Cisco SD-WAN - Direct Internet Access (DIA)
What is Direct Internet Access?
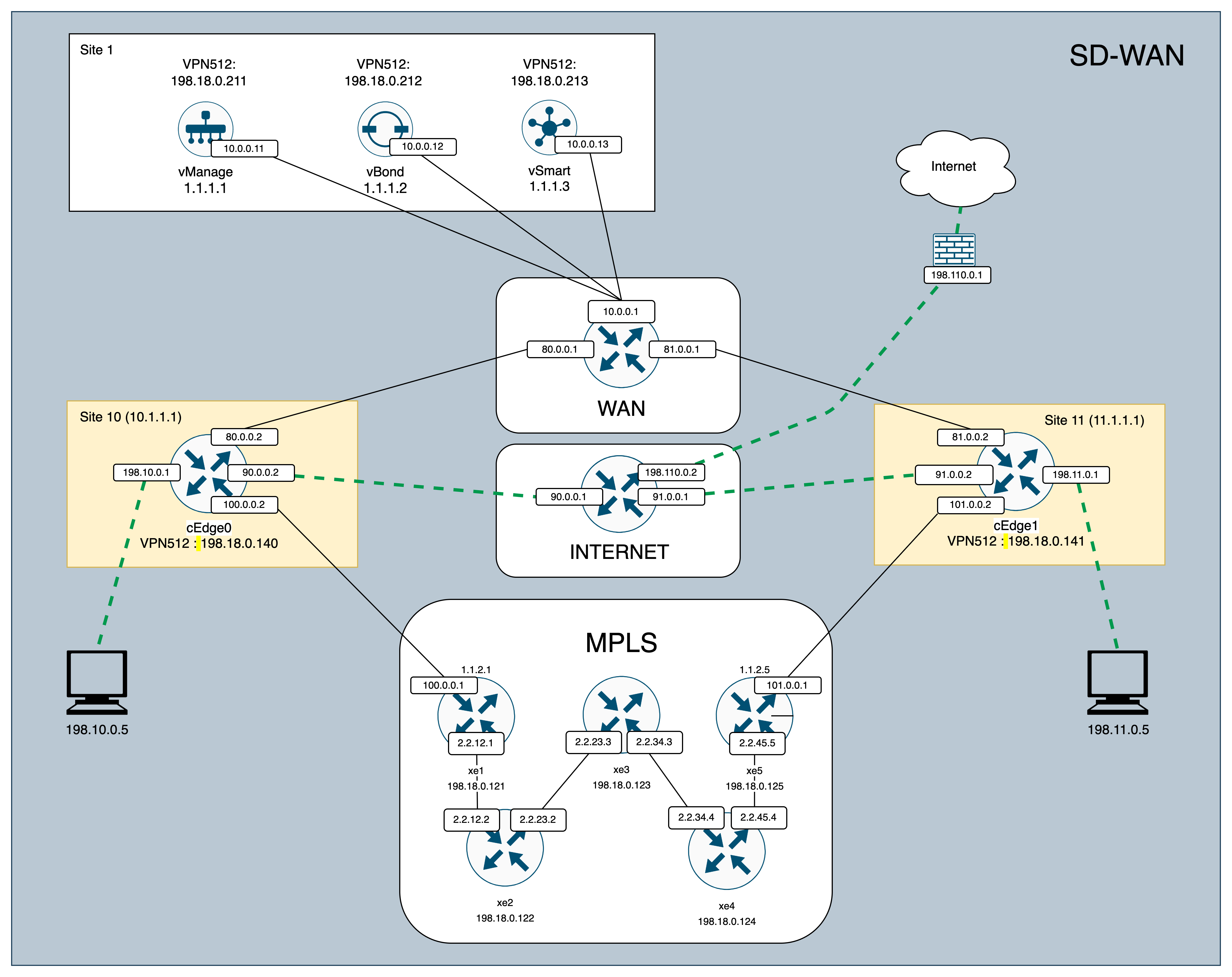
Direct Internet Access is a networking solution that lets branch routers connect directly to the internet for improved performance and efficiency, using intelligent traffic routing and security features.
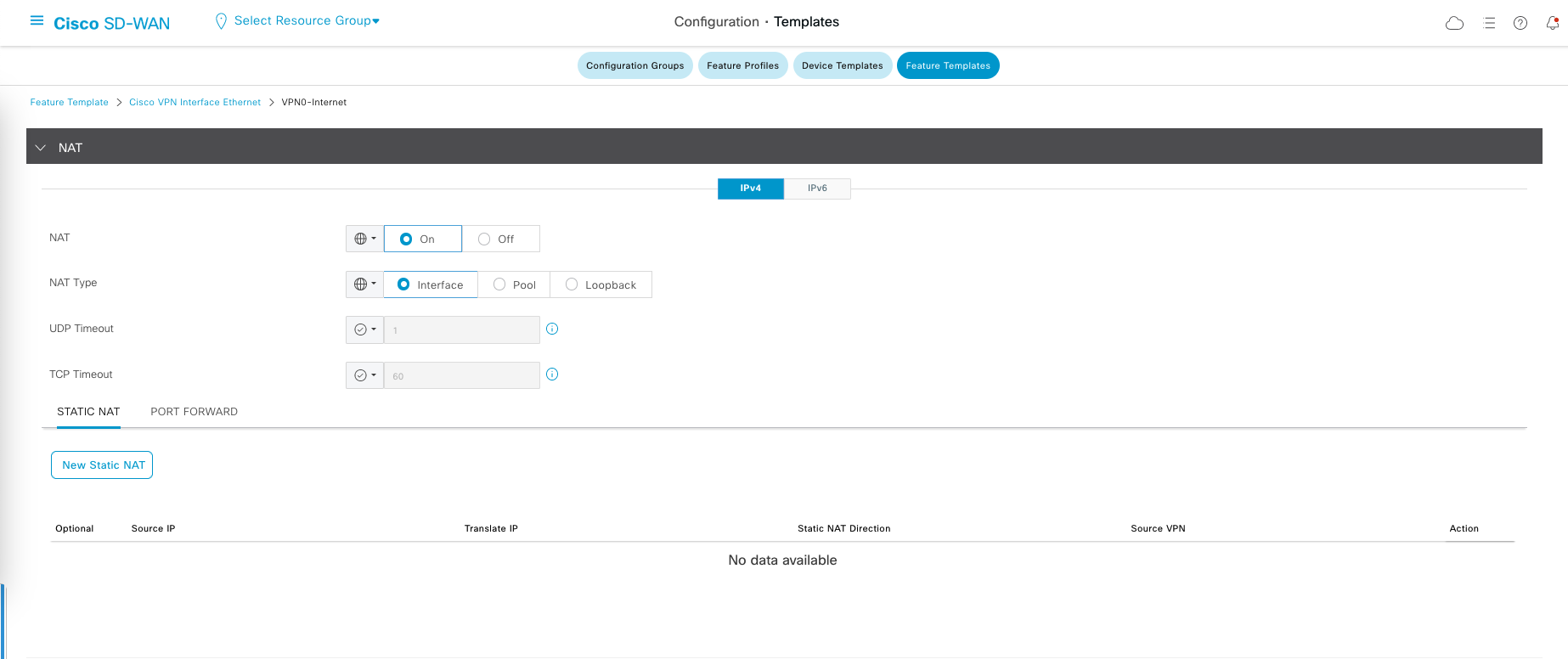
Configuring NAT on Feature Template
First, Open the Feature Teamplate for the Interface facing the Internet, then enable NAT
Configuring Policies
Now we configure policies to allow users on site 10 and 11 to access the Internet.
