pfSense OpenVPN Remote Access
OpenVPN remote access allows users to securely connect to a central network over the internet. Users install OpenVPN client software, authenticate with the server, and establish an encrypted tunnel. Once connected, users can access network resources as if they were on-site, with traffic routed securely through the VPN tunnel.
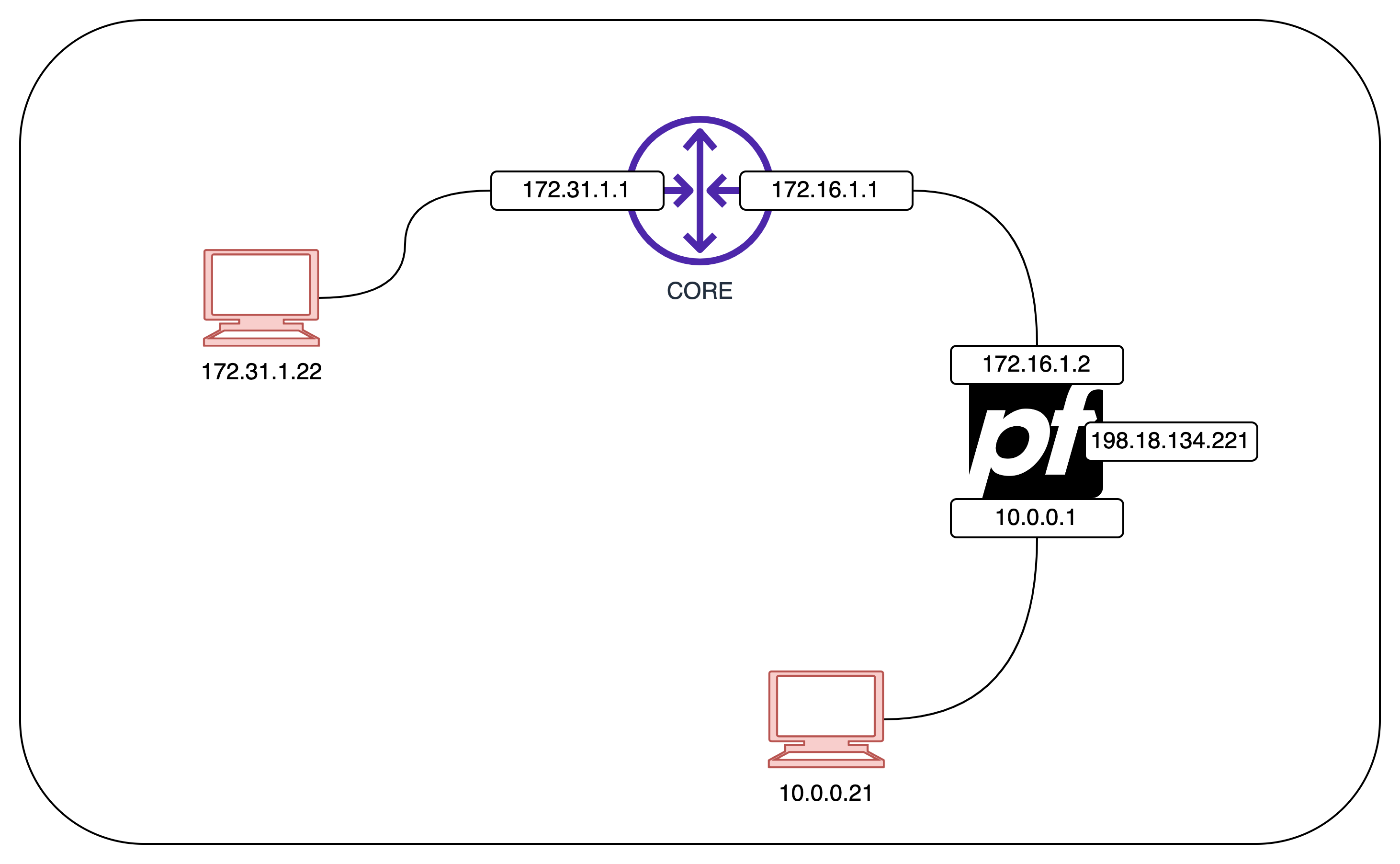
Here’s the topology of this deployment
Managing Certificates
OpenVPN utilizes SSL/TLS protocols for encryption, providing a secure connection over the internet. Certificates play