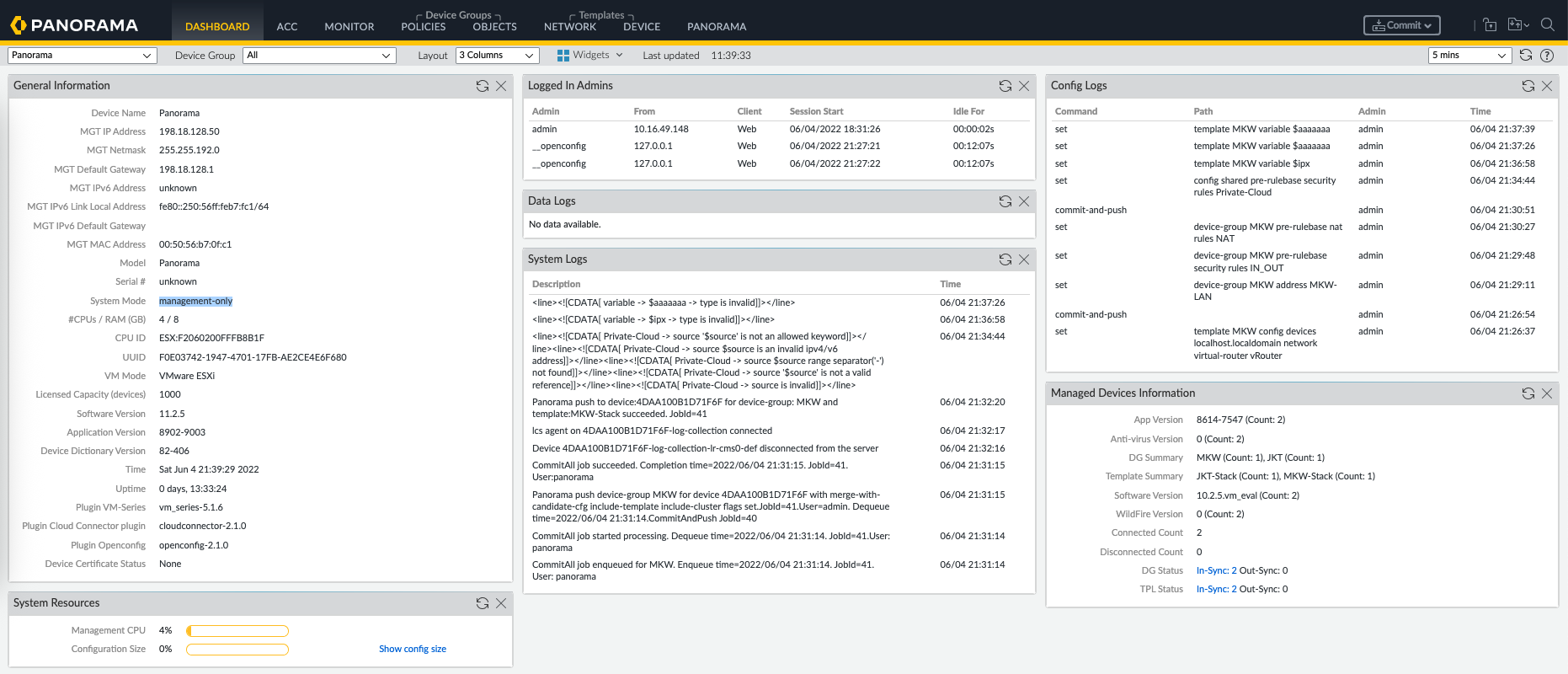
So far our Panorama has been running on Management Only Mode, we will change this to Panorama Mode so we can consume logs from firewalls.
Management Only Mode allows configuration tasks without log collection or visibility features, while Panorama Mode supports full management plus logging and reporting capabilities.