Go to Configuration » Policies, Create new Centralized Policy
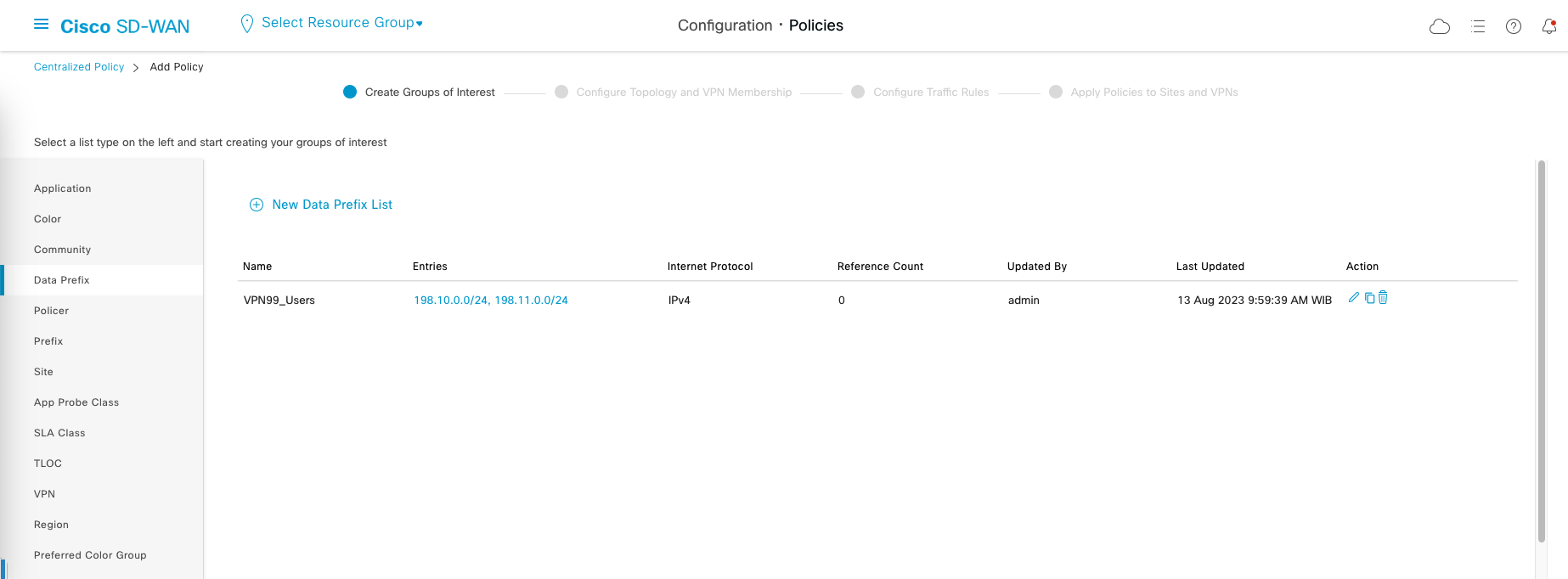
Then on Data Prefix, create a prefix list containing the prefix of Site 10 and Site 11 IP
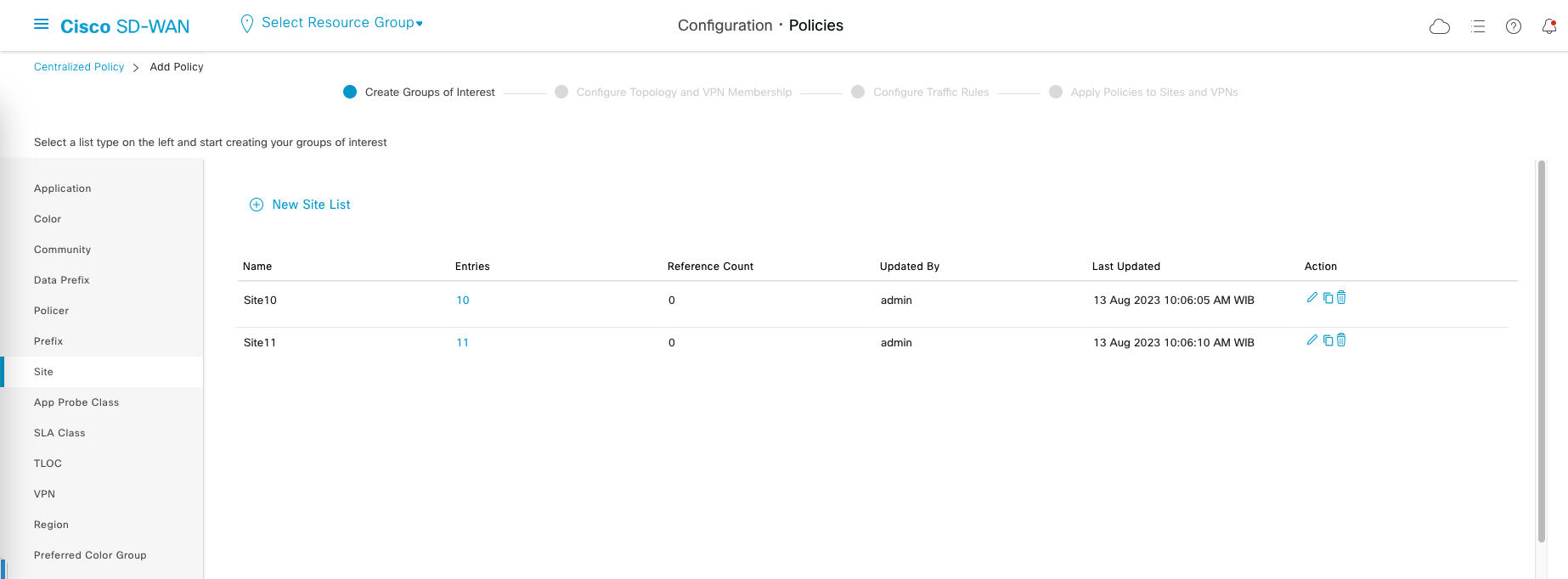
Next create Site Lists
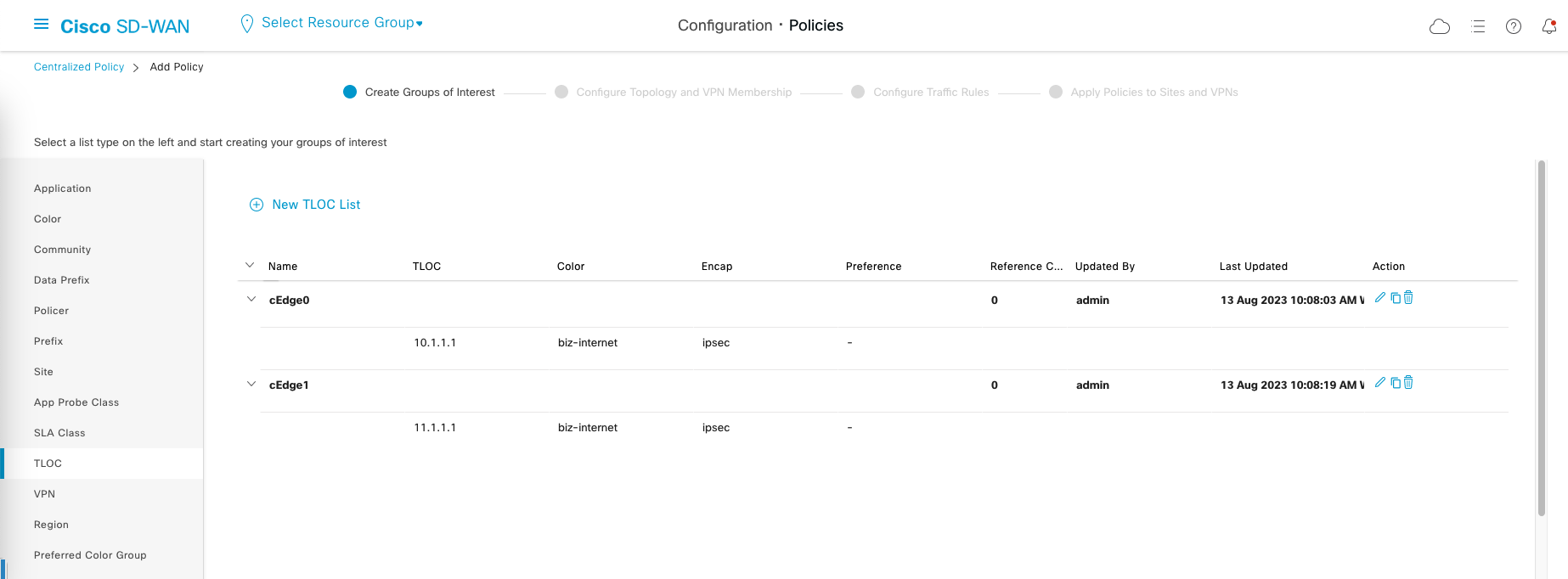
Then create a TLOC lists of both sites