a crucial role in OpenVPN’s security framework, as they are used for authentication between the client and the server.
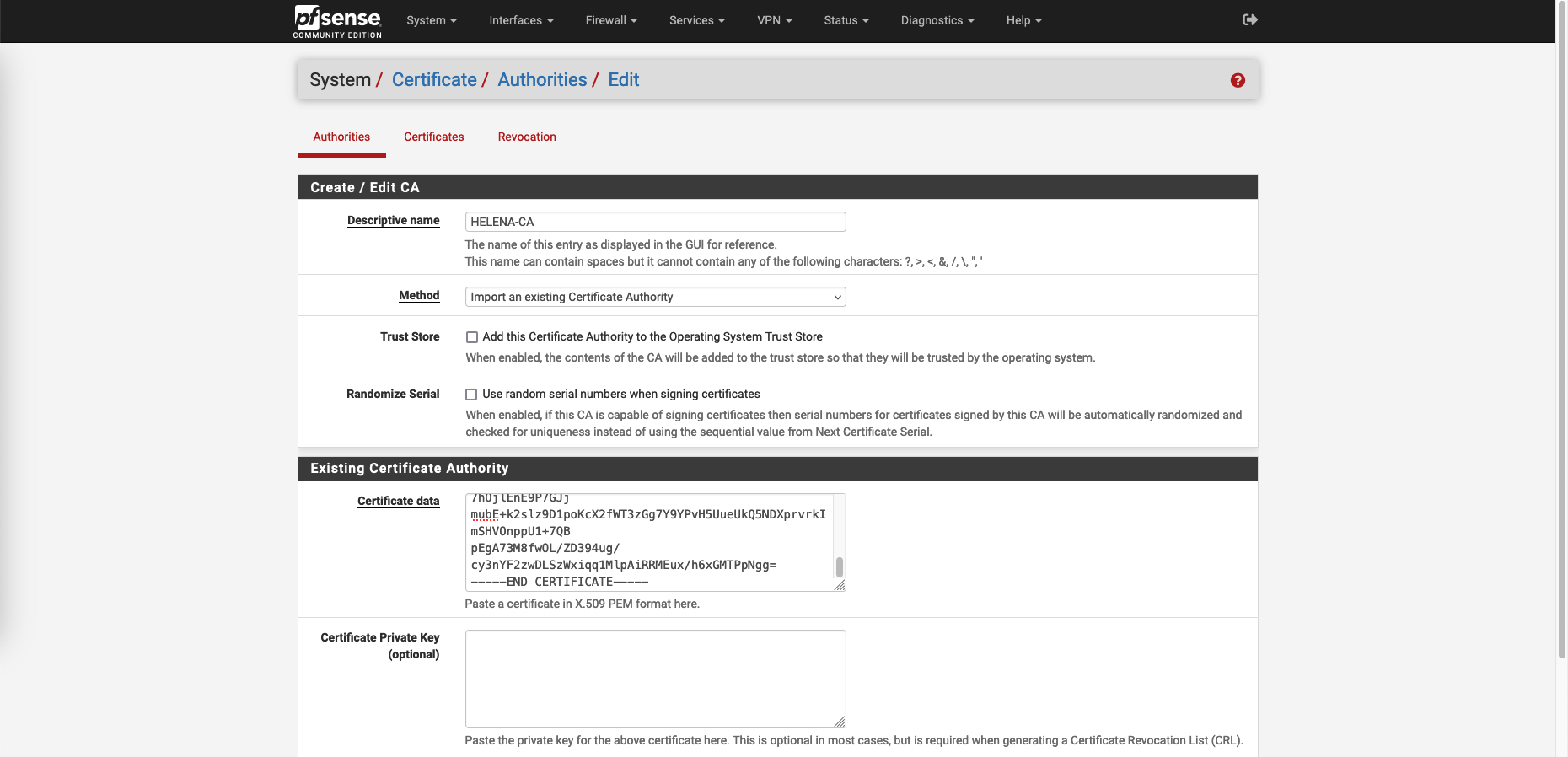
Here we already have a CA server, so lets just add it as our Trusted CA on pfSense on System » Certificate » Authorities
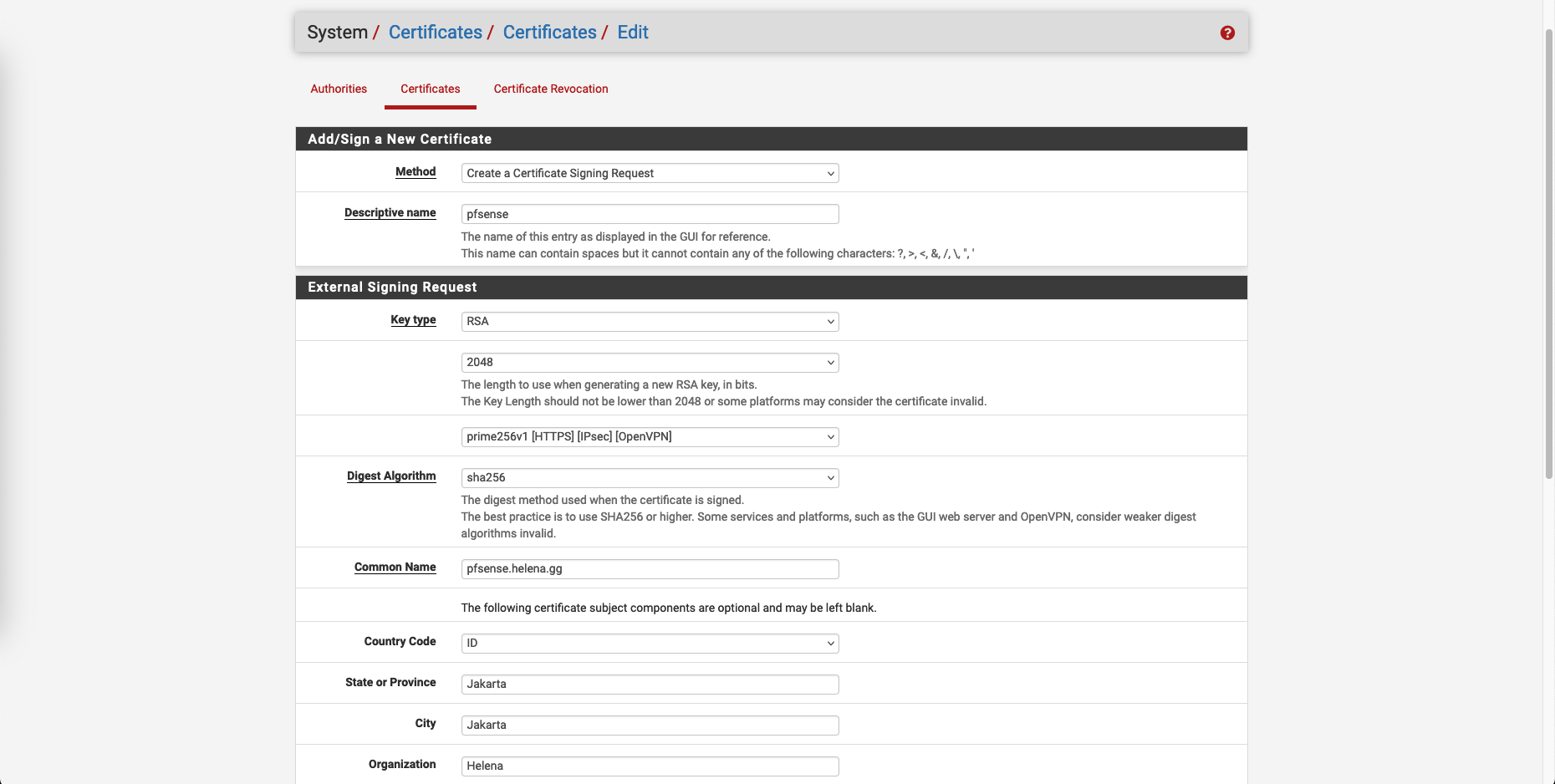
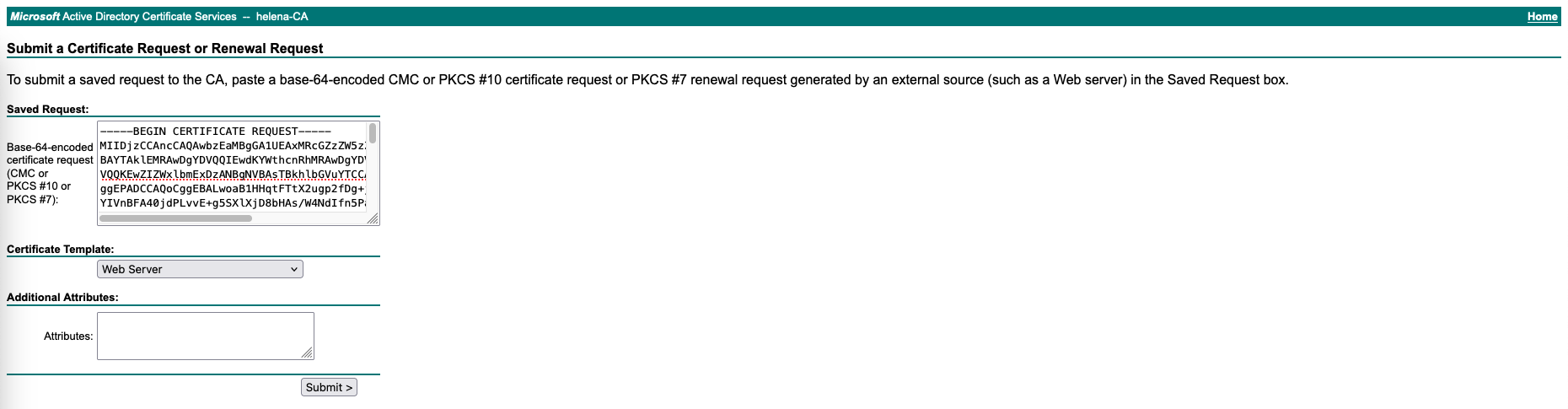
Next create a CSR for our pfSense’s certificate
Sign it on Helena-CA
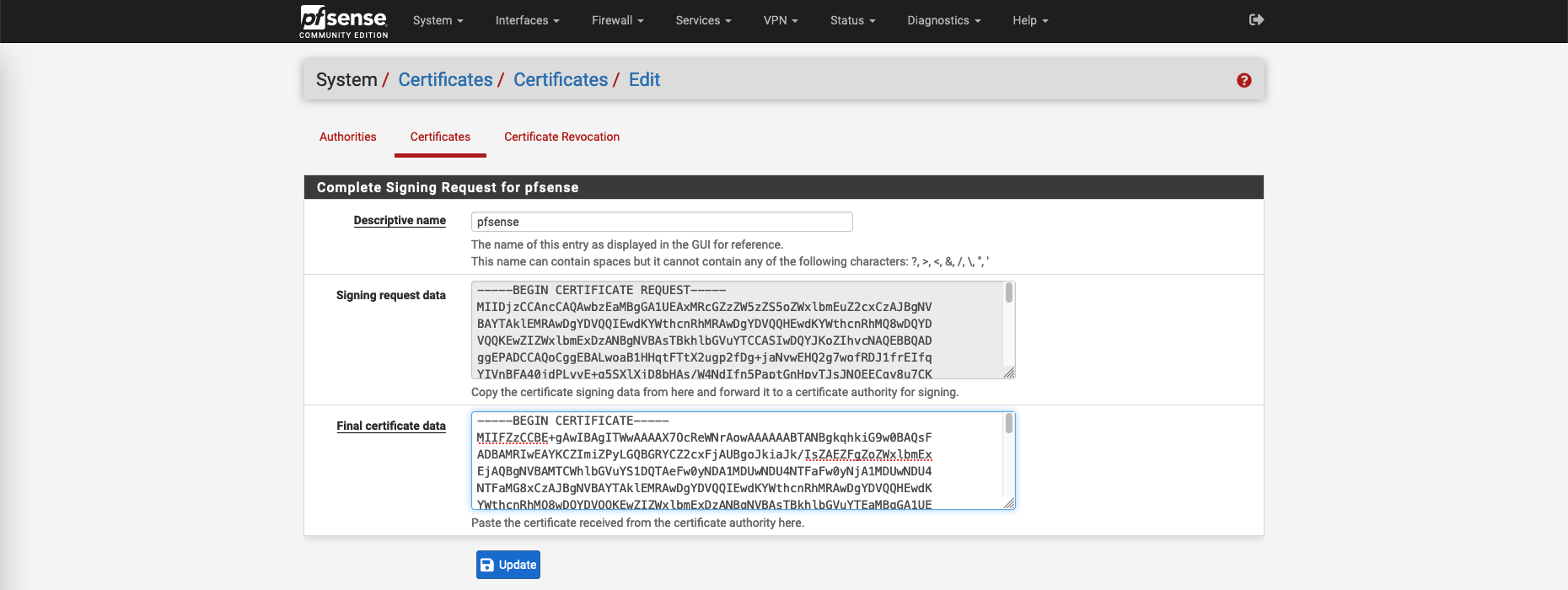
Complete the CSR by adding the final certificate on System » Certificate » Certificates