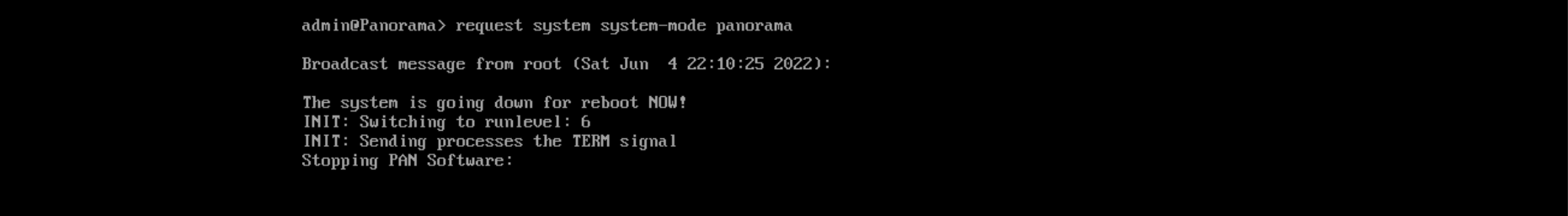
To enable Panorama Mode, we need 16 CPU, 32 GB of RAM, and additional 50 GB disk inserted to the appliance, after that we can enable the mode on CLI
1
request system system-mode panorama
And now we are running in Panorama mode
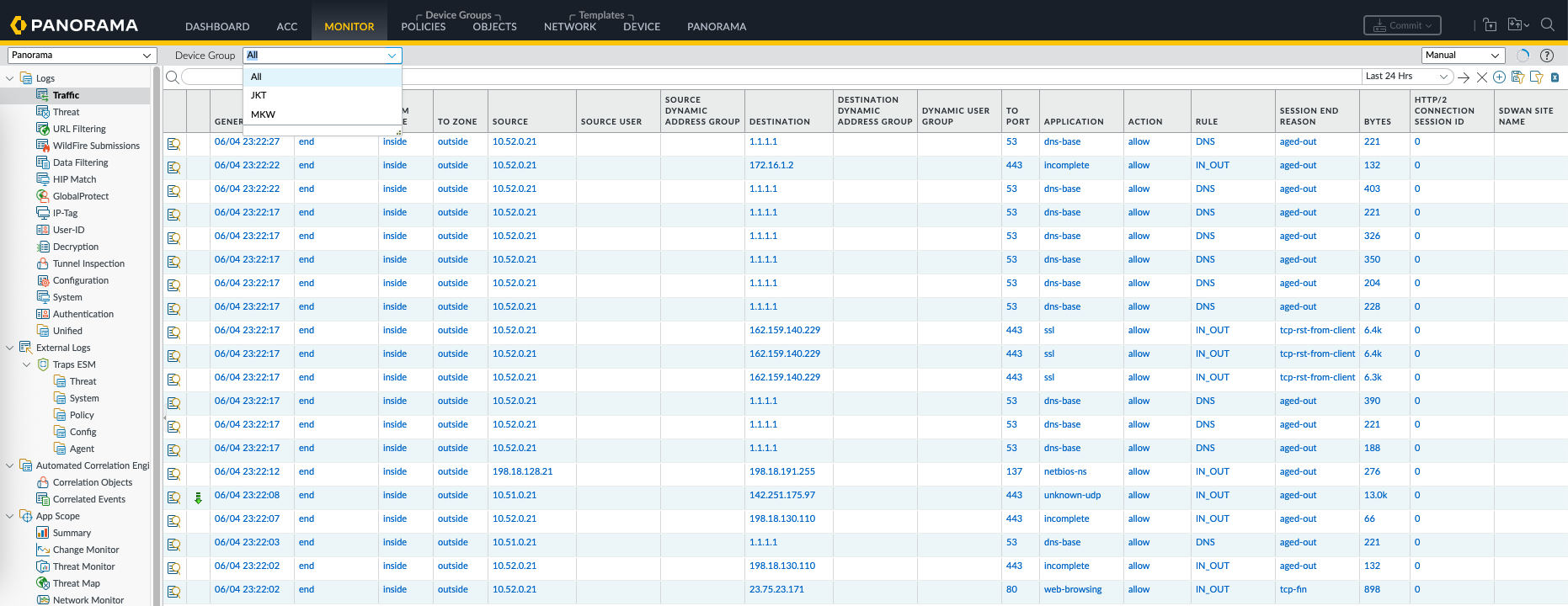
Enabling Log Collector
Log Collector is a dedicated component that collects, stores, and processes logs from multiple managed firewalls, enabling centralized logging and detailed reporting.