TLOC (transport location) refers to a logical representation of a network site’s connectivity options. It defines how a site is connected to the WAN and specifies the transport technologies and characteristics available at that site.
Tlocs determines how traffic is routed and optimized within the SD-WAN network.
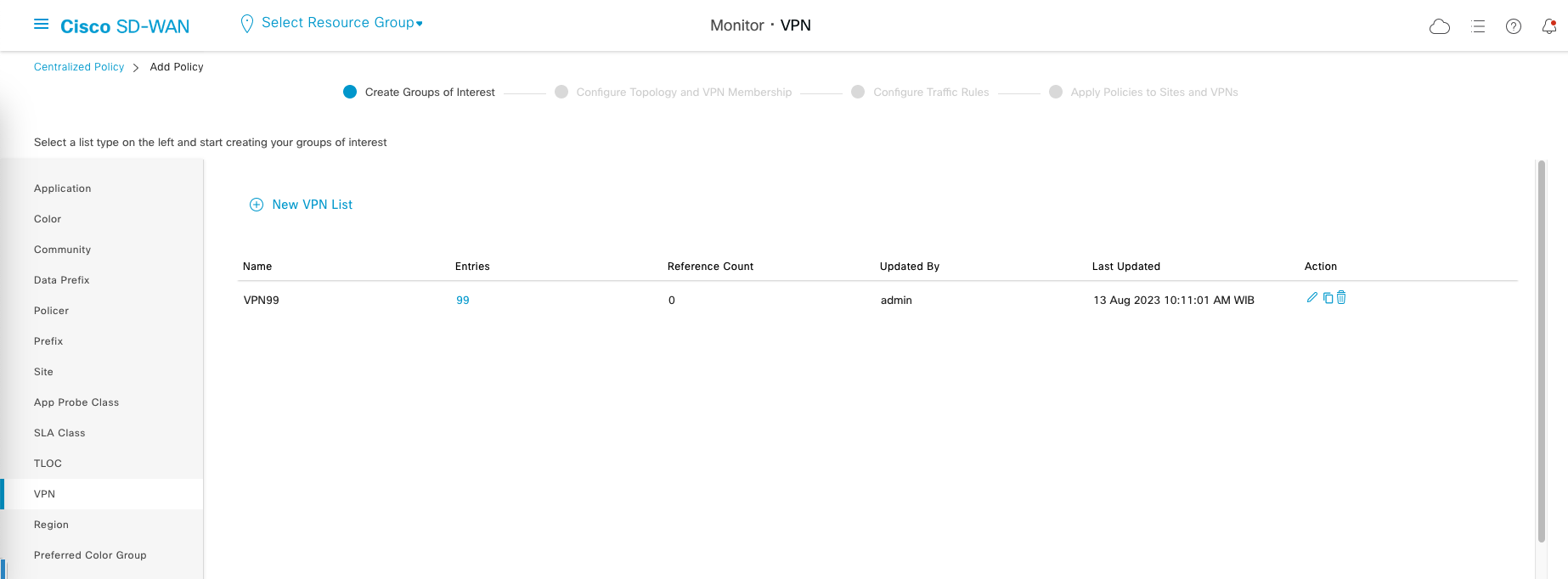