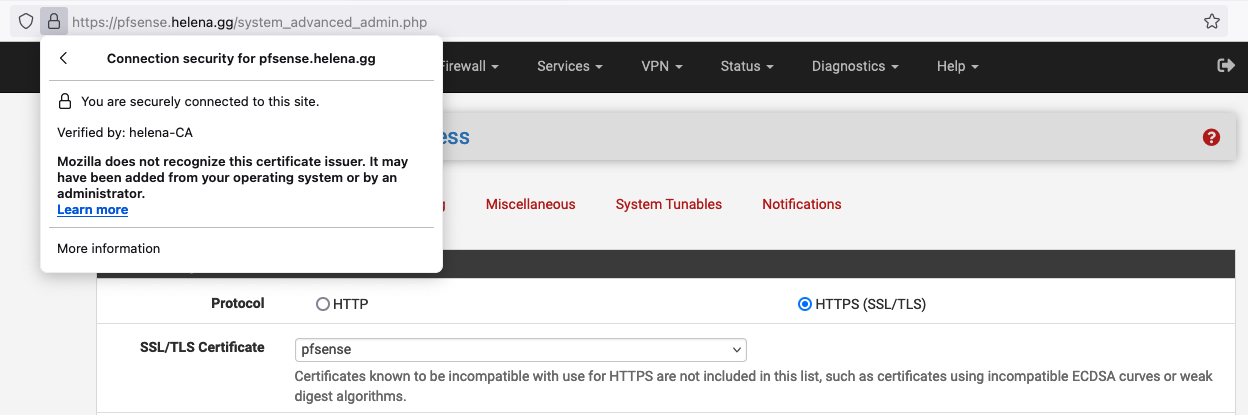
Bonus and completely optional, use that certificate on our web server on System » Advanced » Admin Access so we get a trusted secure HTTPS connection
Configuring OpenVPN Remote Access
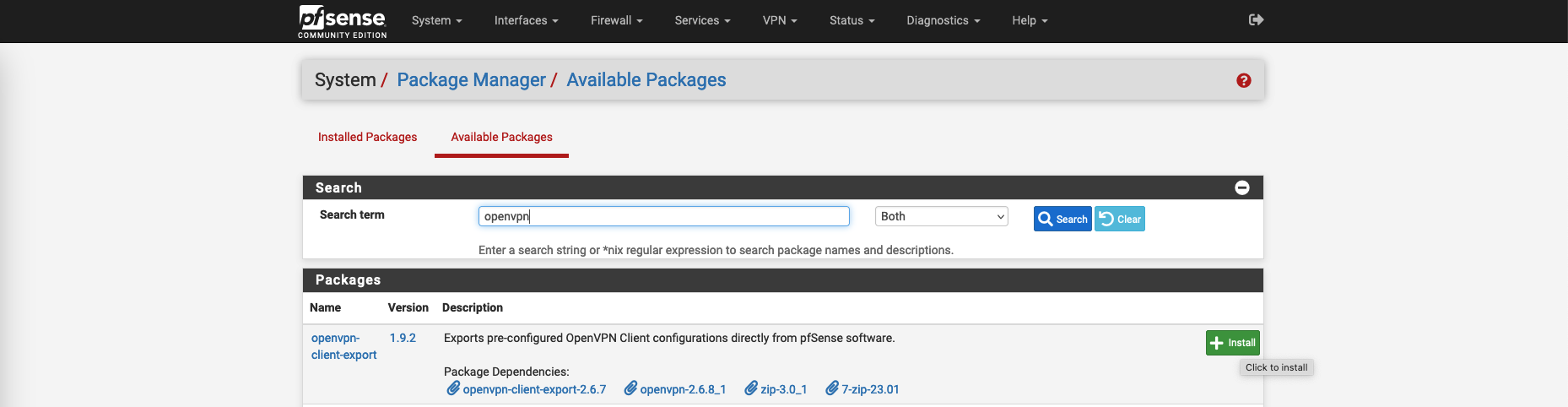
Before configuring OpenVPN, lets install a package to ease the process of exporting OpenVPN Client Configuration later
To configure OpenVPN, go to VPN » OpenVPN » Wizard, select the type of Local User Access
Here select our trusted CA
Then select the newly created certificate
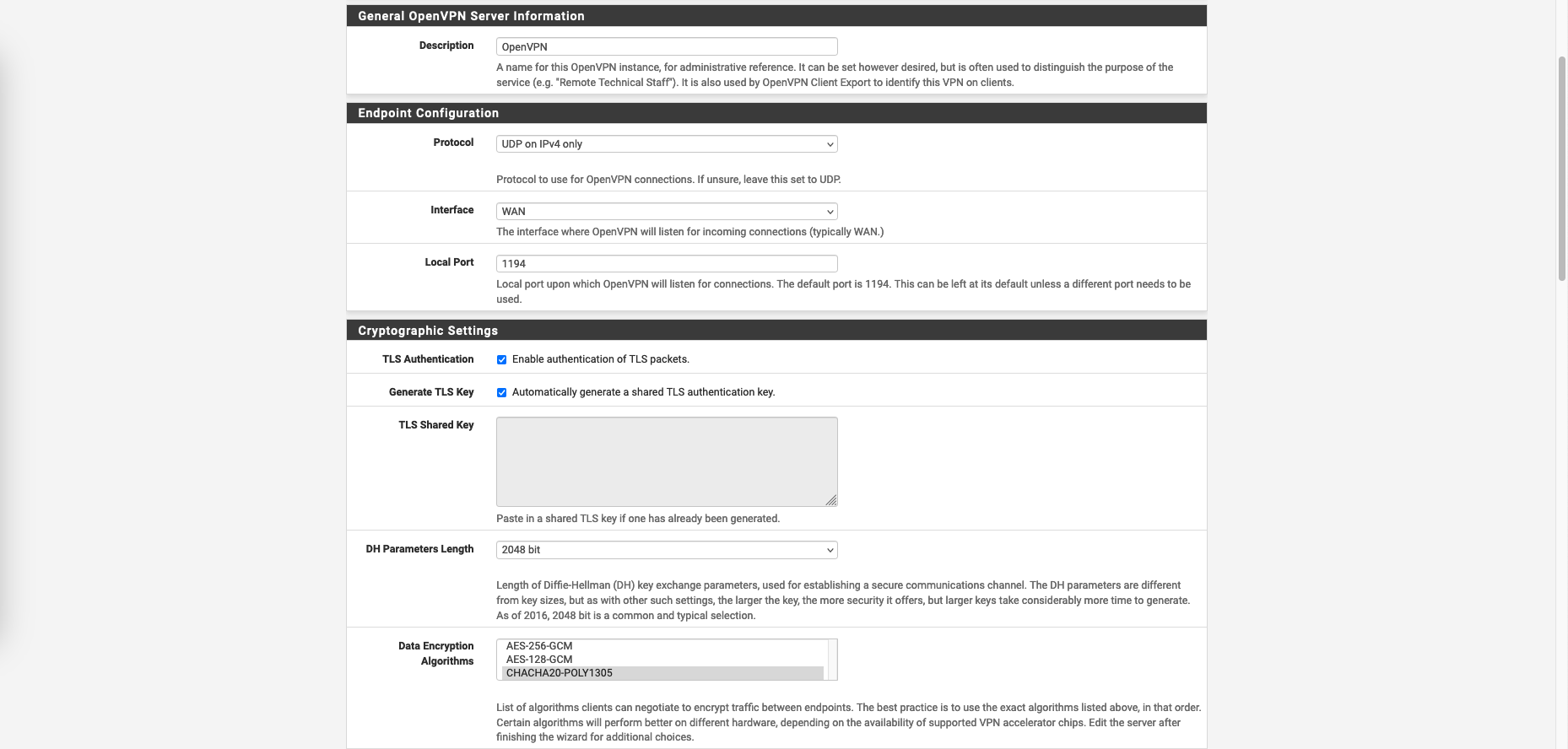