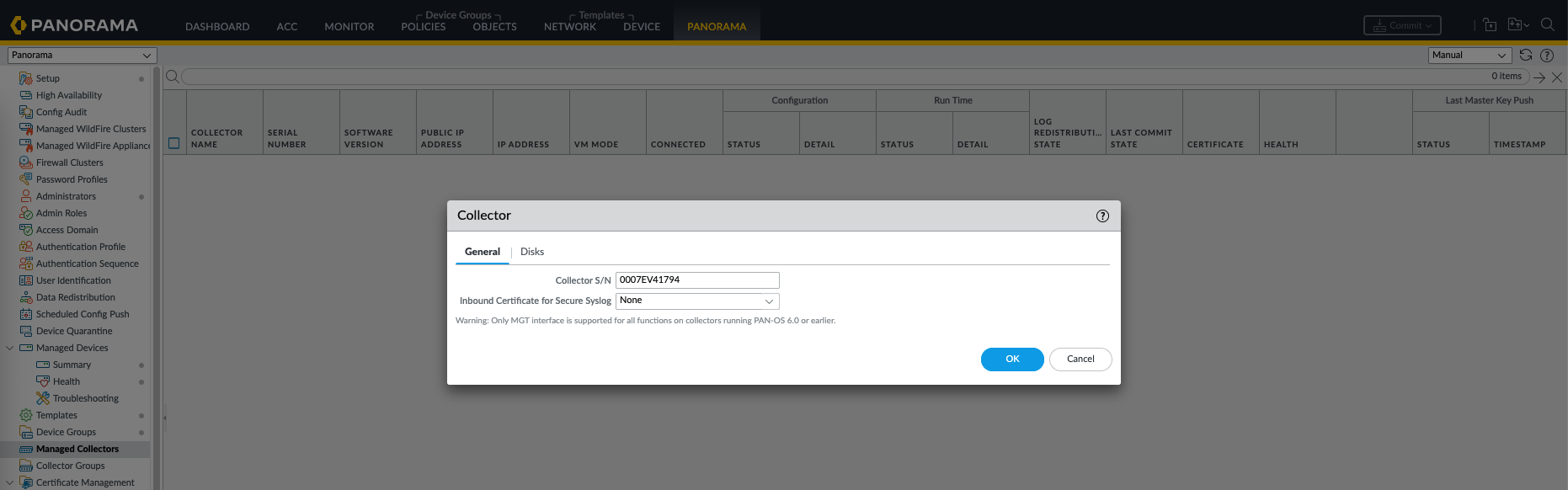
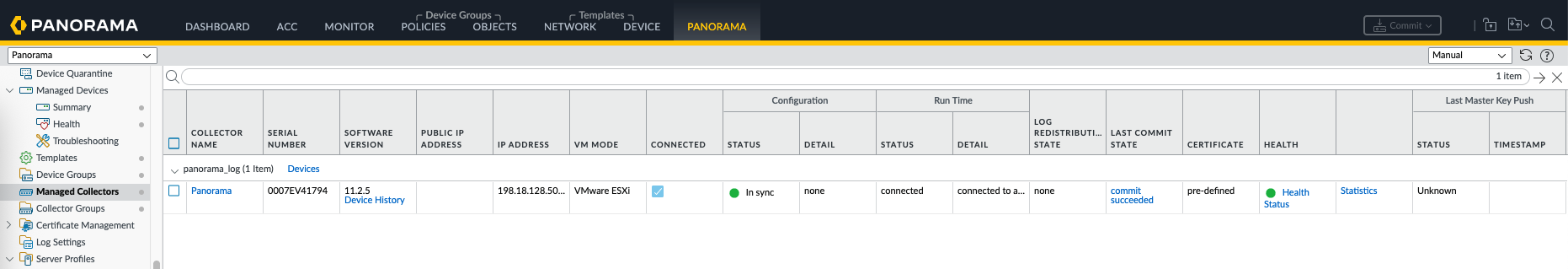
On Panorama » Managed Collectors, add Panorama SN and commit
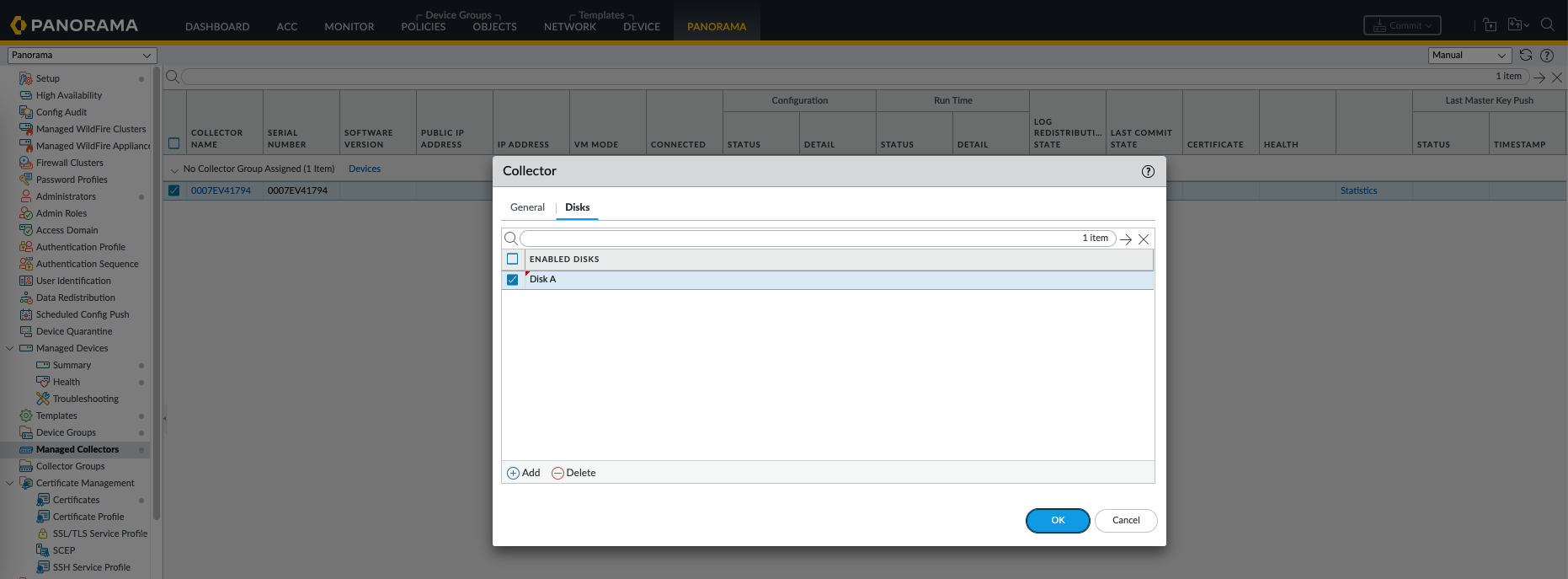
