Cisco ISE TrustSec with Palo Alto Panorama
Palo Alto Networks integrates with Cisco ISE’s pxGrid via Panorama using the Cisco TrustSec plugin to import Security Group Tags (SGTs) and IP-to-SGT mappings. By establishing a secure connection to ISE’s pxGrid controller, Panorama retrieves TrustSec data, enabling Palo Alto firewalls to enforce dynamic, identity-based policies based on Cisco TrustSec classifications.
Installing Plugin
Download the Cisco TrustSec Plugin on the support portal
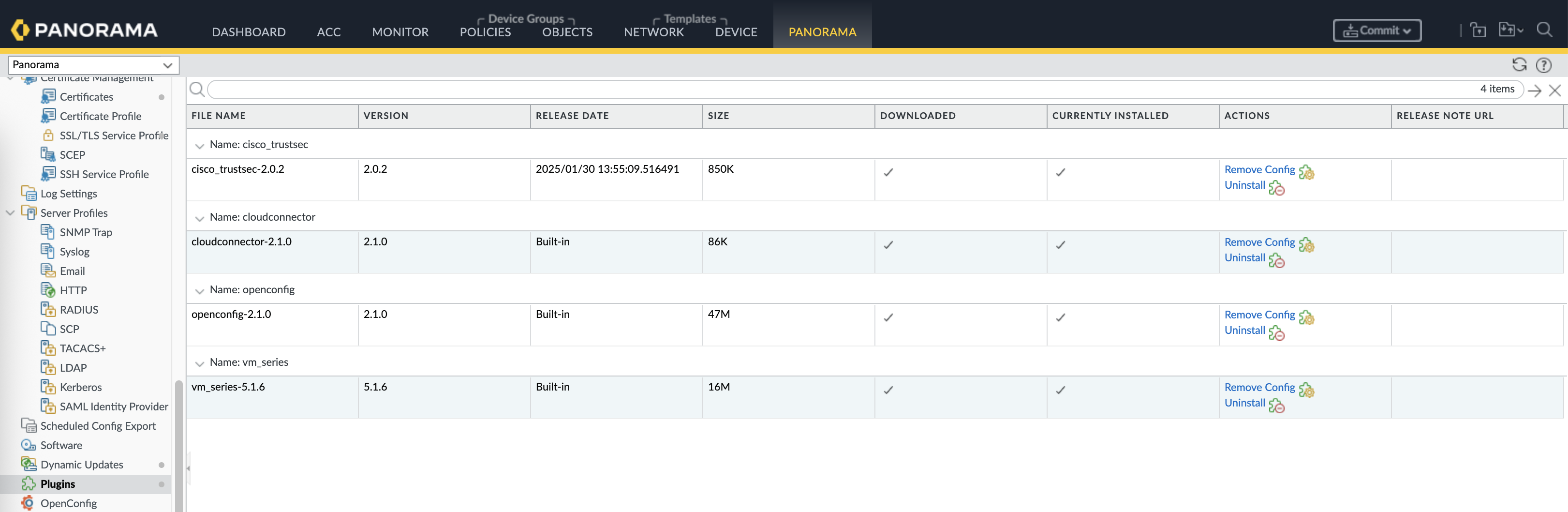
On Panorama » Plugins, upload and install the plugin
Configuring Cisco TrustSec
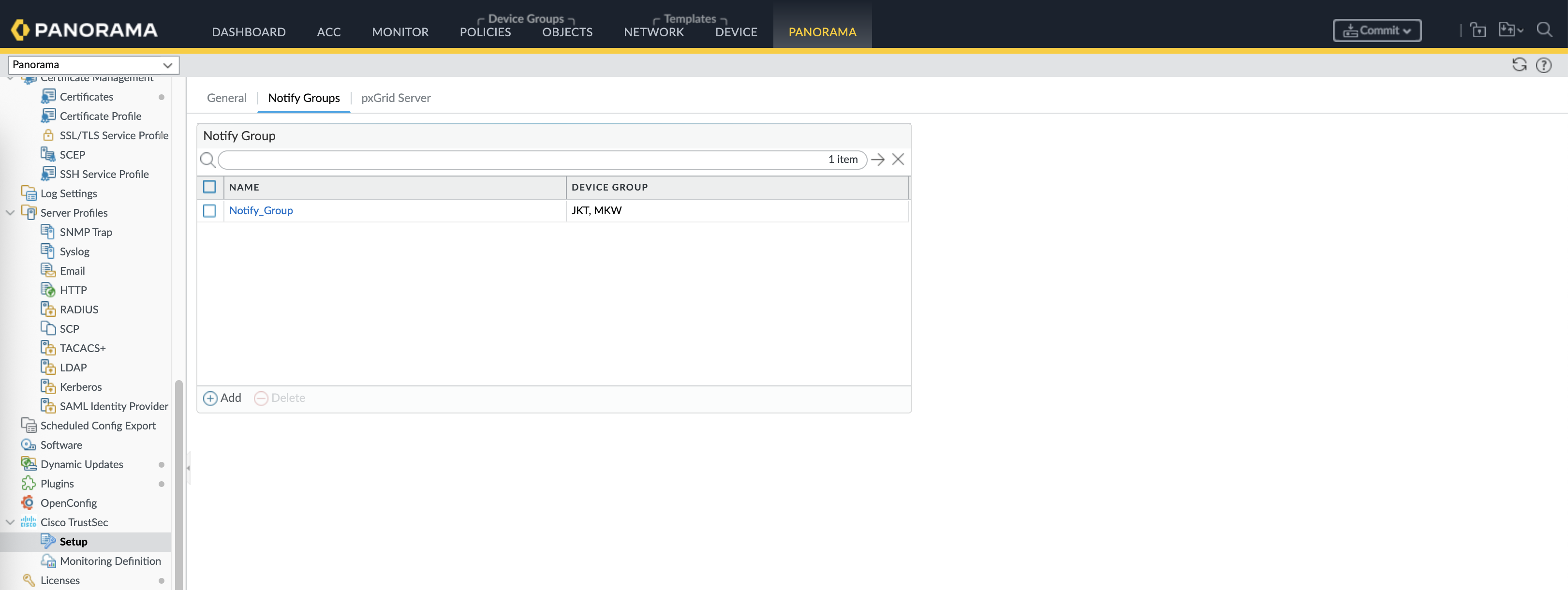
After installing plugin, a new Cisco TrustSec menu will appear, open the setup and enable monitoring
Add new Notify Group, insert the Device Groups we wish to receive this TrustSec configuration