Here give it a name, select the interface and used port
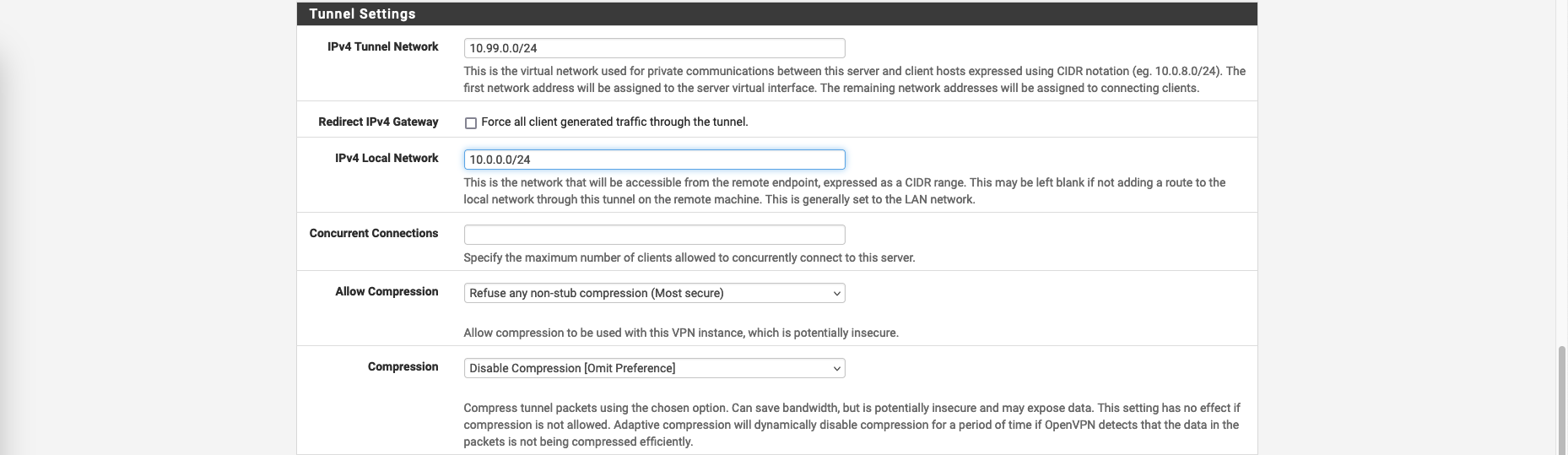
On Tunnel Settings, configure the Tunnel Network for our VPN Clients to use, then declare the internal network to be accessed by VPN users on IPV4 Local Network. Also disable Redirect IPV4 Gateway to enable Split Tunneling
VPN split tunneling is a feature that allows a VPN user to divide their internet traffic into two separate streams: one that is routed through the VPN tunnel to the VPN server, and another that is sent directly to the internet without passing through the VPN.