A new disk will be created that we can select for this collector
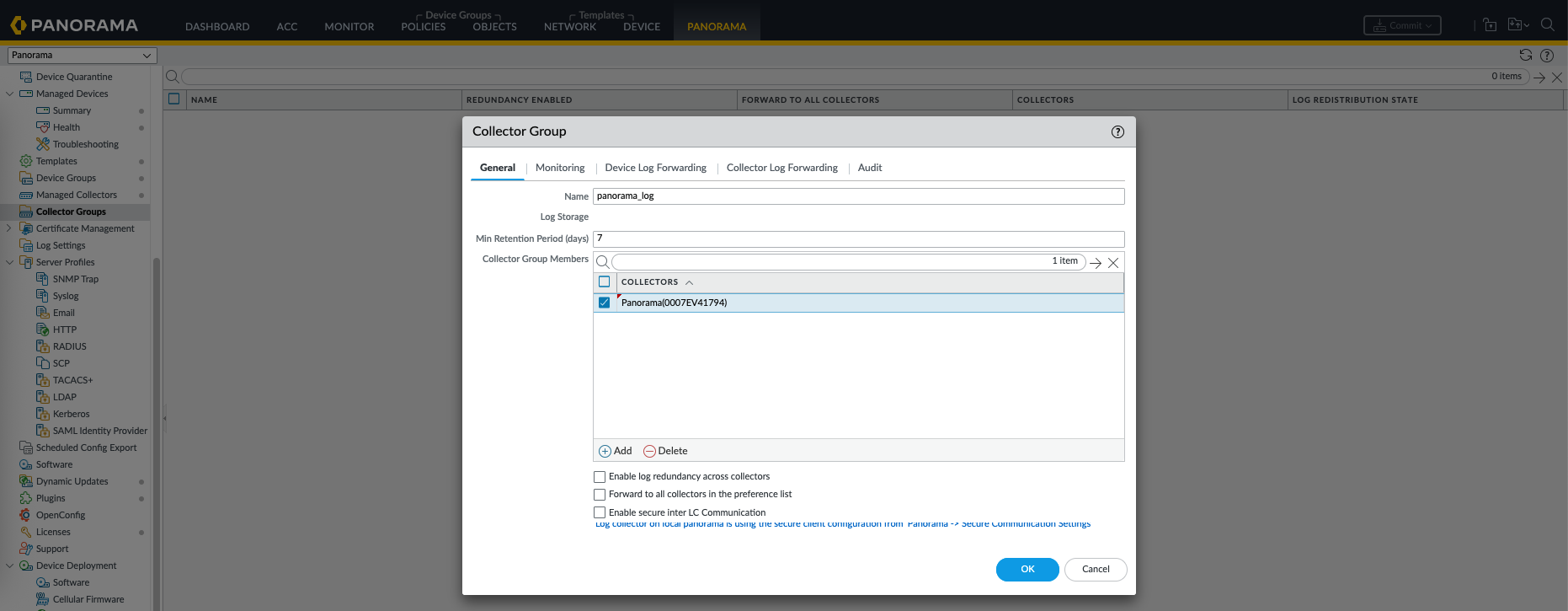
Next on Collector Groups, add the newly created collector
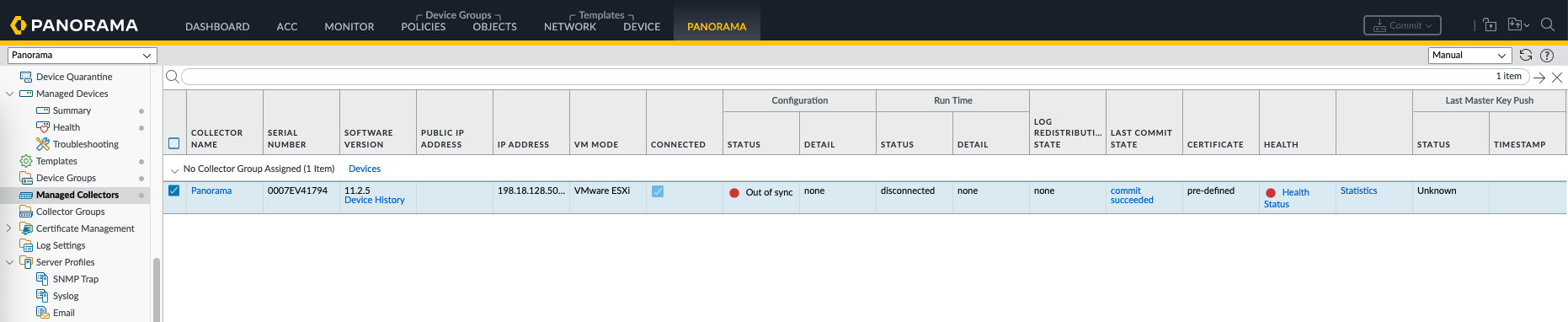