PXGrid Integration
On Cisco ISE, on Administration » PXGrid » Settings, make sure to allow password based account creation
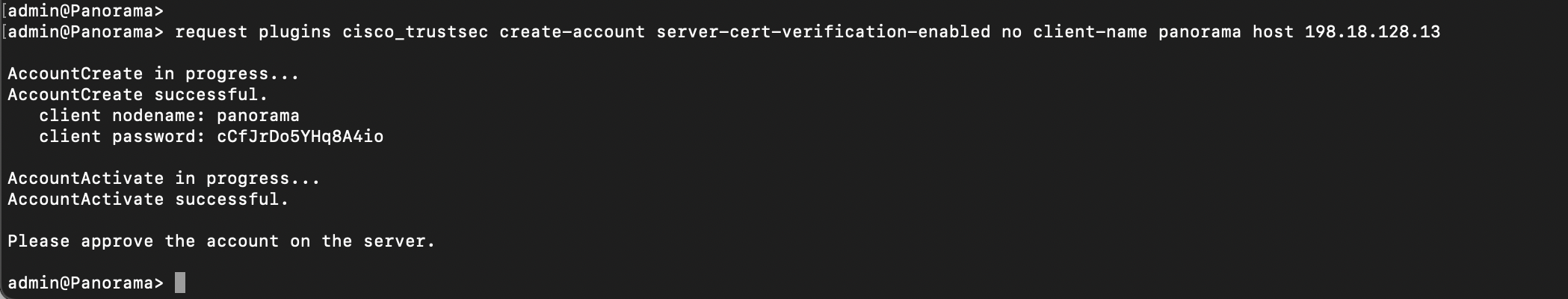
On Panorama CLI, run this command to create the client account without verifying certificates
1
request plugins cisco_trustsec create-account server-cert-verification-enabled no client-name panorama host 198.18.128.13
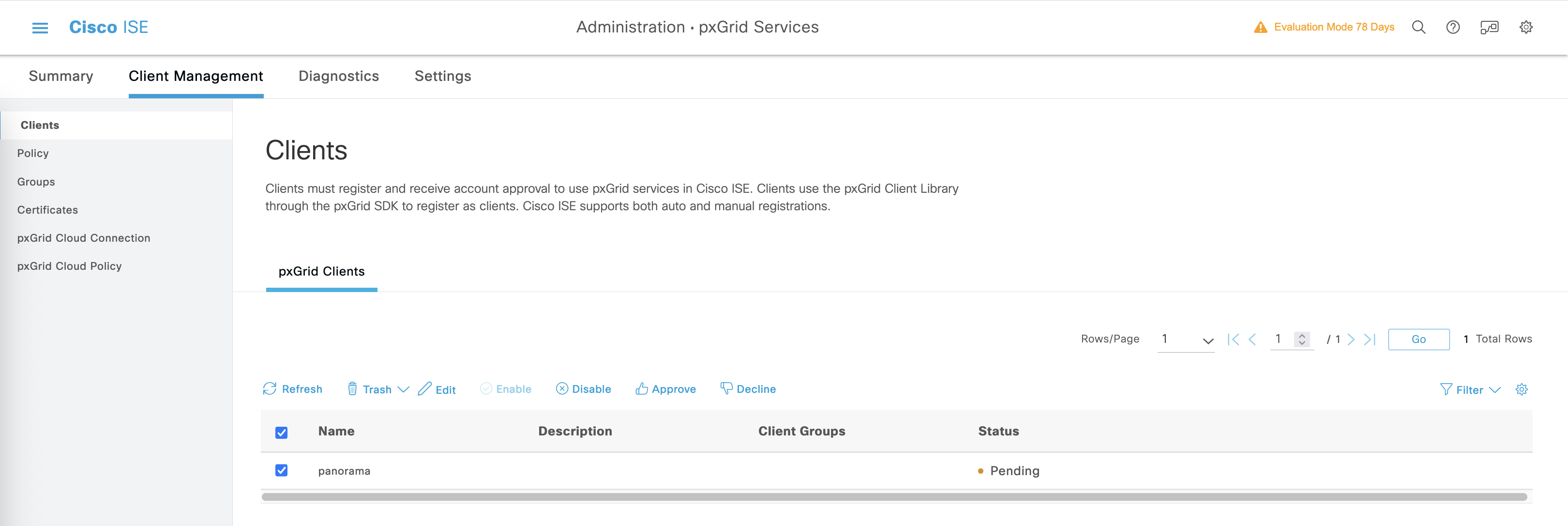