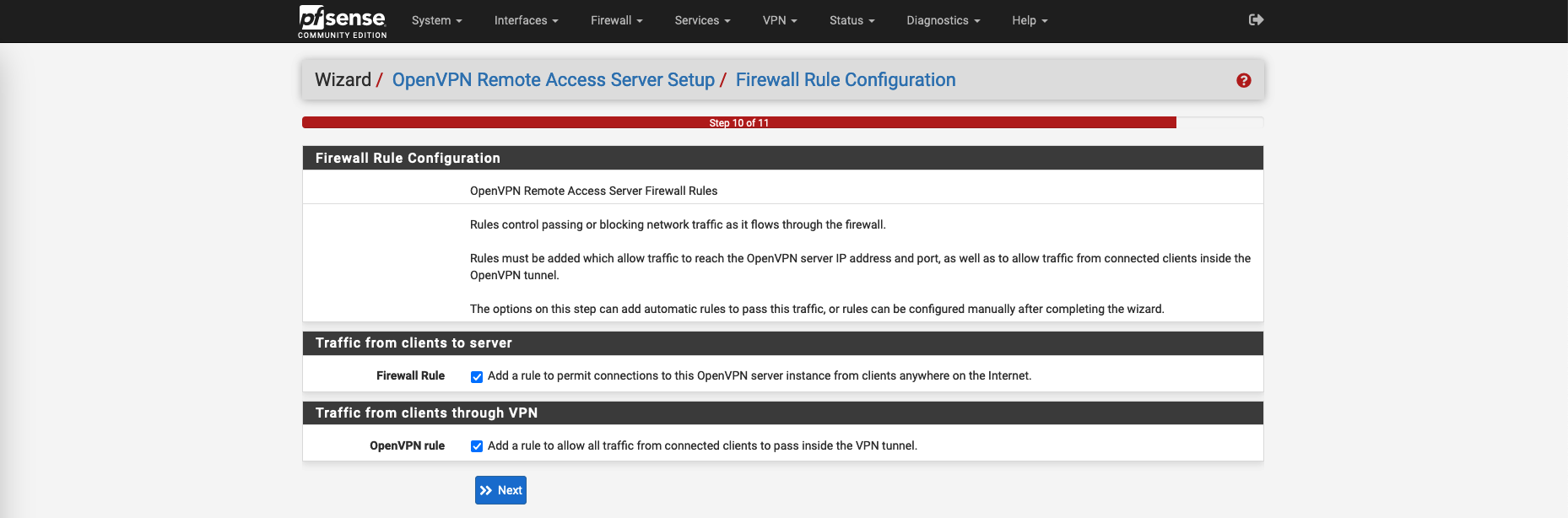
Select both firewall rules to be automatically created by the wizard
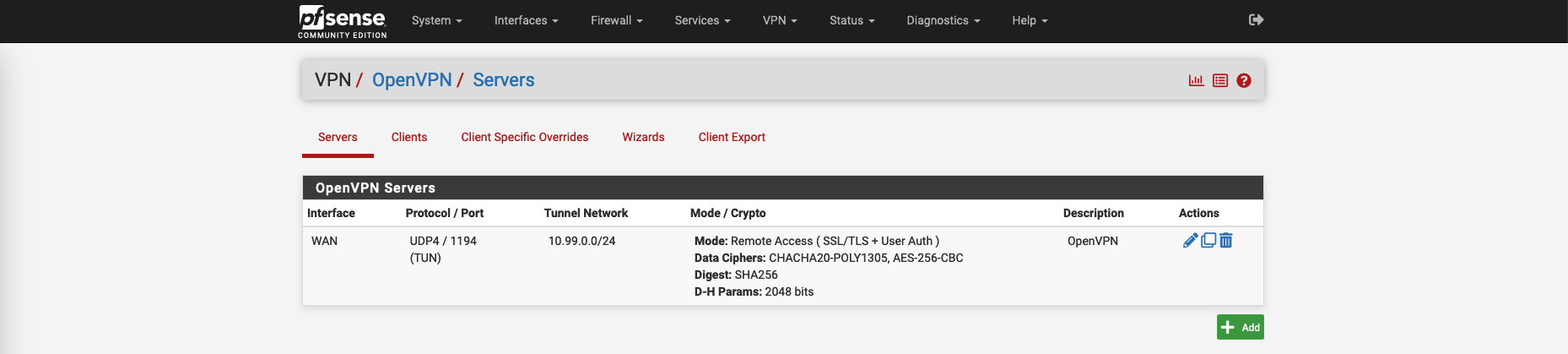
Now the OpenVPN is up and running
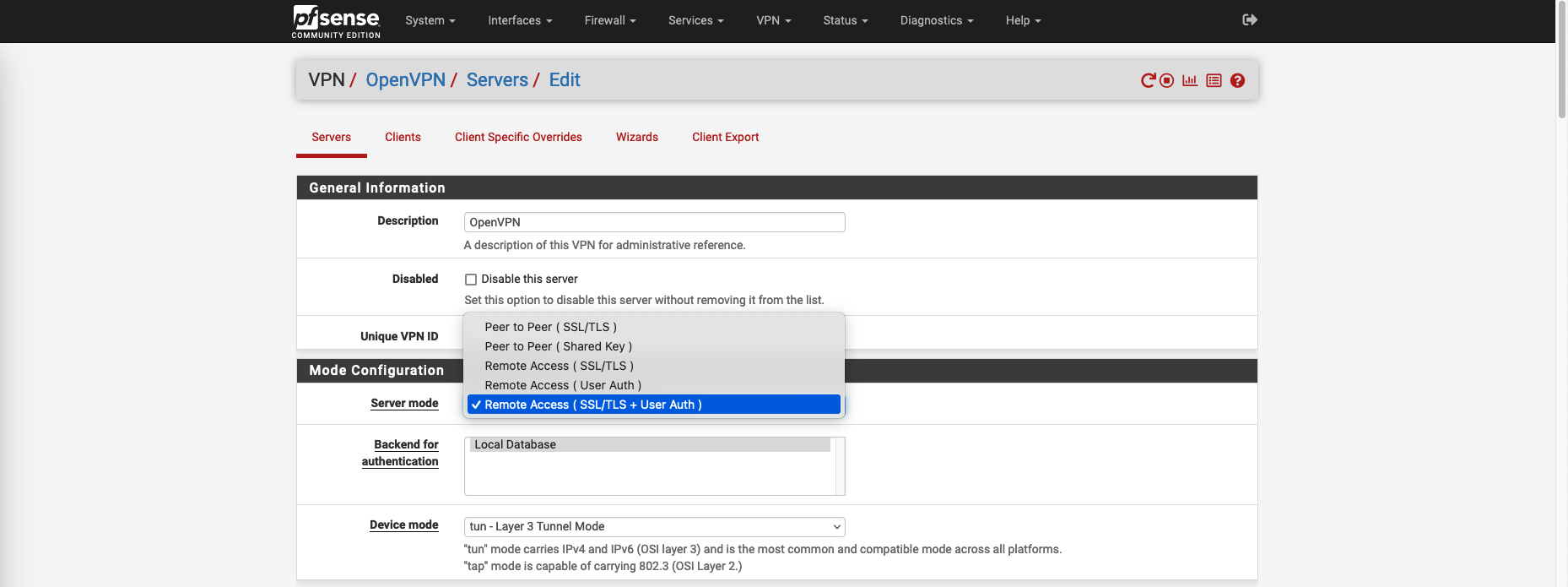
If we edit the VPN, we can see we have multiple server modes, this setting basically dictates how the authentication is done between clients and