And then create VPN list, which we’ll only use the VPN 99, Click Next
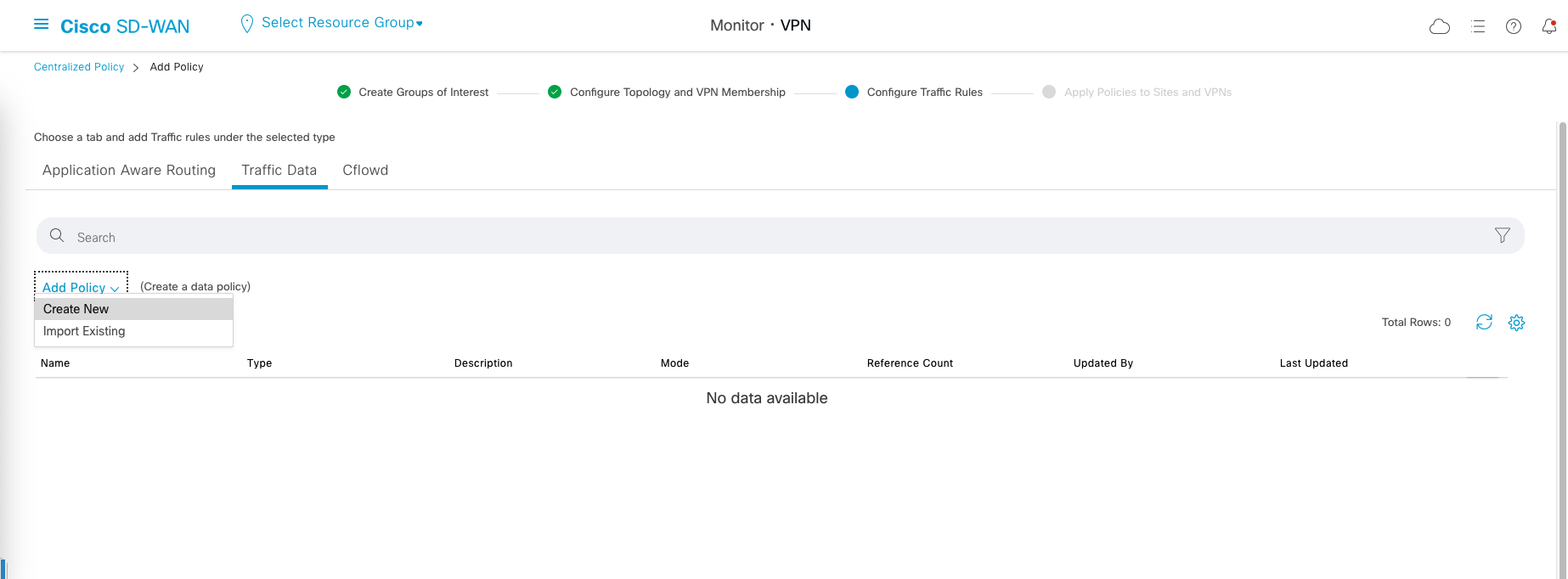
Under Configure Traffic Rules » Traffic Data, Create New Policy
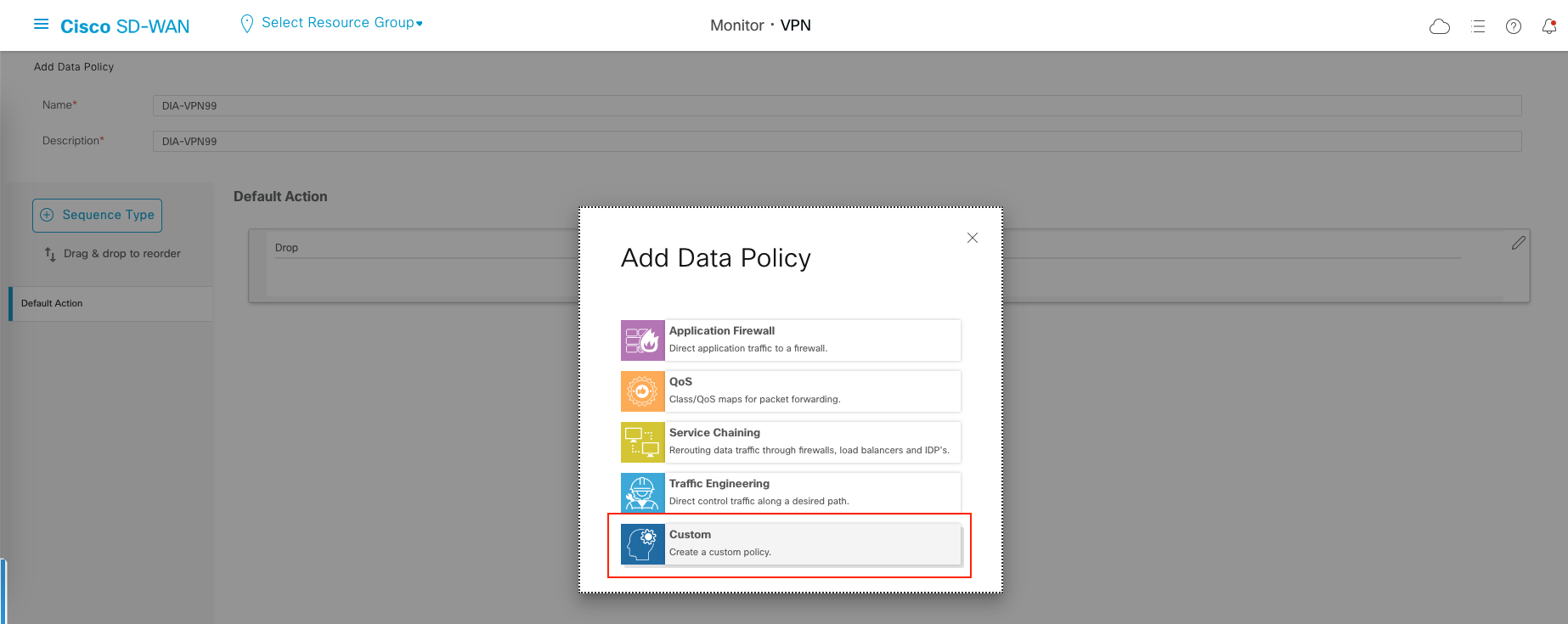
On Sequnce Type, select Custom
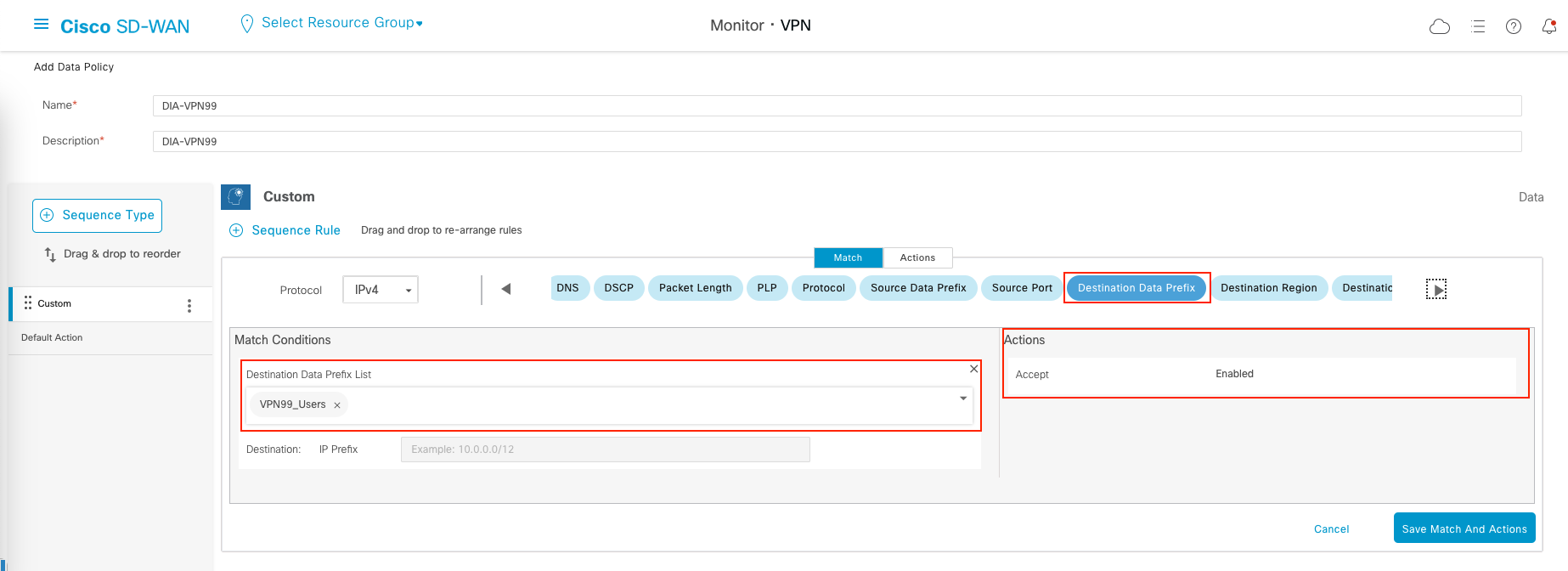
Create a Custom Rule to allow traffic to Destination Prefix of VPN99 Users