Back on ISE, the panorama client should show up
Hit approve so it becomes enabled
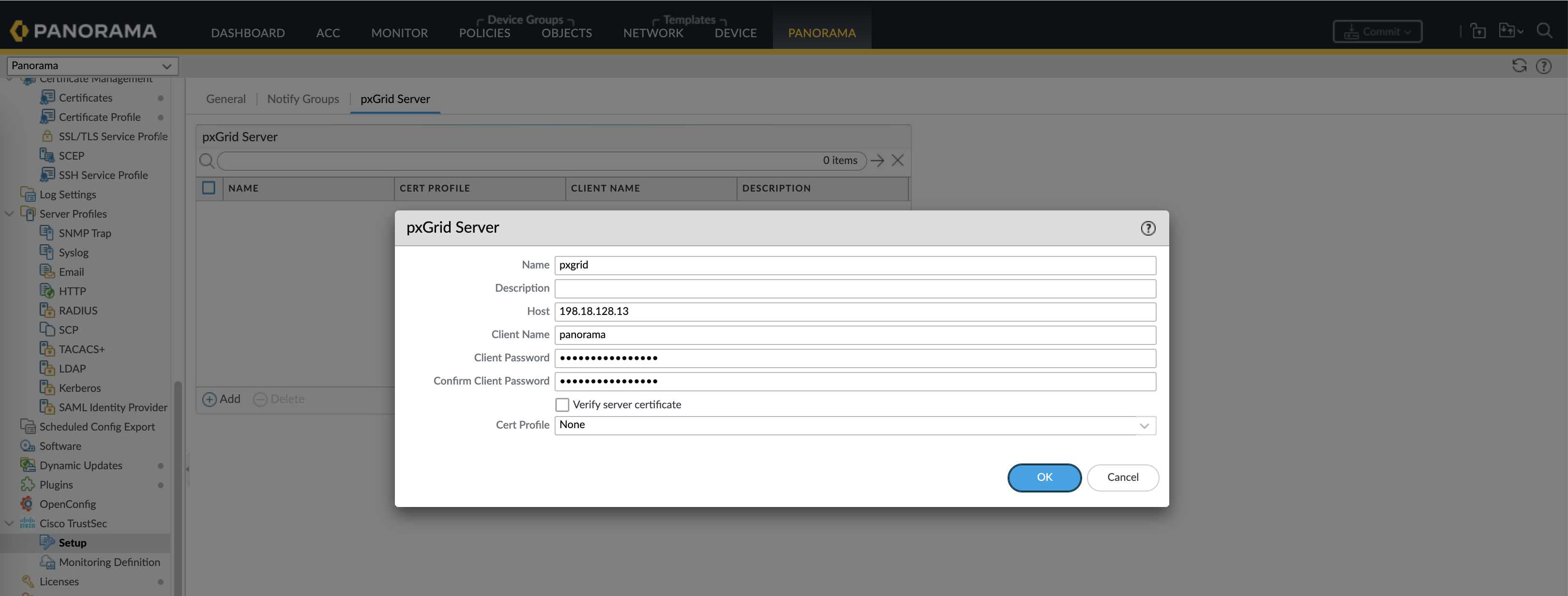
Next continuing the panorama configuration, add the PxGrid server with the generated credential
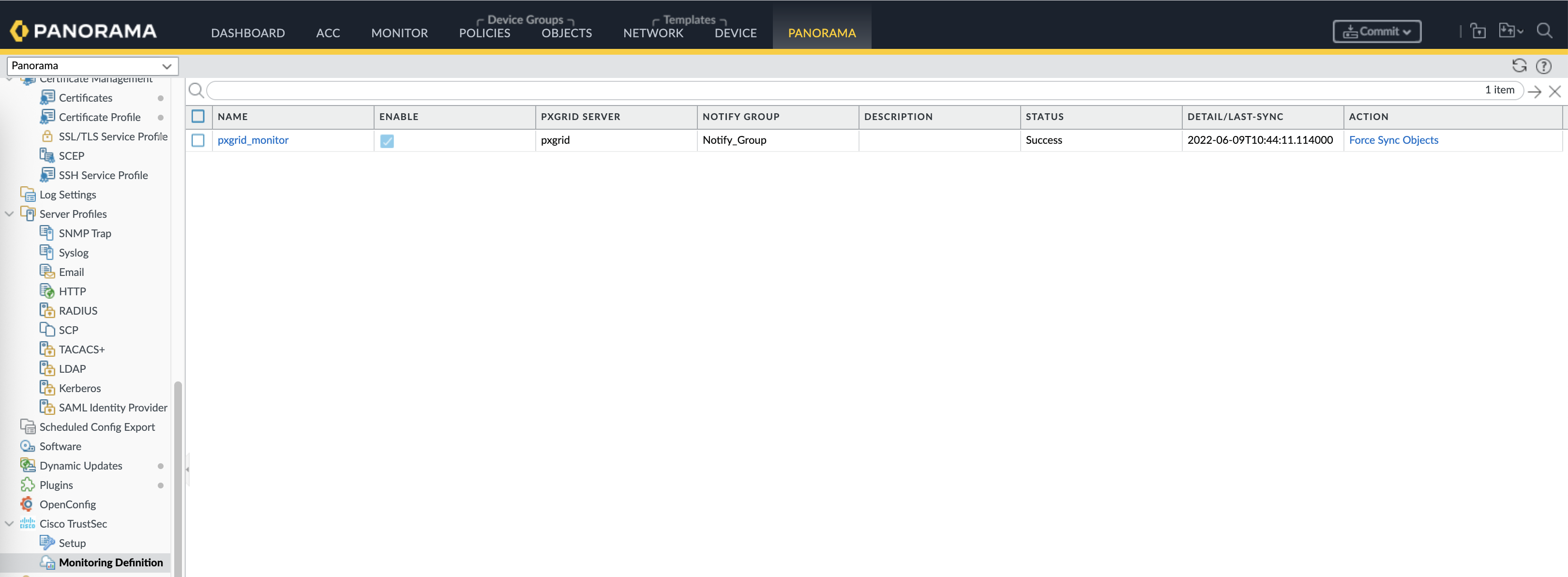
After that on the Monitoring Definition, add new one refrencing the PxGrid Sever and the Notify Group created earlier
Make sure the status is success and synced.