server. Here we select SSL + User Auth meaning clients will be asked to have both personal user certificate and credentials to connect to the VPN.
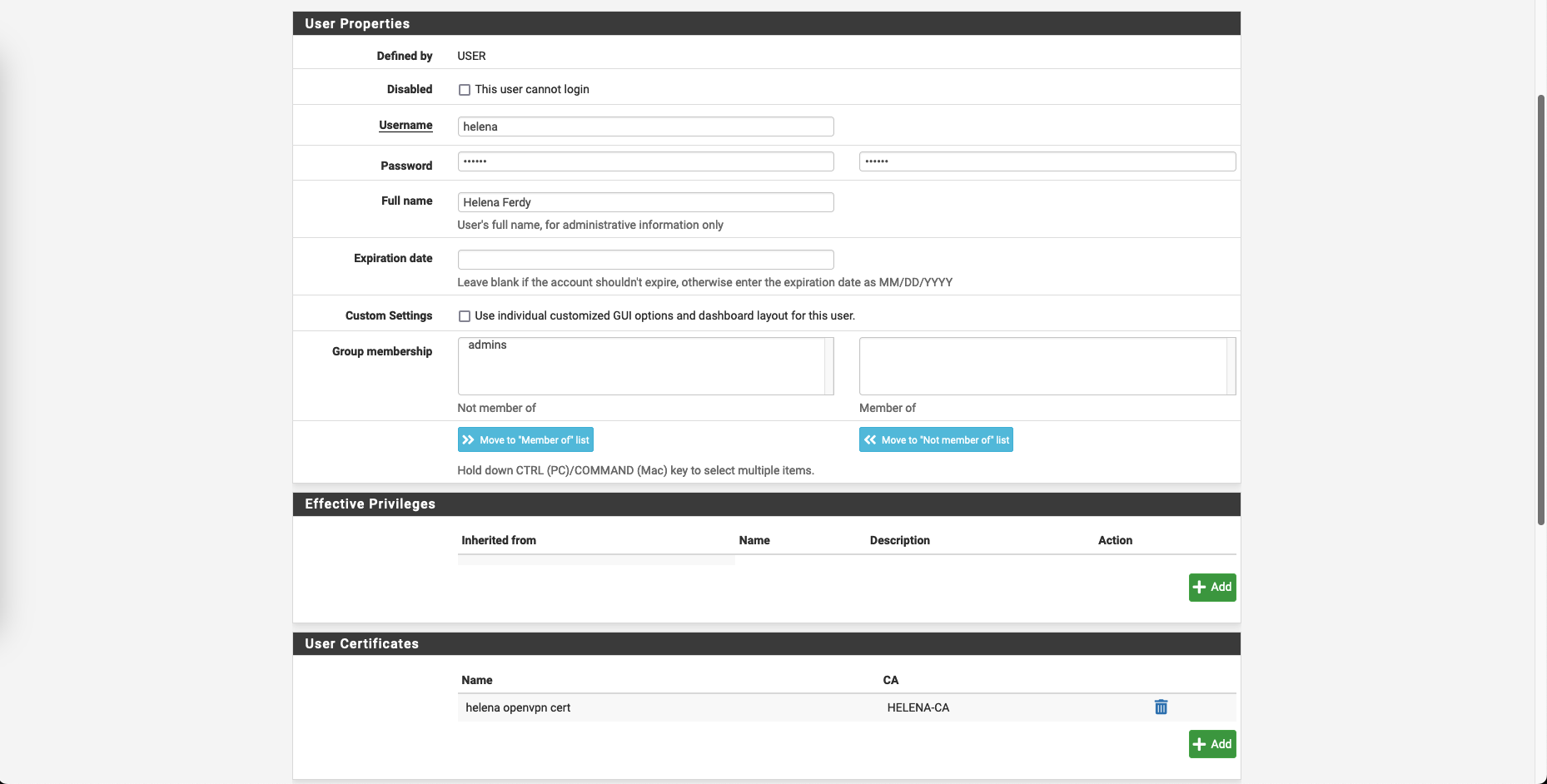
Configuring VPN Users
On System » User Manager, create new user with having user certificate signed by the CA
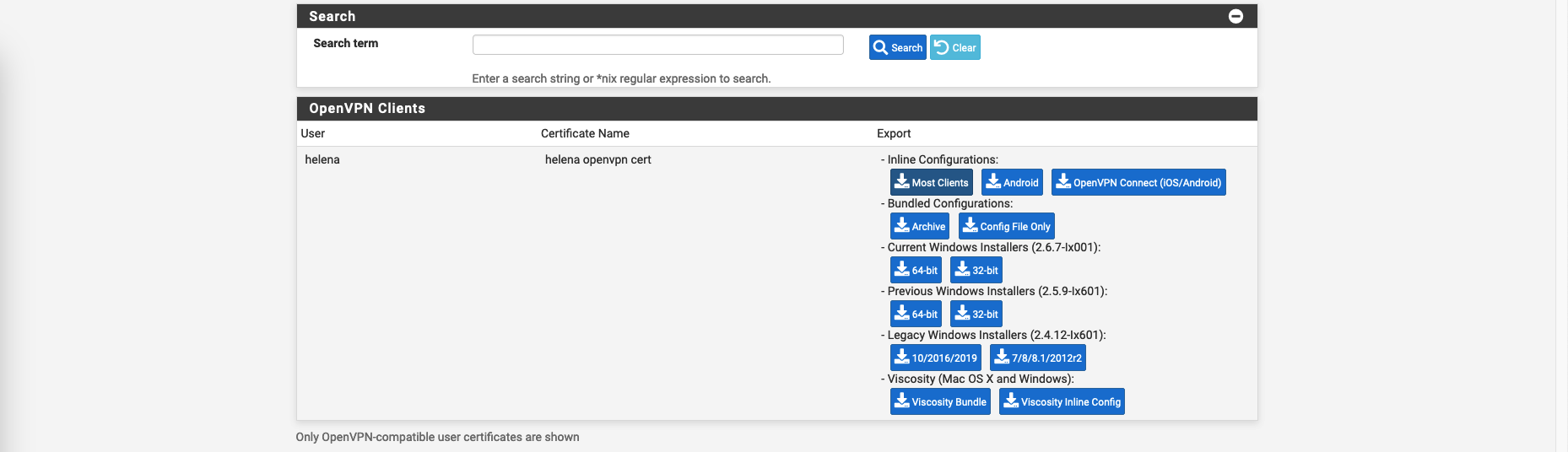
Exporting VPN Configurations