The collector should turn green now
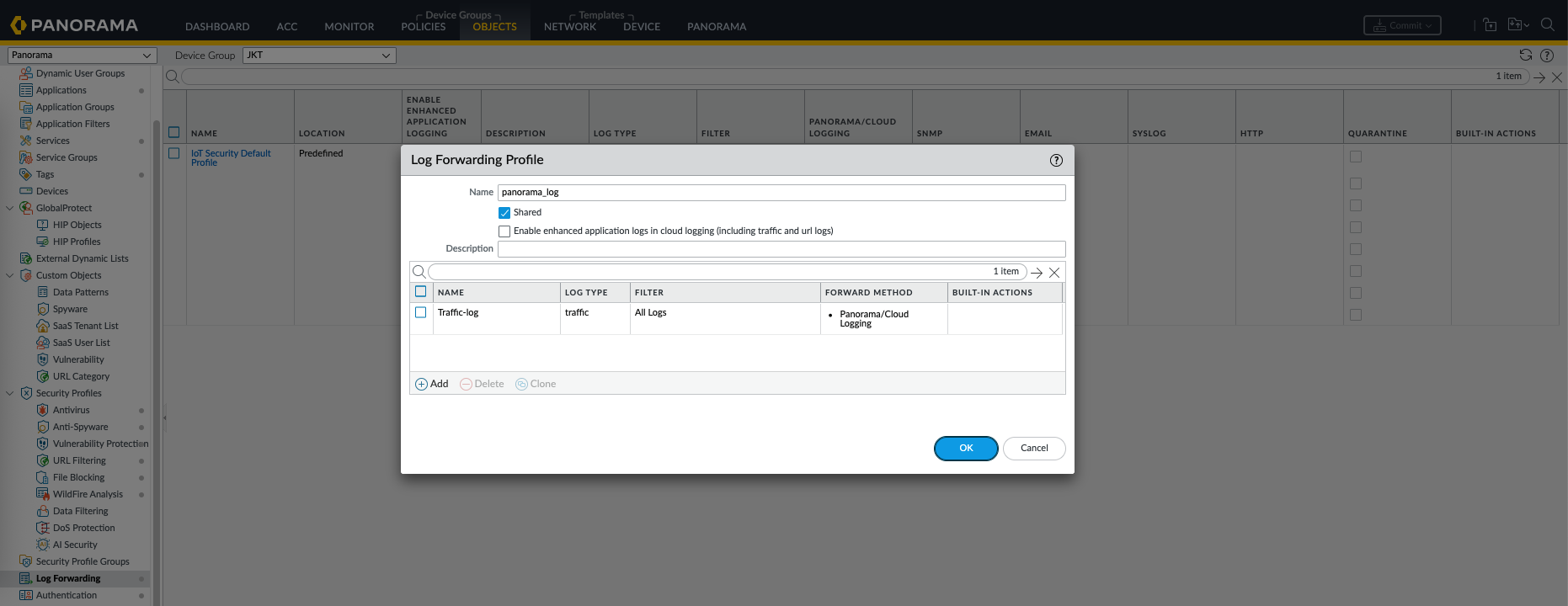
After that, create a new Log Forwarding Profile and select to forward it to Panorama