This process is repeated for every PxGrid server
Using the TrustSec SGT
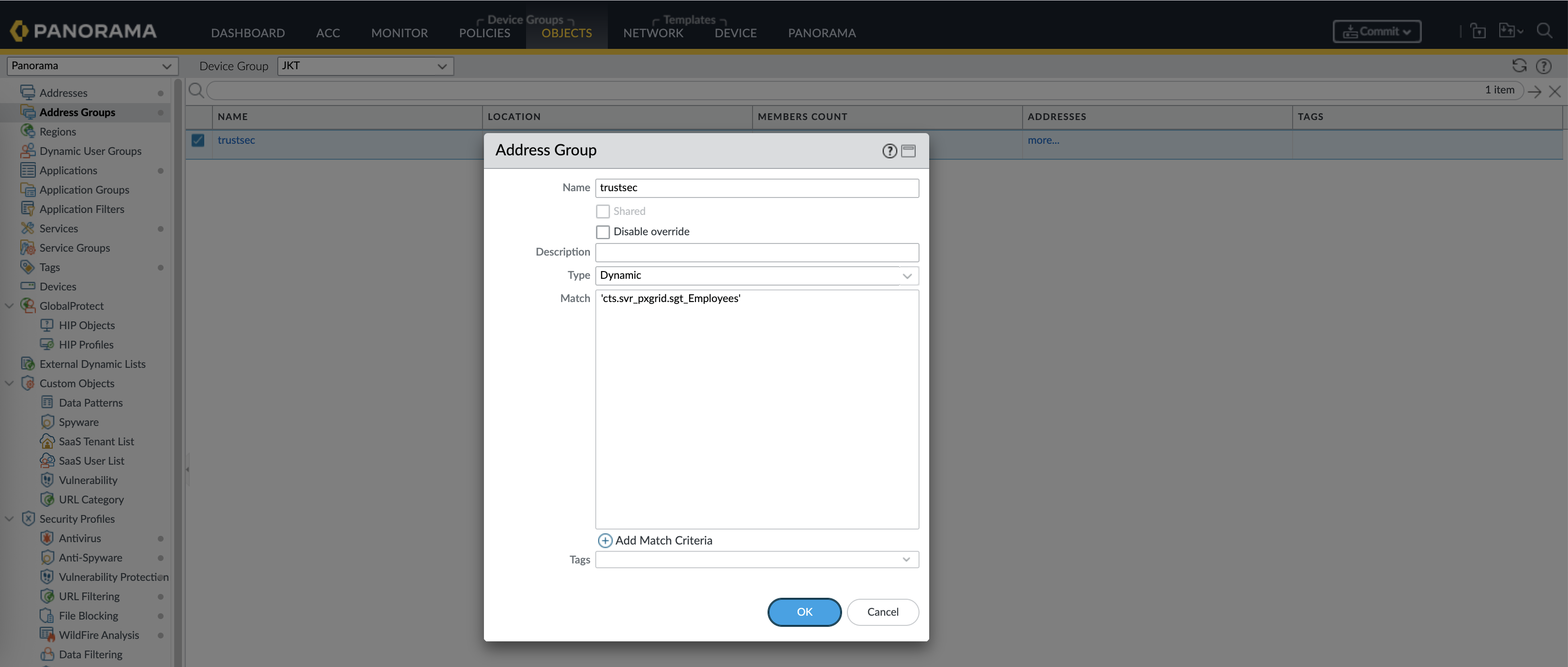
Now we can create a Dynamic Object and map it to an SGT
1
2
3
4
'cts.svr_<pxgrid server name>.sgt_<sgt name>'
## if more than 1 pxgrid server
'cts.svr_<pxgrid1 server name>.sgt_<sgt name>' or 'cts.svr_<pxgrid2 server name>.sgt_<sgt name>'
Next we can use the Dynamic Object in the Policy Rules
Validating TrustSec
Here we have an endpoint with SGT Employees connected to the network
On the Dynamic Object we created, we will be able to see the SGT-to-IP mappings for the specified SGTs