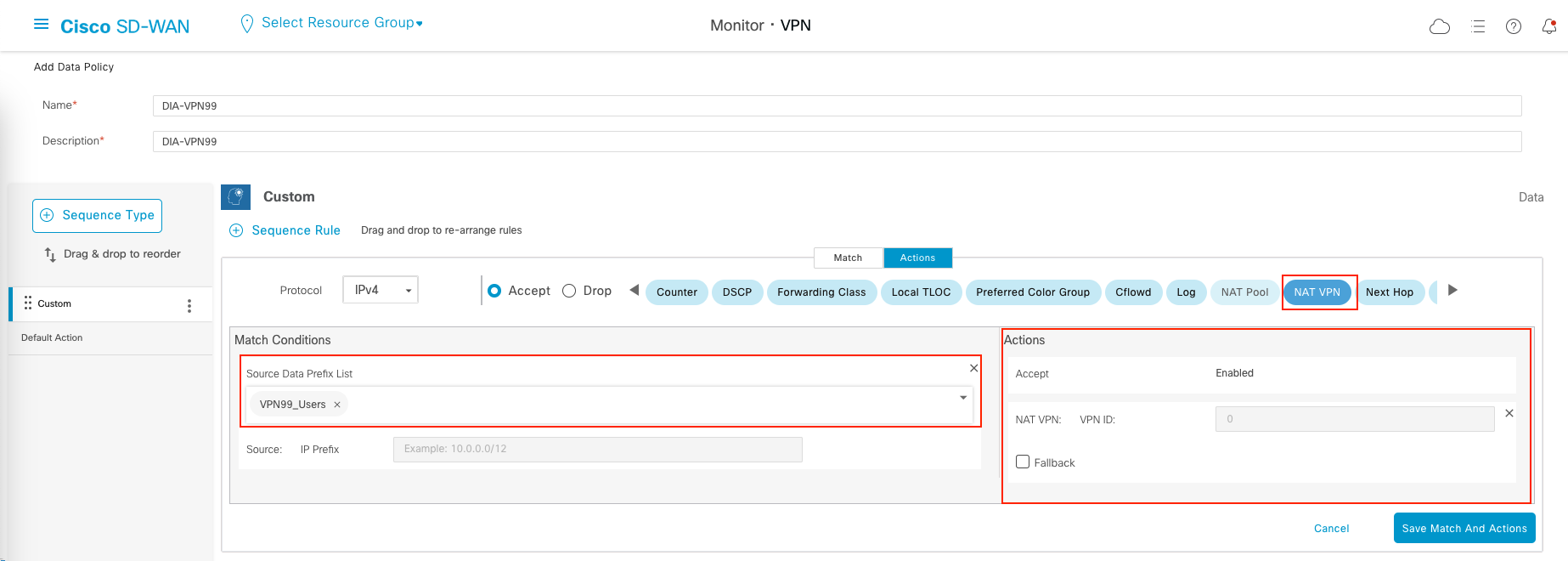
Add another rule that match traffic with Source Prefix of VPN99 Users, then send it to VPN0 NAT Enabled Interface
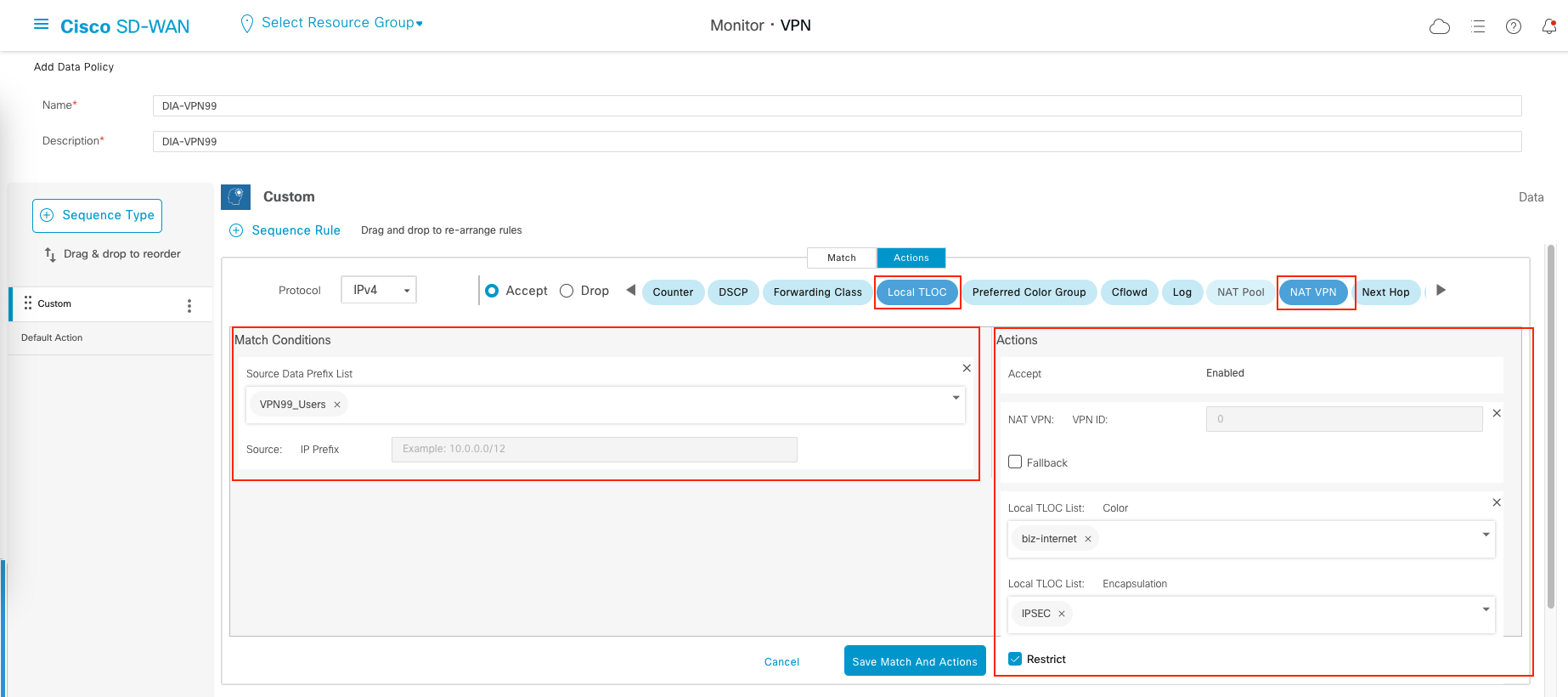
And create the last rule with similar config as the last one, but with additional local TLOC
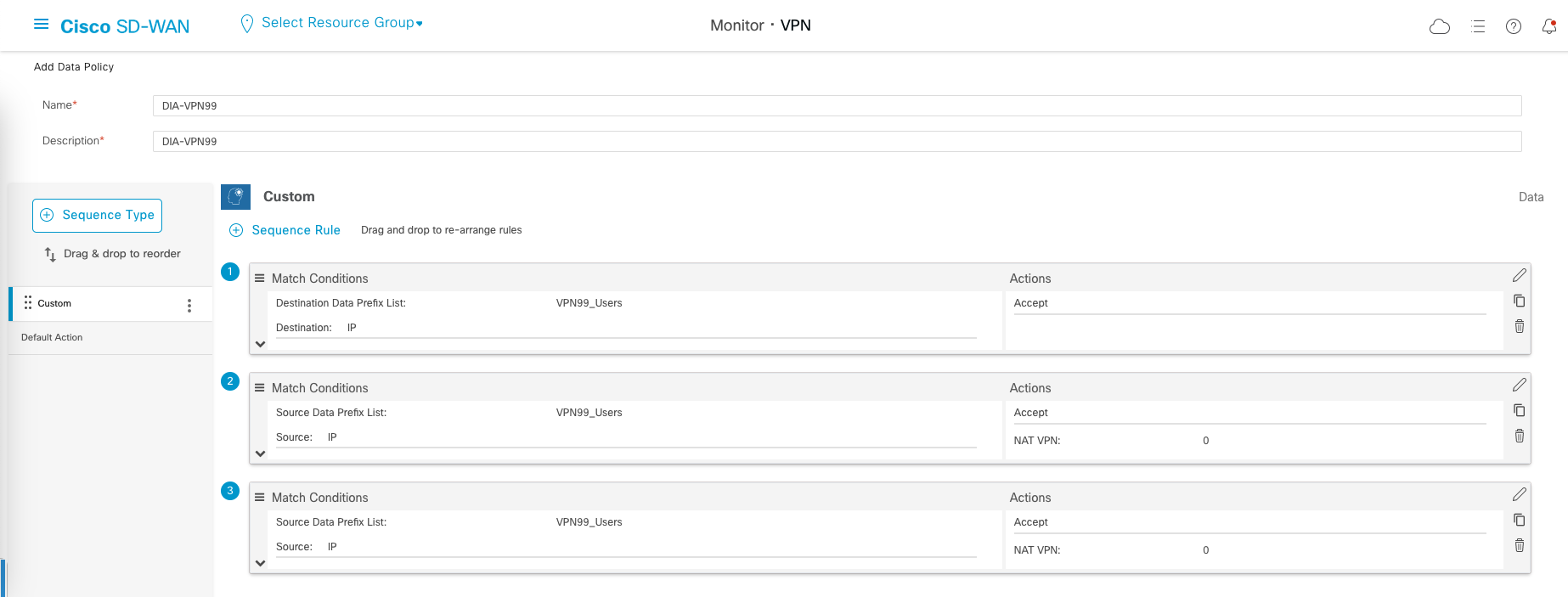