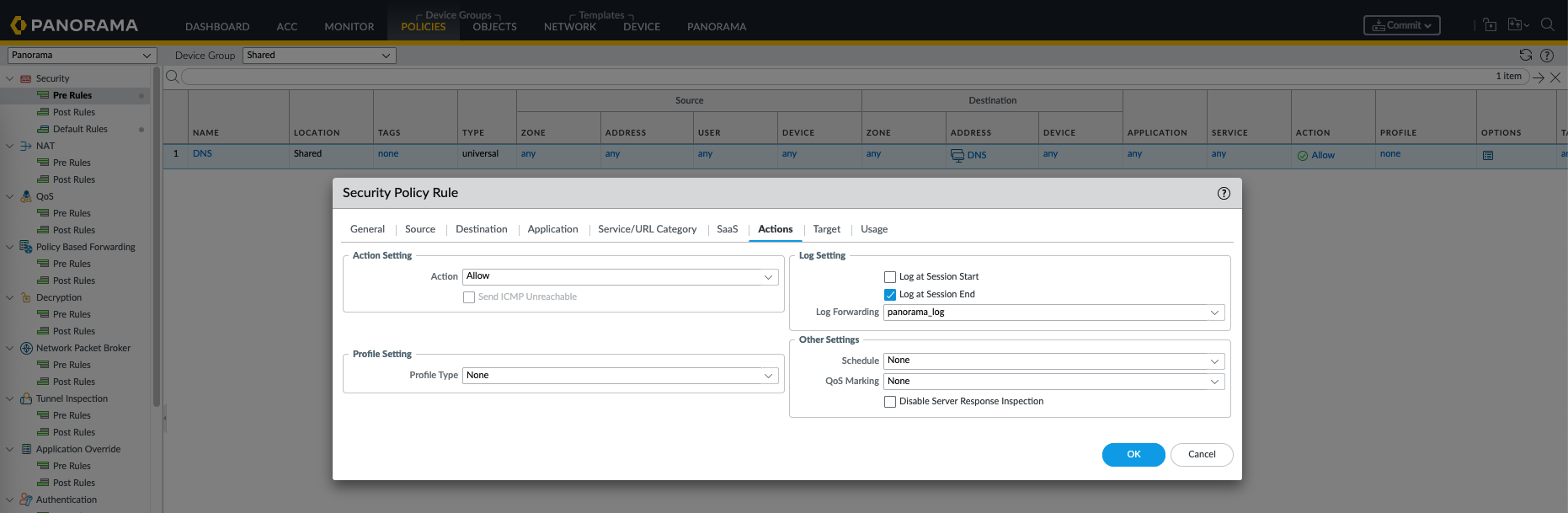
Now all we need to do is to forward logs to the profile for each desired policy
After a commit & push, the logs are now forwarded and visible on Panorama