On VPN » OpenVPN » Client Export, download the Inline Configurations and the VPN Client Installers
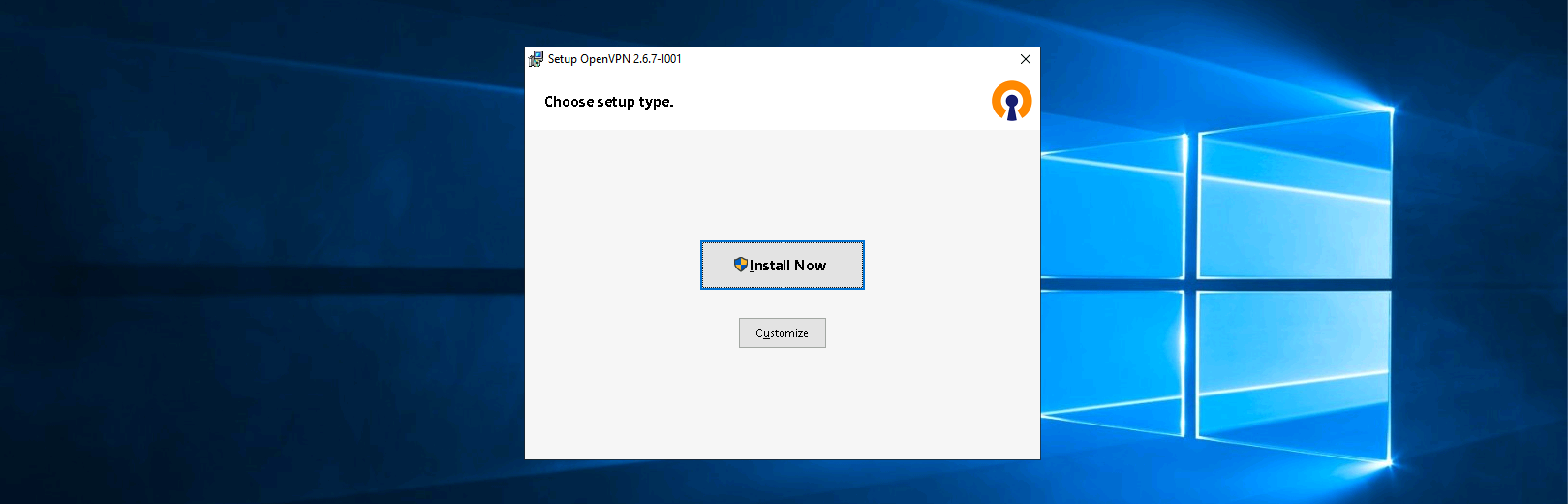
Connecting to VPN
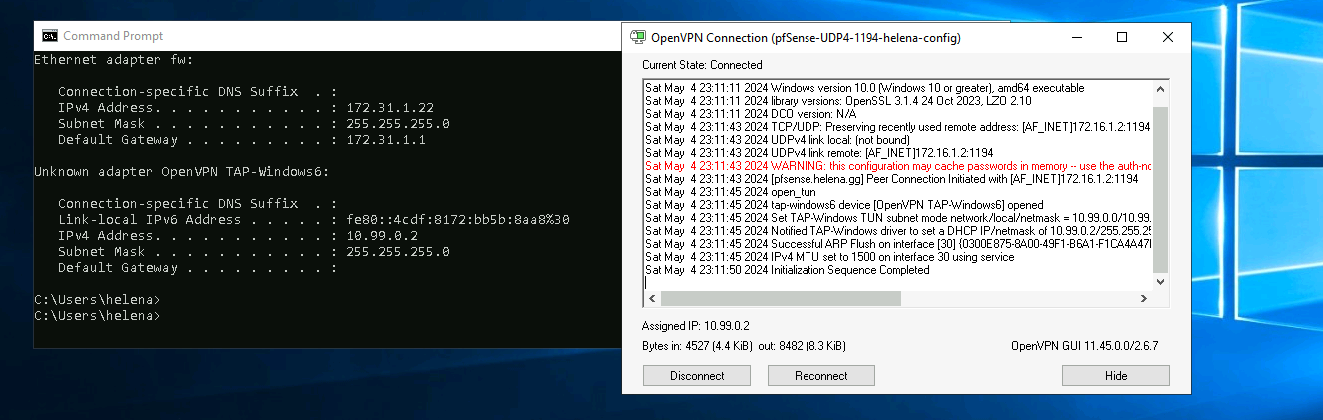
On the Client PC, install the VPN Client
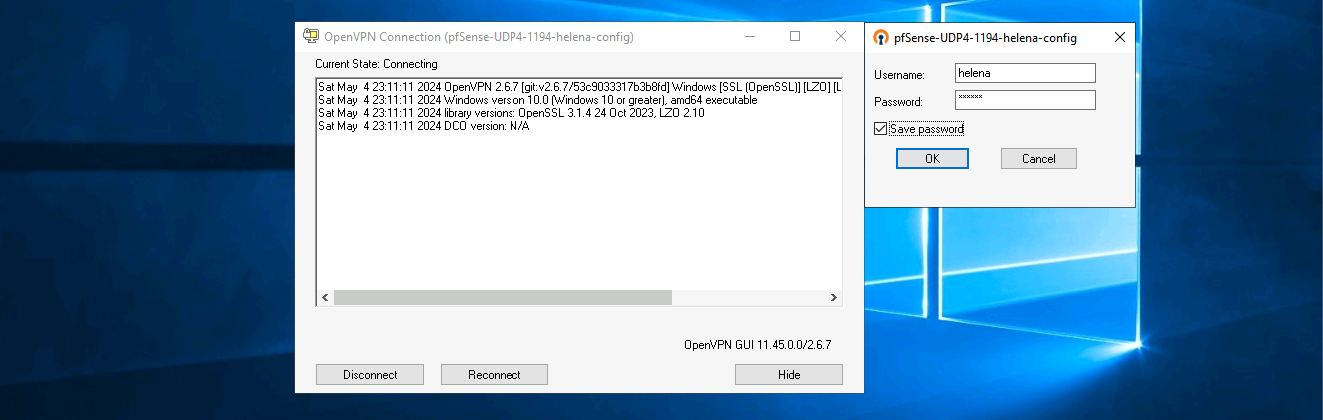
Now connect using the exported config and user/password
And we have successfully connected to the VPN