We end up with 3 sequence rules
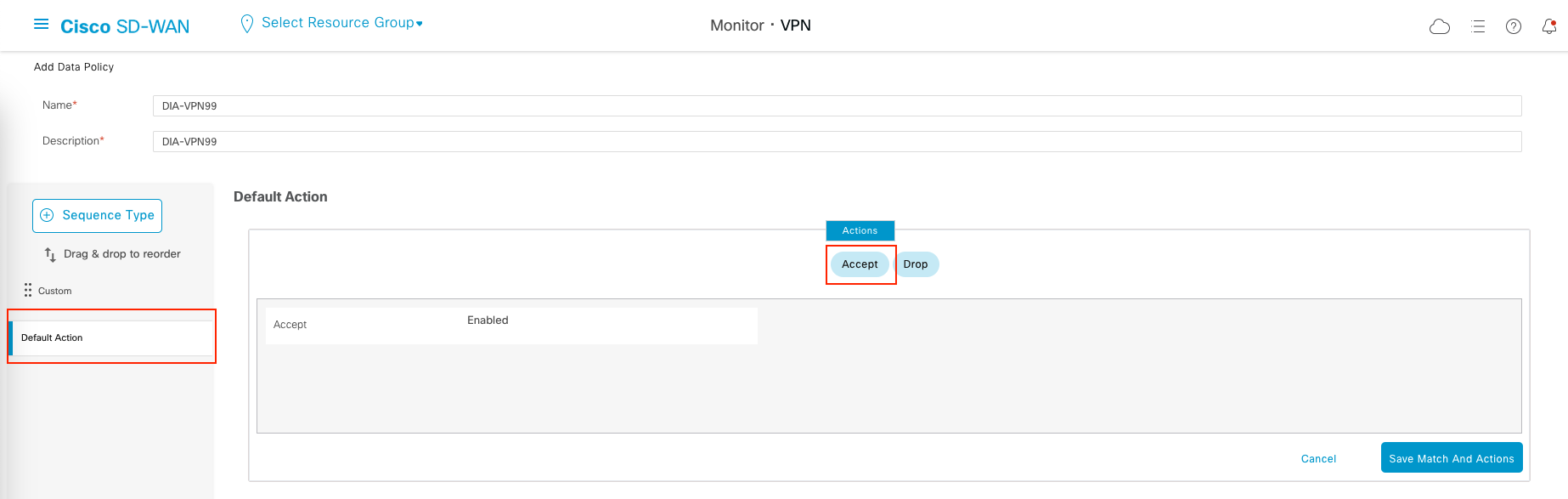
Then go to Default Action and choose accept. Save the Data Policy
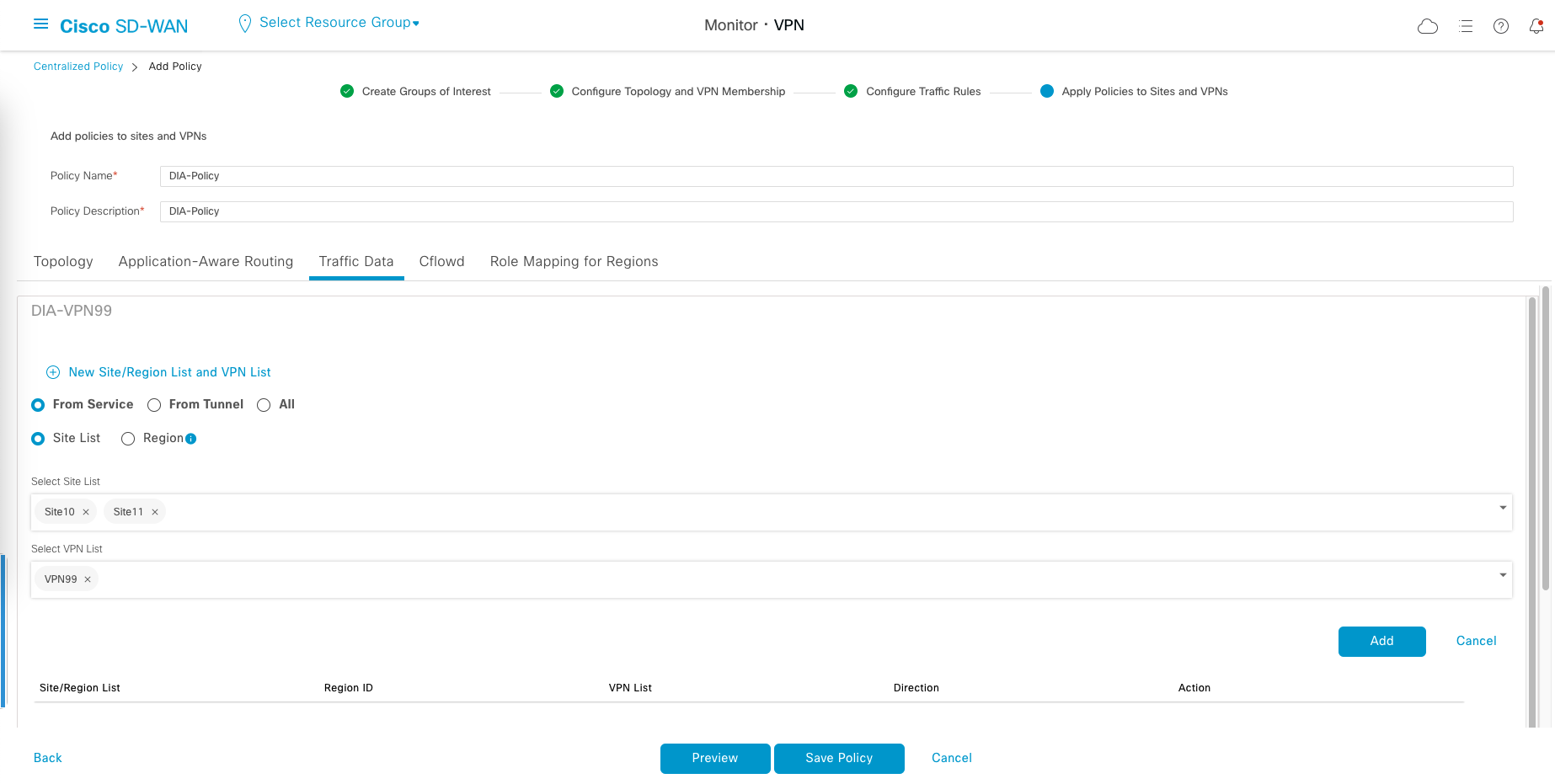
Last one, give the Policy a name and on Traffic Data, select the Service List and VPN List created earlier. Save the Policy
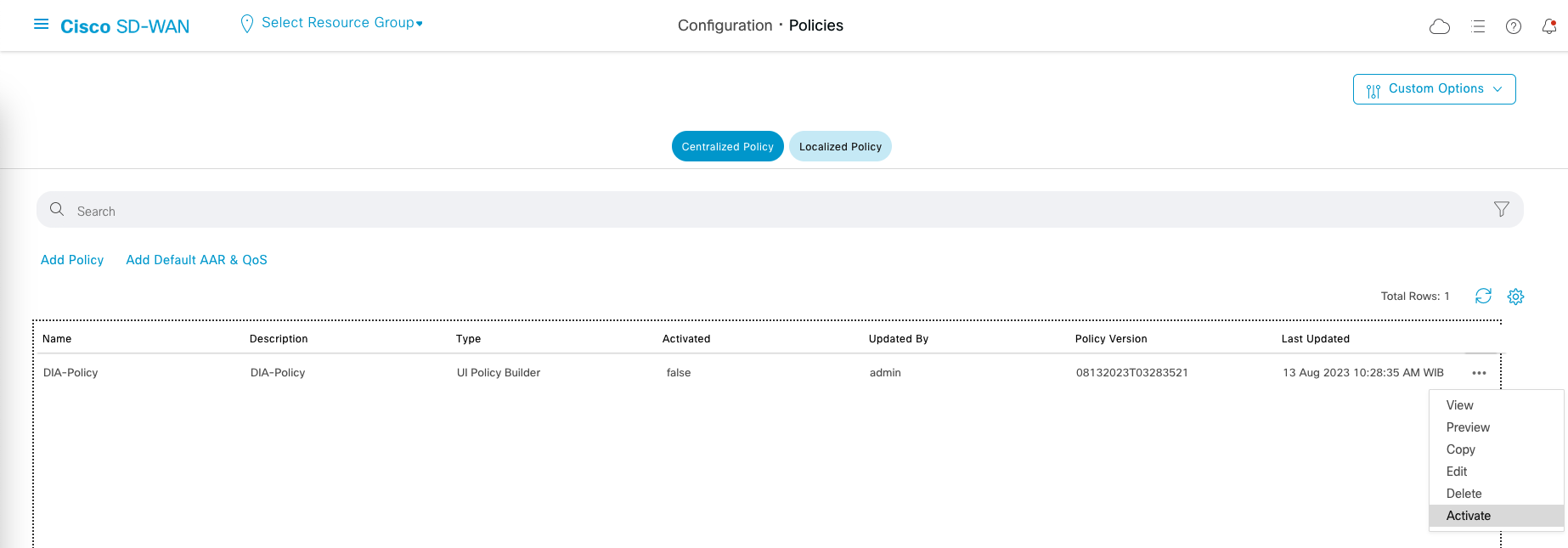
Activating the Policy