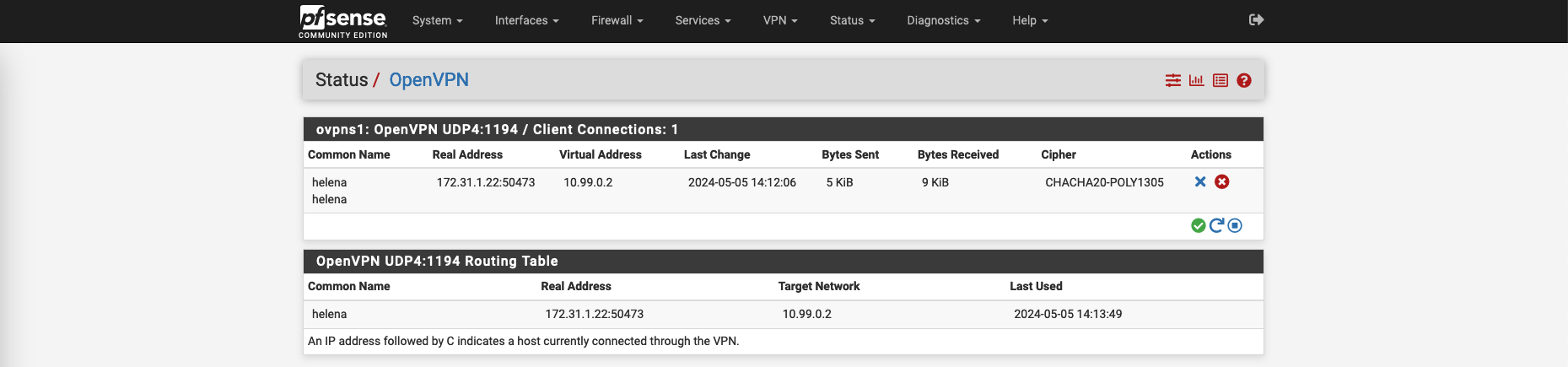
Back on pfSense, on Status » OpenVPN, we can see the user helena is connected
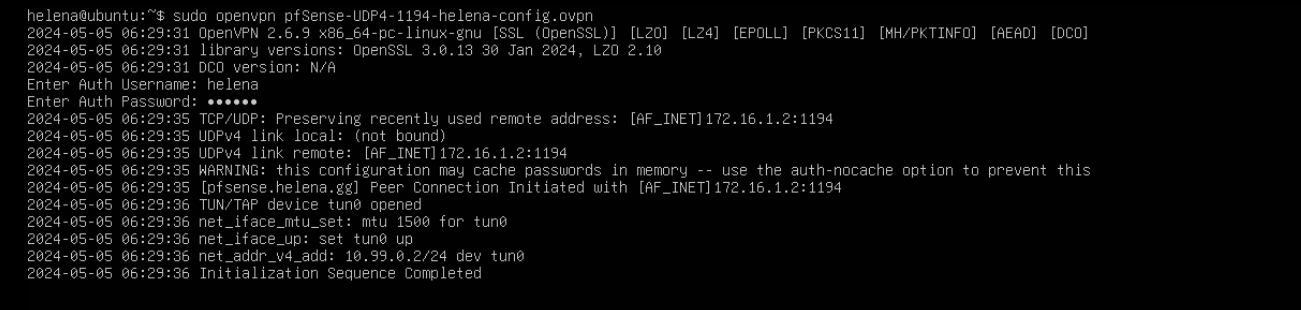
On Linux, we can simply run the command “openvpn” followed by the exported config, then enter credentials
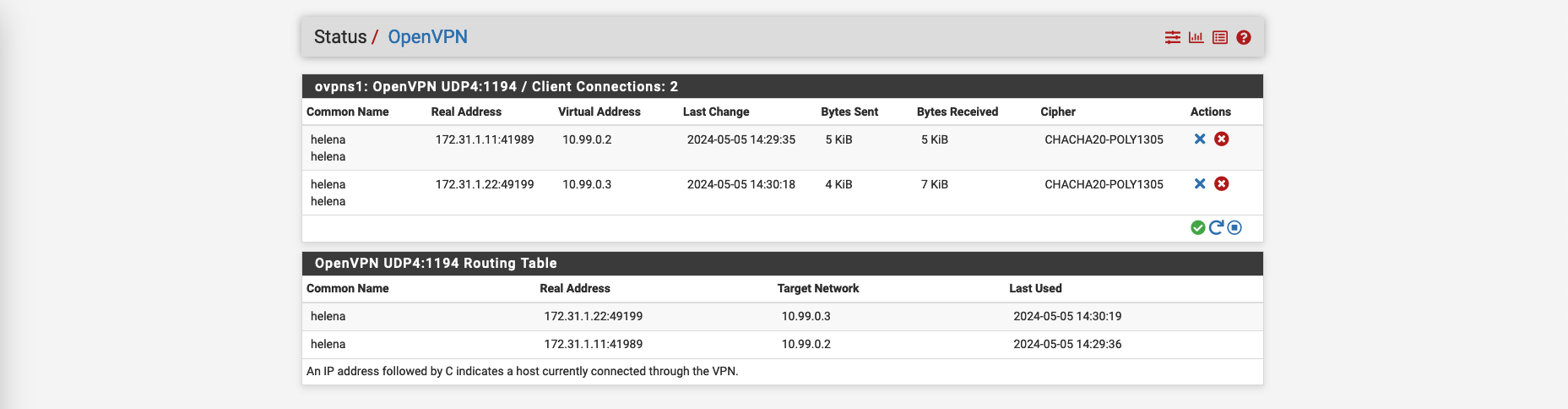
We can see that the linux client has also been connected