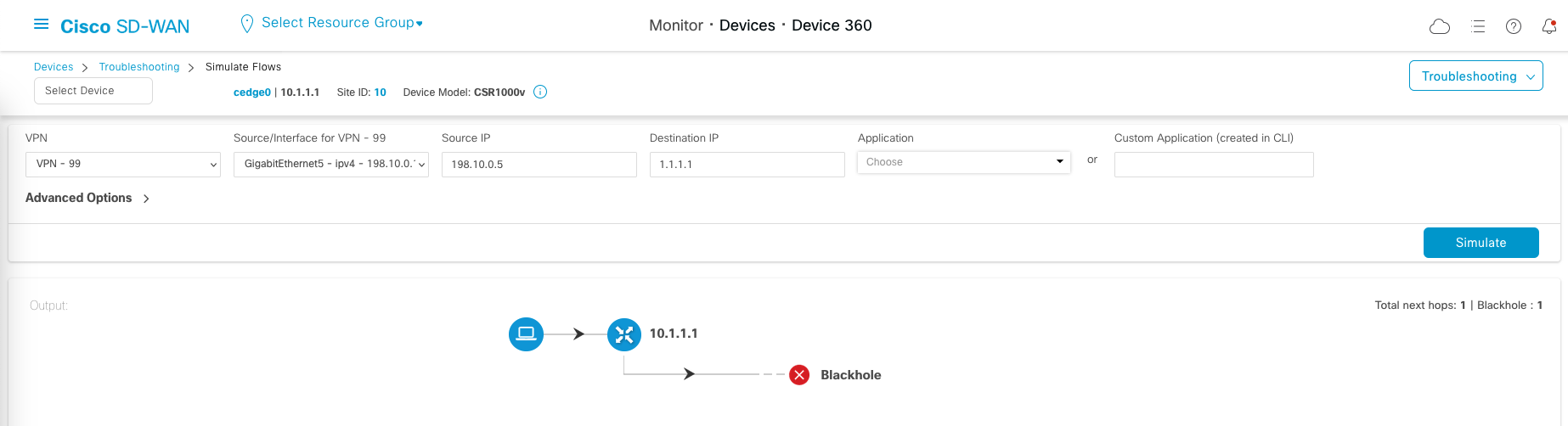
Right now if we try to access the internet from an endpoint on the branch router, it won’t have the route for that
So let’s activate the DIA Policy
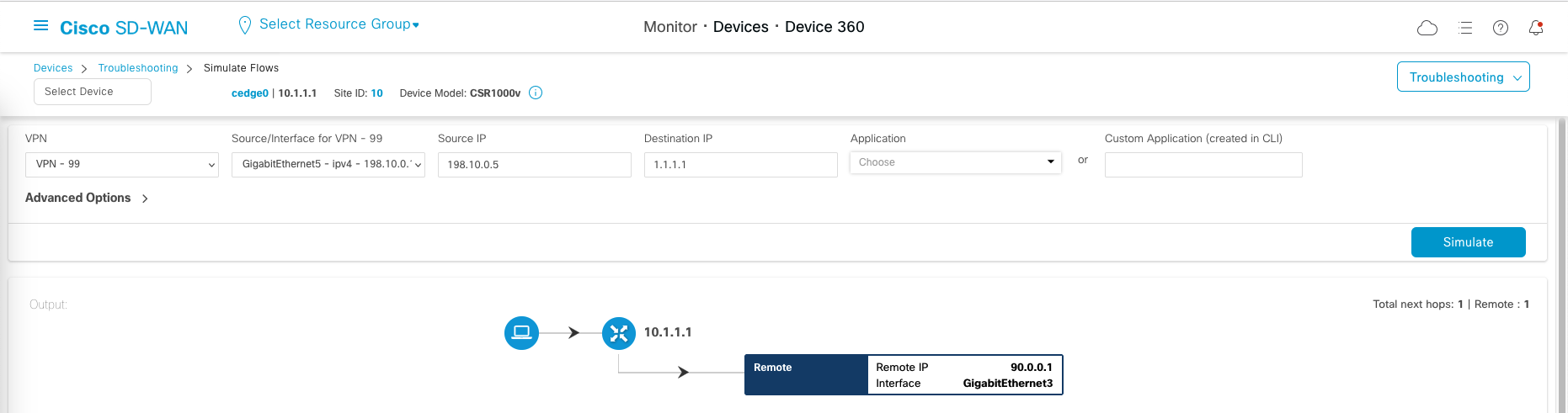
And now if we try simulating an access to internet, it will have a route
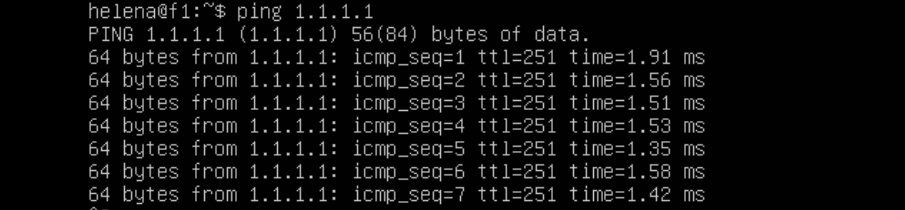
Trying it on the actual end device proves the same
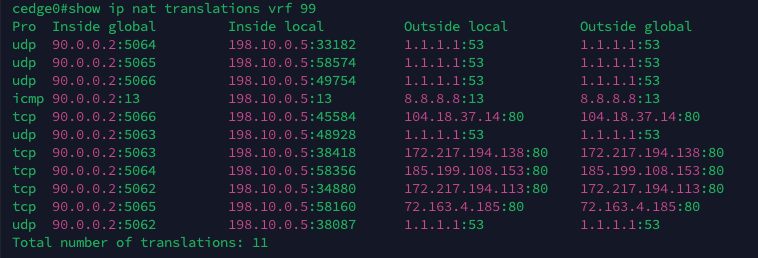
If we take a look at the edge router, we can see the NAT process is working as intended
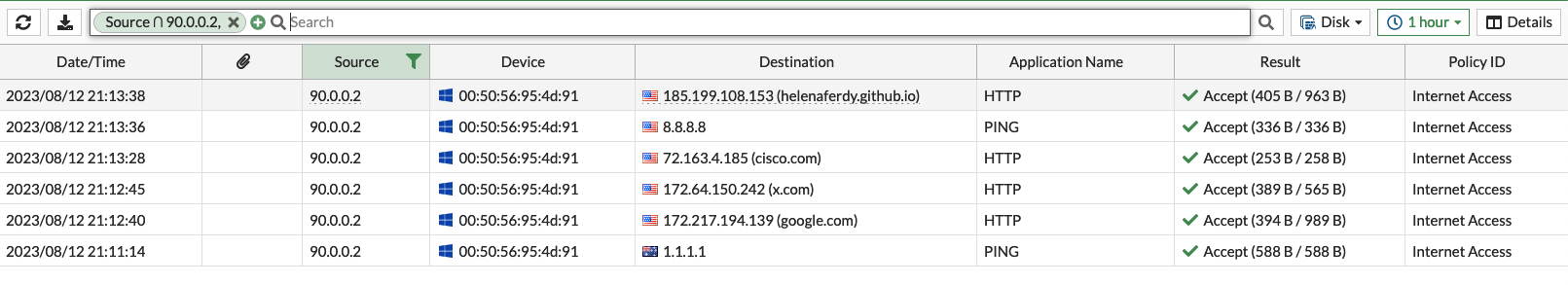
And inspecting the traffic on the firewall also shows that the IP going outside is the edge router’s internet facing interface